-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
-
-
-
In March, 49-year-old Elaine Herzberg became what’s believed to be the first pedestrian killed by a self-driving car. It was one of Uber’s prototypes that struck Herzberg as she walked her bicycle across a street in Tempe, Arizona on a Saturday night. There was a human test driver behind the wheel, but video from the car’s dash cam published by SF Chronicle shows that they were looking down, not at the road, in the seconds leading up to the crash. Police say that the car didn’t try to avoid hitting the woman. The SF Chronicle reports that Uber’s self-driving car was equipped with sensors, including video cameras, radar and lidar, a laser form of radar. Given that Herzberg was dressed in dark clothes, at night, the video cameras might have had a tough time: they work better with more light. But the other sensors should have functioned well during the nighttime test. But now, Uber has reportedly discovered that the fatal crash was likely caused by a software bug in its self-driving car technology, according to what two anonymous sources told The Information. Uber’s autonomous programming detects objects in the road. Its sensitivity can be fine-tuned to ensure that the car only responds to true threats and ignores the rest – for example, a plastic bag blowing across the road would be considered a false flag, not something to slow down or brake to avoid. The sources who talked to The Information said that Uber’s sensors did, in fact, detect Herzberg, but the software incorrectly identified her as a “false positive” and concluded that the car did not need to stop for her. The Information’s Amir Efrati on Monday reported that self-driving car technologies have to make a trade-off: either you can have a car that rides slow and jerky as it slows down or slams on the brakes to avoid objects that aren’t a real threat, or you have a smoother ride that runs the risk of having the software dismiss objects, potentially leading to the catastrophic decision that pedestrians aren’t actual objects. [/url] Efrati pointed to GM’s Cruise self-driving cars as being prone to falling on the overly cautious end of the spectrum, as they “frequently swerve and hesitate.” [Cruise cars] sometimes slow down or stop if they see a bush on the side of a street or a lane-dividing pole, mistaking it for an object in their path. In March, Uber settled with Herzberg’s family, avoiding a civil suit and thereby sidestepping questions about liability in the case of self-driving cars, particularly after they’re out of the test phase and operated by private citizens. Arizona halted all of Uber’s self-driving tests following the crash. Other companies, including Toyota and Nvidia, voluntarily suspended autonomous vehicle tests in the wake of Herzberg’s death, while Boston asked local self-driving car companies to halt ongoing testing in the Seaport District. Source: Sophos
- 2 replies
-
- killed
- self-driving
-
(and 2 more)
Tagged with:
-
-
-
-
-
-
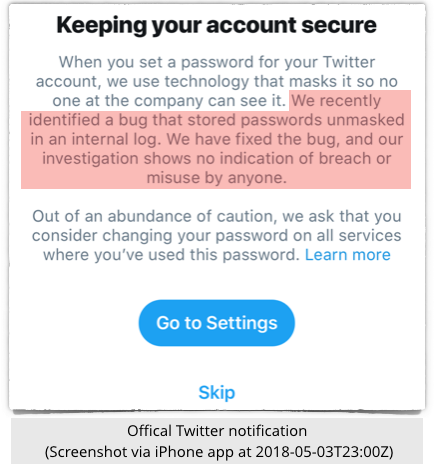
We just received a warning from Twitter admitting that the company had made a serious security blunder: it had been storing unencrypted copies of passwords. You read that correctly: plaintext passwords, saved to disk. What an announcement to have to make on World Password Day! Any regular reader of Naked Security will know that plaintext passwords are an enormous no-no. It’s OK to have passwords in memory temporarily when verifying them at login time, but that’s all you should ever do with raw passwords. You shouldn’t write passwords to a temporary file that you intend to delete later – your program could crash before it cleans up properly, or the disk where you wrote the data could be unmounted before you’ve finished. You shouldn’t even keep passwords in virtual memory that the operating system might page out into the system swapfile, lest the passwords get flipped out to disk when the system is heavily loaded. On Windows, you can use the VirtualLock() system function to keep memory blocks “locked into” physical RAM, thus preventing them from getting paged out to the swapfile. You really, certainly, absolutely shouldn’t let unencrypted passwords get saved anywhere that’s supposed to be permanent… …and that most definitely means taking great care that you DON’T WRITE PASSWORDS INTO LOGFILES BY MISTAKE. Unfortunately, that’s what Twitter realised it’s been doing, thus its mea culpa warning today. [/url] The good news is that the password databases actively used by Twitter to patrol logins were implemented securely. Twitter uses bcrypt, an algorithm that performs what’s known as salt-hash-stretch to turn passwords into cryptographic checksums that you can later use to verify that a password held temporarily in memory was supplied correctly. That’s because a password hashing procedure as bcrypt lets you work forwards from a supplied password to match it against the stored password hash, but not to work backwards from the hash to recover the original password. Even if crooks hack in and steal the password file, they can’t just read the passwords out of the purloined database. Instead, they have to try every possible password (or try a “dictionary” of likely passwords) against each user’s hash and see which passwords they were lucky enough to guess correctly. The bad news here, of course, is that the safety provided by using bcrypt for password verification was undone by writing plaintext passwords to the system logs. If the crooks went for the logs instead of the password database, they could extract the logged passwords directly, with no cracking or “dictionary attacks” required. What to do? Twitter claims that it has now “fixed the bug” and that its investigation “shows no indication of breach or misuse by anyone”. Twitter therefore suggests merely that you “consider changing your password”. We’ll go one step further and urge you to change your password – after all, Twitter isn’t saying how long it’s been logging passwords, or how many it collected by mistake along the way, so there’s no way to judge how far and wide any saved passwords might have been replicated by now. We also suggest that you start using Twitter’s two-factor authentication system, also known as login verification, if you aren’t already. This means you need to supply a single-use code that’s sent to, or calculated by, your mobile phone when you login – your password isn’t enough on its own. Should you stop using Twitter altogether on account of this carelessness? That’s up to you, of course, but we suggest that changing your password promptly is enough. Source: Sophos
-
-
-
Facebook Inc. is going to let users see which websites and apps send the social network data on their activity -- and then give them the option to delete it, with a new "clear history" tool. The Menlo Park, California-based company is developing the feature in response to an outcry about data collection and privacy on its sites, following revelations that an outside developer improperly handled personal information on tens of millions of users. The crisis has spawned questions from lawmakers and privacy advocates about who owns the data that users share on Facebook, and the company has taken other steps to address the concerns, including pausing some developer tools and auditing apps on its platform. "The past several weeks have made clear that people want more information about how Facebook works and the controls they have over their information," Chief Privacy Officer Erin Egan wrote in a blog post on Tuesday, just as the company kicked off its F8 annual developer conference. "If you clear your history or use the new setting, we’ll remove identifying information so a history of the websites and apps you’ve used won’t be associated with your account." It will take months to build the new Clear History feature, Egan wrote, adding that the company will work with privacy advocates, academics, policy makers and regulators for input on how to remove personal information. Chief Executive Officer Mark Zuckerberg said that he learned, while testifying in front of Congress last month, that he didn’t have clear enough answers to questions about data and Facebook should offer users this kind of option to control their information. But he warned people about using it, because “your Facebook won’t be as good while it relearns your preferences,” he wrote in a post Tuesday. Source: IT Pro Today
-
- activity
- clear history
-
(and 2 more)
Tagged with:
-

3rd party apps & Windows 10 April
allheart55 Cindy E replied to peterr's topic in Microsoft Support & Discussions
While it is true that some apps need to be installed from the Windows Store, I can go to a download page on the web, to install certain apps I want to have. For instance, I downloaded and installed Revo Uninstaller from HERE Some apps are not available from the Windows Store, in which case I go to the programmer's website. In any case, always be careful where you download from as there a lot of unsafe sites out there. -
-
So far, so good, Bob!
-
-
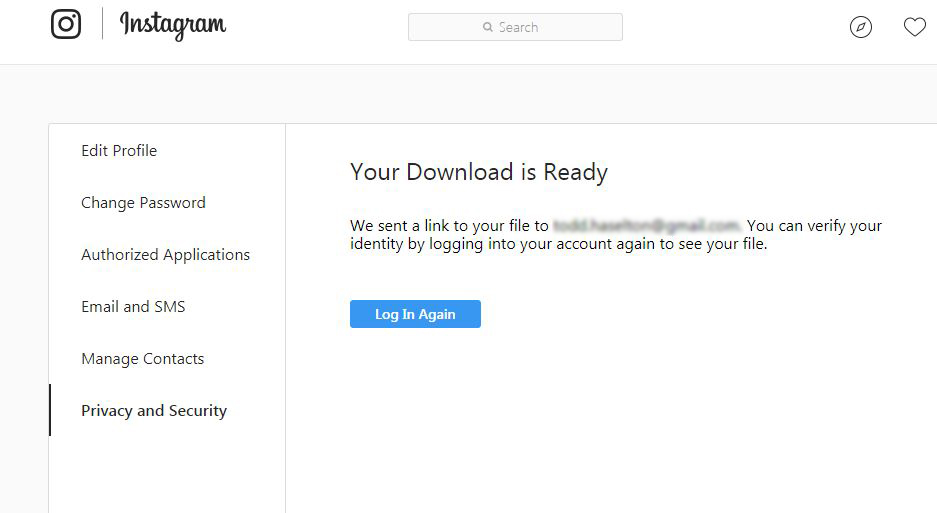
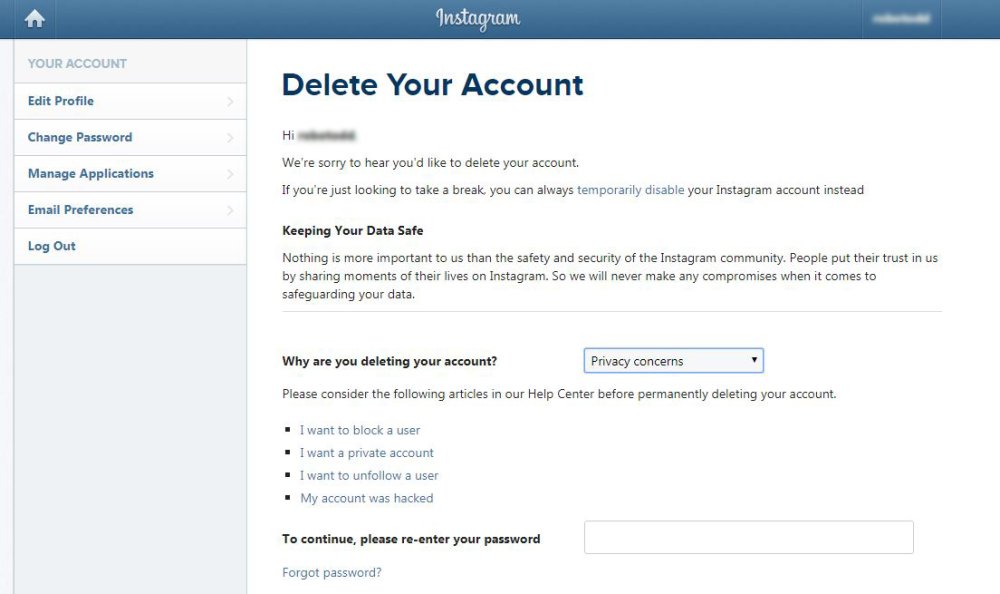
Facebook's Instagram keeps a copy of everything you've ever shared. It's easy to download an archive of that information, so I'm going to show you how. There are two primary reasons you might want to do this: first, it's worth seeing what sort of private information is stored on Instagram's severs. Second, it's convenient if you want to take all of your data and move to another service. I downloaded my archive and discovered that Instagram has access to all my contacts phone contacts -- including their names, email addresses and full names -- even if they don't use Instagram. It also has a copy of: My profile information. Everything I've searched on Instagram. Everyone I follow. Every post I've ever liked. Direct messages I've sent to other users. Every video I've ever posted. Every photo I've ever posted. Every story I've ever shared (Stories are Instagram's Snapchat-like feature.) The Instagram archive doesn't include any data about ads you've viewed or interacted with, or what sorts of ad topics it think you might be interested in. Facebook must have this data somewhere, but it isn't included in the file you download. How to download your data You can download your own archive and discover what Instagram still knows about you. Here's how: Navigate to Instagram.com and select your profile. Click the gear next to your name and select "Privacy and Security." Scroll down to "Data Download" and click "Request Download." Then enter the email you'd like to receive the download link too and verify the request by entering your Instagram password. While Instagram says it can take up to 48 hours, I received my download link in under thirty minutes. The data comes through as a zip file with folders for photos, stories, and videos. Anything that isn't a photo or video -- messages, profile, searches, and settings -- are saved in text format that you can open with notepad on a computer. How to delete your Instagram data: If you don't want Instagram to have this data, you can delete it all. (Instagram confirms in its FAQ that it's actually deleted.) Doing so requires you to delete your entire account permanently, however. If you don't want to do that, you can temporarily disable your account, too. Here's how: Visit Instagram's "delete your account page." Select a reason for why you want to delete your data. Click "Permanently delete my account." That's it. Now you've learned how to download a copy of all of your Instagram data and, if you want, how to delete it. Source: CNBC
-
- copy
- information
-
(and 2 more)
Tagged with:
-
-
-
It certainly isn't looking too good for Eric Lundgren. I'm thinking he deserved what he was given.
- 3 replies
-
- counterfeiting windows
- eric lundgren
-
(and 1 more)
Tagged with:
-
In response to stories about the 15-month jail sentence given to Eric Lundgren, Microsoft has written a strident blog post detailing its perspective on the case. The post, titled “The facts about a recent counterfeiting case brought by the U.S. government,” consists of several assertions drawn from the case itself, the email evidence that was submitted for it, and Microsoft’s own take. Microsoft’s corporate vice president of communication, Frank Shaw, begins by once again asserting Microsoft’s support for refurbishing and recycling. But the main thrust of the post is to re-assert the findings of the court. After noting that it was the US government — not Microsoft — that brought the case, Shaw notes that Lundgren pleaded guilty. He also argues that Lundgren’s emails contain strong evidence that he did, in fact, intend to profit from counterfeiting Windows. Included in the post are multiple emails detailing how Lundgren wasn’t just providing software disks, but going to “great lengths” to make those disks look like they were made by Microsoft or Dell. Earlier today, we published an interview with Lundgren, detailing his side of the story. Although he pleaded guilty, he puts blame directly at Microsoft for his jail time. He feels that this is more about protecting profits made from selling Windows to refurbishers than concerns about counterfeiting or piracy. Microsoft obviously disagrees. Shaw concludes this post thusly: Mr. Lundgren’s scheme was simple. He was counterfeiting Windows software in China and importing it to the United States. Mr. Lundgren intended the software to be sold to the refurbisher community as if it was a legitimate, licensed copy of Windows. It was not. The evidence in the case shows Mr. Lundgren used his knowledge of the PC recycling community to scam the very community he claimed to champion and to evade the law. Had he simply wanted to help this community, why did he set up an entire counterfeit production operation in China to make the CDs appear legitimate? And why did he charge for his counterfeit product and try to make a profit at the expense of the community he was ostensibly trying to help? One of the core issues of the case was the value of the software Lundgren was attempting to distribute. Lundgren and an expert witness contend that the value was essentially zero. That’s because, they argue, the actual value of the software should have been in the license to use the software, not in the restore software itself — which can be downloaded for free from Microsoft’s own website. Here’s how Lundgren characterized the issue: They were comparing it to a new license. You don’t get a license with the restore CD. The government treated the infringed item as if it was a licensed product, the license itself, what Microsoft sells, and it’s not. ... I got in the way of Microsoft’s multi- multi- multi-million dollar business model of recharging people for computers that already have an operating system. Although Microsoft’s response doesn’t directly address the distinction between the restore software and the license to use it, it does seem as though the company is contending that distinction is misleading. Shaw writes: When a refurbisher installs a fresh version of Windows on a refurbished PC, we charge a discounted rate of $25 for the software and a new license – it is not free. Thousands of refurbishers participate in this program legally without confusion, and the program works. Whether or not it’s necessary for refurbishers to pay that $25 fee to Microsoft for a fresh license is still very much still in dispute in the larger community, but that’s the number upon which Lundgren’s sentence was based. Lundgren is resigned to serving his 15 month sentence. As he told The Verge: “I want to write a book in prison about trying to find joy.” Source: The Verge
- 3 replies
-
- counterfeiting windows
- eric lundgren
-
(and 1 more)
Tagged with:
-
-