-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
-
A new Android malware loves users' love of selfies. How much? Enough to ask them to take one so that it can steal access to their accounts, and potentially steal their identity. The unnamed malware masquerades primarily as a video codec or plugin. In some cases, it arrives as a fake Adobe Flash Player app, a tactic which other Android malware including Marcher and Android/Spy.Agent.SI have employed. Amusingly, in at least one of the instances shown above, the attackers have called their malicious app "Abode Flash Player" rather than Adobe Flash Player. Regardless of the disguise, the end result is always the same. If successfully installed, the trojan asks users to agree to a number of permissions, at which point it idles and lays in wait. For what? For a user to have any reason to enter in their credit card details. It's at that point the malware activates, explains McAfee researcher Bruce Snell: "It displays its own window over the legitimate app, asking for your credit card details. After validating the card number, it goes on to ask for additional information such as the 4-digit number on the back." Once the trojan has collected all of a user's financial details, it then sets its sights on obtaining a user's personal information, including their name, date of birth, age, mailing address, and even a photo of the front and back sides of their ID card. For its pièce de résistance, the malware asks for one more data bit: a user's selfie. That picture, along with all of the other pieces of information it has already obtained, is more than enough for an attacker to steal access to victims' web accounts. To protect against this malware, users should pay attention to what permissions their apps are requesting of them. Seriously, why would a video plugin require more than a couple of permissions? If an application asks for more rights than it should need to perform its advertised functions, move on and find another app that asks for fewer permissions. Later on, if a seemingly legitimate app begins asking you for all kinds of sensitive personal and financial bits of information, uninstall it immediately. No app should need a photo of you holding your ID except perhaps a mobile banking service. But if you need to send a copy of your ID anywhere, it's best to mail it via snail mail or better yet deliver it in person. Source: Graham Cluley
-
As a seasoned (some would say ‘power’) user you know how demanding good password selection can be – there are so many different things to consider. It’s a statement and a public performance; a password is a micro-haiku that lets the office newbie know they’re playing with the big boys when you hand them that careworn yellow post-it. It’s precious and you want to get it right because you only get one. YOLOAYORNOPNMWTAGIIS* as they say. Nothing says “I’m logical and good with numbers” like 123456 but is that really the real you? Where do your loyalties lie? Your head says pet’s name but your heart says sports team + championship winning year. And what about humour? Rude words are straight-up funny but the self-mocking, recursive genius of choosing password as your password is just so hard to pass up. And then there’s security. You’ve seen Swordfish and you made it through one and half episodes of Mr Robot. You know what’s what. You want people to think you care about security so you’re going to have to ruin that perfectly good password by putting a number on the end of it. It’s a minefield wrapped in another minefield surrounded by a minefield and, frankly, you could do without it. Thankfully help is at hand. We’ve put our heads together and come up with a simple and easy to understand, cut-out-and-keep guide to choosing impeccable passwords. *You Only Live Once And You Only Need One Password No Matter What That Awkward Guy in IT Said. If you want some advice that might actually help you… …check out our video that shows you how to pick a proper password. Source: Sophos
-
- 1
-

-
- micro-haiku
- password
-
(and 1 more)
Tagged with:
-
-
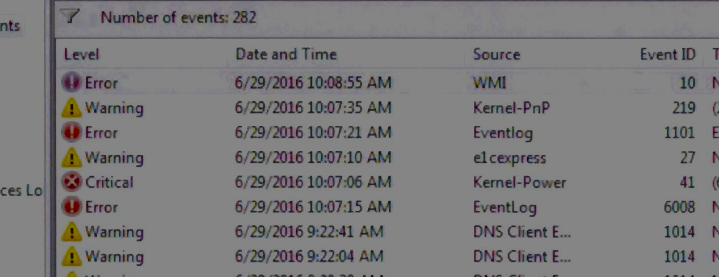
If you’ve ever browsed some of the internet’s seedier nooks and crannies, you might be familiar with a particular type of scam: The pop-up warning (usually accompanied by a loud, alarm-like sound) telling you that your computer has been compromised and you must call tech support immediately. To people who know better, it’s a minor nuisance but to people who aren’t as scam-savvy, it’s a ruse that brings in millions of dollars to jerks around the world, including a Missouri-based operation that has been shut down by the Federal Trade Commission. The FTC announced today that it has filed suit against the owners of four companies that allegedly used fake pop-up warnings to scam victims into paying for tech support they didn’t need. According to the complaint [PDF] filed in a federal court in Missouri, the St. Louis-area defendants — doing business under a number of names like Global S Connect, Yubdata Tech, OneSource Tech Support, and Technolive — would use third-party affiliate marketers to place pop-up ads online. However, the FTC says these ads were made not just to pop up and be an annoyance to the user, but to deceive the recipient into believing their computer had been compromised. The pop-up windows, often complete with warning siren sounds, were designed to look like they were coming from the computer’s operating system, as opposed to the user’s web browser. They sometimes implied that the warning was coming from Apple, Microsoft, or the user’s internet service provider. Users were told through these pop-ups that their computer was at risk and that they needed to call a special toll-free number now. Additionally, some alerts made it impossible or very difficult to browse away from the pop-up, further giving the impression that the computer was infected and impressing on the user a sense of urgency. The FTC says that when you called the number on the screen, you were connected to another defendant in this case: a call center based in India. There, an operator would instruct the victim on how to give the “tech support” staff remote access to the computer. After being connected, both the user and the operator could see what was going on on-screen. According to the FTC’s undercover investigation of this scam, the operator would show the victim the supposed evidence of a virus or malware on the device, but in reality this “evidence” was no indication that the computer had been breached. Using a Windows-based computer that the investigator knew was free from malware and viruses, the FTC investigator contacted the tech support number. According to the complaint, the operator brought up the Event Viewer, where a number of things were listed as “Error,” “Warning,” or “Critical.” In actuality, the events listed on that screen are in no way an indication of a viral infection. Similarly, the scammy operator opened the System Configuration window and allegedly pointed out all the important processes that had been “stopped” because they were not in “running condition.” Again, nothing to do with a virus or malware. If the victim is still on the hook at this point, this is when, according to the complaint, the scammers would hit them up for a $200 “one-time fix” charge, or for those who really wanted to spend money in exchange for nothing, a $400 year-long protection plan. Once the operator had the victim’s credit card info, that could have been the end of the call, but these alleged scammers apparently believe in some degree of verisimilitude, as the operator would remain connected to the victim’s computer for some time, doing “repairs” that the FTC claims may have actually left users’ computers in worst condition than before. The court has granted the FTC’s request for a temporary restraining order [PDF] against the defendants, and has frozen their assets for the time-being. Source: Consumerist
- 1 reply
-
- ftc
- pop-up warning
-
(and 3 more)
Tagged with:
-
Police in Thane, India, last week busted a call center devoted to Internal Revenue Service (IRS) scamming, detaining 700 people and arresting 70 of them for allegedly calling to threaten thousands of Americans with arrest over supposedly unpaid taxes. As the Wall Street Journal tells it, police said at a news conference on Wednesday that 200 police had raided 3 bland buildings in the Mumbai suburb the night before: Police said three nondescript office buildings on the edge of this booming Mumbai suburb were packed with hundreds of people posing as Internal Revenue Service officials in a scam that has vexed Americans for years. Thousands of calls went out from nine call centers on a daily basis as the scammers tried to trick naïve Americans into handing over bank details or sending gift cards to “settle” their cases. The workers were allegedly trained to speak with American accents. According to the Guardian, Paramvir Singh, the police commissioner of Thane, said that 70 workers at the so-called “scam center” have been formally arrested, and around 630 others are being investigated. Police expect “many more” arrests, Singh said. They’ve got plenty of material to go over as they investigate: conveniently enough, the call centers kept recordings of the calls. Singh explains, We had a mole go in to the call centers to verify. The best part is that they were actually recording all their calls. We have recovered 851 hard disks on which the calls were recorded, so we’re going through those now. Employees were allegedly telling their targets that they’d defaulted on tax payments and that the IRS was set to prosecute them, Singh said: They would give an American name and a batch number and tell the [uS] citizen that they owed the authorities $4,000, $5,000 or $10,000. They were instructed to stay on the phone and told that their homes would be raided by police within 30 minutes if they hung up. They made threats, they said: ‘You have to pay, otherwise you will lose your job, your money, your house.’ Police said that the crooks allegedly duped people into giving the callers their bank details. Then, they’d drain the victims’ accounts, transferring the money into a US bank account. Alternatively, the scammers told their victims to stay on the call and go to their nearest Target or Walmart store to buy prepaid gift cards – such as iTunes gift cards – and load them up with thousands of dollars. Police haven’t put an exact figure on how much money the call centers pulled in or whether they were targeting people from other countries. Singh did say, however, that the centers were running for over a year. He estimated that they’d managed to con thousands of people out of billions of rupees. One billion rupee converts to about $15 million USD, or about £12 million. Singh: We’ve been getting calls all morning from American citizens, people saying: ‘I think I got one of these calls. I think my money was stolen.’ At Wednesday’s news conference, Thane police played one of the call recordings they said they’d taken off the call center’s computers. The Wall Street Journal’s description: A caller with a heavy Indian accent told a man he owed more than $11,780 and was facing arrest within hours, a five-year prison term and $100,000 fine if he didn’t settle. The call was handed to a “senior treasury officer,” who told the man he can pay whatever he can afford right away by going to the nearest Walgreens to buy Apple iTunes gift cards worth $1,000. “Keep yourself on speaker and get dressed,” the man was told at one point. “We are running short of time [and] within two hours you will be taken into custody.” It turns out that the target in that particular call hadn’t actually fallen for the ruse: rather, he was just stringing along the caller to waste his time. The script for the calls is a familiar one: a variant is used in the “you didn’t show up for jury duty” scam. Both the you-owe-the-IRS-money fraud and the jury duty scam are the love children of fake support calls and lockscreen ransomware. Bogus support calls bludgeon you into paying for crooks to pretend to remove a virus infection that doesn’t exist. Lockscreen ransomware extorts payment of a pretend fine for a criminal offense you never committed. They all rely on the same type of pressure: they try to scare you to the point that your judgment jumps out the window. The details change, but the spook-you factor remains. So, “Your computer is infected and currently attacking our network with malware! We’re not happy with that, but luckily for both of us, we can help you. For a fee…” …turns into, “You’re delinquent on your tax payments! You’re in big trouble, bub, and we’re sending over the police right now! All you have to do to get out of this mess is pay this fine. Just give us your bank details, or maybe some nicely plumped-up gift cards, and we’ll let you off the hook.” A few years ago, we recorded a podcast about how to avoid fake support calls, and by extension any similar sort of high-pressure “pay a penalty, pay it now” call. If you know anyone who’s been targeted by this sort of scam, please urge them to give the podcast a listen, and help them gain the confidence to hang up at once. (These scammers are notorious for calling over and over again, ramping up the threats, if they don’t succeed right away.) LISTEN NOW (Audio player above not working? Download MP3, listen on Soundcloud or access via iTunes.) The calls may well look like they’re coming from perfectly legitimate places if you check out the caller ID numbers. But bear in mind that there are multiple reasons why a legitimate-looking caller ID might be bogus. It could be that the origin of the call is being spoofed. Alternatively, scam calls often come from outside your own country via a VoIP (voice over IP) service and emerge into the telephone network from some local provider, which not only makes the caller seem nearby but also saves the scammers a small fortune in call costs. What to do? Callers can be convincing: they may know a lot about you, may spoof the caller ID so the call looks like it’s legitimately from the IRS, and/or may use fake names and bogus IRS identification badge numbers. The IRS has published this list of things it never, ever does. They’re a tell-tale sign that a call’s a scam: The IRS will never call to demand immediate payment. Nor will legitimate IRS agents call about taxes owed without first having mailed you a bill. The IRS doesn’t demand that you pay taxes without giving you the opportunity to question or appeal the amount they say you owe. The IRS doesn’t require you to use a specific payment method for your taxes, such as a prepaid debit card. The IRS doesn’t ask for credit or debit card numbers over the phone. The IRS doesn’t threaten to bring in local police or other law-enforcement groups to have you arrested for not paying. Nor does the IRS use unsolicited email, text messages or any social media to discuss your personal tax issue. If you do get a phone call from someone claiming to be from the IRS and asking for money, the IRS has this advice: If you know you owe taxes or think you might owe, call the IRS at 1.800.829.1040. The IRS workers can help you with a payment issue. If you know you don’t owe taxes or have no reason to believe that you do, report the incident to the Treasury Inspector General for Tax Administration (TIGTA) at 1.800.366.4484 or at www.tigta.gov. You can file a complaint using the FTC Complaint Assistant; choose “Scams and Rip-offs” and then “Impostor Scams.” If the complaint involves someone impersonating the IRS, include the words “IRS Telephone Scam” in the notes. Source: Sophos
-
- busted
- call center
-
(and 2 more)
Tagged with:
-
Amazon has reset some customers’ passwords and asked them to change them, according to reports. Amazon says that during “routine monitoring,” it stumbled on a set of email and password sets posted online. Amazon isn’t the only online service to check for reused user credentials: both Facebook and Netflix prowl the internet looking for your username/password combos to show up in troves of leaked credentials. From Amazon’s message, sent to an unknown number of customers: We don’t know the size of the emails/passwords list that Amazon discovered. Nor do we know where, exactly, the credentials were found. All we know is that the drop spot wasn’t on anything Amazon-related. There have been scads of breaches recently. The user credentials could have come from the recent LinkedIn breach, for example. Other potential sources for the Amazon data set include the MySpace mega-breach, the Tumblr breach, or from the Yahoo breach of half a billion accounts. With each breach comes an increased chance that a reused set of login details will be discovered and potentially used by crooks to gain access to any account set up with those details. Amazon’s advice: Hallelujah and amen to all that! This is just one more example of why it’s such a bad idea to use a password twice. For more good reasons, here’s a detailed explanation of the dangers of password reuse. So yes, please do as Amazon suggests and change your password, not just on Amazon but also on any other sites where you use the same login. Make sure each online account has a different password, and make them all strong! Source: Sophos
-
-
-
(Bloomberg) -- Samsung Electronics Co. will end production of its Galaxy Note 7 after reports that replacement phones are exploding like the defective first batch that triggered a global recall. Here’s an explainer on what owners can and should do next. What do I do first? Turn it off. Samsung is advising all consumers to power down the $900 smartphone immediately and contact the seller. While the company hasn’t confirmed the new versions are prone to exploding, it’s not taking any chances while it investigates. But there haven’t been any problems with mine? Doesn’t matter. Whether it’s a model affected by the first recall or one of the replacements offered since late last month, Samsung says keep it turned off. It is giving customers the option of sending it back. Where do I take it? Back to where it was bought, whether that’s a carrier, website or retail outlet. Samsung is covering the cost of shipping Note 7s and offering a full refund on the phone and its related accessories. What if I want another phone? Most carriers are offering alternative devices. Customers opting for another Samsung phone, such as the Galaxy S7, will get refunded the price difference and any accessories. Those sticking with Samsung phones in the U.S. will get a $25 gift card while customers in China are being offered a coupon valued at 300 yuan ($45). Will I be able to get another Note 7? No. The Note 7s are effectively off the market as Samsung called for partners to halt exchanges and sales. The company’s decision to end production means it will scrap this model and instead focus on a Note 8 for 2017. What if I don’t want another Samsung or a refund? Most carriers are letting customers choose something else from their range. Whether that is Google’s upcoming Pixel, a just released Apple iPhone or other brands such as LG and Motorola. Do other Samsung phones have the fire problem? The company says no, the problem is isolated to the Note 7. Source: winsupersite
-
- defective
- galaxy note 7
-
(and 2 more)
Tagged with:
-
Those were the days.....
-
That's too funny. How big is the hard drive, 40 GB's?
-
The state of the PC industry is not looking great. According to analyst firm Gartner, worldwide PC shipments fell 5.7 percent in the third quarter of 2016 to 68.9 million units. That marks the "the eighth consecutive quarter of PC shipment decline, the longest duration of decline in the history of the PC industry," Gartner writes in a press release issued today. The firm cites poor back-to-school sales and lowered demand in emerging markets. But the larger issue, as it has been for quite some time, is more existential than that. "The PC is not a high priority device for the majority of consumers, so they do not feel the need to upgrade their PCs as often as they used to," writes Gartner analyst Mikako Kitagawa. "Some may never decide to upgrade to a PC again." The threat, of course, comes from smartphones, which have more aggressive upgrade cycles than PCs and have over time grown powerful enough to compete with desktop and laptop computers at performing less intensive tasks. Tablets too have become more capable, with Apple pushing its iPad Pro line as a viable laptop replacement. The threat to the PC industry is an existential one PC makers are feeling the pressure. HP, Dell, and Asus each had low single-digit growth, but Acer, Apple, and Lenovo all experienced declines, with Apple and Lenovo each suffering double-digit drops. Meanwhile, the rest of the PC market, which collectively ships more units per quarter than any of the big-name brands, is down more than 16 percent. These results do have some bright spots. The PC makers that did experience year-over-year growth did so largely on the strength of 2-in-1 devices and strong sales in the US, which indicate a clear direction for the market going forward. There’s also evidence that cheaper notebooks are becoming a more attractive replacement option as older computers get either handed down or given away. "While our PC shipment report does not include Chromebooks, our early indicator shows that Chromebooks exceeded PC shipment growth," Kitigawa writes. Source: Business Wire Via: VentureBeat
-
