-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
In the last few days, legislators in both the House and Senate have once again pushed the issue of nuisance pre-recorded, auto-dialed robocalls back into the spotlight — urging telecom providers to give customers more tools for blocking these calls, and trying to roll back the government’s ability to abuse robocalls for its own debt-collection purposes. “If robocalls were a disease, they’d be a national epidemic,” said Sen. Chuck Schumer (NY) at a press conference on Sunday to discuss the need for mobile and landline providers to give customers more options. “We’d have the best and brightest working to combat the scourge.” The senator noted that that Federal Trade Commission, which oversees the Do Not Call Registry, receives more than 3.5 million complaints from Americans every year. [Ed. Note: That is the total number of complaints for all alleged Do Not Call violations/ According to FTC data, robocalls account for around two-thirds of these complaints.] “If there are 3.5 million complaint calls, you can imagine” how big the problem really is, pointed out Schumer, who confessed that not even he has taken the time to complain about the robocalls that he gets. “I’ve gotten them from financial institutions, from stores, from so many things… It drives you crazy, especially when you’re having a nice dinner with your family” Schumer acknowledged that robocalls and complaints did decrease during that brief period about 10 years ago when the Do Not Call Registry was finally up and running, and most people were still primarily using their landlines. But in the years since, new technology has made it easier for robocallers to make huge numbers of calls at once, while also making it more difficult to track down their identity. While there are millions of numbers on the Do Not Call list, and most non-emergency robocalls to cellphones are illegal without the recipient giving their express permission in advance, many of the most pernicious robocallers simply don’t care because they are not legitimate businesses. Instead, they are scammers trying to commit identity theft or fraud. “Stop the robocalls, you can stop the scammers too,” said Schumer, who pointed to the existence of technology like Nomorobo, which Time Warner Cable recently added to its phone service, that could be deployed on a larger scale to help consumers block these unwanted, and often illegal calls. “We’re calling on all major landline and mobile carriers to make robocall-blocking technology available to all consumers,” said Schumer. Beyond that, once these tools are available, the telecom providers need to alert their customers that they have the tools. Schumer is also asking the FTC to put pressure on manufacturers to integrate robocall blocking tech in their devices. “I will introduce legislation in the Senate if the companies don’t do it on their own,” said the senator. “There’s a rotten game of phones going on and it’s giving America a giant headache.” “Nothing drives phone customers more crazy than robocalls that ring day and night,” said Chuck Bell, our colleague at Consumers Union, who joined Sen. Schumer for yesterday’s press conference. “Over half a million Americans have joined Consumers Union’s End Robocalls campaign calling on AT&T, Verizon, and CenturyLink to offer free call-blocking tools to stop unwanted calls. It’s time for the phone companies to take action and provide their customers with the relief they want and deserve.” Unfortunately, while Schumer and other lawmakers combat nuisance phone calls, the federal government itself is poised to become one of the biggest robocallers. Last fall, with a government shutdown looming, a rider attached to a must-pass budget bill created a loophole in the Communications Act that exempts the federal debt collection efforts from laws that severely limit the use of robocalls. Thus, anyone who misses a federal student loan payment, has a federal tax issue, a problem with their home loan through the FHA, or any other debt to the feds, may soon be receiving the very kinds of nuisance calls Schumer is trying to stop — and they’ll be completely legal. The FCC is, as directed by that rider, currently drafting rules for the government to follow. The deadline for those guidelines is this summer. Immediately after the rider was passed, Sen. Ed Markey (MA) introduced the HANGUP Act, which would roll back that revision to the Communications Act and close the robocall loophole. Even though that legislation quickly gathered 16 co-sponsors, and the backing of the attorneys general from 25 states — and even though robocalls is one of the few issues that is not currently a partisan issue — the bill has been sitting idle in committee since being introduced. In hopes of lighting a spark in the House, Representatives Tammy Duckworth (IL) Anna Eshoo (CA) introduced the House version of the HANGUP Act, virtually identical to Markey’s Senate bill. “For more than 25 years, Congress protected student loan borrowers—and all consumers—from being harassed by debt collectors robocalling their cell phones,” said Congresswoman Duckworth. “I’m disappointed these protections were rolled back behind closed doors, but I’m looking forward to working with Congresswoman Eshoo to restore them.” What’s particularly dubious about the debt-collection robocall loophole is that the government’s own budget analysis predicts that this exemption will not result in the government collecting any significant amount of debts. In fact, that analysis say the government could lose as much as $500,000 a year. “The exemption allows private debt collectors to conduct robocalls and send texts to mobile phones for debt owed or guaranteed by the federal government,” said Rep. Eshoo. “The HANGUP Act restores critical protections for consumers by establishing a statutory roadblock to unwanted robocalls and texts.” Source: consumerist
- 5 replies
-
- auto-dialed
- debt-collection
-
(and 2 more)
Tagged with:
-

Color Changing Car Paint
allheart55 Cindy E replied to starbuck's topic in Tech Help and Discussions
This is awesome! I love it. :thumbsup: -
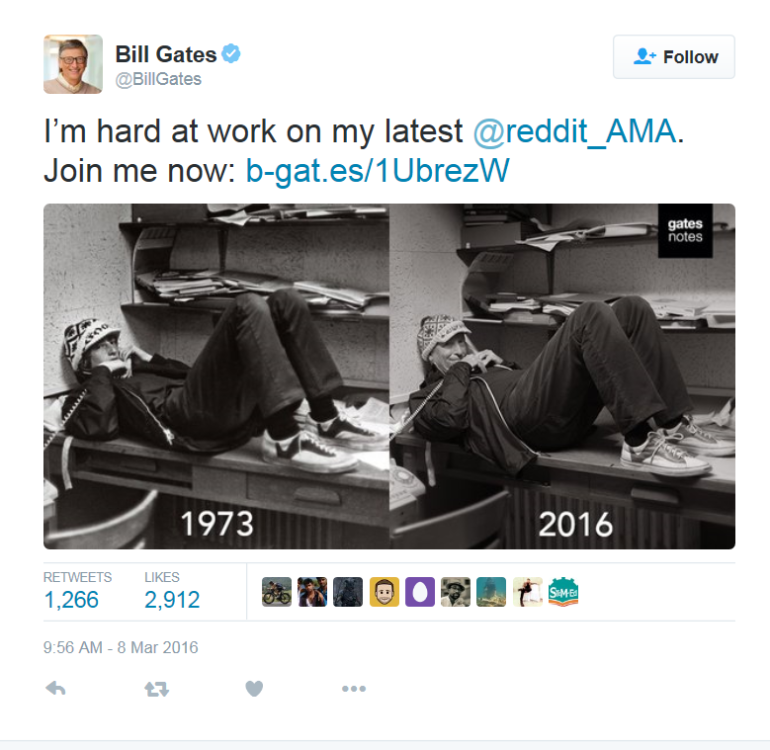
Bill Gates is starting another Ask Me Anything session on Reddit, but as any regular AMA visitor knows, he first needs to verify his identity with a photo. Usually that means holding up a sheet of paper with your name and the date on it, but Gates went for something far more interesting this time: he restaged an extremely chill photo of himself in high school, laying back on a desk while taking a call. It's a wonderfully faithful recreation that has Gates looking... I wouldn't exactly say cool, but as cool as you could hope over 40 years later. Images credit: The Gates Notes. The AMA is just getting started, and already Gates has responded to a question about his views on the iPhone encryption case. His answer is pretty down the center, saying that both sides of the argument have valid concerns, but never quite making a firm commitment to defend either one. Gates first weighed in on the issue a couple weeks ago, initially saying that Apple should help unlock the phone and later clarifying that his remarks had been misrepresented, that he believed there needed to be a "balance" between security and the government's ability to access information for law enforcement purposes. Source: theverge
-

New OS X ransomware discovered in the wild
allheart55 Cindy E replied to starbuck's topic in Tech Help and Discussions
Oh, this is not good. Wait until Bob and Tony see this one.....:real_anger: -
The majority of teenagers alive today weren’t alive in the 90s, meaning the oldest version of Windows they’re likely to be familiar with is Windows XP. If that tidbit makes you feel old, you might not want to watch the latest React video from Fine Brothers Entertainment, in which a bunch of teenagers are exposed to the wonders of mid-90s computing and Windows 95 for the first time in their lives. They’re not impressed. It starts with first impressions. “The fact that the monitor is bigger than the actual computer itself says a lot” said Daniel, 17 years old, who is young enough to only have vague memories of monitors and TVs that aren’t flat. “I’ve no clue what year this is from, but I feel like it was before the year I was born,” said Geneva, age 18, after seeing the mid-90s Dell. Her math checks out. The design flaws we all got used to are evident right away. When asked to turn on the computer, everyone hit the big button on the monitor and waited, something we all probably remember doing at some point. When the computer was turned on, the reactions kept coming. “I don’t think I’ve ever heard a computer make these sounds before in my life,” said Morgan, age 19, making anyone who felt nostalgic upon hearing the floppy drive click instantly feel 10 years older. Then the teens waited for the BIOS screen to go away. “This is taking a while,” said Karan Brar, reminding the entire planet what life was like back in ancient times when computers took five minutes to start up and Pterodactylus savaged our cattle. Things don’t get much better when the operating system’s boot screen is revealed. “95, as in, like, 1995?” asked Alicia, age 16, who has no memories of the 90s but will be able to vote in just two years. Then the operating system finally booted. “Everything looks so dull and ancient,” said Brar. “It seems more rough, the edges are more sharp, it’s a little more impersonal,” said Nora, age 18, who judging by that comment might have a future as a graphic designer. But perhaps the hardest thing to understand for the teens was the lack of wireless connectivity. “How do you get on the Internet if there’s no Wi-Fi?” asked Alicia, as though the question itself were nonsense. When the produced tried to explain dial-up, things got even more confused. “You’d have to use your phone to go on Internet,” one teen said, while actually miming a smartphone in her hand. It shows just how much the meaning of the word “phone” has changed in the course of a generation. The process of connecting to dial-up did not impress anyone, either. “God this is such a pain in the ass,” said Daniel, age 17. It was, Daniel. It was. It’s easy to judge teenagers for not knowing their history, but realistically it’s not their fault. Anyone reading this likely never had to crank their car in order to start it, and probably wouldn’t know where to start if presented with a vehicle requiring that. “It’s not my fault I was born after this,” said Nora, age 18. She’s right, of course: time marchers forward, and kids have no control over when they’re born. We think this whole thing is a fascinating example of how computer and OS design has evolved over the years. Source: yahoo
-

ESET Online Scanner Vs Nod32 AntiVirus Pro?
allheart55 Cindy E replied to N3's topic in Tech Help and Discussions
I use Nod32 and Malwarebytes on each one of my computers. IMHO, Nod32 is the best of all the anti-virus programs that I have used. As Pete says, it has the advantage of having AntiVirus, AntiSpyware, Anti-Phishing, Exploit Blocker etc..... -
When you think of Microsoft, what product first comes to mind? Windows, you say? How quaint. Yes, you’re probably reading this on a Windows-based PC, but Windows itself matters less and less to Microsoft. Ed Bott recently broke down Microsoft’s latest 10-Q, its quarterly report to the Securities and Exchange Commission. What he found out about how Microsoft is making money these days is very interesting. Do you think that Windows is number one in bringing in the cash? It’s a reasonable assumption. Windows for years was the undisputed cash cow for Microsoft, and the company just rolled out a new version, Windows 10, that has been deemed a great improvement over its immediate predecessor, Windows 8. But the assumption is wrong. The biggest cash generator for Microsoft in the fourth quarter of 2015 was its server and cloud divisions. So Windows must have been number two, right? No, that was gaming. There are a lot more Xboxes out there than you might think, and don’t forget that Microsoft recently bought Mojang, makers of Minecraft. Vista and then Windows 8.x, has fallen to the likes of the Mac or Linux. Windows remains the most popular desktop operating system. Microsoft kept trying — and failing — to get anyone to use Windows Phone. It was desperate to get a foothold in the mobile market, because it knows that the desktop has a limited future. But Microsoft is finally facing the hard truth: Windows Phone is a failure. So the boys from Redmond are embracing Android and iOS. Recently, Microsoft bought Xamarin — a mistake, in my book — so its developers could easily port .Net Framework and C# programs to Android smartphones and iPhones. Microsoft hasn’t been waiting around for this plan to work. Internally, it has been exporting its business-oriented software, including the entire Office suite, to Android. What does this have to with the decline of Windows? Everything. Office is becoming a cloud program, not a desktop program. Those server and cloud numbers leading Microsoft’s profit train? They’re increasingly built on Azure cloud services, not stand-alone Server 2012 sales. You see, Microsoft is well on its way to becoming a cloud and services company and not a desktop company. To quote my longtime writing buddy Preston Gralla, “Microsoft’s future is all about the cloud, so much so that one day Windows may become an afterthought.” I only disagree on one point: His use of the word “may.” Microsoft has done the numbers — Windows revenue down 5% in the last quarter, despite Windows 10, while Microsoft’s cloud division saw its revenue grow by 5%. Azure sales were up 140% year over year. As CEO Satya Nadella said after the quarterly report: “The enterprise cloud opportunity is massive. It’s larger than any market we’ve ever participated in.” Yes, he meant it, and yes, he meant bigger than Windows. This marks a transformation, not just for Microsoft and Windows, but for all of personal computing as well. We’re used to thinking even now of the PC as being computing’s core. It’s not anymore. In 1976, Gary Kildall’s CP/M operating system and the first floppy-drive-based computers shifted computing power from IT departments and mainframes to individual users and PCs. In 2016, we’re not just seeing Windows decline, we’re seeing computing power move from individuals to the mainframe’s successor, the cloud. We’re in for interesting times. Source: computerworld
-
- microsoft
- profit train
-
(and 1 more)
Tagged with:
-
Project Fi is ditching the invite system. 10 months after Google unveiled its own mobile network, which lets consumers pay only for the amount of data they use each month, the company is opening access to everyone inside the United States. "With Project Fi, we deliver fast wireless service with the flexibility to use it where you want (even internationally) and a monthly bill that’s simple and easy to understand," wrote Simon Arscott, Fi's product manager, in a blog post. "Today, we’re excited to be exiting our invitation-only mode and opening up Project Fi so that people across the U.S. can now sign up for service without having to wait in-line for an invite." For the next month, Google is discounting the Nexus 5X down to $199 as an inexpensive way to get started with Fi, which only works with Nexus smartphones. Project Fi connects to the cellular networks of both T-Mobile and Sprint, switching between the two to offer customers the best possible coverage. Google is also pushing Wi-Fi and public hotspots in a big way with Fi; over 50 percent of current customers connect to public hotspots using Fi's "Wi-Fi Assistant" on a weekly basis. As for cellular data, Google's Project Fi subscribers are impressively lean in their usage, averaging 1.6GB of data each month. Source: theverge
-
- project fi
-
(and 1 more)
Tagged with:
-
Mozilla has put the YouTube Unblocker add-on on its “blocklist”, as it has been discovered that it was changing users’ security settings and covertly downloading and installing an additional, malicious extension that injects ads in pages visited by users. The popularity of YouTube Unblocker was due to it allowing users to view YouTube videos blocked in their country. The add-on used to be offered for download on the organization’s official portal for Firefox extensions and themes, but no more: The various comments in the discussion about the bug that has been started on Mozilla’s bug tracker a few days ago showed that the developers of YouTube Unblocker have been repeatedly trying to bundle it with adware through the years. Mozilla tried to stop this behaviour by forcing the developers to put the files the add-on was allowed to download on a whitelist, which was to be checked by Mozilla. But the developers found a way to bypass that protection, as well as the protection offered by Firefox’s code signing security feature. Unfortunately, the same thing can be (and apparently has been) done by other developers. “The WebExtensions API is meant to have stronger checks and boundaries that should prevent most if not all situations like this one,” explained Jorge Villalobos, Add-ons Developer Relations Lead at Mozilla, but noted that the current add-ons framework gives add-ons a lot of power, which can lead to problems like this. “This is why we have code reviews for all add-ons submitted to AMO (addons.mozilla.org). In this particular case, the review process failed to catch the bad code.” Perhaps because, as reported, the YouTube Unblocker would not always download the second add-on. Mozilla putting YouTube Unblocker and the malicious add-on on its blocklist means that they will be disabled for all users and will be prevented from running automatically. The blocklist will also prevent the add-ons to be installed in the first place, as they can still be downloaded from the developers’ website. Users who have already installed the offending extension(s) may also want to check this guide on what to do to clear their browsers of them. Source: helpnet
-
A South Florida scuba diver was taken on a terrifying ride through a nuclear power plant's intake pipe that he feared would end in his watery death. What started as a scuba and lobster-diving trip with family and friends became what felt like a ride to hell for Christopher Le Cun last summer when the 30-year-old swam up to what he says was an improperly marked intake pipe to a nuclear plant in Port St. Lucie. For some five minutes back in July, Le Cun was pulled along at seven feet per second through a pitch black, barnacle-encrusted pipe with no idea what lay at the other end. They were five minutes Le Cun said will forever be imprinted on his mind. "We were looking for lobster when we came across a big structure," Le Cun, a Navy veteran who's been diving since age 12, told InsideEdition.com. Watch: Cop Helps Girl, 2, Put On Pants After She Called 911: 'My Heart Went Out to Her' Le Cun and a friend put on their dive gear and left behind Le Cun's then-pregnant wife, two children and a friend's child. As they investigated what he said looked like "three underwater buildings," Le Cun said the current began to pick up. He didn't think anything of it, at first. Posted by Christopher Le Cun on Sunday, June 1, 2014 "Then WHOA," he said. "Within a blink of an eye I'm in a washing machine, tumbling and trying to check my air, hold onto my regulator." As the gravity of what was happening began to dawn on Le Cun, he said he feared the worst. As if in a horror film, he pictured a turbine waiting to chop him to bits at the end. Le Cun said he even considered pulling the regulator out of his mouth and ending his own life before the inevitable came. "But then I though, I got a family. You're gonna have to kill me. I'm thinking about my wife, who was pregnant with our third child at the time," he recalled. Then, Le Cun said he saw what looked at first like a match in the distance. Read: 7-Year-Old Left Speechless When Marine Brother Surprises Him With Early Homecoming "The tiniest light you've ever seen," he said. And finally, "it spits me out. There are huge fish. It almost felt like you're in heaven." Le Cun swam to the surface and discovered he was in a reservoir for sea water used to cool the nuclear reactors. A plant employee spotted him and couldn't believe his eyes. "The staff couldn't believe it, they wanted to take pictures with me," he said. Le Cun borrowed a phone and called his wife. "I'm alive," he told her, as she wept with her children and friends. Le Cun's friend, Robert Blake, told WPTV he saw his friend get sucked into the pipe and all but told the others that Le Cun was dead after watching him get sucked in "like a wet noodle." Now Blake and Le Cun are arguing that there was no warning of the dangers at the intake pipe and that Florida Power and Light failed to properly mark the site. Le Cun, who says he's still traumatized by the incident and still isn't comfortable scuba diving, is now suing the company. Florida Power and LIght has declined to comment on the pending legislation but released this statement: "Nothing is more important safety at our St. Lucie Nuclear Power Plants, which is a reason that we have a protective over the intake piping. The diver intentionally swam into one of the intake pipes after bypassing a piece of equipment to minimize the entry of objects." Meanwhile, Le Cun says he's got an entirely new outlook on life as he spends all the precious time he can with his wife and children. "I am absolutely lucky to be alive, I have whole new perspective on life," he said. Source: yahoo
- 1 reply
-
- christopher le cun
- lobster-diving
-
(and 2 more)
Tagged with:
-
-
Not I but I was just checking it out. There are less expensive plans available.
- 4 replies
-
- emails
- outlook 2016
-
(and 1 more)
Tagged with:
-
Earlier today I wrote about a recently discovered issue between Outlook 2016 and POP3 based email accounts that can cause you to either lose emails on some devices or get duplicates. This got me thinking about how long the POP3 aka Post Office Protocol has been around. The original version of POP was developed in 1984 and POP3 was established in 1988 – if you are counting that is nearly 30 years ago for POP3. The POP standard was a simple one and was easy to implement and basically downloaded content from your email server to your local account. It had no support for folders or any type of storage structure on the server although you could manually organize mail on your local device if your client supported it. There was usually a setting in a POP3 mail client that you could set to leave a copy of the emails on the server after downloading them locally and that could allow you to access the total email store on different devices. The successor to POP is widely considered to be the IMAP or Internet Message Access Protocol but it was also devised by its inventor Mark Crispin in the mid 80's right around the same time as POP. IMAP introduced many more features that allowed you to work in either an offline or online mode, have multiple client access to the same mailbox concurrently, allowed server side searches and supported a folder storage hierarchy on the server. Today we still have systems that support POP3 as well as IMAP, in fact most of the popular web based email providers support both of those still. Services like Hosted Exchange and Office 365, the latter which is now the backbone of Outlook.com, provide even more robust connectivity, accessibility and flexibility for when and where you access your email. My family has been using Hosted Exchange, sometimes referred to as Exchange Online, for our email for over three years now and it is the best $96 dollars I spend each year. It gives us two accounts with 50GB of email storage each and has really made a difference in our email experience. The biggest bonus is that all of it is accessible across all of our devices from the desktop, laptops, tablets and phones. No more moving Outlook PST files between desktops and laptops just to maintain access to all of our current and historical email. I know it would have been possible to have a similar option at no cost and with less storage using Outlook.com or other web based services but this hosted email option also gave me the ability to use our family domain to personalize each account. So – back to the original premise of this article – three reasons to move from POP3 based email accounts to something hosted in the cloud. Number 1 – Portability Since hosted accounts keep the emails on the server by default I can access that account from multiple devices. Read/Unread states are also updated on the server side so emails accessed on other devices that were previously read do not show up as new in other locations. Number 2 – Storage The amount of storage will vary based on the service and options for a purchased service but it allows you to store email messages on the server and in a folder hierarchy that can be accessed from any device that supports that account. I used to store all of my historical emails in a local PST file but always had to remember to back it up and move it out of harm’s way if I needed to reformat or reset that machine. Also, PST’s are not supported across as network so it meant I needed to move these storage files manually between devices to make sure I had the latest version on each device. Now I just grab the device I want to use and it is all there in sync. Number 3 – Easy Restoral If you use Outlook for your email and have created a series of quick access folder shortcuts under the favorites area of Outlook, they are restored whenever you need to reinstall Outlook on a new device. Since your email account is based in the cloud the past emails you have saved in those folders are also synced to your device automatically. You also have the option to control how many months of email to store offline on your local machine in cached storage that is local. So in our house we sync our documents in cloud storage between all of our devices and we do the same with our email. How do you manage your email accounts and related storage? Source: winsupersite
- 4 replies
-
- emails
- outlook 2016
-
(and 1 more)
Tagged with:
-
1. Watch View this image › 2. Print out driving directions in a computer lab that looked like this… 3. …where you’d accidentally snap off the miniature plastic keyboard legs. 4. Bug your friends to sign up for this invitation-only ~beta~ email service. 5. Upload mirror selfies you took with a standalone digital camera. 6. Copy and paste HTML code that reduced your profile into a garish, unreadable, autoplaying mess… 7. …but still agonize over who you could trim from your finely pruned Top 8. 8. Ask this guy your deepest, darkest search queries. 9. Read and bury news stories on the *original* front page of the internet. 10. Download an mp3 over DSL, and then feel personally wronged by the seeder who mislabeled it. 11. Go PKing in the Wilderness. 12. Scribble an angst-ridden tracklist onto the CD-R you burned from low-bit .WMA files. 13. Own a loud-AF external DVD drive… 14. …so you could rip your movies into giant .ISO files… 15. …only to end up watching them on a tiny, two-inch screen with a couple hours of battery life. 16. Pay $40 for a 512MB flash drive and wonder how you’ll ever need that much space. 17. Open multiple windows of this browser ‘cause tabs weren’t a thing yet, and you didn’t know any better. 18. Dream of one day owning a Pocket PC — a computer that fits in the palm of your hand! Source: buzzfeed
-
My Mom had WebTV and used it right up until she passed away in 2013. She was involved in a lot of news groups, mostly political. Her WebTV's browser was Internet Explorer 4. :D:eek: I tried many times to get her interested in using a real computer. I even purchased a lap top for her but she was a die hard WebTV user. She had MSN dial up on her phone line at the cost of $25.00 a month.
- 1 reply
-
- internet terminal
- microsoft
-
(and 2 more)
Tagged with:
-
Do you remember the WebTV? You may not have even known anyone who used them, but they were a device that turned a regular TV into a slow Internet terminal. Some people who find computers intimidating really liked the idea. However, they should not pick up this unit that Liz found on the shelf at her local Walmart, mostly because there’s not much you can do with it. Microsoft owned WebTV, and they shut down the service that powers the device more than two years ago. Much of the technology that went into the WebTV ended up in the Xbox or in set-top boxes. The retail price of the WebTV was about $200 when it was on the market. How much is Walmart selling it for now that the product has possibly been sitting on a shelf for 10 years, and can’t actually connect to the Internet? Some readers inevitably accuse Raiders of the Lost Walmart tipsters of sending us old photos, maybe from 2006 in this case. Here’s a close-up of the price sticker that shows the date it was printed. Source: consumerist
- 1 reply
-
- internet terminal
- microsoft
-
(and 2 more)
Tagged with:
-
Scammers have a new way of getting to you. Their weapon: a phishing email claiming to come from the Social Security Administration. The subject line reads “Get Protected” and the return address appears as “no-reply@ssa.gov.” The email appears to offer new features that will help you monitor your credit report and warn you of unauthorized users of your Social Security number. It even refers to the IRS and mentions the “SAFE Act 2015.” All you need to do to register is click on a link. This Social Security email is a classic phishing ploy, a form of identity theft in which hackers use fraudulent websites and fake emails to attempt to steal your personal data, especially passwords and credit card information. Clicking on the link may open your computer to malware, such as viruses and spyware. Or the link might send you to a spoof site—a copycat version of the Social Security Administration’s site—to trick you into entering your personal information, including your Social Security number. Figuring Out Whether It's Fake Before you click on anylink—ever—take a minute to check it out. These clues from the Social Security email scam will reveal whether the email can be trusted or should be tossed. Here's how to do it: Hover your cursor over the address link. The URL of the fake Social Security email directs you to an unrelated “.com” address, not the Social Security Administration’s legitimate ssa.gov or another .gov site. Examine the name of the sender. In the case of AAFE Act 2015, nothing seems wrong with the name. Phishing emails often use real-sounding names in order to gain credibility. But look further, and there is reason to be suspicious. While the SAFE Act was passed by the House of Representatives last November, the acronym stands for Security Against Foreign Enemies and refers to the Iraq and Syrian refugee crisis. It has nothing to do with the Social Security Administration. Ask yourself why this email ended up in your spam folder. Email providers use filters to prevent phishing scams and spam from infiltrating your email. If an email ends up in your spam folder, it could be a sign that it's not legitimate. Contact the agency yourself. If you’re unsure about a Social Security email that claims to come from the government, call or email the agency. Just be sure to look up the address on Google; if you use the contact info listed in the phishing email, you’ll be directed back to the scammer, who'll try to convince you that the site is authorized. Report all questionable emails to the FTC and to the organization impersonated in the email. Source: yahoo
- 2 replies
-
- credit report
- irs
-
(and 3 more)
Tagged with: