-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
-
-
I feel your pain and aggravation, Kick. What is really annoying to me is, if you do not log in to your Yahoo mail account at least once every ninety days, they automatically de-activate it. Yet when you want your account closed, you must jump through hoops to try and get it shut down, only to no avail.
-
Unconventional
-
-
-
-
In the madness of the holiday shipping season, mistakes are not uncommon. Sometimes, lucky shoppers find themselves on the winning end of those mistakes, like when you get 99 extra knives or when a retailer sends four iPods instead of one. So what's an honest consumer to do? To put it simply: you can keep it. According to the Federal Trade Commission, you have a legal right to keep unordered merchandise and consider it a free gift. That's because federal law prohibits mailing unordered merchandise to consumers and then demanding payment. This question came up recently for Consumerist reader M., who says she ordered an iPad for her mother during Target.com's Black Friday promotions. Her mom ended up with two iPads instead of one, and she asked Consumerist what she should do how could she trust that the returned item would be put back into Targets inventory if she brought it to a store? Would she get an accidental refund on the item if she initiated the return process online? In these situations, a Targets first recommendation is for customers to call a Target.com service rep at (800)591-3869, a spokesperson told Consumerist, noting that guests’ first option is to keep or donate the extra item. “If a guest chooses not to do that, we have an exceptions process where they can return the product in the mail, the spokesperson explains. They should speak with a Target online guest service representative for instructions, and then return the item to us with all order information removed from the package. In general, though you're not legally obligated to tell the seller, if your conscience is pushing you in that direction, the FTC suggests that you notify the seller and offer to return the merchandise, so long as the seller is the one who will pay for all of the return shipping. Give the seller a specific and reasonable amount of time (say 30 days) to pick up the merchandise or arrange to have it returned at no expense to you,� reads the FTC’s FAQ on this topic. Tell the seller that you reserve the right to keep the merchandise or dispose of it after the specified time has passed. Consumerist reader M. is far from alone in receiving merchandise she never asked or paid for: There was the time Williams Sonoma sent a customer 99 knives though he only wanted one; The Consumerist reader who received an Amazon package that was intended for a person who previously lived at his address; The Lululemon customer who received 19 extra running hats in the mail and was told to keep them all; The shopper who ordered one iPod Touch from Walmart and instead, got five devices in the mail; And then there was the year Best Buy seemed intent on sending folks five iPads instead of only one not once, but at least twice, to two different shoppers. Source: Consumerist
-
- 1
-

-
- free gift
- holiday shipping
-
(and 2 more)
Tagged with:
-
-
It's been a big holiday weekend in the United States, with some folks going crazy ape bonkers over the retail bargains available. And today is Cyber Monday when online retailers tend to jump on the bandwagon too. So, it was good to hear that the FBI was going to offer some timely advice for online shoppers over the holiday season. What was disappointing, however, was the advice they offered when they tweeted this: Shopping online this holiday season? Keep your accounts secure, use strong passwords & change them frequently. [HASHTAG]#cyber[/HASHTAG] [HASHTAG]#blackfriday[/HASHTAG] I like the advice to use strong passwords (although mentioning that they should also be *unique* passwords that you aren't using anywhere else would have been helpful). What I don't like is the advice that shoppers should change their passwords regularly. As we have discussed before, regularly changing passwords (unless there's a good reason to believe that passwords need to be changed - such as having a weak password, password reuse or a breach) can lead to folks making poor password choices that actually reduce security rather than increase it. You can find out more in this video I made earlier this year: Source: Graham Cluley
-
- cyber monday
- fbi
-
(and 2 more)
Tagged with:
-
-
San Francisco’s transport system, known as Muni, was hit hard by a ransomware attack this weekend that forced the network to offer free rides to passengers. More than 2000 systems at the public transport agency are believed to have been hit, including Windows workstations, servers and ticketing machines. The first many users would have known that their computer was infected would have been on boot-up, as the modified MBR displayed a stark ransom demand: “You Hacked, ALL Data Encrypted. Contact For Key(cryptom27@yandex.com)ID:681 ,Enter.” Despite the attack, the Muni rail and bus network continued to run, but with passengers allowed to travel for free. The ransomware, which is thought to have struck on Friday afternoon, is a variant of HDDCryptor, that uses freeware and open source tools to encrypt hard drives and network-shared files, and overwrite the master boot record (MBR) on infected computers. Inevitably, the attack and its consequences has made for news headlines and TV reports, but it seems quite possible that the San Francisco Municipal Transport Agency (SFMTA) was not specifically targeted by the extortionists. Instead, it’s very believable that the transport system was an unfortunate chance victim in the way that many individuals and companies fall foul of ransomware every day – by opening a malicious email attachment, visiting a boobytrapped website, or downloading a malware-infected file. When journalists at the SF Examiner contacted the email address displayed on infected computers, the alleged attacker claimed that an SFMTA employee downloaded an infected torrent file. By Sunday it appears that ticketing systems were returning to normal operation, and passengers were once again expected to purchase travel tickets. Journalist Steve Ragan of CSO Online was successful in getting the extortionist to send him his demand: if You are Responsible in MUNI-RAILWAY ! All Your Computer’s/Server’s in MUNI-RAILWAY Domain Encrypted By AES 2048Bit! We have 2000 Decryption Key ! Send 100BTC to My Bitcoin Wallet , then We Send you Decryption key For Your All Server’s HDD!! We Only Accept Bitcoin , it’s So easy! you can use Brokers to exchange your money to BTC ASAP it’s Fast way! At the current exchange rate, 100 Bitcoins is equivalent to over US $70,000. However, there is no indication that SFMTA has paid any ransom, and it’s perfectly possible that SFMTA would be unwilling to give in to the extortion for fear that it will only encourage more attacks in future. One hopes that the organization has an effective disaster recovery strategy that means they are able to recover from clean backups in a prompt fashion and bring systems back to full working order. One thing is clear about such a high profile attack. Law enforcement agencies will be keen to bring whoever was responsible to justice, and the attacker – wherever they might be in the world – might be regretting that their random ransomware victim will result in such attention being shone on them. I have no doubt that the authorities are already investigating, and questions will be being asked as to how Muni’s systems could be better protected from future internet attacks – which could have much more serious consequences. Source: TripWire
-
- free rides
- infected
-
(and 2 more)
Tagged with:
-
-
-
If you plan to shop on Amazon.com this holiday season, be warned. There's a new scam afoot, and the con artists are using Amazon to steal your money. Based on the number of complaints reported to Bamboozled from across the country in the past few months, the problem is widespread, if not rampant. Amazon isn't doing anything about it, according to shoppers who fell victim to the scam. Given that we're at the start of the busy holiday shopping season, one might think Amazon wants to warn its customers. The retail giant is staying silent. We've reported before about fake third-party sellers who lure buyers to leave Amazon's site when it comes time for payment. Through untraceable wire transfers, the fraudsters take money for items they never deliver. This time, the scammers are using Amazon gift cards to pull off the fraud. And it seems to be working beautifully. The dozens of complaints reported to Bamboozled share essentially the same story. And, the readers agree, Amazon hasn't done a thing to help. We reached out to Amazon about these cases and to ask what it's doing to protect consumers as the holiday shopping season gets underway. It hasn't responded to our inquiries. Here's a look at what's happened to some shoppers who put their trust in Amazon. Nick Gladis of Frenchtown wanted to buy himself a birthday present. He decided to buy himself a drone. "It was the biggest purchase I'd made for myself in years," he said. Looking on Amazon on Nov. 1, Gladis found the product he wanted for $500. The seller's ad told him to text the seller before placing the order. A screenshot of some of the many messages between shopper Nick Gladis and a scammer posing as Amazon. Nick Gladis What followed was a series of texts and emails -- emails that looked exactly like authentic Amazon emails -- in which Gladis was instructed to purchase an Amazon gift card to make his payment. He gave the gift card numbers to the seller, and the seller took the money. But no product arrived. When he realized something was wrong, Gladis contacted Amazon. Amazon said the gift card had already been used and nothing could be done to recover the money, Gladis said he was told. "Amazon simply does not care and has very little to say about it, and wants it brushed under the carpet so that they don't have a sketchy name," Gladis said. "Amazon received the money I was scammed for either way." In essence, with the gift cards being used as payment, Amazon has unwittingly become a middleman for fraud, and it's profiting as more gift cards are purchased. And, Gladis said, the phony seller continued to post items on Amazon even after he reported the scam. "That's absolutely unforgivable," Gladis said. He asked Amazon to share information on the fake seller, such as the seller's IP address, but Amazon wouldn't give Gladis any information. THE COMPUTER Gladis isn't the only one reporting this kind of scam and the lack of action by Amazon. Kevin Donaldson of Tempe, Arizona, decided to buy a refurbished computer from a third-party seller on Amazon. On Nov. 3, he found one for $441. Next to the shipping information, the listing said buyers should email the seller before placing an order, and it gave an email address. Donaldson said he figured the email request was to confirm the item was in stock. He put the item in his Amazon shopping cart and emailed the seller. The seller asked for information on the system he wanted, Donaldson said. "After confirming that they had the computer in stock, I noticed in my shopping cart, for that computer, the price had jumped $200," he said. "Since I did not want to lose the deal, I wanted to push the order through to lock in the price." A screen shot of a listing by a phony Amazon third-party seller. The listing instructs customers to email a non-Amazon address before placing an order.Kevin Donaldson He then received an email full of Amazon logos and fonts, giving him link to what was supposedly an Amazon "e-payment" page. He was instructed to buy a gift card and submit the numbers to the seller. "It was Amazon's gift card," he said. "I should have stopped then. I thought that hey, I am using Amazon, I am using an Amazon credit card and they are asking for a Amazon gift card. Everything is directly through Amazon, which I trusted." Within 10 minutes of completing the purchase, Donaldson realized the transaction wasn't showing on his Amazon account. He immediately contacted Amazon and explained he thought he was scammed, and he asked the company to stop payment on the gift card. "They said they could do nothing," Donaldson said, noting he offered all his contact with the seller as evidence. He said the rep suggested he call the police. After continued attempts to get help from Amazon, Donaldson said, the company won't respond to him anymore. "I have not used profanity on any level with them and they have halted communication," Donaldson said. "Amazon only seems interested in working with sellers and have no backing for their customers." THE GENERATOR Ron Eberle of Merritt Island, Fla., tried to buy a $1,000 generator from a third-party seller on Nov. 7. He tells a story similar to other scammed shoppers. Eberle said the generator ad told buyers to text a telephone number before placing an order. He did, and the response instructed him to email the product number and delivery address. The response said, "Amazon will confirm your order and guide you through the payment process once we will receive your details." Eberle asked if he could use his debit or credit card, but the seller didn't respond. Eberle later received an email that used Amazon's logos and fonts and color schemes. The writer said he was from "Amazon Customer support Purchase Protection Program Department." The confirmation email Ron Eberle received from a scammer impersonating Amazon.com. Ron Eberle It confirmed the purchase order number, and said the purchase was eligible for Amazon's buyer protection program. The email instructed him to buy Amazon gift cards, and it listed retailers where he could buy the cards. Eberle did as instructed, buying two $500 Amazon gift cards and giving the numbers to the fake Amazon employee. The next day he received a new request for $1,000 more. Insurance was needed on the purchase for the transaction to go through. "The payment will be secured by our service and you will have your money back once you receive the product," the email said. That's when Eberle realized something was wrong. He tried to cancel, but the seller never responded. Eberle reported the scam to Amazon, which he said offered nothing to help him get his money back. "I feel like a real dumbbell, but the third-party seller emails looked legit, and the real concern for everyone, I think, is that I never would have suspected a fraud scam that I believe was enabled through the Amazon website management," Eberle said. "How many others got robbed?" In the week following the scam, Eberle monitored similar products and found many similarly phony sellers on Amazon, he said. He shared the images with Bamboozled HOW TO AVOID THE SCAM We asked Amazon for protection tips for you, dear readers, but it didn't answer. So here are our suggestions. First, while there are opportunities to contact third party sellers to ask questions about items, the only legitimate contact you would have is on Amazon's site. At the bottom of most items for sale, you can find a Q&A area where you can ask questions, and the seller will respond right there. If a seller tells you to call, text or email for any reason, don't do it. Find another seller. If you do end up in a conversation with a seller, never follow any links where you can supposedly make a payment. The seller may tell you the transaction is covered by Amazon. Well, it's only covered by Amazon if you pay through Amazon Payments directly on the Amazon page -- not on an impersonation page that's made to look like the real thing. And never pay with an Amazon gift card the seller tells you to buy. If you have a gift card, sure, use it -- through Amazon Payments. No legitimate seller will tell you to buy new gift cards to pay for any product. We tried to find Amazon warnings about this new abuse trend, but we couldn't find anything. Sure, it offers a page on how to avoid payment scams, and a page on how to tell if an email really is from Amazon. But what it doesn't seem to do is warn shoppers at the point of purchase that these kinds of scams are out there. Amazon, can't you do better for your customers? Source: Bamboozled
