-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
-
-
Google’s come up with a “naughty” tag for repeat offenders of its Safe Browsing search policy. Starting on Tuesday, it’s set about flagging such sites as “repeat offenders,” giving them a 30-day time-out that prevents webmasters from simply stopping their bad behavior, showing Google their site is clean and then immediately resuming their hi-jinks. Brooke Heinichen, from Google’s Safe Browsing Team, said in a post that the team has seen a “small number” of websites that run afoul of Google’s policies – including its Malware, Unwanted Software, and/or Phishing and Social Engineering Policies – who stop the behavior for long enough to have the warnings removed, and then go right back to whatever they’d been doing. Safe Browsing’s been around since 2005. In 2014, Google added unwanted software download alerts to Safe Browsing warnings, to give users a heads-up when software was doing something sneaky. That could be switching your homepage or other browser settings to ones you don’t want, piggybacking on another app’s installation, or collecting or transmitting private information without letting a user know, for example. Last December, Google extended the service to Chrome, to protect its free-range users. Site operators whose sites fell foul of Google’s Safe Browsing policies were previously able to bring their site into compliance and then request an immediate review of it via Google’s Search Console. Under the new Repeat Offenders policy, webmasters for sites flagged as a Repeat Offender won’t be able to request additional reviews via the Search Console before 30 days have elapsed. During that month, users will see warnings when they visit the offending pages. Repeat Offender site webmasters will be notified that their sites have been labeled as such via email to their registered Search Console email address. This type of quarantine will only be applied to “those sites that repeatedly switch between compliant and policy-violating behavior for the purpose of having a successful review and having warnings removed,” Heinichen says. Sites that have been hacked won’t be labeled as Repeat Offenders; rather, only those that “purposefully post harmful content.” Google’s been hot for tagging risky sites lately. Besides the new Repeat Offenders tag, its years-long campaign to see all sites encrypted with HTTPS included a September announcement that, starting in January 2017, it would start slapping a warning on non-HTTPS sites. Google said that starting with Chrome 56, password or credit card form fields on non-encrypted sites will be labeled “not secure.” Then, in following releases, those HTTP warnings will be extended: for example, by labeling HTTP pages as “not secure” in Incognito mode, where users may have higher expectations of privacy. Eventually, all HTTP pages will be labeled non-secure, and the HTTP security indicator will change to the red triangle/exclamation mark that Google uses for broken HTTPS. Informing users of unsecured sites with tags is no doubt a step in the right direction. But tags can be ignored. There’s nothing stopping users from clicking on an unsafe link, nor from ignoring Google’s subsequent warning page. As it is, researchers have found that people ignore security alerts up to 87% of the time. If Google progresses from this 30-day time-out to something more permanent – say, e-excommunication? – we’ll let you know. Source: Sophos
-
One assessment of the Internet of Things (IoT) is that 2016 has been a bad year. Its woes aren’t hard to locate from the infamous Mirai botnet that led a collection of webcams, PVRs and surveillance cameras to summon up the biggest DDoS in history to a growing unease over privacy. Now, just when you thought it was safe to turn on the light, an Israeli-Canadian study has uncovered a weakness in the design of Philips Hue smart light bulbs that it believes a hacker could use to launch an improvised wireless worm. The attack works by targeting the Atmel ZigBee wireless chip inside each bulb which should, on the face of it, be highly secure. It’s cloaked in layers of cryptographic and non-cryptographic defences which also limit the proximity required to issue new instructions to mere centimetres. Unfortunately, the chip’s proximity detection firmware has a security flaw which allows this to be extended by up to 400 metres, rendering it vulnerable to takeover after issuing a factory reset. The team even came up with a memorable proof-of-concept that involved taking control of bulbs from a drone – dubbed war flying – before flashing back each bulb’s captured status as an SOS in Morse code: What harm could an attacker possibly do with remote control? According to the study’s authors an attack would only need about 15,000 devices in order to spread effectively through a city the size of Paris – a density they claim has “almost certainly been surpassed already”. Hue light bulb users needn’t worry though – the researchers shared details of their attack with Philips in the summer and make it clear that Philips “have already confirmed and fixed the takeover vulnerability”. Philips have posted a statement on their website that reads: Researchers contacted us in the summer about a potential vulnerability and we patched it before the details of findings were disclosed publicly. At no time was a virus created or used to infect any Philips Hue products. We recommend all our customers install the latest software update via the Philips Hue app, as with any other update that we release, despite assessing the risk to Philips Hue products as low. Although there’s no danger for Philips customers today the research is a signpost to what might be possible if the IoT’s security doesn’t improve as the density of devices gets ever greater. The attack can start by plugging in a single infected bulb anywhere in the city, and then catastrophically spread everywhere within minutes, enabling the attacker to turn all the city lights on or off, permanently brick them, or exploit them in a massive DDoS attack. Ironically, the bigger worry is not that this type of ZigBee-based device is connected to the internet but that it isn’t. By using ZigBee, humble devices such as light bulbs can communicate and interact with one another independently of the very communications systems that could be used to remotely exert some control in the event of a worm-like incident. It’s not even clear how defenders would locate the original hacked bulb let alone neutralise it, a problem the researchers liken to stopping a biological infection such as influenza. In a process resembling a nuclear chain reaction, hackers can rapidly cause city-wide disruptions which are very difficult to stop and to investigate. All this to make lights ever so slightly easier to turn on and off. We have been warned. Source: Sophos
-
-
In its latest SEC filing, Yahoo admits some people knew of the 2014 breach shortly after, that the true cost of the breach is still unknown, and that the breach could affect its deal with Verizon. Yahoo has for the first time admitted that staff knew about the data breach two years before it was confirmed publicly, and that the incident could affect the $4.83bn sale deal with Verizon. The internet firm confirmed the breach that is believed to have affected at least 500 million user accounts on 22 September 2016, claiming it first discovered the breach in August 2016, a month after the deal with Verizon. But now, in a US Securities and Exchange Committee (SEC) filing, Yahoo has admitted that some staff knew that a state-sponsored hacker had accessed its network shortly after an attack in 2014. “An Independent Committee of the Board, advised by independent counsel and a forensic expert, is investigating, among other things, the scope of knowledge [about the breach] in the company in 2014 and thereafter,” the company said in its filing. “In addition, the forensic experts are currently investigating certain evidence and activity that indicates an intruder, believed to be the same state-sponsored actor responsible for the security incident, created cookies that could have enabled such intruders to bypass the need for a password to access certain users’ accounts or account information.” The Yahoo breach is believed to be the biggest publicly reported breach of its type to date, overtaking the previous record of just more than 359 million user details exposed in a 2008 breach at MySpace. Confirmation of the breach by Yahoo led to market speculation about whether the news would scupper the deal with Verizon or at least result in a call by the telecoms group for a reduction in price. Although Yahoo has consistently maintained that it is confident in the company’s value and is working towards integration with Verizon, the SEC filing indicates that the company admits that in a worst-case scenario, the breach could affect the acquisition deal. The risks and uncertainties around the pending Verizon listed in the SEC filing include that: “Verizon may assert, or threaten to assert, rights or claims with respect to the stock purchase agreement as a result of facts relating to the security incident, and may seek to terminate the stock purchase agreement or renegotiate the terms of the sale transaction on that basis.” Commentators said while this does not necessarily mean Yahoo sees this as an immediate risk, it is interesting that Yahoo has now mentioned the possibility for the first time. Full cost still unknown Yahoo also admitted that the full cost of the breach is still not clear. While the company said the breach cost only $1m in the third quarter of 2016 and that the incident “did not have a material adverse impact” on the quarter, it said it had subsequently incurred expenses related to remedial actions. The company said it also expects to continue to incur investigatory, legal and other expenses associated with the breach. Yahoo said it will recognise and include these expenses as part of operating expenses as they are incurred, adding that the company does not have cyber security liability insurance. The filing also recognises that Yahoo may also incur costs related to the 23 putative consumer-class action lawsuits that have been filed against the company in US and foreign courts. The SEC filing has laid bare the true cost of cyber attacks, said Neil Fraser, UK manager at communications firm ViaSat. “The real risk doesn’t necessarily come from loss of intellectual property, or damage to business operations, but rather the ongoing harm to the organisation’s reputation. The cost might not be immediately apparent, but over time – or if the business is in a sensitive period – it could easily reach billions of dollars,” he said. The stakes are so high, said Fraser, that organisations need to treat cyber attacks not only as a threat, but as an inevitability. “Whether an attacker is a state, state sponsored, a criminal enterprise or a single individual looking to boost their reputation, they can cause irreparable damage. In this case, an attacker who was looking to sell the stolen data for $1,800 could easily have cost Yahoo a million times that amount,” he said. Yahoo still ‘not taken action’ needed To reduce these consequences, Fraser said organisations need to look at a number of issues, both technical and organisational. “Clearly this includes the security technology in use – from firewalls to antivirus to encryption of both the networks being used, but also the actual data so that any data that is stolen is essentially worthless,” he said. A study by Venafi Labs revealed that, by September 2016, Yahoo had still not taken the necessary action to ensure users are not exposed and that the hackers do not still have access to their systems and encrypted communications. The researchers found Yahoo was still using MD5 cryptographic hashing function for many of its digital certificates, noting that this algorithm had been known to be vulnerable for several years and suffered from many serious and well-documented vulnerabilities. Alex Kaplunov, vice-president of engineering for Venafi, said major breaches such as the one suffered by Yahoo were often accompanied by relatively weak cryptographic controls. In addition to security controls, Fraser said organisations also need to look at the training workers are given, and ensure they not only know how to reduce the risk of a successful attack, but how to react. “This includes isolating and identifying the origin, taking stock of what has been stolen or affected and making sure those who have been put at risk are notified and protected as soon as possible,” he said. In conclusion, Fraser said Yahoo’s decision not to share information about the breach earlier may prove to be costly in the long run. “For whatever reason, it seems Yahoo has deliberately delayed sharing critical information. It is this which will have the greatest effect not only on customer trust, but ultimately its reputation,” he said. The UK’s privacy watchdog, the Information Commissioner’s Office (ICO) is investigating the breach to understand the impact on UK citizens. Announcing the move in September 2016, information commissioner Elizabeth Denham said the number of people affected by the breach is “staggering” and demonstrates just how severe the consequences of a security hack can be. “There is a sobering and important message here for companies that acquire and handle personal data. People’s personal information must be securely protected under lock and key – and that key must be impossible for hackers to find,” she said. Source: Computer Weekly
-
-
-
If you’re looking for an under-21 fake ID, child porn, drugs, tips to cook meth or a hitman, the dark web might just be your best friend. But might it not be so dark, after all? A controversial report claims a lot of fiction may give the onionland an unfairly bad rep. After analyzing 400 random URLs in an automated crawler that scraped information, Terbium Labs says “the majority of the dark web contains perfectly legal content,” mostly porn- and drug- related. The analysis of dark web activity challenges common beliefs that it is mainly a place for criminals to pursue their hidden desires. “These Tor Hidden Services play host to Facebook, European graphic design firms, Scandinavian political parties, personal blogs about security, and forums to discuss privacy, technology, even erectile dysfunction. Anonymity does not equate criminality, merely a desire for privacy,” Terbium Labs says. Here’s what they actually found: many URLs are related to pornography but not all illegal, drugs and pharmaceuticals are also popular (56%), fraud comes third and extremism has only a small share of the content. In their view, legal is defined as an “activity or discussion that was not explicitly illegal,” while a page is legal “if the content on the page was legal, even if the broader site may have contained illegal information, goods, or services.” Based on this argument, the team concluded the content on the dark web is mostly legal. “We hate to break it to you: the dark web is mostly legal. Legal content comprises 53.4% of all domains and 54.5% of all URLs in our sample,” reads the report. 400 URLS are not enough to claim the dark web is a fun land where only a small percentage of ongoing activity is illegal. Many disturbing stories come out of the dark web about deviant human behavior like sexualized torture and killing of animals or crowdfunded assassinations. Let’s take a minute to remember the criminal activity bliss behind the infamous Silk Road or the Playpen case. A study by the University of Portsmouth in 2014 contradicts Terbium Labs’ research, having already revealed that the most common content searched for on Tor is related to child pornography, black markets that mediate transactions for illegal drugs, software exploits and guns, botnet operations, whistleblowing sites, Bitcoin and money laundering services and fraud. A more recent study from February 2016 confirms the previous research and adds that hacking groups sell their services to arrange attacks on banks and financial institutions. Researchers find it difficult to establish how many visitors are actual people and how many are automated crawlers run by law enforcement. “Without knowing how many sites disappeared before looking at them, it’s impossible to know what percentage of fetches went to abuse sites,” said for BBC Roger Dingledine, one of Tor’s original developers. “There are important uses for hidden services, such as when human rights activists use them to access Facebook or to blog anonymously. These uses for hidden services are new and have great potential.” Source: Bitdefender
-
- dark web
- illegal content
-
(and 2 more)
Tagged with:
-
-
Tor, the conduit for below-the-radar browsing, and drugs, weapons and other illegal activities, has been under the microscope by law enforcement in the past two years. In the past months alone, we saw Brian Richard Farrell, who helped run Silk Road 2.0, sentenced to eight years in jail for his work in the dark market. His arrest was part of Operation Onymous, which aimed to take out illegal marketplaces on Tor, back in 2014. Just this week we learned of yet another campaign to take down more illegal marketplaces on Tor. The latest move, Operation Hyperion, was a joint effort by law enforcement agencies in the US, the UK, Europe, Australia, Canada, and New Zealand, and took place between October 22 and 28. Operation Hyperion took down a number of Tor sites selling drugs, stolen identities, weapons and hacking services. It seems a number of the arrests in this latest sting were in the Netherlands, as one of the sites targeted now features a splash page from the National Police and Public Prosecution Service of the Netherlands, with usernames of active, arrested and identified vendors featured, as well as a FAQ. The FAQ helpfully suggests for anyone potentially falsely identified as a “dark market buyer” to get in touch with the Dutch police. Tor is certainly not inherently bad, as its anonymizing abilities provide protections to many users who have concerns about their privacy online, especially for political reasons. But it also attracts the illicit and illegal elements. The message from this latest joint law enforcement operation seems to be that no one is quite as anonymous on Tor as they think, and that law enforcement around the world are banding together to try to stop – or at least slow – illegal marketplaces. Do you think we’ll ever seen illegal marketplaces off of Tor once and for all, or is it a hopeless cause? Source: Sophos
-
- below-the-radar
- illegal marketplaces
-
(and 1 more)
Tagged with:
-
Thousands of holders of current accounts with the UK’s Tesco Bank were unable to access online banking on Monday after some accounts were subjected to “online criminal activity” and money was stolen from some accounts. Chief executive Benny Higgins said that “any financial loss as a result of this activity will be resolved fully by Tesco Bank”, and reassured users that any money stolen would be refunded “as soon as possible”. Tesco Bank hasn’t said how the attack happened, nor who might have been behind it. So what should Tesco Bank customers do? The advice we gave to Yahoo customers after it was revealed that 500 million accounts had been breached still holds: change your password, and if you’ve used that password on any other accounts, change the password for those accounts, too. It goes without saying that you shouldn’t use the same password for more than one account, and that’s doubly important when it comes to online banking. Make sure it’s a strong password: You could also consider resetting your security questions – and remember, they don’t have to be the actual answers to, say, your mother’s maiden name or your first pet. Those answers just have to be something you can remember – or something a password protector such as LastPass or KeePass can generate for you and recall. Keep a sharp eye on your bank statements and online balance for any dodgy transactions, and let Tesco Bank know about them as soon as possible. Watch out for emails claiming to come from Tesco Bank – or anyone else, for that matter – saying you need to reset your bank details and providing a link: it’s not unheard of for other scammers to exploit the security fears sparked by this kind of attack. If a link in such an email takes you to a page inviting you to enter your details, stop right there. It’s much safer to go to your bank’s website by typing the web address into your browser. Have a look at our post offering more detailed tips for how to keep your online banking safe for further advice – and regardless of who you bank with, it’s always a good idea to review your security practices. Source: Sophos
-
- accounts
- online banking
-
(and 1 more)
Tagged with:
-
-
In October, news broke that the CIA was preparing options to launch a cyberattack against Russia following revelations that the country was likely behind hacks at the Democratic National Committee earlier this summer. Now, a source has told NBC News that the US has penetrated key Russian systems, and will be ready to take action in case the country decides to interfere with next week’s elections. The US is preparing in case it is "attacked in a significant way" The systems allegedly include some of Russia’s telecommunications networks, its electrical power grid, and command systems at the Kremlin. NBC reported that the preparations are being made in the event that the US is "attacked in a significant way," according to an anonymous intelligence official and top secret documents that the network had reviewed. While US election infrastructure has significant flaws with outdated voting machines and voter data, the decentralized nature of the election makes it much harder for attackers to outright change the final outcome. Digital security has become a concern during this election cycle, although NBC notes that the officials it spoke with "do not expect Russia to attack critical infrastructure," although they do expect some "cyber mischief", such as releases of fake documents and digital misinformation campaigns. Source: NBC News
-
-
As far as I’m aware, rotary cell phones never existed. The two technologies didn’t overlap much in time, with rotary dials getting replaced by push-button alternatives a decade or so before portable cell phones became popular. But that doesn’t mean rotary cell phones can’t exist now, and YouTube tinkerer Mr. Volt has . It’s beautiful, minimalist, and looks heavy enough to smash a window. The cell phone itself has six basic functions: it can make calls, store a single phone number, text (very slowly), tune into the radio, display system settings, and go to sleep. There’s a 96 x 96 OLED display, its case is made from a mixture of aluminum, brass, and 3D-printed plastic, and the whole thing is powered by an Adafruit microcomputer. It would also make a hell of a statement piece. After all, anti-phones of one sort or another have been in counter-cultural fashion for a while now. Some are purpose built like the credit card-sized Light Phone, which can only make and receive calls. And some, like Nokia feature phones, are just the best phone at a certain price range that might be adopted for reasons other than price. ("I don't want to deal with apps," "I hate being distracted by my phone," etc.) The rotary cell phone would be a different beast altogether: not just restricting functionality, but actively hobbling the user with its weight and unwieldy controls. Still, if some people choose to ride penny-farthings instead of regular bikes, presumably someone would like to try out the rotary cell phone for a while. Wouldn't you, just for fun? Source: The Verge
-
-
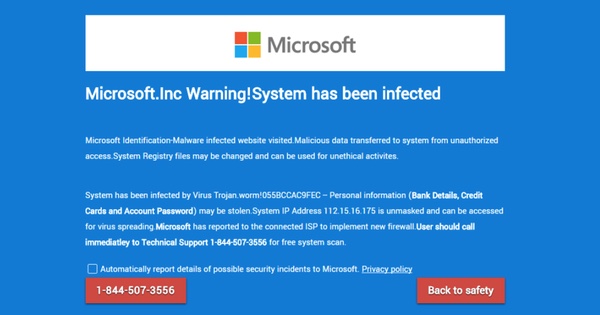
As we all know, tech support scammers like to use a variety of techniques to fool their victims into calling them up. Some impersonate a target's Internet Service Provider, while others warn a user's hard drive will have its contents deleted unless they call straight away. Clever, but not fool-proof. Thanks to the help of public security awareness campaigns, users are getting wise to these scare tactics. As a result, many scammers aren't placing as great an emphasis on scaring their victims. Instead they're concentrating on denying them access to certain functions of their computer. That's what's going on in this new scam. The ruse makes use of a vulnerability that consumes 50 percent of a machine's CPU, ramps up the RAM to 7 Mb/s, and most importantly causes the browser to hang but to not crash. All it takes to exploit the bug is a simple but excruciatingly long for loop built in JavaScript. The flaw works by abusing history.pushState() in HTML5, a method which pushes data onto the session history stack with a title and URL (if provided). Combine that with a fake Microsoft security warning screen, and you got yourself a scam that just won't go away. Microsoft. Inc Warning! System has been infected Microsoft Identification-malware infected website visited. Malicious data transferred to system from unauthorized access. System Registry files may be changed and can be used for unethical activities. System has been infected by Virus Trojan.worm!055BCCAC9FEC - Personal information (Bank Details, Credit Cards and Account Password) may be stolen. System IP address 112.15.16.175 is unmasked and can be accessed for virus spreading. Microsoft has reported to the connected ISP to implement new firewall. Users should call immediately to Technical Support 1-844-507-3556 for free system scan. Think you can terminate the process using Task Manager? You might be able to...or not. Jérôme Segura of Malwarebytes explains: "Depending on your computer’s specifications you may or may not be able to launch Task Manager to kill the browser process. Otherwise your system will be brought to its knees and a hard reboot may be the only option left. Whatever you do, please do not call the phone number for support because it is not Microsoft’s but rather a group of scammers waiting to rob you of hundreds of dollars under false pretenses." Malwarebytes has contacted the Google Safebrowsing team about the bug. It might date back to 2014, but if attackers are exploiting it to trick unsuspecting users, it's important to issue some sort of fix as soon as possible. In the meantime, users can protect themselves against this scam by avoiding clicking on suspicious links, including those that might be shortened. If they come into contact with the scam, they can try to disable the browser process using the Task Manager. If that proves fruitless, they should reboot their computer. Source: Graham Cluley
-
-
A 19-year-old UK teenager from Hertfordshire has pleaded guilty to creating and running the Titanium Stresser booter service, with which he launched 594 denial of service (DDoS) attacks. According to a statement put out by the Bedfordshire Police, Adam Mudd developed the tool when he was just 15 years old. He didn’t just use it to launch his own DDoS attacks. He also sold it online and ran it as a service, distributing it to cyber crooks. Investigators are still working out the total amount Mudd made from the attacks, but their preliminary estimate is around $385,000. Investigators determined that Mudd’s stressor – which is a tool used to flood networks with data, bogging them down until they’re dead in the water, non-functioning and vulnerable to compromise – was used in more than 1.7 million DDoS attacks worldwide. Those attacks were launched against 181 IP addresses between December 2013 and March 2015, the month that Mudd was arrested and the service was shut down. According to Silicon Angle, Mudd kept detailed logs of all the attacks that relied on Titanium Stressor. In fact, it was, for a time, the most popular DDoS-for-hire service available online. One of Mudd’s satisfied customers must have been the hacking group Lizard Squad. According to The Register, Mudd’s creation was the basis for Lizard Stresser, a DDoS tool marketed by the hacking group. Remember Lizard Squad? They ruined Christmas 2014 with a DDoS directed at PlayStation and Xbox servers, timed to make sure nobody could play games during the holiday. A spot of poetic justice was had when the Lizard Stresser service itself got hacked, spilling customer details on to the internet. Interestingly, the very same thing happened recently to vDOS, one of the most disruptive attack-for-hire services on the internet. vDOS was taken down in September, and its alleged co-owners were arrested following a “massive hack” on the site. Tens of thousands of customers’ details were spilled, along with the identities of its teenage owners. Learn More Technically speaking, those who launch these DDoS attacks aren’t hackers, given how little technical skill is required. All they have to do is harness the horsepower provided by botnets, as Sophos’s Mark Stockley noted at the time of the vDOS takedown. Those botnets contain tens of thousands of computers compromised by malware. Perhaps not coincidentally, both security journalist Brian Krebs and DNS service provider DYN – both involved in the vDOS sting – were hit by massive DDoS attacks from the Mirai botnet. As Brian Krebs has reported, Lizard Stresser relies on thousands of hacked home routers to launch DDoS attacks. That’s not dissimilar to Mirai, which also uses poorly secured devices that aren’t laptops, desktops or servers. As we noted at the time of the attack on Krebs, Mirai originated not from malicious bot or zombie software on regular computers, as might have been the case a few years ago, but from so-called Internet of Things (IoT) devices such as routers, web cameras and perhaps even printers. You might not think of such humble devices as having enough brawn to do the damage that DDoSes have wrought, but string them all together, and they can be used to cause a world of hurt. Mirai wasn’t well-coded. But it didn’t have to be scrupulously developed in order to be destructive. To make it all that much worse, in the aftermath of the assault on Krebs, the source code of the malware used in the attack was open-sourced. But back to Mudd: he pleaded guilty to two offenses under the Computer Misuse Act and another of money laundering under the Proceeds of Crime Act. He’s due to be sentenced in December. We don’t yet know how much prison time Mudd may be facing, but Silicon Angle reports that the judge who accepted his guilty plea noted that “a spell in a youth offenders institution will be considered”. Source: Sophos
-
- cyber crooks
- ddos
-
(and 1 more)
Tagged with:
-
-
On October 21, Google informed Microsoft's security team of a zero-day vulnerability. Google says that the vulnerability in the Windows kernel is being actively exploited in the wild by attackers. Yesterday, a little over a week after telling Microsoft and before a patch has been released, Google has disclosed details of the vulnerability (known as CVE-2016-7855): The Windows vulnerability is a local privilege escalation in the Windows kernel that can be used as a security sandbox escape. It can be triggered via the win32k.sys system call NtSetWindowLongPtr() for the index GWLP_ID on a window handle with GWL_STYLE set to WS_CHILD. Chrome's sandbox blocks win32k.sys system calls using the Win32k lockdown mitigation on Windows 10, which prevents exploitation of this sandbox escape vulnerability. If the issue is, as it sounds, deep down within the internals of Windows then it's not something that necessarily can be fixed in a few minutes - and Microsoft will want to do thorough testing of any patch before they push out a fix to its millions of users. And yet Google has once again got ants in its pants, pressuring one of its arch-rivals by sharing details publicly of the flaw. It's not as though Microsoft hasn't stumbled before by releasing security updates before they have been properly tested... And, if there were previously any malicious attackers who didn't know where to look for an unpatched zero-day vulnerability in Windows, they have now got a good idea of where they should be focusing their attention - thanks to Google. Google's security researchers would argue that they're doing the internet community a service by going public and telling Windows users to be sure to apply a patch whenever Microsoft comes up with one. I, however, tend to side more with Microsoft - particularly with the comment that they offered VentureBeat: "We believe in coordinated vulnerability disclosure, and today’s disclosure by Google puts customers at potential risk." No, it's bad that Windows has a zero-day vulnerability that is being exploited. Yes, Microsoft should have found the flaw itself rather than having to depend on a third-party to tell them about it. But I feel confident that Microsoft recognises the importance of fixing the security hole, and is working hard at doing so. Google's security team are being unrealistic about the complexity of fixing software vulnerabilities in such important software, and should have co-ordinated more closely with Microsoft to responsibly disclose the issue when a security patch was made available. But worse than that, Google's petulant insistence that software companies release security patches to unrealistic deadlines imposed by Google puts more users at risk. Update: Microsoft says you'll have to wait another week for critical Windows zero-day patch. Source: Graham Cluley
-
-
We've seen a lot of cunning hackers exploit weak or dumb security measures to compromise users' information. One unidentified hacker did just that in June, for instance, by using a fake passport against an unthinking Facebook customer support representative. But just because you're a hacker doesn't mean you're smart. Don't believe me? Ask Dwayne C. Hans. Last week, law enforcement arrested Hans, 27, of Richland, Washington and charged him suspicion of computer fraud, wire fraud, and money laundering. Why? For being one of the stupidest hackers in history. Hans's first offense came sometime between 28 April and 17 June 2016 when he gained unauthorized access to the United States General Service Administration's Systems for Awards Management (SAM) website. SAM is a website through which vendors that hold contracts with the U.S. government can input their bank account credentials in order to get paid. The defendant went in and altered a financial institution's entry on SAM so that the Pension Benefit Guarantee Corporation (PBGC) was tricked into transferring more than $1.5 million to a bank account under his control. Fortunately, officials were able to spot and reverse the fraudulent transfers before Hans had a chance to withdraw the money. That's because the hacker left a trail. As reported in court documents: "According to Internet Protocol ('IP') address information associated with the defendant's intrusion into SAM.gov, the unauthorized access was gained through IP addresses registered to 'Dwayne C. Hans' at an address in Richland, Washington (the 'Richland address'), at which address the defendant has been observed by the FBI on multiple occasions in August 2016 and and September 2016. In addition, the user information that was provided as part of the process to access the SAM.gov website without authorization was associated on SAM.gov with the email address 'dwayne.hansjr@outlook.com." That's right. Hans used his own IP address, his own name, his own home address, and his own personally identifiable email account to steal money from a site operated by the federal government. But that's not all! Sometime between 15 March and 11 April 2016, Hans set up five bank accounts with the financial institution from which he later stole. He then linked those accounts to an account at JP Morgan so that he could try to steal $134,000 from two corporate accounts at the bank. Those transfers were spotted by the financial institution before they could proceed. Here's why: "The five accounts that the defendant Dwayne C. Hans created were associated with the name 'Dwayne C. Hans' and with information linked to the defendant, including the Richland Address and the defendant's social security number. For example, the new account to which the defendant attempted to link the JP Morgan Account was registered using the name 'Dwayne C. Hans Jr.,' the defendant's birthdate, and the Richland Address. In addition, the defendant listed a home phone number ending in -3434; the same phone number is associated with the bank account that the defendant entered on SAM.gov, as discussed above." "These five accounts created by the defendant Dwayne C. Hans were also accessed using IP addresses registered to 'Dwayne Hans' at the Richland Address and with other IP address associated with Richland, WA." With all that stupid, it didn't take law enforcement long to put all the pieces together and arrest Hans. If only more criminals were that dumb... it certainly would make the job of the FBI's cyber division that much easier. Source: Graham Cluley
-
- computer fraud
- hackers
-
(and 1 more)
Tagged with: