-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
Microsoft's chatbot Tay may have suffered a racist meltdown last week, but the company is not giving up on AI. According to a report from Bloomberg Businessweek, Microsoft plans to unveil several prototype bots at its annual Build conference later today. These AI-powered programs will further Microsoft CEO Satya Nadella's vision of "conversation as a platform," with users able to interact with the bots using natural language, directing them to complete certain tasks. Different bots will have different functions, reports Bloomberg. Some built into Skype will help users schedule deliveries and book holidays, while others will help the visually impaired by describing facial expressions and reading text from images. Microsoft also plans to rehabilitate Tay (although the chatbot seemed to suffer another minor breakdown this morning), and will also release bot templates to help developers create their own programs. Microsoft joins Apple, Amazon, and Facebook in the quest for useful bots Microsoft's ambitions here mirror those of other Silicon Valley giants. Digital personal assistants like Apple's Siri and Amazon's Alexa have got people used to the idea of talking to their computers, while other companies are building bots into chat apps. Facebook, for example, is developing an AI-powered assistant named M that resides in its Messenger app, while Chinese company WeChat already offers in-app bots that let users book cinema tickets and hail taxis, just by texting. We'll have to wait until Build later today to find out exactly what Microsoft has in store, but we know at least one program that's coming: a Domino's delivery bot. Bloomberg reports that the bot will be part of the onstage demo, and will be built into Skype to let users order pizzas just by chatting. As long as it keeps its opinions about Hitler to itself. Source: theverge
-
- ai-powered
- chatbot
-
(and 2 more)
Tagged with:
-
Microsoft is reaching out to Linux developers in a way that the company never has before. "The Bash shell is coming to Windows. Yes, the real Bash is coming to Windows," said Microsoft's Kevin Gallo on stage at today's Build 2016 keynote. The announcement received an uproarious applause from the crowd. The new functionality will be enabled as part of this summer's Anniversary Update to Windows 10. "This is not a VM. This is not cross-compiled tools. This is native," he said. "We've partnered with Canonical to offer this great experience, which you'll be able to download right from the Windows Store." Third-party tools have enabled this sort of thing for years, but a direct partnership between Microsoft and Canonical should offer even more flexibility and convenience for developers who prefer using these binaries and tools. More importantly, it represents Microsoft's refreshing stance on open-source development. VP Terry Myerson teased "more coming soon" in regards to other possibilities signaling a modernized and extremely open Windows 10. This blog post by Microsoft's Scott Hanselman offers a deeper explanation of the move. This is brilliant for developers that use a diverse set of tools like me," he said. "This is a genuine Ubuntu image on top of Windows with all the Linux tools I use." Source: theverge
-
- anniversary update
- bash shell
-
(and 2 more)
Tagged with:
-
During its keynote address at the Build 2016 conference today, Microsoft announced that there are now 270 million computers running Windows 10. The latest version of Windows was released publicly last summer, after a prolonged public test period. Since launch, Microsoft has regularly issued updates to the operating system, giving the impression that Windows 10 is still very much a work in progress. There are, of course, many millions more PCs out there without Windows 10, so Microsoft still has work cut out for it. But given the relatively short time since the new platform's release, this pace of adoption is pretty good and better than it was for Windows 8. In fact, Microsoft says it's the fastest adoption pace of any version of Windows ever. Microsoft also says that users have spent over 75 billion hours in Windows 10 already, and there are over 500 new devices built specifically for the platform. Developing. Check out our Microsoft Build 2016 Live Blog for the latest updates and our Microsoft hub page for all the news! Source: theverge
- 2 replies
-
- 270 million
- build 2016 conference
-
(and 2 more)
Tagged with:
-
If you’ve been around this industry for as long as I have, you’ll remember Steve Gibson clearly – maybe not fondly, but definitely clearly. Steve created a popular application called Spinrite around the time Seagate MFM hard drives were the only type of hard drive available. Spinrite was used to perform diagnostics on those old hard drives, but in my experience destroyed more drives than it saved. As a PC technician from that era, I remember allowing Spinrite to run for hours upon hours and the heat emanating from the hard drive could warm a small village. Still the application has its place in history. If you’re one of those Windows or Windows 8.1 users who have complained about Microsoft’s on-again, off-again Windows 10 upgrade reminders, Gibson Research is offering a new application, called Never10, that is intended to keep Windows 10 off your system until you actually want it. Never10 doesn’t install anything, it just runs to make a few quick changes to the system required to keep the upgrade from happening. Never10 is available as a free download here: Never10 Incidentally, it appears the Gibson Research web site stands as a memorial to the old days, as it seems the web site still sports a very 1980’s look and feel. EXTRA: Another popular tool to block the Windows 10 upgrades is the GWX Control Panel. Source: winsupersite
-
I love it. All of the cats that we have had over the years, none of them have liked to be bathed. We used to have to be very careful when we flea dipped them in the summer or we'd end up with scratches everywhere.
-
Hi Mike, This is the preparation for malware removal help. Preparation guide for receiving Malware removal help
-
-
Apple isn’t the only company fighting against government-backed cyber attacks. While Apple and the FBI bicker over user security, Google is bringing security into the public eye in a different way – by simply telling you what’s going on. The company will be increasing the visibility of Gmail security warnings to try and help people better protect themselves when sending and receiving emails. One of the changes is the expansion of the “safe browsing” notifications, which basically tell you when you’re about to open a suspicious link from an email. These warnings will show up when a link is clicked, but before the link actually opens, presenting users with one final option to retreat instead of visiting the page. Previously, a warning only showed before a link was click, but no block appeared if the user didn’t see the warning or decided to click anyway. Google hopes this new, additional warning, will help stop users from visiting malicious sites. Google is also continuing the fight against state-sponsored attacks, showing a full-page warning when it thinks you’re being targeted by a government-backed hacker. Google does mention in a blog post that less than 0.1 percent of Gmail users will be receiving this warning, however, it highlights the importance of the warnings because of the fact that the people getting them are often journalists, policy-makers, and activists. The new warning of state-sponsored attacks can be shown in addition to, or instead of, current warnings that Google has in place for state-sponsored attacks. Google has been beefing up Gmail security quite a bit of late, and last month announced that it would be warning users who sent an email to a recipient that wasn’t using TLS encryption. According to Google, since adding this message, the number of emails sent over encrypted connections has increased by 25 percent. Source: yahootech
-
- apple
- cyber attacks
-
(and 2 more)
Tagged with:
-
While all of us regular Verizon customers can give a sigh of relief that our information wasn’t posted online in a recent hack attack, nearly 1.5 million customers of Verizon Enterprise Solutions — the portion of the company that deals with other businesses’ data breaches — weren’t so lucky. Krebs on Security reports the data — including contact information for the 1.5 million customers — was posted for sale on an “underground cybercrime forum” earlier this week. Hackers advertised the sale of 100,000 records for $10,000 or all of the information for $100,000. The group also offered the option for buyers to purchase information about security vulnerabilities in Verizon’s Web site. A rep for Verizon Enterprise says the company recently identified a security flaw in its site that allowed hackers to steal customer contact information, and that it is in the process of alerting affected customers. “Verizon recently discovered and remediated a security vulnerability on our enterprise client portal,” the company tells Krebs on Security. “Our investigation to date found an attacker obtained basic contact information on a number of our enterprise customers.” The company says that no customer data was affected by the breach. Krebs warns that if hackers do get their hands on some of the enterprise customer data, they could be targeted for phishing an other attacks. Crooks Steal, Sell Verizon Enterprise Customer Data [Krebs on Security]
-
- cybercrime
- data breaches
-
(and 2 more)
Tagged with:
-
Today is a great day for those of us who edit photos on a PC or Mac. Google GOOGL -0.39% has announced that the entire Nik Collection of image processing tools is now free to download and use. Formerly available at a cost of $150, the suite of seven professional-grade plugins is now available for download without charge in both Mac and Windows versions. Those who purchased the software in 2016 will receive a full and automatic refund in the next few days, according to Google. Google’s entire Nik Collection is now available free of charge (Image Credit: Google) The suite comprises Analogue Efex Pro, Colour Efex Pro, Silver Efex Pro, Viveza, HDR Efex Pro, Sharpener Pro and Dfine. Together, they provide features such as the ability to emulate classic film stock and lenses as well as creating nuanced colour corrections and black and white conversions. There are also plugins for creating HDR effects and tools for sharpening up details and reducing image noise. Google bought imaging specialists, Nik Software, back in 2012, and in so doing acquired the popular iOS-based photo editing app, Snapseed. Unsurprisingly, an Android version of Snapseed followed soon after, although a Windows-based desktop version was simultaneously discontinued. https://www.youtube.com/watch?v=iwUUO8voTxg As part of this acquisition, Google also bought the individual paid-for apps forming the Nik Collection – A software suite with a large enough user base of serious and professional customers to warrant its continued support and sale. At that time it would have cost $499.95 to buy the complete set, but Google immediately bundled them together and reduced the price to $150 for the entire suite. Even at this price, the Nik Collection remained somewhat of an oddity within the company’s portfolio of mostly free-to-use apps. Although still fully supported, the suite has also seen very little development in the time since launch. With competing products such as Alien Skin’s Exposure X and DxO FilmPack still going strong, it’s clear that Google wouldn’t have been able to charge $150 indefinitely without keeping up the pace. You can download the software for Mac and Windows directly from Google. The plugins are compatible with Adobe Photoshop CS4 and newer (CS5 for HDR Efex Pro 2), Adobe Photoshop Elements 9 to13 and Adobe Lightroom 3 and newer. It’ll also work with Apple AAPL -0.45%’s Aperture 3.1 or newer. Source: forbes
-
- free to download
-
(and 2 more)
Tagged with:
-
Yeah, it looks like a flying blue bat to me. :big_ha:
-
She was supposed to come off as a normal teenage girl. But less than a day after her debut on Twitter, Microsoft's chatbot—an AI system called "Tay.ai"—unexpectedly turned into a Hitler-loving, feminist-bashing troll. So what went wrong? TechRepublic turns to the AI experts for insight into what happened and how we can learn from it. Tay, the creation of Microsoft's Technology and Research and Bing teams, was an experiment aimed at learning through conversations. She was targeted at American 18 to 24-year olds—primary social media users, according to Microsoft—and "designed to engage and entertain people where they connect with each other online through casual and playful conversation." And in less than 24 hours after her arrival on Twitter, Tay gained more than 50,000 followers, and produced nearly 100,000 tweets. The problem? She started mimicking her followers. Soon, Tay began saying things like "Hitler was right i hate the jews," and "i fucking hate feminists." But Tay's bad behavior, it's been noted, should come as no big surprise. "This was to be expected," said Roman Yampolskiy, head of the CyberSecurity lab at the University of Louisville, who has published a paper on the subject of pathways to dangerous AI. "The system is designed to learn from its users, so it will become a reflection of their behavior," he said. "One needs to explicitly teach a system about what is not appropriate, like we do with children." It's been observed before, he pointed out, in IBM Watson—who once exhibited its own inappropriate behavior in the form of swearing after learning the Urban Dictionary. "Any AI system learning from bad examples could end up socially inappropriate," Yampolskiy said, "like a human raised by wolves." Louis Rosenberg, the founder of Unanimous AI, said that "like all chat bots, Tay has no idea what it's saying...it has no idea if it's saying something offensive, or nonsensical, or profound. "When Tay started training on patterns that were input by trolls online, it started using those patterns," said Rosenberg. "This is really no different than a parrot in a seedy bar picking up bad words and repeating them back without knowing what they really mean." Sarah Austin, CEO and Founder Broad Listening, a company that's created an "Artificial Emotional Intelligence Engine," (AEI), thinks that Microsoft could have done a better job by using better tools. "If Microsoft had been using the Broad Listening AEI, they would have given the bot a personality that wasn't racist or addicted to sex!" It's not the first time Microsoft has created a teen-girl AI. Xiaoice, who emerged in 2014, was an assistant-type bot, used mainly on the Chinese social networks WeChat and Weibo. Joanne Pransky, the self-dubbed "robot psychiatrist," joked with TechRepublic that "poor Tay needs a Robotic Psychiatrist! Or at least Microsoft does." The failure of Tay, she believes, is inevitable, and will help produce insight that can improve the AI system. After taking Tay offline, Microsoft announced it would be "making adjustments." According to Microsoft, Tay is "as much a social and cultural experiment, as it is technical." But instead of shouldering the blame for Tay's unraveling, Microsoft targeted the users: "we became aware of a coordinated effort by some users to abuse Tay's commenting skills to have Tay respond in inappropriate ways." Yampolskiy said that the problem encountered with Tay "will continue to happen." "Microsoft will try it again—the fun is just beginning!" Source: techrepublic
-
- experiment
- microsoft's chatbot
-
(and 2 more)
Tagged with:
-
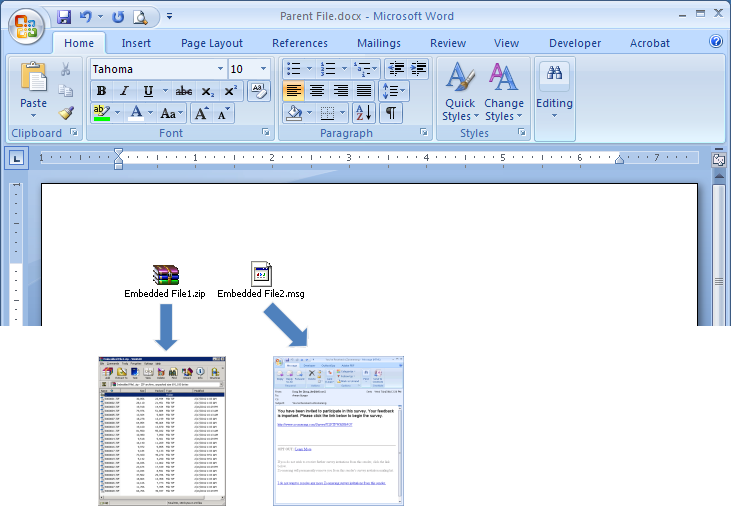
You can extract images from a Microsoft Office document with a simple trick. If you have a Word (.docx), Excel (.xlsx), or PowerPoint (.pptx) file with images or other files embedded, you can extract them (as well as the document’s text), without having to save each one separately. And best of all, you don’t need any extra software. The Office XML based file formats–docx, xlsx, and pptx–are actually compressed archives that you can open like any normal .zip file with Windows. From there, you can extract images, text, and other embedded files. You can use Windows’ built-in .zip support, or an app like 7-Zip if you prefer. If you need to extract files from an older office document–like a .doc, .xls, or .ppt file–you can do so with a small piece of free software. We’ll detail that process at the end of this guide. How to Extract the Contents of a Newer Office File (.docx, .xlsx, or .pptx) To access the inner contents of an XML based Office document, open File Explorer (or Windows Explorer in Windows 7), navigate to the file from which you want to extract the content, and select the file. Press “F2” to rename the file and change the extension (.docx, .xlsx, or .pptx) to “.zip”. Leave the main part of the filename alone. Press “Enter” when you’re done. The following dialog box displays warning you about changing the file name extension. Click “Yes”. Windows automatically recognizes the file as a zipped file. To extract the contents of the file, right-click on the file and select “Extract All” from the popup menu. On the “Select a Destination and Extract Files” dialog box, the path where the content of the .zip file will be extracted displays in the “Files will be extracted to this folder” edit box. By default, a folder with the same name as the name of the file (without the file extension) is created in the same folder as the .zip file. To extract the files to a different folder, click “Browse”. Navigate to where you want the content of the .zip file extracted, clicking “New folder” to create a new folder, if necessary. Click “Select Folder”. To open a File Explorer (or Windows Explorer) window with the folder containing the extracted files showing once they are extracted, select the “Show extracted files when complete” check box so there is a check mark in the box. Click “Extract”. How to Access the Extracted Images Included in the extracted contents is a folder named “word”, if your original file is a Word document (or “xl” for an Excel document or “ppt” for a PowerPoint document). Double-click on the “word” folder to open it. Double-click the “media” folder. All the images from the original file are in the “media” folder. The extracted files are the original images used by the document. Inside the document, there may be resizing or other properties set, but the extracted files are the raw images without these properties applied. How to Access the Extracted Text If you don’t have Office installed on your PC, and you need to extract text out of a Word (or Excel or PowerPoint) file, you can access the extracted text in the “document.xml” file in the “word” folder. You can open this file in a text editor, such as Notepad or WordPad, but it’s easier to read in a special XML editor, such as the free program, XML Notepad. All the text from the file is available in chunks of plain text regardless of the style and/or formatting applied in the document itself. Of course, if you’re going to download free software to view this text, you might as well download LibreOffice, which can read Microsoft Office documents. How to Extract Embedded OLE Objects or Attached Files] To access embedded files in a Word document when you don’t have access to Word, first open the Word file in WordPad (which comes built into Windows). You might notice that some of the embedded file icons do not display, but they’re still there. Some of the embedded files might have partial filenames. WordPad does not support all of Word’s features, so some content might be displayed improperly. But you should be able to access the files. If we right-click on one of the embedded files in our sample Word file, one of the options is “Open PDF Object”. This opens the PDF file in the default PDF reader program on your PC. From there, you can save the PDF file to your hard drive. If WordPad doesn’t have an option for opening your file, make note of its file type here. For example, our second file in this document is a .mp3 file. Then, go back to your “Files from [Document]” folder and double-click the “embeddings” folder inside the “word” folder. Unfortunately, the file types are not preserved in the filenames. They all have a “.bin” file extension instead. If you know what types of files are embedded in the file, you can probably deduce which file is which by the size of the file. In our example, we had a PDF file and an MP3 file embedded in our document. Because the MP3 file is most likely larger than the PDF file, we can figure out which file is which by looking at the sizes of the files and then rename them using the correct extensions. Below, we’re renaming the MP3 file. Note that not all files will necessarily open using this process–for example, our PDF file opened correctly from WordPad, but we couldn’t get it to open by renaming its .bin file. Once you’ve extracted the content of the zipped file, you can revert the extension of the original file back to .docx, .xlsx, or .pptx. The file will remain intact and can be opened normally in the corresponding program. How to Extract Images from Older Office Documents (.doc, .xls, or .ppt) If you need to extract images from an Office 2003 (or earlier) document, there’s a free tool called Office Image Extraction Wizard that makes this task easy. This program also allows you to extract images from multiple documents (of the same or different types) at once. Download the program and install it (there’s also a portable version available if you’d rather not install it). Run the program, and the Welcome screen displays. Click “Next”. First, we need to select the file from which you want to extract the images. On the Input & Output screen, click the “Browse” (folder icon) button to the right of the Document edit box. Navigate to the folder containing the document you want, select it, and click “Open”. The folder that contains the selected file automatically becomes the Output folder. To create a subfolder within that folder named the same as the selected file, click the “Create a folder here” check box so there is a check mark in the box. Then, click “Next”. On the Ready to Start screen, click “Start” to begin extracting the images. The following screen displays while the extraction processes. On the Finished screen, click the “Click here to open destination folder” to view the resulting image files. Because we chose to create a subfolder, we get a folder containing the image files extracted from the file. You will see all the images as numbered files. You can also extract images from multiple files at once. To do this, on the Input & Output screen, click the “Batch Mode” check box so there is a check mark in the box. The Batch Input & Output screen displays. Click “Add Files”. On the Open dialog box, navigate to the folder containing any of the files from which you want to extract images, select the files using the “Shift” or “Ctrl” key to select multiple files, and click “Open”. You can add files from another folder by clicking “Add Files” again, navigating to the folder on the Open dialog box, selecting the desired files, and clicking “Open”. Once you’ve added all the files from which you want to extract images, you can choose to create a separate folder for each document within the same folder as each document into which the image files will be saved by clicking the “Create a folder for each document” check box so there is a check mark in the box. You can also specify the Output folder to be the “Same as each file’s input folder” or enter or select a custom folder using the edit box and “Browse” button below that option. Click “Next” once you have selected the options you want. Click “Start” on the Ready to Start screen. The following screen displays showing the extraction progress. The number of images extracted displays on the Finished screen. Click “Close” to close the Office Image Extraction Wizard. If you chose to create a separate folder for each document, you will see folders with the same names as the files containing the images, whichever output folder(s) you specified. Again, we get all the images as numbered files for each document. Now you can rename the images, move them, and use them in your own documents. Just make sure you have the rights to use them legally.
-
You're welcome, N3.
-
The java that you download for IE will not work with Firefox. You have to download and install separately for both browsers.
-
You are right. The price scanning accuracy guarantee is still in effect in Canada. The US guarantee is no longer being offered. It turns out that the price accuracy guarantee was part of a legal settlement that USA Walmart agreed to in 2008. It was a four year agreement... which has now ended.
- 6 replies
-
- clearance conspiracy
- ploy
-
(and 1 more)
Tagged with:
-
There’s a reason why companies that handle sensitive billing information may ask customers to verify their email addresses before sending any communications. It’s to prevent customers from seeing things they shouldn’t. So why doesn’t AT&T have such a safeguard in place for its customers? Consumerist reader Joshua emailed us recently with an issue he was having trouble getting resolved. He received an order confirmation from AT&T for a home security system at an address in Detroit — which is an issue, because he lives in Minnesota. The order contained the person’s first name, date the order was placed, their address, the type of service, type of credit card used, and the amount billed. “I am an AT&T customer; have been for over a decade. My email address has been on file with them for years now as an authorized user (the account is under my wife’s name),” Joshua wrote. “I was surprised that an account they had on record as belonging to me could be used by someone else without raising any flags.” Reaching Out He contacted AT&T using the phone number in the email, and was bounced from a sales rep to the global fraud prevention department. He explained the issue, telling the rep upfront that the email belonged to him, but that the information was intended for another customer. He told her he didn’t think he should be receiving such information, nor did he think that the other customer would be pleased to know he’d gotten it. He tells Consumerist that the fraud prevention representative was “incredibly rude and downright dismissive.” “When I asked her why AT&T didn’t take the basic step of verifying ownership of an email address prior to using it for billing purposes, she flatly stated that AT&T could not and would not do that, as it ‘was not possible’ in the first place.” Which is odd, Joshua says, considering turnkey services exist for this very reason, and many other businesses will email a unique link or code to the address for confirmation. “She refused to remove my email from the account, refused to even do so much as confirm that someone would look into the issue,” Joshua writes. “I was really taken aback.” Going Social He also vented on Twitter about the issue, and was contacted by a social media manager asking for his email address. He provided it — but then got no response. A few days later, Joshua wrote to Consumerist with his plight, and we reached out to AT&T that day to ask why the company doesn’t verify email addresses used for sensitive communications. With Joshua’s permission, we provided his contact information yet again. That same day, an AT&T social media manager replied to Joshua’s direct message on Twitter, apologizing for the delay in responding and asking for his email address (again), and the billing account number or phone number associated with the email. Joshua didn’t see the message immediately, saying he doesn’t often check his Twitter inbox, as that’s not a method of communication he’s used to using. Besides, he’d given Consumerist permission to share his email address with AT&T AND had shared it directly with the social media rep who asked for it before, so he thought that would be how the company would reach out to him. He once again provided his email address to the person writing from AT&T’s Twitter account, as well as as much information he could glean from the misdirected emails about the other customer’s accounts. Apology Without Action At that time, a rep for AT&T told Consumerist that the company’s policies don’t allow for sharing details about customer accounts in these situations, but said that they were able to “resolve the issue” and would be letting Joshua know that. “We’ll also apologize for the inconvenience and the delay in getting back to his social media queries,” he said. That same day, another AT&T social media rep messaged Joshua saying, “We are here to help, Joshua. Your account details are being reviewed. Thanks!” It’s been a week since then, and Joshua says he’s still receiving email regarding the other person’s account. “Just got one asking me to set up permits for the alarm to avoid fines,” Joshua writes. “It looks as if AT&T does not care whether or not their customer in Detroit is getting fined or not!” Joshua says the situation ticks him off, because it’s an example of an otherwise responsible company not taking “basic steps to validate contact information prior to sending personally identifying information.” That behavior could be dangerous: Joshua notes that AT&T sent him enough information that it would be easy for him to call the other person, pose as an AT&T rep, cite order details, and claim there was a problem with billing, and ask the customer to repeat their card number and confirmation code on the AmEx/Visa/Mastercard/Discover credit card they used to set up the account. And beyond that, he’s still getting those emails meant for a stranger. What’s to prevent AT&T from sending Joshua’s information to other people as well? “I would be furious if they made it this easy for someone else to steal MY info, and then refused to take any action when informed of the problem,” Joshua writes. We’ve reached out to AT&T multiple times since our last communication to ask again, why the company doesn’t offer email verification for customers who choose to have billing and other sensitive account information emailed to them, and have not heard back. “The burden of keeping my information private should be on the company, not on the consumer,” Joshua says. “I can’t stop people from accidentally using my address, but there is absolutely no reason for AT&T not to check the email before sending personal details — especially when the email in question is already in their system, tied to another account, under a different name, in a different state.” Source: consumerist
- 2 replies
-
- at&t
- billing information
-
(and 2 more)
Tagged with:
-
You're welcome, Tony. :thumbsup: I have a habit of checking all stores price accuracy policy, wherever I shop.
- 6 replies
-
- clearance conspiracy
- ploy
-
(and 1 more)
Tagged with:
-
Depending upon the total price of the item, you could have either gotten the item free, if it was under $10.00 or they would have to give you $10.00 off the purchase price of the item. They have a price accuracy policy but here's the thing, you have to request it, they won't offer it to you voluntarily. They got off cheap with you, Tony. It didn't cost them anything. :D
- 6 replies
-
- clearance conspiracy
- ploy
-
(and 1 more)
Tagged with: