-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
-
It seems that the hackers used malware to attack. What defense does anyone have, really?
- 4 replies
-
- ddos attack
- internet
-
(and 2 more)
Tagged with:
-
A cyberattack that took down large swaths of the internet around the world on Friday was carried out, in part, by unsuspecting devices connected to the internet. Security firm Flashpoint said it believes that digital video recorders and webcams in people's homes were taken over by malware and then, without owners' knowledge, used to help execute the massive cyberattack. Hundreds of thousands of devices appear to have have been infected with the malware. It was a distributed denial-of-service, or DDoS, attack. Using the malware, hackers were able to flood a website with so much traffic that it impaired normal service. The DDoS attack overwhelmed the servers of New Hampshire-based company Dyn and came in three waves Friday starting around 7 a.m. ET. Dyn says the attack has ended. Dyn is part of the backbone of the internet. It works as a middleman to make sure that when you type in a URL like twitter.com, you get to the correct site. As a result, throughout the day Friday many users were unable to connect to popular platforms like Twitter, Netflix, Spotify and the Financial Times in various parts of the U.S. and Europe -- mainly the American northeast and the U.K. Software IT company Dynatrace monitors more than 150 websites, and found that 77 were impacted Friday. The disruption may have lost companies up to $110 million in revenue and sales, according to CEO John van Siclen. The FBI said Friday that it was "investigating all potential causes of the attack," and the U.K.'s Home Office said it was looking into the matter. So far, no one has pointed a finger at a particular group or nation. "It's too soon to know," Doug Madory, a director at Dyn told CNNMoney. The methods used in Friday's attack were very similar to the one carried out against the website of cyber researcher Brian Krebs last month, as well as French internet service provider OVH, according to Flashpoint. It's unknown if the attacks are related. After the cyberattack against Krebs, the source code used to carry out the strike was released online. Since then other hackers have been using the malware to carry out their own attacks. While DDoS attacks are nothing new, research shows they're becoming increasingly sophisticated and frequent. Friday's cyber-blitz demonstrated just how vulnerable the internet's infrastructure is to these type of bombardments. Source: CNN
- 4 replies
-
- ddos attack
- internet
-
(and 2 more)
Tagged with:
-
-
-
Update: Dyn reports that as of about 9:30 a.m., service has been restored and affected sites and services should start returning to normal. Read on to see what happened and how big it was. Original story: Users of dozens of popular sites and services — including Spotify, Twitter, Github, Reddit, Airbnb, and others — are grumbling about slow load times, missing content, or sites just plain being down periodically today. The good news is: no, it’s not just you. The bad news is: big chunks of the internet aren’t working because of a deliberate attack. The core issue is a massive DDoS attack against DNS host Dyn, as TechCrunch first spotted. A DNS hosting service is one that basically connects a server to a name, and makes it so you can type a website name into your browser and have it resolve into a specific set of hosted content somewhere. So translating this all out of tech and into English, what’s happening is that some party or parties is/are sending massive amounts of coordinated traffic to one particular hosting company — Dyn — in order to overwhelm its ability to function. As a result, legitimate users connecting to sites managed by Dyn may not be able to access the content they’re looking for, due to the barrage of robotic requests running interference. The attack particularly seems to be affecting the US East region, and began around 6:00 this morning Eastern time — the hour when East Coast dwellers are first getting up, checking their phones, and heading into work, there to use the internet. Sites that may be affected include Dyn itself, Twitter, Etsy, Github, SoundCloud, Spotify, the New York Times, all Vox Media sites, and more, according to TechCrunch and Hacker News. Other tech companies like Level 3 and ZenDesk have also been reporting connection issues related to this particular attack. A look at the homepage of Down Detector right now is a pretty stark visual of how many sites are affected — you can see the spikes everywhere, and look up specific sites you’re trying to reach. Some of the most-reported outages on Down Detector as of about 9:15. There’s not much individual users can do about it right now except be patient and try not to spam reload requests too much. Source: Consumerist
-
- deliberate attack
- internet
-
(and 2 more)
Tagged with:
-
One of the early victims of an exploding Samsung Galaxy Note 7 said that the company offered to cover his expenses, including damage to the hotel room he was staying in at the time his phone caught fire. Now that the phone has been officially recalled and Samsung is in crisis, customers report that Samsung hasn’t handled customers whose phones have actually caught fire very well. The Guardian US spoke to multiple fire victims who have remarkably similar stories. They who say that Samsung has been uninterested in helping customers whose homes were damaged or left uninhabitable by fires started by exploding phones, and that the company has made it clear that getting the phones back was its first priority. That’s understandable, especially since Samsung reportedly still isn’t 100% sure what has caused the explosions, but it means leaving customers with thousands of dollars’ worth of damage to their homes hanging if they won’t give their phones back. “[samsung was] only interested in retrieving the phone,” one customer whose nightstand was damaged and home filled with smoke told the Guardian. “Once I told them I was giving the phone to the Consumer Product Safety Commission (CPSC), they went dark.” Samsung owners furious as company resists paying up for Note 7 fire damage Source: Consumerist
-
-

iMessage Users Report Attempted Hacks
allheart55 Cindy E replied to allheart55 Cindy E's topic in Tech Help and Discussions
It's pretty messed up. I hope that they find a fix for it soon.- 3 replies
-
- hack attempt
- imessage
-
(and 2 more)
Tagged with:
-
Welcome to Week 3 of National Cyber Security Awareness Month! This week’s theme, brought to you courtesy of the National Cyber Security Alliance of US businesses and government agencies, is about recognizing and combating cybercrime. That includes all manner of online crime, be it crooks stealing personal information for monetary gain, identity theft, or online radicalization and recruitment to terrorist networks. It also includes things that some of us might not even realize are crimes, like guessing at passwords, using somebody else’s photo, trolling, cyberbullying or getting back at an ex by posting their intimate photos online. Here are examples we’ve seen of such crimes, how harmful they can be, and the potential consequences in store for people who commit them. Impersonating someone online This includes guessing at somebody’s password, using their photo, and/or pretending to be someone else: an art that phishers have honed in their quest to part us from data, information, money and more. Phishing is how many serious cyberattacks begin. It was at the heart of the 2014 Celebgate nude-photo-theft scandal, for one. The consequences can be severe. Besides the anxiety the victims endured, we’ve already witnessed the conviction of multiple perpetrators, with ongoing investigations holding out the potential for more. What about using somebody else’s photo online? There are so many cases where imposters have targeted kids by putting up fake photos, such as the guy who posed as Justin Bieber in order to trick kids into stripping in front of a webcam, or the 22-year-old from New Jersey who posed as a teenager to stalk girls online. Adults have their own flavors of lying sleazebag fraudsters too: cybercrooks who prey on vulnerable love-seekers on dating sites, who convince them they’re sending money to needy soldiers; who send bogus emails claiming you’ll get a payment just as soon as you first pay a “shipping agent” (known as “advance fee fraud“); or by voluptuous women who, strangely enough, are forced to find love online – presumably because Russia is fresh out of men who like buxom blondes. Short of child stalking or fraud, just doing something like putting up a fake Facebook profile is illegal. It’s a violation of Facebook’s terms, for one thing, but that should be the least of your worries. After all, Facebook isn’t going to haul all of its fake people into court, for very good, very voluminous reasons. What’s more serious than breaking Facebook’s terms of service is the fact that if the photo you’re using was found through a Google search or taken off somebody’s profile, you’re guilty not only of misrepresenting your identity, but also of stealing intellectual property and possible commission of identity theft. With regards to guessing at somebody’s password, sorry, but lame, easily guessed passwords simply aren’t a justification to access anybody’s account without authorization. One example of this was Chris Correa, the former baseball scouting director for the St. Louis Cardinals. In July, he was sentenced to 46 months in jail after guessing a rival team’s password. The lack of a strong password allowed Correa to gain unauthorized access to an internal network of the Houston Astros and enabled the theft of closely guarded information about players, including internal discussions about trades, proprietary statistics and scouting reports. In short, it was a case of corporate espionage. The courts didn’t give a hoot whether the guessed-at password was strong or feeble. Even if it was as drop-dead simple as the word “Password” or that good old favorite “123456,” it