-
Posts
7,282 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
Legitimate businesses create video ads to promote their products, so why shouldn’t companies that can provide you with the supplies to commit crimes? Here are some videos where sellers of the tools of the ATM skimmer trade show off how their products work, in case you’ve always wondered how to insert and remove a super-thin ATM skimmer. The ever-awesome Krebs on Security obtained some videos from security experts of skimmer sellers showing off their wares to potential customers. From the videos, we learn that This type of skimmer slides in the card reader, and is invisible to anyone using the ATM. The thief will also need a device to harvest customer PINs, which could be a tiny camera somewhere on the outside of the ATM, or an overlay that sits on top of the PIN pad and collects numbers as customers type them in. You can see video captured from a separate device like that in a recent post. In this video, you see the special tools that come with a skimmer that are used to insert it and remove it. Then the seller manually inserts and rejects the card to show you how the skimmer stays in place even as the ATM goes about its business. https://www.youtube.com/watch?v=Nlx_GDeaEtI Also, you learn that “The Chicken Dance” is apparently a valid ringtone choice in the criminal underworld. Here’s a skimmer being removed from a real ATM out in the wild, using what looks like a special magnetic-stripe card and a tool that looks something like a flathead screwdriver. The best way to protect yourself against ATM skimmers is to cover your hand while you type in your PIN: without it, scammers won’t be able to drain your checking account of cash. It’s not foolproof, which is why you should check for temporary overlays on the PIN pad or anything else that doesn’t look right when you withdraw cash, but it will protect you from the more common pinhole camera version. ATM Insert Skimmers In Action [Krebs on Security]
-
-

FLocker Android Ransomware Now Infects Smart TVs
allheart55 Cindy E replied to starbuck's topic in Tech Help and Discussions
This can't be good. :( -
Microsoft just surprised the world with its LinkedIn acquisition. Valued at $26.2 billion, it's a huge price to pay for a social network, and it tops the charts as Microsoft's biggest-ever acquisition. As Microsoft CEO Satya Nadella's first major acquisition, the success or failure of LinkedIn will define him as the leader of Microsoft's increasingly service-driven future. While many are surprised at the cash figure, the question on everyone's lips is, why does Microsoft want LinkedIn? Nadella's internal memo does a good job of providing a basic outline to partially answer that question, and more. Nadella points out that LinkedIn is "how people find jobs, build skills, sell, market and get work done." It's a key tool in the professional work space, with 433 million members and more than 2 million paid subscribers. Microsoft itself has more than 1.2 billion Office users, but it has no social graph and has to rely on Facebook, LinkedIn, and others to provide that key connection. LinkedIn provides Microsoft with immediate access to more than 433 million members and a solid social graph that, thanks to its professional nature, is matched closely with the software and services Microsoft provides. In the same way that most kids play Minecraft, it's reasonable to assume most adults in the US use LinkedIn for finding jobs, connecting with colleagues, or just general work-related networking. "This combination will make it possible for new experiences such as a LinkedIn newsfeed that serves up articles based on the project you are working on and Office suggesting an expert to connect with via LinkedIn to help with a task you're trying to complete," says Nadella. As these experiences get more intelligent and delightful, the LinkedIn and Office 365 engagement will grow. And in turn, new opportunities will be created for monetization through individual and organization subscriptions and targeted advertising." Microsoft wants LinkedIn profiles to become a central identity in the workplace Nadella's example in his internal memo is only a small part of how Microsoft envisions its future with LinkedIn. LinkedIn will be the central professional profile that will be surfaced in apps like Outlook, Skype, Office, and even Windows itself. Microsoft wants to turn LinkedIn profiles into a central identity, and the newsfeed into an intelligent stream of data that will connect professionals to each other through shared meeting, notes, and email activity. It's a future of using a strong social graph and linking it directly into machine learning and understanding, an area Microsoft has showed great interest in recently. Microsoft even provides an example of Cortana connecting to LinkedIn to provide context on people you might be meeting professionally. It's something the company has been working with LinkedIn to integrate recently, but it's clear Microsoft sees LinkedIn as a big part of making Cortana more intelligent in the workplace. LinkedIn still has a reputation for being a spam machine, and recent password dumps have dented its security credentials. Microsoft will need to clear up both of these problems if it wants LinkedIn to be taken even more seriously by businesses. A social graph allows Microsoft to keep Facebook and Google out of the workplace These product examples and features all feed into a social network that's designed to combat rivals in the workplace. Google and Facebook have both shown interest in expanding into the social workplace, but LinkedIn has the advantage of being seen as the professional network. Microsoft might not be discussing rivals just yet, but this LinkedIn acquisition is a big bet on the future of machine learning and the ability to secure its control of enterprise software and services. Microsoft now has a huge social network to fend off advances from Google's suite of productivity services, but it still needs to convince businesses not to use Facebook at Work or Google Apps instead. It also faces the tough job of integrating LinkedIn into Microsoft's software, services, and management. Microsoft's previous acquisitions have been mixed affairs. The software maker acquired Yammer nearly four years ago, and bought Skype for $8.5 billion back in 2011. Both of those acquisitions have been integrated more closely into Microsoft's Office business, but they haven't been particularly rewarding. LinkedIn is a different beast, and many outsiders will be watching patiently to see exactly how well Microsoft integrates the social network into everything the company provides for businesses. Microsoft’s enterprise-centric intentions are clear, and it has gone on the offense today to prove it. Source: theverge
- 1 reply
-
- acquisition
-
(and 2 more)
Tagged with:
-
-
Nearly every modern smartphone comes with a fingerprint reader — but they’re not as secure as they look. All it takes to fake a fingerprint is dentistry paste and some Play-Doh.
-
- fingerprint
- reader
-
(and 1 more)
Tagged with:
-
If you’re doing your best to improve your Wi-Fi at home, you might be curious about who’s using your network, and if they’re slowing it down. It’s possible that your internet provider is just lying about the speeds that you should really expect on your network, but it’s also possible that there’s someone other than you (and your roommates or family members) using your Wi-Fi network. So how do you find out whether your network feels sluggish thanks to your household’s Netflix habit or thanks to an unauthorized user stealing your bandwidth? The best way to resolve the question is to use one of a few simple tools to take a look at what’s going on with your network, and to check whether the devices that are connected to it are ones you recognize, or ones that look suspicious and can’t be accounted for when you take stock of the Wi-Fi-connected gadgets in your home. Depending on your level of interest and your technical ability, there are some easy ways to find out. The New York Times’ J.D. Biersdorfer notes that there are a couple of easy ways to determine who’s using your Wi-Fi. Check your router’s administrative page One way to see what devices are connected to your Wi-Fi network (and to check whether you recognize all of them) is to log on to your router’s administrative page and check its DHCP Client Table, DHCP Client List, or the list of Attached Devices. From there, you’ll be able to see all of the computers, smartphones, tablets, and any other devices connected to your wireless router. The website of your router’s manufacturer (or the print manual that’s been collecting dust since you purchased the router) should include instructions on how to log in to your router, which Biersdorfer notes usually requires typing the router’s Internet Protocol (IP) address into your web browser, and logging into the page with the administrator name and password. You can also find your router’s IP address using text-based commands on either a Windows machine or a Mac. For instance, PC users can type “cmd” in the Start menu’s Search box, open the Command Prompt (cmd.exe) program, and enter “ipconfig” to find the router’s address, which Windows calls the Default Gateway. Or, Mac users can find the router’s IP address by opening the System Preferences icon, clicking the Network icon, and looking at the number that’s listed next to “Router.” Use an app to scan the network Source: Linksys.com If you don’t want to bother with logging in to your router’s administrative page, you can download an app that will do the dirty work for you. There are a number of apps that will scan your network for connected devices. In fact, your router’s manufacturer may have its own app, like Netgear’s Genie, Linkys Connect, or Apple’s AirPort Utility for iOS. Or, if you don’t like the manufacturer’s software or prefer to find another option, there are plenty of programs from third-party developers, apps that are equally capable of lending a bit of clarity to the assortment of devices that are connected to your network. A few choices include NirSoft Wireless Network, Watcher, Who’s on my WiFi for Windows, or the Fing network scanner for Android and iOS. How to use the list to determine who’s using your Wi-Fi Once you’ve gotten the app of your choice to show you a list of the gadgets that are connected to your network, you can determine which ones are yours, and see if there’s anything suspicious going on with your network. Your computer should show up, as well as your smartphone and your tablet (which you’ll probably be able to identify in the list by the manufacturer’s name). If the list is confusing and the device names difficult to parse, you can turn off each of your gadgets or disable their Wi-Fi in turn to figure out their names. It’s possible that all of the devices on the list will be accounted for, but if you find a device connected to the network that doesn’t belong to you, you know that someone else is using your Wi-Fi. It’s possible that the unauthorized user is connecting to your network only sporadically, so you may need to perform checks a few times to determine if the device is responsible for slowing down your Wi-Fi. Biersdorfer notes that some “sophisticated network moochers” are resourceful about disguising themselves while using your bandwidth. But if you have suspicions about who’s using your network, or if you’ve noticed that there are more devices connected than you and your household can account for, then you should consider changing your network’s password. It should go without saying that you should ensure that your network is appropriately secured, but if your network is already encrypted and someone is still connecting, then the least you should do is change your password immediately. After that, you should check on the network periodically to ensure that the only devices on the network are yours. If an unauthorized user manages to connect to your network again, you should return your router to factory settings and configure it again from scratch. If, on the other hand, you determine that no unauthorized users are connecting to your Wi-Fi network, and you’re still experiencing problems with the speed of your network, you probably have other problems to troubleshoot. You should test the speed of your internet via both ethernet and Wi-Fi, and if your Wi-Fi speed is much slower than your wired connection speed, that may indicate that you need to replace your router. There are some other straightforward ways to improve your Wi-Fi’s performance. But if those tips don’t solve the problem, you may want to get in touch with your internet provider and see if there’s a problem that the company can help you resolve. Source: cheatsheet
-
- internet provider
- network
-
(and 2 more)
Tagged with:
-
I know, right? :big_ha: It takes some nerve.
- 3 replies
-
- 19 iphones
- apple store
-
(and 3 more)
Tagged with:
-
It's not the most thrilling heist in the world, but it's definitely effective. Last week, police in New York reported that a pair of thieves managed to steal 19 iPhones from an Apple Store simply by dressing like employees. According to DNAinfo, a thief "dressed similarly" to Apple's own workers walked into the electronics repair room of a SoHo store on June 1st. He grabbed the iPhones — worth $16,130 — and handed them over to an accomplice who hid them under his shirt. The pair then walked out the store. The thieves presumably had more on their side than just the correct clothing (you'd need to know the layout of a store to confidently walk over to the spare iPhones), but it's not the first time Apple has been hit with this ruse. In March, the New York Post reported that thieves robbed one Upper West Side Apple Store twice in a matter of weeks using a similar trick. Thieves hit the same store twice Three criminals, including "a woman disguised as an Apple worker," stole eight phones from the store on February 16th, while a male accomplice distracted the store's real employees. Then, on March 22nd, another trio (it's not clear if they were the same gang), managed to steal 59 iPhones worth some $44,000 using the same ploy. That time, a man dressed as an Apple Store worker grabbed the devices before passing them to a female accomplice in the bathroom. A third acted as a lookout. The kicker is that this particular Apple Store is used as a training location by the company. A source from the store told the Post that this meant "nobody would question" an unfamiliar face — as long as they were wearing a familiar shirt. Sometimes, good branding can get the better of you. Source: theverge
- 3 replies
-
- 19 iphones
- apple store
-
(and 3 more)
Tagged with:
-
-
Twitter has responded to reports indicating that tens of millions of usernames and passwords for the social media service are currently available on the dark web, specifying that it is "confident the information was not obtained from a hack of Twitter's servers," and that the purported passwords may have come from breaches of other sites and malware hidden on its users' computers. News that more than 32 million purported Twitter passwords were being traded on the dark web surfaced Wednesday night. A day later, after cross-checking the password dump with its records, Twitter identified some of its accounts as requiring extra protection, locking them and requiring a password reset. It's not clear how many accounts Twitter chose to lock, but the company told the Wall Street Journal the number was in the millions, and that those affected will have already received an email explaining the situation. Twitter has locked some of the accounts it says were affected. The company has not denied that at least some of the user data on the dark web was accurate, but has distanced itself from the likes of LinkedIn and Myspace, both of whom had user passwords stolen when hackers breached internal databases. Twitter says computers infected with malware capable of scrubbing their owner's login details may be responsible for some of the passwords making their way online, but also shifted the blame onto its recently hacked peers. "When so many breaches are announced in a short window of time, it may be natural to assume that any mention of 'another breach' is true and valid," the company explained in a blog post. "Nefarious individuals leverage this environment in order to either bundle old breached data or repackage accounts from a variety of breaches, and then claim they have login information and passwords for website Z." People should "scrutinize the merits of any credential claim." Speaking to Ars Technica, security researcher Troy Hunt said he was "highly skeptical that there's a trove of 32M accounts with legitimate credentials for Twitter," specifying that "the likelihood of that many records being obtained independently of a data breach and them being usable against active Twitter accounts is extremely low." Twitter itself said people should consider news of such "hacks" carefully and "scrutinize the merits of any credential claim." News of the purported passwords circulating on the dark web was first provided by LeakedSource, a service that claims to allow people to remove themselves from such lists. LeakedSource echoed Twitter's line, telling the Wall Street Journal that it has "very strong evidence that Twitter wasn't hacked, rather the consumer was," identifying formatting techniques that suggested the data was captured from malware-infected computers rather than a master Twitter database. Twitter took the chance to reiterate safety guidelines in its blog post explaining the situation, advising people not to use the same password across multiple services amid a spate of celebrity Twitter takeovers. Last weekend, Mark Zuckerberg's Twitter account was briefly hacked, the infiltrators gaining access using the same password the Facebook CEO used for his LinkedIn account. That password — "dadada" — was exposed when LinkedIn's database were hacked in 2012. Source: theverge
-
-
-
Facebook recently patched a vulnerability that allowed attackers to change the content of their messages sent via the Android Messenger app. On Tuesday, Check Point security researcher Roman Zaikin published a blog post in which he outlines the details of the bug: "The vulnerability allows a malicious user to change conversation thread in the Facebook Online Chat & Messenger App. By abusing this vulnerability, it is possible to modify or remove any sent message, photo, file, link, and much more." Not just anyone could exploit the vulnerability. Only people who were already part of a conversation and who had used proxy servers or malware to discover a message's ID number could mess around with their Messenger content. The Messenger website also logs each of its conversations with original messages, meaning a user could access the original text of the conversation in another version of Messenger. These limitations notwithstanding, Zaikin argues an attacker could leverage the vulnerability to manipulate message history to commit fraud, to hide potentially illegal content, or to incriminate others. They could even deliver malware to unsuspecting victims, as the researcher notes: "An attacker can change a legitimate link or file into a malicious one, and easily persuade the user to open it. The attacker can use this method later on to update the link to contain the latest C&C address, and keep the phishing scheme up to date." A demonstration of this exploit can be viewed below: Check Point reported the flaw to Facebook's security teams, who patched the vulnerability in early May. The social networking site has since published a blog post about the bug in which it challenges several of Zaikin's findings, including the idea that an attacker could have exploited the vulnerability to manipulate any message's content or to distribute malware: "Content could have only been adjusted by the person who sent the message. The bug did not provide the ability to change someone else's messages.... [And] because even new content was subject to our anti-malware and anti-spam filters, this bug did not introduce the ability to send malicious content that would have been blocked in the original message." Trust goes a long way towards protecting yourself against digital attacks on social media. With that in mind, it's a good idea to not add any connections or friends whom you don't already know or trust. Source: grahamcluley
-

Problem installing to new HDD on HP 410-010
allheart55 Cindy E replied to mikehende's topic in Tech Help and Discussions
That'll do it. -
-
Most of us provide IT support to our family members at some level and if that is the case you know that one relative that keeps clicking on things they should not be clicking on. Whether it is installing a browser toolbar, another web browser or malware, it all wreaks havoc on their computer system and eventually results in a phone call asking for help because their system is running slow, etc. Although it is not always the case, many times these are older relatives who might not have the same level of computer skills as some one younger. There are companies out there who understand this dilemma and they cater to it by selling computers that have an entire interface layer over top of the operating system and come with 24/7 phone and remote support. In this interface you will find big bright buttons pointing to common programs the user wants to access and I am sure it works well but why add another level of complexity to the system and something else that could fail. I have someone who has asked me to take care of their system on multiple occasions because it has slowed down. When I arrive and take a look at the device I almost always find an extra toolbar installed on their browser because they got prompted to install an update for one of their helper programs such as Adobe Flash or an update to their web browser. About two months ago they called me and asked me to take a look at the system because it had slowed down again. When I arrived to grab the computer it had two extra toolbars installed on the browser and was slow as described. I took the computer home with me and the plan was to clean install Windows 7 once again and get them back up to speed. However, what occurred to me was that in a few weeks it would be back to the same state. So I took a chance and installed Windows 10 on the system with the current free upgrade offer. Once Windows 10 was installed I left the Windows Store set to update apps automatically and also configured Windows Updates to automatically install and restart the computer when it was not in use. Since they use Yahoo! Mail I downloaded and installed the Yahoo! E-Mail app from the Windows Store and set up their account in that. It is only a web wrapper but it eliminates many of the distractions that come along with the web experience. I placed a shortcut to the app on the Taskbar for quick access. Next I opened up Microsoft Edge and created a Favorites Toolbar that contained a shortcut to the Yahoo! Mail website as a backup to the app that I installed earlier. Since they are a big English Football fan I also added shortcuts to the websites they like to get their football news from. I opted for Edge because external toolbars can not be installed on it, not even inadvertently, and it has pretty fast performance. After returning the computer I explained the bare necessities of what they needed to know for getting e-mail and football news and left them with the system. Last week I got a call from them indicating there was some type of issue with the system and if I could come over and check it out. When I got there I was very concerned about what I would find but it ended up being a non-issue with e-mail replies and it had resolved itself before I got there. I then asked the big question - how is the system performing? Very quickly they replied that it was running great and had not slowed down at all! I have to tell you after 8 weeks that was very good to hear and shows that Windows 10 can help remedy the issues that many everyday users experience because of the security of the Edge browser and the automatic system maintenance. Maybe a setup like this could help you sort out the computer of one of your everyday users as well. Thoughts? Source: winsupersite
- 4 replies
-
- family members
- help
-
(and 1 more)
Tagged with:
-

How Windows 10 became malware
allheart55 Cindy E replied to allheart55 Cindy E's topic in Tech Help and Discussions
This is exactly what happened to my husband's notebook running Win 8.1. It upgraded without his permission, over night. It tried to install on my Win 7 computer automatically but I was able to prevent it as I was in front of the computer at the time.- 3 replies
-
- operating system
- stealth means
-
(and 1 more)
Tagged with:
-
Any software — even a premier operating system — that gets onto computers through stealth means has crossed over to the dark side. Several weeks ago my wife came fuming into my office. “Windows 10 just hijacked my computer,” she complained. “Without asking, Microsoft upgraded me from Windows 7, even though I didn’t want Windows 10, and I had to wait for the installation to finish before I could get any work done.” I asked her whether she had accidentally clicked “OK” on any upgrade notifications, ignored any warnings that she had received or gotten any other notices about the upgrade. No on all counts, she answered before leaving to wrestle with her new operating system. I admit to having been skeptical. Would Microsoft really take over someone’s computer without warning and install a significant chunk of software without explicit permission? That’s what malware does, I thought, not software from one of the biggest tech firms on the planet with the largest operating system installed base on desktop and laptops PCs. All this made me wonder: If software from any other company behaved the way the Windows 10 upgrade does, would it be considered malware? To find out, I delved into how the controversial upgrade works. Microsoft has been aggressive in its attempts to get as many people as possible to upgrade to Windows 10 in advance of the company’s self-imposed July 29 deadline for free upgrades from Windows 7 and Windows 8.1. Last year Microsoft installed its Get Windows 10 app on millions of Windows 7 and Windows 8.1 PCs. It alerted people that they could “reserve” the free upgrade if they wanted. When the app popped up on people’s PCs, they could close its window and block any action it might take in the time-honored way of clicking on the X in the upper right of the dialog box. Microsoft tells developers that clicking an X to close a dialog box and halt any action the box might take is the right way to do things. The company writes on a website devoted to design guidelines, "The Close button on the title bar should have the same effect as the Cancel or Close button within the dialog box. Never give it the same effect as OK.” In this case, that’s exactly what clicking X did: gave it the same effect as OK. So is the Windows 10 upgrade malware? One place to look for clues is in Microsoft’s document, “How to prevent and remove viruses and other malware.” That document warns, “Never click 'Agree' or 'OK' to close a window that you suspect might be spyware. Instead, click the red 'x' in the corner of the window or press Alt + F4 on your keyboard to close a window." And it defines spyware, in part, this way: “Spyware can install on your computer without your knowledge. These programs can change your computer’s configuration or collect advertising data and personal information.” So let’s see: The Windows 10 upgrade downloads its bits to your PC without your knowledge. It changes your computer’s configuration. By default, Windows 10 collects advertising data and personal information. And if you try to stop the upgrade by doing what Microsoft tells you to do with every other application — click the X on its dialog box — it installs anyway. Sounds like malware to me, malware that forces a Windows 10 upgrade. Sure, it isn't malware that's designed with a malicious purpose. It's not being installed on your computer with the aim of stealing your data or locking up your files until you pay Microsoft a ransom. But getting upgraded to a new operating system against your will can have drastic consequences, such as programs that won't work with the newer OS. If you unexpectedly find your PC upgraded to Windows 10, you might have to shell out for upgrades to other programs just to accomplish what you could do before the upgrade. Microsoft should immediately reverse course and let people decide for themselves whether they want to upgrade to Windows 10, rather than to use malware tricks to get them to upgrade. Source: computerworld
- 3 replies
-
- operating system
- stealth means
-
(and 1 more)
Tagged with:
-
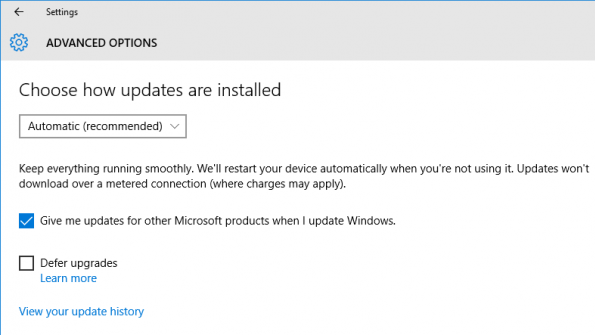
Anyone using a consumer version of Windows 10 knows by now that system updates, including drivers, are mandatory on the operating system. Unfortunately, an issue that existed in previous version of the Microsoft operating system seems to have carried over into Windows 10 when it comes to these automatic updates. This of course is the poorly timed installation and subsequent reboot of your system at the absolute worst times like in the middle of a meeting or when you really want to get on your device and get some work done. I have not had one Windows 10 based system do this to me in the 18 months since I joined the Windows Insider Program or since I transitioned all of our systems to Windows 10 last July when it was first released to the public. However, I follow social media and see people tweeting their frustration at these occurrences so something is askew on some systems. When an operating system is installed on the massive variety of devices it can be difficult to figure out exactly why it happened to any one individual. Now in Windows 10 Current Branch there are two options when it comes to these automatic updates and how your system should respond when it needs to restart to complete the installation of those updates. If you go to Settings > Update & security > Windows Update > Advanced Options there is a drop down box labeled Choose how updates are installed right at the top. The default recommended setting is Automatic. This option will restart your device when you are not using it. Since I like to maintain some control over these updates and restarts this is not the option I have selected on my systems however, it is the one I use on my wife's desktop with Windows 10. The second option in this drop down, the one I use as my default is Notify to schedule restart. This option will pop up a restart dialog after the updates are downloaded and the system is ready for a restart. As you can see above there are two options in this dialog as well. The first one is a suggestion from the system on what it believes is the best time to restart the device and the second option is for you to pick the time and day for the restart. I do not have an active restart screen in front of me but as I recall you can only pick today or tomorrow when you select the restart time. Now, as I mentioned earlier, it seems that even with these options there are some folks out there seeing their system restart unexpectedly. Whether that is a result of forgetting the time they selected for the restart or a bug is an unknown but Microsoft's goal with these options it to give you the control over that timing. Current testing builds of the Windows 10 Anniversary Update implements a new setting for scheduling restarts of your system after updates and it is called Active Hours. This new option should provide a lot more flexibility in scheduling system restarts after updates however, it can only cover a 10 hour range. We will have more details about this and other new features in our Windows 10 Anniversary Update coverage beginning next month. Source: winsupersite
-
- mandatory
- system updates
-
(and 1 more)
Tagged with:
-
Definitely not. :thumbsup:
-
Internet Explorer, Firefox, Chrome, Safari, Opera... these are just some of the web browsers available to today's internet users. While each browser might differ somewhat from their competitors, the major players in the web browsing game all come pre-equipped with a certain set of features. Today I'm going to talk about one such property known as "incognito mode" (also sometimes known as "private browsing"). First of all, what is Incognito mode? Incognito mode is a particular method of surfing the web via a web browser. It allows a user to hide their web activities from other users on a single, shared personal computer by automatically erasing their browsing/search history and by deleting all cookies at the end of each session. Sounds interesting. Why would I want to use it? Many think incognito mode is useful only when it comes to helping users privately search for adult content online. But that couldn't be further from the truth. There are plenty of practical, less potentially embarrassing reasons why you would want to use incognito mode. These include the following: Privacy on a public computer. Sometimes you might need to log into one of your web accounts from a computer at a library, cafe, or other public place. You don't want the browser to save any of your passwords, and you also don't want it to store any of your browsing history so that someone could come across the login page for your personal website. Browsing online via incognito mode will help protect your privacy by not storing any of these types of information. Multiple accounts. Many web services such as Google allow you to sign into only one registered account at a time. This might be inconvenient if someone maintains multiple Gmail accounts for personal use and work activities. To get around this obstacle, you can open two windows in your browser--one in normal mode, one in incognito mode--and sign in to access your different Gmail accounts at the same time. Outsmarting paywalls. We've all run into paywalls online. They're those nuisances hidden behind the firewalls of many news and blogging websites that notify us we've read the maximum number of articles for free in a given month. It doesn't take much to run out a paywall's limit. Fortunately, you can use incognito mode to visit a website an infinite number of times, as a website's paywall will think you're a new user whenever you initiate a new incognito session. I'm in. How do I activate incognito mode on my web browser? It's pretty easy. In most web browsers, click on "File" to display a drop-down menu of clickable options. You will have the ability to open up a new tab or a new window using that menu. You can also activate a browsing session in incognito mode. For Google Chrome, this option is known as "New Incognito Window," whereas for Firefox, it's known as "New Private Window." Click on that feature, and when the new incognito window pops up, you can begin browsing in incognito mode to your heart's desire. Meanwhile, in Internet Explorer 8 or later you can access what Microsoft calls "InPrivate Browsing" under the Tools menu (or press Ctrl+Shift+P). (NOTE: You can access incognito mode in major mobile web browser applications, as well. To turn on incognito browsing, simply visit your mobile browser's "Settings" page.) Great! I can't wait to begin browsing the web with true privacy! Whoa, hang on a minute! No one said anything about incognito mode guaranteeing true privacy. Sure, incognito mode hides your Internet activities from other users on a shared computer, but it doesn't hide your search history from the rest of the world. Not even close! Websites can still capture your computer's identifying IP address, and internet service providers, malicious software and potentially intelligence agencies can track what you're doing online. To better protect your privacy, you should consider using your web browser in tandem with a virtual private network (VPN), which masks a user's location and IP address. For added protection, you can dispense with your regular web browser and use the Tor web browser instead. So all in all... Incognito mode is a great way to hide your browsing history from local users, but it does not protect you from the rest of the internet spying on you. Source: grahamcluley
- 2 replies
-
- incognito mode
- internet users
-
(and 1 more)
Tagged with:
-
That looks like a nice one, Jim. I am partial to Logitech. I have Logitech keyboards, mice and microphones.
-
That's a nice one, Bill. It looks like Frank's.