-
Posts
7,278 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Articles
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
The Federal Communications Commission has told America’s wireless carriers that it’s fine if they want to drastically cut back the speed of data (or “throttle”) that their heaviest users have access to: they need to spell out to customers exactly what behaviors lead to throttling. T-Mobile has spelled this out quite clearly…in an internal memo for employees, not necessarily a clear guide for customers. Of course not. However, the blog T-Mo News has the information that aspiring data hogs need to stay within the rules. According to the memo, beginning this Sunday, August 17, T-Mobile will find, warn, and throttle customers who are using their data plans to do things that are against T-Mobile’s Terms and Conditions. You know, that long page of things that you probably didn’t read before you agreed to them. What’s against the T-Mo T&Cs? Live webcams, BitTorrent, and other peer-to-peer file-sharing. From the memo: T-mobile has identified customers who are heavy data users and are engaged in peer-to-peer file sharing, and tethering outside of T-Mobile’s Terms and Conditions (T&C). This results in a negative data network experience for T-Mobile customers. Beginning August 17, T-Mobile will begin to address customers who are conducting activities outside of T-Mobile’s T&Cs. If you’re caught engaging in any of these forbidden activities on the network, there’s a special team at T-Mobile that will call you up and let you know that you’ve been bad. No, really: T-Mobile will contact customers to explain terms and conditions to them, and then advise them that data speed could be reduced until the next billing cycle IF they continue to misuse the data service. The new rules only apply to customers on Unlimited High-Speed Data (LTE) plans. However, after you get the call telling you that you’ve “misused” your data plan, if you’re caught “misusing” it again, that’s when the Network Abuse ninja team will throttle you. Does this count as disclosing to consumers what it takes to get throttled? The warning call is certainly helpful, and that’s better than simply throttling users without telling them what they did wrong. In theory, this is all clearly spelled out in the terms and conditions, assuming that you read them when you first signed up. Did you? T-Mobile to throttle customers who use unlimited LTE data for torrents/p2p
-
"I'm sorry. Our intentions were good." Ethan Zuckerman was a designer and programmer for the early web-hosting service Tripod.com when a car company freaked out. The unspecified manufacturer had bought a banner ad on a page that "celebrated anal sex," and was not too pleased at the association of its brand with sexual escapades. Tripod had the solution: what if an advert could launch in its own window? Zuckerman wrote the code for the world's first pop-up ad, and for many years it was impossible to browse without being inundated by pop-ups. You'll still find some pop-ups in the seedier parts of the internet, of course, but they're few and far between. Thanks to work from Netscape and Opera, who were the first to add pop-up blockers into their products, the majority of web browsers now prevent sites from launching hundreds of ad windows. Regardless of public opinion, the pop-up ad was instrumental in defining advertising as the primary business model for websites, but Zuckerman now believes there's a better way. In a long essay for The Atlantic, he explains how online advertising became the behemoth that it is, and what we can do about it.
-
- advert
- advertising
-
(and 3 more)
Tagged with:
-
We’ve oohed and ahhed over interactive maps that detail the world’s mysterious network of undersea Internet cables, but a new report over at Builtvisible is taking things to an entirely new depth. The exhaustive account looks at the entire history of the process, ranging from experiments in the 1840s to a rash of undersea surveillance taps in the 1970s. Today, there are 263 active cables that carry upwards of 95 percent of global Internet traffic, with 22 new drops planned for the coming years. Hungry for a few more nuggets from the report? Underwater cables carried 51 billion gigabytes of data per month in 2013, and that figure is expected to swell to 132 billion gigabytes in 2018. While 10 billion “things” accessed the Internet in 2010, Cisco expects that figure to increase fivefold by 2020. Currently, less than 40 percent of the worldwide population has any access to the Internet at all. In Africa, some 70 percent of its population has a WiFi-connected device, but only 10 percent have access to the Internet The planet’s least reliable undersea Internet cable? The drop between Rockport, Maine and two tiny islands just a few miles offshore. This single stretch had a staggering 45 faults between 1990 and 2005, largely attributed to the rocky sea bed below.
-
I've only run Linux from a live CD enough to muddle my way around it. Other than that I have used it many times to pull data from an unbootable machine.
-
SAN FRANCISCO - An app that's been reported in Asia says it will change the color of Facebook profiles from the default blue. The app, which doesn't appear to have gotten much traction among users, is a scam. It allows hackers to gain access to the user's profile and spam their friends. Multiple Facebook color change scams have been reported over the years. This one has been dubbed the "Facebook Color Changer." It takes users to a malicious phishing site that asks them to watch a tutorial video, says Hugh Thompson, a security expert with the computer security company Blue Coat in Sunnyvale, Calif. When users click the video link, they allow the site to implant viruses and malicious code (malware) on their computers. If the user doesn't view the video, the site instead attempts to download a pornography video player if they're on a PC, according to Cheetah Mobile Security, a Chinese security company that reported the scam in a blog post last week. Users on Android devices get a warning that their device is infected with a virus and advising them to download an app, which is of course also malware, to clean it, Cheetah said. Facebook says it hasn't gotten many reports on this one and that it doesn't appear to have spread very widely. "We work quickly to block these scams by disabling apps and using a combination of automated systems to stop links from spreading on our platform. We warn against false color change apps and offer free software from anti-virus partners to help remove malware from people's computers," a spokesman for Facebook said via email. Facebook has information about how to avoid scams such as this one on its security page. It also offers information about free antivirus programs. Similar scams, perpetrated by other hackers, have been making the rounds for year. Security experts advise users to immediately change their password and then delete the app by going to Facebook settings if they've fallen victim to this scam.
-
Microsoft Virtual Academy offers hundreds of free courses for anyone interested in improving their computer or IT skills. Many of the courses, as you might expect, are geared towards Microsoft products: developing Windows apps, migrating from Windows Server, Office 365 training, and so on. There are also some that are more universal, like learning JavaScript and C#. Anyone is eligible for the courses, which you can pause and resume at any time, and once you sign in with your Microsoft Live ID, the site will keep track of your courses for you. Sessions include videos, PowerPoint presentations, and a short quiz at the end. Get started with your free training at the link below. Microsoft Virtual Academy via Techwork
-
- live id
- microsoft virtual academy
-
(and 2 more)
Tagged with:
-
Not to worry, Kick. Any informative discussion is always a good discussion. I've been following this thread with interest. I have much less experience with Linux than you or Rich do and I love learning. That's what it's all about. :)
-
Microsoft is rolling out a new feature to its Bing search engine today: conversations. It’s not quite the Cortana digital assistant just yet, but if you search for queries like "who is the president of the United States?" you can follow up that search result with "how old is he?" to quickly get Barack Obama’s age. Bing will maintain the context through search queries to provide a conversation-like feature. Cortana has similar follow-on search features, as does Google Now, but these are largely contained to mobile platforms. Bing’s update for its desktop search version is part of Microsoft’s continued efforts to leverage the company’s search work as a platform across all of its services and apps. The conversation feature might be a good addition, but it’s not visible unless you know it’s there. Microsoft is planning "additional improvements" in the days ahead, but it looks like the company is betting on users searching in similar ways on the desktop with the same queries used on mobile devices.
-

Antec Micro Case $19.99 with free freight
allheart55 Cindy E replied to Rich-M's topic in Tech Help and Discussions
I like the looks of it but it's not something I would ever use for myself. I also like the Antec cases for customer builds. I'm sure you remember, my first two builds (Mine and my daughters) were both with Antec cases. Since then, I've gone with Thermaltake cases for my own use. -

Antec Micro Case $19.99 with free freight
allheart55 Cindy E replied to Rich-M's topic in Tech Help and Discussions
That's not a bad looking case for a customer build. It's pretty small though, isn't it? -
Windows 9 could be a free upgrade for users of Microsoft’s older operating systems, like Windows XP, Windows Vista, and Windows 7, according to ZDNet. Users of these dated but still popular (aside from Vista) operating systems could be offered “some kind of deal” to poke and prod them toward Microsoft’s next desktop OS, a report suggests. However, it’s worth noting that Windows 8/8.1 users were not mentioned as possible recipients of this upgrade offer. They have been mentioned as possible free update recipients in the past, however. Rumored features in Windows 9 include a new Start menu, and Metro apps that can run in windowed mode in the classic desktop UI. Though Microsoft hasn’t announced Windows 9 yet, rumors indicate that Redmond’s next big desktop OS could land sometime in Spring 2015 – with the release of a free, public beta as early as this fall. Microsoft is no doubt aware that Windows 8 and 8.1 usage numbers have been very weak. For the month of July, Windows 8.1′s desktop share stood at 6.56 percent. That’s a minor drop from 6.61 percent in June, but a drop nonetheless. Meanwhile, Windows 8′s share fell from 5.93 percent in June to 5.92 percent last month, a teeny tiny decrease of 0.01 percent. Regardless of the size, it’s a trend Microsoft must be unhappy with. Combined, Windows 8 and 8.1 occupy just 12.48 percent of the desktop OS pie as of July. That’s not much, considering that Windows XP occupies roughly double that even though it’s well over 10 years old. Then there’s Windows 7, whose share spiked in July to 51.22 percent. That’s up from 50.55 percent in June, an increase of 0.67 percent. Microsoft will need to do something radical with Windows 9 to ensure that it’s adoption numbers aren’t a repeat of what the tech giant has endured with Windows 8 and 8.1. Read more: http://www.digitaltrends.com/computing/windows-9-could-be-a-free-upgrade-for-windows-xp-vista-and-windows-7-users/#ixzz3AHL6Z3ca
-
A new report reinforces the notion that Cortana, Windows Phones’ voice assistant, will make its debut on the PC with Windows 9. The new whispers, which come courtesy of Neowin, indicates that Cortana has been promoted past the “Can this work in Windows 9″ stage of development. This increases the likelihood that Cortana will appear in Windows 9 whenever it’s released. What’s more, it appears that Cortana in Windows 9 will take the form of an app, instead of being baked into Windows itself. Theoretically, if Cortana is an app in Windows 9, it could be uninstalled, and therefore avoided altogether. If that’s the case, we’re glad that Microsoft is giving users the option of using Cortana. That’s part of the reason why Windows 8 has flopped to this point; radical changes like the Charms bar, and the Metro UI, were forced on users, instead of giving them the choice to turn those on and off. Keep in mind though, Cortana is not yet a lock to appear in Windows 9, but it’s indeed looking more likely. If it does make it, users will reportedly be able to put Cortana to work either by typing in a question, or by voicing queries orally, just like it works in Windows Phone 8.1. At this point, Windows 9 rumors indicate that it will be released sometime in Spring 2015, will include a revamped version of the Start menu that was stripped out in Windows 8, will allow for Metro apps to run in Windowed mode, and will eliminate the Charms menu that debuted in Windows 8. However, Windows 9 has yet to be formally announced by Microsoft. Read more: http://www.digitaltrends.com/computing/cortana-voice-assistant-app-coming-to-windows-9-threshold/#ixzz3AHK3pCbR
-

August 2014 Security Updates
allheart55 Cindy E replied to allheart55 Cindy E's topic in Tech Help and Discussions
That's what I heard too...... -
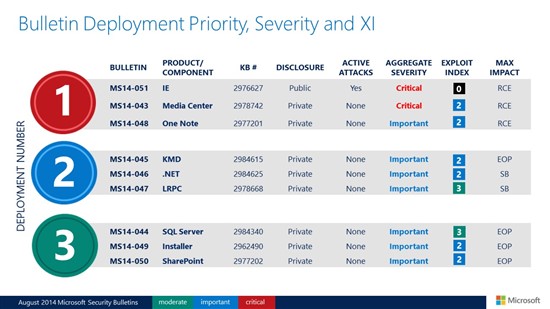
Today, as part of Update Tuesday, we released nine security updates – two rated Critical and seven rated Important – to address 37 Common Vulnerabilities & Exposures (CVEs) in SQL Server, OneNote, SharePoint, .NET, Windows and Internet Explorer (IE). We encourage you to apply all of these updates, but for those who need to prioritize their deployment planning, we recommend focusing on the Critical updates first. Here’s an overview slide and video of the security updates released today: Microsoft also revised Security Advisory 2755801: Update for Vulnerabilities in Adobe Flash Player in Internet Explorer. For more information about this month’s security updates, including the detailed view of the Exploit Index broken down by each CVE, visit the Microsoft Bulletin Summary Web page. If you are not familiar with how we calculate the Exploitability Index (XI), a full description is found here. You may notice a revision in the XI this month, which aims to better characterize the actual risk to a customer on the day the security update is released. Customers will see new wording for the rating, including a new rating of “0” for “Exploitation Detected.” More information about XI can be found here: http://technet.microsoft.com/en-us/security/cc998259.aspx. Last week, Microsoft announced some other news that relates to Update Tuesday: On August 5, Windows published a Windows blog post discussing its non-security update strategy moving forward, which is now on a monthly cadence as part of Update Tuesday. On August 6, IE announced in its IE Blog that it would begin blocking out-of-date ActiveX controls. This feature will be part of the August IE Cumulative Security Update, but no out-of-date ActiveX controls will be blocked for 30 days in order to give customers time to test and manage their environments. On August 7, .NET and IE announced that Microsoft will support only the most recent versions of .NET and IE for each supported operating system. Jonathan Ness and I will host the monthly bulletin webcast, scheduled for Wednesday, August 13, 2014, at 11 a.m. PDT. For all the latest information, you can also follow the MSRC team on Twitter at @MSFTSecResponse. Thanks, Dustin Childs Group Manager, Response Communications Microsoft Trustworthy Computing Continue reading...
-
Windows 9 is going to establish a balance between the mobile capability and desktop muscle Microsoft Corporation (NASDAQ:MSFT) is working to bring Windows 9, code-named Threshold, to users by spring 2015. Not surprisingly, the company has officially announced the end of support date for “business” Windows 8 users. According to ZDNet, business users will have to upgrade from Windows 8.1 to Windows 8.1 Update 1 by August 12, 2014 if they want to keep getting fixes and patches from Microsoft. Leaked features of Windows 9 garnering positive reaction August 12 is the software giant’s Patch Tuesday, when the company is expected to release a number of updates. Anyway, Microsoft would want to get over the Windows 8 debacle as soon as possible. Recent leaks clearly suggest that most of the features Windows 8 emphasized upon, such as Charms Bar, will be scaled back in Windows 9. Reports suggest that the beta version of Windows 9 will be released by the end of this year, and the final OS will hit the markets in the first half of 2015. Windows 8 focused dramatically on mobile computing. Meanwhile, Windows 9 is going to establish a balance between the mobile capability and desktop muscle, says Alex Wilhelm of TechCrunch. That fits well int the bigger picture of the computing market where PC sales have started to stabilize while tablet growth is slowing. That doesn’t mean Windows 9 is going to ignore tablets. The focus will be more even with the next-gen OS. Many leaked features of Windows 9 are already garnering positive reactions from the user community. Microsoft is expected to bring back the Start menu and ditch the much-maligned Charms Bar with Windows 9. The new OS will also reportedly have the virtual desktops feature, which is wildly popular among enterprise customers and power users. Ubuntu and Mac OS X already support virtual desktops. Existing Windows users could get Windows 9 for free But Microsoft won’t entirely go back to the desktop. The company won’t back down from the Windows Store. The Start Screen and Live Tiles are here to stay. Microsoft is trying to provide a Windows 7-like desktop experience, while combining that with its mobile-friendly interface and apps. That’s in line with previous reports that Windows 9 will have Metro apps running in a windowed fashion. Moreover, veteran tech reporter Mary Jo Foley recently said that Microsoft will give existing users a compelling incentive to upgrade to Windows 9, which includes the possibility of giving it away for free.
-
- 1
-

-
- metro
- patch tuesday
-
(and 2 more)
Tagged with:
-
Last week a particular patent submitted by Apple outlined its plan to bring the mobile virtual assistant Siri to the desktop. It looks like Microsoft might be planning the same thing by brining the Windows 8.1 voice assistant Cortana into Windows 9 proper. Cortana has actually been running within Threshold—Microsoft's codenamed OS build widely belived to be Windows 9—for some time, according to Neowin, but now the integration looks like it's moving forward. Neowin describes Cortana's "graduation" from a testing stage to a "let us push this forward and see if we can ship it" stage. It seems that Cortana would run as a separate but built-in app, and instead of taking up your whole screen like in Windows Phone (which on desktop would be unforgivably annoying) Cortana will pop up in a screen about one-fourth the size of your display. It'll also be displayed directly in the center, somewhat like Apple's improved Spotlight function in Yosemite. Of course lots can change between now and Threshold/Windows 9's eventual release. Microsoft could decide to drop Cortana from Windows 9, at least at first, or reversely more updates to the virtual assistant could allow for even deeper integration into the OS. Mary Jo Foley with ZDNet notes how Cortana integration in Windows (and eventually Xbox) would be in step with the company's new "One Windows" strategy, which includes plans for "universal" apps. It would also be a nice new addition to Windows whereas most leaks and rumors have just been about scaling back from Windows 8, including the return of the Start menu and the removal of the charm bar entirely. Windows 9 looks to be reorienting itself to a more recognizable desktop experience rather than being concerned with creating a mobile-friendly interface, and if Microsoft can pull in one of its best Windows Phone features with Cortana, Windows 9 could be the fresh new face we're waiting for. [Neowin via ZDNet]
-
I used an AS Rock board on Sam C's rebuild. It was the first UEFI board I ever worked with. (ASRock 870iCafe)
-
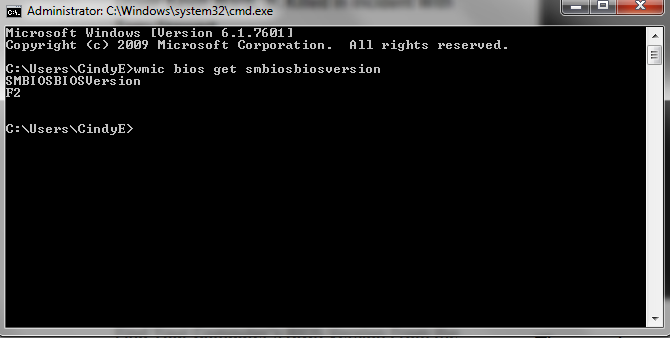
The next time you update your PC or try to troubleshoot compatibility problems, you'll may need to know your current BIOS. You could reboot the computer, but it's much easier to use the Windows command line utility. In the command prompt window type: wmic bios get smbiosbiosversion You'll get back the computer's BIOS version. It's that easy, no reboot necessary!
-
This post was originally published on Oct. 31, 2009, and updated on Aug. 7, 2014, by Brandon Widder. The following instructions now pertain to BitLocker as our previous software choice, TrueCrypt, is no longer available. Michael Brown and Emily Schiola contributed to this post. In this day and age, we all know backing up your files is important (and easy given the cloud). However, what happens if your desktop computer is unexpectedly stolen, or your leave your premium notebook at the local coffee shop? Although it’s a scenario you likely don’t want to think about, it’s also one you’ll likely encounter at some point during the course of your lifetime. A thoroughly executed back-up plan can alleviate data loss, but unfortunately, you also don’t want random strangers perusing the highly personal information you’ve stockpiled on your machine over the last three years. Fortunately, there is more than one way to protect your precious information from falling into the wrong hands — or at least keep unwanted hands from accessing said information without your approval. Protecting your files is essentially a two-step process. Not only does it require you to properly encrypt the data on your hard drive so you can control access via passwords, but it also involves completely wiping your hard drive to prevent others from retrieving your data once you decide it’s time to put your personal machine out to pasture. Here is our guide on how to erase a hard drive and encrypt your files using the freemium BitLocker, DiskCryptor, and Active@KillDisk. We can’t guarantee it will keep the most tech-savvy thief from obtaining your information, but it sure as hell will make things a bit more difficult. How to encrypt your files using BitLocker One of the best ways to secure your private data is to encrypt it on your hard drive. Encryption software uses an algorithm to scramble data in such a way that it can be read only by someone who possesses the special key that’s required to descramble it. Although the Internet is peppered with third-party applications for encrypting your hard drive, Microsoft’s BitLocker remains one of the most viable options given the software comes standard on Windows Vista, 7, and any Windows operating system later than 8.1. Once you set up a recovery password, the simple program will automatically password protect everything from documents to entire drives, shielding your data from prying eyes in the process. Assuming you have the Ultimate or Enterprise version of Windows 7, Vista, or 8 — along with a Trusted Platform Module (TPM) chip — simply launch BitLocker. To do so, access the Start menu, select the Control Panel option, followed by System and Security. Afterward, select BitLocker Drive Encryption and click the blue Turn On BitLocker link before launching into the on-screen wizard. Also, don’t fret if you’re not sure if you’re computer possess the necessary requirements for the software — BitLocker will let you know if it doesn’t. Follow the instructional wizard until you reach the final step. Stay away from names and birthdays when it comes time to choose a recovery password, and instead, opt for something that is a mix of letters, numbers, and symbols as outlined in our guide to choosing a strong password. Though likely a pain to remember, keep it more than 20 characters to ensure the utmost security. Once finished, the utility will automatically encrypt any file you save to the drive, thus restricting access to the file without the proper password. How to encrypt your files using DiskCryptor Although BitLocker may not be compatible with your machine or OS, there’s a good chance the open-source DiskCryptor is. Best of all, the freemium utility can encrypt entire drives — including the one on which Windows is installed — without requiring you to format your Windows drive akin to most other encryption software. Sure, you may have to enter a designated password to launch the software every time you boot your computer, but it’s a small price to pay for across-the-board protection. To enable DiskCryptor, first navigate to the software’s respective download page and click the blue installer link on the left-hand side corresponding to the latest software build. Afterward, launch the software accept the resulting software agreement, and follow the on-screen wizard before restarting your computer. Launch DiskCryptor again after restarting your computer, select the system drive you wish to encrypt — typically C: — and click the gray Encrypt button on the right-hand side of the application window. Though you can adjust the various encryption options afterward, we recommend simply clicking through the resulting prompts using DiskCryptor’s default options. Stay away from names and birthdays when it comes time to choose a recovery password, and instead, opt for something that is a mix of letters, numbers, and symbols as outlined in our guide to choosing a strong password. Though likely a pain to remember, keep it more than 20 characters to ensure the utmost security. The utility will then begin encrypting your requested drive, and once encrypted, the drive will listed as “mounted” beneath the Status column. You may not be able to use outside utilities (LiveCDs, USB drives, etc.) without first decrypting the system drive, but in the meantime, you’re files will remain under password protection. How to erase your hard drive using Active@KillDisk When your PC (or its hard drive) has reached the end of its useful life, you should remove all traces of your personal information before sending it into retirement; especially if your disposal plan entails donating it to someone whose computing needs are more modest than yours. Simply deleting the files isn’t good enough, even if you empty the PC’s recycle bin. All that really does is tell the OS that the storage space those files occupy is available for storing new data. What’s more, unidentified copies of sensitive files could be scattered in other places on your drive. Reformatting the drive isn’t a sure-fire solution, either. Anyone with the least bit of skill will still be able to recover files in either scenario with minimal effort. The solution is to use software that’s specifically designed for the purpose of wiping a hard drive clean. You’ll find a number of programs capable of doing this, but we like LSoft Technologies’ freemuim Active@KillDisk because it’s extremely thorough and is designed to meet government standards. The developer does sell more comprehensive versions of the software featuring more robust capabilities and customization, but said programs will cause you an upwards of $50 depending on your respective system. First, head over to the Active@KillDisk download page and choose which version of the software fits your computing needs. Next, insert a blank CD in your burner and initiate the installation process, which will burn an ISO image to the disc. If your computer isn’t already set up to boot from its optical drive, you’ll need to tweak your computer’s BIOS. Restart your machine and click the hot key — typically the Delete key — to access the BIOS settings. Tab over to the Boot menu and configure the BIOS so that the CD/DVD drive tops the list of boot devices. After you save this setting and exit the BIOS menu, your machine should boot from the CD/DVD drive and automatically launch Active@KillDisk. Keep in mind the free version of the software only supports only a One Pass Zeros method, which means the software will write zeroes or random characters across the entire hard drive, thus destroying any data in the process. Doing so will make it nearly impossible for a casual user to access any old data on the drive. Once open, press the Enter key to acknowledge the message and Active@ KillDisk will display all the drives attached to your computer. Afterward, check the box directly beneath the drive(s) you wish to erase and press the F10 key, or click the Kill button in the toolbar to start the process. Then, select your desired method from the resulting list — likely One Pass Zeros — and choose your desired parameters before clicking the Start button in the bottom-right corner of the window. Just to make sure you really intend to destroy the data on this drive, Active@ KillDisk will ask you to type the phrase “ERASE-ALL-DATA” into a box and hit the Enter key once more, or simply click the Yes button. The program will then do its thing, conveniently displaying a progress bar below the disk you’re erasing in the left panel. When it’s finished, it will display a report showing what it did and how long it took. Repeat this process for any additional hard drives or partitions on your computer. When you’re finished, press the Escape button to exit the program. You can now safely dispose of your PC with little worry that someone will be able to resurrect any of the information you had previously stored on it. Read more: http://www.digitaltrends.com/computing/how-to-erase-and-encrpyt-a-hard-drive/#ixzz39vanpREe
-
Gmail doesn't display a true message count by default, because Gmail uses the conversation view. Turn the conversation view off to see the real number of individual messages in your Gmail account. It's sometimes useful to know how many messages you have from a certain sender or on a particular date. Since Gmail uses the conversation view by default, you only see the number of conversations. When you turn conversation view off, you'll see the individual message count for your inbox, sent mail, labels, and in search results. You'll see something like, "1-50 of 2,139," in the upper right-hand corner of your message list. Find the Number of Gmail Messages