-
Posts
7,278 -
Joined
-
Last visited
-
Days Won
2,416
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by allheart55 Cindy E
-
Update: Lenovo has now provided an official corporate statement about the Superfish situation and it is not going to help at all in my opinion. Original article... I think the conversation about the extras installed on OEM computers is about to heat up and one company we have to thank for that is the one in the hottest seat of them all – Lenovo and their Superfish story. Over on the Cigital Justice League Blog there is an excellent summary of just how bad this is: It is hard to overstate how catastrophically bad this design is. It doesn’t merely insert advertisements into web pages. It undermines every secure connection the Windows computer might make. Lots of software—way beyond web browsers—use the certificate store to fetch certificates. Cisco VPN clients use the Windows Certificate Store to verify that they’re talking to the right end point. Database consoles (like Toad or SQL Developer) will use Windows to verify that they are connected securely to the database server. Programs like TweetDeck will use the Windows Certificate Store to check the identity of Twitter before connecting. Everything on a Lenovo computer that says it is “making a secure connection” is now lying. Except maybe Firefox, which has its own trust store. The discussion around junk that comes pre-installed on a brand new computer has been going on for some time so the story itself is nothing new. However, to learn that Lenovo has installed this Superfish software on their brand new computers heading out the door to customers shakes trust to its core. To install a trusted certificate that breaks security on the system in so many ways is almost criminal. Any business worth their salt knows that trust is the cornerstone of a successful endeavor of any type but most definitely when it comes to any dealings with customers. No matter how great Lenovo’s hardware maybe, and they do make some awesome gear, this is going to impact a customer’s decision to buy a computer from them. When you place your bottom line above the trust of your customers then there will be fall out. Lenovo leadership is also failing this situation miserably. Back in January a Lenovo forums administrator, Mark Hopkins, posted this in their online support forums in response to the uproar about Superfish: “Superfish comes with Lenovo consumer products only and is a technology that helps users find and discover products visually. The technology instantly analyzes images on the web and presents identical and similar product offers that may have lower prices, helping users search for images without knowing exactly what an item is called or how to describe it in a typical text-based search engine. “Superfish technology is purely based on contextual/image and not behavioral. It does not profile nor monitor user behavior. It does not record user information. It does not know who the user is. Users are not tracked nor re-targeted. Every session is independent. When using Superfish for the first time, the user is presented the Terms of User and Privacy Policy, and has option not to accept these terms, i.e., Superfish is then disabled.” Interestingly enough Mark’s signature in the forums indicates he is the Program Manager for Lenovo’s Social Media Services but this social outreach has backfired beyond what he likely expected from the above post. It is a good example of what happens when you break the trust of your customers. At least they have now posted instructions on how to remove Superfish from these infected systems. So what needs to happen? Well first OEM’s must change this habit of bundling all the junk on computers but that is going to be difficult for them because first they have to acknowledge they have a problem. Right now they simply do not see it or they choose to ignore it. The reality is we will never know the dollar figure impact this bundling of junk has on their bottom line but there is only one reason they do it – because they make money from it. This is not done for the convenience of the customer – that may be what comes out of their mouths but it is not why they do it. The other half of this equation is the users. As a help desk support technician I see the everyday computer user and their computer issues. They are not like us and by us I mean those of us who stay connected to the tech community and know this junk comes on a new computer and needs to be removed. The vast majority of users operate their computer like an appliance such as their TV or microwave. They want to be able to hit the power switch and just have it work – period. So these users do not see the problem and are simply unaware of it. For that reason the idea of replacing the income an OEM makes from including all of this junk on their systems with a special fee to get a clean Windows machine would not likely work. Microsoft has a very popular program the Microsoft Signature PC Experience and this means you get your new computer or tablet with zero junk or extras on it. The cost of this is zero – nadda – zilch. The HP Stream 7 I picked up last week was offered under this service and it is such a treat to get a new system, go through the out of box experience and be ready to go – well short of installing published Windows updates. Here is my last comment on this and it is about perception. When users have issues with the junk pre-installed on their system the blame does not usually go towards the OEM – it is pointed at Windows. That means the company with the most at stake here is Microsoft and they should lead the efforts to remedy this issue as soon as possible. Thoughts? http://winsupersite.com/hardware/my-take-lenovo-oems-and-junkware-new-computers
-
By David Robinson on February 18, 2015 in Top Story Linux might not have found a comfortable home on the desktop, but for backend services, it’s everywhere. Here’s a guide to Linux, showing why intermediate and advanced Windows users might want to take a look at this open-source operating system. site) released a version that was acceptable to an average personal-computer user. But even then, its enhancements were well behind Apple’s rapidly developing OS X. While Microsoft struggled with antitrust issues, security concerns, engineering delays, and product flops through the 2000s, Apple positioned itself as the safe and stylish anti-Microsoft. With innovations such as the iPod and iPhone, Apple’s market capitalization surpassed Microsoft’s in 2010. Brilliant advertising campaigns defined consumer choices as being exclusively Windows versus Mac. And though Microsoft continued to dominate business computing, Apple clearly won the pop-culture battle. Google eventually made Linux — aka Android — the leader in the mobile market, but there was no deep-pocket champion for Linux on the desktop. Equally decisive was Microsoft’s aggressive marketing strategy against free and open-source software — especially Linux. During Microsoft’s bad old days, when many in the computing industry viewed it as an abusive monopoly, the folks in Redmond had good reason to fear Linux’s zero-cost licensing and early dominance on Web servers. Linux threatened Microsoft’s enterprise-software strategy, which envisioned tightly integrated Microsoft products on every computer, from servers to the desktop. Microsoft responded with a so-called “fear, uncertainty, and doubt” campaign (see Wikipedia page) targeting businesses that might be tempted by lower-cost Linux options. Microsoft was accused of buying off a major UNIX vendor, as recounted by Eric Raymond on his site. As reported in another Wikipedia article, Microsoft quietly backed UNIX vendor SCO in its intellectual-property battles against several Linux distributors and customers. Although SCO eventually went into bankruptcy, the disputes cast a very public shadow over the legal status of free and open-source software for much of the 2000s. Meanwhile, the fight for the enterprise market was accompanied by a lot of intemperate language. As reported in a July 31, 2000, The Register article, Microsoft’s Steve Ballmer equated Linux with “communism” and was quoted in a June 1, 2001, article, declaring that “Linux is a cancer.” Ostensibly, those terms might translate into: Communism: Linux and other free software are developed outside normal business models by volunteer developer communities. Cancer: Open-source code, if incorporated into any Microsoft product, would transform it into an open-source product as well — a possibility counter to Microsoft’s business model. These characterizations simply aren’t true. Much of the development work on the Linux kernel was — and still is — carried out by for-profit businesses such as Microsoft’s old nemesis, IBM. The view of Linux as a “cancer” is based on disputed interpretations of the operating system’s license. But that concern is mostly unfounded, according to a SitePoint article. (Under less restrictive licenses, Microsoft could incorporate open-source code into its products and still maintain its closed-source intellectual-property rights.) Ultimately, much of the invective against Linux disappeared with advances in server virtualization, which brought much-needed flexibility to IT operations. To be taken seriously in the enterprise, Microsoft’s own Hyper-V virtualization technology (more info) had to support alternative operating systems and open technical standards. The concept of locking in businesses to one technology vendor, famously espoused by IBM, is now a pipe dream — especially with the recent rise of cloud computing. Microsoft must now compete in a platform-independent market. Today, you can deploy a Linux system on Microsoft’s Azure cloud in minutes and never give a thought to Microsoft’s own server products. more info). The GPL requires the source code to be available to all users; allows modification, redistribution, and sale of the code or compiled versions; allows private use of modified code and compiled versions without restriction; and requires public release of modified code (also under the GPL) if modified and compiled versions are sold or given to the public. Linux itself is only a kernel — the core OS component that controls memory and other computer hardware functions. To be usable, it’s generally packaged together with the GNU (site) system libraries and utilities. It’s also combined with the X Window System (site), which provides a graphical environment similar to that of Windows or Mac OS X. Ready-to-use Linux packages are called distributions or “distros.” These are developed, maintained, and marketed by for-profit and not-for-profit organizations. Some of the best-known distributions are Red Hat, Debian, and Ubuntu. Though Linux carries no licensing fees, for-profit Linux companies make money by selling support services, primarily to business customers. While Windows reigns as the business PC of choice and Apple still claims the hearts of many writers, artists, and musicians, Linux is now the favored desktop system for programmers, IT professionals, and others who have very specialized requirements for their computers. Some of their priorities might overlap with yours. Here are some examples: Price: Yes, Linux can be acquired for free. A popular Linux-community saying is “Free as in freedom” or “Free as in beer.” Linux is both. That means you can download a Linux distribution and modify it as you like. Also, Linux distribution sites let you download it free of charge, burn it to a CD-ROM, install it on as many computers as you like, and make copies for friends. (The situation is somewhat different for enterprise users, who will in many cases also purchase a support contract.) Look and feel: Just as Windows and OS X appear and operate somewhat differently (they’re more alike than not), so do Linux distributions. Although each flavor of Linux has its own default user interface, most distributions also let you choose freely among alternative desktop designs. Depending on your personal-computing skills and tastes, this is either confusing or liberating. To greatly oversimplify, there are three broad approaches to look and feel in the Linux world. Microsoft/Apple clones: Macintosh begat Windows (arguably), and Windows begat desktop frameworks GNOME (site) and KDE (site) — plus dozens of other interfaces riding on them. Essentially, they all resemble what we thought of as Windows before Windows 8 came along. The native UNIX design tradition: Before Linux, this group of interfaces was used by UNIX-server admins and rarely seen in public. Stuffed with widgets, they offered useful ideas (such as virtual desktops, my favorite) that Microsoft and Apple have mostly deemed too confusing for their users. Mobile-inspired, touch-ready, cross-platform desktops: That was the mantra of Windows 8, but Linux got there first. (Apple is probably headed there, too.) You can see an example of each in the following screenshots. Figure 1. Linux Mint: For those who dislike Windows 8, the Cinnamon desktop updates the classic Windows look. Figure 2. Bodhi Linux: The Enlightenment menu option offers Unix specialties such as application docks and virtual desktops. Figure 3. Ubuntu Linux: Like Windows 8, the clean, blocky, touch-ready Unity desktop reflects the impact of mobile devices on interface design. Versatility: Linux is much more modular than Windows; you can install only those components of interest to you. You don’t have to accept a mass of unneeded software that takes up disk space, slows the system down, and opens security vulnerabilities. You also won’t have to contend with much-hated, preloaded, commercial “crapware” (all those trial versions of programs that pop up and nag you but which won’t truly work until you pay a license fee). Linux also runs happily on older hardware. If you have a working Windows XP computer that you want to update to something modern, chances are that a newer Windows version will run poorly — if at all. Linux will run just fine. Using older hardware also avoids one of the Linux limitations: possible lack of support for the latest cutting-edge hardware. Applications: The sketchy selection of popular consumer applications is still an issue for Linux. Web browsing isn’t a problem because Firefox and Chrome are fully supported. Email support has improved, in part due to the wide adoption of Web-based mail managers such as Gmail. But in most other application categories — graphics programs, word processors, spreadsheets, audio/video applications, and many others — familiar programs are missing. Fortunately, most of those apps can be replaced by satisfactory — often excellent — free/open software. Many have all the functions you’re expecting, but the severity of the learning curve will depend on your specific software needs and skills. (If you’re interested in programming, Linux’s tools are second to none.) Linux Mint Bodhi Linux Ubuntu Fedora Project http://windowssecrets.com/newsletter/an-introduction-to-linux-for-windows-users/
- 1 reply
-
- applications
- developement
-
(and 4 more)
Tagged with:
-
-

How Many Users Use These Windows Tools?
allheart55 Cindy E replied to donetao's topic in Tech Help and Discussions
Sure, I have. -

How Many Users Use These Windows Tools?
