-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
-
If you’ve been delaying your upgrade to Windows 10, Microsoft has just outlined a pretty sweet deal. For a limited time (lasts until July 29, 2016), if you bring your current PC into a Microsoft Store, employees will upgrade it by close of business or they’ll give you a free Dell Inspiron 15. There are obviously a few caveats that come with the deal. They are… PC must be checked into the Answer Desk at a participating retail store before 12 noon local time. If your PC isn't compatible with Windows 10, they'll recycle it and give you $150 toward the purchase of a new PC If the store runs out of Dell Inspiron 15 PCs, Microsoft reserves the right to select the free device that will be provided to eligible customers. Limit of 1 offer per customer, per device/PC. To see if your local Microsoft store is participating, follow the link: https://www.microsoft.com/en-us/store/locations/windows-10-upgrade-challenge Source: winsupersite
- 1 reply
-
- delaying
- free dell inspiron
-
(and 2 more)
Tagged with:
-
Is there such a thing as good malware? The FBI would argue that there is, if they are the ones who created it. The origins of the case date back to February 2015, when the FBI seized control of a child sexual abuse website called Playpen. You might have expected the FBI to shut down the site immediately. But instead, rather sneakily, they chose to continue to make the site available from a government server, planting code that could grab identifying information about computers – such as IP addresses – used by the site’s users, as well as downloading malware to their computers. What makes that particularly interesting is that Playpen was on the dark web, and its users were attempting to remain anonymous by using Tor to cover their tracks. That’s all very well and good, but when the FBI refused to share details of how it had managed to exploit Tor with a “Network Investigative Technique” (NIT) to discover the identities of alleged pedophiles, a judge threw out the evidence. Now, as Julian Sanchez noted on Twitter, the FBI has claimed in a legal brief that its code simply isn’t malware. Source: Twitter As William Turton at Gizmodo reports, the FBI is bristling at the suggestion that its malware could in any way be considered.. umm… malware: Obviously, the FBI is not pleased with any suggestion that what the agency may have done is wrong or that its malware wasn’t above board. In fact, the FBI is saying, well, it couldn’t possibly be malware because FBI agents are the good guys! Hmmmmmmmmm. If you didn’t know, malware is just short for malicious software. Now, the FBI is trying to dispute what it really means. Source: hot for security
-
- child sexual abuse
- fbi
-
(and 2 more)
Tagged with:
-
Robots might be cheaper to employ than humans, but it seems they still need to work on their people skills. Last week, a robot security guard at the Stanford Shopping Center in Silicon Valley knocked down a toddler while on duty and then apparently just kept on driving. A report from local news channel ABC7 says the bot hit 16-month-old Harwin Cheng, knocking him to the floor. Cheng was not seriously hurt by the incident, but we're still going to chalk this up as a violation of Isaac Asimov's first law of robotics: "A robot may not injure a human being or, through inaction, allow a human being to come to harm." Here's ABC7's story: The robot in question was the Knightscope K5, a five-foot, 300-pound machine that began trials in the mall last year. The robot trundles about on wheels and uses an array of sensors and cameras to monitor its environment. Human security guards can direct it to certain locations to see what's going on, and the bot is supposed to report any unusual activity to a central guard station. The robot's creators describe it as possessing a "commanding physical presence" combined with "advanced technology." The k5 costs just $6.25 an hour to employ — less than minimum wage It's not clear exactly what happened with Harwin Cheng, and Knightscope has yet to issue any statement on the matter or respond to requests for comment from The Verge. And while it seems the incident with Cheng was minor, Knightscope obviously wouldn't want something like this to happen again. Even though the K5 only costs $6.25 an hour to employ (that's lower than minimum wage), no-one's going to hire a robot that runs into children. Source: the verge
-
-
Amid the crowds of roving Pokémon Go players out there following virtual monsters around with their phones, there are likely some who might be interested in downloading third-party or ancillary apps to help you in your quest. But like with any popular tech phenomenon, there could be dark forces lurking out there, shady apps that you should avoid. Fans of Pokémon Go may have already encountered one such bad player, when someone released a malicious, unofficial version of the app for Android on the internet, as security firm Proofpoint reported over the weekend. Because Nintendo and Niantic have only released the game in the U.S., Australia, and New Zealand so far, players in other parts of the world had been passing around APK files (Android application package) to share it that way instead. Folks would install these unofficial versions of the game by “sideloading” — when you tell your phone to trust a version of an app that’s not from an app store — and one of those files came with a whole bunch of malware. One big red flag to watch out for in situations like this is to compare a downloaded app’s list of permissions to the list of permissions required by the authorized version, advises Noah Swartz of the Electronic Frontier Foundation. “The way that you can tell if it’s malware is if it requests more permissions than the app says it does,” he explained to Consumerist. “So you can go check in the Play Store and see what permissions Pokémon Go app would normally request, and then you can see what the app on your phone requests.” In the case of the recent fake Pokémon Go app that was being circulated, for example, the permissions it was requesting should’ve made it somewhat easy to spot: while the real version of the app only wants location data and the ability to say things to your phone, the malware version wanted access to users’ contacts, a full data connection — basically, “it wanted all of these things that the normal one didn’t,” Swartz notes. If you really want to have a guarantee of security, Swartz recommends you only download official apps from the App Store or the Play Store, depending on your device, from verified sources like Niantic. Then there are the third-party apps that offer to guide you on your Pokequest, or help you in some way (though cheating with “unofficial or modified software” is against Niantic’s Trainer Guidelines). These apps won’t necessarily request the same list of permissions as the app for the game itself does, but taking a careful look at the permissions they DO ask for can also be a good way to suss out any bad actors: are they reasonable, considering what the app is supposed to do? For example, an app that promises to sort your assorted Pokémon probably won’t need access to your contacts, or access to your network. “If they’re requesting permissions that they seem like they shouldn’t be using, to do the thing that they’re claiming to do, then there’s probably something going on,” Swartz says. To illuminate this point, Swartz uses the example of flashlight apps that were popular back before smartphone operating systems built in the ability to turn on the light on the back of your phone. Back then, “they’d download these apps that would say, ‘I will turn on the light on your phone!’ but if you looked at all of them, they all had these crazy permissions they wanted,” Swartz explained. “They wanted your contacts, and your location, and full network access — for a flashlight app. Which means that they’re probably doing something malicious.” Basically, if something feels off or if it’s requesting access to your personal information, just avoid it and save yourself the trouble. “There’s no canonical example of what the permissions should be,” for any given app, he adds. “You have to use your best judgment.” Source: consumerist
-
- pokemon go
- shady apps
-
(and 2 more)
Tagged with:
-
There are lots of reasons — price hike, a content library that no longer appeals to you, infrequent use, poor internet connection — that you might cancel your Netflix service. One thing that’s not on that list is “Netflix employee doesn’t realize that two people could have the same name.” Consumerist reader Rob recently contacted us when he found himself caught up in an unusual — almost ridiculous — situation with Netflix simply because he shares the same name as another customer. The issues started earlier this month when he began receiving password reset emails from Netflix, then suddenly found that his account was no longer active. Initially, Rob assumed that someone with the same name was able to cancel his account by simply providing his name and email address, but no other verifying information. This, he tells Consumerist, seemed like a glaring security issue with the streaming service. “I called Netflix customer service and they informed me that earlier today, someone did in fact call and cancel my account,” he says. “Apparently another customer with the same first and last name as mine tried to cancel their account and cancelled mine instead.” Consumerist reached out to Netflix about the issue and found the entire ordeal was actually a big mix-up that resulted from a confluence of circumstances so unusual it’s unlikely to happen to too many other subscribers. #1. Have A Common Name: In Rob’s case, the entire ordeal began simply because he has the same name as another Netflix subscriber. So let’s call him Rob #1 and the other guy Rob #2. You can’t really blame either of the Robs — or Netflix — for this aspect of the story, but it’s the fountainhead from which this farce flows. As with many people who have common names, Rob’s email address is also similar to his same-name counterpart. In this case, Rob #2 was mistakenly using Rob #1’s email address to log in to his account to add a second device. This is why Rob received several password reset prompts. #2. Not Knowing Your Own Email Address: As occasionally happens with people who have common names, the two Robs also have similar email addresses that they used for logging into Netflix. That’s fine, so long as each Rob only uses their respective login info. However, Rob #2 was mistakenly using Rob #1’s email address when he tried to authorize Netflix on a new device. This explains all the previously received password reset emails, but not how Rob #1’s account was ultimately closed out. #3. Calling Netflix: After unsuccessfully trying to reset his password (with the wrong email address), Rob #2 called Netflix to have a customer service representative add the second device to his account — not cancel the account, a spokesperson for the streaming service tells Consumerist. #4. Confusion Over Two Accounts: Once Rob #2 reached a CSR, the rep noticed there were two accounts associated with the same name. At this point, the rep assumed that this was a case of an accidentally duplicated account. He informed Rob #2 that he would simply consolidate the accounts, as to avoid confusion in the future. While that’s an understandable move, it was a wrongful assumption on the rep’s part, Netflix admits to Consumerist. #5. Failing To Verify: In order to consolidate the two accounts under the same name — or to make any changes to an account — a customer must provide verifying information, often the credit card number associated with the account, the Netflix spokesperson explains. While Rob #2 has the same name as Rob #1 — and while he incorrectly thinks Rob #1’s email address belongs to him — he doesn’t have Rob #1’s credit/debit card info. That should have been a red flag that halted the process, but it wasn’t. #6. Canceled Account: Unable to merge the two accounts without the correct payment card information, the Netflix rep simply decided that the two accounts were duplicates — and canceled Rob #2’s Netflix access. “This was done on behalf of customer service,” says the Netflix spokesperson. “No one had access to anyone’s account. It was a wrongful assumption that it was a duplicate account.” The spokesperson says that no one can cancel an account without providing verifying information to an account services rep. Finding Resolution Rob #1 tells Consumerist that he was able to call Netflix and have his account reactivated by providing his name, email, and password. Additionally, he asked the company to put a note in his account to ask for specific verifying information before anyone is able to make changes to his account — including a change made on behalf of Netflix customer service. “His account should never have gotten canceled,” reiterated the spokeswoman, noting again that the customer’s private information was never breached or at risk of being accessed by another customer. “Bottom line is no one’s account was unsecured,” she says. Customers with questions or concerns about Netflix security can visit netflix.com/security for additional information. Source: consumerist
-
-
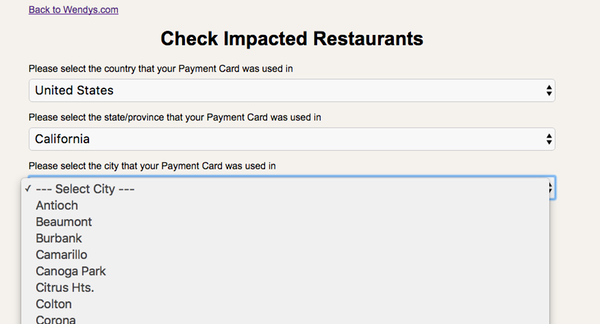
Fast food giant Wendy’s says that it now believes that more than 1000 of its restaurants across the United States have fallen victim to a hacking gang, who used malware to steal customers’ credit and debit card information. In a statement posted on Wendy’s website, president and CEO Todd Penegor apologize's to affected customers, and explains that the company has been investigating the data breach since earlier this year: Wendy’s first reported unusual payment card activity affecting some restaurants in February 2016. In May, we confirmed that we had found evidence of malware being installed on some restaurants’ point-of-sale systems, and had worked with our investigator to disable it. On June 9th, we reported that we had discovered additional malicious cyber activity involving other restaurants. That malware has also been disabled in all franchisee restaurants where it has been discovered. We believe that both criminal cyberattacks resulted from service providers’ remote access credentials being compromised, allowing access – and the ability to deploy malware – to some franchisees’ point-of-sale systems. Wendy’s believes that the malware has been effectively deployed on some franchisee systems since late fall 2015, stealing the following payment card data: cardholder name, credit or debit card number, expiration date, cardholder verification value (different from the three digits on the back of your card), and service code. Of course the longer malware lies undetected on a retailer’s systems, the more information it can potentially steal. Although Wendy’s has declared that at least 1,025 restaurants have been hit by the hackers it has not said publicly how many customers it believes might be impacted by the data breach. The use of malware to infect point-of-sale (POS) systems at retailers is something we have seen more and more in recent years, with a variety of stores and hotels forced to confront attackers that have used sophisticated surreptitious malware to intercept credit card details. And the fact that Wendy’s is pointing a finger of blame towards the hackers gaining access to their network via a third-party provider’s login credentials will surely ring a bell in the memory of those who recall the monumental hack against Target – whose network was breached after login credentials were stolen from an HVAC subcontractor. If Wendy’s suspicion that the attacks were assisted by the hackers exploiting the usernames and passwords of third-party service providers then there is a clear message for all businesses: If you must give service providers access to your network, insist upon strong password policies (for instance, unique, hard-to-crack passwords for each login) and additional levels of authentication to reduce the chances of hacker exploitation. Even if you trust your service provider, limit what they can do on your network – keeping access to the absolute minimum that they require to do their job. Have systems in place to monitor who accesses your network, what data they access, and have it report suspicious or unusual activity so it can be investigated. Require your third-party suppliers and partners to comply with baseline security procedures. If you don’t feel confident that they can meet your standards, don’t give them access to any part of your network. Of course, you are probably wondering if you might have been impacted by the breach. Fortunately Wendy’s has provided a webpage where you can easily choose your location from a drop-down list, and see if your local restaurant is one of those which is known to have been struck by the hackers. Wendy’s is offering potentially impacted customers who paid with a card one complimentary year of fraud consultation and identity restoration services. With so many big retailers falling foul of credit card-stealing hackers in recent years, you might be wise to pay in cash next time you fancy a burger. Source: welivesecurity
-
-
When you see a brand-name handbag or laptop being sold on Amazon for well below its retail price, it’s hard to not hit the “Buy” button. But is it a good deal or just a counterfeit in brand-name clothing? A new report from CNBC claims that a growing number of products sold by third parties on Amazon are fakes, and that the e-tail giant is having a difficult time getting a handle on the problem. As a result, sellers of legitimate goods say their revenues are hurting as more and more companies copy their products and offer them at steep discounts, while customers are complaining that their newly acquired items aren’t the real deal. Here’s what we learned about Amazon’s counterfeit problem, and what the company is doing to make it right. #1: Opening the floodgates: CNBC reports that counterfeiting on Amazon has grown significantly in recent years as the company welcomed Chinese manufacturers into its operations. Sales from China-based sellers more than doubled last year. #2: A mixed bag of products: The increase in sales from Chinese companies on Amazon has been made possible, in part, because the company has made it easier for these manufacturers to get their products to customers quickly. For example, Amazon registered with the Federal Maritime Commission to provide ocean freight for Chinese companies to ship goods directly to Amazon fulfillment centers, cutting out costs and inefficiencies. #3: Commingling and false security: The increase in products from Chinese merchants has led to commingling of products at Amazon fulfillment centers. This allows the company to put together orders with products from different sellers, making it difficult to know you’re purchasing a counterfeit item. These orders, because they come from an Amazon fulfillment center, often contain a FBA (Fulfilled By Amazon) tag. Critics say this gives customers a false sense that their products are legitimate. CNBC suggests that a counterfeit jacket could be sent to an Amazon facility by one merchant and actually sold by another. #4: A lack of safeguards: Critics say that Amazon hasn’t done enough to prevent the influx of counterfeit items or prepare shoppers for the possibility that they might not be buying what they thing they are. This is evidenced, CNBC says, in the number of sellers that offer high-end products at deep discounts. While these sales should raise a red flag for both customers and Amazon, that simply doesn’t appear to be occurring. “As long as the logo looks legit, people assume you have that item,” a Canada Goose seller offering a $1,000 jacket for $650 on Amazon, tells CNBC. #5: Trying to make it up: CNBC reports that while counterfeiting is supposedly on the rise at Amazon, the company is trying to help customers after the fact. If customers can verify that they’ve bought counterfeit goods, Amazon will push sellers to refund the purchase or they kick the sellers off the site, Walter Price, a portfolio manager at Allianz Global Investors, tells CNBC. “Amazon does stick up for the consumer,” he says. “They put the customer first, not the merchant.” However, some customers and sellers have run into issues with these policies. Back in 2012, a man who purchased a pair of headphones from a third-party seller on Amazon told Consumerist that when he tried to resell them on the site they were flagged as counterfeit. Additionally, Amazon does have an anti-counterfeiting policy that works to respond to infringement notices submitted by sellers who feel their products are being ripped off. CNBC reports that the fraudsters often make it difficult by changing the names of their stores and relaunching as quickly as they were removed from the site. “They’ve been reactive, not proactive,” Chris McCabe, a former Amazon merchant account investigator, tells CNBC. “Amazon can’t watch everyone all the time, and they don’t pretend they can.” Amazon’s Chinese counterfeit problem is getting worse [CNBC]
-
- amazon
- brand-name
-
(and 3 more)
Tagged with:
-
The Chicago area is one of Comcast’s larger markets, but until now it has avoided being part of the cable colossus’s expanding “test” of data caps. That’s about to change, with Comcast subscribers all over the Chicagoland area getting the bad news that they will soon face limits on their monthly data usage. Several Chicago-area Comcast customers have forwarded us emails from the cable/internet provider, with the title “Introducing a Terabyte Internet Experience,” which is the marketing department’s way of informing subscribers that they will soon be capped at 1TB of data/month. The cap will kick in on Aug. 1, according to the emails we’ve seen. These subscribers did not previously have any sort of monthly limit on their Comcast usage. Chicago now joins other major Comcast markets, including Miami and Atlanta, as part of the years-long “trial” that underwent a significant expansion in late 2015. This FAQ from Comcast on the capped plans has the full, current list of markets impacted by the not-really-a-trial-anymore. Earlier this summer — amid thousands of complaints from Comcast customers that their data was being measured inaccurately, or that they were being charged for data they couldn’t possibly have used — Comcast more than tripled the size of the monthly cap to a full terabyte. While that’s more than enough for the large majority of home broadband users, consumers are only going to increase their data usage as streaming video (and especially 4K streaming video) grows more popular, and as more in-home devices are connected to the internet. Additionally, Comcast will soon be rolling out its DOCSIS 3.1 technology that allows for fiberoptic-like data speeds over existing cable lines. That too will only encourage subscribers to devour more data, eventually pushing them to toward the terabyte limit. Of course, with the more forgiving data cap, Comcast made it more expensive to go beyond the cap, raising the monthly add-on price for “unlimited” data to $50 (up from $35). Comcast confirms to Consumerist that Chicago has been added to the not-really-a-trial-anymore-if-we’re-being-honest-about-it, but declined to name which other markets will be added in the future. Several of Comcast’s largest markets — including Philadelphia, Boston, D.C., Seattle, Minneapolis, and Houston — have yet to be included in the cap trials, but the addition of Chicago seems to indicate that even the largest Comcast audiences are destined for data caps. The below map shows all the Comcast markets — circled in yellow — that are now part of the cap trials. The remaining areas in orange are what remains of the un-capped Comcast footprint: Internal Comcast documents confirm that the company is not enacting these caps to deal with excess congestion. Instead, the company has painted these thresholds as a way of getting the heaviest users to pay more, much like someone who uses a lot of electricity pays the most. However, critics — including Consumerist — have pointed out that Comcast’s analogies in this argument don’t track, as people who use electricity (or water, or natural gas) often pay less on their monthly bill. Comcast offers no such sort of discount for light users. There is also the issue of Comcast exempting data for its own on-demand and streaming content from these data caps, a practice that consumer advocates have called on the FCC to put an end to. Source: consumerist
-

Event Viewer reports failed file security audit
allheart55 Cindy E replied to Kick's topic in Tech Help and Discussions
Personally, I think it's just an unexplained glitch in the Event Viewer. Are you having any problems with the operation of your computer? -
It is based on your hardware, Tony but linking the upgrades to your MS account will show you your digital rights entitlement.
- 5 replies
-
- 30 days
- free offer
-
(and 1 more)
Tagged with:
-
Once you have linked the upgrade install to your Microsoft account, you will be given the Digital Rights for Win 10. This is what I am going to do with one Win 7 and one Win 8.1 computer. I had planned to do it this weekend, providing the cable company is finished working and I don't lose internet.
- 5 replies
-
- 30 days
- free offer
-
(and 1 more)
Tagged with:
-
-
The year long free upgrade offer to Windows 10 for Windows 7/8.1 users is coming to an end on 29 July. While I expect there will be a big push of upgrades leading up to the offers expiration in a little more than three weeks, most individuals who were likely to take advantage of the free offer have already done so. Others may be using the tactic of upgrading their current system to Windows 10 to get their Digital Entitlement/License and then reverting back to Windows 7 or 8.1 until they are ready to make the move up to Windows 10. However, there will be plenty of users who never heard about the free offer or simply opted to not change anything on their systems. For them it appears the upgrade process to Windows 10 after 29 July from their existing system will be different than Windows upgrades from eligible systems were in the past. In my research there are currently only two retail versions of Windows 10 being offered for purchase - Windows 10 Home ($119) and Windows 10 Professional ($199). The retail packaging for each of those versions are labeled as full versions and not upgrades. That means they can be used to upgrade existing Windows 7/8.1 systems or to clean install on Windows XP and Vista machines. In the past, when new versions of Windows were being released, there was always an upgrade version available for eligible systems at a reduced cost compared to the full version. In addition, there was also the actual full retail versions of the new operating system available for those who wanted to install it on a system that was not eligible for that less expensive upgrade version. After 29 July, when a user decides they want to upgrade to Windows 10 and they have not previously taken advantage of the free upgrade options to Windows 10, it looks like there will be just one path to that migration to Windows 10 and that is the full versions that are being offered for sale through retail channels. Since the full retail versions of Windows 10 will have their own product keys included in the package any hardware that meets the minimum specifications will be able to run the new OS and it will not matter what version of Windows was previously installed. You won't even need your old Windows product key to validate your upgrade eligibility. Of course, one less expensive upgrade offer that will remain in place is the option to upgrade Windows 10 Home to Windows 10 Professional through the Windows Store for $99. If you upgraded from Windows 7/8.1 Home versions for free during this past year then this $99 offer is a great way to move up to the Pro version of Windows 10 at a savings of $100. Of course, the vast majority of new users on Windows 10 after 29 July will get the operating system when they purchase their next computer off a store shelf or from an OEMs website. However, the looming question after 29 July is whether or not Microsoft can reach their ambitious goal of Windows 10 being on one billion devices by July 2018. At this point, with over 350 million active devices now running the year old operating system, they only have 650 million to go. I have reached out to Microsoft to confirm the absence of the less expensive upgrade options so I will update this article once I hear back from them. Source: winsupersite
-
Amazon increasingly promises faster, quicker, more local delivery. UPS, FedEx, and the Post Office can’t handle all that, of course, so the e-retail giant turns to local couriers, its own Amazon-branded fleet… and, increasingly, folks who volunteer to drive your stuff around for a few bucks an hour. Word about Amazon’s plan to expand their “Amazon Flex” program leaked out a few months back, and the pilot continues. Inasmuch as delivery drivers use their own cars and remain individual contractors (not employees), the service is fairly comparable to the big car-hailing dinosaur in the room, Uber. But there are two big, key differences in how Amazon Flex operates. One: drivers report to the company, not to individual users. And two: it’s not entirely on-demand, but rather based on choosing time Anyone who signs up via Amazon’s (Android-only) “Delivery” app can retrieve and deliver residential customers’ packages for $18 an hour (plus tips). After completing video orientations, drivers can sign up for time slots in which they will be delivery drivers (like “Wednesday, 1-3 p.m.”). After that, they’re expected to show up at their local sorting facility when their “shift” begins, and haul packages until it ends. So to find out what it’s really like, tech writer Sam Machkovech over at Ars Technica signed up to be a driver, and the site made a video of his adventures in independent contracting. When Machkovech showed up at the Amazon fulfillment center near Seattle, he got a firm dictate from a man who was emphatically not his manager. “I am not your manager, I am not your boss. You guys are independently contracted with Amazon. I can’t tell you in what order to deliver them in, I can’t even tell you to deliver them on time,” the man said. “I thought the app would sequence the deliveries for you,” another driver suggested. The not-a-boss replied with, “It’s supposed to, but they turned that feature off a few weeks ago.” He continued, “I don’t have access to scheduling, why you can’t sign up,” before showing the drivers how the app and map work, describing the 210,000 Amazon Now customers in greater Seattle — and how spread out they are, and how terrible the Seattle traffic is. Logistically, it’s all pretty complicated, and far from perfect. Packages use a detailed coding system, and the app proves less than 100% user-friendly for Machkovech — who, as a professional tech writer, is pretty familiar with using and optimizing technology. The app is a big bottleneck, Machkovech found. “There is so little information in this program right now in terms of what I can and can’t do,” he vented after his first delivery. “I would absolutely be winging it if I had to deal with signing… all I know is that I’m required.” “I was told, ‘use your best judgment,'” Machkovech said with a shrug (indeed, a ¯\_(ツ)_/¯ ). “It’s very Wild West of them right now, and I think there’s going to be big concerns with them as they go along, if anybody gets weird about it.” Machkovech is right that Amazon may continue to encounter big challenges if it scales up the program nationwide. Lawyers, lawmakers, and regulators are becoming increasingly interested in the all-contracting, all-gigging, no-employment land of modern work in the on-demand economy, and Amazon has already found Prime Now drivers accusing it of wage theft and paying less than minimum wage (after expenses). Source: consumerist
-
- amazon
- amazon flex
-
(and 1 more)
Tagged with:
-
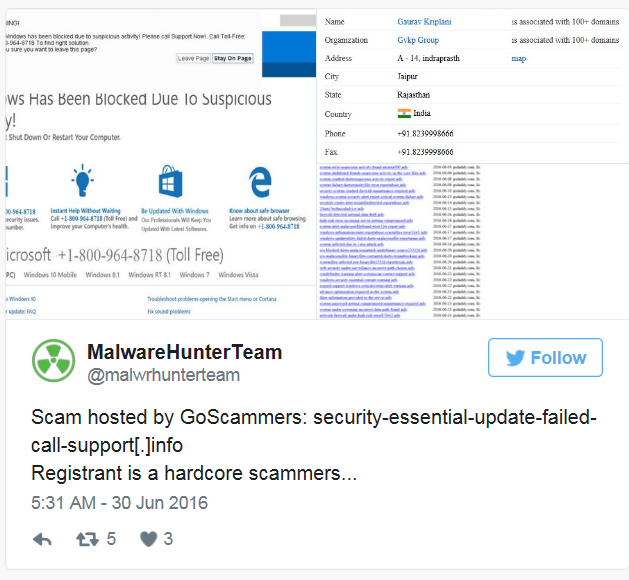
Security researchers have spotted an individual who registered 135 domains to host and push out tech support scams. According to MalwareHunterTeam, the individual's name and address are tied to 135 tech support scam domains, including 120 which are hosted on Internet domain registrar GoDaddy. This isn't the first time crooks have abused GoDaddy accounts for malicious purposes. For instance, back in May, a rogue advertiser hijacked poorly protected GoDaddy accounts, which they in turn incorporated into a malvertising attack that targeted two TV stations affiliated with the American CBS TV network. Most of the domains registered in the individual's name host tech support scams, which may or may not lock a user's computer screen or impersonate their ISP. Some host scareware, while others appear to currently be offline. Then again, it's no surprise something mischievous would originate from system-blocked-due-to-malacious-activity-error101c11cmd[dot]info or security-essential-update-failed-call-support[dot]info. What is a surprise to MalwareHunterTeam is the fact that there's no blacklist to prevent known bad actors from registering scam domains. As the researcher told Softpedia: "This is a big business. And no one on Earth does anything against them. The main problem is that this man could register 100+ scam domains (the domain names are telling that they are scam) starting from the first days of April, without any problem. It's simply crazy... And it's just one man." MalwareHunterTeam also claims they sent a full text file of the scam domains to GoDaddy but that the registrar has done nothing. Catalin Cimpanu of Softpedia attributes this lack of action to an overabundance of reports flooding GoDaddy's abuse department: "Nobody's saying that GoDaddy is protecting such activities, but its abuse department is completely overwhelmed at the moment. To be fair, there are plenty of other Web hosting firms that don't even run an abuse department, and the only way to reach them is through the national CERT teams. But, there are also awesome hosting firms, that kill these sites in three or seven minutes, only after a tweet and without having to fill in countless of forms." In the absence of meaningful action from GoDaddy and other domain registrars, users are urged to not fall for a tech support scam. No one from a legitimate technology company will ever contact you out of the blue and warn you about suspicious programs on your computer, so be sure to not give those people any personal or financial information. If you feel you have a tech support issue, make sure to contact the appropriate company directly using its published contact details. Source: graham cluley
-
Have you been flirting with a computer program behind your wife's back? "Life is short, have an affair" was the slogan of infidelity website Ashley Madison, which was famously hacked in 2015. What they didn't say was that you might be having a strictly online affair with a fake female profile, designed to trick you into entering your credit card details, under the misapprehension that you were chatting with a real woman rather than an algorithm. Now Reuters reports that Ashley Madison's parent company Avid is being investigated by the US Federal Trade Commission (FTC) after class action law suits were filed in the United States and Canada on behalf of customers whose details were exposed following the hack, and amid allegations that fake female profiles were used by the site to manipulate users: An Ernst & Young report commissioned by Avid and shared with Reuters confirmed that Avid used computer programs, dubbed fembots, that impersonated real women, striking up conversations with paying male customers. Avid shut down the fake profiles in the United States, Canada and Australia in 2014, and by late 2015 in the rest of the world, but some U.S. users had message exchanges with foreign fembots until late in 2015, according to the report. Ashley Madison had been planning to IPO before it was royally hacked. You have to imagine that it would have found itself in even hotter water if it had successfully floated on the stock market only to have it later revealed that it had been less than transparent with investors about its true (human) membership numbers. The controversial dating site is under new management following the departure of CEO Noel Biderman (who has since been busy trying to clean the internet of references to his past with Ashley Madison), and the site has a brand new look which de-emphasises having an affair and claims it "is about so much more than infidelity." New bosses Rob Segal and James Millership tell Reuters that the firm is spending millions on security and privacy improvements. But that, of course, is going to be little comfort for those have already been burnt by Ashley Madison - having had their personal information exposed, and in some cases found themselves on the receiving end of blackmail letters or even driven to suicide. The greatest irony of all is that some men have had their lives ruined and privacy invaded, when their chances of having an affair were close to zero, because they were speaking to a computer program rather than a flirting female. Source: graham cluley
-

Animals before and after they were taken home.
allheart55 Cindy E replied to DSTM's topic in Tech Help and Discussions
Our current rescue dog is a German Shepherd. He's a beautiful, loyal and loving dog. -
A hacker successfully commandeered a Facebook user's profile by conducting a social engineering attack that involved a fake passport. The hack occurred on June 26 when an unidentified attacker contacted the Facebook support team posing as Aaron Thompson, a legitimate Facebook user and resident of Michigan in the United States. The hacker's original message reads: "Hi. I don't have anymore access on my mobile phone number. Kindly turn off code generator and login approval from my account. Thanks." In its response, Facebook provided the hacker with a few recommendations for how they could regain access. They also said the Thompson poser could provide Facebook with two things if it still wasn't possible to access the profile: a scan of a photo ID and a description of the issue being experienced. The attacker replied with this fake passport. Facebook could have easily determined that none of the details provided in the passport match the real Aaron Thompson's profile. Still, it was enough for the site's support staff, who disabled Thompson's login approval settings and granted the hacker access to the account. Facebook sent a message to the email address attached to Thompson's profile explaining the change in his account settings: It was then that Thompson first learned of the hack. But, by then, the attacker had already gained access to Thompson's account, including his access to several business pages he managed on Facebook. Motherboard reports Thompson is convinced the hacker targeted him in an attempt to monetize his pages. But the attacker did no such thing. Instead he sent out only a few messages to the hacked user's friends. Most notably, he sent an image of his genitals to the victim's girlfriend. Thompson contacted Facebook support but initially experienced some difficulty in resolving the issue. Frustrated, he decided to share his story on Reddit, where he said he was "pretty devastated" about the "blatant harassment" the hacker had perpetrated against him and his social circle. Shortly thereafter, Facebook's support team stepped it into high gear and helped Thompson regain access to his account and business pages. A Facebook spokesperson said the incident should never have happened: "Accepting this ID was a mistake that violated our own internal policies and this case is not the norm." Clearly, no matter how many security features we might enable on our accounts, including two-step verification (2SV), human error can still threaten our account security. That's why companies like Facebook should continuously review and update their security policies, not to mention regularly train their employees to not fall for a social engineering attack like the one that locked Thompson out of his account. Source: graham cluley