didn’t make it right, or even remotely legal, for Correa to break into the account. He was convicted of five counts of computer hacking under the CFAA. Trolling/cyberbullying Forget that saying about sticks and stones breaking our bones: words and virtual mobs can hurt us just as horribly. Even one teenager’s suicide caused by being mocked on social media is a tragedy, but we’ve seen far more than just one. One of the more recent court cases we’ve seen was that of a student who filmed a schoolmate in the school toilet. The student posted the 10-second video to Snapchat and Vine. In spite of Snapchat videos only lasting 24 hours, the video went viral, spreading not only throughout the school but beyond, to other schools. The boy in the video, 14-year-old Matthew Burdette, was mercilessly bullied. He killed himself in November 2013, writing in a suicide note that… I can’t do school anymore. I have no friends. I don’t want to kill myself but I have no friends. The boy who posted the video, identified only as MH in court documents, was charged with invasion of privacy. A minor at the time, he was sentenced to probation. We’ve seen girls as young as 12 kill themselves because they just couldn’t stand the cyberbullying. In the case of Rebecca Ann Sedwick, even her death didn’t stop the bullies. They bragged on Facebook about driving her to it. In the US, nearly all states have bullying laws, many with cyberbullying or electronic harassment provisions. In the UK, the Crown Prosecution Service earlier this month published new guidelines in order to make it clear to prosecutors that those who encourage others to participate in online harassment campaigns can face criminal charges under the Serious Crime Act 2007. That covers doxxing – i.e., publicly publishing a target’s personal information, such as home address or bank details – or creating a derogatory hashtag to encourage others to pick on victims. Revenge porn Legislators continue to pass new laws against revenge porn – what’s also called nonconsensual porn. In the first year of the UK’s new law against nonconsensual porn, we’ve seen children as young as 11 be victimized by the sharing of private sexual images without the subject’s consent, with the aim of inflicting distress. It’s an act for which prosecutors had previously sought convictions under existing copyright or harassment laws. Convictions for revenge porn in the UK have included: Jason Asagba, the 21-year-old who sent a woman’s photos to her family and shared them on Facebook a mere three days after the new law went into effect on 13 April 2015 David Jones, a 53-year-old married man who was sentenced to three months in jail after posting images of his ex on social media. She said she felt “complete terror” when she saw the sexually explicit images Luke King, who swapped out his WhatsApp profile picture for a naked picture of his ex-girlfriend. The 21-year-old was prosecuted under the Protection from Harassment Act 1997 and sentenced to 12 weeks of jail time in November 2014 It’s one thing to go after the people who commit these acts, but it’s another to hold accountable the services that enable the dissemination of these images. Criminals often choose Facebook as the forum in which they prefer to torment. The social network has seen its share of legal woes because of it. In 2014, it was hit with a $123 million lawsuit in the US for hosting, for months, a page dedicated to humiliating one Texas woman with Photoshopped clips of her face pasted onto porn shots. Since then, Facebook has said that it’s bolstered its report abuse infrastructure, appointing a worldwide team of experts to investigate the complaints around the clock in order to remove offending images as soon as possible. Instagram and Snapchat say that they’re also on top of abuse reports 24/7. What’s more, Google and Facebook this year teamed up to host an EU Child Safety Summit that focused on how to keep young people safe online and how both of the internet giants are fighting revenge porn. Those are just a few of the cybercrimes that some of us don’t seem to realize are crimes. Do you see people blithely invading others’ privacy with their mobile phones? Sneaking into their partners’ accounts by guessing their passwords? Feel free to share your stories below – particularly if you’ve found yourself enlightening those who don’t seem to know any better when it comes to their own illegal actions. Source: Sophos
-
- cybercrime
- identity theft
-
(and 2 more)
Tagged with:
-
Windows 10’s cumulative updates have ballooned in size, and a similar bloat will also affect the Windows 7 updates that Microsoft revamped this month. According to data published last month by LANDesk and refreshed by Computerworld with October’s numbers, Windows 10 cumulative updates for the three versions of the new OS have surged in size. Updates for Windows 10 version 1507—the debut that launched in July 2015—have grown 153% (for the 32-bit edition) and 181% (64-bit), from 184MB and 368MB to 466MB and 1,034MB (or over a gigabyte), respectively, in just over a year. Those for version 1511—Windows 10’s first “feature update,” issued in November 2015—exploded in comparison: The first 64-bit 1511 update was 49MB, but the cumulative update released earlier this month was a whopping 989MB, for a growth rate of 1,918% in under 12 months. The newest Windows 10, version 1607—released in early August—has also expanded, with the 64-bit edition climbing 591% from 113MB in August to 781MB this month. “Cumulative updates start out big and become enormous over time,” Stephen Brown, director of product management at LANDesk, a maker of enterprise endpoint management software, wrote in a post to a company blog on Sept. 21. Updates increase in size because they are cumulative; October’s 989MB update for 1511 included not only new fixes, but also those in every prior update. September’s, in turn, included new fixes as well as those in August’s and July’s and June’s and.... And so on and so on. August announcement of the change to Windows 7’s update scheme. The “convenience roll-up” Mercer mentioned was about 477MB in size (for the 64-bit version). Microsoft issued the roll-up in May. In another answer, Mercer got more specific. “Eventually [the Windows 7] Monthly Roll-up will grow to around the 500MB size,” he said. If Windows 7’s updates were to grow at the pace of 10’s, the former would top the roll-up within a few months: Using the expansion of Windows 10 1511’s updates as a guide would mean Windows 7’s cumulative update for April 2017 would be approximately 1.6GB, or more than triple Mercer’s bet. That’s not likely, said McMillan, for the simple reason that Microsoft is not fiddling with Windows 7 features at this point, but instead patching vulnerabilities and fixing bugs. McMillan predicted that the Windows 7 cumulative updates would reach Mercer’s 500MB estimate, probably within a few months, but then grow from there only slowly. But even updates of that size will choke some customers. A few users and IT administrators expressed concern about the expanding updates as soon as Microsoft announced the new servicing regime. “This may impact bandwidth to download and install,” wrote someone identified as Kiran in a comment appended to Mercer’s August blog post. McMillan has been fielding similar inquiries from LANDesk customers. “I’m getting multiple calls each week about bandwidth,” he acknowledged, referring to the Windows 7 cumulative updates. “A lot of them just don’t have a fat pipe, so this is an entirely new problem for them.” McMillan cited retailers and healthcare organizations as examples of users with limited Internet bandwidth—some with nothing more than dial-up connections, others who rely on satellite-based Internet—who will face time-consuming downloads as the cumulative updates grow in size. Previously, updates could be individually selected—each security patch or hot-fix approved or rejected by IT administrators—to fit the specific needs of each system, resulting in small-sized downloads. But with the all-or-nothing nature of the new Windows 7 cumulative updates, those users were suddenly locked into taking everything Microsoft offered, or leaving machines vulnerable to attack. Windows users would have had to deal with the cumulative concept at some point—when they migrated to Windows 10—but the change to the Windows 7 servicing rules put it front and center months or years earlier than many figured. “This will have a huge impact,” McMillan said. “[users] are having to make choices they haven’t had to make before.” Data: LANDesk, Microsoft Windows 10 cumulative updates have ballooned in size as code changes accrete. Version 1511’s latest update was more than 20 times larger than its first update just 12 months ago. Source: PC World
-

iMessage Users Report Attempted Hacks
allheart55 Cindy E posted a topic in Tech Help and Discussions
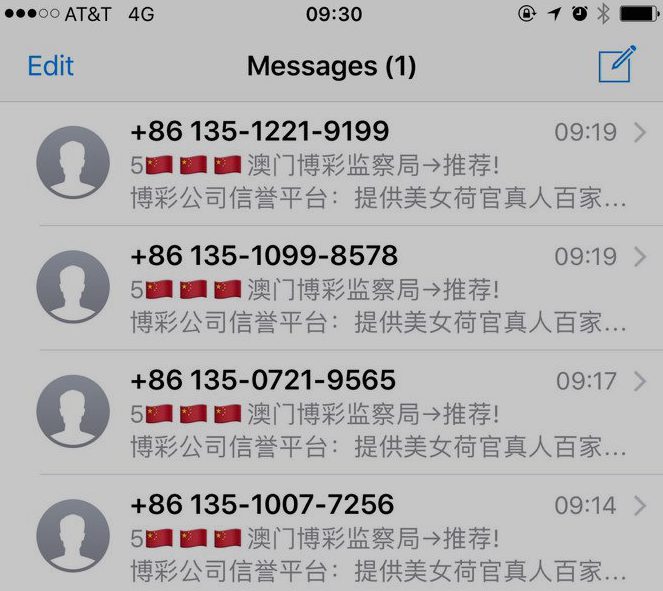
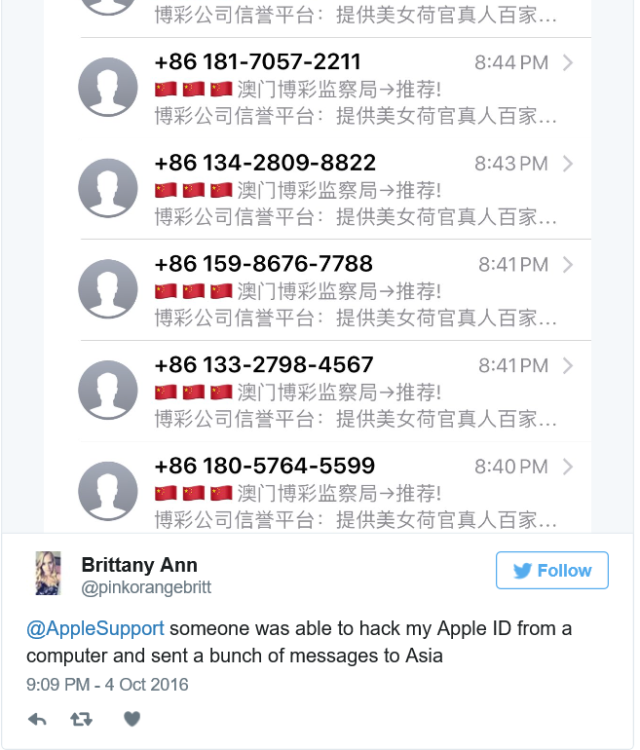
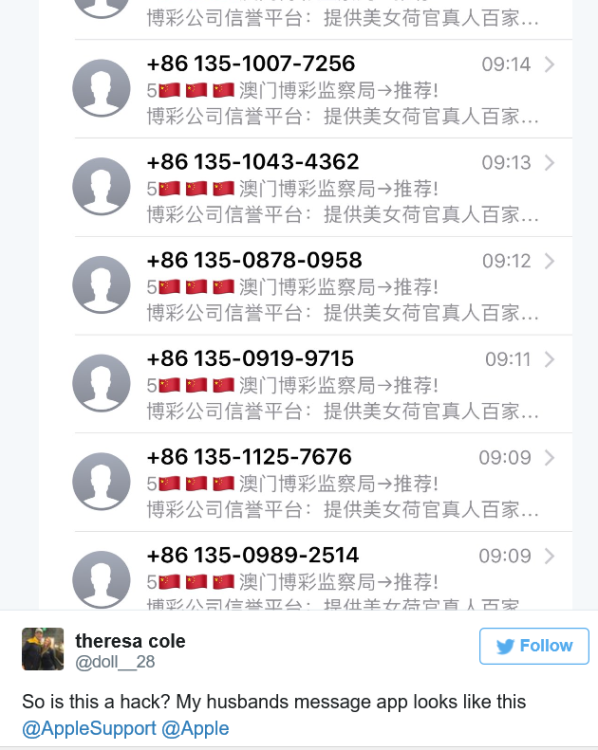
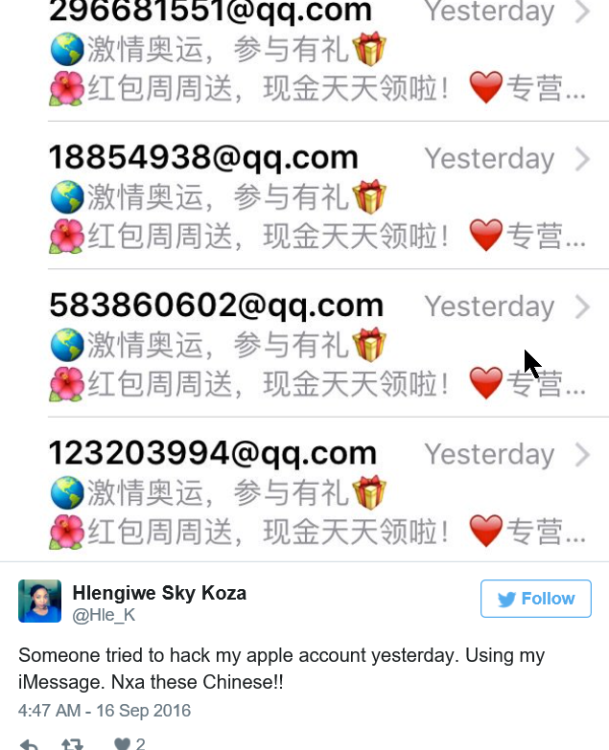
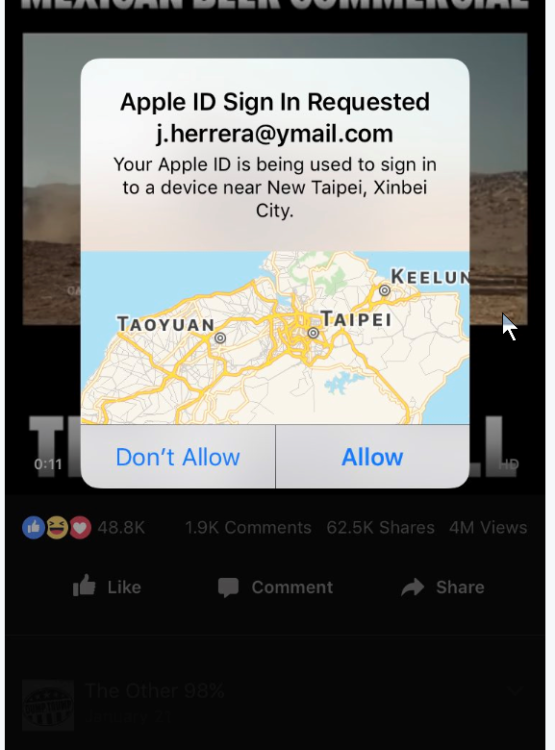
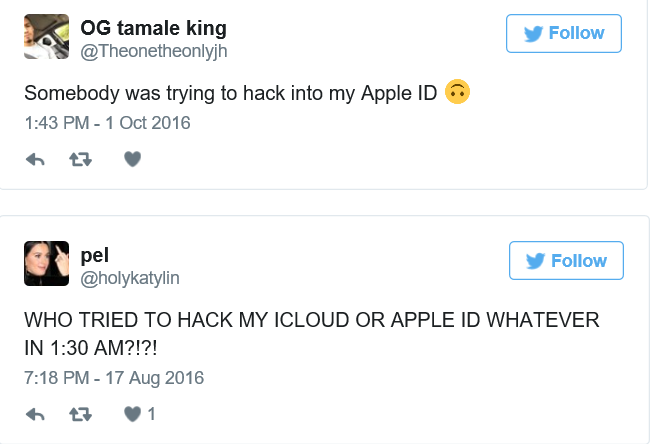
When it comes to trying to breach the data on iPhones, scammy text messages are apparently all the rage. In just the last year, we’ve had the text that could instantly crash an iPhone, and the flaw that allowed hackers to steal your saved passwords with a single text. Now, some Apple users are reporting another possible hack attempt, this time through their iMessage accounts. Mashable reports that Apple users, including one of the publication’s own employees, have been suffering hack attacks tied to their iMessage and Apple ID accounts, both on their computers and smartphones. The issue, which Apple support says is likely an attempt by hackers to steal personal information, began for the Mashable employee when she received a message in her computer’s iMessage account from a foreign number, with a message written in Chinese. A short time later, she says she received a notification that her Apple ID was being used on another device. The only prompt connected to the notification was to click “OK.” Immediately after clicking on the button, her iMessage account was flooded with messages from a foreign number, written Chinese. The Mashable employee changed her Apple ID password, security questions, and contacted Apple support. A rep for Apple said the hack is fairly new and that developers are currently working on a fix. The company was unsure if users’ personal information had been compromised. Still, Apple users on Twitter have been reporting the issue for several weeks. Source: Consumerist- 3 replies
-
- hack attempt
- imessage
-
(and 2 more)
Tagged with:
-
-

Malwarebytes acquires AdwCleaner
allheart55 Cindy E replied to starbuck's topic in Tech Help and Discussions
This should be interesting, to say the least. -
ATM explosive attacks increased by as much as 80 percent in the first half of 2016, reveals a new report. The European ATM Security Team (EAST) tracked 492 explosive attacks. Some used solid explosive material to pull off their heists, though they were a minority at 110 of the incidents. All the rest made use of gas. But let's be frank. It doesn't matter that much to us what bad guys are using to blow up the cash machines. EAST Executive Director Lachlan Gunn says while it's not good that thieves are conducting those types of attacks in the first place, the fact that those techniques are on the rise is extremely concerning. As he explains in a blog post: "This rise in explosive attacks is of great concern to the industry in Europe as such attacks create a significant amount of collateral damage to equipment and buildings as well as a risk to life. The EAST Expert Group on Physical Attacks (EGAP) is working to analyse the attacks and to share intelligence best practice information across the industry and law enforcement that can help to mitigate the threat." Let's frame it another way. Out of the approximately 1,600 physical attacks (including robbery and ram raids), explosive attacks registered across one quarter of those incidents and caused an average cash loss of €16,631 (approximately US $18,295). That doesn't include any damage the explosives might have caused to a financial institution's properties and/or buildings. But as EAST is right to point out, those losses usually exceed the funds stolen in the attacks. At the same time, let's keep things in perspective. The €27 million lost to ATM physical attacks is but a fraction of the €174 million seized by Transaction Reversal Fraud (TRF) and other types of fraud. There were also about ten times as many incidents in that particular category of ATM attacks. Meanwhile, logical attacks like jackpotting and 'cash out' campaigns registered only 28 incidents that collectively stole approximately €0.4 million from ATMs. Computer criminals are always thinking of new, sometimes explosive ways to target financial institutions. Sometimes they're after the cash stored in an ATM. Other times, they want access to an employee's email or customers' banking accounts. For that reason, users should take extra care to protect their financial accounts with a strong, unique password and two-step verification (2SV). They should also watch out for phishing attacks, as should anyone who works at a bank or similar organization. If ATM explosive attacks continue to increase, perhaps financial institutions should lend some extra thought to where they physically place their cash machines on their premises. Source: Graham Cluley
-
Netflix is telling some password-reusing customers to reset those well-trodden logins after it spotted some of them in a batch of purloined credentials. The news was first reported by AdWeek, where writer Steve Safran said on Friday that he’d received this email: As part of our regular security monitoring, we discovered that credentials that match your Netflix email address and password were included in a release of email addresses and passwords from a breach at another company. The email didn’t give details about how many accounts were affected. Netflix is resetting affected users’ passwords for them and then prompting them to change it to a new one. The email said that Netflix wasn’t aware of anybody having compromised Safran’s account. Netflix confirmed to the Register that yes indeed, it’s sending out the emails as a precautionary measure due to the recent disclosure of credentials from other sites. This is part of our ongoing, proactive efforts to alert members to potential security risks not associated with Netflix. There can be a variety of triggers such as username and password breaches at other companies, phishing schemes, and malware attacks. Like many online services, Netflix’s routine security monitoring includes sniffing around online to see if it will find its user IDs circulating in breach lists. That’s how Amazon found a cache of reused passwords and likewise told some customers recently to swap the passwords out. Facebook is also known to prowl the internet looking for your username/password combos to show up in troves of leaked credentials. So where did the breached passwords originally come from? Netflix isn’t saying, and honestly, it could be from any of a growing list of mega-dumps. The credentials could have come out of the LinkedIn breach of millions of passwords, for example. Or it could have been the MySpace mega-breach, the 65 million passwords in the Tumblr breach, or from the gargantuan Yahoo breach of half a billion accounts. With each breach comes an increased chance that a reused set of login details will be discovered and potentially used by crooks to gain access to any account set up with those same details. If you’ve got some scruffy reused passwords kicking around, we agree with Netflix: put those mangy things out to pasture and get yourself some new ones to ride around on. Make sure every one of your passwords is unique, too. After all, cloned passwords are sickly things. If one service gets breached, crooks can try them on all your other accounts. So if you don’t want crooks watching porn, or Disney films, for that matter, with you footing the Netflix bill, make sure you’ve got a unique, strong password on that account. Here’s a detailed explanation of the dangers of password reuse, and here’s how to make every one of those passwords robust. “So many passwords!” you may say. “I must now lie down and take a nap!” you may wail. Please, no! Nap not! With all the “security breach!!!” and “reset your password NOW!!!” news coming at us constantly, we know it’s tempting to more or less just give up. Instead of giving up on security, though, consider using a password manager. We think they’re a great tool. All you have to remember is one good, strong master password for the manager. Source: Sophos
-
- breach
- credentials
-
(and 2 more)
Tagged with:
-
How easily are computer users fooled by bogus technical support scams? For anyone living in the US, a new study from Microsoft suggests the chances of losing money when encountering this kind of scam are a surprising – and shocking – one in five. The firm questioned 12,000 people who’d run into tech support cons in 12 countries (1,000 per country) uncovering marked national variations in susceptibility. Top of the list was India, where 22% of those targeted fell for the ruse, with the US and China close behind on 21% and 16% respectively. Only 2% of Britons lost money, making them by some distance the most resistant nation of those studied, with Germany, Denmark, France and Canada also achieving low victim rates. This kind of scam has several forms. The oldest and simplest is where criminals cold call home users pretending to be from a legitimate company with the news that an infection has been ‘detected’ on their PC. There is no infection of course, but scammers will try to persuade users they should pay a fee of between $50 and $300 to clean up the non-existent problem, usually after taking remote control of their computer to generate false alerts. Another variation involves computer pop-ups, which borrow tactics from the fake anti-virus industry to try and convince users they need to pay through the nose for remote tech support when all the users really end up with is an empty wallet. After the fall The difference Microsoft found between countries and age groups is intriguing. The young (18 to 34) were significantly more likely than older users to fall prey to these scams regardless of nationality, which Microsoft speculates could be due to their trusting nature. An alternative explanation is that younger people use the internet in a way that makes them more likely to encounter certain kinds of tech support scam. For example, the young reported experiencing more web redirects of the sort that often lead to sites hosting tech support scam pop-ups. It could simply be that this tactic is more effective. A second outlier was the high number of US users who report losing money to tech support scammer – ten times the rate for the UK. Users also seem to be more susceptible to tech support fraud when the caller or remote support assistant claims to be from a company they trust. Ironically, one of the brands tech support scammers are most likely to impersonate is Microsoft itself, despite the company’s warning that it does not use remote support in this way: Microsoft will never proactively reach out to you to provide unsolicited PC or technical support. Any communication we have with you must be initiated by you. And yet in the US, the study found that nearly half of users thought that Microsoft would be very or somewhat likely to do such a thing. The figures for email contact mirrored this perception. However, many firms do use such channels as part of their marketing, so it’s no wonder that consumers end up confused about where boundaries for normal communication lie. Tech support scams might be an old con but they could be with us for some time yet. Source: Sophos
-
- computer users
- scam
-
(and 1 more)
Tagged with:
-
-
I don't miss my Yahoo email account at all. I have my Yahoo dumping into my Outlook account and that suits me just fine. I stopped trusting Yahoo a long time ago.
-
Some people prefer the software but my mouse/keyboard do everything that I need it to do without it.
-
I have the Logitech 520 keyboard and mouse as well. I never installed the software and both work just fine.
-
900 bugs. That’s a lot. $5,000,000. That’s a lot, too. That’s how many bugs Facebook’s pioneering bug bounty program has uncovered since it launched five years ago – and how much Facebook has paid for them. The social network giant celebrated the program’s fifth anniversary with a blog post and self-assessment – and for anyone who’s either running or contemplating a bug bounty program, it’s quite instructive. As The Register notes, Facebook’s program: Pays generously when it receives notice of flaws and working proof-of-concepts, provided they are not already public or used in attacks against users. Simple math shows the average payment has run roughly $5,500, but some have earned much more. Just a few weeks ago, we told you about Arun Sureshkumar, who earned $16,000 for uncovering a zero-day vulnerability in Facebook Business Manager that would’ve allowed anyone to capture or delete any page on Facebook. And in March, Anand Prakesh earned $15,000 for discovering that Facebook’s beta sites weren’t rate-limiting password-reset PINs, making them easy to attack via brute-force scripts. Overall, average payments seemed to drop a bit in the first half of 2016: Facebook reports doling out $611,741 to 149 researchers, or about $4,100 per person. On the other hand, the averages seem a lot higher than they were when we covered the program back in 2014. Meanwhile, the program seems to be thriving. Facebook got 9,000+ bug reports during the first half of this year, and started accepting bug reports for its WhatsApp division, too. (You’ll notice the vast majority of those bugs didn’t earn cash. That’s true for most bug bounty programs. Before you submit, you might want to check out Facebook’s page on what does and doesn’t qualify.) Learn More If you do make it through the sieve, Facebook will now be happy to pay you in Bitcoin, should you so desire. Whatever currency you prefer, Facebook says its payment process has recently been automated, so you should get your loot that much sooner. In his post, bug bounty team blogger Joey Tyson also shared a few best-practice program tweaks that might be useful to folks following in Facebook’s footsteps. Our award notifications now include information on how the specific bounty was determined. We continue to make these decisions based on real (rather than perceived) risk and will share more details on the thinking behind each award. We’re also preparing to share more educational resources on security fundamentals and topics specific to our products. Beyond finding bugs, Facebook notes that its security team has recruited many new security professionals from those who’ve submitted bugs. In today’s competitive market for security talent, that’s a distinctly non-trivial benefit. Of course, it goes both ways: as Facebook’s program has moved forward, some team members have moved on, using their expertise to start and operate bug bounty programs elsewhere. Facebook wishes them godspeed: We’re proud of former team members who’ve helped us along the way and continue to launch new programs around the world. Source: Sophos
-
- attacks
- bug bounty
-
(and 3 more)
Tagged with:
-
Verizon could reduce the price it will pay to acquire Yahoo, or walk away from the deal completely. That could happen if Verizon cannot be reassured that the consequences of Yahoo's massive data breach hasn't had a material impact on the troubled search engine's business, reports BBC News: A legal representative for Verizon, Craig Silliman, told reporters: "I think we have a reasonable basis to believe right now that the impact is material and we're looking to Yahoo to demonstrate to us the full impact. If they believe that it's not then they'll need to show us that." He added that Verizon was "absolutely evaluating [the breach] and will make determinations about whether and how to move forward with the deal based on our evaluation of the materiality". A clause in the agreement of the takeover purchase states that Verizon can withdraw if an event "reasonably can be expected to have a material adverse effect on the business". You can't really blame Verizon. If they're going to spend close to $5 billion buying Yahoo, they're going to want to be sure that there aren't any nasty surprises still waiting to be unearthed. For those of you haven't been following the story, here's a quick catch-up: Yahoo, data breaches and security snafus May 2013: 200 million users of Yahoo Japan are advised to change their passwords, after hackers allegedly accessed a database of 22 million Yahoo Japan email addresses. Sept 2013: Marissa Mayer, CEO of Yahoo, says that she doesn't have a passcode on her smartphone. A security firm wins a paltry $12 Yahoo t-shirt as a reward, after reporting a vulnerability to Yahoo that could have allowed a hacker to hijack any Yahoo user's account. Late 2014: Hackers break into Yahoo's systems and steal over 500 million users' credentials, including names, email addresses, telephone numbers, dates of birth, hashed passwords and security questions and answers. The hack is not discovered by Yahoo for almost two years. June 2015: Alex Stamos, a respected member of the computer security industry, quits his job as head of security at Yahoo to join Facebook. According to some sources, Stamos left Yahoo after the company did not consult with the security team before giving in to a US government request to scan every incoming email with snooping code that itself could have been exploited by a hacker. May 2016: US Congress blocks all emails coming from Yahoo, after being hit by a wave of ransomware attacks from compromised Yahoo accounts. Jul 2016: Telecoms giant Verizon announces it is acquiring Yahoo for almost $5 billion in cash. Aug 2016: A hacker offers for sale on the dark web what he claims are 200 million stolen Yahoo credentials. Yahoo begins to investigate whether it might have suffered a data breach. Sept 2016: Yahoo confirms it suffered a massive hack in 2014 that saw attackers steal details of 500 million accounts. The hack also impacts users of BT Yahoo, Sky and other services. Yahoo users are advised to change their passwords, if they have not changed them since late 2014. Yahoo claims the attack was "state-sponsored", although some observers pour cold water on the theory. It is revealed that Yahoo rejected the option of resetting users' passwords two years ago as a site-wide security measure. Yahoo is sued for the 2014 hack. Oct 2016: Yahoo is accused of making it harder for users to leave the service, after taking away the option of auto-forwarding email to external accounts. Verizon says that the hack could impact its acquisition of Yahoo. Source: Graham Cluley
-
How do you think your customers would feel if they visited your business’s website one day and were greeted with an offensive image, malicious code, religious propaganda or a form designed to steal their passwords? My guess is that you wouldn’t be happy, and your customers would be concerned that your website might have been hacked and that their personal information could have fallen into the hands of criminals. So how would you feel knowing that hackers could pull off an attack like this without changing a single byte of your website’s code? Without even having to access the content on your web server. Welcome to domain hijacking. The first thing to realise is that the internet is built on numbers. Although you might know websites like google.com, ebay.com or bitdefender.com by their names, that’s just a convenient shorthand to make it easier to remember how to visit your favourite sites. When you browse to a website by entering a URL – icann.org, for instance – your request is converted into a sequence of numbers understandable by the internet, known as an IP (Internet Protocol) address. Internet ‘telephone directories’, known as DNS (Domain Name System) records, match names to IP addresses, meaning that your request to visit icann.org tells your browser to visit a web server hosted at the IP address of 192.0.32.7. So far, so simple. But, imagine what can happen if a malicious hacker manages to alter the DNS records for your website, held at a third-party registrar. That could mean that anyone trying to get to your website via its human-readable name, could instead be taken to an IP address under the control of a malicious hacker, rather than your company. Just such attacks have happened in the past against well-known sites including WhatsApp, anti-virus firms AVG and Avira, and this week managed to take down Blockchain.info, the world's most popular Bitcoin wallet service. It’s important to emphasise that the websites themselves have not been hacked, and user information has not been exposed. Instead, criminals are simply redirecting legitimate visits to the website to go to sites under their control instead. And, in the case of Blockchain.info that meant that some eight million Bitcoin wallets were inaccessible to their owners – at least until the issue was resolved. Blockchain.info issued a statement, explaining it was working on a fix: "Earlier today, we discovered our DNS registrar had been compromised. We took immediate action to resolve the issue. To be abundantly cautious, we’re waiting for the DNS to propagate universally across the web before bringing our services back. Once DNS has propagated, we expect to restore services ASAP. Our sincerest apologies for any inconvenience." Blockchain.info is now accessible to the world again, and customers can access their Bitcoin wallets. But it’s easy to imagine how just such an attack could have panicked users, or could have attempted to steal login credentials. Furthermore, it’s not just website traffic which can be re-routed via a DNS attack. The attackers could also start receiving a targeted domain’s email traffic too – opening opportunities for criminals to commit all manner of other crimes based on the information they receive. So how can you stop your website domain from suffering a DNS hijack? You typically make changes to your website’s DNS entry by communicating with your registrar via email, their website or a telephone support call. And that’s where a hacker could potentially strike. If they manage to access your account at your DNS registrar (perhaps because you foolishly reused a password, or had not enabled two-factor authentication) then they have carte blanche to make whatever changes they wish to your entries and hijack traffic supposed to go to your website. Similarly, if your email account is not properly locked down with decent security (again, two-factor authentication can play a part here) then they could trick your domain registrar into changing your website’s DNS entry. Finally, good old fashioned social engineering could see a bold attacker phoning up your domain registrar and pretending to be you in order to request a password reset, and then make additional changes to your DNS entries. My recommendation is that you enable two-factor authentication. Even if an attacker manages to get their hands on your credentials, a password alone is not going to grant them access to your account so their job will be much harder. Secondly, ask your domain registrar to phone you in the future, to confirm that you really want to make a change to your website’s critical DNS records. It may be your last chance to stop a malicious attacker meddling with a vital tool of your business. And finally, of course, make sure that your domain name records are protected by a decent password. That means a password that you’re not reusing anywhere else, a password that you haven’t shared with others, a password that is strong, complex and impossible to guess. Source: Bitdefender