Yahoo has really been in the firing line in the past few weeks. First came the news that the company had confirmed a data breach of half a billion (5 × 108) records. The age of the breach was as worrying as its size: the data was stolen back in 2014, but Yahoo only reported it recently. The late publication of the report was not, apparently, out of any attempt to cover it up or to delay the news deliberately, but because the company only figured out something had gone wrong in August 2016. That news was followed by claims that Marissa Mayer, Yahoo’s CEO, had previously put the kibosh on a policy requiring passwords to be reset in the event of a breach, apparently because password resets, no matter how desirable they might be in an emergency, are annoying to users. (Mayer, you may remember, famously welcomed Apple’s iPhone fingerprint scanner by admitting she didn’t lock her phone, admitting that she “can’t do this passcode thing, like, 15 times a day.”) Although adopting a mandatory password reset policy doesn’t prevent breaches, and is always a last resort, it didn’t reflect very well on Yahoo’s security attitude to hear that it apparently decided to put ongoing user convenience ahead of security, even after a catastrophe. Next came allegations that Yahoo may have searched its email database for an unknown set of keywords at the official request of US authorities. Actually, as we wrote at the time, the “official request” was more of a “classified demand,” which is not at all the same thing. Nevertheless, Yahoo’s competitors wasted no time stating not only that they’d never received such a demand, but also that they’d have fought it publicly if ever they had received one. The latest bad news for Yahoo surrounds the fact that its mail forwarding service has recently been suspended, at least for anyone who isn’t already using it. Mail forwarding is pretty much what it says: email received by one server is automatically redirected to another, just as you might forward your PO Box in one town to a new box in another town if you moved house. One popular use for mail forwarding is as a temporary measure to help you migrate from one email service to another, so that you don’t have to keep logging on to two different websites until you’ve told everyone your new email address. In short, forwarding mail from service X to service Y often means that X pays, but Y benefits. That’s led to suggestions that Yahoo has done this deliberately as a sort of “lock-in”, in the hope of discouraging users from leaving the service following the recent negative news stories. We’ll give Yahoo the benefit of the doubt and assume that security is the cause. Mail forwarding is a risky feature, because a crook who manages to turn it on unlawfully can effectively take over your account in a way that isn’t as obvious as changing your password. Also, once a crook has forwarded your email, even if he does change your password to keep you out, he’s able to read it without logging back into your account. This means he’ll leave a slightly less damaging (or at least a more convoluted) audit trail if anyone ever decides to investigate. So, we’re prepared to assume that Yahoo’s new mail forwarding system has been temporarily suspended out of what the marketing folks like to call “an abundance of caution,” while the company conducts a security review on it. We’re assuming this isn’t a commercial trick aimed at discouraging dissatisfied passengers from getting off the train at the next station. What do you think? Has Yahoo done this to improve security or to control commercial damage? Source: Sophos
-
The kid had a plan: put up some music videos of his band on YouTube, plug into Google’s AdSense program to run ads alongside, make enough money to buy instruments, play music, get rich and go buy a mansion. Great plan! One little hitch: he got AdSense confused with AdWords. AdSense is the advertising service from Google that pays online publishers to display and make money off ads when visitors click. AdWords is the advertising service that charges online advertisers when visitors click on their ads. From that little hitch came a big surprise: it’s how the parents of José Javier, 12, from the Alicante town of Torrevieja, in Spain, wound up staring at a bill of €100,000 ($111,000 USD, £90,000 GBP) from Google, according to a report from the Spanish daily El País . Google, fortunately, has written off the amount and let José off the hook. The company’s Spanish offices sent a statement to El País saying that after analyzing the case, and after not having received any money from José, it was canceling the outstanding AdWords balance. Google said that like many online services, AdWords has age restrictions on use. As you can see on Google’s age limits support page, in Spain, you have to be 14 or older to open any type of Google account at all. The age limit goes up to 18+ to open either AdSense or AdWords accounts. At 12, José was obviously too young for any of Google’s accounts. In its statement, Google also referred to its Family Safety Center. But José’s mom isn’t swallowing the gentle rebuke implied by handing over that link. This is Google’s fault, she said, telling El País that it should never have been so easy for him to open the account in the first place. All José had to do was to provide a bank account number – one from an account his family had opened to save up for future expenses, like a driving license – and to reserve a product name. That was in mid-August. The charges started to rack up in early September. The balance started out modest, at around €15, but eventually climbed to €19,700. At €2,000, the account was already in the red. The bank called, and that’s when José’s parents first found out about the bill. They immediately blocked the account and returned the previous receipts. That didn’t keep Google from trying to load it up again with another €78,000. At first, they punished their son by restricting his computer use. But eventually, an analysis of the computer uncovered the innocent mistake. The boy’s parents retained a lawyer, but given that Google dropped the charges, they didn’t have to take the matter to court. José’s mother, Inma Quesada: He thought he was making money and not vice versa. [He] wanted to buy instruments for the band and stuff, but [one of his friends] also told him that if they got rich, they could have a mansion. I guess that in the Tales from the “you should have read the terms of service!!!” Crypt, this is small potatoes. After all, José didn’t accidentally sign away his firstborn. Source: Sophos
-
When scammers come calling, the temptation is to try and turn the tables on them. Some experts actually do, but is it a good idea for would-be vigilantes to follow suit? Florian Lukavsky, director of application security services firm SEC Consult, is an expert at these things. He scammed a group of whalers by playing them at their own game. Instead of targeting random employees hoping to worm their way into a system somewhere, whalers are more targeted, going after important execs with access to cash. Whalers impersonate the CEO or some other board-level honcho, convincing their target that they should send a large sum of money to a fraudulent account. Typically, they’ll pretend that it’s an invoice that needs paying. The numbers speak for themselves – in April, the FBI said that whaling attacks have risen 270% in the last three years. Attackers have walked away with $2.3 billion. Lukavsky played along with an incoming whaler, sending them an infected PDF that he said was a transaction confirmation. The malware harvested personal information including Twitter handles and Windows credentials from the attacker’s machine. His company then passed these details along to the police. SEC Consult says that it worked with law enforcement to pull this one off, and was able to give the information to officers, but most of us aren’t experts in this field, and don’t have police co-operation. We’ve seen cases where individuals have turned the tables by effectively trying to hack back. And there are other variations on this theme, such as Japan’s cyberweapon virus, which was designed to automatically seek and destroy attackers. Manipulating other people’s computers – to seek revenge or to fix them – is a bad idea, and not just for the reasons that Naked Security has laid out here. The biggest problem for civilians who would hack the hackers is that altering your attacker’s computer in any way is simply illegal in many places. In the UK, for example, the Computer Misuse Act explicitly forbids you to secure access to someone else’s machine. In the US, the Computer Fraud and Abuse act says much the same thing. This means that you could technically be prosecuted for knowingly fiddling with an attacker’s computer. Do governments hack back? Of course they do. Law enforcement, military and intelligence operatives are all authorized to intrude on targets’ computers, but there’s a difference. There is legal approval at a high level, and then at least theoretically a chain of command and an audit trail that documents exactly what is being done, how, and why. That doesn’t exist at an individual or company level, though, and hacking anyone’s computer – even if they’re trying to scam you out of millions – is a form of vigilante justice that could easily get out of hand. All kinds of unexpected things can happen along the way. You may be infecting the wrong machine, as attackers have a tendency to compromise other people’s computers and launch their attacks from there. Or there’s a risk you may end up incurring some form of physical retribution from your attacker, who may know a lot about you. If hacking back became a thing, then we’d be living in the wild west again, with vigilantes who were just as culpable as their attackers. And innocent users would doubtless be caught in the crossfire. For most of us, the best form of defence is not offence, but education. Take the lady who posts detailed public service announcements on Craigslist warning vulnerable young students how to spot an online rental scam. She hacks public awareness, which is a far safer thing to do. After all, knowing how to spot a scammer and disengage immediately is one of the best ways to protect yourself. It’s also a lot less work. Leave the Jason Bourne stuff to the professionals. DEALING WITH FAKE SUPPORT CALLS Here’s a short podcast you can recommend to friends and family. We make it clear it clear that these guys are scammers (and why), and offer some practical advice on how to deal with them. (Originally recorded 05 Nov 2010, duration 6’15”, download size 4.5MB) Source: Sophos
-
I think that they are both disgraceful. For the first time in forty years, I'll not be voting in the presidential election.
-
https://www.youtube.com/watch?v=o6TfhWY6WoI Microsoft is building a Windows 10 version of its famous Paint tool. While the software maker has barely updated Paint in recent releases of Windows, the new Paint app will be completely overhauled. Twitter user WalkingCat has discovered video demonstrations of the new app, and it's clearly designed with Windows 10 in mind. A launch video notes that the new "Paint Preview" app includes all the familiar features of the regular version of Paint, but Microsoft is adding in 3D object support — an ideal addition for HoloLens. Paint Preview users will be able to create 3D objects, and annotate them freely. Microsoft has a range of markers and art tools to help artists create objects, and brushes that can be used directly on 3D objects. All of the tools appear to be pen- and touch-friendly, with an interface that mixes 3D models, 2D images, stickers, and community tools for 3D content. This isn't the first time we've seen evidence that Microsoft is building a Windows 10 version of Paint. Screenshots leaked of the app back in May, but it appears the app has progressed since then. Microsoft appears to be testing early "alpha" versions of the Paint app, and the videos indicate it could be ready to be released publicly soon. A new version of Paint for a new Surface The timing of the Paint videos come just hours after Microsoft revealed it's planning to hold a special event in New York City later this month. Microsoft is widely expected to unveil a new Surface device at the event, with rumors suggesting it will be an all-in-one desktop PC. Sources familiar with Microsoft's plans tell The Verge that any potential AIO PC will be aimed at creatives. Microsoft is said to be working on software and hardware that will enhance the use of stylus, touch, and traditional inputs on a full desktop PC. Microsoft's new Paint app for Windows 10 will play into this plan, alongside apps from third parties. Any potential Surface hardware will compliment the company's software improvements. The Verge will be reporting live from Microsoft's October 26th event. Source: WalkingCat (Twitter)
-
-
Do you use the same password for multiple sites? Do your eyes glaze over after sites like LinkedIn or Yahoo get massively hacked and, like clockwork, the security wonks come wagging their fingers at you for reusing your passwords? Do you shrug and say “Hey, it’s not my job to keep those sites from getting turned upside down and shaken by their ankles until all the data tumbles out – it’s theirs!” If any of that rings a bell, you’re not alone. Either you need to take a nap, and/or the people who write security warnings need to figure out how to make it all simpler for users, because many of us are suffering from a common malady called security fatigue. That’s what it’s called in a new study from the National Institute of Standards and Technology (NIST) on what makes computer users feel hopeless and act recklessly. The study defines security fatigue as “a weariness or reluctance to deal with computer security.” One of the study research subjects put it this way: I don’t pay any attention to those things anymore… People get weary from being bombarded by ‘watch out for this or watch out for that.’ Brian Stanton, one of the study’s co-authors and a cognitive psychologist: The finding that the general public is suffering from security fatigue is important because it has implications in the workplace and in people’s everyday life. It is critical because so many people bank online, and since health care and other valuable information is being moved to the internet. If people can’t use security, they are not going to, and then we and our nation won’t be secure. The study was published this week in IEEE’s IT Professional. It surveyed subjects ranging in age from their 20s to their 60s who come from a diverse mix of suburban and rural areas and who hold a variety of jobs. The researchers focused on people’s work and home computer use, specifically about online activity, including shopping and banking, computer security, security terminology, and security icons and tools. Another of the study’s co-authors, computer scientist Mary Theofanos, said the researchers didn’t even have security fatigue in their sights when they set out to do the study. It just oozed out of all those fed-up people, she said: We weren’t even looking for fatigue in our interviews, but we got this overwhelming feeling of weariness throughout all of the data. Years ago, you had one password to keep up with at work. Now people are being asked to remember 25 or 30. We haven’t really thought about cybersecurity expanding and what it has done to people. Indeed. Here’s what it’s done to one study participant quoted by NIST: I get tired of remembering my username and passwords. Right about now is when security people will say, “Well, you shouldn’t have to remember your passwords – whether it’s 10 of them or 100! That’s what password managers are for: they’re applications that remember your passwords for you!” Another study subject: I never remember the PIN numbers, there are too many things for me to remember. It is frustrating to have to remember this useless information. Security wonk line: “Password managers can store secure notes, too, so you don’t have to remember PINs, either!” All you have to do is install a password manager on your mobile devices and desktop. Then when you want to get at, say, your bank’s site to do a little banking from your phone, you just have to start the password manager by pecking at your phone’s teensy tinsy keyboard to input your one very, very strong master password (which, OK, yes, you do have to come up with [here’s