-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
-
When you update to or install Windows 10 there are quite a few first party apps that are installed at that time. Many of them are key elements of the operating system including Mail, Calendar, Groove Music, Movies & TV, Sports, Money and others. However, there are a couple that are installed by default that are not as critical to the OS such as Candy Crush and the Get Office app. Attempts to uninstall these non-critical apps meet with mixed success. Sometimes once removed they stay gone but many times they show back up as an update in the Windows Store. Luckily Candy Crush does not push any notifications to the Action Center but the Get Office app does even if you already have Office installed. However, you can use the built in Notifications & actions settings to prevent any further announcements from Get Office. Step One: Open Windows Settings for Notifications & Actions Open Windows Settings using the WINDOWS and I keys or using the Windows Settings icon on the Start Menu. Select Notifications & actions and then scroll down on the right hand side of the window until you find the Get Office entry. Note: The Get Office app will not show up in this list of apps until it has sent at lease one alert to the Action Center. Step Two: Turn Off Get Office Apps Notifications This is the easy part - just toggle the On/Off button shown in the above screenshot to Off and you will not see any further alerts in Action Center from the Get Office app. Bonus Tip You can use these steps to silence and/or customize the notifications from any app that is installed on your Windows 10 system. The only caveat is that the app you want to customize must have sent at least one alert to your Action Center so it shows up in the list. -------------------- Source: winsupersite
-
- apps
- get office
-
(and 1 more)
Tagged with:
-
There was an “anomaly” today during testing of a SpaceX rocket at Cape Canaveral… the kind of “anomaly” that creates a spectacular fireball, goes “BOOM,” and leaves a smoke plume in the sky. Happily, nobody was hurt during the incident. However, one very expensive piece of high-profile technology went BOOM along with. That tech would be a broadband satellite meant to expand Facebook’s Internet.org access, as Recode reports. The payload was meant to be launched on Saturday (Sept. 3), and now will not be launching at all because much of it (and the rocket) has been reduced to its component atoms. In a statement, SpaceX said it “can confirm that in preparation for today’s standard pre-launch static fire test, there was an anomaly on the pad resulting in the loss of the vehicle and its payload. Per standard procedure, the pad was clear and there were no injuries.” The of the “anomaly” gives a pretty good sense of just how big an explosion it was. Scroll ahead to the 1:11 mark for the flames… and then wait until 1:22 for the sound to catch up: When Facebook CEO Mark Zuckerberg found out, he posted — where else? — to Facebook that he was “deeply disappointed” at losing the satellite “that would have provided connectivity to so many entrepreneurs and everyone else across” Africa, where he currently is. Facebook, however, does not have all its eggs in this one very expensive and disintegrated basket. “Fortunately,” Zuck continued, “we have developed other technologies like Aquila that will connect people as well. We remain committed to our mission of connecting everyone, and we will keep working until everyone has the opportunities this satellite would have provided.” Source: consumerist
-
It doesn’t happen a lot, especially if you’re an Amazon Prime member, but occasionally if you order an item from an Amazon third-party seller you might end up with an item shipped in a Target box, or containing a shipping receipt from Walmart. It’s not illegal or a scam, but it probably means you paid more than you should have. CNBC’s Courtney Reagan writes about an experiment her team tried, ordering a bunch of identical items from Amazon, Walmart.com, and Target.com, shipped to various addresses around the country. They didn’t use an Amazon Prime membership, as Prime items are generally purchased directly from Amazon or fulfilled through Amazon warehouses. One item they ordered a bunch of were bookshelf sets. All four of the sets ordered from third-party Amazon sellers arrived in packaging still covered in Walmart labeling. Another item purchased from Amazon third-party sellers was Tide detergent. This time, CNBC reporters received detergent that had been purchased and resold from Walmart and Target. They know this because there were actual shipping orders from those sites in their respective boxes. It’s a practice known as “retail arbitrage,” which is just a fancy way of saying “buying stuff from Retailer A to resell on your own.” It’s nothing new. My first job ever was at a mom-and-pop grocery store, and I can recall a number of times when the owner bought things like cases of soda or bottled water at another store just to keep shelves stocked while waiting for a delivery from his distributor. There’s also an ongoing international legal battle involving Pirate Joe’s, a small Canadian retailer that stocks his store with items purchased at Trader Joe’s stores across the border. As CNBC points out, Amazon doesn’t allow third-party sellers to buy items directly from a competing online retailer and have it shipped to the customer. That doesn’t mean it doesn’t happen, but the instances in this story appear to just be cases where Amazon sellers are buying for less from Walmart or Target then re-shipping. Aside from clearing up the mystery of why the shelves you order from Amazon might come in a box with Walmart tape or stocking label, the story is a reminder that you should never assume Amazon has a lower price than websites for bricks-and-mortar retailers. For example, the shelves bought from Amazon sellers averaged $15.22 more than the $68 Walmart.com price, while the Tide from Target and Walmart was, on average $10.26 less expensive than the price charged by the Amazon sellers. So it just goes to show that doing a quick price check on a few e-tail sites is always a good idea. Source: consumerist
-
-

Internet Explorer has stopped working
allheart55 Cindy E replied to Tony D's topic in Tech Help and Discussions
It's good that you figured it out. -

Internet Explorer has stopped working
allheart55 Cindy E replied to Tony D's topic in Tech Help and Discussions
It looks like this might be malware Tony. https://www.hybrid-analysis.com/sample/e9502f90bdae6a285a7f0865dbfa51d42665b7d5579dff3edecf8aa5e5b3c212?environmentId=1 -
-

Internet Explorer has stopped working
allheart55 Cindy E replied to Tony D's topic in Tech Help and Discussions
That's weird Tony. -
Earlier this year, reports first began to appear that a historic data breach at Dropbox may have exposed tens of millions of user passwords, after a file claiming to contain approximately 100 million Dropbox account details was made available for anyone to download. At the time, security commentators such as Brian Krebs, Troy Hunt and myself urged internet users to be wary of the claims - as they had not been verified. After all, it seemed possible that the data had been collected from heavily-reported mega breaches at Tumblr, LinkedIn and MySpace. Now, however, Dropbox has confirmed to the media that a 5GB archive of files, containing the email addresses and hashed passwords for some 68,680,741 accounts, is genuine. "Our security teams are always watching out for new threats to our users. As part of these ongoing efforts, we learned about an old set of Dropbox user credentials (email addresses plus hashed and salted passwords) that we believe were obtained in 2012. Our analysis suggests that the credentials relate to an incident we disclosed around that time." Sure enough, Dropbox did warn that it suffered a security breach back in 2012, and that an undisclosed number of users' email addresses were exposed - although the company made no mention at the time that hashed passwords may also have been put at risk. Next time you log into Dropbox, the site will prompt you to choose a new password if it believes your credentials were at risk. Of course, it's unlikely that 68 million people will have to do that as many may have already changed their passwords since the breach occurred in 2012. My advice? Enable two-step verification on your Dropbox account. Whether your Dropbox account has been put at risk or not, this is just a bloody good idea. If you believe you might still be using the same Dropbox password as the one you were using in 2012, change it now. If you believe you might have reused that password anywhere else on the web, change it now. Get out of the habit of reusing the same passwords. It's a recipe for disaster. My recommendation is that you get yourself a decent password manager to generate and securely remember your passwords for you. The point about not reusing passwords cannot be underlined enough. When Dropbox was breached back in 2012, it appears that their systems were compromised because one of their staff had made the mistake of... yes, you've guessed it... reusing passwords. From Dropbox's 2012 blog post: A stolen password was also used to access an employee Dropbox account containing a project document with user email addresses. We believe this improper access is what led to the spam. We’re sorry about this, and have put additional controls in place to help make sure it doesn’t happen again. And yes, you might well ask why a Dropbox employee might have had such easy access to a file containing users' account details... For more discussion of the dumped Dropbox data, read this blog post by HaveIBeenPwned's Troy Hunt. Source: Graham Cluley
-
- data breach
- dropbox
-
(and 1 more)
Tagged with:
-
In the few markets where it exists — however sparingly — Google Fiber has managed to provide enough of a threat of competition that the nation’s biggest cable/telecom providers have been willing to cut prices and/or improve service. But a number of recent developments, including a report that the Fiber staff is being significantly downsized, have some questioning the future of the service. Last week, The Information reported that Larry Page, CEO of Google parent company Alphabet, had ordered the head of Fiber to cut the staff in half, to around 500 people. Google isn’t talking about that story, but a source familiar with the situation tells Consumerist that the report is inaccurate. What the company has said on the record is that it plans to continue investing in Fiber, but investing capital-F Fiber the company is not the same as investing in fiberoptic cable. Laying Fiber Is A Drag As Fiber has tried to enter new markets, it’s hit roadblocks like squabbles with incumbent telecom companies over access to telephone poles, or legal claims from existing competitors that Fiber is getting preferential treatment. The cost, hassle, and time it takes to build out an entirely new network in each city has led to some markets, including Portland (the one on the left side of the country) and Google’s Silicon Valley backyard, reportedly giving up hope of getting Fiber anytime soon. Faster, Cheaper, Better Thus, the company is looking at faster, smaller ways to quickly deploy Fiber access in some cities. For example, in Atlanta Fiber is simultaneously building its own line while paying to use fiber cables already run by the city. And in Huntsville, AL, Google won’t have to dig any trenches or squabble with the phone companies over pole access at all, as the city’s utility company is building out its own fiber network that Google (and possibly others) will pay to use. Google is taking a similar approach in San Francisco, utilizing more than 100 miles of city-owned fiber to connect to schools, office buildings, and apartments. In what was an apparent move to expedite the San Francisco deployment, Google bought a small gigabit broadband company called Webpass in June. Webpass already has fiber service deployed in parts of the Bay Area. But as Bloomberg pointed out in July, Webpass brings with it an efficient method for providing high-speed broadband wirelessly. Wireless Fiber Alphabet execs have made it known in interviews that they believe that Google may someday be selling Fiber without the fiber. Well, not entirely without fiber. Our source says the wireless tech being tested by Google isn’t intended to replace the Fiber network, but to speed deployment to end users, much like the way it’s easier and more convenient to have a WiFi router in your house than having to physically connect each device to the internet. Even so, that could avoid some of the more time- and money-consuming aspects of launching Fiber in a new market, or expanding existing Fiber service in the few cities where it already exists. It also raises questions, like will it be as fast as the gigabit speeds currently offered by Fiber? How will the data be encrypted? Will the wireless service be able to carry the live TV channels that Google sells in addition to broadband? And, most importantly… Will People Sign Up? Alphabet has remained remarkably tight-lipped about how many paying customers have actually signed up for Fiber. Even in its financials, Alphabet lumps Fiber in with Nest and Google’s Verily life sciences divisions (along with a few others) under the umbrella of “Other Bets,” so the best anyone without inside information can do is work with the numbers that are available. In the most recent quarterly report, Alphabet said that Other Bets brought in $185 million in revenue, but wouldn’t break it down by divisions. Earlier this year, Recode reported that Nest had brought in $340 million for the company last year, which comes out to $85 million a quarter. Assuming, for this exercise, that the Nest figure is the same this year, that leaves around $100 million. Let’s be incredibly generous and say that all of that remaining amount comes from Fiber. That would put the total number of Google subscribers somewhere between 250,000 and 500,000. Again, that’s making some rather huge assumptions and putting the full $100 million in revenue under Fiber, which is unlikely. Regardless, it gives you a general idea of where Google Fiber sits compared to Comcast and Charter, each of which have more than 20 million customers now, and it’s far short of the company’s reported former goal — according to The Information — of reaching 5 million subscribers within its five years. Granted, Alphabet’s market value is currently around $540 billion, more than three times that of Comcast, but it remains to be seen how long Alphabet will tolerate spending billions, but only making millions, on Fiber each year. Source: consumerist
-
- cable/telecom
- downsized
-
(and 1 more)
Tagged with:
-
-
Awesome! Thanks for letting us know, Dougie. You don't see those types of errors very often.
-
-
Do you mean that chkdsk won't run at all?
-
-
Amazon is the biggest online retailer in the US, but it's also not without problems. One of the ways Amazon became so big was by opening up its distribution network to third-party retailers, who use Amazon's warehouses and website to sell their own products. Buying from these retailers means you're not buying from Amazon proper, and that means you can be burned. How-To Geek has the story of how one author got scammed by a mini PC with a cracked version of Windows. When you're paying good money for a computer off a giant website, it shouldn't arrive with pirated software. And yet: The particular PC I purchased was sold by “MarsKing“. Sure, that’s a Chinese manufacturer I’ve never heard of, but it’s solid Intel hardware inside. It was also marked by Amazon as the “#1 New Release” in this category and had solid 4-to-5-star reviews at the time. It even had a “Prime” logo, which meant that it would be shipped to me from an Amazon warehouse. Looks legit, right? Nope! The PC came with a KMS Loader activation crack installed and was using a KMS key–a common way to activate pirated Windows licenses. Windows Defender found the KMS activation crack and complained about malware as soon as Windows Update ran automatically. After I left a bad review and returned the product to Amazon, MarsKing contacted me through Amazon with an offer: “We would like to sell you a new pc box with legitimate [Windows license] at 50% money off as apologize.” I didn’t take them up on it. As the author points out, the reason he was burned was because he was buying from a third-party seller. Since Amazon never really verifies or tests products that it sells on behalf of third parties, there's very little quality control in the system. In fairness, Amazon is still better than buying from a scammer on eBay or Craigslist. Amazon's customer service is designed to keep the customers happy, so you can always return products, and I've personally been offered small discount vouchers when my Amazon purchases have gone wrong. But still, you don't want to go through the time and hassle of buying and returning something that's fake. To that end, How-To Geek has some good, simple tips to use when buying off Amazon. Avoid products that are sold and shipped by third-party sellers, and instead look for things sold by Amazon.com, or at least shipped by Amazon. Reading reviews is also important, but that's its own minefield. Amazon reviews have become tainted as of late. There's an entire cottage industry dedicated to writing fake Amazon reviews, and many companies have started trading discounted (or free) products in return for favorable reviews. Reviews aren't worthless (yet!), but you should pay attention when reading them to try and avoid reviews that have been incentivized. Source: Yahoo Tech
-
- 1
-

-
- amazon
- distribution network
-
(and 1 more)
Tagged with:
-
If you’re worried about the security of mobile banking, you’re not alone. Mobile banking apps use a wide array of complicated passwords, biometric tools (like thumbprint or facial scanning), and two-factor authentication to make sure you’re you before “you” try to mess with your money. But preventing anyone from being able to guess how to log in to your account does no good if your phone’s got malware on it that gives would-be baddies a wide-open back door. As the Wall Street Journal reports, the presence of mobile malware designed to steal banking credentials is on the rise. The software, including programs like Acecard and GM Bot, has drawn the attention of both the FBI and U.S. banking regulators, according to the WSJ. There’s just not as much money in stealing credit card numbers anymore, as the seeming inevitability of wide-scale retail breeches means the market is oversaturated with stolen cards. Even criminal markets are subject to the law of supply and demand, and so that card data is just not worth as much to the criminal trying to sell it anymore, on average. That means the enterprising digital thief needs to take a new approach. This particular kind of malware spreads when a phone user opens a loaded text or advertisement. It then sits around on your phone until you open one of the targeted banking apps. When you do open your banking app, the software creates a customized overlay — a fake front — that lets it grab the credentials you put in as you put them in. And boom: your password’s stolen. According to the WSJ, Acecard alone has those overlays ready for 50 of the biggest banking apps. Phones are considered particularly vulnerable, because there are so many ways to get someone to open a link and so few users — not even a third, overall — use any kind of antivirus or anti-malware software. So how can you protect yourself? Know what your banking apps should look like, and don’t use them if anything about them looks “off.” Keep an eye on your statements and let your bank send you alerts for any unusual transactions. Try to avoid clicking any link that you don’t recognize, especially in strange texts — and consider trying one of the many free, reputable protection options for your phone. Source: consumerist
- 1 reply
-
- biometric tools
- mobile banking
-
(and 2 more)
Tagged with:
-
-
-
The hardware specifications for the Windows operating system lay out the minimum requirements to install and run the OS. Of course, many of us have likely installed Windows on a system that was under the published specs but still found that it would operate on that hardware. I even installed Windows 10 on an early Windows Vista era laptop and it did run on it - just not great. So here are the published minimum specs for the Windows 10 Anniversary Update - Version 1607 - that was just released on 02 August 2016. CPU 1GHz processor or SoC (System on a Chip) RAM 2GB for either 32-bit or 64-bit version of Windows 10; 1GB for 32-bit or 64-bit OS upgrade Hard Drive 16GB for 32-bit and 20GB for 64-bit version of Windows 10 Graphics Card Must support DirectX 9 or higher and have a WDDM (Windows Display Driver Model) 1.0 driver Display Resolution 800 x 600 pixels Obviously, the more hardware specs you can throw at Windows then the better it will perform on many levels but at a minimum Microsoft states that you must have the above specs to run Windows 10. If you want to take advantage of other new features in Windows 10 such as Windows Hello, Secure Boot, Hyper-V and Miracast you must have compatible hardware on your system. You can review the entire hardware requirements for Windows 10 Version 1607 aka Anniversary Update over on MSDN. -------------------- Be sure to check out all of our Windows 10 Anniversary Update Coverage. Source: winsupersite
-
- hardware specifications
- minimum requirements
-
(and 1 more)
Tagged with:
-
-
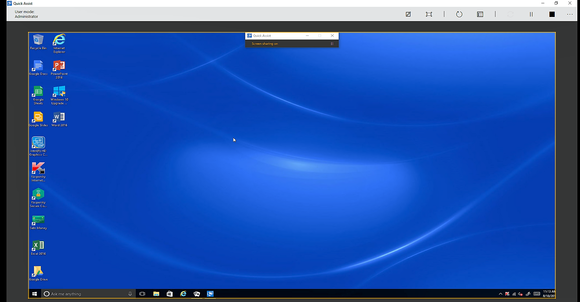
If you’re the unofficial “tech support” for your family, a new feature hidden deep within Windows 10’s Anniversary Update should be welcome news. It’s called Quick Assist. Anyone who works in the computer industry, or has a reputation for being technologically savvy, knows the sinking feeling that accompanies these words: “So I bought a new computer.” Those six words inevitably mean you’re going to end up on a long telephone call trying to explain something like how to save a web document as a PDF, with each participant becoming more frustrated by the minute. Wouldn’t you just like to perform the task for them and be done with it? Quick Assist makes that possible—and without the car ride. For years, Microsoft added a feature called Remote Desktop to the Professional versions of Windows, and you could use either it, or a number of other third-party apps, to remotely control your PC. (Remote Desktop Connection is still part of Windows 10 Professional.) Mark Hachman Quick Assist can be slightly hard to find. Quick Assist is a bit different: You’re not controlling your own PC from afar, but asking permission from another person to control their PC (or vice versa), and with the understanding that either party can disconnect the connection at any time. It can’t solve any hardware problems, like a mouse that’s out of batteries; however, it does allow a remote user to check if the mouse’s Bluetooth settings are properly configured and the drivers are up to date. Basically, Quick Assist lets you use your mouse and keyboard to remotely control a friend’s PC, doing everything that you could otherwise do on your own machine. Get started with Quick Assist One of the most challenging aspects of Quick Assist is just finding the darn thing. You can quickly launch Quick Assist by typing the app’s name in the Cortana search box, or by scrolling to Apps > Windows Accessories. (When my father bought his new PC, I simply pinned the app to his Start menu where it would be easy to find.) From there, Quick Assist makes it simple. Launching the app presents you with one of two choices: give assistance or get it. I chose the former, as I tested it remotely with my father’s new PC, an hour’s drive away. Mark Hachman This is your first choice: Do you need help, or are you providing it? It’s important to note that Quick Assist requires two people to initiate the connection; you won’t be able to remotely tweak your aunt’s PC while she’s out jogging. If you choose to give assistance, you’re first asked to log in with your Microsoft account. You’re then provided with a six-digit security PIN code that you must provide to the person you’re assisting within 10 minutes. (Both parties must enter the same code.) Again, Microsoft bends over backwards to help you, offering to email the PIN to your friend or family member, or save it to your clipboard to paste into a chat app. Mark Hachman The security code is active for 10 minutes, after which it will simply be replaced with another. (Note: The care that Microsoft takes to ensure both parties have the correct PIN made me suspect that entering an incorrect code might open up the remote PC to an unauthorized takeover by a stranger. Microsoft’s support staff says that’s not true. Instead, mistyping the PIN will simply cause the connection to fail.) Mark Hachman If you’re receiving assistance, you’ll be asked to input a code as well. Working within Quick Assist Let’s assume you’re the one giving assistance. Once Quick Assist is active, you’ll see a window displaying the other person’s desktop, which is surrounded by a border containing several icons. You’ll need to click inside that window to allow your cursor to take control of the other PC. Mark Hachman Quick Assist doesn’t come with any limitations; you can see someone’s entire desktop on your screen and run apps. The icons in the border allow you to annotate the window with digital ink, expand the Quick Assist window into full-screen mode, reboot the remote computer, or bring up the Task Manager. A “pause” and “stop” button also allows you to pause or disconnect from the remote PC as well. According to Microsoft’s support staff, navigating the remote computer gives you all the rights and privileges as that computer's owner: You can change settings, personalization options, and so on, provided that the remote user already has the appropriate permissions. (One thing you can’t do, however, is right-click a file and download it to your PC, though you could certainly open the remote PC’s email or chat app and send it that way.) Still, it’s another reason that the person receiving assistance should implicitly trust the person giving assistance—beware of phone scammers warning that your Windows system has “bad data” or a possible virus, and offering to “help” fix it! Mark Hachman There’s an annotation tool, though it’s slightly awkward to use with a mouse. Because Quick Assist allows the user receiving assistance to look over your shoulder, so to speak, he or she can follow along. When explaining what I was doing on my dad’s PC, I found that merely pointing to a menu item or setting with the mouse cursor did the trick. The annotation feature is there if you want to draw special attention to something, however. Unfortunately, the annotating feature in Quick Assist does not allow inking via the Surface Pen stylus, so you’ll have to use a mouse. Remember, Quick Assist uses a network connection, so tweaking the network settings may accidentally disconnect Quick Assist. The remote reboot option will also require some hand-holding, as the reboot still requires the remote user to type his or her password to log in. After the user logs in, though, Quick Assist will automatically reconnect. Remember, either party can also choose to disconnect from the Quick Assist connection, which should be as easy as closing the application. Mark Hachman You’ll receive a message when you reboot the remote PC. (Note: After I remotely rebooted my father’s PC, his login password didn’t work, he reported. I manually guided him into rebooting his PC once more, though, and that seemed to solve the problem.) Both my father and I concluded our test impressed with the Quick Assist tool. My father had never seen remote desktop software before, so he was fairly tickled by the notion of his cursor moving on its own. And for me, the freedom of being able to launch a quick session to show him how to use a feature was extremely convenient. Keep in mind, though, that Quick Assist opens the front door to your digital world. If you’re asking for help, remember that anything on your desktop or in your folders—be it “Christmas list 2016,” “Bankruptcy plans,” or “Honeymoon pics”—can be seen by your friend or family member, even if you’re watching them the whole time. Quick Assist is a powerful, convenient tool for remote assistance, but it requires trust on both sides. Source: pcworld
-
- anniversary update
- feature
-
(and 2 more)
Tagged with: