-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
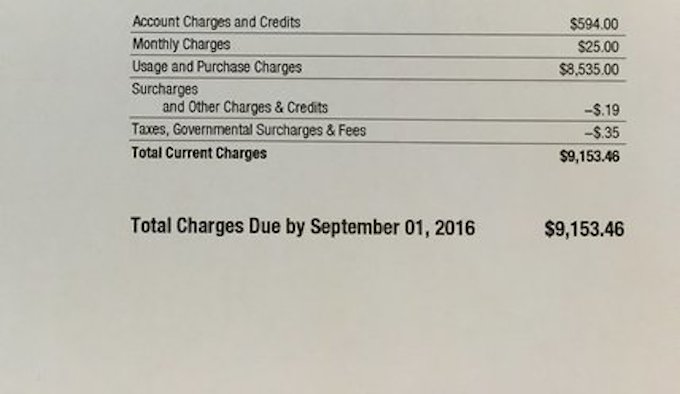
A Florida woman who says she barely ever uses her monthly allotment of data recently received a bill from Verizon Wireless for $9,153, claiming she had used 569 GB of data in the span of about 10 days. Every month since February, when she started using Verizon Wireless, the Tampa-area woman says she’s paid $118 for a package that includes 4 GB of data, The Plain Dealer reports. She says she’s never gone over her data allotment, which she uses to listen to Pandora and for work-related activities that don’t use more than 0.5 GB. Everything changed in July when she went out of town for a wedding. She had plenty of unused data, so even if there was on WiFi while she was gone, she figured it’d be fine. On July 21 Verizon sent her a text warning her that she’d used almost all of her 4 GB, so she paid $20 to get another 4 GB, considering she still had almost two weeks before the end of the month. An hour later, she got another text saying she had only 10% left on the data she had just purchased. Again, she chose to play it safe and upgraded her plan to 8 GB a month for another $20. Over the next few hours, she says she received anywhere from 40 to 50 texts telling her she had to buy more data. She turned notifications off because she thought it was a glitch, something she says she now regrets. She should have contacted the company at that time, she admits, but didn’t want to get stuck on hold with customer service. When it came time to pay her bill, she found she owed $6,480 for using 490 GB of data. A tech support employee told her her phone had pinged at Amazon.com more than 400 times in a span of days. On Aug. 1, a customer service representative told her she’d used 490 GB just since July 21. The next day, her phone was turned off and she was told her data usage had gone up to 569 GB — and her bill was now $8,535. “I told them that there was no way that I could have gone from 490 to 560 in a day,” she said. “The person said, ‘Yes there is.'” That was enough, and she left the carrier for T-Mobile — earning a $600 fee from Verizon in the process, which she says she will gladly pay. As for the rest of that bill, she doesn’t have answers yet from Verizon Wireless, and says will fight the charges, even if it goes to collections and damages her credit. She’s also planning to file a complaint with the Federal Communications Commission. “I understand that it is a big company and it cannot call everyone who appears to be going over his or her usage,” she says. “But I had never gone over my amount of 4 gigs. And then to get a bill that high makes you wonder.” We’ve reached out to Verizon Wireless for comment, as well as information on how such an excessive use of data could happen in such a short span of time. We’ll update this post when we hear back. Verizon data overages, other charges hit Florida mom for $9,100 [The Plain Dealer]
-
We learned today that the Windows 10 Anniversary Update, which was released more than six weeks ago, may not finish its full upgrade roll out until early November. Although many enthusiasts used the Windows 10 Update Assistant and the Media Creation tool from Microsoft to get the upgrade immediately there are likely many everyday users who are probably waiting on their system to automatically upgrade through Windows Update. We want to find out how many of you opted to force the update or are you being patient and waiting for it to arrive on its own schedule? Thanks for participating in our poll and letting us know! Source: winsupersite
-
What is the best way to test some of the protection related features on your Windows system like SmartScreen Filter and Windows Defender? One option, which we do not recommend because it is frankly very reckless, would be to just start browsing for malicious sites and waiting for one of them to try and drop a suspicious file on your system or serve up a phishing/malware laced site in your browser that wants to grab your information or infect your system. No - we definitely do not recommend doing something like that. However, there is great value in understanding how detection tools like the SmartScreen Filter works in Microsoft Edge and Internet Explorer and pushes alerts to your screen to protect you. The same thing goes for Windows Defender and knowing it is prepared to react to an infected file that arrives on your system. We could of course show you images of this process and those screenshots would give you an idea of how the process works but sometimes there is something about seeing your system react to those threats that really helps the learning process. That is where two tools, the Microsoft SmartScreen Demo Pages and the EICAR Anti-Malware Test File, come in handy because they give you a safe environment to trigger these system tools so you can see them in action. Microsoft SmartScreen Demo Pages This page consists of test pages that will show you how the SmartScreen Filter will react to threats in both Microsoft Edge and Internet Explorer. As you can see above, the test pages are separated into two categories with one showing how the URL reputation detection works and the other showing the same type of detection for downloadable files. You can click on each one of them yourself to see how SmartScreen will handle the detected threat and here are some explanations of how you can interact with these pages when it is a real threat. URL Rep Demos Is this phishing? Alert the user to a suspicious page and ask for feedback. This is the one scenario where you will be asked to verify if the site is safe or not and report that result back to Microsoft. The Phishing, Malware and Exploit pages will turn your screen bright red with a warning: The smartest move when you encounter a page that gives you a warning like this is to close your browser and not continue. However, if you are 100% confident that this site is not a threat then you can click on the More information link at the bottom for a couple of additional options: Again, be 100% sure that the page you are trying to reach is not a threat and select to either report that back to Microsoft or go ahead to the site. As you can see that is not recommended - do not visit that page just because you want to go there and browse it. A very large portion of computer security is using that organ that is between your ears and your mouse clicking finger - your brain! The Malvertising demo will show you an ad based threat in its own frame that has been detected and blocked: Finally, the Blocked Download will show you how any Internet downloads are blocked when they are detected by the SmartScreen Filter: App Rep Demos The last three SmartScreen Filter demos are for downloaded files and show you how your system will react to known good, unknown or known malware programs. Remember, you can click on the demos alongside of this article or on your own to see the protection in action on your system. Of course, a known good program that does not contain a threat will download normally and be saved to your system in your Download folder so there is no need to show what that looks like here and you can click that demo and download the file if you want to see it in action. However, it is likely you have already done this many times in the past. Unknown Program As you can see this is detected as a file that is not commonly downloaded and you are warned that it can cause harm. You have three options and again must engage the brain to evaluate where you are downloading the file from and if that is a safe source. You must be 100% sure about these details otherwise abandon the download and delete it from your system. Known Malware This warning means that the file you just downloaded matches a known signature for a malicious file. As you can see there are only two options - delete it or view your downloads folder. Once again, if you have any doubt about the origin of this file or the site you are trying to download it from then delete it and protect your system. Even the files that get downloaded with warnings from SmartFilter get tagged in the download folder as you view them: Go ahead and click on one of these demo files and see what happens - after the warning pops up click on the More info link. You will see this dialog box with an option to ignore this, which is at least the third warning about an infected file, and go ahead and run the file. Hopefully, three distinct warnings at this point will deter your intent to use this file - at least it should. However, this is any aware you are in control and Microsoft will let you ruin the file anyway despite their best efforts to warn you about the risk. EICAR Anti-Malware Test File As a prosumer or IT Pro you certainly do not want to be sending and receiving live virus samples to test Windows Defender however, the EICAR Test File can be used to safely test Windows Defender's detection process. As the Microsoft Malware Protection Center states this is not a malicious file but is used to check that your security software is working. As you can see any attempts I made to download the file triggered an alert from Windows Defender in my Alert Center and also quarantined the file on the system - the exact same process that would occur if you encountered a real threat. Here are the detection alerts in Action Center on Windows 10: This is the History tab in Windows Defender showing you the quarantined files that were detected on your system. After these files are no longer a threat you can delete them from your system on this same page in Windows Defender. So hopefully these test pages give you a sense of how your system will react when threats are detected and give you an opportunity to practice dealing with those threats and the related alerts on your system. As I said earlier, protecting yourself on the Internet from threats is a combination of using security software and employing the gray matter between your ears to avoid suspicious websites and downloads. Tools like the SmartScreen Filter in Microsoft Edge and Internet Explorer plus Windows Defender can go a long way to help protect us but if we ignore those warnings on multiple levels that is a recipe for disaster. In that case I hope you have a functioning backup of all your important documents and software because you are eventually going to need them. Stay safe, educated and protected out there! Source: winsupersite
-
- protection
- smartscreen
-
(and 1 more)
Tagged with:
-
A 14-year-old girl from Northern Ireland is suing Facebook after a naked photo was published on a “shame” page and repeatedly reposted. At a hearing in Belfast’s High Court, the girl’s attorney said that Facebook should have made blocking the image from being republished a “red-line” issue, the BBC reported on Thursday. Her barrister: A naked [14-year-old’s] picture was being put on a shame page. If [Facebook] had blocked it, all this subsequent publication of her naked image would not have taken place. Her lawyers claim that the picture was extorted from her and published over and over again online as a form of revenge. Facebook has claimed that it took the photo down as soon as it was notified about it. The girl, who can’t be identified, is seeking unspecified damages for misuse of private information, negligence and breach of the Data Protection Act. The judge reserved his decision on an application to have the case halted, The BBC reports. That means that he’s reserving judgment until he can research the issues and write a judgment that summarizes the parties’ arguments and his research results. It’s shocking to think of a 14-year-old being subjected to sextortion, but kids even younger — as young as 11 — have been victims of revenge porn. As far as keeping your kids safe when they’re online goes, there are tools that can help us do it. These include parental controls that let you set your children’s privacy settings, control whether they can install new apps, enforce ratings restrictions on what they can buy on iTunes, or that can even limit what type of app they can use. We’ve got more tips to keep your kids safe online here. And if you’re not even sure what your kids are up to online, this could help. Source: Sophos
-
-
-

TEENS REACT TO WINDOWS 95
allheart55 Cindy E replied to allheart55 Cindy E's topic in Tech Help and Discussions
No, Al actually went straight from Win95 to Vista. I remember he came on paltalk the night before his Vista computer was to be delivered. He was very excited about it. A couple of the guys decided to lie to him and they told Al that Fed-Ex and UPS just went on a huge strike and not to expect delivery of his computer. He got really upset and they thought it was funny. I told him the truth because I thought that was really mean. -

Did this forum change in the last year.
allheart55 Cindy E replied to Peter N.'s topic in Tech Help and Discussions
I've sent you a private message, Peter. -

Did this forum change in the last year.
allheart55 Cindy E replied to Peter N.'s topic in Tech Help and Discussions
Hi Peter, Yes the forum has changed names in the last year. We used to be Free PC Help Forum (Free PC Help Forum) We changed the name to PC Help Forums. If you tell me what your original user name was, I will gladly merge the accounts for you. (I think that your user name was @peterr) -
-
-
As the makers of recruiting platforms are happy to remind us, your social media self is extremely likely to be perused by recruiters who’ll either snap you up when they see the results or turn up their noses at, say, your posts about OMG how much you HATE your boss and hope he DIES! According to one such vendor, as of 2013, 93% of recruiters were likely to look at a candidate’s social profile, and 42% had been moved to give the thumbs-up or -down based on what they turned up. There have been various tools put forth that make it easier for employers to get at your “true” self. (And before you protest that our social media selves are not, in fact, our “true” selves, I need to point out that researchers say otherwise. “Disagreeable” or “non-conscientious” people are, in fact, more likely to emit the unpleasant aroma of, say, bad-mouthing peers and employers on social media.) Now, there’s another such tool to go beyond just plain old running a search on a candidate. Called The Social Index, the online service promises to rifle through the digital footprints of short-listed job candidates and present employers or recruiters with a report. That report is an infographic that, the company claims, maps out a candidate’s “personal brand.” It crunches data from Facebook, Twitter and LinkedIn. According to a report from Mashable, The Job Index focuses on those three social platforms partly because they’re common, but also because, typically, they’re the ones most relevant to a company’s client activities or reputation. It takes about 30 seconds for the candidate to be analyzed before their “social footprint” is ready. Within 24 hours the report will be delivered to both the client and the job seeker. It’s a lot faster than slogging through Google searches for a name. Plus, as the founder of the Australian company, Fiona McLean, points out, when you rely on search engine results, you can’t even be sure the profile you’re looking at is for the right person. As far as privacy goes, McLean points out that the system only looks at public information, and it doesn’t share people’s posts with companies. If it’s not online, then a client can’t see it in the report. The system maps out when, where, and how often people are posting. It also gives a timeline for your career, highlighting both the good – say, when you got promoted, or your average tenure – and the bad – say, unaccounted chunks of time that don’t reflect your being employed, or a brief average tenure that could point to a pattern of getting shown the curb after a few months. Like Klout, it also shows how much of an influencer you are: How many connections you have on any given platform, for example. The system also does some sentiment analysis to show how positive your digital self is. Employers will be able to tweak it to fit a given role. McLean gave the example of a job that requires a lot of social media interaction: if your profile shows that you don’t post much, that’s bad. I worked with someone early on who was hiring for a social media role, and they were getting a lot of people who were saying ‘well I know social media, I do a lot of it,’ but the reality was they knew the theory of it but couldn’t demonstrate it. …on the other hand, if you’re spending all day posting when social media interaction isn’t part of your gig, that’s pretty bad too, McLean said: If the role is a back office accountant and they are equally on social media between 10 and 4, the chances are, they are not doing the core part of the role as well as they could. But wait, isn’t it illegal to ask employees for their account logins? Illegal, as in, it’s against user policies to share your account passwords? Back in June, we got wind of a service that offered to scour potential tenants’ social media profiles for landlords. The service, called Tenant Assured, still hasn’t launched, but its plan is to provide detailed reports assessing rental applicants’ personality traits, creditworthiness and financial risk by directly accessing their Facebook, Twitter, LinkedIn and Instagram profiles, with the applicant’s consent. Consent needs to be given for either of these social media-mining apps. That still doesn’t answer the question, though: isn’t it illegal to demand workers’ passwords? No, it’s not, at least in the US. As it is, a number of US states have tried to make it so, but the US House has declined to ban the practice. At any rate, job candidates and tenants alike can decline to hand over access to their accounts. But if apps like Tenant Assured and The Social Index become widely used, will we even have a choice? My way or the highway or, in this case, pry way or the highway! Hand over access, or some day you could well find yourself being disregarded for an apartment or a job. When it comes to The Social Index, the small mercy is that they’re only going after publicly posted data. It’s yet another very good reason to clean up your past posts and to lock down your privacy. To maintain privacy, use privacy controls. Millions of Facebook users are oblivious to, or just don’t use, privacy controls. Don’t be one of them, and while you’re at it, don’t let your friends or family fall into that category. To see who can find the things you’ve shared, you can use privacy shortcuts and Activity Log to review your personal trail of glory and misdeeds. Go to Facebook’s Activity Log page for a list of your posts and activity, from today back to the dawn of your Facebook life. There, you can find stories and photos you’ve been tagged in, Pages you’ve liked, friends you’ve added, your photos, and photos you’re tagged in that are shared with Public. Besides photos we’re tagged in without our permission, most of the stuff that’s in our Graphs is up because we put it there. To further clean up our Facebook personae, we can always remove a tag from a photo or post we’re tagged in. As Facebook outlines here, you do that by hovering over the story, then clicking and selecting Report/Remove Tag from the drop-down menu. Then, remove the tag or ask the person who posted it to take it down. Also, to further lock down your profile, take a gander at these three ways to better secure your Facebook account. Source: Sophos
-
-
-
When police put your photo on a “Wanted” poster for violating probation on two counts of battery, it’s not the best idea to use that photo as your Facebook profile picture. A 42-year-old Florida man learned that lesson the hard way. Police arrested Mack Yearwood last Tuesday on outstanding warrants from Citrus County, on Florida’s Gulf Coast, according to local publication the Palm Beach Post. Police from the town of Stuart said on their Facebook page that the picture came from a “Wanted of the Week” poster. Beyond the bad judgment on what photo to use on Facebook, Yearwood also apparently forgot that he allegedly had a bag of weed in his jeans pocket. While police were taking him into custody, he asked to put on the pair of jeans, which were lying on the floor. Yearwood thus managed to pick up an additional charge of possession of cannabis under 20 grams. We have no indication that Florida police got fancy with facial recognition technology – or even that they thought to use Google reverse image search – to identify Yearwood. Learn More Rather, as a police spokesman told the Palm Beach Coast, an officer who responded to a disturbance on Monday night told other investigators about Yearwood’s outstanding warrants. An officer checked Yearwood’s Facebook page, and that’s where the Wanted poster photo showed up: according to the screen capture posted by police, that photo was updated on 2 March. That’s a good 6 months that Yearwood flaunted his “Wanted” status. Does that make him the new Crown Prince of Incriminating Selfies and “Come Find Me, I’m Over Here!” crooks? He’d be taking that crown from the felon who posted a selfie posing with his gun collection: a selfie that got him a jail sentence of more than 15 years. We better hold off on crowning Yearwood, for now: he hasn’t been convicted, and of course he’s innocent until proven guilty. And at least he didn’t send police a more flattering photo! Source: naked security
-
- "wanted" poster
-
(and 2 more)
Tagged with:
-
I’m a Linux guy, but I kind of like Windows 10. However, its luster has been wearing thin. First, there was Cortana’s eavesdropping. Then there was the insanely buggy Windows 10 Anniversary Update. Adding insult to injury, Microsoft now force-feeds us updates and gives us only 10 days to roll them back. But, thought I, I could still run Windows 7, my favorite Microsoft operating system, when I needed to run Windows. Wrong! I should have seen the handwriting on the wall. Back in January 2016, Microsoft announced that it would support new Intel Skylake-powered PC with Windows 7 and 8.1 only until July 2017. Just 18 months of support for a PC that’s likely to be used for over four years? I don’t think so. After much screaming by customers, Microsoft backed off on that plan.Windows 7 support will now expire on Skylake-powered PCs on Jan. 14, 2020, with support for Windows 8.1 ending on Jan. 10, 2023. Intel’s forthcoming Kaby Lake or AMD’s Zen chips. Only Windows 10 will be supported on the next generation of CPUs. Bad enough that I had to fight to keep Windows 10 off my Windows 7 PCs; now I can’t install it on new processors! Not fair, Microsoft, not fair at all. Microsoft told AMD, Intel and Qualcomm, with its 8996 CPU, to support only Windows 10. As an Intel spokesperson said, “We are committed to working with Microsoft and our ecosystem partners to help ensure a smooth transition given these changes to Microsoft’s Windows support policy.” Specifically, “No, Intel will not be updating Win 7/8 drivers for 7th Gen Intel Core per Microsoft’s support policy change.” What does that really mean? Will Windows 7 run on Kaby Lake processors? It should. The x86 instruction set has a long history, and Intel isn’t going to change what isn’t broken. That said, Windows 7 on newer processors might be glitchy. I don’t want to find that out after spending a grand for a brand-new, top-of-the-line computer. A goal of 1 billion Windows 10 users by 2018. Windows 10 has been adopted faster than any other version of Windows to date, but that’s not what Microsoft wanted. So, instead of trying more carrots — say, offering free upgrades again — Microsoft is resorting to the stick: You will run Windows 10 on new machines or nothing. Thanks, Microsoft. Thanks a lot. This just makes me glad that I’m a desktop Linux user. Linux, you see, will support the newest chips. Chromebook users can also look forward to running the fastest chips. Windows 7 and 8.1 users? Not so much. Source: computerworld
-
-
A bad malware signature caused Sophos antivirus products to detect a critical Windows file as malicious on Sunday, preventing some users from accessing their computers. The false positive detection flagged winlogon.exe, an important component of the Windows Login subsystem, as a Trojan program called Troj/FarFli-CT. Because the file was blocked, some users who attempted to log into their computers were greeted by a black screen. Sophos issued an update to fix the problem within a few hours and said that the issue only affected a specific 32-bit version of Windows 7 SP1 and not Windows XP, Vista, 8 or 10. "Based on current case volume and customer feedback, we believe the number of impacted systems to be minimal and confined to a small number of cases," the company said in a support article. One Twitter user who was affected by the issue said that he highly doubts only a small number of customers were affected, while another one reported that he's been on hold trying to reach Sophos Support by phone for over two hours. "An email would have been nice," one user told Sophos via Twitter. "I cannot imagine the costly overtime $ and panicked IT staff like myself working on this." Another user joked that this false positive actually removed some of his weekend. In many cases administrators will only need to clear the bogus alerts from the Sophos Enterprise Console, Sophos Central or Sophos Home by marking them as resolved or acknowledged, the company said. Users who encountered the black screen will have to reboot in Safe Mode, disable the Sophos Anti-Virus service from starting automatically and then boot into the OS normally. More detailed instructions are available in Sophos' support document. Sophos is not the first antivirus company to issue a bad definition that affected users' computers. To its credit, the company reacted promptly and fixed the issue in a timely manner during a weekend, but questions remain as to why in 2016 an antivirus program can still flag legitimate Windows system files as malicious. False positive detections used to be much more frequent years ago, but most antivirus companies have since built whitelists of known software to avoid such incidents. Windows files in particular should be a top priority for whitelisting because blocking or deleting them can leave a computer unusable. Source: pc world
-
- bad malware signature
- critical windows file
-
(and 2 more)
Tagged with:
-
Your fridge is getting so smart, security-software maker Kaspersky Lab thinks you probably shouldn’t trust it. As makers of household appliances fill their machines with computer chips to make them smarter, consumers and privacy watchdogs should beware the data collected by these objects and how it’s used, Marco Preuss, a director on Kaspersky’s global research and analysis team in Europe, said at the IFA consumer electronics conference in Berlin. "A fridge is no longer only a fridge, it’s now also a sensor collecting private information," Preuss said. "Vendors need to say what data they collected, where it’s stored and who’s using it, and regulators need to work on standards and requirements to make companies more transparent about this. It’s the only way to bring consumer trust back." The search engines and social networks of the world have made consumers more aware that information is being collected about their behavior and used for commercial purposes. The growth of the so-called Internet of Things will lead to millions of appliances coming online and harvesting data about people’s habits in their homes. At IFA, Samsung Electronics Co. showed off a refrigerator that sends statistics and pictures of the food inside to your phone. A 21.5-inch display lets family members leave each other messages, order groceries and share their calendars. Qingdao Haier Co., the Chinese company that bought GE’s appliances business, introduced a cloud-based robot to manage smart appliances and a mini-fridge that delivers chilled beverages via remote control. Kaspersky said manufacturers could learn a lot about consumers from the data that transits through such objects, and third parties would be very interested in getting access. "Do you really want your health insurance provider to know if your fridge has only beer and chocolate in it?" Preuss said. "Vendors need to think about the privacy of such information. Not everything connected and gathering data is allowed to share it." Arcelik AS, Turkey’s biggest maker of home appliances, unveiled a kitchen system that links with a smartphone and projects virtual control panels on countertops, removing the need for physical buttons and handles. Connected appliances can be found beyond the kitchen, and Kaspersky highlighted risks from objects such as power meters that “can know what you’re doing at home, when you sleep and when you leave the house, or even what TV show you’re watching." A majority of German consumers feel using digital tools exposes their privacy, according to a Kaspersky survey published in August. Of all respondents, 71 percent said they’re worried about internet companies collecting their personal data, and nearly 1 in 2 respondents said they had negative feelings about the digital future. For software and services companies, from Kaspersky to Symantec Corp. and Microsoft Corp., more objects coming online may be an opportunity to expand their own businesses. Source: winsupersite
-
- computer chips
- fridge
-
(and 2 more)
Tagged with:
-
-
If you’re hitting the road this holiday weekend, you might find yourself visiting some unfamiliar gas stations, ATMs, or kiosks that accept credit cards. The recent arrest in California of two men who are accused of draining $500,000 from US Bank customers’ accounts should remind people across the country and all over the world: be careful where you swipe your debit card, and be protective of your PIN. KCAL reports that the two men are suspected of multiple skimmer thefts, and they were caught in a sting by police. In these incidents, the suspects used a super-thin device about as wide as a credit card that captures the information on a card’s magnetic strip, and a pinhole camera fitted inside a device that blends in with the rest of the ATM. Here’s how to protect yourself from skimmer crimes: Use a credit card instead of a debit card, if you have one: you’ll have a chance to dispute the charges and won’t have to fight to get the cash back after it’s removed from your account. Cover your hand when entering your PIN: this is a tricky maneuver when using a drive-up ATM, but will keep a pinhole camera from capturing your digits. This keeps scammers from taking cash or cash advances out from your account. Jiggle any pieces of the ATM or kiosk that don’t seem to fit: if something looks like it isn’t part of the machine, it might be an extra card reader or a container for a pinhole camera. Source: consumerist
-
- atms
- credit cards
-
(and 3 more)
Tagged with:
-