allheart55 Cindy E replied to donetao's topic in Tech Help and Discussions
I've used many of them over the years, some more often than others. -
We're all so used to buying a phone with intentions of using it on a carrier that we often don't consider what it will operate like without a SIM in it. Rest assured that your phone will operate just fine without active service from a carrier, leaving it as a Wifi-only device. Looking to order an unlocked [Galaxy Note 4] N910A off eBay. I'm moving in a couple of months, but where I live now I have no service at all so I'm wondering if I can use the phone's Wifi features in the mean time or do I need to activate it with a carrier before I can use any features at all? Whether you're buying to use the phone on Wifi permanently or just for a short period of time — perhaps while you're traveling abroad — you won't find many issues. Great apps like Hangouts will even let you make VoIP calls without any carrier involvement, provided you're able to find good Wifi connections. There are just a few things to be aware of when buying a phone to use without a carrier, though. Of course you're overpaying a bit for a device with cellular capabilities you aren't using, so consider weighing the difference in price between that unlocked phone and perhaps a small Wifi-only tablet. Also remember that phones use cellular connections to help with location information, so when you're out of the house without Wifi it's going to be a pain relying on just GPS with no data connection. And lastly, if you choose to buy a carrier-branded phone off-contract, you may run into issues getting software updates without an active SIM from that carrier in the phone. That being said, picking up an unlocked phone to use just on Wifi can be a great solution if you're not ready to pay monthly for a phone plan or just want a second phone around for a specific use! http://www.androidcentral.com/ask-ac-can-i-use-my-phone-just-wifi-without-carrier
-
Using a password manager is smart security. That’s nothing new. However, the best password managers keep your credentials locked behind a single "master" password that only you know. But what happens if you lose that master password? If you lose or forget your master password, getting in usually isn't as simple as just clicking a "forgot password" button, like you would for any other account on the web. In most cases, you have to jump through a few hoops—or you can't get it at all. In this post, we'll look at some of the popular password managers out there and what you can do to avoid getting into this sticky situation. Popular Password Managers and Their Master Password Policies When you start using a password manager, it’ll likely warn you that it's important to remember your master password. If there's any password you should be sure to remember, it's your master password. After all, that’s the whole point: It's easier to remember (or secure) one good, strong password and let it generate the rest for you. Depending on the password manager you choose, losing your master password can be easily remedied, or a nightmare to recover from. Here are some of the most popular, and how they handle lost master passwords. LastPass LastPass has a whole guide dedicated to account recovery if you've lost your master password. In short, if you've really forgotten or lost your password, you can activate a One Time Password (OTP) to access your vault. It'll work once (you'll have to reset your password afterward), and you'll need access to the email account you use for your LastPass account. If the issue is that you've recently changed your master password and can't get in, you can revert your vault to a previous state. You'll be able to get in using your old password, but any changes you've made since the old version are lost. Of course, all of this assumes you lost your master password, but you DO remember (or can access) the email account associated with LastPass, which may be a catch-22. If that doesn't work, or you no longer have access to that email address, you're sadly out of luck—and out of your account. You can delete your vault and start over, but your passwords will be lost and you'll need to start over from scratch. Dashlane Dashlane is a little more restrictive than LastPass, which is both a good and bad thing. In short, no one at Dashlane can access or grant access to your account. That means if you lose your master password, your vault is locked forever, even if it's synced across devices or saved in the cloud. If you use Dashlane's mobile apps and you have a device PIN set up (and you have the app set to only ask for your password when your phone restarts) you may be able to access your passwords long enough to write them down elsewhere. You can't change your master password from the mobile apps. Beyond that, your only option is to create a new account or reset your existing one (so you can reuse the same email address.) Doing that deletes all of the data in your account, though, so you're starting from scratch. This may seem draconian, but for a password manager, it's actually a good thing. While it may be inconvenient, it also means there's no way someone can socially engineer their way into your account. KeePass KeePass lets you secure your vault with a master password, a "key file," or both. Since your password vault is always stored on your computer, you never have to worry about a third party getting their hands on it. You can sync it across devices using Dropbox or Google Drive, but you still need your password or key file to open it. Here's the catch, though: Since KeePass is free, open-source, and not really supported by a central team, if you lose your master password or your key file, you're out of luck. There's no backdoor, no password reset feature, nothing. If you're locked out is because you changed your password and you have backups of your old vault, you can restore from backups and use the old password. There's more information on this here. Now, you might consider trying to crack your KeePass database. It's probably a bad idea. KeePass has built-in protection against brute force and cracking attempts, but there are tutorials that try to show you how to do it anyway. However, if your master password or key was strong (and it should be), most experts agree that there's no secret method that works, and it's really not worth the time and effort. It's an option, but we don't recommend it. 1Password 1Password's approach to your password vault is much like Dashlane's. They don't have access to your vault, or its encryption key, so there's no way for them to reset your password or grant you access to your data. They explain why here, and offer a few tips that might help here, but they boil down to the same ones as earlier: If you can restore from a backup where you know the password, do that, but any changes between then and now are lost. If you're logged in to 1Password on another device, you may be able to access your passwords and save them, but once you're asked to log in again, you'll be locked out. Similarly, 1Password doesn't support two-factor authentication for your account, so there's nothing to lose there (but also no added protection). Either way, the result is the same—lost your master password? You're out of luck. RoboForm Roboform has been in the business of password management for a long time, but if you forget your master password, you're just as out of luck as any other service. They explain in greater detail here, but the bottom line is this: If you're logged out of Roboform and you've forgotten your master password, you can reset it, but you'll delete all of your data in the process. If you have Roboform set up to always remember your master password, though, you'll never be in this situation (unless something happens to log you out, like a software update or a reinstall.) Roboform will let you password protect some things but not others once, but if you're logged out and can't log back in, you have to start from scratch. How to Keep This From Happening to You If you've noticed a theme, it’s that you’re pretty much screwed if you lose your password. Most password managers require you to either back up to when you knew the password, or start over. The best way to get into your password vault later is to prepare now. Here are a couple of things you can do, before it's too late: Write Down or Export Your Backup Codes/One-Time Passwords: Many password managers support backup codes and other one-time passwords that can be used in an emergency. Usually they're presented to you once, like when you set up an account, or when you generate them on-demand. They'll work as a method to change your password or get back into your account, but you have to write them down or keep them safe somewhere outside of your password vault. The process is similar to what happens if you lose your phone and you have two-factor authentication set up. If you export those codes and keep them somewhere safe now, you'll be able to access your data later. Write Your Master Password Down and Store It Somewhere Safe: We normally don't recommend writing a password down at all, since your master password is the key to all of your passwords. Don't keep it somewhere obvious, of course, but sometimes there's value in jotting down your password somewhere safe, just in case you forget it or something else crazy happens to it. You could even encrypt it in a file somewhere, but then you'll need the encryption key, and then you're headed down the rabbit hole of encrypting the things you need to decrypt the encrypted stuff. You could even write it on a slip of paper and put it in a fireproof safe, just in case something crazy happens and you forget what it is, but remember it's there. Make Use of Emergency Contacts: If your favorite password manager supports password sharing or emergency contacts, make sure you have an emergency contact set up. Dashlane, for example, supports emergency contacts who can access your vault if you're unable to. The feature is generally intended for things like medical emergencies, but it works just as well for forgotten passwords. They won't be able to reset your password and get you back in, but they will have access to your accounts—which is more than you'll have. With their help, you can write down, export, or reset your other passwords. Export Your Passwords Now, While You Have Access: It's important to choose services that give you "data freedom," or the ability to easily export your data and take it with you if they ever shut down, or if you want to try something new. Make sure your password manager gives you that option. Even if they don't, they should have some export ability, even if it just dumps a plain-text CSV of account user IDs and passwords on your desktop. If it does, export your data, and then save that file somewhere safe. There are obvious downsides here—any updates or password changes you make mean you'll have to dump a new file, and if the file is unencrypted, you'll probably want to put it somewhere secure, like a USB drive you can stash somewhere safe, or someplace encrypted through another method (which then introduces another password to the mix.) Still, having a dump of your passwords that's a few days old when you're locked out of your vault is better than having nothing at all. Back Up Your Data: In the same vein as backing up your password vault somewhere safe, make sure you back up your data in general. It's just good practice to have solid backups, but most password managers store your encrypted data locally. If you restore an old version of the app and its files, you can get in using an old password (you'll have an older version of your vault, but again, it's better than nothing.) This will only help you out if the issue is that you've changed your master password and you can't get in using it or the new one, but restoring an old version is a common tip from customer support for all of the popular password managers. Of course, the best time to prepare for losing your master password is before you lose it. It goes without saying that you should try not to forget or misplace your master password, even if you choose to back it up specifically somewhere safe. If you do, most of these methods will get you up and running in some state if something happens. Either way, it's important to remember that password managers aren't like your email account or your internet banking account—they won't just send you an email with a link to reset your password, after which everything is fine. Most assume that if you're prudent enough to secure all of your passwords, you're prudent enough to make sure you have continued access to your vault. http://lifehacker.com/what-to-do-if-you-lose-the-master-password-to-your-pass-1686432765
-

HP Print and Scan Doctor!!
allheart55 Cindy E replied to donetao's topic in Tech Help and Discussions
I've used this quite a few times before and it worked quite well in all cases. Thanks, Gary. -
I'm sorry to hear that, James. I didn't have the pleasure of knowing her but you obviously did. :(
-
-
Three sisters age 92, 94 and 96 live in a house together. One night the 96 year old ...draws a bath, puts her foot in and pauses. She yells down the stairs, "Was I getting in or out of the bath?" The 94 year old yells back, "I don't know, I'll come up and see." She starts up the stairs and pauses, then she yells, "Was I going up the stairs or coming down?" The 92 year old was sitting at the kitchen table having tea listening to her sisters. She shakes her head and says, "I sure hope I never get that forgetful." She knocks on wood for good measure. She then yells, "I'll come up and help both of you as soon as I see who's at the door."
-
Hello Jim and a Big WELCOME to Free PC Help Forum! We're very happy to have you aboard. Make yourself at home.
-
We may have a green rating now but it says..............
-
-
I have yet to see a 3 TB drive for this low price! Awesome deal.
- 4 replies
-
- 3tb drive
- hard drive
-
(and 1 more)
Tagged with:
-

There Are Thieves Among Us
allheart55 Cindy E replied to allheart55 Cindy E's topic in Tech Help and Discussions
Thanks, Gary! I'm happy to be back. :D -
Thank you, Gary! I just voted as well but we need more votes because not enough users have rated it. https://www.mywot.com/en/scorecard/freepchelp.forum
-
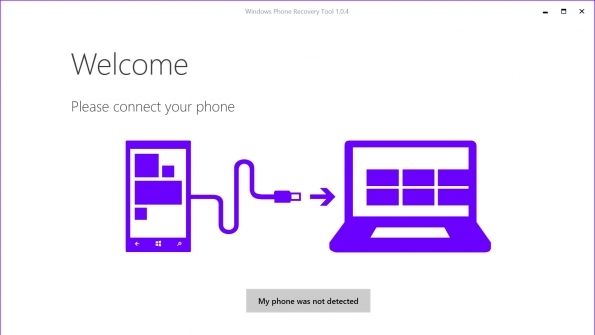
For some, installing and using the Windows 10 Technical Preview for Windows Phones has worked pretty well. But, for others, the ride has been a bit bumpy. Even handsets Microsoft reported to be supported for this first wave have had problems for one reason or another. Microsoft knew this would happen, so the company released a recovery tool along with the first Build so users can recover from frozen or trashed phones. Rollback functionality was promised and Microsoft delivered, however, the mechanism is a bit different than everyone originally thought. The Windows Phone Recovery Tool is designed as a PC application. It should run on most versions of Windows, but I've confirmed that it works on Windows 10 Technical Preview Build 9926, Windows 8.1, and Windows 7. So, instead of a function built directly into Windows 10 Technical Preview for phones, recovery requires that the Windows Phone be connected to an available USB port on a PC. The direct download: Windows Phone Recovery Tool While this direct download link is correct now, Microsoft could alter the download link and file name in the future, so it's best to use the link placeholder page on Microsoft's site if you have problems downloading it. Here it is… Having problems with your phone? Since the Windows Phone Recovery Tool is a PC application, you must connect your Windows Phone to your PC using a USB cable to start the restore process. The restoration is basically a wipe and replace scenario, so make sure you have good backup. Of course, you should already have already performed a backup before installing Windows 10 Technical Preview for phones on your supported device. You did do that, right? The restoration process erases all personal content and then restores the handset to the latest version of Windows Phone for your specific device. Here's a quick look at the application's other options… Settings – Preferences Make it pretty... Settings – Network For custom connection requirements... Settings – Troubleshooting Create a log file that can be delivered to support... http://winsupersite.com/windows-phone/windows-phone-recovery-tool-windows-10-technical-preview-phones
-
- microsoft
- recovery tool
-
(and 3 more)
Tagged with:
-
As I said on Paltalk, Wednesday night, I love the Comcast services, I just don't like the cost of the monthly bill.
-

The Best 500 GB SSd $179.99-24 hours only
allheart55 Cindy E replied to Rich-M's topic in Tech Help and Discussions
This was a great deal, Rich. I'm sorry I missed out on it! -

There Are Thieves Among Us
allheart55 Cindy E replied to allheart55 Cindy E's topic in Tech Help and Discussions
Thanks, Bob! I understand you went through it too. -

There Are Thieves Among Us
allheart55 Cindy E replied to allheart55 Cindy E's topic in Tech Help and Discussions
The hubcaps were one of my favorites! -
If we at Free PC Help Forum are gray then we all need to go vote so that we have a good rating.
-
I like these things. I never have a problem with reading them but then again, I do love to read!