-
Posts
7,278 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Articles
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-

Ad-Muncher Is Now Free!
allheart55 Cindy E replied to allheart55 Cindy E's topic in Tech Help and Discussions
Years ago, it was the best thing you could have..... -

Ad-Muncher Is Now Free!
allheart55 Cindy E replied to allheart55 Cindy E's topic in Tech Help and Discussions
Well, they are asking for a monthly $5 or $10 donation. Strictly voluntary, of course. I bought the rest of mine when they were 65% off..... -

Ad-Muncher Is Now Free!
allheart55 Cindy E replied to allheart55 Cindy E's topic in Tech Help and Discussions
I own eight Ad-Muncher lifetime licenses that I haven't used in almost a year. I have been using Ad-Block Plus ever since you recommended it and I think it's much better than the current Ad-Muncher. -
Ad-Muncher is now free. http://www.admuncher.com/free
-
If you've read some of my recent articles, then you know that when Windows 10 Technical Preview came out, I was extremely excited about the return of a real Start Menu. And I have to tell you, I haven't been disappointed in what I've found so far. The new Start Menu / Start Screen amalgamation in Windows 10 is really great. To get a primer on this great comeback, take a look at Tony Bradley's recent TechRepublic article, "How to customize the Windows 10 Start Menu (or Screen)." Despite all of the fancy stuff in the Windows GUI, I still like working from the Command Prompt, as you can probably tell from some of my recent posts. So, when I heard that -- in addition to bringing the Start Menu back -- Microsoft has spent a great deal of effort to make the Command Prompt a much more respectable environment to work in, I was intrigued. After all, the Command Prompt has essentially remained unchanged for years. Once I began investigating the new features in Microsoft's Windows 10, I couldn't help but shout "FINALLY!" for some of them and "WOW!" for the others. Let's take a closer look. Getting started While the new features are available in Windows 10's Command Prompt, they need to be enabled. To do so, launch the Command Prompt as you normally would, access the Properties dialog, and select the Experimental tab. Then, select all of the check boxes (Figure A). Figure A You'll enable the new Command Prompt features on the Experimental tab. While the tab is titled Experimental in the Technical Preview, I'm betting that these settings will become a permanent part of the Command Prompt once Microsoft sees how well received they are -- and my guess is that the tab will be renamed something like Advanced Settings. To continue, click OK. Then close and re-launch the Command Prompt. Windows 10 Command Prompt Finally, the Command Prompt window is being treated as a real Windows application! Here are some of the things you'll discover. Resizable window Once you enable the Experimental features, the Command Prompt window works like all the other windows in the operating system. Click in the Maximize button, and the Command Prompt window fills the entire screen. To put it back, click the Restore button. Want to manually resize the Command Prompt window? Simply position the cursor on one of the corners and, when the pointer turns into a double headed arrow, click and drag. Word wrap When you resize the Command Prompt window, you'll see that any text in the window responds accordingly. Make the window smaller, and the text wraps at the end of the line. Make the window larger, and the text extends to the edge of the window. Text selection Need to select some key text in the output of a command? For example, let's say you've used the ipconfig /all command and want to select the IPv6 Address. With Quick Edit Mode enabled, you can highlight the exact text that you want with the mouse pointer (Figure B); no more block selection. Figure B Precise text selection is much easier now that the old block selection method is history. Copy and paste Once you've highlighted some text in a Command Prompt window, press [Ctrl]+[C] to copy the text to the clipboard -- just like in any other application. Want to paste a long path from File Explorer into a Command Prompt window? No problem, just copy the path, click the command line, and press [Ctrl]+[V]. Want to select and copy all the text in a Command Prompt window? Just press [Ctrl]+[A] followed by [Ctrl]+[C]. High resolution support If you have a super high resolution display, you can select one of the Command Prompt's TrueType fonts and the operating system will now automatically scale the font to an appropriate size, based on the size of the monitor. This will make the text in the Command Prompt much easier to read at high resolutions. Transparency I never thought that I would see this feature natively supported in a Command Prompt. Using the slider on the Experimental tab, you can drop the opacity of the Command Prompt windows down from 100% to 30% or anywhere in between. Thus, it allows you to keep tabs on any window that happens to be behind the Command Prompt window (Figure C). Figure C Having a transparent Command Prompt window can come in handy. The setting you choose on the Experimental tab will be the default for any Command Prompt window that you open. However, once the window is in use, you can use keyboard shortcuts to adjust the opacity setting on the fly. Press [Ctrl]+[shift]+[+] to increase transparency. Press [Ctrl]+[shift]+[-] to decrease transparency. PowerShell All of the same settings and features are also available for PowerShell command window. This allows you to switch back and forth between the two command-line environments and have all of the features remain consistent. Copy and paste, resizable windows, high resolution support, and transparent windows -- it's all there in PowerShell. More details If you want more details and a deeper dive behind the scenes, be sure to investigate the article "Console Improvements in the Windows 10 Technical Preview" on the Microsoft Building Apps for Windows blog.
-
When Google quietly launched its new Search by Image function last June, the official suggested uses for the new service were fairly benign. Try searching "places, art, or mysterious creatures," the product description still suggests. To do that, you simply drag and drop an image into the search bar at images.google.com. Google then crawls its database and provides matches for those images. It all sounds so innocent, right? But come on, forget identifying that wildflower or national monument, we want to know if this service -- which can also be described as a reverse image search -- can help us find out who Smartdude99 is. And apparently, it can. A friend of mine decided on a whim to drag into Google's image search a photo of someone he'd been corresponding with on an online dating site, and wham -- Google pulled up his prospect's full name and place of work. He also found that by dragging about 35 anonymous photos from dating sites like Match.com and Howaboutwe.com into Google's Image Search field, six came back with hits that revealed the person's identity. In two cases, it brought up Facebook profiles with first and last names; in two other cases the results showed the individuals' work websites, including their full names and place of business. In one case, the image returned an identity match on JDate (thus revealing the man's religious background), and in one case what it revealed was not the person's identity at all, but instead that he was using a press photo of a Bollywood movie star. All of which is cool if you are the one doing the searching, but what if you aren't? At this stage, Search by Image is based on computer vision technology, not facial recognition technology, which actually recognizes faces by analyzing facial features, looking for matches in nose shapes, distance between eyes, etc. Instead it's "content-agnostic," meaning that it only pulls up matches when it's the exact same image, even if cropped or resized. (Tags and filenames are irrelevant, so it doesn't matter what the images are labeled.) This means if you're using the same photo somewhere else on the web, Google will find it -- and with it, all the accompanying information about that person. In other words, Search by Image has made internet stalking dramatically easier. That can be positive, of course -- it might be good, for instance, to know before you go on vacation if the Airbnb user whose place you're renting is a founder of the local S&M club. It's an easy way to check whether check to see if anyone is using your photo in an unauthorized manner (another one of my friends was surprised to see that a few sites were using his headshot without permission). But it's also a handy way for a guy on an online dating site you use to find out your name and other personal information. It gets creepier: If there's enough data on you out there, Google can pull up who you are even if it's not the exact same photo. Its "Visually Similar" feature can pull up different photos of the same person because, according to a Google spokesperson, more "documentation and activity around an object" leads to more results. For now, it seems like it only works for famous folks like Derek Jeter, or in this disturbing case, Michelle Obama -- but as more and more data and images gets added to the web, the search could eventually identify ordinary users (for example, it identifies Amy Gonzalez, the faux love interest in Catfish). Google also allows you to search by an image plus keyword--so if you have a few data points about the person, like a first or last name, your search becomes even more powerful. Believe it or not, the service technically doesn't violate any privacy laws. "It's positively spooky," says Ben Edelman, an assistant professor at Harvard Business School who specializes in online privacy issues. "But it's hard to point to a U.S. privacy law that this violates. The data is there, fair and square." Jeffrey P. Cunard, an attorney who works in digital privacy issues at Debevoise & Plimpton, LLP, agrees. "I don't think there are any legal issues here -- privacy laws are violated if you tell the user you're going to do one thing with their information, and then you do something else. That's not happening here -- Google is just finding and matching publicly available information." (If Search by Image did use facial recognition technology, it might be wading into tricky legal territory. "We won't add face recognition unless we have strong privacy protections in place, and we don't have anything to announce," a Google spokesperson told me.) So how can you prevent yourself from being easily stalked online via your photo? "Don't use images of yourself when it's not needed," suggests one Silicon Valley tech expert. "Use an avatar or symbolic photo instead." And definitely don't use the same photo of yourself in work and a dating or anonymous setting. This doesn't just include photos of yourself, but your home, kids, even your pets -- given how wide Google's database is now, and how much more powerful its search is with images in the mix (it has indexed 10 billion images to date), connections can be pulled up in an instant. If you search and find unauthorized images of yourself on the web, you should first contact the webmaster of the site to take it down. You can also use a tool called Me on the Web, a feature of the Google Dashboard that helps you monitor and learn about how to control your identity on the web. In the meantime, check out your photo, take down unnecessary pics, and scope out your prospective dates (especially before they read this). Bollywood poseurs, be warned.
-
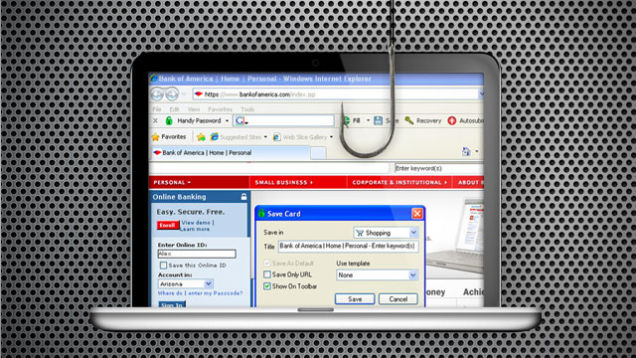
Phishing scams—the ones that try to get you to provide private information by masquerading as a legitimate company—can be easy to uncover with a skeptical eye, but some can easily get you when you let your guard down for just a second. Here's how you can boost your phishing detection skills and protect yourself during those times when you're not at full attention. The Complete Guide to Avoiding Online Scams (for Your Less Savvy Friends and Relatives)The Complete Guide to Avoiding Online Scams (for Your Less Savvy Friends and Relatives)The Complete Guide to Avoiding Online Scams (for Y What You Can Do The way most phishing scams find victims is through email, but sometimes you'll come across a phishing site in the wild as well. Either way, here are the basic principles you want to follow to keep a cautious eye out for these malicious traps. Check the URL Phishing scams are designed to look like official emails and web sites from actual companies, but they aren't actually those things—they're just imitations. Because the emails and web sites are imitations they'll probably look a little different from what you'd expect in general, but more importantly those sites can't have the same URL as the web site they're pretending to because they are different sites. To check the URL, just hover of the link you're thinking of clicking. At the bottom of your window you should see the URL displayed. Once you do that, you have to figure out if it is a good URL or a bad URL. Using PayPal as an example, you'll generally see http://www.paypal.com as part of the URL. Sometimes you'll see something like http://subdomain.paypal.com as well. Both of these URLs are okay, because they end in paypal.com. A phishing URL, however, might look something like this: http://paypal.someotherdomain.com. In this case, "paypal" is attached to another domain name (someotherdomain.com). URLs like this are the ones you want to avoid. Type the Address Yourself The best thing you can do to avoid phishing scams is always go directly to the web site you want to visit rather than clicking a link. This way you don't have to figure out if the URL is safe or not because you'll be using a URL in your bookmarks (or your brain) that you already know is safe. Doing this can also help protect you from phishing scams when you let your guard down because you'll be in the habit of visiting sites directly rather than clicking links. I fell for a phishing scam once when I read the email right after I woke up in the morning. It was from my bank and they'd sent me a lot of verification notices lately since I'd been traveling and using my debit card all over the place. When I got another one, I didn't even think about it because I'd just woken up. I went to the site, filled in my info, and then immediately realized I'd just provided that information to a phishing scam site. I called the bank to let them know right away and got a new card, but had I changed my default behavior to calling the bank of visiting the bank's web site this probably wouldn't have happened. Of course, that's what I do now and it hasn't been a problem since. What Your Browser Can Do For You Detecting phishing scams on your own mainly require the mild paranoia and the behavioral adjustment described above, but there are a few other things you can do to make your everyday browsing safer. Turn Off Form Autofill One great feature of many web browsers is the autofill feature. It makes it really easy to fill out forms using information already stored in the browser. It also makes it easy for you to ignore the form you're filling out and just submit it, causing you to potentially miss a phishing scam when you're rushing through the process. While this precaution isn't necessary, and you might prefer the convenience of autofill to the safety benefits that deactivating it can provide, turning it off will provide a little added protection. Utilize Your Browser's Built-In Tools Most browsers come with some phishing protection built-in to help protect you, but it isn't always enable by default. Google Chrome keeps track of common phishing sites and can alert you when you visit one, but you may need to go through the short setup process to make it work. Firefox also offers phishing and malware protection in a similar way, and you can enable it in the Security section of Firefox's preferences. Bump Up Your Phishing Protection with Web of Trust Web of Trust is one of our favorite browser extensions because it automatically lets you know if a web site is trustworthy or not. While it can't possible verify every single site on the internet, it can make you aware of potentially harmful sites and phishing scams. All you have to do is install the extension for your browser and it will display a trust rating in your browser's toolbar. (You can read more about this here.) Web of Trust is available to download for Google Chrome, Firefox, Internet Explorer, Opera, Safari, and as a bookmarklet for other browsers.
-
-
-
-
One of the weirder—and I have to think unfinished—changes we see in the Windows Technical Preview is the new Home view in File Explorer. This view presents what one has to assume Microsoft believes is useful information—your File Explorer favorites, frequent folders, and recent files—but I find it to be quite cluttered and borderline useless. Fortunately, you can clean it up a bit. This tip is very much relegated to the Windows Technical Preview version of Windows 10. I expect/hope that Microsoft will provide better controls for managing this view and, better yet, a way to customize which view appears by default when you launch File Explorer. For now, however, we're stuck with the Home view as-is. On my PC, when I launch File Explorer, I see this mess. I have several issues with Home, and it's not just the pedantic fact that "frequent" folders and "recent" files both appear to really just list recent folders and files, respectively, and not folders or files I use frequently. Whatever. I've seen a bizarre tip about cleaning this up using the Registry Editor. But you can do so more easily assuming you know the trick: Just access Taskbar and Start Menu Properties, which I admit isn't exactly intuitive. (Right-click on the taskbar and choose Properties.) On the Start Menu tab—again, not intuitive—there is an option titled "Store and display recently opened items in the Start menu and the taskbar." Uncheck that and click Apply. The, refresh File Explorer's Home view. As you can see, it's all cleaned up. (The Favorites group at the top maps to the File Explorer favorites you seen in the navigation bar on the left of the window.) Much better. No less useless. But much less crowded.
-
By the numbers alone, basically everyone in the country has been the victim of at least one data breach in the past year, if not more. 106 million Americans had their card data stolen from Target and Home Depot alone, to say nothing of the data breaches at Jimmy John’s, Dairy Queen, P.F. Chang’s, UPS, Albertsons, Jewel-Osco, ACME, Shaw’s, Sally Beauty Supply, Goodwill, some Marriott hotels, Neiman Marcus, and Michael’s craft stores. And that isn’t even considering other breaches that were too small to make national headlines, or that simply haven’t been discovered yet. Websites, online services, and databases get hacked too, of course, as Chase, Adobe, and Sony could unhappily tell you. But hacks in good old-fashioned brick-and-mortar retail stores have skyrocketed in recent years. And it’s not just about how often they happen; it’s about how widespread they are able to become. So if you, as you replace your credit card for the third time in a year, are tempted to shout to the sky, “Why?! Why does this keep happening? Make it stop!,” then read on. Why do these hacks keep happening? As with any crime, there are three main elements to massive retail hacks: means, motive, and opportunity. The means? You need three things: a computer, an internet connection, and an education, either formal or informal, in how to use them. It’s a big world, with a lot of people in it who have plenty of coding know-how and both the desire and ability to break — or break into — something. So why use those powers for evil, instead of for good? That’s a driving motive easy enough for anyone to understand: if you are good at it, crime pays. It pays really, really well. Indeed, the annual Verizon Data Breach Investigations Report (2014 version available here), finds that although ideology and espionage are both also drivers, the vast majority of attacks, hacks, and breaches are motivated by plain old financial gain. Security expert Brian Krebs — the man who discovered and broke the news about both the Target and Home Depot hacks, among others — has delved into the markets where stolen card numbers are resold. When the cards stolen from Target were new, he found, they went for between $26.60 and $44.80 each. By February, prices were as low as $8 because the card numbers were less likely still to be valid. Krebs later estimated that somewhere around 2%-4% of the card numbers stolen from Target were successfully sold. Out of 40 million cards, that’s somewhere between 800,000 and 1.6 million sales. Even if you assume none of those sold for more than $8, that’s still a total of between $6.4 and $12.8 million. That’s the lowest, most conservative estimate. More likely, the group who sold those credit card numbers netted something like $15-$20 million for them all, if not far more. Not a bad haul for a few months’ work done from the comfort of a desk chair. And certainly a much better risk-benefit proposition than walking into a bank with a gun and a note. And opportunity? Well, that’s everywhere. In the specific sense, many stores’ payment systems are not as secure as they should be (more about that in a moment) and since they can be hacked, they will be. But in the broader sense, globalization, and the worldwide reach of the internet, also help provide the opportunity. The malware is often designed and sold by Russian hackers, who are able easily to target American stores, and can then sell the stolen credit cards to buyers worldwide. Criminals can reach across national borders more quickly than retailers and law enforcement can. That’s not to say that the FBI can’t catch crooks who make their home bases abroad, because they can. But catching Americans is easier. There are also some political underpinnings. The individuals and groups behind the Target and Home Depot hacks, specifically, have some anti-western, anti-American leanings and are happy to target American capitalism for political reasons as well as the practical ones. The window of opportunity, though, may eventually be closing. The United States is poised finally to begin joining the rest of the world with smarter credit card technology, that’s less susceptible to POS attacks, in 2015 and beyond. How do hacks happen? From a high level, the process of stealing 50 million credit card numbers is surprisingly straightforward. Sneak into a company's network Install malware on the system Let credit card numbers roll in Profit!!! But of course, the devil is in the details. The Tools BlackPOS. IT security experts discussed the highly technical ins and outs with Krebs earlier this year, but the gist is that BlackPOS is a “RAM scraper” that manages to grab unencrypted information out of a terminal’s memory. It’s not the first — RAM-scraping is an old idea — but it is, for now, the biggest. When we go shopping, most of us just swipe or tap our cards at the register and don’t really think about it much more than that. But a point-of-sale (POS) system is, like so many other things, basically just a small and specialized computer. It has the part you physically slide your card through, which is the hardware. And it has the programmed parts that tell the hardware what to do and how to do it, and that capture information from the magnetic strip in your card and turn that information into payment: the software. The malware used in the retail hacks is basically a giant virtual skimmer: it captures information from the payment card at the moment you swipe, and sends that information flitting away through the internet into the bad guys’ virtual pocket. The vendors who create payment systems aren’t stupid; they (are supposed to) adhere to a set of data security standards that requires payment information to be encrypted end-to-end. That is, data is encrypted when it’s transmitted or received. But that leaves two vulnerable moments: when the data is captured before being transmitted, and when the data is decrypted for processing after being received. A payment system, like most other computer systems, has short-term system memory that it uses to hold information while it processes. The RAM-scraping malware installed on POS systems reaches into that memory in the instant the card has been swiped, and grabs the shadow of the unencrypted payment information in the split second before it vanishes. Retailers and payment vendors do of course use industrial-strength virus and malware scanners to identify and remove threats from their systems. But the bad guys who make the malware are often one step ahead. In the case of BlackPOS, Krebs explains, the version of the software that hit Home Depot was able to disguise itself as part of that very antivirus program. How They Get In Almost any system has a way to break in. In the case of Target, hackers didn’t steal access information from anyone at Target. Instead, they focused on a weaker link: a third-party vendor. That vendor, a heating and air conditioning company, had a connection to Target’s networks that they used for “for electronic billing, contract submission and project management,” as they explained in a statement last February. Home Depot, meanwhile, did leave themselves vulnerable, according to former IT employees. After talking with those employees, the New York Times reports that in 2012 and 2013, Home Depot was still using security software from 2007-2008, and also not thoroughly scanning their network for suspicious activity. By the time the store finally took strong action, in the wake of the Target data breach, it was too late: the hack was already in progress. Two years ago, in 2012, the company did finally hire a new IT security architect to deal with their network issues, and they promoted him in 2013. However, in April of this year he was convicted of sabotaging network security at his previous employer and sentenced to four years in federal prison. So… not exactly the most reliable guy to fix your glaring network security holes. In fact, people are the weakest link in pretty much any network security setup. The infamous annual hacker conference, DEFCON, has for several years run a very successful social engineering competition, in which the hackers use simple web research and phone calls to get all of the information they need out of unsuspecting company employees. In 2012, for example, the contest’s winner successfully got a Walmart store manager to tell him everything he would need to know in order to infiltrate the store’s whole network, which would give a less ethical hacker all the access he needed to work some malware into the system. And while the Walmart call was the winner, for collecting the most “flags” (pieces of vital information), participants calling Target, FedEx, Verizon, Cisco, AT&T, Hewlett-Packard, and UPS were also able to extract a significant amount of information within the twenty-minute time limit. And of course, there’s the good old-fashioned trick of stealing login credentials directly, either through phishing expeditions or through website hacks. That’s why we’re all supposed to use different passwords for every site and network. That way when your password for a hobbyist forum is stolen, the thieves who stole and possibly sell it won’t get anywhere trying to use it on other sites and networks you access — both personal and professional. Home Depot employs over 340,000 people. Target has 366,000. And Walmart employs over 1.3 million just in the U.S. (over 2 million worldwide). With a pool of tens or hundreds of thousands of potential targets at the country’s biggest corporations, chances are someone, somewhere will make a critical error and let the wrong information slip. Profit! So how does a pile of thousands or millions of stolen credit card numbers become cold, hard cash? The hackers who collect them don’t use them; they sell them, in bulk and wholesale batches. There are plenty of sites among which the discerning cybercriminal can choose. As a computer security expert explained to USA Today last week, there’s a whole supply chain for stolen cards. So the hackers are the manufacturers and the wholesalers. Then come middlemen. The people who buy black-market credit card numbers use them to make cloned cards. The equipment to take a bunch of plastic blanks and throw embossed numbers and magnetic strips onto them costs about $500 — a very low barrier of entry. So the middlemen take their list of numbers and expiration dates and make passably valid cards. (This is why chip-and-pin (EMV) card technology is less susceptible to POS hacking: because without the computer chip in the original card being physically present, no cloned card will work. Duplicating the information in the magnetic strip alone is not enough to create a working EMV card.) Armed with a nice big stack of fake credit cards, the folks at the next level down in the operation get to work. They go out and buy things that can be resold for large amounts of cash. So there are plenty of big-screen TVs and Xboxes on the shopping list, as you might expect. But, USA Today explains, one of the most popular targets? Gift cards. Pretty much any grocery or drug store these days has in it a display containing gift cards for dozens or hundreds of other stores. They are incredibly effective money-laundering tools: once there’s $100 on a gift card, it stays valid. It doesn’t matter where that hundred bucks came from or if the credit card used to fill the gift card is cancelled. After that, the gift cards can either be kept and used, or — like big-ticket physical goods — resold for cash in hand. How can we stop hacks from happening? Here’s a cheerful thought: there is absolutely nothing that you can do about this situation. Individual consumers are pretty much powerless to prevent retail hacks. Call your card-issuing bank. Some banks proactively contact customers and/or issue new cards, after a major data breach makes headlines. If your bank doesn’t, call them! Tell them which data breach you got dinged in and that your number is out in the wild. They’ll probably offer to replace your card. That free credit monitoring won’t help (but it probably won’t hurt, either). It’s stage 2 of the public mea culpa every company goes through: offering a year of free credit report monitoring to affected consumers… even though credit report monitoring is completely useless for protection when just payment card info is stolen. And don’t forget to do your own free credit report monitoring as well. That’s not to say that we shouldn’t all be aware of security best practices, and we’ve heard them all a thousand times: use good passwords. Change them often. Don’t re-use them. Enable two-factor authentication on all the things. Be smart about where you shop. Look for skimmers. Cover the PIN pad when you enter your code. Keep an eye on your surroundings. Don’t use sketchy-looking stand-alone ATMs. Check your credit and debit card statements regularly. Get your annual credit reports. But almost every action an individual consumer can take is about mitigating or recovering from harm, not preventing it. And most of what we know how to do deals with online or mobile shopping, not traditional brick-and-mortar stores. Whether it’s a mom-and-pop candy shop or the world’s largest Walmart, protecting point-of-sale transactions is something that retailers and payment processors have to work out on their end. We can’t do much except choose where (not) to shop. So what is it retailers need to do differently? The Verizon report concludes its section on point-of-sale hacks with some common-sense admonitions to retailers of every size. Among them: Restricting outside access to the network, enforcing strong password policies, forbidding the use of social activities on computers that also have sale functions, and using (and updating!) anti-virus software. But although those are all good ideas and best practices, those tricks alone will not protect a nationwide retailer. Not by a long shot. For a national chain, the Verizon report has a few extra suggestions. One: stores need to “debunk the flat network theory.” The POS network, the report suggests, should be treated completely separately from the corporate network. That way someone who gets into the latter can’t run rampant in the former. Two: retailers really need to be looking for suspicious network activity. Watch the traffic! If there is network traffic going out when it shouldn’t be, from a place where it shouldn’t be, that’s a sign that there is a problem. And three: what’s good for individuals is good for business. The report recommends that companies really should develop and enable two-factor authentication processes for both internal users and authorized third parties. If the hacker somewhere in Eastern Europe doesn’t have the cell phone that a network access request texted a passcode to, that would prevent a host of potential problems right there. The combination of internal protections like two-factor authentication, combined with smarter, more hack-proof EMV cards, will almost certainly help companies and consumers both by dramatically cutting down on the number of store hacks and the amount of physical credit card fraud we see. But in the meantime, we will almost certainly keep hearing of small- and medium-scale hacks pretty much every week. It’s all but inevitable: there are literally more hacks, breaches, and “incidents” happening every minute. And the next giant breach on the scale of Target or Home Depot? That one’s probably already underway somewhere, too.
-
-
-
-
Microsoft is currently soliciting feedback for Windows 10 as part of a Technical Preview program to improve the features of the company’s next version of Windows. While testers are voting on a variety of changes that Paul Thurrott has documented well, Microsoft has also opened its own Windows feature suggestion page at the Uservoice feedback site. The software maker has previously used Uservoice for Windows Phone, and strong Uservoice support for the Cortana name actually swayed the company to keep the name following several leaks. So it’s clear the company looks at Uservoice closely. Here are the top 10 requests for Windows 10 features. Add tabs to File Explorer This suggestion is self explanatory. A tabbed interface for File Explorer would allow Windows 10 users to simply tab through different folders instead of having multiple folders open that clutter the desktop. A number of third-party solutions currently exist, and the suggestion includes the ability to view two tabbed folders side-by-side in a single Explorer window. Make Windows Update the one stop for all drivers Again, another simple request. Microsoft has added a variety of OEM drivers to its Windows Update service, but more often than not you still have to dig around the web to find the latest drivers. It shouldn’t be this way, especially for consumers. A lot of PC makers now have their own separate update tools, and the suggestion calls for Microsoft to own the process entirely to make Windows Update the one stop for all PC drivers. Add a Persian calendar to Windows This might not seem like the most obvious addition for Microsoft, but it’s clearly one that some Windows users want. With 983 votes at Uservoice, it’s as simple as adding a Persian calendar to Windows 10. Bring back Aero Glass With Apple bringing some transparent effects to OS X Yosemite, some Windows users are calling for the return of Aero Glass. Microsoft first introduced this feature in Windows Vista, but Microsoft cut most of the window transparency in Windows 8 to focus on improved battery life. The feedback request notes that millions of PCs are desktops and are equipped with capable graphics cards and memory to handle Aero Glass. Microsoft has added some drop shadow effects to the Windows 10 Technical Preview, so there are signs the UI could change a lot before the operating system ships. Redesign and Replace Windows users have been calling on Microsoft to redesign its ancient iconography for years. Although some recent versions of Windows have improved upon this, there are still a number of areas you can stumble across where you’ll see an icon from 20 years ago. Long Zheng, a user experience designer from Australia, created a Windows UI Taskforce ahead of the Windows 7 release to encourage Microsoft to fix its many user interface quirks. Unfortunately, many still exist in Windows 8 today. There are signs in the Windows 10 Technical Preview that Microsoft is overhauling its iconography, as the File Explorer icon has a flat look to it now. Provide a better Notepad application The basic Notepad.exe application in Windows hasn’t really changed over the years. While Paint has been improved with a Ribbon and interface tweaks, Notepad is as simple as ever. While there is a Wordpad alternative built-in, some on Uservoice feel the default notepad application should be better. No support for Unix line endings, double click to select words is inconsistent, and undo doesn’t work well according to the feature request. Those are reasonable observations, and it’s probably about time Microsoft offered something as good as Notepad++ as the default in Windows 10. Make Windows free for everyone Anything free makes it into any good list, and some Windows users just don’t want to pay for the next version of Windows. "Simple as that," notes the feedback, but it’s far from it. Microsoft still generates a huge amount of revenue from Windows, and although the company has made Windows Phone and Windows free for tablets under 9 inches, it’s highly unlikely the company will extend that to everything else anytime soon. Microsoft may, however, make Windows 10 free for Windows 7 and Windows 8 users. That would be a wise move to avoid Windows 7 becoming the next Windows XP. Let me pin anything to the Start Screen The Start Screen in Windows 8 supports "Metro-style" apps and traditional desktop apps for pinning, alongside Internet Explorer bookmarks. If you want to pin a file you’re out of luck. This popular feature request asks for exactly that, just let people pin anything to the Start Screen to make it more useful. Let us bind programs to specific audio outputs Microsoft made some good progress with its audio management as part of Windows Vista, allowing you to individually control the volume of applications, but people want more. Some Windows users with headsets are calling for Microsoft to allow them to map a certain application to a specific audio output. The scenario could allow an app with essential notifications to output over the speakers, while music could play on the headphones. It’s a niche scenario, but there are environments, particularly in offices, where you might want an audio alert for your team members, but still want to keep your personal music tastes confined to your headset. Merge PC settings and Control Panel This seems like an obvious one, but even in the Windows 10 Technical Preview there are still separate areas for the new friendly PC settings and the traditional Control Panel. Microsoft has tried to dumb down its Control Panel with a simple UI over the years, rather than a list of options, but there’s still a number of settings that don’t exist in the new PC Settings app. "Why do I have to go the PC settings to forget a network and Control panel to change IP settings? Can't this all be done from a single place?" It’s a fair criticism, and one that Microsoft should look to address with Windows 10. Number 11 bonus Internet Explorer plugins and extensions Microsoft’s Internet Explorer browser started to fall behind Firefox when it took what felt like forever to add tabs to the browsing interface. Ever since then it's been a slow process watching Internet Explorer catch up. Although Internet Explorer does support add-ons, they’re often basic or nonexistent compared to the offerings available on Firefox and Chrome. It’s an area where Internet Explorer falls short, but rumors suggest IE12 will overhaul its extensions support so there’s hope yet.
-
-
-
-

National Radio Quiet Zone: No Cell Phones Allowed
allheart55 Cindy E replied to N3's topic in Tech Help and Discussions
Perfect! -
As with any product that’s still in development, running Windows 10 Technical Preview has risks. The safest and easiest way to install and work with the preview of the next Windows is within a virtual machine — here’s how. Long-time readers might recall a similar article, the March 14, 2012, Top Story, “Step by step: How to safely test-drive Win8.” Today’s article is in the same vein but covers recent changes in virtual PC (VPC) software and the process of installing Windows 10 Technical Preview (Win10 Preview, for short). If you’d like a quick refresher on what a VPC is and how it works, please see that March 14 article. VPCs are not only safe and simple to set up — you can run them on just about any operating system. And in this case, both Windows 10 Preview and the virtual PC software are 100 percent free. Best of all, running in a VPC, Windows 10 Preview presents essentially no risk to your primary (host) system. It’s as if Win10 were installed on its own, separate, physical PC! The three major steps to get everything going These steps assume that you don’t have virtual-PC software already installed. As with that earlier Windows 8 article, we’ll use Oracle’s VirtualBox. Not only is it free, but it’s highly capable and relatively easy to set up. (Note: VirtualBox is updated frequently. If you already have it installed, now is a good time to get the latest version.) The steps are: Download and install VirtualBox on a standard PC; Use VirtualBox to create a new virtual machine that’s optimized for running Win10 Preview; Download Win10 Preview and install it on the new virtual machine. Before you begin, some important preliminaries The requirements for running Win10 Preview inside a VirtualBox VPC are relatively modest. The vast majority of today’s PCs, running any current version of Windows — Vista, Win7, or Win8 — will likely meet or exceed the minimum specifications. Here’s what you need: At least 3GB of system RAM: Win10 Preview needs at least 1GB of RAM, VirtualBox needs about another 512MB, and the host system typically needs at least another 1GB or so. Add a skosh more memory for shared system functions. It’s better to have more than 3GB of RAM — the typical PC sold today comes with 6GB to 12GB. (To quickly check your system’s installed memory, click Start/Control Panel/System. In the System section, look for the heading “Installed memory [RAM].”) A minimum 30GB of available disk space: Win10 Preview needs about 25GB of free space plus another 4GB or so for the Win10 installation file — but as with RAM, more free drive space is always better. (You will, of course, get that space back when you delete the Win10 VPC.) The Win10 virtual machine doesn’t need to reside on your primary (C:) drive, but this will make the setup process a bit easier. Hardware-virtualization support: Almost all PCs sold in recent years feature built-in, hardware-level support for the kind of virtualization used by VirtualBox (and similar VPC/VM products). But older systems might not have this needed feature. Here are ways to determine whether your PC has virtualization support: One method is to simply install VirtualBox and set up a new VPC (more on that below). Next, click the VPC’s VirtualBox Settings icon and go to the System section. Click the Acceleration tab and check whether Enable VT-x/AMD-V is — or can be — checked, as shown in Figure 1. (Note: On some systems, you might have to enable hardware-virtualization support in the host system’s BIOS. See this Windows SevenForums page for a quick how-to. For more on this topic, see “Details about hardware virtualization” on the “VirtualBox Technical background” page.) Figure 1. VirtualBox's hardware-virtualization setting is under Settings/System/Acceleration. If your system doesn’t support hardware virtualization, simply uninstall VirtualBox. If you’d rather find out in advance, Intel offers its free “Does my processor support Intel Virtualization Technology?” utility (more info). Likewise, AMD offers the “AMD Virtualization Technology and Microsoft Hyper-V System Compatibility Check Utility” on its Utilities page. (Scroll down toward the bottom of the list or click this direct download link.) You can also try Microsoft’s “Hardware-Assisted Virtualization Detection Tool” (Download Center page), but the app works only on XP, Vista, and Win7 — not Win8. You can also look up the model number of your CPU on the manufacturer’s site and check the listed specs. But again, almost all machines sold in recent years include virtualization support. Finally, before you proceed, make a backup of your current system. Although none of the following steps is particularly risky, it’s simply good practice to make a current backup before you install new software or make any changes to your host system. Setup step 1: Download and install VirtualBox Head over to the download section on VirtualBox.org. Under the VirtualBox platform packages heading, select VirtualBox {version number} for Windows hosts (as of this writing, it’s Version 4.3.16). It’ll run on all current versions of Windows. Note: Oracle also offers the VirtualBox Extension Pack, a separate download that lets a guest operating system more fully integrate with a host OS. Your particular PC setup might — or might not — require the Extension Pack. To keep things simple, I suggest installing just the basic VirtualBox package. If the Extension Pack is required, you’ll receive a prompt to that effect later on. You can then return to the VirtualBox download page to install the Extension Pack. Once the VirtualBox for Windows hosts installation file has fully downloaded, click it and let the software begin the setup process (Figure 2). Figure 2. Oracle's free VirtualBox provides a safe environment for testing software such as Windows 10. After the opening screen, VirtualBox will offer two Custom Setup dialog boxes, the first of which is shown in Figure 3. Technical Preview works fine with the default settings — make no changes; simply click Next in both dialog boxes. Figure 3. Accept the default settings for both this Custom Setup dialog box and the next. You’ll receive a warning that your network interfaces will be reset (Figure 4). VirtualBox requires this step to hook into your PC’s networking system and allow a VPC (guest) operating system — Win10, in this case — to go online. Figure 4. VirtualBox's warning that your network will be reset This network interruption is brief, but it will temporarily drop your Internet connection. Make sure you don’t have any tasks such as software downloads in progress. Click Yes to continue with the VirtualBox setup. Next, you’ll see a Ready to install confirmation screen. Click Install. From that point on, the process is mostly automated; you’ll simply be prompted to allow various permissions along the way. Grant the required permissions and accept all default settings — eventually, you’ll see a final dialog box (Figure 5) reporting that the VirtualBox installation is complete. Click Finish. Figure 5. Click the Finish button, and you're ready to set up a virtual PC. Step 2: Save time; start the Win10 download now Depending on the speed of your Internet connection, downloading Win10 Preview will take about 30 to 45 minutes (the ISO download files range in size from 2.91GB to 3.96GB). Configuring a virtual PC will take only a few minutes. So this is a good time to start downloading the Win10 Preview installation file. Let it download in the background while you set up the new Windows 10 VPC. Win10 Preview is free but requires that you have a Microsoft account and that you sign up for the also-free Windows Insider Program (site). Once that’s done, click the “Install Technical Preview” link, which takes you to the ISO-file download page. Select the language and bittedness (32 or 64) of your choice and click Download. If you’re currently running 64-bit Windows, you can download and run either the 32-bit or 64-bit version of Win10 Preview; if you have a 32-bit system, you can use only the 32-bit version. Note that there’s only one key — NKJFK-GPHP7-G8C3J-P6JXR-HQRJR — but you probably won’t need it. Keep in mind that an ISO image file is essentially an image of a DVD. VirtualBox can use a Win10 Preview installation file directly — you don’t have to burn the image to an optical disk or flash drive. Just leave it on your PC in an obvious place, such as the Downloads folder. Step 3: Create a new VPC for Win10 Preview The first time you launch VirtualBox, its main VirtualBox Manager will display a welcome screen (Figure 6). Begin the process of setting up a new virtual PC by clicking the blue New icon in the manager’s upper-left corner. Figure 6. Clicking New begins the process of creating a virtual machine. VirtualBox will now walk you through a series of setup screens. VPC name and OS: It’s best to keep virtual-machine names simple and obvious. In the following examples, I’ll set up a 64-bit version of Win10 Preview. So in the Name field, I’ve entered the utterly obvious title: Win10-64 Preview. Name your VPC as you like. Next, in the Type field, define the operating system: Microsoft Windows. Last, use this handy shortcut when selecting the Version. The Win10 Preview uses the same VirtualBox presets as does Win8.1. So if you downloaded the 32-bit Win10 Preview, select Windows 8.1 (32-bit); if you downloaded the 64-bit Win10 Preview, select Windows 8.1 (64-bit). Figure 7 shows my choice. Figure 7. Enter a name for the new Win10 VPC and then select Type and Version. When you’re done, click Next. Configure virtual memory size: In the “Create Virtual Memory” dialog box (Figure 8), make sure your Win10 VPC is assigned at least 1GB of RAM. More is better. Moving the slider control along the color-coded scale adjusts the amount of RAM available to the VPC. Keep the slider within the green section so that both the VPC and the host system have sufficient memory to run efficiently. Figure 8. Keeping the memory slider out of the orange and areas will ensure that the host system has sufficient RAM for its own operation. Click Next when you’re done. The rest of the configuration settings: You’ll next step through screens for Hard drive, Hard-drive file type, Storage on physical hard drive, and File location and size. Simply accept the default setting for each screen (“Create a virtual hard drive now,” “VDI,” “Dynamically allocated,” and “25GB” for the virtual-drive size). When you’re done, you’ll have created a basic, empty, and unmodified VPC — ready for a new operating system. Step 4: Two final, preinstallation tweaks By default, a new VPC will try to boot from its virtual hard drive. But the virtual drive for your VPC is currently empty. To install Win10 Preview on the empty drive, the VPC must first boot the downloaded ISO file, using a virtual optical drive. (At this point, however, the file is probably still downloading. Take a coffee break.) Selecting the VPC’s virtual optical drive takes only a few clicks — as does the other preinstallation tweak, choosing the VPC’s pointer. Let’s start with the pointer. Select the new Win10 VPC in VirtualBox Manager and click the Settings icon (the big orange gear), as shown in Figure 9. Figure 9. Click the Settings icon (the orange gear) in VirtualBox Manager. Click to the System section in the Settings window. Under the Motherboard tab, click the Pointing Device dropdown box and choose PS/2 Mouse, USB Tablet, or USB Multi-Touch Tablet, depending on what pointing device your host PC uses. I’m using a standard, mouse-based PC, so I’ve selected PS/2 Mouse (see Figure 10). Click OK once you’ve made your choice. Figure 10. Select the Pointing Device that your host system uses. You now have to tell VirtualBox to use the Win10 Preview installation (ISO) file. The process is effectively inserting a virtual setup DVD into the VPC’s virtual optical drive. (The next few steps are illustrated in Figure 11.) Click the main Settings icon again and select Storage. Next, in the Storage Tree box, under Controller: IDE, click Empty (#1 in Figure 11). New options will appear on the right side of the Storage screen. Now, under Attributes, tick the Live CD/DVD check box (#2) and then click the disc icon next to CD/DVD Drive: IDE Secondary Master (#3). A pop-up menu will appear; select Choose a virtual CD/DVD disk file (#4). Figure 11. The Win10 ISO is opened in a virtual CD/DVD drive. Follow the steps described in the text. That step opens a familiar, Explorer-like window. Navigate to the location of your downloaded ISO file — most likely in your Downloads folder — and select the file (typically labeled something similar to WindowsTechnicalPreview-x; see Figure 12). Click Open. Figure 12: Find and select the downloaded Win10 Preview .iso. You’ll then be returned to the Settings/Storage screen. Click OK. Note: As mentioned earlier, you might see a dialog box prompting you to install the VirtualBox Extension Pack. The Extension Pack is free and can be downloaded from the same VirtualBox.org page where you obtained the base VirtualBox installation file. Congratulations! The VPC setup is now complete; you’re ready to install and run Windows 10! Step 5: Installing Win10 Technical Preview In the VirtualBox Manager’s main menu, either double-click the Win10 VPC or select it and click the Start icon (Figure 13). Figure 13: Start the Win10 VPC to install and set up the new operating system. The VPC will now boot from the ISO installation file in the virtual DVD drive and launch Win10 Preview’s setup. Its initial screens will likely be familiar to you — they’re very similar to those of previous Windows versions. Note: Your first click inside the VPC’s window might trigger a VirtualBox message stating that your cursor will be temporarily captured within the window. This is normal. If or when you wish to navigate outside the VPC window, simply press the left (or, on some systems, the right) Ctrl key to return mouse control to the host PC. The first Win10 setup screen will ask you to confirm or change your language and keyboard type. Next, you’ll see a screen with an Install now button. Click it. You’ll then be asked to accept the license terms — do so. A Which type of installation do you want? dialog box will open. Select the Custom install, as shown in Figure 13 — that’s the correct option for setting up Win10 on a previously unused hard drive, such as the VPC’s. (Figure 14) Figure 14: Select Custom Install to set up Win10 on the VPC's empty hard drive. Click Next and accept the offered defaults from here on out; Win10 will go through a complete, from-scratch setup on your VPC’s hard drive. After some time, the VPC will reboot. Ignore the prompt to “Press any key to boot from the CD/DVD” and let the VPC boot normally from its hard drive. After the reboot, you’ll be stepped through a final series of Win10 settings (the defaults work fine) and personalization settings such as a request for your Microsoft Account credentials. If you don’t have an MS account — or you don’t want to use an existing account — you can create a new account on the fly, for free. The final setup options and features are self-explanatory; again, they’ll look familiar to Win8/8.1 users (more on this at the end of this article). When you’re done, Win10 will be up and running, ready for your test drive. If you selected a mouse-based pointing device, you’ll be taken directly to the Win10 Desktop, shown in Figure 15. Figure 15. If all goes well, you'll have Win10 Technical Preview up and running in a virtual PC. Note: Win10 Technical Preview has already had several updates. One of your first tasks should be to launch Windows Update. (Right-click the Windows-flag Start button and click Control Panel from the popup menu, click System and Security/Windows Update, and then click the Check for Updates link.) A bit of housecleaning for smoother boots At this point, your VPC is still set up to boot from the ISO-based installation file. If you leave things as is, you’ll get a “Press any key to boot from the CD/DVD” prompt every time your VPC starts up. To avoid this, you need to disconnect the ISO file from the virtual DVD drive. Doing so takes only a few simple steps. Shut down Win10 normally — i.e., right-click the Win10 Start button and select Shut down or sign out, then Shut down. When Win10 closes, you’ll be back at VirtualBox Manager. (Note: Most settings for a virtual PC can’t be changed while a virtual machine session is running.) With the Win10 VPC selected, click the VirtualBox Settings icon and navigate to the Storage section. (You’ve been there before; see Figure 11.) On the right-hand side of the Storage window, click the disc icon next to the IDE Secondary Master item. In the popup list of options, select Remove disk from virtual drive, as shown in Figure 16. Figure 16. Once Win10 is running properly, select Remove disk from virtual drive in VirtualBox's Storage menu. Click OK to close the Settings/Storage window. You’re done! Taking Windows 10 Technical Preview for a spin If you’re familiar with Windows 8, you’ll feel mostly at home with Win10 Technical Preview. The overall design is much the same but with many welcome improvements. For more information, see the “Highlights of the Windows 10 Technical Preview” subsection in the Oct. 9 Top Story, “Why you should join Win10′s tech-preview process.” If you’ve never used Win8, the new OS might be a bit baffling. Windows Secrets’ previous Win8/8.1 articles should help you find your way. Three good ones to start with: “How to spend your first hour with Windows 8.1″ – Oct. 3, 2013, Top Story “Touring through the final Windows 8.1″ – Sept. 19, 2013, Top Story “What you should know about Windows 8.1 Update” – April 3, 2014, Top Story Enjoy your Win10 Technical Preview test drive!
-
It’s official: Most people who tried Windows 10 ignored our warnings. Microsoft released some glowing Windows 10 stats on Monday. Already more than 1 million people have registered with Windows Insider to become a Windows 10 tester. Great! More than 200,000 suggestions or complaints have been filed via the Windows feedback app. Awesome! That’s what the Technical Preview’s for, after all. A full 64 percent of Windows 10 users installed the Preview straight to their hard drive. Wait. What? Granted, most people previewing Windows 10 in Technical Preview form are likely savvy computer users, but at this stage it’s still in a very early state, with bugs and rough edges. While Windows 10 is already more polished than most alpha software, using early pre-release operating systems is an invitation for catastrophe if any hiccups occur. The beauty of virtual machines is that you can just shut down the program and start over if disaster strikes. That’s why PCWorld’s Windows 10 installation guide recommends giving the operating system a whirl in a VM. But only a third of all Windows 10 testers listened, it seems. The Windows 10 Technical Machine running as a virtual machine. Maybe most of you aren’t afraid to nuke and reinstall Windows 10 repeatedly if need be. Maybe the kind of person enticed by the Windows 10 Technical Preview is the kind of person who has a spare PC or two lying around. Or maybe I’m just bitter after the ISO-less Windows 8.1 Preview refused to update to the full version after its release and left my work laptop borked for months. Either way, the fact that only 36 percent of Windows 10 installations occur in virtual machines made me do a double take. The precautions you need to take There’s no denying that operating systems run better straight from the metal rather than virtualized, however—at least if you’re using a consumer PC. And for all my preaching, after installing the Technical Preview in a VM on my personal machine I did overwrite Windows 8.1 with it on my work laptop. I’m a sucker for punishment, I guess. Fingers crossed it doesn’t break again! (Consider this my premature apology to the IT department if it does.) There are a couple precautionary steps you’ll want to take if you install the Windows 10 Technical Preview over your Windows 8.1 installation or on its own hard drive partition, however. First and foremost, back up your data. Load up an external hard drive, subscribe to Carbonite, whatever you need to do—just do it! You don’t want Windows 10 to burp and wipe out crucial files. PCWorld’s backup guide and introduction to free backup tools can help if you need it. Next, you’ll want to create a recovery drive for the operating system already on your PC. If you’re running Windows 7 or Vista, your PC’s maker hopefully included a recovery disc with the system, or a recovery partition on your hard drive. Skip down to the “Use your manufacturer’s recovery partition or discs (Windows 7 or earlier)” section of PCWorld’s How to reinstall Windows like a pro for details for more details. Creating a recovery drive in Windows 8. Windows 8 and 8.1 let you create your own recovery drive, however. Press the Windows key on your keyboard to land on the Start screen (the one with all the colorful tiles) and type “Recovery drive.” A list of search results will pop up on the right edge of your screen; select Create a recovery drive and follow the steps from there. It’s very straightforward. The vanilla option should fit on a 500MB flash drive, but if you’re backing up a retail PC with a recovery partition provided by the manufacturer, you’ll probably need a 16GB or larger USB drive. Be warned: Creating a Windows 8 recovery drive wipes any data you may have already had on the thumb drive. With backup and recovery drive in hand you’re ready to take the plunge and install the Windows 10 Technical Preview on your PC’s hard drive. Here’s hoping you never need to use the backups, but they’re invaluable if wonkiness does occur. If the mere idea of playing with pre-release operating systems makes you queasy, be sure to check out PCWorld’s pictorial guide to all the changes in the Windows 10 Preview.
-
- recovery
- windows 10
-
(and 1 more)
Tagged with: