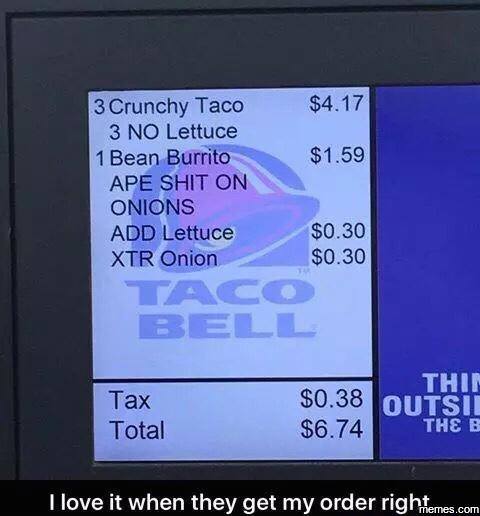
-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
Have you ever “purchased” an ebook, mp3, or video only to found you can only access it on a certain number or type of devices, or that it must be played through a specific player, or only accessed when you’re connected to the internet? Maybe that’s the sort of thing you’d like to know before you paid for this content. The Electronic Frontier Foundation — along with a coalition of publishers, consumer advocates, and other interested parties — have written to the Federal Trade Commission asking it to require that “locked” digital content be labeled accordingly. Pointing to the digital rights management (DRM) restrictions placed on content bought from Amazon, Google, Apple, and elsewhere, the letter [PDF] argues that the “confusing spectrum of restrictions” placed on digital content prevents shoppers from making an informed choice about what they are buying. The issue of DRM and copyright protection is divisive in the media community. On one end of the spectrum is the argument that DRM is necessary to protect content creators by preventing rampant, illegal duplication and distribution. If you can make infinite, pristine copies of the same file and share them globally in a matter of seconds, what’s to stop you? At the other end are those who contend that DRM is anti-consumer and anti-competitive, inextricably tying the buyer to the seller of the content. Can you imagine buying a paperback book at Barnes & Noble and then being told when, where, and how you can read it? Or buying a movie at West Coast Video (RIP) only to have a West Coast staffer come to your house a few months later and snatch it off your shelves because the store’s license to sell that video lapsed? “The use of DRM is controversial among creators; studios, publishers and labels; and audiences,” acknowledges EFF’s Cory Doctorow in the letter. “What should not be controversial is that a purchaser should be able to tell whether she is buying a DRM-encumbered product before she spends her money.” The letter accuses the companies that use DRM of wanting to have things both ways — pointing to the fact that consumers are buying locked content as evidence that DRM is acceptable to consumers, while simultaneously claiming that a DRM label would hurt sales. “If, on the other hand, some customers are unaware of DRM at the point of purchase, they are being mis-sold a product that comes with unexpected, unpredictable restrictions,” writes Doctorow. The groups signing on to the letter aren’t asking for some huge sticker or burst — or even that shoppers would have to acknowledge they are purchasing DRM-locked content. Instead, it could be as simple as adding a category to the details listed for a piece of content. The letter gives this side-by-side example of how a book would be listed on Amazon: If there were DRM on that title, it would read “DRM Restricted” with a link to more details about those restrictions. “Without DRM labeling, it’s nearly impossible to figure out which products have digital locks and what restrictions these locks impose,” explains Doctorow in an emailed statement. “Customers have a right to know about these restrictions before they part with their money, not after.” Source: consumerist
-
- access
- certain number
-
(and 4 more)
Tagged with:
-
-
In its latest tribute to retro gaming, the Internet Archive has uploaded a treasure trove of games, applications, and demos for the Amiga family of computers. You can play all of them for free, directly in your browser, but be warned — you might run into a few glitchy titles. There are more than 2,000 games online, including classics such as Bubble Bobble, R Type, and Double Dragon. However, our searching couldn't find a number of well-loved Amiga titles, such as Elite, Cannon Fodder, and The Secret of Monkey Island (all of which were available on other platforms as well). There are also thousands more applications and demo titles, designed to shown off the hardware's capabilities, though, of course, we've not had time to look through them all. This follows other uploads of retro titles from the Internet Archive, including MS-DOS games, Arcade titles, and a whole mess of games from Atari. If you didn't know what your plans were today, why not take a dip into gaming history. ViaTechCrunch
-
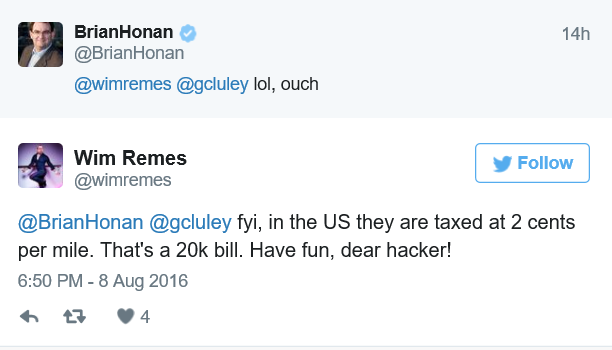
Vulnerability researcher Olivier Beg from Amsterdam has been handsomely rewarded with one million airmiles by United Airlines, after finding some 20 security holes in the company's software. As the Dutch Broadcast Foundation reports, the 19-year-old has benefited from the bug bounty scheme that the airline introduced last year to encourage bug hunters to disclose their findings responsibly to the airline rather than publish them to others on the net who might attempt to exploit them. According to reports, the most serious bug found by Olivier Beg earned the teenager a stonking 250,000 airmiles. He claims to have found vulnerabilities in software from other companies including Yahoo, Google and Facebook. All the signs are that there is certainly the need for airlines to run such bug bounties - United has suffered in the past from hackers breaking into customers' flight reward accounts, and has been criticised more recently for its tardy response to flaws reported in its flight reservation system. Personally, I think it might be better if firms like United offered researchers hard cash rather than airmiles for their efforts. After all, what if you're a bug hunter who is petrified of flying, or simply cannot stand the food on United planes? Surely you don't want to discourage those folks from responsible disclosure... Regardless, a bug bounty is better than no bug bounty - even if it's only counted in airmiles. And don't think that Olivier Beg is now flying around the world for free. He says he didn't have to pay for his flight Las Vegas last week, but still had to pay five Euros airport tax... PS. My thanks to Win Remes who points out that there may be a painful sting in the tail for anyone receiving "free" airmiles: Source: Graham Cluley
-
- bug bounty scheme
- security holes
-
(and 1 more)
Tagged with:
-
-
It looks like Microsoft is starting to make some attempt at closing the Windows 10 Free Upgrade loopholes. The Media Creation Tool, which provides detailed options for upgrading, now prompts Windows 7 or Windows 8 systems for a product key. The Media Creation Tool takes into consideration, users, who might have downgraded a previously installed and activated Windows 10 installation; by giving them the option to reinstall Windows 10, exempting them from the product key requirements. The new Digital License function attaches a Windows 10 license to the machine, permitting unlimited reinstalls without the need to have a product key or contact support to get the software reactivated. When users download the download the Windows 10 Media Creation Tool, they will see the following screen as usual. If the option to Upgrade this PC now is selected, the user will be prompted the enter a valid Windows 10 product key. Any attempts to enter a Windows 7 or Windows 8 product key will be invalidated: A new option has been added to the setup screen for users reinstalling Windows 10 on a previously installed and activated system. If your system has a Digital License attached to it, Windows 10 will automatically upgraded: Users can still circumvent the prompt for a product key by selecting the option Create installation media for another PC. There is another step users will have to follow in order to avoid being prompted to enter a product key. Even when installing from ISO, users can be prompted for a product key if the option Download and install updates (recommended) is selected. Instead, users should select the option Not at the moment. This will permit the upgrade to continue. I am sure Microsoft is working on a more concrete solution to ultimately end the free upgrade offer. In the mean time, you can still get it while door slowly closes. Thanks to Philip Yip of DellReinstallGuide for the tip! Source: Windows 10Forums
-
- free upgrade loopholes
- media creation tool
-
(and 2 more)
Tagged with:
-
-

20 Signs The World Is Against You
allheart55 Cindy E replied to allheart55 Cindy E's topic in Tech Help and Discussions
:big_ha:Unfortunately, #18 happens to me all of the time on the beach.:real_anger: -
Nobody ever accused Microsoft (MSFT) of having consistent naming sequences. Let’s see: Windows versions have been named, in order, 1, 2, 3, 95, 98, 2000, ME, XP, Vista, 7, 8 and 10. And today, there’s a new version: Windows 10 Anniversary Update. Why use three syllables when 10 will do? Windows 10 was already very good. Beautiful, fast, coherent, and compatible with those 4 million Windows apps the world depends on. What Windows 10 AU offers, though, is mostly catchup and refinement. It’s a bunch of features that follow in Google’s and Apple’s footsteps (haters, relax — yes, we know those companies have also stolen from Microsoft), and a lot of fleshing-out of features that were bare-boned in the original Windows 10. Since Windows 10 AU is free, and since every copy of Windows 10 will soon begin auto-installing the update, you may as well know what you’re getting into. Here’s a quick rundown of what you have to look forward to. Edge browser Microsoft’s speedy but stripped-down new web browser, Edge, has finally started to fill in its bald spots. The big news is that it can now accept extensions — feature plug-ins from other companies — just like Firefox, Chrome, and Safari can. There aren’t many so far, but the essentials — ad blockers, password memorizers and so on — are already available. Edge can now pass along notifications (they appear with your other notifications, in the Action Center) from websites that offer them. You can now pin a tab in Edge (shrink it to an icon that’s anchored at the left end of the tab bar), so that you can’t close it accidentally. Finally, Edge uses up a lot less battery power than its rivals, according to Microsoft. Log in with your face Already, on Microsoft tablets and laptops, you can teach the special camera (an Intel RealSense camera) to recognize you, and log you in with your face. Yes, you can unlock your tablet or laptop just by looking at it — fast, clean, foolproof. (Literally. No photo, sculpture of your head, or even twin can fool this feature.) That face recognition, along with fingerprint recognition on appropriately equipped laptops, is part of a feature called Windows Hello — and now, Microsoft says, apps and websites can use it, too. Someday soon, you could, in theory, log into your email or bank site just by looking at it. If it catches on, that will be a huge feature. No more passwords, no more stupid Captcha puzzles to solve. You, and only you, can log in. (Your face or fingerprint is stored only on your machine, and never transmitted.) Ink If you were kind enough to buy a Microsoft tablet or touchscreen laptop, the company wishes to thank you by bringing you a wagon full of gifts. You know the pen that came with your recent Surface tablet? You can now program the clicker on the top to do some cool stuff — like opening the new Ink Workspace, a collection of pen-friendly apps like Stickies, Sketchpad (for freeform drawing, featuring a virtual ruler you can use as a straightedge), Screen Annotation (lets you draw on a screenshot), and OneNote. (There’s a taskbar icon that opens this Workspace, too.) The new Stickies app recognizes handwritten phone numbers, stock symbols, times, and web addresses (they turn blue once recognized), and offers to dial, look up, create reminders for, or open them when you tap them. That’s neat. The best part of all of this: You can set up the pen-clicker thing to bring up the Ink Workspace even before you’ve logged in — at the Lock screen. Finally, a tablet is as useful as a legal pad. You’re suddenly getting the phone number of somebody attractive? Click your pen and start writing it down, without first logging in like some kind of painful nerd.(All of this, Microsoft says, may also work with other companies’ Bluetooth pens.) The Start menu Microsoft continues to tinker with the Start menu, the all-knowing oracle that gives you access to everything useful on your PC. Now, the All Programs button is gone; instead, the left side of the Start menu is your All Programs list. (The File, Settings, Power and account buttons are now tiny icons at the even farther left of the menu). This change makes screaming sense. Every OS includes both a master list of apps and a customizable subset of the ones you use most often — think of the Home screens in Android, or the Dock on the Mac. In Windows 10, the fly-out tiles are your custom subset; the left-hand column should display the master list. You’ll fall in love with this feature fast.Too bad you can’t type-select an app’s name once the list is open, though. (You can type-select only before you’ve opened the Start menu, using the Search box.) Cortana upgraded Cortana still isn’t as smart as Siri or Google Now (here’s my comparison). But it’s getting steadily better. In AU, you can speak reminders that aren’t associated with a particular time or place (“Remember that my Delta frequent flyer is …”), and even add photos to them. Apps and web pages can be programmed to add reminders directly to your list, too. For example, you can save a Map directly into Cortana’s reminder list. Better yet, you can use certain Cortana commands at the lock screen — before you’ve even logged in. You can ask her about the news, stocks, or weather, for example, or ask her to tell you a joke. None of this is personal information, so none of it requires signing in. Taskbar updates If you click the clock, you now get a pop-up mini-calendar; click a number to see your appointments for that day. And if you click the volume icon, you can switch playback sources — from speakers to headphones, for example. “Badges” can now appear on app icons, too, just as on the Mac or the iPhone, showing you (for example) how many new messages or emails have come in.Finally, the Action Center (notification list) at the right side has been redesigned— it has its own icon to the right of the clock, which sprouts a number to show you how many notifications have piled up — and so has its corresponding Settings screen. Phone-PC communication Apple may have introduced the world to the marvels of using your computer to send and receive calls and texts, using your smartphone as a cellular antenna. But in Windows 10 AU, Microsoft has its own version. The idea is that if you have an Android phone with the Cortana app (or if you’re among the six people with Windows phones), all of its notifications and even low-battery alerts can now appear on your Windows desktop, as pop-up alerts. It’s pretty crude — still in beta — and making it work involves crawling through a bunch of settings on both machines. And, of course, it’s not as slick as Apple’s; for example, you can’t use your laptop or tablet as a speakerphone, as you can on Macs and iPads. But this is a start. Lots of misc. Windows 10 AU reserves more slots (10 instead of 5) for ads among your Start-menu tiles (though you can remove them). Your email address no longer appears on the Lock screen. You can four-finger swipe between virtual desktops. You can now use both Microsoft’s free antivirus program (Windows Defender) and one that you’ve bought. Defender acts like a second opinion. New emoji symbols, including bacon and various skin shades. Lots of the basic starter apps have sprouted new refinements of their own Source: Yahoo Tech
-
- anniversary update
- features
-
(and 2 more)
Tagged with:
-
-
My niece put 76 miles on her vehicle the other night.
- 5 replies
-
- battery packs
- extra batteries
-
(and 2 more)
Tagged with:
-
I have a handful of younger family members that I believe are addicted to Pokémon Go. :big_ha:
- 5 replies
-
- battery packs
- extra batteries
-
(and 2 more)
Tagged with:
-
People really weren't joking about needing extra batteries to play Pokémon Go. Battery pack sales doubled in the US during roughly the two weeks that followed the game's release, according to The NPD Group. It reports seeing a year-over-year growth of 101 percent, with 1.2 million mobile battery packs being sold between July 10th and July 23rd, just days after the game's July 6th release. For those extra-long pokéwalks Pokémon Go really seems to be the only explanation here. NPD notes that while battery pack sales have generally been increasing from 2015, sales were only up 4 percent in the weeks prior to the game's release. So Pokémon Go very much seems to be what triggered it. The custom pokéball batteries that popped up may have helped, too. The question now is how battery packs — and Pokémon Go — will fair in the weeks ahead. It's not outrageous to assume that the Pokémon Go phenomenon will fade with time, and battery pack sales are likely to go down along with it. How soon will that happen? Niantic still has most of the world to roll the game out to, but it'll want to do that without annoying existing players too much. ViaTechCrunch
- 5 replies
-
- battery packs
- extra batteries
-
(and 2 more)
Tagged with:
-
Yesterday my colleague Sam Byford beefed about Apple’s habit of selling outdated laptops and desktops, some of which haven’t had spec bumps in years despite the availability of faster components like CPUs and GPUs. That got me to wondering: how old is your primary laptop or desktop computer? There was a time that I would never consider using a laptop or desktop that was more than a few years old. I’m talking back in the days when Macs were used primarily as digital hubs in the home and workplace PCs needed new Intel or AMD processors just to keep pace with the latest versions of Windows and Office. Now, however, we’re keeping our computers longer, thanks in part to the computing load being distributed across phones, tablets, and fast connections to the cloud. Lightweight desktop OSes that work well on older machines have also helped extend the life of our computing hardware. "[The] replacement cycle for the PC has extended," said intel CEO Brian Krzanich in June. "Four years was the average, now it has moved to about five to six years." A trend that computer makes don't like, to say the least. My primary computer is a three-year-old iMac that feels just as fast as the day I got it. What about you, how old is your primary computer? Source: the verge
- 2 replies
-
- cpus
- faster components
-
(and 1 more)
Tagged with:
-
Microsoft only started rolling out Windows 10's Anniversary Update this week, but it's already discussing future updates for the operating system. A new blog post detailing update changes for IT professionals sheds some light on Microsoft's plans for Windows 10. "This will be our last feature update for 2016, with two additional feature updates expected in 2017," says Microsoft's Nathan Mercer. Understandably, Microsoft isn't detailing exactly what features are coming just yet, but the next big feature update to Windows 10 is rumored to release some time early next year before spring. Codenamed "Redstone 2," the Windows 10 update may coincide with hardware updates to Microsoft's Surface Pro and Surface Book devices. Microsoft is already working on Redstone 2, with internal builds out for testing. Redstone 2 should be the more significant update out of the two, and the second "Redstone 3" update will arrive later next year. Microsoft originally released Windows 10 last July under the "Threshold 1" codename, and issued its first big update in November (codenamed Threshold 2). This week's Anniversary Update (codenamed Redstone 1) marks the second big update to Windows 10 since its introduction last year, and it appears Microsoft looks set to settle on two big updates per year for Windows 10 moving forward. ViaWindows Central
-
- feature update
- microsoft
-
(and 2 more)
Tagged with:
-
Plugging in that USB stick you found lying around on the street outside your office could lead to a security breach. This is no secret, of course. We have all (hopefully) been aware of the dangers of inserting an unknown USB device into our computers for some time. Heck, the technique has even made it into the Mr Robot TV series. But what may not be widely known is just how successful the tactic can be for allowing hackers to compromise your computer systems. Research presented this week at BlackHat by Elie Bursztein of Google’s anti-abuse research team shows that the danger is alarmingly real: …we dropped nearly 300 USB sticks on the University of Illinois Urbana-Champaign campus and measured who plugged in the drives. And Oh boy how effective that was! Of the drives we dropped, 98% were picked up and for 45% of the drives, someone not only plugged in the drive but also clicked on files. It seems folks just can’t resist picking up a USB stick that they see lying around – Bursztein says that it only took six minutes for the first device that he “lost” to be picked up. Bursztein was curious as to whether there were ways of influencing the likelihood of someone plugging a found USB stick into their computer, so they left five different types scattered across the University of Illinois campus: drives labeled “exams” or “confidential”, drives with attached keys, drives with keys and a return address label, and generic unlabeled drives. One would like to imagine that people are less likely to plug in a USB drive if it is clearly labelled with the owner’s contact details, and that appears to be borne out by the statistics. On each type of drive, files consistent with the USB stick’s appearance were added. So, “private” files were added to USB sticks that were unlabeled or were attached to keys or a return label, “business” files to sticks marked confidential, etc. However, in reality each of the files was actually an HTML file containing an embedded image hosted on the researcher’s server. In this way they were able to track when files were accessed. Upon opening the HTML file, users were asked if they wished to participate in a survey asking why they plugged in the drive. Approximately 20% agreed (perhaps encouraged by the promise of a gift card for their assistance). Just over two thirds of the people who responded to the survey said that they accessed the USB sticks with the intention of returning them to their rightful owner. 18% admitted that they were “curious”, and 14% gave other explanations. Now from the security point of view it’s worth recognizing that a security breach could already have happened by this point. The most basic – and simplest to conduct – attack would have seen malicious code placed in the HTML file that would have been automatically activated upon viewing, perhaps downloading further malware from the internet. Alternatively, users could have been taken to a phishing site, and tricked into handing over login credentials through social engineering. In addition, there is also always the danger that an attacker might have planted executable malware directly onto the USB stick, and hoped that an unsuspecting user would allow it to run on their computer. A more sophisticated attack, however, would see the use of a device using HID (Human Interface Device) spoofing to trick a computer into believing that it was in reality a keyboard. As soon as the “USB stick” is plugged in it would inject keystrokes – building a set of commands that could open a reverse shell that could give a hacker remote access to the victim’s computer. In a blog post, Bursztein explains in depth how he was able to camouflage a keyboard-spoofing device so that it looked near-identical to a genuine USB stick. Keyboard-spoofing is not the most sophisticated type of attack possible through a malicious USB stick however. Perhaps the most complex and stealthy attack would see the plugged-in device exploiting a zero-day vulnerability in the computer’s USB driver – similar to the method used in the notorious Stuxnet attack against the Natanz uranium enrichment facility in Iran. Your chances of having a USB zero-day vulnerability used against your organization is remote, unless you are of particular interest to an intelligence agency or state-sponsored hackers. Keyboard-spoofing HID attacks and especially basic social engineering attacks tricking users into opening files on a newly-found USB stick, however, are much more likely, which means it is essential that you educate your workers about the risks and urge them to hand lost property in rather than attempting to identify a device’s owner themselves. In short: USB devices should be treated with caution. Never plug in an unattended, unidentified USB stick. Keep your security defenses, policies and patches up to date. Source: tripwire
-
- compromise
- dangers
-
(and 4 more)
Tagged with:
-
It’s not often that we see a perfect crime ouroboros, but when we do, it just feels like some kind of cosmic joke. To wit: two people were arrested this week for trying to sell stolen video game consoles and some other stuff back to the guy they’re accused of stealing them from. Police in Clarksville, TN said on Facebook that a man and woman visited a local pawn store with a few things to sell on Tuesday (via The Leaf Chronicle), including two PlayStation consoles. The store’s owner realized that some of that stuff looked awfully familiar, and decided to head home to check on his belongings. You know, just in case. Lo and behold, upon arriving home he found someone had broken into his house and stolen several things, including — you guessed it! — two PlayStation consoles and their controllers, as well as video games and DVDs. All told, the property was valued at $1,000. The pawn shop owner called the police while the twosome were still in the store, and they were arrested soon after on charges of aggravated burglary. Theft suspects tried to pawn items back to owner [The Leaf Chronicle]
-
- cosmic joke
- perfect crime
-
(and 1 more)
Tagged with:
-
Have you gone on a bad date recently? Maybe he had food in his teeth the whole time, or perhaps she wouldn’t stop talking about her Precious Moments collections. It could’ve been worse, though. Your date could’ve ordered a bunch of food and drinks at a pricey steakhouse and then fled, leaving you with the bill. That’s what happened to a Los Angeles area woman who said she was faced with a $163 dinner bill after her online date dined and then, well, dashed. And it seems like this isn’t the first time he’s pulled that move. She told CBS L.A. that he’d sent her a flattering message on dating site Plenty of Fish. After a few exchanges, they decided to meet a steakhouse in downtown L.A., even though it was a bit on the pricey side for her. Her date was definitely in the mood… to eat, at least. “He ordered a lot of food. He had an appetizer. He ordered a steak. This restaurant is all al la carte,” she explained. “He even ordered a couple sides, a glass of wine. So he was looking like he was really enjoying himself.” Towards the end of the meal he said he had to go make a phone call. After waiting for him for 15 minutes, it dawned on the woman that he wasn’t coming back. “When I went to message him on the app, he had blocked me. And I thought, ‘Oh my gosh! Is this really happening right now?’ ” she said. So she started spreading the news of what had happened on social media, posting photos of the man, who police have no identified. Authorities say he’s also accused of failing to pay for a haircut and coloring job at a Burbank salon, and is facing two pending cases of petty theft. The woman says others he’s duped for a free meal have come forward after she shared her story online. “I heard from a lot of people say he did the same thing. It’s typically very high end restaurants,” she said. She’s not giving up on dating, but for everyone else out there, she just wants others to be on your guard. Woman Says She Was Left With $163 Tab After Man She Met On Dating Site Dined, Then Dashed [CBS L.A.]
-
-

Older Than Dirt?
allheart55 Cindy E replied to allheart55 Cindy E's topic in Tech Help and Discussions
I only remember 16 of them but that still makes me older than dirt. :big_ha: -