-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
-
A hacker group has stolen a variety of corporate and personal information from the United States glue and adhesive company Gorilla Glue. The group, which calls itself The Dark Overlord, claims to have made off with 500 GB of company data including R&D materials and access to personal email accounts of those who work at Gorilla Glue. To prove it, the hackers sent 200 GB worth of files to Motherboard. The cache appears to contain financial documents, invoices, and presentations. A screenshot of an internal presentation the hackers obtained with content redacted. (Source: Motherboard) Also included in the haul were personal photos apparently of Gorilla Glue's executives and their family members. Motherboard has attempted to verify those documents with Gorilla Glue and other companies implicated in the documents, but it has yet to hear a response. Meanwhile, the photos didn't yield any hits when entered into a reverse image search engine. Unsurprisingly, The Dark Overlord is quite pleased with its handiwork. One of its members intimated as much to Motherboard in a recent online chat: "We have everything they ever created." Nothing like a smug criminal to get your blood boiling. Beyond aggravating, that cheekiness isn't a good sign. It signals that the hacker group feels in control, that everything is going their way. But where exactly does this hack go from here? For one possible answer, ask WestPark Capital, a Los Angeles-based investment bank which a suffered a security incident at the hands of The Dark Overlord in September. The extortionists ultimately decided to publish sensitive documents after the bank refused to agree to its "handsome business proposal." Uh-oh. Given what The Dark Overlord said about its most recent hack, that doesn't bode well for Gorilla Glue. As quoted by Motherboard: "We approached them with a handsome business proposition. However, there has been a moderate dispute." If the hacker group plans to extort Gorilla Glue, and if the information in the Dark Overlord's possession is legitimate, there's very little the company can do. They could do nothing and accept the fact that their reputation will probably suffer some damage in the aftermath of several data dumps. Or they could pay the ransom and signal their willingness to pay up for the return of their data, a tendency which other criminals could exploit in the future. It's a lose-lose situation, which is why companies need to use the incidents at Gorilla Glue and WestPark Capital as a motivation to boost their own defenses. In particular, organizations should implement layered defenses that place sensitive data out of the reach of criminals like The Dark Overlord. They should also review their security policies when it comes to patching for vulnerabilities, and they should think about training their employees to watch out for phishing scams and other attacks. Source: Graham Cluley
- 2 replies
-
- dark overlord
- gorilla glue
-
(and 1 more)
Tagged with:
-
-
-
You might be wrong to assume that when you buy a shiny new Android phone that there's nothing malicious on it. Researchers at Kryptowire claim that several Android smartphones sold through major retailers like BestBuy and Amazon have firmware pre-installed on them which transmits sensitive information to third-party servers in China, without the owner's knowledge or consent. Affected handsets include the BLU R1 HD, which ships with firmware developers by Shanghai Adups Technology Co. Ltd. Selling for about $60 on Amazon, the unlocked BLU R1 HD Android smartphone is unsurprisingly a big seller. However, the researchers discovered that personal information was being collected by Adups software every 24 hours from the phones and transmitted in encrypted form to servers in Shanghai. Furthermore, some phones were transmitting call logs and the content of text messages every 72 hours. The data collection could not be disabled by the end user. BLU has responded to Kryptowire's advisory by publishing its own security notice to customers: BLU Products has identified and has quickly removed a recent security issue caused by a 3rd party application which had been collecting unauthorized personal data in the form of text messages, call logs, and contacts from customers using a limited number of BLU mobile devices. Our customer’s privacy and security are of the upmost importance and priority. The affected application has since been self-updated and the functionality verified to be no longer collecting or sending this information. BLU's advisory says that its R1 HD, Energy X Plus 2, Studio Touch, Advance 4.0 L2, Neo XL, and Energy Diamond models are impacted and goes on to describe how handset owners can confirm if their device is affected or not. Even if BLU has resolved the issue, it doesn't seem to have apologized to affected users or done anything to explain just why its phones were collecting sensitive personal information about its customers and their communications. Source: Graham Cluley
- 1 reply
-
- android phone
- firmware
-
(and 1 more)
Tagged with:
-
Facebook founder Mark Zuckerberg has had extraordinary success at building a social network that has attracted over a billion users. But that’s not to say that he’s had such luck in every other area of IT. Take securing his online accounts from attack, for instance. To misquote Oscar Wilde’s “The Importance of being Earnest”: “To lose control of one social media account, Mr Zuckerberg, may be regarded as misfortune; to lose multiple looks like carelessness.” The hacking group OurMine has targeted Zuckerberg for the second time in recent months, managing to break into his Pinterest account and posting a message suggesting they could help him with his online security: “Hacked By OurMine (Read the description) “Hey, it’s OurMine, don’t worry we are just testing your security, please contact us to tell you more about that and help you to keep your accounts safe” Back in June when Mark Zuckerberg’s Twitter, LinkedIn, Instagram and Pinterest accounts were hacked, the blame was put on him for reusing the same password – the monumentally insecure “dadada” – that was uncovered by the hackers behind the mega-breach at LinkedIn. OurMine claims that its latest breach of Zuckerberg’s Pinterest account did not rely upon shared credentials being found in leaked databases. Instead it told ZDNet that it relied upon an “exploit on Pinterest”. Whether such an exploit, if it exists, could be used against millions of other Pinterest users is unclear. OurMine isn’t sharing any more information, which leaves its claim open to question. The hacking group also claimed to have determined the password for Zuckerberg’s Twitter account, but it was foiled from hijacking that as it seems Facebook’s founder has enabled login verifications since he last suffered a breach. In other words, things could have been worse. My advice for users is to always choose unique, hard-to-crack, impossible-to-guess passwords for their online accounts, as well as to further harden their defences by enabling two-step verification/two-factor authentication when made available by services. Multi-factor authentication is not a cast-iron guarantee that your online accounts will never be hacked, but it certainly can make a hacking attack much more difficult for an attacker to accomplish. When faced with such a challenge, many criminals may decide to find an easier head to scalp. Source: Tripwire
-
We’ve done plenty of reporting on tech support scams, be they online or by phone, but how about the sort where you walk into a huge, supposedly legit gizmo box store and they try to sell you the same load? Seattle station KIRO-TV, tipped off by a whistleblower and bolstered by confirming employees, is accusing Office Depot staffers of doing just that: diagnosing brand-new, just out of the box computers with malware infections that some stores suggested would cost up to $200 to clean up. According to Shane Barnett, an ex-Office Depot employee turned whistleblower, staffers need to sell fixes to keep their jobs. It’s not an option to run the program. You have to run it on all machines that come in the building. Sales targets for support services – including the so-called PC Health Check that found “malware” on four out of six computers reporters brought to Office Depot stores in Washington and Oregon – are posted in the employees’ break room. Staffers are also handed orange cards with the goals to stick in their pockets at the beginning of shifts, Barnett said. That all sounds like a standard-issue retail environment. But Barnett and other Office Depot employees told the station that the stores are grooming aggressive associates who push hard to sell unnecessary protection plans. KIRO 7 took the same new computers that had been inspected by Office Depot to an independent security company, IOActive, which found the “infected” computers to be clean as a whistle. IOActive’s Will Longman: We found no symptoms of malware when we operated them. Nor did we find any actual malware. Longman said it looks like PC Health Check appears designed to sell products to unsuspecting customers, “so there is that potential for a consumer to be misled and want to or need to fix things that aren’t actually broken.” Office Depot on Tuesday put out a statement saying that it doesn’t condone selling needless services and that it’s launched an investigation into the allegations. Office Depot in no way condones any of the conduct that is alleged in this report. We intend to fully review the assertions and take appropriate action. But Barnett and other employees who confirm his account say that they told management about the problems with PC Health Check – two years ago – and they “did nothing to stop it.” In a followup report, KIRO-TV reporter Jesse Jones said that the station’s reporters had told the stores that the computers were running too slow. So employees ran the free PC Health Scan, which requires Office Depot techs to ask customers four questions: about pop-up problems, slow speeds, virus warnings and random shut downs. If a tech checks a box, the software automatically signals a malware problem: a “predetermined result followed by a sales pitch,” Jones reports. How to fend off brick-and-mortar tech support scams? We tell people to just hang up when they get an unsolicited tech support call. Sometimes you’re the one who makes the call – say, when a “warning” arrives in an SMS or a pop-up, urging you to call a “support line,” typically a free number that seems harmless enough to dial. Whatever the route, you end up talking to an earnest-sounding person who typically poses as a Microsoft or Windows “support tech” or some other official-sounding title that gives him or her purported credentials to back up whatever they’re feeding you. But it always winds up the same meal: a plate full of bogus. But how do you protect yourself against a rip-off packaged in a reputed box store? One of the tips we use for other tech support rip-offs applies here, as well: If you need help with your computer, ask someone you know and trust. That means “someone you’ve actually met in person,” as opposed to just online, where nobody can tell who’s a dog or who’s a fraud. And as Consumerist advised in a report on Best Buy’s $40 “optimization” services tacked on to PC sales (a “big stupid annoying waste of money,” in other words), you can optimize your own damn PC. Ditto for installing your own damn security software! Source: Sophos
-
- malware infections
- office depot
-
(and 1 more)
Tagged with:
-
-
-
That's an excellent point, Pete. Most people just don't pay proper attention to what they are doing.
- 2 replies
-
- android trojan
- downloaded
-
(and 1 more)
Tagged with:
-

Windows 7 - lots of issues
allheart55 Cindy E replied to Tony D's topic in Tech Help and Discussions
I've seen it before. -

Windows 7 - lots of issues
allheart55 Cindy E replied to Tony D's topic in Tech Help and Discussions
Windows updates especially for Win 7 are a mess. I always go with the MS update roll up for convenience and to keep my sanity. You can find it here at the MS Update Catalog. Windows 7 SP1 and Server 2008 R2 SP1 convenience roll-up now available at a download location near you! (KB3125574) -
-

Windows 7 - lots of issues
allheart55 Cindy E replied to Tony D's topic in Tech Help and Discussions
Did he have any type of registry cleaner or computer optimizer software on board Tony? -

Windows 7 - lots of issues
allheart55 Cindy E replied to Tony D's topic in Tech Help and Discussions
Sorry that we couldn't be of more help. -
If you’ve never heard any Pentatonix performance, this is the one to start with. If you’re a fan, this will blow you away. They just released their Christmas album and their version of holiday classic Hallelujah is so good it draws tears to my eyes. There are no instruments, just the sheer power of human voices merged together into something that puts you closer to God when you listen to it. I say human voices, but they sing like a choir of angels. If something more earthly is what you prefer, check out their version of Dolly Parton’s Jolene.
-

Windows 7 - lots of issues
allheart55 Cindy E replied to Tony D's topic in Tech Help and Discussions
Have you tried running sfc /scannow a few times, Tony? -
-
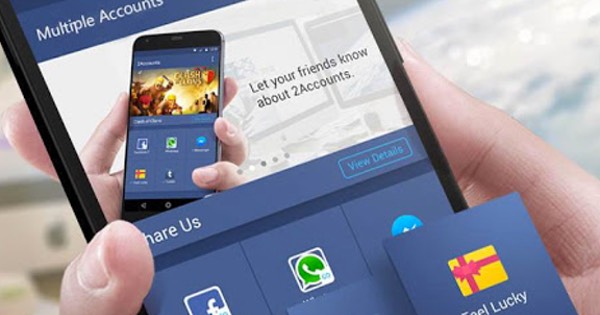
More than a million users have downloaded a particularly sneaky Android trojan that's available on the official Google Play Store. The Russian security firm Doctor Web found that the malware, known as Android.MulDrop.924, likes to disguise itself as games and other apps on Google Play Store and other app marketplaces. One of its preferred masks is an app called "Multiple Accounts: 2 Accounts." It allows users to set up multiple accounts for games, email, messaging, and other software on their devices. The app hasn't received too many bad reviews, either. No doubt such a good reputation played a part in convincing at least one million users to download it. The app, which is still available on Google Play, might appear to be benign in functionality. But it hides a dark secret. Doctor Web explains more: "The Trojan has a unique modular architecture. Part of its functionality is located in two auxiliary modules, which are encrypted and hidden inside a PNG image in the resource catalog of Android.MulDrop.924. Once launched, the Trojan extracts and copies these modules to its local directory in the section /data and then loads them into the memory." Let's focus on the module "main.jar" in particular. It loads up several plug-ins designed to generate income. One of those is the trojan Android.DownLoader.451.origin, which is like Android.Slicer.1.origin and Android.Spy.277.origin in that it covertly downloads applications and displays unwanted advertisements on the infected device. But that's not all main.jar can carry. Other versions of Android.MulDrop.924 came with Triada, a trojan which leverages exploits to achieve root privileges on the device. This particular trojan goes to show just how difficult it is sometimes to avoid a malware infection. With that in mind, users should maintain an up-to-date anti-virus solution on their phones and download apps only from trusted developers on Google Play Store. It's not a foolproof anti-malware strategy, but it's your best bet when trojans as clever as Android.MulDrop.924 are out there. Source: Graham Cluley
- 2 replies
-
- android trojan
- downloaded
-
(and 1 more)
Tagged with:
-
-
Researchers in a team from Shanghai, Boston and Tampa recently published an temptingly titled paper about password stealing. Dubbed When CSI Meets Public Wi-Fi: Inferring Your Mobile Phone Password via Wi-Fi Signals, the paper makes you think of Crime Scene Investigation, but that’s just a handy collision of acronyms. This CSI is short for “channel state information,” a collection of readings that describes what’s happening at the lowest level of the data link between a Wi-Fi sender, such as your laptop, and a receiver, such as as an access point. If you remember the cassette tapes on which early home computer programs were stored, you’ll know that there wasn’t much CSI going on: there were typically two sound frequencies, 1200Hz and 2400Hz, and the pitch of the recording warbled between them every few milliseconds to denote zeros and ones. In modern Wi-Fi standards, however, connections are much more complex, with each radio channel divided into many sub-channels that transmit in parallel, and multiple antennas that measure different signal paths, thus turning echoes and reflections into an advantage, not a liability. Chopping your radio spectrum into lots of sub-channels is a bit like sending 20 bicycle couriers across town at the same time, each carrying a modest amount of correspondence, instead of stuffing the whole lot in a van and delivering it in one go. When you have numerous indepedant delivery channnels, your throughput copes much better with localised interference, because you haven’t got all your communication eggs in one basket. Now imagine that you have a stream of real-time information about how what route each courier is taking, and how much progress each of them has made so far. You can build up a picture of what the traffic looks like in various parts of the city, and you can guess at what’s causing the various holdups. After all, protesters converging on parliament cause a different pattern of disruption than a pile-up on the airport access road. That’s the kind of approach that the researchers tried in this paper. They used specially modified firmware downloaded into a Wi-Fi network card to create an access point that could keep track of minute variations in the underlying communication signal and correlate those changes with your typing. They dubbed their attack WindTalker. Their idea was that if they could get their rogue access point close enough to your phone, then the interference caused even by your fingers moving in front of the on-screen keyboard might produce detectable differences in the CSI data that they measured. And if they could guess when you were about to start entering a PIN using just 10 widely spaced positions on the screen, rather than when you were busy with the more complicated business of navigating through a web form or typing words from the entire keyboard… …then they could focus their attention on the moments when they had the best chance of success. Limitations of the attack The paper is mathematically rather technical: it helps if you are already familiar with techniques such as discrete wavelet transforms, dynamic time warping and machine learning. But the bottom line, in brief, is that the researchers do, indeed, claim modest success in guessing PINs tapped in on nearby mobile phones. Fortunately, the current version of the attack seems to have many limitations: The attack only works with one model of Wi-Fi network card, which limits the range of Wi-Fi devices that can be modified for malicious purposes. The attack relies on modified firmware code that is prone to crashing, which limits its usefulness. The attack only works on unencrypted networks, because the authors haven’t yet managed to squeeze both the CSI-grabbing code and Wi-Fi decryption code into the limited firmware space available. The tests were done in what looks like a rather sterile radio environment, without the levels of interference you might expect in real life. The attack relies on a consistent stream of network replies from your phone (800 ping replies per second) to form the basis of the CSI measurements, at a volume and consistency that we found hard to maintain when we tried in an office environment. The attack doesn’t yet seem to scale from PIN entry to full-on passwords, so it isn’t applicable to all login pages you may use. The attack is thwarted by two-factor authentication (2FA), because it relies on guessing a password that can be re-used indefinitely. What to do? You can probably guess our advice in this case. Use 2FA whenever you can, and you will be taking a big step towards a digital lifetstyle in which you greatly reduce the risk of sniffed and stolen passwords. If the crooks can’t figure out what tomorrow’s login code is going to be, there’s no longer much point in stealing today’s. Source: Sophos
-
- access point
- password stealing
-
(and 1 more)
Tagged with:
-
An unusual bug on Facebook briefly labelled many people as dead. The error on Friday caused the social network to show a memorial banner on user profiles for people who were still alive. Users posted status updates to reassure friends and family they were not dead, despite Facebook's message. "Victims" of the Facebook death bug included founder Mark Zuckerberg himself. A Facebook spokesperson apologies for the monumental cock-up: "This was a terrible error that we have now fixed. We are very sorry that this happened." What was Facebook motto, again? Oh yeah, "move fast and break things". Hope they didn't break too much when they told folks their loved ones had died. Source: Graham Cluley
-