-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
Antivirus tools are the aircraft flotation devices of PCs: They give you a false sense of security. Despite efforts by security companies to thwart cyber attacks, hackers keep finding new ways into unsuspecting people's computers and systems. That's why Microsoft is adding a new feature to its Windows Defender line of anti-hacking tools: When hackers do get in, Microsoft will help customers identify the attacks and stop them before they spread. Windows Defender Advanced Threat Protection isn't admitting defeat, per se. But it's taking an important step towards coping with reality: Your system is going to get hacked, and you'd better be prepared when it does. Microsoft says the new tool analyzes information from more than 1 billion Windows devices, 2.5 trillion websites and 1 million suspicious files. When it senses an attack happening to one of its customers, Microsoft will send a notification. For example, the tool might detect that a suspicious IP address is trying to connect with a device on a customer's network, and the IT guy will get an alert. But Windows Defender ATP will also use that intelligence to alert other customers whose systems appear to be suffering from a similar attack too. Related: Apple vs. the FBI ... in 2 minutes Advanced detection is crucial. Microsoft said it takes corporate customers 200 days on average to detect a security breach and 80 days to contain it. That average cost is $12 million per cyber attack. "There will always be this possibility of attack," said Terry Myerson, Microsoft's Windows chief. "Instead of taking 200 days to detect, this could catch attacks very quickly." Windows Defender ATP is available for corporate customers who have deployed Windows 10 on their PCs. Microsoft (MSFT, Tech30) is trying to pitch Windows 10 as a necessary upgrade for any organization concerned about security. The Windows Defender ATP announcement comes a couple weeks after Microsoft revealed that all 4 million of the Pentagon's PCs will be upgraded to Windows 10 within the next 12 months. Source: cnn
-
- cyber attacks
- microsoft
-
(and 2 more)
Tagged with:
-

Show us your Pets. Current or long gone.
allheart55 Cindy E replied to DSTM's topic in Tech Help and Discussions
Such a beautiful kitty, Dougie. We haven't had any cats for almost ten years. Unfortunately, our German Shepherd, who is a rescue dog, does not like cats. We adopted Jax from a no kill shelter called Save, ten years ago. He is the most loyal and loving dog we have ever had. He also thinks that the grandkids are his puppies. :D -
Kittens free to a good home. Appear to be part Siamese. I think they're feral and abandoned by their mama. They are a little bitey and scared. They don't seem to purr.
-

Install IE9 update on Vista
allheart55 Cindy E replied to Tony D's topic in Tech Help and Discussions
That's great. Hiding the update was the only thing that worked for me. -

Install IE9 update on Vista
allheart55 Cindy E replied to Tony D's topic in Tech Help and Discussions
You don't want to delete the winsxs folder. It's used during Windows updates, service packs, hot fixes etc. -
https://www.youtube.com/watch?v=k6SVsf0k2i0 Ahead of the Oscars, Microsoft has started airing a series of ads that focus on Windows 10, gross bugs, and the features Windows machines have that Macs don't. The spots all feature a pair of women discussing how Windows 10 helps their business — they highlight Cortana, touchscreens, and Windows Hello. But the real point of the ads is that Apple doesn't offer equivalents to any of these things on the desktop. "I don't have a touchscreen on my Mac. I'm jealous of that," one woman says. In another, "[Cortana's] so helpful ... Even on the new Macs, they don't have that." Each ad takes a moment to call out something the Mac doesn't have or can't do. The spots end with the tagline, "Windows 10 PCs do more." It's a small but clear signal that Microsoft is getting more aggressive about advertising Windows 10, straying from the heartwarming tone its launch ads channeled. Microsoft has been hoping that the launch of its new operating system can stem the years-long decline in PC sales. That hasn't happened yet, but it looks like Microsoft will be putting Windows 10 in front of a lot more eyes tonight. So far, the ads have been airing over and over during E!'s coverage of the Oscars' red carpet. https://www.youtube.com/watch?v=VOV1tQpgAs8 https://www.youtube.com/watch?v=ln5LU532GuY https://www.youtube.com/watch?v=WHoHKjjttvQ Source: theverge
-

Install IE9 update on Vista
allheart55 Cindy E replied to Tony D's topic in Tech Help and Discussions
I've run into this problem before. The newer version of IE 9 is already installed. You should be able to right click the update and hide it so that it doesn't keep trying to do that. -
Our creative director Aurich Lawson is building a PC to power a custom arcade cabinet, and he was having trouble picking a processor. Not because he didn’t know what he needed, but because he was having trouble matching what he needed (the cheapest quad-core CPU that meets the recommended requirements for Street Fighter V) with what Intel was offering (five different obfuscated brands spread out over multiple sockets and architectures). And if you’re building a PC now after having been out of the game for a few years, it can be exceptionally confusing. Around the turn of the millennium you just had Celeron and Pentium. One name meant “cut-down low-end” and one meant “high-end, more features,” and you just bought the fastest one you could reasonably afford. Things got a little more confusing in the Core and Core 2 days (the Core branding continues to survive alongside the Celeron and Pentium brands), but you could at least use names like “Core Solo” and “Core 2 Quad” to guess which architecture and how many cores you were getting. Now there are three separate Core brands, Pentium and Celeron brands, and a long series of letters that you need to know to figure out what CPU you’re getting. It's been a few years since the last time we demystified Intel’s CPU lineup, and in truth things haven’t changed too much. In broad strokes, the rules are the same. But Intel has introduced and retired a few CPU architectures and brands since then. We’ll run down the basics for both desktops and laptops to help you make some sense of things whether you’re building a computer or buying one from someone else. First: Know your architectures Right this second we’re in a sort of transitional phase where some old CPUs are still filtering out as new ones filter in. In brief: The old chips, codenamed Haswell, are generally identifiable by their 4000-series model numbers or the “4th generation Core” label. The desktop chips use socket 1150 motherboards. In general, we would recommend against considering these for new builds or purchases unless you can get a really good deal—Haswell is at the end of its life and Intel won’t be making new chips for its socket in the future. There are also a handful of 5000-series, 5th-generation Broadwell desktop chips that use the same socket—Intel didn't do a full release of these CPUs because of manufacturing delays, so you'll find the majority of them in laptops instead. The new chips, codenamed Skylake, have 6000-series model numbers and a “6th generation Core” label. The desktop chips use socket 1151 motherboards, which is likely (not guaranteed, but likely) to see additional use in the upcoming Kaby Lake and Cannonlake architectures later this year and into next year. If you care at all about future-proofing, the small price premium is worth paying if you're building a desktop. Desktops: Celeron, Pentium, and Core There are a total of five separate processor brands that all share the Skylake architecture and the socket. I’ll list the high-level differences of each along with exceptions, and then we’ll get into model number suffixes. Celerons and Pentiums Both of these are budget brand names, and processors in both lines tend to be differentiated by clock speed and not much else. Skylake Pentiums are G4000-series chips, while Celerons are G3000-series. They’re all dual-core CPUs with no Turbo Boost, no Hyperthreading, and 3MB of cache, and they’re typically paired with the basic Intel HD 510 integrated GPU. Core i3 CPUs are a little faster, but Pentiums will give most price-conscious people the best bang for their buck. Exceptions: The Pentium G4500-series chips get an Intel HD 530 GPU that’s quite a bit faster than the 510 (within the realm of integrated graphics, anyway). Core i3 These CPUs are still dual-core but add Hyperthreading, which presents two logical processor cores to the operating system for every physical core. This can definitely help performance in multithreaded workloads, though it’s nowhere near the boost you’d get from moving to a quad-core CPU. Core i3-6100 CPUs include 3MB of cache while 6300-series chips include 4MB of cache; nearly all of them use the Intel HD 530 GPU. Exceptions: The Core i3-6098P uses an Intel HD 510 GPU. Core i5 These are all quad-core CPUs without Hyperthreading, and they probably represent the best balance of price and performance for high-end users. They also use Intel’s Turbo Boost feature, which let the CPU run at higher clock speeds when there’s enough thermal headroom or when fewer cores are being actively used. Not all workloads will benefit from two extra processor cores, but video editing, Photoshop work, and an increasingly large number of games are all happier with four cores. All of these CPUs include 6MB of cache and most of them have Intel HD 530 GPUs. Exceptions: The Core i5-6402P includes an Intel HD 510 GPU. Core i7 These are best described as Core i5 chips with Hyperthreading, higher clock speeds, and and 8MB of cache. Otherwise they’re the same. As with Core i3 CPUs, Hyperthreading definitely does help performance in heavily threaded programs, but jumping from a Pentium or Core i3 to a Core i5 will get you a much larger performance bump than jumping from an i5 to an i7. Exceptions: None. There aren’t many of these processors yet. Desktop Processors The Celeron, Pentium, and various Core labels tell you most of what you need to know about a given CPU, but the model number suffix is important too. Here’s what these suffixes mean (and note that some CPUs have more than one letter attached). No suffix: These are “mainstream” CPUs with no particularly special properties. T-series: These are low-power desktop chips with lower TDP values, which generally (but not always) translates into lower power consumption. These power savings are usually realized by reducing the CPUs’ maximum clock speed. For example, a Core i7-6700 has a TDP of 65W, a base frequency of 3.4GHz, and a Turbo frequency of 4.0GHz. A Core i7-6700T has a TDP of 35W, a base frequency of 2.8GHz, and a max clock speed of 3.6GHz. K-series: This relatively rare suffix denotes a multiplier-unlocked CPU that can be overclocked when paired with a high-end Intel Z170 chipset. The chips also have a higher 91W TDP, relative to the standard 65W for a quad-core CPU. E-series: E is for “embedded,” which implies that these are mostly going to come with pre-built systems or soldered to motherboards. System builders can mostly ignore this one. P-series: Back in the Core 2 days, a P-series chip didn’t include an integrated GPU. Now, P-series chips just include slower integrated GPUs. Go figure. Laptops: A big ol’ mess If you thought the desktop lineup was complicated, wait until you see how messy the laptop lineup is! In this case, the processor suffixes are a better way to keep track of the different processors. The different processor brandings mean different things based on the amount of power the CPU is designed to use and the kind of system it was designed to fit in. As with the desktop Core i3, i5, and i7 chips, 4000-series means Haswell, 5000-series means Broadwell, and 6000-series means Skylake. Each successive CPU generation includes minor-to-negligible improvements in CPU performance alongside more tangible improvements to GPU performance, something to keep in mind as you decide whether to buy something cutting-edge or save money on an older or refurbished model. Since upgrading the processor isn't even possible most of the time, you can worry less about having a future-proofed motherboard. That said, we'll focus primarily on Skylake here. Laptop processor suffixes Enlarge / Thin-and-light Ultrabooks like Dell's XPS 13 use dual-core U-series processors, which are the most common laptop chips Intel sells. Peter Bright U-series These are all dual-core processors that have become Intel’s bread-and-butter laptop chips, in everything from high-end Ultrabooks to mainstream laptops to low-end models (though the low-end Celeron and Pentium U models appear less often in budget laptops than Atom-derived versions we’ll talk about shortly). There are three different types of U-series Core i3, i5, and i7 Skylake processors, differentiated by their TDPs and integrated graphics processors. One way to tell is by the four-digit model number: if it ends in two zeroes, it’s a 15W processor with an Intel HD 520 GPU. If it ends in the number 50 or 60, it’s a 15W processor with an Intel Iris 540 GPU, which adds 64MB of eDRAM to alleviate memory bottlenecks. If it ends in a 7, it’s got an Intel Iris 550 GPU and a higher 28W TDP which means that both CPU and GPU can run at higher speeds for longer amounts of time. U-series Celerons are dual-core chips with 2MB of cache and an Intel HD 510 GPU. Pentiums and better include Hyperthreading. Core i3s include 3MB of cache, Core i5s and better add Turbo Boost, and Core i7s include 4MB of cache. Core i3s, i5s, and i7s all include either an Intel HD 520 GPU or an Iris 540/550 GPU as outlined above. Whew. HQ-series This one applies only to Core i5 and i7 chips, so at least there are only a few of them to keep track of. Again, you’ll need to know a combination of the suffix and the model number to get the full picture. These are all quad-core processors; Core i5s have 6MB of cache and Core i7s include 8MB of cache and Hyperthreading. Some members of the family come with beefier integrated GPUs than others, though, and that’s where model numbers come in. If the model number ends with the numbers 50 or 70 (for Core i5s and i7s, respectively), you’ve got a chip with Intel’s Iris Pro Graphics 580 GPU, the most powerful integrated GPU Intel has ever shipped. Thanks to an increased number of execution units (EUs) and 128MB of eDRAM cache, Iris Pro performance approaches that of a midrange dedicated GPU. That eDRAM can also serve as a fast memory cache for the CPU, which will provide a speed boost to certain workloads that have nothing to do with graphics. If the processor model number ends with anything else—00, 20, or 40—you’ve got an Intel HD 530 GPU with no eDRAM. These processors are significantly cheaper than the Iris Pro versions and their processor cores may be able to run faster for longer since they’re not sharing a CPU package with a big GPU and a bunch of eDRAM. You just have to live with the lower graphics performance (and lack of extra cache memory) that comes with it. HK-series Only one CPU belongs to this family: The Core i7-6820HK. It’s an unclocked, overclockable quad-core laptop processor. If you’re the kind of person who thinks that sounds like a good idea, go to town. H-series Another rare suffix which as of this writing applies only to the Core i3-6100H. This denotes a dual-core CPU with Hyperthreading and a 35W TDP, considerably higher than the more common U-series. The extra TDP headroom will let it run at its max speed of 2.7GHz for longer periods of time, and it makes room for an HD 530 GPU, slightly better than the HD 520 GPU more common in the U-series. The H series seems to be a replacement for the bygone M-series, which used to be Intel’s mainstream dual-core laptop chips until the U-series improved enough to totally replace them. Low-power and low-end: Core M and Braswell (respectively) Enlarge / Skinny, fanless laptops like Apple's MacBook use Core M CPUs instead. Andrew Cunningham Core M These get their own category because they're a special case. As of Skylake, Intel has three Core M brands: Core m3, m5, and m7. All of them are dual-core CPUs with Hyperthreading, Turbo Boost, 4MB of cache, and an Intel HD 515 GPU. From a user’s perspective, the only real difference is peak clock speed, which ranges from 2.2GHz for the Core m3 up to 3.1GHz for the Core m7. These processors have rather low base frequencies and rely on Turbo Boost to keep systems feeling responsive, so they’ll be more prone to throttling than U-series chips or others with higher TDPs (Core M is designed to fit into a 4.5W TDP, less than a third of a U-series chip). In exchange, systems that use Core M are often totally fanless, which is easy to get used to if you’re coming from a standard Windows laptop with an overactive fan. The Skylake version of Core M isn’t bad, but at this point we’d recommend against buying the older Broadwell version of Core M (which is just sold as Core M, not Core m3/m5/m7). Its performance was less consistent and more compromised, and in our testing the Skylake version has been a significant step up in every way. N3000-series Celerons and Pentiums These chips are sold under the Celeron and Pentium branding but they use a different CPU architecture called “Airmont.” These chips (also referred to as “Braswell” when you’re talking about the entire chip instead of just the CPU) have lower CPU and GPU performance, and are generally found only in entry-level PCs and Chromebooks. These Celerons and Pentiums aren’t all that bad in and of themselves, but the unfortunate fact is that they’re usually paired with slower storage and paltry amounts of RAM. It’s not my fault this is so confusing The days when Intel processors were differentiated mostly by clock speed are long past, and as Intel has gotten more serious about GPUs the integrated graphics chip the processors come with has just become another piece of the puzzle. And we didn’t even touch the Xeon chips that you can consider if you’re really looking at a high-end workstation. If you’re building a desktop, at least, things are pretty clean. If you want a quad-core, get the best Core i5 you can afford; if you’re on a budget, the dual-core Pentium chips give you solid value for the money. Laptops are harder to figure out, but as long as you keep your eyes open and figure out the model number you ought to be able to avoid unpleasant surprises. Source: arstechnica
-
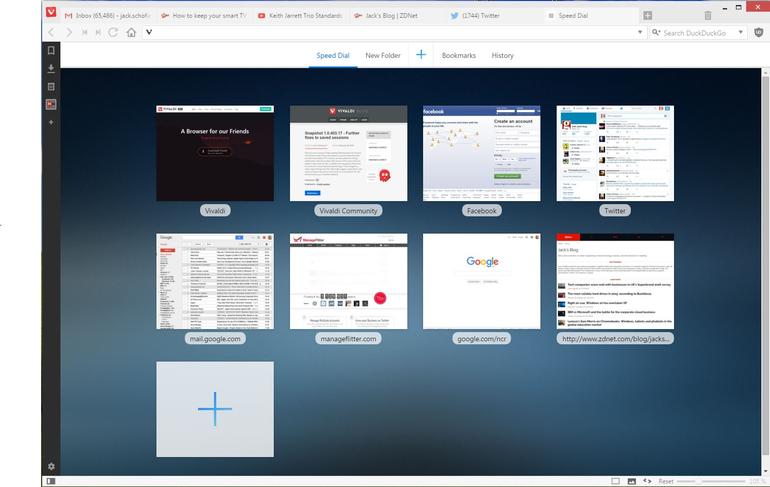
The Vivaldi browser now offers a Google-free replacement for Chrome on Microsoft Windows, Mac OS X and Linux. Switching requires very little effort because, like several rivals, it's based on open source Chromium code, and renders websites exactly like Chrome. Vivaldi even runs extensions from the Chrome Web Store, including uBlock Origin and TinEye Reverse Image Search. (I've not had problems, but test your must-haves before switching.) However, the long-term aim is to deliver a browser that does what its users need, not one that needs overloading with extensions that slug the performance. Why would anyone want to switch away from Chrome? Generally, there are three reasons. First, there's a dislike of Google's surveillance-based business model. Second, Chrome is aimed at the mass market, whereas Vivaldi is aimed at "power users". Third, there's Chrome's avaricious consumption of PC resources. The days when Chrome was "lean and mean" are long gone. Vivaldi solves the first two problems, but not the third. If anything, it consumes slightly more resources than Chrome. The extra features come with a price. While I switched my main browser from Chrome to Mozilla Firefox a couple of years ago, I still used Chrome every day. However, that's changed since Vivaldi went beta late last year, and it's now in beta 2. Yes, it still has a few bugs, and it's missing some planned features. However, for Windows users, it is now good enough for full time use for most purposes. (I haven't tested the other versions.) The main controls are, by default, distributed around the browser: 1) The V in the top left has a drop-down menu with access to File, Edit, View, Tools and other commands. 2) Like Firefox, Vivaldi has a separate search box that makes it easy to use a different search engine by picking one from a drop-down menu. 3) A vertical black toolbar on the left provides access to bookmarks, downloads, and notes (with mail and contacts to come) via slide-out panels. You can drag the panel as far as you like across the screen to view two web pages side by side. 4) The cogwheel in the bottom left provides fast access to settings. 5) A small cluster of controls at the right-hand end of the status bar provide various page actions, such as toggling images, and magnification via a slider. 6) A waste bin the top right holds the tabs you've closed. If you regret closing one, you can easily retrieve it. Page Actions menu However, you can do most things by hitting F2 for a searchable quick-list of commands, and by using the Opera-style Speed Dial tabs. The trick is to use New Folder to create several sets of Speed Dial tabs, one for each area of interest. If you're the sort of person who prefers to use keyboard shortcuts, there's a huge selection. Interesting ones include Shift-Esc for the task manager, and Ctrl-F11, which removes the browser chrome (including tabs etc) without making the image full screen. Either way, the Vivaldi interface - which is written in JavaScript and other web technologies - is generally easy to customize. For example, you can have your tabs at either side or at the bottom, and you can move the vertical black bar from the left to the right hand side. On the downside, both Vivaldi and Chrome still have limited tab handling compared to Firefox, and the more tabs you open, the tinier each tab becomes. Hovering over a tab produces a small page preview - or, if you're tab-stacking, several small page previews - which helps. Otherwise, there's a list of pages (under Window), or you can use the mouse-wheel to scroll rapidly through tabs. Vivaldi is not planning on world domination, and Jon von Teczchner says he only needs a few million users to break even, with a search-based income of roughly $1 per user per year. There are more than enough geeks to make that modest aim a reality. Vivaldi should also be able to attract the people who still use Opera 12 for its tab stacks, custom keyboard shortcuts, mouse gestures and note-taking, all of which Vivaldi has. Launching a new browser sounds like a tough job. But in von Teczchner, Vivaldi has a CEO who not only knows what he's doing, but has done it before. Source: zdnet
-

The Good Morning, Afternoon or Evening Thread
allheart55 Cindy E replied to AWS's topic in Tech Help and Discussions
I was just looking at them on Amazon. They are a little pricey, aren't they? -

The Good Morning, Afternoon or Evening Thread
allheart55 Cindy E replied to AWS's topic in Tech Help and Discussions
The Aladdin Lamp sounds like an interesting idea, Bill. I will definitely check it out. We have been lucky so far this year but the past two winters we didn't fare as well. -
I've actually found that Skype, in a pinch is great for large files. Dougie and I use it frequently. It sounds to me as if OSX is better than Windows with a lot of things. I have been thinking about purchasing a MacBook a lot lately.
- 3 replies
-
- mnetwork
- network speed test
-
(and 3 more)
Tagged with:
-
Millions of people do their banking online through their computers, laptops or tablets and find their experience to be quick, easy and convenient. In addition, according to a study last year by the Federal Reserve, 52% of smartphone owners use their smartphones for mobile banking, which is not surprising since so many of us, particularly younger Americans, do much of our financial transactions of all kinds on our smartphones. But how safe are we when doing online or mobile banking? The bad news is that we can be quite susceptible to having our identities stolen and our bank accounts emptied when doing online or mobile banking. The good news is, however, that how susceptible we are to this danger is largely within our control. Most banks require a person to enter a user name and a password when banking online or by using a smartphone. Scam artists, the only criminals we refer to as artists, can be quite adept at getting you to provide your user name and password to them. Using a knowledge of psychology that would have made Sigmund Freud envious, they use phishing techniques, most commonly through emails or text messages that trick you into either providing this information directly in response to the email or text message or luring you into clicking on links containing keystroke logging malware that can steal your user name and password from your electronic device along with all of the other information stored on your device. These phishing emails are often designed to make you think that there is an emergency, such as a security breach of your bank account requiring you to provide confirming information. Many times the emails are quite poorly designed, for instance carrying a salutation of “Dear Customer,” and coming from an address with no relationship to your bank and containing poor grammar. However, other times, through a technique called “spear phishing,” the scammer uses personal information about you that may have been gathered through hacking of the computers of companies with which you do business to make the email or text message look more legitimate. It will be directed to you by name, the email address from which it is sent may appear to legitimately be that of the bank with which you do business, the grammar is good and it may even carry the logo of your bank, which is easy to forge, on the email. Spear phishing can be hard to recognize which is why it has been at the heart of many of the major cyberattacks we have seen in recent years ranging from the data breach at the OPM to the recent ransomware attack at the Hollywood Presbyterian Medical Center. Once the criminal has your user name and your password, he or she can access your account at many banks and steal your money. So what can you do to protect yourself from this danger? Remember my motto, “trust me, you can’t trust anyone.” Never provide personal information in response to a phone call, text message or email you receive until you have independently confirmed that the request for information is legitimate. In addition, it is a good idea to have anti-phishing security software installed on all of your devices. As an additional security measure, some banks require that you provide answers to security questions in addition to merely providing your user name and password in order to access your bank account online or through your smartphone. This provides an additional measure of protection, however, in many instances, the security questions are little more than your mother’s maiden name, which is simple for an identity thief to find online. Even what would appear to be more difficult security questions such as the name of your pet or your favorite sports team, can be easy for an identity thief to determine merely by looking at what you post online through social media. The first way to make security questions more secure is to limit the amount of personal information you provide online through social media. However, perhaps the best way to dramatically improve the strength of your security question is to use a nonsensical answer when you set up the account. For instance, if the security question is what is your mother’s maiden name, make your answer something ludicrous, such as “grapefruit.” This is an answer that no identity thief will ever find and it is silly enough to make it easy to remember. For increased security, some banks, such as Bank of America and Chase even offer dual factor authentication by which when you enter your user name and password to access your account, a random password is sent to your smartphone that must be used to gain access your account. This seems like it would be foolproof, but never underestimate the power of a fool. Scammers are now calling their victim’s mobile service providers posing as their victim and telling the provider that their victim’s phone has been damaged, lost or replaced and that they need to reactivate their mobile number to a new SIM card in a phone controlled by the criminal. A SIM card is an integrated circuit that stores information used to authenticate subscribers on smartphones. Once the SIM cards have been swapped, when the criminal uses the already stolen user name and password to begin the access to the victim’s account, when the bank sends the one time password to access the account, it is sent to the new SIM card in the phone of the criminal. Better use of security questions before service providers will change SIM cards can help to reduce this risk. Online banking on your computer or smartphone can be safe if you take the right precautions. As with so many things, the best place to find a helping hand is at the end of your own arm. Source: usatoday
-
- banking online
- mobile banking
-
(and 1 more)
Tagged with:
-
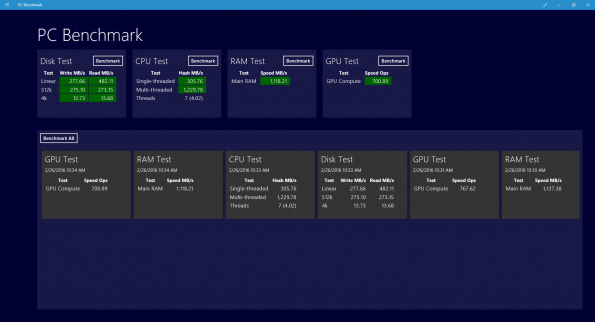
mNetwork This app helps you monitor the upload and download data totals on your systems connected network card. Although not a perfect replacement for measuring tools from your ISP this can give you a good estimate of how much data you are using. Download mNetwork (PC) Reader Instead of installing the bloated Adobe Reader just install this Windows Store app for quick looks into not only your PDF files but also XPS and TIFF ones. Download Reader (PC) Network Speed Test I think everyone who connects to the Internet wants to measure their connections speed. You can either go to a website full of ads or you can use this app to get a quick check of your current network speed. It also maintains a history of your tests which can be useful when you are on the phone with your ISP. Although it is not a universal app there are versions available for both PC and Mobile. Download Network Speed Test (PC) Download Network Speed Test (Mobile) Remote Desktop If you manage remotely connected computers on your network or access remote services on your work servers then this app is a must have. It is a universal app and available on both PC and Mobile. Download Remote Desktop (PC and Mobile) Bonus: You can also test new features for this app by installing the Microsoft Remote Desktop Preview (PC). Features get tested in this preview and are eventually migrated to the Remote Desktop app. PC Benchmark This app will give you a quick snapshot of the performance for your Disk, CPU, RAM and GPU. It keeps a history of your benchmarking as well. Download PC Benchmark (PC) Source: winsupersite
- 3 replies
-
- mnetwork
- network speed test
-
(and 3 more)
Tagged with:
-
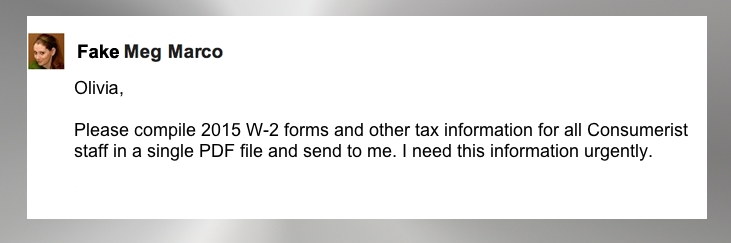
We know that the above email couldn’t be real for a few reasons: Consumerist doesn’t have our own payroll department, and Olivia is a cat. Yet there’s a new variation of the now-classic CEO scam, where someone impersonates your boss over email and requests a massive wire transfer. In this version, the boss impersonator does exactly what Fake Meg does above: they request a file of employee W-2 forms enabling them to commit identity theft, including filing fraudulent tax returns. Krebs on Security reports that this variant showed up in the mailbox of someone in the accounting department of, appropriately enough, a company that provides training on security awareness. Fortunately, the appropriate staff members were well-trained enough to be suspicious, and knew not to send such sensitive documents by email in the first place, and knew that the email itself looked rather fishy. The emailer wasn’t connected with the company and definitely wasn’t the CEO. “Imagine if we would have sent off those W-2’s!” the real CEO told Brian Krebs. “It would have opened up our employees to identity theft because the W-2’s have their full name, address, wages and Social Security number.” Phishers Spoof CEO, Request W2 Forms [Krebs on Security] Source: consumerist
-
- fraudulent
- identity theft
-
(and 2 more)
Tagged with:
-
On Windows, there’s an ever-growing number of utilities designed for cleaning up your directories and thereby maximizing hard drive space. Some even intend on optimizing memory and processing speeds along the way. While Microsoft doesn’t typically acknowledge these types of cleanup software, it is starting to call out some of the more deceptive tools disguised as cleaner/system-tuner resources. While being advertised as enhancements to your PC’s performance, the reality is that some of these programs are more likely to eat away at your computer speeds. Alternatively, some of these apps even charge money after revealing an extensive list of hindrances on your PC’s efficiency. Now Microsoft is saying that any programs guilty of these crimes will be marked as “unwanted software,” meaning that — assuming you’re on Windows 10 — the company’s built-in Windows Defender will automatically remove them from your downloads. This is according to a post published on the Malware Protection Center blog, on which Microsoft clarifies that the aforementioned subset of these programs leaves its customers with “arbitrary and fear-based” purchasing decisions. More specifically, it’s widely known that some of these programs detect a Windows system file variant, prefetch (.pf) files, as malware. In reality, though, these files are conceived by the operating system itself to reduce the load times of certain apps. Rather than improving on performance as advertised, these programs can actually be quite detrimental to your computer’s health. The way this works for Windows Defender is remarkably straightforward. By developing an objective criteria for how malware programs “back up their claims, so that you have the ability to assess what the program found and deems to be errors,” users can determined if they would “like to take the program’s recommended actions.” Essentially, this means that if the programs meddle with your system files, absent a necessary explanation for doing so, Defender will strike back with an equally terminal blow. Source: yahootech
-
- cleanup software
- optimizing
-
(and 2 more)
Tagged with:
-

The Good Morning, Afternoon or Evening Thread
allheart55 Cindy E replied to AWS's topic in Tech Help and Discussions
Wow! I am going to stop complaining about our summer heat here. -
This is happening more and more lately for a lot of people. Microsoft needs to fix this or many will revert back to Win 7 or 8.
-

The Good Morning, Afternoon or Evening Thread
allheart55 Cindy E replied to AWS's topic in Tech Help and Discussions
That is good news! We had snow last week and today it is 54 degrees. This is the weirdest winter we have ever had. -
Want to make a purchase online? Say cheese! MasterCard (MA) is rolling out new technology that would allow any online shopper to authenticate their identity with the super high-tech power of...a selfie. Here’s how it works: When you shop online using a MasterCard-issued credit card, the merchant will ping you with a text and ask you to verify your identity through MasterCard Identity Check (you’ll have to download the app on your phone first). From there, you can either pose for a photo or use your fingerprint to verify your identity. If you go for the photo option, the app will prompt you to blink once or twice. And that blink is everything. It’s how the app prevents hackers from being able to break into a user’s account simply by using a photo. The technology, which MasterCard has been testing in the Netherlands for several months, is due to roll out in the U.S. later this year. MasterCard executive Bob Reany, who heads up the company’s authentication efforts, said with any luck no one will be using standard issue passwords and PINs a few years from now. “People hate passwords because passwords are dangerous and they’re frequently compromised,” Reany told Yahoo Finance. “I’m a busy person. I can’t remember 40 passwords.” Most cyber security experts have long decried use of old-school passwords, which are easily hackable (“12345” and “password” have been the most commonly used passwords in the U.S. for several years running). Identity theft is still the fastest growing crime in this country. Of the 16.4 million Americans who were the victim of ID theft in 2014, more than half experienced credit card fraud. You rarely need to verify your identity when you use a credit card online, which makes it a breeze to shop but also makes it easier for fraudsters to steal your credit card or bank info and make purchases. Adding an additional verification step, while it might seem like a nuisance, is a way to thwart that, Reany says. Credit card issuers — and just about every other business in the world — have been trying to come up with a viable solution for years. Some require fingerprint authentication to complete a purchase. Others use two-step verification, which prompts users to punch in a unique code sent to their phone by text message. Wells Fargo, HSBC, and Barclays are among several institutions experimenting with voice recognition tools. MasterCard has also been testing heartbeat verification using the Nymi band, which is able to track the user’s unique heartbeat rhythms. MasterCard Identity Check will roll out in mid-2016 in the U.S. for both Android and iPhone users. Source: yahoonews
- 3 replies
-
- app
- master card
-
(and 2 more)
Tagged with:
-
I'll take a look.:D