how!] and yes, you do have to remember that one), search for the bank’s URL in your password manager’s vault, launch it, then… um… watch as it gives you an error message and fails to log you in, so you launch the bank’s app separately, switch back to your password manager, copy the password, switch back again to the bank app, paste in the bank site password, and presto! Another slice of your life has dribbled away for the cause of cyber security. “Umm… NO!!!,” much of the world says to all that, including this tired lab rat: It also bothers me when I have to go through more additional security measures to access my things, or get locked out of my own account because I forgot as I accidentally typed in my password incorrectly. The multidisciplinary research team found that the majority of average computer users “felt overwhelmed and bombarded,” got fed up with being on constant alert, having to adopt safe behavior, and trying to understand the nuances of online security issues. Too many security decisions than they can manage leads to decision fatigue, which leads to security fatigue, which leads to feelings of resignation and loss of control, which in turn lead to just avoiding those decisions entirely. What fills in that gap: very bad choices – including, for example, using the same password multiple times – impulsive behavior, and ignoring security rules. Some of the other notions that feed into security fatigue: Why would a cyberattacker target me? I’m not important enough for anyone to want my information, and I don’t know anyone who’s ever been hacked. Safeguarding data is someone else’s responsibility, be it my bank, an online store or someone with more experience. How am I supposed to protect my data when big organizations can’t even do it? Stanton and Theofanos suggest that to fix this situation, it will take a multidisciplinary team of computer security experts, psychologists, sociologists and anthropologists working together to improve computer security issues, including behavior. The researchers offered these three ways to ease security fatigue and help users maintain secure online habits and behavior: Limit the number of security decisions users need to make Make it simple for users to choose the right security action Design for consistent decision making whenever possible Source: Sophos
-
-
Indonesian police have arrested a man for allegedly streaming porn on a billboard viewable to passing motorists in the south of Jakarta, the BBC reports. The AP has named the man as Samudera Al Hakam Ralial, a 24-year-old IT analyst, and reports that he has confessed. According to Jakarta Police Chief Muhammad Iriawan, the suspect claims that the porn broadcast was accidental. The billboard displayed footage from a Japanese porn film for 5 minutes on Friday before power was eventually cut off. However, that was long enough for an untold number of motorists to capture video clips on their mobile phones, and the porn rapidly spread on social media from there. Outside of Indonesia, there are, of course, plenty of cases where jokesters have messed with road signs. They’re typically portable road signs: the kind that usually display messages to inform drivers that an exit’s closed, or that there’s construction work ahead, rather than spreading updates about things like… Zombie genitalia ahead Donald Trump is a shape-shifting lizard The more simple reference to “POOP” A warning about a British invasion A warning about an incursion of Daleks Zombies ahead, as in, more than just zombie genitalia A recommendation to Drive Crazy Y’all We could add “porn on billboards” to the list of defaced public signage, but it’s a discordant mix. Unlike the cases above, the Indonesia case isn’t amusing, given the high-stakes penalties Indonesia could impose. Even in the US, which has a more relaxed approach to porn, messing with these signs is a serious crime: it’s a third-degree felony punishable with prison time. Learn More Iriawan told news outlets that Ralial could face up to 6 years in jail for the crime. Online porn is blocked in the Muslim-majority country of Indonesia, and the penalties for breaking its anti-porn laws can be harsh. Passed in 2008, Indonesia’s Anti-Pornography Law bans manufacture, production, reproduction, copying, distribution, broadcasting, importing, exporting, offering, reselling, renting or providing pornography, which is defined to include nude images. Iriawan has said that the perpetrator could be charged under either that law, which carries a prison sentence of up to 12 years, or under the Electronic Transaction Law, which carries a maximum prison sentence of 6 years and a fine of 1 billion rupiah ($77,000). Indonesia has in the past banned Tumblr for distributing porn, as well as Imgur, Reddit, and video-sharing website Vimeo. The country has also ordered social networking sites to remove any emojis representing same-sex couples. The IT analyst was arrested in his office. He allegedly pulled off the stunt after having spied login details displayed on the billboard. In other words, the highway equivalent of scribbling a password onto a sticky note affixed to a monitor. He snapped a photo with his phone, then logged in from his office. That adds up to two security blunders: displaying a password where anybody and everybody could see it, and taking advantage of that fact by using those credentials. It’s like we always say: just because you leave your window open doesn’t justify a burglar breaking in. The same goes here too: just because you find a password doesn’t make it OK to use it. It’s still trespassing, and the law doesn’t take kindly to it. Source: Sophos
-
It worked on my Windows phone. Good link Tony!