-
- amazon
- con artists
-
(and 1 more)
Tagged with:
-
-
The Fareit trojan is using an uncommon file type as a disguise as it is spread via phishing and other spam mail campaigns. Fareit has been around for a little while now, and we all know that Locky ransomware and other malicious programs hide within .zip, .js, and other file types to trick unsuspecting users into opening them. But the Fareit trojan is doing something a bit different in this campaign: See that Payment_Advice.mht attachment at the bottom of the scam email? Like in most spam campaigns, the attachment's disguised as a document having something to do with payment. But unlike other malware campaigns, it's using the .mht file type. Researchers at Cisco Talos explain what that is: "MHT files, also referred to as .mhtml files, are MIME HTML files. These files are commonly created when trying to save a document or other content as a web page. MHT files can be created using various types of applications including web browsers and word processors. In this case we found a small spam campaign purporting as a billing payment document from HSBC." It wasn't easy linking the fake attachment to Fareit. Looking at the .mht file, the researchers found two things: a link to a .hta file and an inexplicable reference to the musical group Deftones. Source: Cisco Talos The team experienced some difficulty in analyzing the .hta file, for someone had cleaned up the compromised website and taken down the file. But that didn't stop the researchers: "Talos was placed in a situation where there was a threat that was once active but had been cleaned up. This is a common problem and provides an opportunity to demonstrate how data and threat intelligence can be used to find the missing links and rebuild the infection chain. In this particular case we had URL pointing to an hta file that no longer existed. We were able to find instances of the file being blocked from being downloaded. Normally that would not be particularly interesting, but in this case we were able to find a file hash (a95a01472fdb42a123e1beb6332cb42c9372fdfe33066b94a7cabdac3d78efe1). We then started searching through various data sources for the file in question and found it in multiple locations including VirusTotal." Even then, they weren't in the clear just yet. An analysis of the file uncovered a vbscript that pointed to an even more elusive file. Using the same techniques, they searched the file based upon its URL path and name to arrive at a hash. It was then that the researchers finally linked the spam campaign to Fareit. Clearly, attackers are willing to go to extreme lengths to avoid raising a red flag among users and security researchers. Sometimes that involves using a file type that people don't ordinarily come across. But that works both ways. Just as malicious programs don't often disguise themselves as .mht files, ordinary users rarely if ever receive a file of the same format attached to one of their emails. Computer users should therefore follow the advice that's paradoxically set forth in Fareit's spam email: they should never open emails sent from suspicious sources, especially those that contain unusual file types. Source: Graham Cluley
-
- fareit trojan
- malicious
-
(and 2 more)
Tagged with:
-
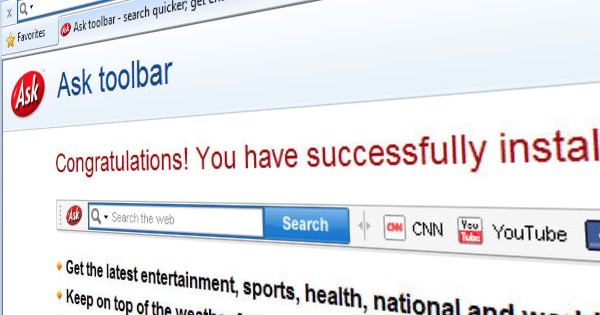
An unknown attacker hijacked the update mechanism employed by Ask Partner Network (APN) to download suspicious code onto unsuspecting users' PCs. APN is best known for the Ask.com search engine browser toolbar. It's a potentially unwanted program (PUP) that is infamously bundled with installers for Java. The Ask toolbar and other software designed by APN, a so-called provider of "solutions to help software developers acquire and monetize users," have annoyed users for years. Given their bundling-based distribution method, the manipulation of search results, and their persistence as downloaded software, it's no wonder Microsoft decided to block the Ask toolbar in 2015. Even so, many users have chosen to not remove the Ask Toolbar. That might be because the programs themselves have - for the most part - never directly threatened people's computer security... that is, until recently. The research team at Red Canary came across an issue in the beginning of November, as they explain in a blog post: "On 5 November, Red Canary detected suspicious activity associated with Windows applications distributed by the Ask Partner Network (a.k.a. APN, Ask.com, or simply Ask). Upon further inspection, we discovered that Ask’s software was being co-opted by a malicious actor to execute malicious software on victims’ endpoints" The team spotted some Windows processes associated with Portable Executable (PE, or "binary") files having abnormal extensions. In particular, they detected apnmcp.exe, the update mechanism for Ask Partner Network, associated with a image file named logo.png that was signed a bit too recently for their liking. Curious, the researchers dug a little bit deeper and observed some suspicious behavior: "Note the network connection initiated by logo.png, which was used to pull down 2-3 unique, later-stage binary files that were then executed by logo.png before logo.png itself was deleted from the disk. "Of the dozen victims that we observed, all of the first stage (logo.png) binaries were unique, but the later-stage payloads were the same across all victims. Our suspicion is that we caught this during the early stages of deployment or testing, as these processes took very few actions on the victim endpoints. This may have been intentional, or it may have been due to bad payloads or configurations." A complete listing of the binaries is available on Red Canary's website. So what can we learn from this story? We already know that PUPs are a nuisance. But what we don't know is to what degree providers like APN invest in maintaining their solutions. They might not be following security best practices, which means an attacker could compromise their software and try to infect unsuspecting users. With that being said, it doesn't matter what the potentially unwanted program is. It still constitutes a potential security threat. Therefore, if an unwanted program downloads itself onto their computer, users should remove it as soon as possible. Period. Source: Graham Cluley
-
-
-
I had to leave the site ClickClickClick. It wasn’t too happy about it. I turned the audio on, as ClickClickClick told me to do, so I can still hear the site begging me not to go. Are you still there? You haven’t been around for quite some time now. I’m thinking, do you still like me? The running audio commentary on my clicks, mouse movements and activity/inactivity is made in a jaunty Dutch accent – the site was created by Dutch media company VPRO and the Amsterdam-based interactive design company Studio Moniker. It’s a simple site – a white screen with a big green button labelled “Button” in the middle – and it has a simple mission: to observe and comment on everything that visitors do on the site, in great detail, and to thereby remind visitors about just how closely our online behavior is monitored. As a cyber wolf would have said to a cyber Little Red Riding Hood, all the better to profile and target-market at you, my dear! Wait… is ClickClickClick sniffling? Is it crying? Subject! Stay focused! …inactive… waiting possibly for something to happen? Come on, subject. You were being so great. Do something. Moving around a lot now. Curious and energetic. Interesting. Studio Monkier designer Roel Wouters told news.com that ClickClickClick was designed to remind people about the serious themes of big data and privacy. Fellow designer Luna Maurer said that her own experience with target marketing came into play: I am actually quite internet-aware, but I am still very often surprised that after I watched something on a website, a second later I get instantly personalized ads. There’s nothing unique about ClickClickClick’s tracking. The only thing that’s unique is that it’s upfront about it, letting us see the granularity of that tracking in an ongoing log that streams on-screen with notations including where on the screen you moved, whether you zigzagged or moved straight, how many pixels, how long you were inactive and the like. No, there’s nothing new about any of it: capturing the X and Y coordinates of where the cursor is on a page is a simple task in Javascript, and it has been for a very long time. Back in 2013, Facebook was mulling silently tracking users’ cursor movements to see which ads we like. Some reacted to the possibility by swearing off Facebook entirely. It’s not just Facebook, though: any site can do it. It’s very easy. It’s the job of user interface designers to understand how people interact with web interfaces. Their job is to figure out where users have problems and how to improve their overall experience. Collecting user behavior on sites enables those designers to work on issues such as where and why users drop off at a checkout page on an e-commerce site, for example. They do it through mouse tracking, heat maps, click tracking, or eye tracking, among other techniques. Unusual behavior… Subject has been gone for 10 minutes… Very slow. Boring like hell. If the thought is off putting, what’s the answer? Swearing off Facebook, or smart pages by witty Dutch programmers, isn’t going to stop you being tracked minutely online. And unlike ClickClickClick, you won’t know when it’s happening. So you either have to put up with it, stop using the web or use something like NoScript – an extension that blocks JavaScript, Java, Flash, Silverlight, and other “active” content by default in Firefox – to block the execution of scripts that you’re unsure of. Subject seems unsatisfied… hmmm… is subject thinking about Facebook or something? No, you funny Dutch psychotherapist cyber bloodhound, I’m not thinking about Facebook. I’m thinking of all the other stunts sites can pull using JavaScript – like this one, where JavaScript was being used to slip files in quietly and automatically, like a drive-by download. Subject possibly neglects social obligations. A loner? [yawn]. A loner? Possibly! But still open to being chatted up, and educated, by a site like ClickClickClick! Source: Sophos
-
- activity/inactivity
- clickclickclick
-
(and 2 more)
Tagged with:
-
[HASHTAG]#BrickPony[/HASHTAG], a life-size LEGO® replica of the "1964½" Ford Mustang V8 coupe, will go on permanent display outside the Ford Driving School attraction at LEGOLAND® Florida Resort in Winter Haven, Fla.
-
You would think an iPhone 7 is an iPhone 7, right? Apples famous for making one consistent device that's the same inside, and works the same way, from carrier to carrier. So its a little surprising that one carriers version of the phone actually could work faster than another and even more surprising that Apples set it up not to perform as well as it can. The Verizon Wireless version of the iPhone 7 is technologically capable of downloading data at 600 Mbps over LTE. That's super fast! But as two research firms told Bloomberg News, in practice the phone is not optimized, and can't exceed 450 Mbps the maximum download speed that the competing AT&T iPhone 7 can reach. Now, granted, most users won't notice the difference. Real-world tests, like the one PC Mag runs every year, find that the average 4G LTE connection speed you get ranges between 19 and 30 Mbps depending what city you're in and which of the four major carriers you're using. The top download speed recorded in their tests last year was 160 Mbps, on a Verizon phone in the northwest part of the country. That means the 450 Mbps download speed a Verizon iPhone 7 limits itself to, and that AT&T users get, is still a solid four times faster than anything most users will ever be able to connect with. iPhone parts are sourced from a whole bunch of different companies. It's not just that one company makes glass and another makes CPUs and a third makes modems; for a huge number of internal components, there are several different manufacturers for each individual part, too. That's basically the key difference here, the research firms tell Bloomberg: the Verizon/Sprint model has a Qualcomm chip in it; the AT&T/T-Mobile one uses a slightly different Intel chip. The Qualcomm one is both newer and faster than the Intel one. MORE: It takes dozens of companies to make your iPhone Still, analysts told Bloomberg it's straight up weird for a technology company to throttle itself in this way. But that brings us back to the top, and most consumers (and developers!) assumption that an iPhone is an iPhone is an iPhone. They don't want one version to get the reputation that it is better, one analyst told Bloomberg. If Apple had a guiding principle, it's that they want to make sure customers were having a consistent performance. Other analysts pointed out that not only does Apple need to create a unified customer experience, but also will want to keep all wireless carriers equally happy. Apple likely has some incentive to balance the performance of its iPhones across its U.S. operator partners,� a different expert told Bloomberg. It would be difficult, for example, to explain to AT&T, which remains the U.S. carrier with the most iPhone subscribers, why Verizon is offering a superior product. Was this helpful? We’re a non-profit! You can get more stories like this in our twice weekly ad-free newsletter! Click here to sign up. Apple Chip Choices May Leave Some IPhone Users in Slow Lane [bloomberg]
-
-
More than 50 years ago, on November 20, 1963, MIT's campus newspaper The Tech published what is believed to be the first ever mention of computer hacking. Many telephone services have been curtailed because of so-called hackers, according to Profess Carlton Tucker... The hackers have accomplished such things as tying up all tie-lines between Harvard and MIT, or making long-distance calls by charging them to a local radar installation. One method involved connecting the PDP-1 computer to the phone system to search the lines until a dial tone, indicating an outside line, was found. It was a different time - Kennedy was just a couple of days away from being assassinated, and in a few months The Beatles would appear on the Ed Sullivan show. So next time your parents or grandparents shake their heads about the malicious hacks that take place today, perhaps point them towards this and remind them "It's your generation which started all this!" According to MIT, the word "hack" itself (in terms of meddling with technology, at least) dates back even earlier, to 1955. Learn more by reading the article on MIT's Slice. Source: Graham Cluley
-
- 1
-

-
- 50 years
- computer hacking
-
(and 1 more)
Tagged with: