-
Posts
27,570 -
Joined
-
Last visited
-
Days Won
73
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by AWS
-
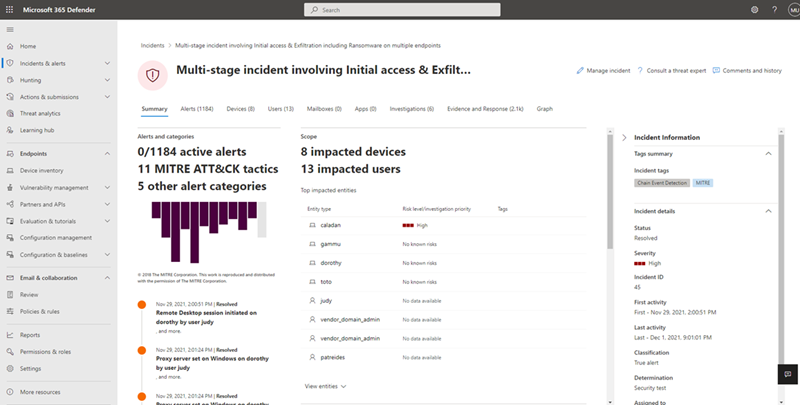
For the fourth year in a row, the independent MITRE Engenuity Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) Evaluations demonstrated Microsoft’s strong detection and protection capabilities thanks to our multi-platform extended detection and response (XDR) defenses. The ever-evolving threat landscape continues to deliver adversaries with new techniques, revamped tactics, and more advanced attack capabilities. Such threats demand comprehensive security solutions that provide a holistic view of the attack across endpoints and domains, prevent and block attacks at all stages, and provide security operations (SecOps) with automated tools to remediate complex threats and attackers in the network. This year’s ATT&CK Evaluations concentrated on advanced threat actors Wizard Spider and Sandworm. These actors are known for deploying sophisticated human-operated ransomware campaigns designed to destabilize infrastructure and institutions. The testing included detection benchmarks and protection simulations across platforms, such as Windows and Linux, of more than 100 steps and 66 unique ATT&CK techniques across the attack chain. We’re proud to report that Microsoft 365 Defender successfully detected and prevented malicious activity at every major attack stage, demonstrating comprehensive technique-level coverage across endpoints and identities. Rich threat intelligence synthesized from trillions of security signals on a daily basis proved key to informing both controls to be implemented in a Zero Trust approach and threat hunting. MITRE Engenuity’s ATT&CK Evaluations results emphasized that Microsoft’s success in this simulation was largely due to our: Industry-leading XDR. Microsoft 365 Defender simplified thousands of alerts into two incidents and a clear timeline spanning identity and endpoint to enable rapid resolution. Superior EPP and EDR. Microsoft Defender for Endpoint both prevented attacks and quickly identified and contained suspicious activities in the pre- and post-ransom phases to stop attacks. Comprehensive multi-platform protection. Microsoft 365 Defender demonstrated maturity in protecting multi-platform environments. In addition to Windows, Microsoft Defender for Endpoint’s behavioral and machine learning models blocked and detected every major step on Linux for the second year in a row. Figure 1. MITRE Engenuity’s ATT&CK Evaluation results demonstrated that Microsoft 365 Defender protects against ransomware with industry-leading XDR, EPP and EDR, and multi-platform protection. Microsoft defends against human-operated ransomware with industry-leading XDR One of the most prominent dangers in today’s threat landscape are human-operated ransomware campaigns, which leverage the playbook of advanced nation-state actors, where a threat actor actively targets one or more organizations using custom-built techniques for the target network. These campaigns also often involve encryption and exfiltration of high-value data, making it critical for security solutions to address the threat quickly and aggressively. If successful, human-operated ransomware attacks can cause catastrophic and visible disruption to organizations, their customers, and the rest of their communities. Protecting against these attacks requires a holistic security strategy that can resist a persistent attacker, including the ability to isolate and contain the threat to prevent widespread damage. As demonstrated in the evaluation, Microsoft 365 Defender protected against these sophisticated attacks with: Prevention at the earliest stages of the attack to stop further attacker activity without hindering productivity Diverse signal capture from devices and identities, with device-to-identity and identity-to-device signal correlation Coverage across device assets, including Windows, Linux, Mac, iOS, and Android Excellent pre-ransom and ransom protection for both automated remediation of the persistent threats and complete eviction of the attacker in network Integrated identity threat protection proves critical With human-operated ransomware, threat actors are constantly advancing their techniques. This year’s test included domain trust discovery activity, pass-the-hash, pass-the-ticket, and stealing credentials through Kerberoasting. Microsoft supports billions of identity authentications per day, and Microsoft 365 Defender has deep integration with both on-premises and cloud identities, thus enabling a level of detection and visibility that far exceeds what is possible with endpoint data alone and by fusing endpoint and identity data. Microsoft 365 Defender protects hundreds of millions of customer identities today, and the integration of identity threats into the events timeline was instrumental in detections during evaluation. Aggregating alerts into prioritized incidents streamlined the investigation experience Microsoft 365 Defender streamlined the investigation experience by correlating more than a thousand alerts into significant incidents and identified complex, seemingly unrelated links between attacker activities across various domains. Time to remediate is critical in a ransomware attack, and Microsoft 365 Defender’s incidents page simplifies the SecOps experience by providing essential context on active alerts, key devices, and impacted users. It also allows defenders to enable both automatic and manual remediations that offer insightful and actionable alerts, rather than filtering through unrelated events that can add strain on resources, particularly during an existing attack. EDR further enables analysts to approach investigations through multiple vectors, providing detailed behavioral telemetry that includes process information, network activities, kernel and memory manager deep optics, registry and file system changes, and user login activities to determine the start and scale of an attack. Figure 2. Microsoft 365 Defender’s incidents page correlating all the devices, users, alerts, and evidence that describe the attack simulated by MITRE Engenuity. Microsoft 365 Defender delivers mature multi-platform protection The attack scenario mimicked a threat actor’s ability to target heterogeneous environments and spread across platform ecosystems. We’re proud to state that Microsoft 365 Defender’s security capabilities provided superior detection and protection and complete Linux coverage for the second consecutive year. Microsoft 365 Defender offers comprehensive capabilities across the popular desktop and mobile operating systems, such as Linux, Mac, Windows, iOS, and Android. These capabilities include next-generation antivirus, EDR, and behavioral and heuristic coverage across numerous versions of Linux. Microsoft has invested heavily in protecting non-Windows platforms in the last four years and, today, offers the extensive capabilities organizations need to protect their networks. Microsoft takes a customer-centered approach to tests The evolving threat landscape demands security solutions with wide-ranging capabilities, and we’re dedicated to helping defenders combat such threats through our industry-leading, cross-domain Microsoft Defender products. Microsoft’s philosophy in this evaluation is to empathize with our customers, so we configured the product as we would expect them to. For example, we didn’t perform any real-time detection tuning that might have increased the product’s sensitivity to find more signals, as it would have further created an untenable number of false positives if in a real-world customer environment. We thank MITRE Engenuity for the opportunity to contribute to and participate in this year’s evaluation. Learn more For more information about human-operated ransomware and how to protect your organization from it, refer to the following articles: Human-operated ransomware Rapidly protect against ransomware and extortion Take advantage of Microsoft’s unrivaled threat optics and proven capabilities. Learn more about Microsoft 365 Defender or Microsoft Defender for Endpoint, and sign up for a trial today. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. The post Microsoft protects against human-operated ransomware across the full attack chain in the 2022 MITRE Engenuity ATT&CK® Evaluations appeared first on Microsoft Security Blog. Continue reading...
-
- 1
-

-
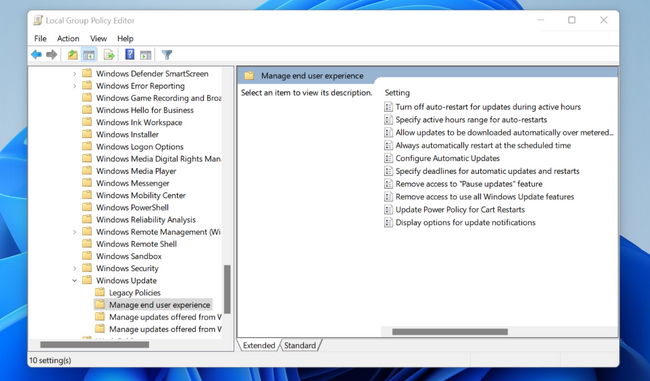
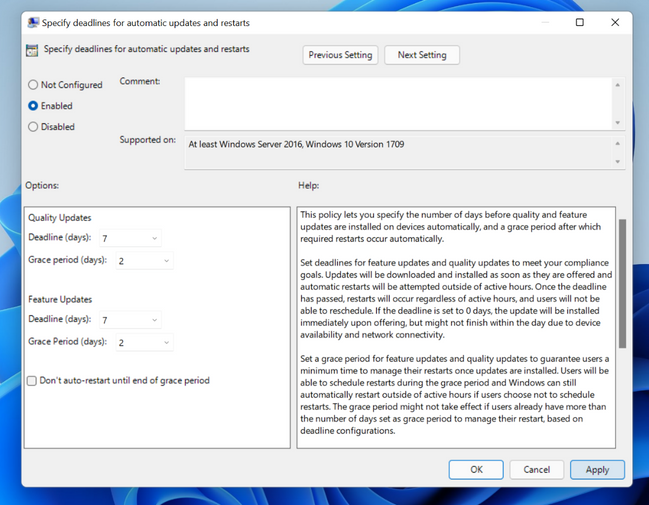
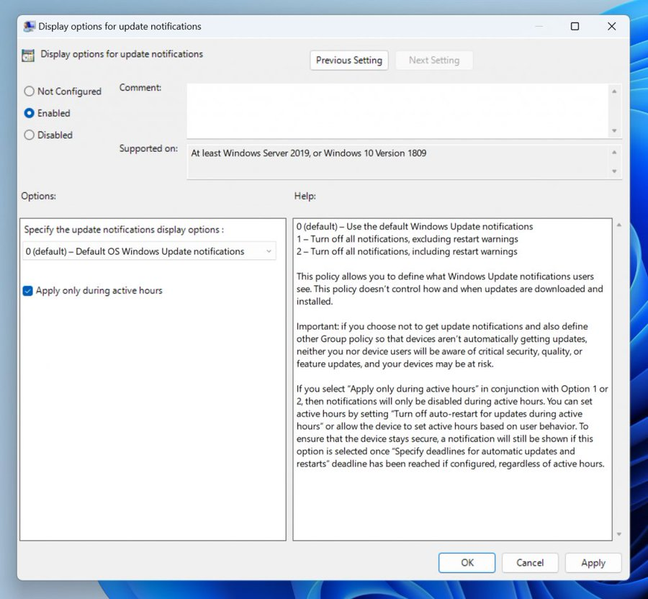
Welcome to an easy, go-to reference to help you manage single-user devices, multi-user devices, education devices, kiosks, billboards, factory machines, and more. In my January 19th blog on why you shouldn't set these 25 Windows policies, I shared how the Windows update experience has evolved over the last few years, how that impacts the Windows update policies we recommend, and a list of which Windows update policies you should not set and why. Driven by your feedback, I now want to share a list of the policies you should be setting and offer insight on why those policies can be helpful when managing updates for a variety of use cases, specifically: Single-user or personal devices Multi-user devices Education devices Kiosks and billboards Factory machines, rollercoasters, and similar things Microsoft Teams Rooms devices Leverage the defaults Let's start with the basics. Our recommendation? The fewer policies, the better. Leverage the defaults! The default experience is often the best experience for ensuring that users remain productive and that their device(s) remain secure. By default, devices will scan daily, automatically download and install any applicable updates at a time optimized to reduce interference with usage, and then automatically try to restart when the end user is away. For most scenarios, this is the best experience. In fact, it is also what hundreds of millions of Windows users experience on their home or personal computers. That said, below you will find some common use cases we see in various organizations with a list of additional supported controls you may want to leverage in order to meet that scenario's specific user experience requirements. All policies discussed below can be found in the following paths: Group Policy path: …/Windows Components/Windows Updates/Manage end user experience CSP database: Policy CSP - Update Policy settings for managing the end user experience as they appear under Windows Update settings in the Local Group Policy Editor Managing single-user devices Single-user devices are user-owned or corporate-owned devices used by a single person. In addition to personal computing tasks, these devices might also be used for hybrid work activities including meetings, presentations, and any number of other tasks. For any of these tasks, interruption would hinder productivity. Given that these devices are often connecting to corporate network(s) and accessing sensitive information, it is imperative they stay secure. Given that heightened need for security, there are some supported policies that should be considered. This scenario may require: Fewer disruptions during the workday or when actively using the device. Device can't be taken down during meetings and/or presentations. All data must be saved. Want to have some level of control over their device. Devices must meet a specific compliance standard. Note: All the requirements, outside of ensuring devices meet a specific compliance standard, are achieved by the default experience. Policy Description When to set it and why GP name: Specify deadlines for automatic updates and restarts GP setting name): For quality updates: Deadline (days), Grace period (days) For feature updates: Deadline (days), Grace period (days) CSP names: For quality updates: ConfigureDeadlineForQualityUpdates, ConfigureDeadlineGracePeriod For feature updates: ConfigureDeadlineForFeatureUpdates, ConfigureDeadlineGracePeriodForFeatureUpdates This policy allows you to specify the number of days before an update is forced to install on the device during active hours, when the user may be present. This policy is always recommended for commercial or education environments where there is a compliance need or where it is pertinent that devices stay secure. Note: Security is paramount from our point of view, and deadlines are a great way to ensure such. Specifying deadlines for automatic updates and restarts through policy Multi-user devices Multi-user devices are shared devices that are used by multiple people over a period of time. This is a common scenario especially for devices like a HoloLens or a PC that is being used in a laboratory or library setting. For these devices, there may be a set period when they are able to be used. For example, if they are plugged in overnight in a laboratory that doesn't allow access post 12AM, you could confidently update them at that time. Additionally, you likely don't want to have the end user schedule the update as they may inconveniently schedule it during a time another user is present, which would result in a poor experience. This scenario may require: Few to no notifications during the period of use. No automatic reboots during the period of use. End user(s) shouldn't be able to schedule the reboot. Scheduling automatic wake and reboot for a specific time. Devices to stay secure and protected. Note: Most of the above can be achieved through the default experience with no policies configured. That said, if the default experience is not meeting your needs, you can consider the following. Policy Description When to set it and why GP name: Configure Automatic Updates GP setting name: Schedule install time: Daily at X time CSP names: AllowAutoUpdate = 3, ScheduledInstallTime This policy enables you to manage automatic update behavior. Schedule install time (3) restricts the device to installing at that specified time until deadline is reached. If the policy is not configured, end-users get the default behavior (Auto install and restart). If no day and time are specified, the default is 3 AM daily. This policy is only recommended if there is a regular specific window when the multi-user device will not be in use. GP name: Remove access to use all Windows Update features GP setting name: Not applicable CSP name: Update/SetDisableUXWUAccess This policy will remove the end user’s ability to scan, download, or install from the Windows Update settings page. This policy is only recommended if you have end users who are configuring update settings and causing update behaviors that are disrupting other users who share the device. GP name: Turn off auto-restart for updates during active hours GP setting name: Active hours: Start, End CSP names: ActiveHoursStart, ActiveHoursEnd This policy enables you to specify the hours during which a device should not restart. This overrides the default intelligent active hours, calculated on the device based on user usage. We recommend that you simply leverage the default, built-in intelligent active hours that are calculated on the device. That said, you can leverage this policy if you feel it necessary and if there is a set period of time during which the device is allowed to be used or during which reboots are unacceptable. For example, if this is a device in a library or a lab, and you are finding intelligent active hours not to be meeting your needs, you may want to set active hours to the working hours of that building to ensure the device doesn’t update until it is no longer in use. GP name: Specify deadlines for automatic updates and restarts GP setting name): For quality updates: Deadline (days), Grace Period (days) For feature updates: Deadline (days), Grace Period (days) CSP names: For quality updates: ConfigureDeadlineForQualityUpdates, ConfigureDeadlineGracePeriod For feature updates: ConfigureDeadlineForFeatureUpdates, ConfigureDeadlineGracePeriodForFeatureUpdates This policy allows you to specify the number of days before an update is forced to install on the device during active hours, when the user may be present. This policy is always recommended for commercial or education environments where there is a compliance need or where it is pertinent that devices stay secure. Note: Security is paramount from our point of view and deadlines are a great way to ensure such. Education devices Education devices are single user or shared devices that are leveraged by students and teachers in a school setting. This encompasses both personal devices and those that may be stored in a computer cart in the classroom for shared use. For this scenario, any form of notification may be extremely disruptive in a classroom setting. This scenario may require: No notifications during the school day. No automatic reboots during the school day. Devices to stay secure and protected. Note: While not automatically rebooting during the school day can likely be achieved by the default settings, you may want to consider the following to ensure devices stay protected and to prevent notifications during the school day. Policy Description When to set it and why GP name: Display options for update notifications GP setting name: Turn off notifications. Check the box for “Apply only during active hours" CSP names: UpdateNotificationLevel, NoUpdateNotificationsDuringActiveHours (currently only in Active Branch) This policy allows you to define what Windows Update notifications users see, including the ability to turn off all notifications, including restart warnings. “Apply only during active hours” results in notifications only being turned off during active hours. The ability to “Apply only during active hours” is new and is currently only available to devices in the Windows Insider Program for Business leveraging the Dev or Beta channels. This policy enables you to turn off Windows update notifications during active hours only. Please try out the experience in the Beta Channel and provide feedback! For those on Windows 10 or Windows 11, version 21H2 devices, we do not recommend configuring this and instead recommend leveraging the default experience. GP name: Specify deadlines for automatic updates and restarts GP setting name): For quality updates: Deadline (days), Grace Period (days) For feature updates: Deadline (days), Grace Period (days) CSP names: For quality updates: ConfigureDeadlineForQualityUpdates, ConfigureDeadlineGracePeriod For feature updates: ConfigureDeadlineForFeatureUpdates, ConfigureDeadlineGracePeriodForFeatureUpdates This policy allows you to specify the number of days before an update is forced to install on the device during active hours, when the user may be present. This policy is always recommended for commercial or education environments where there is a compliance need or where it is pertinent that devices stay secure. Note: Security is paramount from our point of view and deadlines are a great way to ensure such. GP name: Turn off auto-restart for updates during active hours GP setting name: Active hours: Start, End CSP names: ActiveHoursStart, ActiveHoursEnd This policy enables you to specify the hours during which a device should not restart. This overrides the default intelligent active hours, calculated on the device based on user usage. We recommend that you simply leverage the default, built-in intelligent active hours that are calculated on the device. That said, you can leverage this policy if you feel it necessary and if there is a set period of time during which the device is allowed to be used or during which reboots are unacceptable. For example, if this is a device in a library or a lab, and you are finding intelligent active hours not to be meeting your needs, you may want to set active hours to the working hours of that building to ensure the device doesn’t update until it is no longer in use. Display options for end user update notifications Kiosks and billboards Kiosks are simple user interfaces that can be used without training or documentation to accomplish a specific task or get information. An example would be an automated teller machine (ATM). These devices are often left unattended for long periods of time, meaning that there is no end user there to interact with or trigger a reboot. Similarly, billboards, which convey information, are often meant to display or get interaction from the end user, but do not have an end user who is interacting with the update(s). Nevertheless, these devices need to stay secure and up to date, although without end users walking or driving by seeing “Restart now” notifications across the screen. This scenario may require: No notifications. No automatic reboots during certain periods. Scheduling the reboot for a specific time during low visibility/usage. No end user interaction. Note: By default, the device will automatically restart outside of active hours, after installation is complete. However, to ensure there are no notification disruptions, we recommend the following be configured. Policy Description When to set it and why GP name: Display options for update notifications GP setting name: Turn off notifications CSP names: UpdateNotificationLevel This policy allows you to define what Windows Update notifications users see. This includes the ability to turn off all notifications, including restart warnings. This policy is recommended for devices that do not have active end users, where notifications can be disruptive and serve no purpose (such as kiosks and billboards). GP name: Configure Automatic Updates GP setting name: Schedule install time: Daily at X time CSP names: AllowAutoUpdate = 3, ScheduledInstallTime This policy enables you to manage automatic update behavior. Schedule install time (3) restricts the device to installing at that specified time until deadline is reached. If the policy is not configured, the device will follow the default behavior (Auto install and restart). If no day and time are specified, the default is 3 AM daily. This policy is available for use when there is a specific period when there is either low usage or visibility of the kiosk or billboard. That said, you can achieve a similar result through configuring Active Hours (see next line). GP name: Turn off auto-restart for updates during active hours GP setting name: Active hours: Start, End CSP names: ActiveHoursStart, ActiveHoursEnd This policy enables you to specify the hours during which a device should not restart. This overrides the default intelligent active hours, calculated on the device based on usage. You can configure active hours to the window when the device is most likely in use or visible. This will ensure that reboots occur outside of that window when it is likely to cause less disruption. GP name: Specify deadlines for automatic updates and restarts GP setting name): For quality updates: Deadline (days), Grace Period (days) For feature updates: Deadline (days), Grace Period (days) CSP names: For quality updates: ConfigureDeadlineForQualityUpdates, ConfigureDeadlineGracePeriod For feature updates: ConfigureDeadlineForFeatureUpdates, ConfigureDeadlineGracePeriodForFeatureUpdates This policy allows you to specify the number of days before an update is forced to install on the device during active hours, when the user may be present. This policy is always recommended for commercial or education environments where there is a compliance need or where it is pertinent that devices stay secure. Note: Security is paramount from our point of view and deadlines are a great way to ensure such. Factory machines, rollercoasters, and similar things There are some devices that we often don't even think of as needing to update, unless we are the ones managing them. Machines on the factory floor, rollercoasters at amusement parks, and other critical infrastructure can all require updates. Given the criticality of these devices, it is pivotal that they stay secure, stay functional, and are not interrupted in the middle of a task. Often these are some of the devices in the final wave when rolling out an update after everything else has been validated. This scenario may require: End user initiating an update or updating at a specific time. No automatic reboots – ever. Note: This is one of the only use cases where compliance deadlines are not recommended given automatic updates are never acceptable in this scenario. Policy Description When to set it and why GP name: Configure Automatic Updates GP setting name: Schedule install time: Daily at X time OR Notify to download / Notify to Install CSP names: AllowAutoUpdate = 3, ScheduledInstallTime OR AllowAutoUpdate = 0 This policy enables you to manage automatic update behavior. Schedule install time (3) restricts the device to installing at that specified time until the deadline is reached. Notify to download (0) will require the end user to take action (via notifications or the settings page) to download the update. The schedule install policy is recommended for use when there is a specific period when the device is not in use. Notify to download or Notify to install is only recommended in scenarios where any unexpected updates not triggered by an end user have negative consequences. Note: If full control is needed, you can also disable automatic updates by disabling this policy the end user will have to manually kick off scans, downloads, installs, and restarts. This is only recommended in specific cases which require high touch management of updates. This puts the device at high risk of becoming insecure and missing updates. Microsoft Teams Rooms devices Microsoft Teams Rooms are actively managed by Microsoft “out-of-box". This enables you to have a hands-off approach where no policies are needed for Microsoft Teams Rooms to successfully stay up to date with validated updates. By default, only updates that Microsoft has validated will be offered to the device and will be automatically installed. We recommend against configuring any policies on a Microsoft Teams Rooms device, especially any offering policies, as they are likely to conflict with what the Microsoft Teams Rooms management has already put in place. These conflicts can lead to a degradation of experience. Learn more about Microsoft Teams Rooms update management. Conclusion The above are just some of the common use cases we hear about from organizations like yours. For those of you interested in Windows update management recommendations for servers, stay tuned! And don't forget to leverage the defaults! We are always learning and trying to improve. To that end, please let us know if there are gaps in the capabilities that we are providing. Additionally, if you have questions or see a use case missing that you want guidance on, please just drop a comment below, message me at @ariaupdated on Twitter, or ask us questions during the next Windows Office Hours! Continue the conversation. Find best practices. Visit the Windows Tech Community. Stay informed. For the latest updates on new releases, tools, and resources, stay tuned to this blog and follow us @MSWindowsITPro on Twitter. Continue reading...
-
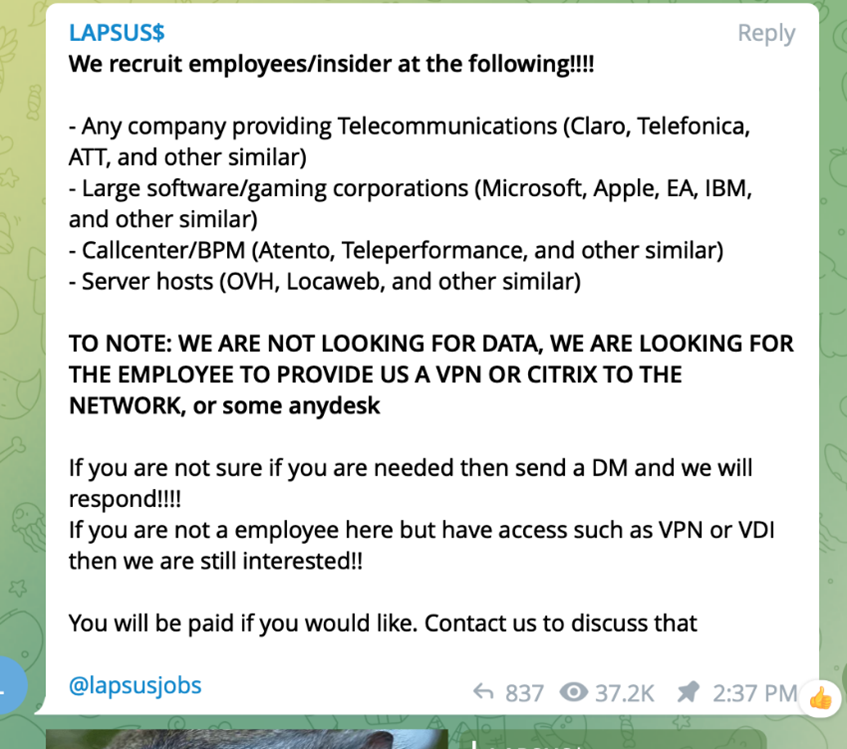
In recent weeks, Microsoft Security teams have been actively tracking a large-scale social engineering and extortion campaign against multiple organizations with some seeing evidence of destructive elements. As this campaign has accelerated, our teams have been focused on detection, customer notifications, threat intelligence briefings, and sharing with our industry collaboration partners to understand the actor’s tactics and targets. Over time, we have improved our ability to track this actor and helped customers minimize the impact of active intrusions and in some cases worked with impacted organizations to stop attacks prior to data theft or destructive actions. Microsoft is committed to providing visibility into the malicious activity we’ve observed and sharing insights and knowledge of actor tactics that might be useful for other organizations to protect themselves. While our investigation into the most recent attacks is still in progress, we will continue to update this blog when we have more to share. The activity we have observed has been attributed to a threat group that Microsoft tracks as DEV-0537, also known as LAPSUS$. DEV-0537 is known for using a pure extortion and destruction model without deploying ransomware payloads. DEV-0537 started targeting organizations in the United Kingdom and South America but expanded to global targets, including organizations in government, technology, telecom, media, retail, and healthcare sectors. DEV-0537 is also known to take over individual user accounts at cryptocurrency exchanges to drain cryptocurrency holdings. Unlike most activity groups that stay under the radar, DEV-0537 doesn’t seem to cover its tracks. They go as far as announcing their attacks on social media or advertising their intent to buy credentials from employees of target organizations. DEV-0537 also uses several tactics that are less frequently used by other threat actors tracked by Microsoft. Their tactics include phone-based social engineering; SIM-swapping to facilitate account takeover; accessing personal email accounts of employees at target organizations; paying employees, suppliers, or business partners of target organizations for access to credentials and multifactor authentication (MFA) approval; and intruding in the ongoing crisis-communication calls of their targets. The social engineering and identity-centric tactics leveraged by DEV-0537 require detection and response processes that are similar to insider risk programs–but also involve short response timeframes needed to deal with malicious external threats. In this blog, we compile the tactics, techniques, and procedures (TTPs) we’ve observed across multiple attacks and compromises. We also provide baseline risk mitigation strategies and recommendations to help organizations harden their organization’s security against this unique blend of tradecraft. Analysis The actors behind DEV-0537 focused their social engineering efforts to gather knowledge about their target’s business operations. Such information includes intimate knowledge about employees, team structures, help desks, crisis response workflows, and supply chain relationships. Examples of these social engineering tactics include spamming a target user with multifactor authentication (MFA) prompts and calling the organization’s help desk to reset a target’s credentials. Microsoft Threat Intelligence Center (MSTIC) assesses that the objective of DEV-0537 is to gain elevated access through stolen credentials that enable data theft and destructive attacks against a targeted organization, often resulting in extortion. Tactics and objectives indicate this is a cybercriminal actor motivated by theft and destruction. While this actor’s TTPs and infrastructure are constantly changing and evolving, the following sections provide additional details on the very diverse set of TTPs we have observed that DEV-0537 is using. Initial access DEV-0537 uses a variety of methods that are typically focused on compromising user identities to gain initial access to an organization including: Deploying the malicious Redline password stealer to obtain passwords and session tokens Purchasing credentials and session tokens from criminal underground forums Paying employees at targeted organizations (or suppliers/business partners) for access to credentials and MFA approval Searching public code repositories for exposed credentials Using the compromised credentials and/or session tokens, DEV-0537 accesses internet-facing systems and applications. These systems most commonly include virtual private network (VPN), remote desktop protocol (RDP), virtual desktop infrastructure (VDI) including Citrix, or Identity providers (including Azure Active Directory, Okta). For organizations using MFA security, DEV-0537 used two main techniques to satisfy MFA requirements–session token replay and using stolen passwords to trigger simple-approval MFA prompts hoping that the legitimate user of the compromised account eventually consents to the prompts and grants the necessary approval. In some cases, DEV-0537 first targeted and compromised an individual’s personal or private (non-work-related) accounts giving them access to then look for additional credentials that could be used to gain access to corporate systems. Given that employees typically use these personal accounts or numbers as their second-factor authentication or password recovery, the group would often use this access to reset passwords and complete account recovery actions. Microsoft also found instances where the group successfully gained access to target organizations through recruited employees (or employees of their suppliers or business partners). DEV-0537 advertised that they wanted to buy credentials for their targets to entice employees or contractors to take part in its operation. For a fee, the willing accomplice must provide their credentials and approve the MFA prompt or have the user install AnyDesk or other remote management software on a corporate workstation allowing the actor to take control of an authenticated system. Such a tactic was just one of the ways DEV-0537 took advantage of the security access and business relationships their target organizations have with their service providers and supply chains. In other observed activity, DEV-0537 actors performed a SIM-swapping attack to access a user’s phone number before signing into the corporate network. This method allows the actors to handle phone-based authentication prompts they need to gain access to a target. Once standard user credentials or access was obtained, DEV-0537 typically connected a system to an organization’s VPN. In some cases, to meet conditional access requirements, DEV-0537 registered or joined the system to the organization’s Azure Active Directory (Azure AD). Reconnaissance and privilege escalation Once DEV-0537 obtained access to the target network using the compromised account, they used multiple tactics to discover additional credentials or intrusion points to extend their access including: Exploiting unpatched vulnerabilities on internally accessible servers including JIRA, Gitlab, and Confluence Searching code repositories and collaboration platforms for exposed credentials and secrets They have been consistently observed to use AD Explorer, a publicly available tool, to enumerate all users and groups in the said network. This allows them to understand which accounts might have higher privileges. They then proceeded to search collaboration platforms like SharePoint or Confluence, issue-tracking solutions like JIRA, code repositories like GitLab and GitHub, and organization collaboration channels like Teams or Slack to discover further high-privilege account credentials to access other sensitive information. DEV-0537 is also known to exploit vulnerabilities in Confluence, JIRA, and GitLab for privilege escalation. The group compromised the servers running these applications to get the credentials of a privileged account or run in the context of the said account and dump credentials from there. The group used DCSync attacks and Mimikatz to perform privilege escalation routines. Once domain administrator access or its equivalent has been obtained, the group used the built-in ntdsutil utility to extract the AD database. In some cases, DEV-0537 even called the organization’s help desk and attempted to convince the support personnel to reset a privileged account’s credentials. The group used the previously gathered information (for example, profile pictures) and had a native-English-sounding caller speak with the help desk personnel to enhance their social engineering lure. Observed actions have included DEV-0537 answering common recovery prompts such as “first street you lived on” or “mother’s maiden name” to convince help desk personnel of authenticity. Since many organizations outsource their help desk support, this tactic attempts to exploit those supply chain relationships, especially where organizations give their help desk personnel the ability to elevate privileges. Exfiltration, destruction, and extortion Based on our observation, DEV-0537 has dedicated infrastructure they operate in known virtual private server (VPS) providers and leverage NordVPN for its egress points. DEV-0537 is aware of detections such as impossible travel and thus picked VPN egress points that were geographically like their targets. DEV-0537 then downloaded sensitive data from the targeted organization for future extortion or public release to the system joined to the organization’s VPN and/or Azure AD-joined system. DEV-0537 has been observed leveraging access to cloud assets to create new virtual machines within the target’s cloud environment, which they use as actor-controlled infrastructure to perform further attacks across the target organization. If they successfully gain privileged access to an organization’s cloud tenant (either AWS or Azure), DEV-0537 creates global admin accounts in the organization’s cloud instances, sets an Office 365 tenant level mail transport rule to send all mail in and out of the organization to the newly created account, and then removes all other global admin accounts, so only the actor has sole control of the cloud resources, effectively locking the organization out of all access. After exfiltration, DEV-0537 often deletes the target’s systems and resources. We’ve observed deletion of resources both on-premises (for example, VMWare vSphere/ESX) and in the cloud to trigger the organization’s incident and crisis response process. The actor has been observed then joining the organization’s crisis communication calls and internal discussion boards (Slack, Teams, conference calls, and others) to understand the incident response workflow and their corresponding response. It is assessed this provides DEV-0537 insight into the victim’s state of mind, their knowledge of the intrusion, and a venue to initiate extortion demands. Notably, DEV-0537 has been observed joining incident response bridges within targeted organizations responding to destructive actions. In some cases, DEV-0537 has extorted victims to prevent the release of stolen data, and in others, no extortion attempt was made and DEV-0537 publicly leaked the data they stole. Impact Early observed attacks by DEV-0537 targeted cryptocurrency accounts resulting in compromise and theft of wallets and funds. As they expanded their attacks, the actors began targeting telecommunication, higher education, and government organizations in South America. More recent campaigns have expanded to include organizations globally spanning a variety of sectors. Based on observed activity, this group understands the interconnected nature of identities and trust relationships in modern technology ecosystems and targets telecommunications, technology, IT services and support companies–to leverage their access from one organization to access the partner or supplier organizations. They have also been observed targeting government entities, manufacturing, higher education, energy, retailers, and healthcare. Microsoft will continue to monitor DEV-0537 activity and implement protections for our customers. The current detections and advanced detections in place across our security products are detailed in the following sections. Actor actions targeting Microsoft This week, the actor made public claims that they had gained access to Microsoft and exfiltrated portions of source code. No customer code or data was involved in the observed activities. Our investigation has found a single account had been compromised, granting limited access. Our cybersecurity response teams quickly engaged to remediate the compromised account and prevent further activity. Microsoft does not rely on the secrecy of code as a security measure and viewing source code does not lead to elevation of risk. The tactics DEV-0537 used in this intrusion reflect the tactics and techniques discussed in this blog. Our team was already investigating the compromised account based on threat intelligence when the actor publicly disclosed their intrusion. This public disclosure escalated our action allowing our team to intervene and interrupt the actor mid-operation, limiting broader impact. Recommendations Strengthen MFA implementation Multifactor authentication (MFA) is one of the primary lines of defense against DEV-0537. While this group attempts to identify gaps in MFA, it remains a critical pillar in identity security for employees, vendors, and other personnel alike. See the following recommendations to implement MFA more securely: Do: Require Multifactor Authenticator for all users coming from all locations including perceived trusted environments, and all internet-facing infrastructure–even those coming from on-premises systems. Leverage more secure implementations such as FIDO Tokens, or the Microsoft Authenticator with number matching. Avoid telephony-based MFA methods to avoid risks associated with SIM-jacking. Use Azure AD Password Protection to ensure that users aren’t using easily-guessed passwords. Our blog about password spray attacks outlines additional recommendations. Leverage passwordless authentication methods such as Windows Hello for Business, Microsoft Authenticator, or FIDO tokens to reduce risks and user experience issues associated with passwords. Do NOT: Use weak MFA factors such as text messages (susceptible to SIM swapping), simple voice approvals, simple push (instead, use number matching), or secondary email addresses. Include location-based exclusions. MFA exclusions allow an actor with only one factor for a set of identities to bypass the MFA requirements if they can fully compromise a single identity. Allow credential or MFA factor sharing between users. Require healthy and trusted endpoints Require trusted, compliant, and healthy devices for access to resources to prevent data theft. Turn on cloud-delivered protection in Microsoft Defender Antivirus to cover rapidly evolving attacker tools and techniques, block new and unknown malware variants, and enhance attack surface reduction rules and tamper protection. Leverage modern authentication options for VPNs VPN authentication should leverage modern authentication options such as OAuth or SAML connected to Azure AD to enable risk-based sign-in detection. Modern authentication enables blocking authentication attempts based on sign-in risk, requiring compliant devices for sign in, and tighter integration with your authentication stack to provide more accurate risk detections. Implementation of modern authentication and tight conditional access policies on VPN has been shown to be effective against DEV-0537’s access tactics. Strengthen and monitor your cloud security posture DEV-0537 leverages legitimate credentials to perform malicious actions against customers. Since these credentials are legitimate, some activity performed might seem consistent with standard user behavior. Use the following recommendations to improve your cloud security posture: Review your Conditional Access user and session risk configurations: Block or force password reset for high/medium user risk for all users Block high sign-in risk logins for all users Block medium sign-in risk logins for privileged users Require MFA for medium sign-in risk logins for all other users [*]Alerts should be configured to prompt a review on high-risk modification of tenant configuration, including but not limited to: Modification of Azure AD roles and privileged users associated with those roles Creation or modification of Exchange Online transport rules Modification of tenant-wide security configurations [*]Review risk detections in Azure AD Identity Protection Risk detections highlight risky users and risky sign-ins Administrators can review and confirm individual sign-ins listed here as compromised or safe More information is available here on how to Investigate risk Azure AD Identity Protection Improve awareness of social engineering attacks Microsoft recommends raising and improving awareness of social engineering tactics to protect your organization. Educate members of your technical team to watch out for and report any unusual contacts with colleagues. IT help desks should be hypervigilant about suspicious users and ensure that they are tracked and reported immediately. We recommend reviewing help desk policies for password resets for highly privileged users and executives to take social engineering into consideration. Embed a culture of security awareness in your organization by educating employees about help desk verification practices. Encourage them to report suspicious or unusual contacts from the help desk. Education is the number one defense against social engineering attacks such as this one and it is important to make sure that all employees are aware of the risks and known tactics. Establish operational security processes in response to DEV-0537 intrusions DEV-0537 is known to monitor and intrude in incident response communications. As such, these communication channels should be closely monitored for unauthorized attendees and verification of attendees should be performed visually or audibly. We advise organizations to follow very tight operational security practices when responding to an intrusion believed to be DEV-0537. Organizations should develop an out-of-band communication plan for incident responders that is usable for multiple days while an investigation occurs. Documentation of this response plan should be closely held and not easily accessible. Microsoft continues to track DEV-0537’s activities, tactics, malware, and tools. We will communicate any additional insights and recommendations as we investigate their actions against our customers. The post DEV-0537 criminal actor targeting organizations for data exfiltration and destruction appeared first on Microsoft Security Blog. Continue reading...
-
The massive shift toward remote and hybrid work over the last two years has prompted many security professionals to reassess where siloed security may create vulnerabilities.1 For that reason, Zero Trust has become the gold standard for enterprise security. An effective Zero Trust approach requires comprehensive security—a holistic solution that covers all users, devices, and endpoints with central visibility. And any security solution you entrust with protecting your organization should be vetted by trusted industry sources. There’s a reason Microsoft Security generated more than USD15 billion in revenue during 2021 with 45 percent growth.2 We’re a Leader in four Gartner® Magic Quadrant reports,3 eight Forrester Wave reports,4 and six IDC MarketScape reports.5 As we head into another year marked by rapid change, Microsoft Security continues to deliver industry-leading protection across Zero Trust pillars, including identity, endpoints, applications, infrastructure, and data. Read on to see how we can help you move forward fearlessly. Strengthen identity verification Zero Trust security starts with strong identity verification. That means determining that only those people, devices, and processes you’ve authorized can access resources on your systems. As the cornerstone of Microsoft’s identity solutions, Microsoft Azure Active Directory (Azure AD) provides a single identity control plane with common authentication and authorization for all your apps and services, even many non-Microsoft apps. Built-in conditional access in Azure AD lets you set policies to assess the risk levels for a user, device, sign-in location, or app. Admins can also make point-of-logon decisions and enforce access policies in real-time—blocking access, requiring a password reset, or granting access with an additional authentication factor. Gartner recognized Microsoft as a 2021 Leader in Gartner Magic Quadrant for Access Management.6 Microsoft was also named as a Leader in the IDC MarketScape: Worldwide Advanced Authentication for Identity Security 2021 Vendor Assessment. From the IDC MarketScape report: “As telemetry is the rocket fuel for AI- and machine learning-infused endpoint security solutions, Microsoft’s breadth and volume are unequaled geographically and across customer segments. With the support of macOS, iOS, and Android, Microsoft’s telemetry pool is expanding and diversifying.” Comprehensive endpoint management Microsoft Endpoint Manager combines both Microsoft Intune and Microsoft Configuration Manager to enable all user devices and their installed apps (corporate and personal) to meet your security and compliance policies—whether connecting from inside the network perimeter, over a VPN, or from the public internet. We believe this comprehensive coverage led to Microsoft being named a Leader in the 2021 Gartner Magic Quadrant for Unified Endpoint Management Tools,7 including Microsoft 365 Defender with extended detection and response (XDR) capabilities and its easy integration with Microsoft 365 apps. Endpoint Manager also ranked as a Leader in the 2021 Forrester Wave: Unified Endpoint Management Q4 2021. As the Forrester report states: “Endpoint Manager excels at helping customers migrate to modern endpoint management, with differentiating features, such as policy analysis, to determine readiness for cloud management, templated group policy migration, and pre-canned reports for co-management eligibility.” In the 2021 IDC MarketScape Vendor Assessments, Microsoft was again named as a Leader in five categories, including Worldwide Modern Endpoint Security for Enterprises8 and Small and Midsize Businesses,9 as well as Worldwide Unified Endpoint Management Software,10 Worldwide Unified Endpoint Management Software for Ruggedized/Internet of Things Deployment,11 and Worldwide Unified Endpoint Management Software for Small and Medium-Sized Businesses.12 Endpoint security and protection Microsoft Defender for Endpoint was named Leader in the 2021 Gartner Magic Quadrant for Endpoint Protection Platforms,13 as well as being recognized as a Leader in The Forrester Wave: Endpoint Security Software as a Service, Q2 2021. In the Forrester report, Defender for Endpoint received the highest possible scores in the criteria of control, data security, and mobile security, as well as in the criteria for Zero Trust framework alignment. As Forrester reported: “Third-party labs and customer reference scores both point to continued improvement over antimalware and anti-exploit efficacy where Microsoft frequently outperforms third-party competitors.” Microsoft 365 Defender again made the top ranks later in the same year, placing as a Leader in The Forrester New Wave: Extended Detection and Response (XDR), Q4 2021. “[Microsoft 365 Defender] offers robust, native endpoint, identity, cloud, and O365 [Microsoft Office 365] correlation… singular and cross-telemetry detection, investigation, and response for Microsoft’s native offerings in one platform.” Application usage and management Knowing which apps are being accessed by the people in your organization is critical to mitigating threats. This is especially true for apps that might be acquired independently for use by individuals or teams, also known as shadow IT. Microsoft Defender for Office 365 was named a Leader in The Forrester Wave: Enterprise Email Security, Q2 2021, and received the highest possible score in the incident response, threat intelligence, and endpoint detection and response (EDR) solutions integration criteria. Defender for Office 365 also received the highest possible scores in the product strategy, support and customer success, and performance and operations criteria. Microsoft 365 Defender was again recognized by Forrester as a Leader in The Forrester New Wave: Extended Detection and Response (XDR), Q4 2021. Forrester found that Defender “offers robust, native endpoint, identity, cloud, and Office 365 correlation… [and] provides singular and cross-telemetry detection, investigation, and response for Microsoft’s native offerings in one platform.” Forrester also stated that Microsoft Defender for Endpoint’s “rich native telemetry yields tailored detection, investigation, response, and mitigation capabilities.” Microsoft is committed to helping you gain visibility of your cloud apps and protect sensitive information anywhere in the cloud, as well as assess compliance and discover shadow IT. We’re proud to report that Microsoft Defender for Cloud Apps ranked as a Leader in The Forrester Wave: Cloud Security Gateways, Q2 2021, receiving the highest score in the strategy category. Secure your network Today’s modern architectures span on-premises systems, multiple cloud and hybrid services, VPNs, and more. Microsoft provides the scalable solutions needed to help secure any size network, including our cloud-native Microsoft Azure Firewall and Microsoft Azure DDoS Protection. Our XDR, security information and event management (SIEM), and security orchestration, automation, and response (SOAR) solutions—Microsoft 365 Defender and Microsoft Sentinel—empower your security operations centers (SOCs) to hunt for threats and easily coordinate your response from a single dashboard. On-premises and cloud infrastructure Accurate infrastructure monitoring is critical for detecting vulnerabilities, attacks, or any anomaly that could leave your organization vulnerable. Staying on top of configuration management and software updates is especially important to meet your security and policy requirements. Because today’s SOC is tasked with protecting a decentralized digital estate, Microsoft Sentinel was created as a cloud-native SIEM and SOAR solution, designed to protect both on-premises and cloud infrastructure. Only a year after its introduction, Microsoft was named a Leader in The Forrester Wave: Security Analytics Platforms, Q4 2020. By using graph-based machine learning and a probabilistic kill chain to produce high-fidelity alerts, Microsoft Sentinel reduces alert fatigue by 90 percent. Forrester reported that customers “note the ease of integration across other Microsoft products like Azure, Microsoft 365, and Defender for Endpoint as a big benefit… [and] call out automation as another strength.” Limit access to your data Limiting access to your data means upholding the three pillars of Zero Trust security—verify explicitly, apply least privileged access, and assume breach—across all files, wherever they reside. With Microsoft Information Protection, built-in labeling helps you maintain accurate classification, and machine learning-based trainable classifiers help deliver an exact data match. Microsoft Information Governance provides capabilities to govern your data for compliance or regulatory requirements, and Microsoft Data Loss Prevention empowers you to apply a consistent set of policies across the cloud, on-premises environments, and endpoints to monitor, prevent, and remediate risky activity. In the field of data protection, Microsoft was named a Leader in the 2022 Gartner Magic Quadrant for Information Archiving,14 as well as a Leader in The Forrester Wave: Unstructured Data Security Platforms, Q2 2021. Forrester gave Microsoft the highest score in the strategy category, as well as the highest score possible in APIs and integrations, data security execution roadmap, performance, planned enhancements, Zero Trust enabling partner ecosystem, and eight other criteria. The comprehensive coverage you need with Microsoft Security Competing in today’s business environment means being able to move forward without constantly looking over your shoulder for the latest cyber threat. An effective Zero Trust architecture helps make that possible through a combination of comprehensive coverage, easy integration, built-in intelligence, and simplified management. Microsoft Security does all four—integrating more than 40 disparate products for security, compliance, identity, and management across clouds, platforms, endpoints, and devices—so you can move forward—fearless. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. 1Why Security Can’t Live In A Silo, Douglas Albert, Forbes Technology Council, Forbes. October 5, 2020. 2Microsoft beats on earnings and revenue, delivers upbeat forecast for fiscal third quarter, Jordan Novet, CNBC. January 25, 2022. 3Microsoft Security is a Leader in four Gartner® Magic Quadrant reports, Microsoft Security. 4Microsoft Security is a Leader in eight Forrester Wave categories, Microsoft Security. 5IDC MarketScape: Worldwide Advanced Authentication for Identity Security 2021 Vendor Assessment, Doc # US46178720. July 2021 IDC MarketScape: Worldwide Modern Endpoint Security for Enterprises 2021 Vendor Assessment, Doc # US48306021. November 2021 IDC MarketScape: Worldwide Modern Endpoint Security for Small and Midsize Businesses 2021 Vendor Assessment, Doc #48304721. November 2021. IDC MarketScape: Worldwide Unified Endpoint Management Software 2021 Vendor Assessment, Doc # US46957820. January 2021. IDC MarketScape: Worldwide Unified Endpoint Management Software for Small and Medium-Sized Businesses 2021 Vendor Assessment, Doc # US46965720. January 2021 IDC MarketScape: Worldwide Unified Endpoint Management Software for Ruggedized/Internet of Things Deployment 2021 Vendor Assessment, Doc # US46957920. January 2021 6Gartner, Magic Quadrant for Access Management, Henrique Teixeira, Abhyuday Data, Michael Kelley, 1 November 2021. 7Gartner, Magic Quadrant for Unified Endpoint Management Tools, Dan Wilson, Chris Silva, Tom Cipolla, 16 August 2021. 8IDC MarketScape: Worldwide Modern Endpoint Security for Enterprises 2021 Vendor Assessment, Michael Suby, IDC. November 2021. 9Microsoft named a Leader in IDC MarketScape for Modern Endpoint Security for Enterprise and Small and Midsize Businesses, Rob Lefferts, Microsoft Security Blog, Microsoft. November 18, 2021. 10IDC MarketScape: Worldwide Unified Endpoint Management Software 2021 Vendor Assessment, Phil Hochmuth, IDC. January 2021. 11IDC MarketScape: Worldwide Unified Endpoint Management Software for Ruggedized/Internet of Things Deployment 2021 Vendor Assessment, Phil Hochmuth. January 2021. 12IDC MarketScape: Worldwide Unified Endpoint Management Software for Small and Medium-Sized Businesses 2021 Vendor Assessment, Phil Hochmuth. January 2021. 13Gartner, Magic Quadrant for Endpoint Protection Platforms, Paul Webber, Peter Firstbrook, Rob Smith, Mark Harris, Prateek Bhajanka, Updated 5 January 2022, Published 5 May 2021. 14Gartner, Magic Quadrant for Enterprise Information Archiving, Michael Hoeck, Jeff Vogel, Chandra Mukhyala, 24 January 2022. Gartner and Magic Quadrant are registered trademarks of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. The post A Leader in multiple Zero Trust security categories: Industry analysts weigh in appeared first on Microsoft Security Blog. Continue reading...
-
Microsoft released a security update to address CVE-2022-23278 in Microsoft Defender for Endpoint. This important class spoofing vulnerability impacts all platforms. We wish to thank Falcon Force for the collaboration on addressing this issue through coordinated vulnerability disclosure. Cybercriminals are looking for any opening to tamper with security protections in order to blind, confuse, or … Guidance for CVE-2022-23278 spoofing in Microsoft Defender for Endpoint Read More » Continue reading...
-
- 1
-

-
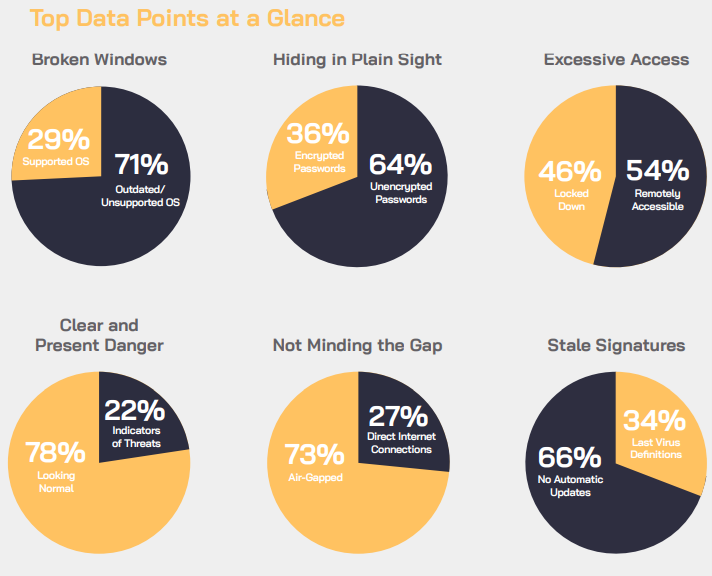
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. In recent years, malicious actors have started attacking industrial control systems and key sectors of nations’ critical infrastructure to inflict damage that transcends the cyber world and traditional IT assets. The risk to public safety cannot be overstated, as these types of cyberattacks have real-world potential to inflict harm on humans. These “industrial control systems” that control the many facets of our nation’s critical infrastructure are more commonly known as operational technology (OT) devices. The same goes for IoT devices and industrial internet of things (IIoT) devices. IoT is the network of physical objects that contain embedded technology to communicate, sense, or interact with the internal or external state of its environment. The public and private sectors have many OT and IoT devices in industries such as defense, power generation, robotics, chemical and pharmaceutical production, oil production, transportation, and mining—to name a few. OT devices are hardware and software that monitor or control physical equipment, assets, and processes—and they are being compromised at an increasing rate.1 Alarmingly, in 2021 there were two incidents of local water treatment plants in the US being a target of cyberattacks. One cyberattack occurred in the San Francisco Bay area in January 20212 and another occurred in February 2021 in Oldsmar, Florida.3 In the Oldsmar, Florida cyberattack, the malicious actors attempted to increase the amount of sodium hydroxide in the water supply to potentially dangerous levels. Thankfully, the attack was thwarted by a plant supervisor who caught the act in real-time and reverted the changes. These cyberattacks occurred on OT devices used for critical infrastructure at local level, but similar cyberattacks are playing out in the real world on a national level as well. On May 7, 2021, Colonial Pipeline, an American oil pipeline system responsible for 45 percent of all fuel consumed on the US East Coast, suffered a ransomware cyberattack that crippled all pipeline operations for about six days.4 The aftermath of this attack caused fuel shortages in six US states as well as the US capital, Washington D.C. These cyberattacks on OT devices may not be new, but they underscore how dangerous the threat is to our critical infrastructure, as well as how great the risk is to our overall public safety. The US government has taken notice of the increased threat against OT systems and has responded accordingly. Per the President’s Executive Order on Improving the Nation’s Cybersecurity issued on May 12, 2021, “The Federal Government must bring to bear the full scope of its authorities and resources to protect and secure its computer systems, whether they are cloud-based, on-premises, or hybrid.5 The scope of protection and security must include systems that process data (information technology (IT)) and those that run the vital machinery that ensures our safety (operational technology (OT)).” The Quzara CybertorchTM solution, in conjunction with Microsoft Defender for IoT and Microsoft Sentinel, help agencies meet compliance with various aspects of this executive order. This includes, but is not limited to, providing agencies a means to monitor IT and OT operations and alerts, respond to attempted and actual cyber incidents, and facilitate logging, log retention, and log management. With the threat of cyberattacks impacting OT and IoT devices on the rise, it is important now more than ever for national, state, local governments, and their private sector partners to be vigilant in securing their OT and IoT devices that operate or assist critical infrastructure. The current state of cybersecurity in OT and IoT environments While it is encouraging that the US Government is giving greater emphasis to secure OT and IoT infrastructure, they and private corporations with OT and IoT devices face an uphill battle. This is because many OT and IoT environments use outdated (and therefore, unsecure) operating systems and software. A comprehensive report from CyberX (acquired by Microsoft) in June 2020 titled Global IoT and ICS Risk Report was compiled based on data gathered from 1,821 production OT and IoT networks using passive, agentless monitoring with patented deep packet inspection (DPI) and network traffic analysis (NTA) algorithms. These production networks spanned diverse IoT and ICS systems—including robotics, refrigeration, chemical, and pharmaceutical production, power generation, oil production, transportation, mining, and building management systems (heating, ventilation, and air conditioning (HVAC), closed-circuit television (CCTV), and more). These are the findings in the report: 71 percent had outdated or unsupported operating systems. 64 percent had unencrypted passwords. 54 percent were remotely accessible. 22 percent had indicators of threats. 27 percent had direct internet connections. 66 percent had no automatic updates. Figure 1. CyberX report high-level findings. Securing and monitoring OT and IoT devices It is critical for national, state, local governments, and their private sector partners to secure their OT and IoT environments from cyberattacks—but first, security must be made easier to incorporate. To make it easier for these entities to incorporate OT and IoT security, Quzara CybertorchTM, a managed security service provider (MSSP), partnered up with Microsoft to leverage Microsoft Defender for IoT. By leveraging Microsoft Defender for IoT, Quzara CybertorchTM is able to discover all OT and IoT devices in an environment, identify vulnerabilities present on these devices, and provide continuous security monitoring of these devices. Automated asset inventory Microsoft Defender for IoT is an agent-less solution that—connecting to a mirroring port on a network’s switch—passively listens to real-time OT and IoT traffic in the industrial network. Quzara CybertorchTM uses this tool to quickly create an “Asset Inventory Map” that shows all assets on the network, identifies which machines are interacting with each other, and at which layer of the Purdue model they operate.6 Figure 2. Auto-generated Asset Inventory Map in Purdue model layout. By identifying which assets communicate with each other in a Purdue model format, valuable information is gathered that depicts which machines can communicate out to the internet from the OT network. These internet-connected machines are the ones we prioritize locking down and monitor more closely for suspicious traffic. Identifying internet-connected assets is just one example of what the Asset Inventory Map can display. The Asset Inventory Map also reveals any shadow devices that are on the OT and IoT network. In other words, by revealing all assets on the OT network, the Asset Inventory Map will identify any IT, OT, and IoT devices that the IT department may not be officially aware of. Furthermore, the Asset Inventory Map helps IT security teams identify “single points of failure” in their environment based on the network topology and architecture. Quzara CybertorchTM encourages hardening these assets that are “single points of failure” and creating redundancy to ensure operations aren’t disrupted if these assets were to ever go down unexpectedly. Vulnerability management of OT and IoT devices Quzara CybertorchTM can identify known vulnerabilities on OT and IoT devices by leveraging Microsoft Defender for IoT. Microsoft Defender for IoT proactively identifies vulnerabilities such as unpatched devices, unauthorized Internet connections, and subnet connections. Beyond identifying vulnerabilities, Microsoft Defender for IoT also identifies changes to device configurations, programmable logic controller (PLC) code, and firmware. Quzara CybertorchTM consolidates all this information and generates executive summary reports listing out all the vulnerabilities for all OT and IoT devices in a network—which includes prioritized remediation steps. Prioritized remediation steps may include prioritizing fixes based on risk scoring (for example, through common vulnerability scoring system (CVSS) scores and other factors) and automated threat modeling. These reports contain an overall security score for the OT and IoT devices on the network. As remediation occurs, continuous improvement can be measured by subsequent reports showing the overall security score improving. Figure 3. Vulnerabilities present on an OT workstation. Continuous monitoring for OT and IoT devices Quzara CybertorchTM is a security operations center as a service that leverages Microsoft Sentinel to continuously monitor IT environments as well as OT and IoT environments. Microsoft Sentinel is a security information and event management (SIEM) tool with security orchestration, automation, and response (SOAR) capabilities. Microsoft Sentinel has native interoperability with Microsoft Defender for IoT and is cloud native. Using Microsoft Sentinel, Quzara CybertorchTM can ingest logs from IT, OT, and IoT devices, creating a unified bird’s-eye view across IT and OT boundaries and empowering our security operations center (SOC) analysts to then analyze for signs of malicious activity. When using other products, typically a lot of work and expertise is required to create rules that aggregate disparate alerts into consolidated incidents. Quzara CybertorchTM greatly reduces the work that is required to create targeted rules for OT and IoT incidents, as Microsoft Sentinel has pre-built analytics rules for OT and IoT devices when used in conjunction with Microsoft Defender for IoT. Functionality also exists to create custom rules and playbooks from these OT and IoT alerts. This functionality empowers our SOC analysts to help detect, alert, and assist personnel in mitigating vulnerabilities on OT and IoT devices. Figure 4. Microsoft Defender for IoT analytics rules in Microsoft Sentinel. If your team, company, or clients have an OT or IoT environment and are interested in obtaining an OT or IoT cybersecurity risk assessment, please reach out to Quzara CybertorchTM or by email here. About Quzara Cybertorch Quzara Cybertorch is a security operations center as a service and managed detection and response (MDR) purpose-built to meet the needs of U.S. Civilian, Department of Defense (DoD), and Defense Industrial Base (DIB) customers for extended detection and response (XDR), Vulnerability Management, OT and IoT monitoring, and security monitoring needs. Their security operations center as a service, vulnerability management, and XDR capabilities are based on the National Institute of Standards and Technology (NIST) 800-53 FedRAMP HIGH controls. Their entire technology stack leverages FedRAMP HIGH Authorized systems. Quzara Cybertorch’s team of Security Analysts are all based and operate within the US, with emphasis on security clearances and government support experience. Explore Quzara Cybertorch and visit the Quzara Cybertorch listing in the Microsoft commercial marketplace. Learn more Explore Microsoft Defender for IoT. Start using Microsoft Sentinel today. To learn more about the Microsoft Intelligent Security Association (MISA), visit our website where you can learn about the MISA program, product integrations, and find MISA members. Visit the video playlist to learn about the strength of member integrations with Microsoft products. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. 1Crimes of Opportunity: Increasing Frequency of Low Sophistication Operational Technology Compromises, Mandiant, May 25, 2021. 2Hackers Tried to Poison California Water Supply in Major Cyber Attack, News Week, June 18, 2021. 3The Florida water plant attack signals a new era of digital warfare—it’s time to fight back, Darktrace, February 16, 2021. 4Ransomware Attack Shuts Down A Top U.S. Gasoline Pipeline, NPR, May 9, 2021. 5Executive Order on Improving the Nation’s Cybersecurity, The White House. May 12, 2021. 6The “Purdue Model” is a structural model for industrial control system security concerning physical processes, systems, and the IT machines that manage or interact with them. The post Secure your OT and IoT devices with Microsoft Defender for IoT and Quzara Cybertorch™ appeared first on Microsoft Security Blog. Continue reading...
-
We've invested in Windows Server for nearly 30 years, and we continue to find new ways to empower businesses who trust Windows Server as the operating system for their workloads. Over this time, we understand that business requirements have become more complex and demanding. Thus, we are energized when we hear how customers continue to trust Windows Server to navigate these ever-evolving requirements and run business and mission-critical workloads. We want to continue to invest in your organizations' success and enable you to get the most out of Windows Server by keeping you informed of the latest product announcements, news, and overall best practices. Here are the top five to-do's for you to make the most out of Windows Server: 1. Patch and install security updates without rebooting with Hotpatching Windows Server Hotpatching is now generally available. As part of Azure Automanage for Windows Server, this capability allows you to keep your Windows Server virtual machines on Azure up-to-date without rebooting, enabling higher availability with faster and more secure delivery of updates. Other capabilities that are part of Azure Automanage for Windows Server include SMB over QUIC, as well as extended network for Azure, which lets you keep your on-premises IP addresses when you migrate to Azure. Learn more about why Azure is the best destination for Windows Server. 2. Take the recently available Windows Server Hybrid Administrator Certification Invest in your career and skills with this brand-new Windows Server certification. With this certification, you can keep the Windows Server knowledge you have built your career on and learn how to apply it in the current state of hybrid cloud computing. Earn this certification for managing, monitoring, and securing applications on-premises, in Azure, and at the edge. Learn more about Windows Server Hybrid Administrator Associate certification today. 3. Upgrade to Windows Server 2022 With Windows Server 2022, get the latest innovation for you to continue running your workloads securely, enable new hybrid cloud scenarios, and modernize applications to meet your ever-evolving business requirements. Learn more about investing in your success with Windows Server. 4. Protect your workloads by taking advantage of free extended security updates (ESUs) in Azure While many customers have adopted Windows Server 2022, we also understand that some need more time to modernize as support for older versions of Windows Server will eventually end. For Windows Server 2012/2012 R2 customers, the end of support date is October 10, 2023. For Windows Server 2008/2008 R2 customers, the third year of extended security updates are coming to an end on January 10, 2023. Customers can get an additional fourth year of free extended security updates (ESUs-only) on Azure (including Azure Stack HCI, Azure Stack Hub, and other Azure products). With this, customers will have until January 9, 2024 for Windows Server 2008/2008 R2 to upgrade to a supported release. We are committed to supporting you as you start planning for end of support if you are running workloads on older versions of Windows Server. Learn more about end of support deadlines for Windows Server 2008/R2 and 2012/R2 and your options. 5. Combine extended security updates with Azure Hybrid Benefit to save even more In addition to all the innovative Windows Server capabilities available only on Azure, it also has offers for you to start migrating your workloads with Azure Hybrid Benefit. It is a licensing benefit that allows you to save even more by using existing Windows Server licenses on Azure. Learn more about how much you can save with Azure Hybrid Benefit. Ask questions and engage in our community Get started implementing these Windows Server best practices today! Join the conversation by sharing stories or questions you have here: Windows Server Tech Community. @windowsserver on Twitter. The post Get the most out of Windows Server with these 5 best practices appeared first on Microsoft Windows Server Blog. Continue reading...
-
You’d be forgiven for missing the White House announcement on federal Zero Trust strategy on January 26, 2022.1 After all, on that day alone a Supreme Court Justice announced his intention to retire, the Federal Reserve announced its plan to raise interest rates, and the State Department was busy trying to reduce international tensions. Even if it didn’t lead the evening news, the security announcement is a crucial milestone for all those that understand the importance of a Zero Trust model and are working hard to implement it. It’s no secret that government support for a technology can turbo-boost adoption—ask anyone who uses GPS, the internet, or electronic medical records.2 US Federal Government support for Zero Trust is similar: the Office of Management and Budget (OMB) has started an accelerated adoption curve for tens of millions of new endpoints. There are 2.25 million full-time equivalent employees in the US federal executive branch, and 4.3m if you count postal workers and other staff in the judicial, legislative, and uniformed military branches.3 These also include many frontline workers, a critical security topic that I discuss in the blog post Reduce the load on frontline workers with the right management technology. The US Federal Government also sets the tone for technology policy in state and local government, which adds another 19.7 million workers, before we even begin to count federal government suppliers who will be asked to comply.4 Even at a ratio of one employee per endpoint (and the ratio could be higher with personal devices and IoT), not counting the endpoint strategy updates by overseas governments, we’re looking at tens of millions of endpoints that will be managed according to Zero Trust governance principles. In full, I encourage you to read the memorandum press release, Office of Management and Budget Releases Federal Strategy to Move the U.S. Government Towards a Zero Trust Architecture. Here are my three takeaways: Zero Trust is now relevant to every organization. Leadership alignment is the biggest obstacle to driving Zero Trust agendas. Zero Trust architecture requires holistic, integrated thinking. Zero Trust is now relevant to every organization Hybrid work, cloud migration, and increased threats make Zero Trust now relevant to every organization. The concept of Zero Trust is not new. The term was first coined by then Forrester analyst John Kindervag in 2010.5 Yet, as the OMB paper says: “The growing threat of sophisticated cyber attacks has underscored that the Federal Government can no longer depend on conventional perimeter-based defenses to protect critical systems and data. The Log4j vulnerability is the latest evidence that adversaries will continue to find new opportunities to get their foot in the door.” Yet, in our 2021 Zero Trust Adoption Report, only 35 percent of organizations claim to have fully implemented their Zero Trust strategy. Zero Trust is now vitally relevant for every organization for two reasons. First, the shift to remote work and the accompanying cloud migration is here to stay. Gartner® estimates that 47 percent of knowledge workers will work remotely in 2022.6 This is not just a pandemic-era emergency that will reset to perimeter-based solutions once COVID-19 cases decrease. Today, security solutions must start from the fact that endpoints could be outside of a perimeter defense set-up and be tailored accordingly. Second, cyber threats continue to increase. The US Federal Government referenced the Log4j flaw but could equally have mentioned Kaseya, SolarWinds, or other recent disruptions. These disruptions are expensive—a 2021 IBM report put the average total cost of a breach of 1 to 10 million records at USD52 million, with a mega breach of 50 to 65 million records costing companies more than USD400 million.7 The US Federal Government is signaling that Zero Trust is essential for the current times. Zero Trust requires customers to think beyond firewalls and network perimeters and assume breach from within those boundaries. Leadership alignment is the biggest obstacle to driving Zero Trust agendas My second takeaway is that leadership alignment is critical to organizations making the proper progress in Zero Trust. OMB requires that every agency nominate a Zero Trust strategy implementation lead within 30 days. Furthermore, the memorandum states: “Agency Chief Financial Officers, Chief Acquisition Officers, senior agency officials for privacy, and others in agency leadership should work in partnership with their IT and security leadership to deploy and sustain Zero Trust capabilities. It is critical that agency leadership and the entire ‘C-suite’ be aligned and committed to overhauling an agency’s security architecture and operations.” In short, this is not simply a technology problem that can be handed over to IT, never to be thought of again. Zero Trust requires, at a minimum, C-suite engagement and, given the risks involved in a security breach, also warrants board oversight. Our Zero Trust Adoption Report that explores the barriers to Zero Trust implementation also highlighted leadership alignment. Fifty-three percent mentioned this as a barrier, covering C-suite, stakeholder, or broader organizational support. Other key barriers to adoption included limited resources, such as skills shortages in areas like change management, or the inability to sustain the length of time for implementation. For example, according to a 2020 annual Cybersecurity Workforce Study by (ISC)2, there remains a shortage of 3.1 million cybersecurity workers, including 359,000 in just the US.8 Related to this, budget constraints were mentioned by 4 in 10 survey respondents. Anticipating and proactively addressing leadership alignment, limited resources, and budget are key to the broader rollout of Zero Trust architectures, independent of any technology choices. Zero Trust architecture requires holistic, integrated thinking Zero Trust architecture thinking is more akin to conducting an orchestra than just flipping a switch. The US Federal Government’s plans encompass identity (including multifactor authentication and user authorization), devices (including endpoint detection and response), networks (including Domain Name System, HTTP, and email traffic encryption), apps and workloads, and data. This is not a project that can be done in silos or quickly. Indeed, the OMB asks federal agencies that “Within 60 days of the date of this memorandum, agencies must build upon those plans by incorporating the additional requirements identified in this document and submitting to OMB and Cybersecurity & Infrastructure Security Agency (CISA) an implementation plan for FY22 to FY24 for OMB concurrence, and a budget estimate for FY24.” Microsoft’s and the US Federal Government’s Zero Trust frameworks are very similar. They overlap into five categories. Microsoft calls out infrastructure separately from networks, while the OMB memo combines the two. When thinking about Zero Trust, any organization needs to consider: Identities and authentication: Protecting identities against compromise and securing access to resources, including multifactor authentication. Endpoints and devices: Securing endpoints and allowing only compliant and trusted devices to access data. Applications: Ensuring applications are available, visible, and securing your important data. Data: Protecting sensitive data wherever it lives or travels. Networks: Removing implicit trust from the network and preventing lateral movement. Infrastructure: Detecting threats and responding to them in real-time. Underscoring these pillars is centralized visibility, which enables a holistic view. Being able to see how all apps and endpoints are deployed and whether there are security issues is vital to maintaining as well as setting up a Zero Trust posture. An endpoint management solution provides a central repository for security policies and a place to enforce those policies should an endpoint no longer comply. Solutions should enable built-in encryption across all platforms, whether Windows, macOS, iOS, Android, or Linux. Equally, unified endpoint management will make the network journey towards Zero Trust easier, regardless of the type of network. Visibility matters in Zero Trust, and effective endpoint management is a major factor in delivering it. Picking a starting point Having a consistent framework for Zero Trust and constant visibility is a good starting point. Nonetheless, it doesn’t answer the question of where and how to start implementing Zero Trust for your organization. The answer will be specific to every organization—there is no one-size-fits-all approach for Zero Trust. Organizations may start at different points, but the Microsoft 365 Zero Trust deployment plan gives all organizations a practical guide to introduce Zero Trust. The deployment plan has five steps and can help organizations implement a Zero Trust architecture: Configure Zero Trust identity and device access protection to provide a Zero Trust foundation. Manage endpoints by enrolling devices into management solutions. Add Zero Trust identity and device access protection to those devices. Evaluate, pilot, and deploy Microsoft 365 Defender to automatically collect, correlate, and analyze the signal, threat, and alert data. Protect and govern sensitive data to discover, classify, and protect sensitive information wherever it lives or travels. Management of your apps and endpoints plays a vital and foundational role in any Zero Trust deployment. By enrolling devices into management, you can configure compliance policies to ensure devices meet minimum requirements and deploy those configuration profiles to harden devices against threats. With a solid foundation established, you can defend against threats by using device risk signals and ensure compliance using security baselines. In this way, you’re protecting and governing sensitive data, no matter what operating system platform your devices are using. CISA Director Jen Easterly wrote in the memo’s press release: “As our adversaries continue to pursue innovative ways to breach our infrastructure, we must continue to fundamentally transform our approach to federal cybersecurity.” Zero Trust is a critical US Federal Government priority, which will accelerate mass adoption. If your organization is just starting to implement Zero Trust or further along, I hope the free resources below are helpful. Learn more Explore Microsoft’s resources and products to help you implement a Zero Trust strategy: Zero Trust Guidance Center Microsoft Zero Trust Deployment Plan Microsoft Endpoint Manager Manage devices with Intune Read more about the US Federal Government’s Zero Trust strategy announcement: US Government sets forth Zero Trust architecture strategy and requirements OMB Federal Zero Trust strategy Additional resources: 4 best practices to implement a comprehensive Zero Trust security approach Reduce the workload on frontline workers with the right management technology by Steve Dispensa KuppingerCole Leadership Compass: Microsoft named a Product, Innovation, Market, and overall Leader in Unified Endpoint Management, 2021-22 Download: Omdia recognizes Microsoft as a Leader in the Unified Endpoint Management Solutions market radar report, 2021-22 To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. 1US Government sets forth Zero Trust architecture strategy and requirements, Joy Chik, Microsoft. February 17, 2022. 250 inventions you might not know were funded by the US government, Abby Monteil, Stacker. December 9, 2020. 3Federal Workforce Statistics Sources: OPM and OMB, Congressional Research Service. June 24, 2021. 4Number of state and local government employees in the United States from 1997 to 2020, by full-time/part-time status, Statista. 5Forrester pushes Zero Trust model for security, Dark Reading. 6Gartner, Forecast Analysis: Remote and Hybrid Workers, Worldwide, Ranjit Atwal, Rishi Padhi, Namrata Banerjee, Anna Griffen, 2 June 2021. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved. 7Cost of a Data Breach Report 2021, IBM. 8Cybersecurity Workforce Study, (ISC)2. 2020. The post The federal Zero Trust strategy and Microsoft’s deployment guidance for all appeared first on Microsoft Security Blog. Continue reading...
-
To help protect the United States from increasingly sophisticated cyber threats, the White House issued Executive Order (EO) 14028 on Improving the Nation’s Cybersecurity, which requires US Federal Government organizations to take action to strengthen national cybersecurity.1 Section 3 of EO 14028 specifically calls for federal agencies and their suppliers “to modernize [their] approach to cybersecurity” by accelerating the move to secure cloud services and implementing a Zero Trust architecture. As a company that has embraced Zero Trust ourselves and supports thousands of organizations around the globe on their Zero Trust journey, Microsoft fully supports the shift to Zero Trust architectures that the Cybersecurity EO urgently calls for. We continue to partner closely with the National Institute of Standards and Technology (NIST) to develop implementation guidance by submitting position papers and contributing to communities of interest under the umbrella of the National Cybersecurity Center of Excellence (NCCoE). Microsoft helps implement Executive Order 14028 The memo clearly describes the government’s strategic goals for Zero Trust security. It advises agencies to prioritize their highest value starting point based on the Zero Trust maturity model developed by the national Cybersecurity & Infrastructure Security Agency (CISA). Microsoft’s position aligns with government guidelines. Our maturity model for Zero Trust emphasizes the architecture pillars of identities, endpoints, devices, networks, data, apps, and infrastructure, strengthened by end-to-end governance, visibility, analytics, and automation and orchestration. To help organizations implement the strategies, tactics, and solutions required for a robust Zero Trust architecture, we have developed the following series of cybersecurity assets: Cloud Adoption Framework: A rich repository of documentation, implementation guidance, and best practices to help accelerate cloud adoption. Zero Trust rapid modernization plan: A downloadable suggested phased rollout plan to accelerate adoption of a Zero Trust security approach. Zero Trust scenario architectures: A downloadable PDF of key architecture scenarios mapped to NIST standards. Multifactor authentication (MFA) deployment guide: Guidance on using Microsoft Azure Active Directory (Azure AD) to meet Zero Trust Architecture and MFA requirements. Interactive guide on the Cybersecurity EO: Clear, concise guidance to help organizations better understand near- and long-term milestones, build a strategic response aligned to security modernization priorities and Executive Order requirements, and determine how technology partners can help accelerate the journey. New capabilities in Azure AD to help meet requirements A blog by my colleague Sue Bohn, Guidance on using Azure AD to meet Zero Trust Architecture and MFA requirements, provides a great summary of how Azure AD can help organizations meet the requirements outlined in EO 14028. We recently announced two additional capabilities developed in response to customer feedback: cloud-native certificate-based authentication (CBA) and cross-tenant access settings for external collaboration. Certificate-based authentication Phishing remains one of the most common threats to organizations. It’s also one of the most critical to defend against. According to our own research, credential phishing was a key tactic used in many of the most damaging attacks in 2021. To help our customers adhere to NIST requirements and effectively counter phishing attacks, we announced the preview of Azure AD cloud-native CBA across our commercial and US Government clouds. CBA enables customers to use X.509 certificates on their PCs or smart cards to authenticate applications using Azure AD natively. This eliminates the need for additional infrastructure such as Active Directory Federation Services (ADFS) and reduces the risk inherent in using on-premises identity platforms. Cloud-native CBA demonstrates Microsoft’s commitment to the federal Zero Trust strategy. It helps our government customers implement the most prominent phishing-resistant MFA, certificate-based authentication, in the cloud so they can meet NIST requirements. Read the documentation on Azure AD certificate-based authentication to get started. Cross-tenant access settings for external collaboration Our customers have told us they want more control over how external users access apps and resources. Earlier this month, we announced the preview of cross-tenant access settings for external collaboration. This new capability enables organizations to control how internal users collaborate with external organizations that also use Azure AD. It provides granular inbound and outbound access control settings based on organization, user, group, or application. These settings also make it possible to trust security claims from external Azure AD organizations, including MFA and device claims (compliant claims and hybrid Azure AD joined claims). Consult the documentation on cross-tenant access with Azure AD External Identities to learn more. More capabilities coming soon We’re continuing to work on new capabilities to help government organizations meet Zero Trust security requirements: The ability to enforce phishing-resistant authentication for employees, business partners, and vendors for hybrid and multi-cloud environments. Comprehensive phishing-resistant MFA support, including remote desktop protocol (RDP) scenarios. Resources for your Zero Trust journey Microsoft is committed to helping the public and private sectors with a comprehensive approach to security that’s end-to-end, best-in-breed, and AI-driven. To advance your Zero Trust implementation, we offer the following: Cybersecurity EO resources for federal agencies. Zero Trust Guidance Center. Microsoft Cybersecurity Reference Architectures. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. 1Executive Order (EO) 14028 on Improving the Nation’s Cybersecurity. The post US Government sets forth Zero Trust architecture strategy and requirements appeared first on Microsoft Security Blog. Continue reading...
-
Today’s threat actors don’t see barriers, they see opportunities. As the old firewalls protecting the corporate network become obsolete amid the rush to adopt a hybrid workspace, implementing Zero Trust security has become an imperative across all sectors, both public and private. During this time of unprecedented change, Microsoft Security is committed to helping you be fearless in pursuing your vision for growth and success. Because an effective Zero Trust approach needs to operate holistically across your complex digital estate, Microsoft Security solutions function as a unified whole to protect your people, data, and business. We’re uniquely positioned to simplify and strengthen security across your entire enterprise—even integrating easily with your existing third-party products. In this blog, we’ll look at four guidelines for implementing a comprehensive Zero Trust strategy that can help your organization continue to move forward confidently in these uncertain times. Figure 1. Microsoft Zero Trust architecture. 1. Build Zero Trust with comprehensive coverage Despite what the name implies, a Zero Trust approach empowers organizations to grant employees greater freedom across all data, apps, and infrastructure. In a recent Microsoft-commissioned study conducted by Forrester Consulting, The Total Economic Impact (TEI) of Zero Trust Solutions From Microsoft, the principal architect at a logistics firm described how Microsoft’s comprehensive Zero Trust implementation allowed them to create a bring your own device (BYOD) program for the company’s seasonal frontline workers, leading to efficiency gains. “Before, our seasonal workers would have to be paired with our full-time employees when [performing field visits]. But now, they can go out on their own.” The interviewees said that “by implementing Zero Trust architecture, their organizations improved employee experience (EX) and increased productivity.” They also noted, “increased device performance and stability by managing all of their endpoints with Microsoft Endpoint Manager.” This had a bonus effect of reducing the number of agents installed on a user’s device, thereby increasing device stability and performance. “For some organizations, this can reduce boot times from 30 minutes to less than a minute,” the study states. Moreover, shifting to Zero Trust moved the burden of security away from users. Implementing single sign-on (SSO), multifactor authentication (MFA), leveraging passwordless authentication, and eliminating VPN clients all further reduced friction and improved user productivity. Figure 2. Microsoft Zero Trust solutions and capabilities. 2. Strengthen Zero Trust with AI and integration The Forrester study also found that “existing solutions failed to provide the high-fidelity signals, comprehensive visibility, and end-to-end self-healing capabilities needed to defend against today’s sophisticated attackers and volume of cyberthreats.” For the interviewed organizations, “prior solutions could not provide telemetry of a threat’s effect on data, a user’s exact activity on the network, or a timeline for effective remediation.” And because the organizations relied on security solutions from multiple vendors, “consolidating telemetry information for triage and analytical work was difficult and time-consuming.” Microsoft Sentinel solves the problem of vulnerable security silos by providing a single solution for alert detection, threat visibility, proactive hunting, and threat response. As a cloud-native security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution, Microsoft Sentinel uses AI to eliminate security infrastructure setup and maintenance by automatically scaling to meet user needs. Because Microsoft Sentinel is available out of the box with service-to-service connectors, it’s easy to gain real-time integration with Microsoft 365 Defender, Microsoft Azure Active Directory (Azure AD), Microsoft Defender for Identity, and Microsoft Defender for Cloud Apps. Any truly comprehensive Zero Trust implementation requires functionality across multiple platforms. Microsoft Sentinel also contains 30 new out-of-the-box data connectors for Cisco, Salesforce Service Cloud, Google Workspace, VMware ESXi, Thycotic, and many more. These data connectors include a parser that transforms the ingested data into Microsoft Sentinel normalized format, enabling better correlation for end-to-end outcomes across security monitoring, hunting, incident investigation, and response scenarios. Microsoft Sentinel automates routine tasks—with a 90 percent reduction in alert fatigue—so, your security team can focus on the most critical threats. For example, by adhering to the values of Zero Trust, the Microsoft security operations center (SOC) assumes that any device or user can be breached. That means we end up scrutinizing roughly 600 billion security events each month. But because we utilize Microsoft Sentinel and our other security tools that leverage machine learning, threat intelligence, and data science, we’re able to filter 600 billion monthly events down to around 10,000 alerts. We also use capabilities to find and fix low-level malware instances and other nuisance alerts. Microsoft Defender for Endpoint AIR capabilities can also clean up a device, delete the service, erase the file, and tell us when the problem has been remediated. This reduces noise for our SOC and helps shrink those 10,000 monthly alerts down to a manageable 3,500 cases for investigation. Whittling those numbers down is what helps us—and you—zero in on real threats. 3. Simplify for easier compliance and identity and access management (IAM) The five organizations in the Forrester study struggled to comply with regulatory requirements because “the complexity of their IT environments made it difficult to audit their environments or effectively implement governance policies.” Sound familiar? Fortunately, Zero Trust requirements can sometimes exceed some compliance requirements; meaning, organizations sometimes find that they’re better off than they had been previously. As a feature in the Microsoft 365 compliance center, Microsoft Compliance Manager solves this common problem with intuitive management and continuous assessments—from taking inventory of data risks to implementing controls, staying current with regulations and certifications, and reporting to auditors. Compliance Manager’s machine learning and analytics even help sort through relevant data to respond to your legal, regulatory, and internal obligations based on requirements from the International Organization of Standardization (ISO), National Institute of Standards and Technology NIST), Cybersecurity and Infrastructure Security Agency (CISA), and General Data Protection Regulation (GDPR). It automatically measures your progress toward completing necessary actions—providing a compliance score around data protection and regulatory standards—along with workflow capabilities and built-in control mapping to help carry out improvements. To make compliance even easier, the new Microsoft Sentinel: Zero Trust (TIC 3.0) Workbook features a redesigned user interface, new control card layouts, dozens of new visualizations, and better-together integrations with Microsoft Defender for Cloud to monitor compliance posture deviations across each TIC 3.0 control family. The new workbook also provides a mechanism for viewing log queries, Azure Resource Graph, metrics, and policies aligned to TIC 3.0 controls—enabling governance and compliance teams to design, build, monitor, and respond to Zero Trust requirements across 25 plus Microsoft products. Microsoft also offers more than 300 pre-built risk assessment templates to help you comply with evolving regulations, as well as integrated workflows to help ensure the right people across security, HR, legal, and compliance can investigate as soon as a risk is identified. The director at a manufacturing firm explained that “Microsoft Secure Score reduced the time it took us to be compliant with the California Consumer Privacy Act (CCPA) and GDPR. And Azure AD and Microsoft 365 E5 really enhance our security capabilities.” Secure Score simplifies your security posture by providing centralized visibility across all your Microsoft 365 workloads. This helps identify potential improvements, as well as benchmark your organization’s status over time. Embedded guidance enables you to evaluate each recommendation and determine which vectors of attack are a priority, and how they can be mitigated. Organizations in the Forrester study also stated that “Legacy infrastructures made it difficult for IAM teams to meet organizational security requirements and the needs of their users.” Azure Active Directory integration enabled these businesses to streamline sign-in and easily deploy applications companywide, as well as enable SSO and automate user provisioning. These efficiency gains allowed their IAM teams to focus on improving security by implementing additional Zero Trust policies. By adopting Azure AD, the IAM teams also reduced time spent managing IAM infrastructure, provisioning and de-provisioning users, managing vendors, and dealing with application downtime and remediation. 4. Look for best-in-breed protection When looking for a Zero Trust solution you can rely on, there’s a confidence that comes from knowing your security provider has seen more than 40 percent year-over-year growth and more than USD10 billion in revenue. As Thomas Mueller-Lynch, Service Owner Lead for Digital Identity at Siemens put it, “There aren’t too many vendors on the planet that can create a solution capable of providing consolidated insights into large, complex environments like ours. That’s why we chose Microsoft.” Microsoft Security is a leader in five Gartner Magic Quadrants and eight Forrester Wave categories and ranked the highest in the MITRE Engenuity® ATT&CK Evaluation. Microsoft was also named a Leader in IDC MarketScape for Modern Endpoint Security. By unifying security, compliance, and identity, we can help you improve productivity and protect your entire environment—from Windows and macOS to Linux, iOS, Android, and Amazon Web Services (AWS). For built-in intelligence, easy integration, and simplified management that addresses all three Zero Trust pillars, Microsoft Security provides the comprehensive solution you need to move forward—fearless. Learn more Be fearless—evaluate your security posture today. Explore our Zero Trust approach to comprehensive security. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. The post 4 best practices to implement a comprehensive Zero Trust security approach appeared first on Microsoft Security Blog. Continue reading...
-
New year, new features. Since Microsoft Ignite in November, we’ve continued to listen to your feedback and make investments in Windows 365 to meet your needs. This month, we’re excited to release two top requested features into Public Preview in Windows 365 Enterprise: Azure AD Join Windows 365 Cloud PC support – This has been by far the most requested feature since Windows 365 reached general availability. With Azure AD Join as a Cloud PC join type option, you no longer need an existing Azure infrastructure to use the service, just your Azure AD users. Localized first-run experience – This has been another huge feature request from organizations around the world. With this new option, you now have an expanded list of languages you can select from when creating Cloud PCs for your users, which will define the default Cloud PC experience for your users. Azure AD Join Windows 365 Cloud PC support Azure AD Join technology has been a huge investment across Microsoft, and we’re excited to bring that to Windows 365 Enterprise. Starting now in Public Preview, you no longer need an Azure subscription to provision Cloud PCs for your users. In the provisioning policy creation flow, simply select Microsoft Hosted Network and the desired region. Selecting Azure AD Join and Microsoft Hosted Network option when creating a provisioning policy through the Microsoft Endpoint Manager admin center If you do want to bring your own Azure virtual network, you can do that too! You’ll first need to create a new Azure AD Join network connection. Once those steps are completed, you can select your network from the Network drop-down menu during provisioning. Selecting an existing network when creating a provisioning policy through the Microsoft Endpoint Manager admin center That’s it! Once you progress past the General tab in the provisioning workflow, you’ll continue creating the provisioning policy like normal. That said, included in the “new normal” is the option for a localized first-run experience. Localized first-run experience Supporting our global Windows 365 customers is a top priority. We want to ensure that the configuration process for local language Cloud PCs is easy and available at first login. Now in Public Preview, when you create a provisioning policy, you can configure a Language & Region pack to be installed on the Cloud PCs during provisioning. There are 38 languages available. Selecting the language and region for Cloud PCs when creating a provisioning policy through the Microsoft Endpoint Manager admin center Additionally, you can change the configured language for existing provisioning policies and reprovision any desired Cloud PCs. If you have been localizing Cloud PCs by manually installing language packs onto a custom image, you can now skip that lengthy process and simply configure language settings in a gallery image! We are excited for you to begin using this feature. If you are currently using our Windows 365 Business offering and would benefit from this same feature, please provide feedback at Windows 365 feature requests. New regions available today As part of the February 2022 update for Windows 365, we’re also adding two new supported regions: US Central Germany West Central These new regions are available today. If you plan on using the new functionality of Azure AD Join and Microsoft hosted network, you will see these options in the Region drop-down. If you plan on bringing your own network, make sure you have already created the virtual network in one of these new regions, then create a new on-premises network connection with this virtual network. Stay informed, join the conversation With these new additions to Windows 365 Enterprise, we encourage you to learn more by watching a special episode of Windows in the Cloud. We'll demonstrate the new Azure AD Join capability plus other recent enhancements to Windows 365 Enterprise. We're also hosting monthly Windows 365 Ask Microsoft Anything (AMA) events, the fourth Wednesday of each month, to provide you with an opportunity to ask questions, learn valuable tips and tricks, and hear best practices on how to get the most from Windows 365. Our first AMA will be held Wednesday, February 23rd at 8:00 AM Pacific Time. Finally have feedback or suggestions? Visit Windows 365 feature requests to share your ideas and help shape the future of Windows 365! Continue reading...
-
Our discovery and analysis of a sophisticated Mac trojan in October exposed a year-long evolution of a malware family—and depicts the rising complexity of threats across platforms. The trojan, tracked as UpdateAgent, started as a relatively basic information-stealer but was observed distributing secondary payloads in the latest campaign, a capability that it added in one of its multiple iterations. Reminiscent of the progression of info-stealing trojans in other platforms, UpdateAgent may similarly become a vector for other threats to infiltrate target systems. Since its first appearance in September 2020, the malware displayed an increasing progression of sophisticated capabilities, and while the latest two variants were sporting much more refined behavior compared with earlier versions, they show signs that the malware is still in the development stage and more updates are likely to come. The latest campaign saw the malware installing the evasive and persistent Adload adware, but UpdateAgent’s ability to gain access to a device can theoretically be further leveraged to fetch other, potentially more dangerous payloads. UpdateAgent lures its victims by impersonating legitimate software and can leverage Mac device functionalities to its benefit. One of the most advanced techniques found in UpdateAgent’s latest toolbox is bypassing Gatekeeper controls, which are designed to ensure only trusted apps run on Mac devices. The trojan can leverage existing user permissions to quietly perform malicious activities before deleting the evidence to cover its tracks. UpdateAgent also misuses public cloud infrastructure, namely Amazon S3 and CloudFront services, to host its additional payloads. We shared our findings with the team at Amazon Web Services, and they have taken down the malicious URLs–another example of how intelligence sharing and collaboration results in better security for the broader community. Threats like UpdateAgent are proof that, as environments continue to rely on a diverse range of devices and operating systems, organizations need security solutions that can provide protection across platforms and a complete picture of their security posture. Microsoft Defender for Endpoint delivers and coordinates threat defense across all major OS platforms including Windows, macOS, Linux, Android and iOS. On macOS devices, Microsoft Defender for Endpoint detects and exposes threats and vulnerabilities through its antivirus, endpoint detection and response (EDR), and threat and vulnerability management capabilities. In this blog post, we share the evolving development of the UpdateAgent trojan targeting Mac users and detail the malware’s recent campaign to compromise devices, steal sensitive information, and distribute adware as a secondary payload. Progression of UpdateAgent UpdateAgent is uniquely characterized by its gradual upgrading of persistence techniques, a key feature that indicates this trojan will likely continue to use more sophisticated techniques in future campaigns. Like many information-stealers found on other platforms, the malware attempts to infiltrate macOS machines to steal data and it is associated with other types of malicious payloads, increasing the chances of multiple infections on a device. The trojan is likely distributed via drive-by downloads or advertisement pop-ups, which impersonate legitimate software such as video applications and support agents. This action of impersonating or bundling itself with legitimate software increases the likelihood that users are tricked into installing the malware. Once installed, UpdateAgent starts to collect system information that is then sent to its command-and-control (C2) server. Notably, the malware’s developer has periodically updated the trojan over the last year to improve upon its initial functions and add new capabilities to the trojan’s toolbox. The timeline below illustrates a series of techniques adopted by UpdateAgent from September 2020 through October 2021: Figure 1. Tracking the evolution of UpdateAgent September–December 2020: The initial version of UpdateAgent was considered to be a fairly basic information-stealer. At the time, the malware was only capable of performing reconnaissance to scan and collect system information such as product names and versions. Once gathered, the data was then sent as heartbeats to the malware’s C2 server. January–February 2021: Approximately two months later, UpdateAgent maintained its original capabilities and added a new one: the ability to fetch secondary payloads as .dmg files from public cloud infrastructure. DMG files are mountable disk images used to distribute software and apps to macOS, allowing the trojan to easily install additional programs on affected devices. March 2021: Upon its third update, the malware altered one of its prior functions to fetch secondary payloads as .zip files instead of .dmg files. The malware’s developer also included two new capabilities: the ability to bypass Gatekeeper by removing the downloaded file’s quarantine attribute and the ability to create a PLIST file that is added to the LaunchAgent folder. The quarantine attribute forces Gatekeeper to block the launch of any file downloaded from the web or other unknown sources, and it also displays a pop-up warning that users cannot open the respective file as “it is from an unidentified developer”. By removing the attribute, the malware both prevented the pop-up message warning users and allowed the files to launch without being blocked by Gatekeeper. Moreover, as the LaunchAgent folder specifies which apps and code automatically run each time a user signs into the machine, adding the malware’s PLIST file allowed it to be included in these automatic launches for persistence upon users signing into the affected device. August 2021: The malware’s fourth update further altered some of its prior capabilities. For one, it expanded its reconnaissance function to scan and collect System_profile and SPHardwaretype information. Additionally, UpdateAgent was changed to create and add PLIST files to the LaunchDaemon folder instead of the LaunchAgent folder. While targeting the LaunchDaemon folder instead of the LaunchAgent folder required administrative privileges, it permitted the malware to inject persistent code that ran as root. This code generally takes the form of background processes that don’t interact with users, thus it also improved the trojan’s evasiveness. October 2021: We detected the latest variants of UpdateAgent just over a year since its release into the wild. Sporting many of the updates found in the August 2021 variant, UpdateAgent still performed system reconnaissance, communicated with the C2 server as heartbeats, and bypassed Gatekeeper. Additionally, the October update expanded the malware’s ability to fetch secondary payloads as both .dmg or .zip files from public cloud infrastructure, rather than choosing between filetypes. Among its new capabilities, UpdateAgent included the ability to enumerate LSQuarantineDataURLString using SQLite in order to validate whether the malware’s downloaded app is within the Quarantine Events database where it would be assigned a quarantine attribute. The upgrade also allowed the malware to leverage existing user profiles to run commands requiring sudo access in addition to the ability to add arguments using PlistBuddy to create and edit PLIST files more easily. Lastly, the trojan included the ability to modify sudoers list, allowing the malware to bypass a prompt requiring high privilege user credentials while running UpdateAgent’s downloaded app. October 2021 Campaign In the October 2021 campaign, UpdateAgent included a larger set of sophisticated techniques than ever previously observed. The attackers distributed the trojanized app in .zip or .pkg format, conforming with a campaign observed in early 2021: Figure 2. Attack chain of the latest UpdateAgent campaign Upon analyzing UpdateAgent’s infrastructure, we determined that the infrastructure used in the October 2021 campaign was created at the end of September 2021, and we also discovered additional domains with payloads. This indicates that the trojan is still in the developmental stage and is likely to add or modify its capabilities in future updates and continue its track of improving its overall level of sophistication. We further observed two separate variants of the UpdateAgent trojan in its October 2021 campaign. Each variant leveraged different tactics to infect a device, as detailed below: Variant 1 The first variant of UpdateAgent takes the following steps to infect a device: A .zip file named HelperModule.zip downloads and installs UpdateAgent using a specific file path – /Library/Application Support/xxx/xxx. This .zip file is installed in /Library/Application Support/Helper/HelperModule. UpdateAgent collects operating system and hardware information about the affected device. Once the compromised device connects to the C2 server, the trojan uses a curl request to send this data to the C2 server. Upon successful connection, UpdateAgent requests a secondary payload, usually a .dmg or .zip file, which is hosted on a CloudFront instance. Once the secondary payload downloads, UpdateAgent uses the xattr command – /usr/bin/xattr -rc /tmp/setup.dmg, to remove the quarantine attribute of downloaded files and bypass Gatekeeper controls. UpdateAgent then extracts the secondary payload (.dmg or .zip). Once the file is mounted, it unzips and copies the payload files to a temporary folder, assigning executable permissions, and launches these files. UpdateAgent also uses PlistBuddy to create PLIST files under the LaunchAgent folder to remain persistent through system restart. UpdateAgent removes evidence by deleting the secondary payload, temporary folders, PLIST files, and all other downloaded artifacts. Variant 2 The second variant of UpdateAgent takes the following steps to infect a device: A third-party WebVideoPlayer application (WebVideoPlayer.pkg) with a post-install script downloads additional apps or .zip files as /Applications/WebVideoPlayer.app/Contents/MacOS/WebVideoPlayer. Notably, this application included a valid certificate that was later revoked by Apple in October 2021. The application scans the user profile to identify existing user IDs and assigned groups. The WebVideoPlayer application uses SQLite3 commands to determine if the .pkg file is within the Quarantine Events database, which contains URLs of downloaded files, mail addresses, and subjects for saved attachments. The .pkg payload extracts and drops UpdateAgent in /Library/Application Support/WebVideoPlayer/WebVideoPlayerAgent. The WebVideoPlayer application also assigns executable permissions to UpdateAgent and attempts to remove the quarantine attribute of the file using the xattr command to bypass Gatekeeper controls. The application then launches UpdateAgent and collects and sends the OS information to the attacker’s C2 server. Like the first variant, the second variant sends curl requests that download additional payloads, such as adware, and removes evidence by deleting all files and folders that it created. Adload adware UpdateAgent is further characterized by its ability to fetch secondary payloads that can increase the chances of multiple infections on a device, with the latest campaign pushing adware. We first observed UpdateAgent distributing adware as a secondary payload in its October 2021 campaign, identified as part of the Adload adware family by Microsoft Defender Antivirus. Similar to UpdateAgent, adware is often included in potentially unwanted or malicious software bundles that install the adware alongside impersonated or legitimate copies of free programs. In Adload’s case, we previously observed the adware family targeting macOS users had spread via rogue installers often found on malicious websites. Once adware is installed, it uses ad injection software and techniques to intercept a device’s online communications and redirect users’ traffic through the adware operators’ servers, injecting advertisements and promotions into webpages and search results. More specifically, Adload leverages a Person-in-The-Middle (PiTM) attack by installing a web proxy to hijack search engine results and inject advertisements into webpages, thereby siphoning ad revenue from official website holders to the adware operators. Adload is also an unusually persistent strain of adware. It is capable of opening a backdoor to download and install other adware and payloads in addition to harvesting system information that is sent to the attackers’ C2 servers. Considering both UpdateAgent and Adload have the ability to install additional payloads, attackers can leverage either or both of these vectors to potentially deliver more dangerous threats to target systems in future campaigns. Defending against macOS threats UpdateAgent’s evolution displays the increasing complexity of threats across platforms. Its developers steadily improved the trojan over the last year, turning a basic information-stealer into a persistent and more sophisticated piece of malware. This threat also exemplifies the trend of common malware increasingly harboring more dangerous threats, a pattern also observed in other platforms. UpdateAgent’s ability to gain access to a device can theoretically be leveraged by attackers to introduce potentially more dangerous payloads, emphasizing the need to identify and block threats such as this. Defenders can take the following mitigation steps to defend against this threat: Encourage the use of Microsoft Edge—available on macOS and various platforms—or other web browsers that support Microsoft Defender SmartScreen, which identifies and blocks malicious websites, including phishing sites, scam sites, and sites that contain exploits and host malware. Restrict access to privileged resources, such as LaunchDaemons or LaunchAgents folders and sudoers files, through OSX enterprise management solutions. This helps to mitigate common persistence and privilege escalation techniques. Install apps from trusted sources only, such as a software platform’s official app store. Third-party sources may have lax standards for the applications that they host, allowing malicious actors to upload and distribute malware. Run the latest version of your operating systems and applications. Deploy the latest security updates as soon as they become available. As organizational environments are intricate and heterogenous, running multiple applications, clouds, and devices, they require solutions that can protect across platforms. Microsoft Defender for Endpoint offers cross-platform security and a unified investigation experience that gives customers visibility across all endpoints and enables them to detect, manage, respond, and remediate threats, such as the capability to detect UpdateAgent’s anomalous use of PlistBuddy. Microsoft Defender for Endpoint customers can apply the following mitigations to reduce the environmental attack surface and mitigate the impact of this threat and its payloads: Turn on cloud-delivered protection and automatic sample submission on Microsoft Defender Antivirus. These capabilities use artificial intelligence and machine learning to quickly identify and stop new and unknown threats. Enable potentially unwanted application (PUA) protection in block mode to automatically quarantine PUAs like adware. PUA blocking takes effect on endpoint clients after the next signature update or computer restart. PUA blocking takes effect on endpoint clients after the next signature update or computer restart. Turn on network protection to block connections to malicious domains and IP addresses. Defender for Endpoint’s next-generation protection reinforces network security perimeters and includes antimalware capabilities to catch emerging threats, including UpdateAgent and its secondary payloads, C2 communications, and other malicious artifacts affiliated with the trojan’s reconnaissance activities. Moreover, macOS antimalware detections provide insight into where a threat originated and how the malicious process or activity was created, providing security teams a comprehensive view of incidents and attack chains. Finally, this research underscores the importance of understanding a macOS threat’s progression to not only remedy its current abilities, but to prepare for increased capabilities and sophistication of the threat. As threats on other OS platforms continue to grow, our security solutions must secure users’ computing experiences be it a Windows or non-Windows machine. By sharing our research and other forms of threat intelligence, collaboration across the larger security community can aid in enriching our protection technologies, regardless of the platform or device in use. Detection details Antivirus Microsoft Defender Antivirus detects threat components and behavior as the following malware: Trojan:MacOS/UpdateAgent.B Trojan:MacOS/UpdateAgent.A Trojan:MacOS/Agent.A Adware:MacOS/Adload.A Behavior:MacOS/UpdateAgent.B Endpoint detection and response (EDR) Alerts with the following titles in the Microsoft 365 Security Center can indicate threat activity within your network: macOS Gatekeeper bypass Executable permission added to file or directory Suspicious database access Suspicious System Hardware Discovery Suspicious binary dropped and launched Advanced hunting To locate activity related to UpdateAgent, run the following advanced hunting queries in Microsoft 365 Defender or Microsoft Defender Security Center. File quarantine attribute Look for file quarantine attribute removal for the specific packages involved in the campaign. DeviceProcessEvents | where FileName has "xattr" and (ProcessCommandLine has "-rc Library/Application Support/WebVideoPlayer/WebVideoPlayerAgent" or ProcessCommandLine has "-r -d /Library/Application Support/Helper/HelperModule") Quarantine Event database Look for quarantine event database enumeration through sqlite3 for the packages involved in the campaign. DeviceProcessEvents | where FileName has "sqlite3" and ProcessCommandLine has "WebVideoPlayer.pkg" Curl request Look for UpdateAgent’s curl requests. DeviceProcessEvents | where FileName has "curl" and ProcessCommandLine has "--connect-timeout 900 -L" Indicators Files (SHA-256) 1966d64e9a324428dec7b41aca852034cbe615be1179ccb256cf54a3e3e242ee ef23a1870d84e164a4234074251205190a5dfda9f465c8eee6c7e0d6878c2b05 519339e67b1d421d51a0f096e80a57083892bac8bb16c7e4db360bb0fda3cb11 cc2f246dda46b17e9302242879788aa114ee64327c8de43ef2b9ab56e8fb57b2 5c1704367332a659f6e10d55d08a3e0ab1bd26aa97654365dc82575356c80502 c60e210f73d5335f57f367bd7e166ff4c17f1073fd331370eb63342ab1c82238 f01dec606db8f66489660615c777113f9b1180a09db2f5d19fb5bca7ba3c28c7 4f1399e81571a1fa1dc822b468453122f89ac323e489f57487f6b174940e9c2e 9863bc1917af1622fdeebb3bcde3f7bebabcb6ef13eae7b571c8a8784d708d57 a1fba0bb0f52f25267c38257545834a70b82dbc98863aee01865a2661f814723 81cfa53222fa473d91e2a7d3a9591470480d17535d49d91a1d4a7836ec943d3a 78b4478cd3f91c42333561abb9b09730a88154084947182b2ec969995b25ad78 91824c6a36ef60881b4f502102b0c068c8a3acd4bceb86eb4ffd1043f7990763 86b45b861a8f0855c97cc38d2be341cc76b4bc1854c0b42bdca573b39da026ac 84ff961552abd742cc2393dde20b7b3b7b2cfb0019c80a02ac24de6d5fcc0db4 0ee6c8fd43c03e8dc7ea081dfa428f22209ed658f4ae358b867de02030cfc69b 443b6173ddfbcc3f19d69f60a1e5d72d68d28b7323fe2953d051b32b4171aa9a 409f1b4aeb598d701f6f0ed3b49378422c860871536425f7835ed671ba4dd908 77f084b5fc81c9c885a9b1683a12224642072f884df9e235b78941a1ad69b80d cbabbbb270350d07444984aa0ce1bb47078370603229a3f03a431d6b7a815820 053fbb833ac1287d21ae96b91d9f5a9cfdd553bc41f9929521d4043e91e96a98 29e3d46867caddde8bb429ca578dd04e5d7112dd730cd69448e5fb54017a2e30 356d429187716b9d5562fe6eee35ea60b252f1845724b0a7b740fbddec73350f a98ecd8f482617670aaa7a5fd892caac2cfd7c3d2abb8e5c93d74c344fc5879c c94760fe237da5786464ec250eadf6f7f687a3e7d1a47e0407811a586c6cb0fc eb71d15308bfcc00f1b80bedbe1c73f1d9e96fd55c86cf420f1f4147f1604f67 0c08992841d5a97e617e72ade0c992f8e8f0abc9265bdca6e09e4a3cb7cb4754 738822e109f1b14413ee4af8d3d5b2219293ea1a387790f207d937ca11590a14 0d9f861fe4910af8299ac3cb109646677049fa9f3188f52065a47e268438b107 a586ef06ab8dd6ad1df77b940028becd336a5764caf097103333975a637c51fa 73a465170feed88048dbc0519fbd880aca6809659e011a5a171afd31fa05dc0b d5c808926000bacb67ad2ccc4958b2896ea562f27c0e4fc4d592c5550e39a741 7067e6a69a8f5fdbabfb00d03320cfc2f3584a83304cbeeca7e8edc3d57bbbd4 939cebc99a50989ffbdbb2a6727b914fc9b2382589b4075a9fd3857e99a8c92a c5017798275f054ae96c69f5dd0b378924c6504a70c399279bbf7f33d990d45b 57d46205a5a1a5d6818ecd470b61a44aba0d935f256265f5a26d3ce791038fb4 e8d4be891c518898dd3ccdff4809895ed21558d90d415cee868bebdab2da7397 9f1989a04936cd8de9f5f4cb1f5f573c1871b63737b42d18ac4fa337b089cbdc b55c806367946a70d619f25e836b6883a36c9ad22d694a173866b57dfe8b29c9 e46b09b270552c7de1311a8b24e3fcc32c8db220c03ca0d8db05e08c76e536f1 f9842e31ed16fe0173875c38a41ed3a766041350b4efcd09da62718557ca3033 bad5dc1dd6ff19f9fb1af853a8989c1b0fdfeaa4c588443607de03fccf0e21c9 Download URLs hxxps://d35ep4bg5x8d5j[.]cloudfront[.]net/pkg hxxps://d7rp2fva69arq[.]cloudfront[.]net/pkg hxxps://daqi268hfl8ov[.]cloudfront[.]net/pkg hxxps://events[.]optimizerservices[.]com/pkg hxxps://ekogidekinvgwyzmeydw[.]s3[.]amazonaws[.]com/OptimizerProcotolStatus[.]zip hxxps://lnzjvpeyarvvvtljxsws[.]s3[.]amazonaws[.]com/ConsoleSoftwareUpdateAgent[.]zip hxxps://qqirhvehhnvuemxezfxc[.]s3[.]amazonaws[.]com/ModuleAgent[.]zip hxxps://dpqsxofvslaxjaiyjdok[.]s3[.]amazonaws[.]com/ProtocolStatus[.]zip hxxps://oldbrlauserz[.]s3[.]amazonaws[.]com/setup[.]zip hxxps://grxqorfazgqbmzeetpus[.]s3[.]amazonaws[.]com/SetupUpdateAgent[.]zip hxxps://phdhrhdsp[.]s3[.]amazonaws[.]com/setup[.]zip hxxps://xyxeaxtugahkwrcvbzsw[.]s3[.]amazonaws[.]com/BundleAgent[.]zip [.]s3[.]amazonaws[.]com/GuideServices[.]zip hxxps://tnkdcxekehzpnpvimdwquzwzgpehlnwgizrlmzev[.]s3[.]amazonaws[.]com/HelperModule[.]zip hxxps://svapnilpkasjmwtygfstkhsdfrraa[.]s3[.]amazonaws[.]com/WizardUpdate[.]zip The post The evolution of a Mac trojan: UpdateAgent’s progression appeared first on Microsoft Security Blog. Continue reading...
-
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. To improve an organization’s cybersecurity readiness, you need to test that your detection and prevention technologies work as intended and that your security program is performing as best it can. Research from a Poneman Institute survey found that amongst over 500 information technology and security leaders across sectors, 53 percent said they were uncertain about the effectiveness and performance of their cybersecurity capabilities.1 The reason? Even the most advanced security controls fail due to human error and configuration drift, and when they do, they fail silently. They need to be tested continuously to ensure performance. By analogy, even the best sports teams in the world need to exercise and prepare their defenses for attacks. If they don’t train, they atrophy. To ensure readiness, everyone needs to prepare for known threats. Measuring security effectiveness using MITRE ATT&CK® The good news is that the MITRE ATT&CK framework provides cyber defenders with known tactics, techniques, and behaviors that adversaries use to conduct an attack. Today, Microsoft and AttackIQ are working together, including through the Microsoft Evaluation Lab, to automate testing using MITRE ATT&CK and a threat-informed defense. AttackIQ is a part of the Microsoft Intelligent Security Association (MISA), an ecosystem of independent software vendors and managed security service providers that have integrated their solutions to better defend against a world of increasing threats. MISA helps break down silos between security organizations to build better-combined solutions and improve the world’s cybersecurity posture. AttackIQ enables Microsoft customers to test their use of Microsoft Defender for Endpoint, Azure native cloud security controls, and Microsoft Sentinel, running adversary emulations against the security program to generate detailed data that the team can use. With granular performance data, the customer can make informed decisions about people, processes, and technology, and elevate the security program’s overall performance. Let’s look at some of the ways the two companies work together. Emulating the adversary to test Microsoft Defender for Endpoint To validate cybersecurity readiness, to emulate cyberattacks with realism and specificity. It does so at scale and continuously, testing Microsoft Defender for Endpoint’s machine learning and AI-enabled technologies to generate granular data about security program performance. Testing Microsoft Azure and Microsoft Sentinel In addition to testing Microsoft Defender for Endpoint, the AttackIQ Security Optimization Platform runs assessments and scenarios against the native cloud controls in Microsoft Azure, leveraging research from MITRE Engenuity’s Center for Threat-Informed Defense that maps the native security controls in Azure to MITRE ATT&CK. AttackIQ has built assessments to measure the effectiveness of native cloud controls. In addition to Azure’s native controls, AttackIQ is integrated with Microsoft Sentinel, enabling Microsoft Sentinel users to test their detection pipeline and fine-tune security processes across their organization. Generating actionable performance data Security teams can schedule assessments to run against Microsoft Defender for Endpoint and Microsoft Azure as frequently as needed. Based on continuous testing, the AttackIQ Security Optimization Platform generates point-in-time and longitudinal data about security control performance, giving teams a sense of the program’s overall readiness. Aligning MITRE ATT&CK with Microsoft AttackIQ brings a deep alignment with MITRE ATT&CK to its automated security control validation for Microsoft’s security capabilities, leveraging a deep scenario library of tactics, techniques, and sub-techniques to validate security program performance. AttackIQ scenarios Below is an image of an AttackIQ interface scenario that provides a basic function check of Microsoft Defender for Endpoint. Within the AttackIQ Security Optimization Platform, users can select this scenario out of a range of scenarios within the platform to validate the effectiveness of Microsoft Defender for Endpoint. From there, the user can assign the scenario to run against Microsoft Defender for Endpoint to validate its effectiveness through their infrastructure. After running the scenario, the AttackIQ Security Optimization Platform shows results of how well Microsoft Defender for Endpoint performed in its prevention and detection functions, tipping the customer’s security team to any configuration challenges or other issues that may need attention. The AttackIQ Security Optimization Platform also includes scenarios for testing Azure blog storage accounts, as the below image shows. Beyond atomic tests of how well Microsoft Defender for Endpoint works in detecting and preventing an attacker’s tactics, techniques, and procedures (TTPs), AttackIQ’s Anatomic Engine chains together TTPs, aligned to the MITRE ATT&CK framework, in a realistic and comprehensive adversary attack flow to run a range of adversary TTPs against an organization. AttackIQ’s Anatomic Engine is designed to test advanced AI and machine learning-enabled defense capabilities like those within Microsoft Defender for Endpoint, Microsoft Azure, and Microsoft Sentinel, emulating the adversary with specificity and realism every step of the way. Once tests have been conducted, AttackIQ generates reports from a single point in time, or longitudinally over a period of time, to show how a security control or set of security controls have performed against the MITRE ATT&CK-aligned scenarios and attack flows that AttackIQ has built and run. The below illustrative diagrams show how AttackIQ generates performance data for detection and prevention failures and successes for a security control. The benefits of automated testing extend beyond single point-in-time analysis. The detection and prevention results can be aggregated longitudinally to show program performance over time. With real performance data, teams can identify control failures and gaps in the organization’s defensive posture, make adjustments or investments to improve performance and investigate unseen, underlying issues that may be impacting operations. Human performance evaluation Why is this important? It is not just about testing technology. All our technologies are run by human teams. Human factors, therefore, play a key role in security program performance, and the process of discovering the issues that are impacting a security team requires deeper investigation than simple acts of configuration management. But if you don’t test your controls, you will never know if you’re having a problem. Consider the example of a large AttackIQ healthcare customer. Automated testing revealed a security control failure in the customer’s defense capabilities, and on further investigation, they learned that it was due to a lapse in a managed security service provider (MSSP) contract. The security leader investigated the issue and discovered that his large security team faced a problem with attrition due to discrepancies in pay scales. His next call was to the head of human resources to talk about raising salaries. The technology, in this case, was not the problem: the issue was one of pay, not technology management. The process of continuous security validation revealed underlying issues in human resources that had a negative impact on the team’s ability to use an advanced technology effectively. A comprehensive partnership Security controls falter for a range of reasons, and continuous testing helps reveal areas of weakness and strength in a customer’s security program. Microsoft and AttackIQ are helping make cyberspace safe and secure by validating Microsoft’s security technologies through automated testing, underpinned by the MITRE ATT&CK framework. By emulating the adversary with realism and specificity every step of the way, AttackIQ helps Microsoft customers achieve their highest return on investment from the company’s security products. About AttackIQ AttackIQ, a leading independent vendor of breach and attack simulation solutions, built the industry’s first Security Optimization Platform for continuous security control validation and improving security program effectiveness and efficiency. AttackIQ is trusted by leading organizations worldwide to identify security improvements and verify that cyber defenses work as expected, aligned with the MITRE ATT&CK framework. The company is committed to giving back to the cybersecurity community through its free AttackIQ Academy, open Preactive Security Exchange, and partnership with MITRE Engenuity’s Center for Threat Informed Defense. For more information, visit their website. You can also follow AttackIQ on Twitter, LinkedIn, and YouTube. Learn more Visit Microsoft Defender for Endpoint. Explore Microsoft Azure. Start using Microsoft Sentinel today. To learn more about the Microsoft Intelligent Security Association (MISA), visit our website where you can learn about the MISA program, product integrations, and find MISA members. Visit the video playlist to learn about the strength of member integrations with Microsoft products. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. 1Security Investments Increasing, But 53% Leaders Unsure of Effectiveness, Jessica Davis, Health IT Security. July 30, 2019. The post Measure the effectiveness of your Microsoft security with AttackIQ appeared first on Microsoft Security Blog. Continue reading...
-
Microsoft has invested significant effort into understanding why Windows devices are not always fully up to date. One of the most impactful things we explored was how much time a device needs to be powered on and connected to Windows Update to be able to successfully install quality and feature updates. What we found is that devices that don’t meet a certain amount of connected time are very unlikely to successfully update. Specifically, data shows that devices need a minimum of two continuous connected hours, and six total connected hours after an update is released to reliably update. This allows for a successful download and background installations that are able to restart or resume once a device is active and connected. We call this measurement Update Connectivity: the time (in hours) that a device is powered on and also connected to Microsoft services such as Windows Update. This data can enable you to: Better understand which devices simply don’t have enough connected time to successfully update. Examine how to treat those devices in reporting and success measurements. Consider how to evaluate the security risk these rarely connected devices actually pose to your environment. For an indication how impactful Update Connectivity is, let's look at the portion of Windows 10 devices that are not on a current update and do not meet the minimum connectivity requirements. Approximately 50% of devices that are not on a serviced build of Windows 10 do not meet the minimum Update Connectivity measurement Approximately 25% of Windows 10 devices that are on a serviced build, but have security updates are more than 60 days out of date have less than the minimum Update Connectivity. Clearly, insufficient Update Connectivity is a significant cause of devices not being current. So how can you utilize this data to better help your organization? How Update Connectivity impacts update management You can work to ensure that more devices across your organization meet the minimum Update Connectivity measurement by communicating with device owners, encouraging them to leave their devices plugged in and connected—instead of powering them off overnight—so that updates can download and install properly. Impress upon them the importance of keeping their devices connected so their devices can stay protected and they can stay productive. Another consideration is power management. Some power settings and related policies put a device into a deep sleep or hibernation too quickly, which can prevent updates from occurring outside active hours. The Optimizing Windows Update Adoption provides recommended power settings that are a good balance of power savings while also enabling devices to keep up to date with the latest security updates. If you are using Group Policy Objects to manage policies, you can use the settings in the Windows security baselines, available as part of the Security Compliance Toolkit, to configure power settings. You might also want to consider filtering out devices that do not have the minimum Update Connectivity from your success metrics. The reasoning is that those devices are not currently "update healthy" and changing policies or targeting them with more updates will not get them to update until they meet the minimum Update Connectivity measurement required for update success. When thinking about the security impact of devices with insufficient Update Connectivity, a question to consider is do these devices pose less security risk because they have a very low level of connectivity? Every organization will, of course, have different business requirements and levels of risk tolerance, but Update Connectivity can be a useful tool in determining just how much risk these devices introduce and what actions, if any, should be taken to improve update compliance. When troubleshooting update issues, we have found it is best to select devices that have sufficient Update Connectivity. If a device has insufficient Update Connectivity, then investigating other update issues is complicated because the low Update Connectivity can create new issues that go away once there’s enough connectivity. Where to find Update Connectivity data You can currently see which devices have Insufficient Update Connectivity in Microsoft Intune. To find devices with an update policy not meeting the minimum Update Connectivity requirements navigate to Devices > Monitor and select either the Feature update failures or Windows Expedited update failures report. A failure report filtered to the Insufficient Update Connectivity alert, which shows devices with Insufficient Update Connectivity. The Insufficient Update Connectivity alert is also available in the Summary report in Intune. Navigate to Reports > Windows updates, then select the Reports tab, and select Windows Expedited update report. Devices with Insufficient Update Connectivity can be found using the Alert type column, as shown below. How devices with Insufficient Update Connectivity show up in the Windows Expedited update report in Intune Update Connectivity data is provided on a per-device basis and only measures how much time a device is active and has connectivity to Microsoft Windows Update services. This data is not correlated to user activity or behaviors, as a device can easily be in use, but not connected to the Internet. To summarize, Update Connectivity is a powerful way to understand why certain devices are not updating successfully and to evaluate how you measure deployment success by more accurately counting devices that meet the minimum requirements to update. Have questions or feedback? Drop a comment below or join us for Windows Office Hours every third Thursday here on the Windows Tech Community. Continue reading...
-
We have recently uncovered a large-scale, multi-phase campaign that adds a novel technique to traditional phishing tactics by joining an attacker-operated device to an organization’s network to further propagate the campaign. We observed that the second stage of the campaign was successful against victims that did not implement multifactor authentication (MFA), an essential pillar of identity security. Without additional protective measures such as MFA, the attack takes advantage of the concept of bring-your-own-device (BYOD) via the ability to register a device using freshly stolen credentials. The first campaign phase involved stealing credentials in target organizations located predominantly in Australia, Singapore, Indonesia, and Thailand. Stolen credentials were then leveraged in the second phase, in which attackers used compromised accounts to expand their foothold within the organization via lateral phishing as well as beyond the network via outbound spam. Connecting an attacker-controlled device to the network allowed the attackers to covertly propagate the attack and move laterally throughout the targeted network. While in this case device registration was used for further phishing attacks, leveraging device registration is on the rise as other use cases have been observed. Moreover, the immediate availability of pen testing tools, designed to facilitate this technique, will only expand its usage across other actors in the future. MFA, which prevents attackers from being able to use stolen credentials to gain access to devices or networks, foiled the campaign for most targets. For organizations that did not have MFA enabled, however, the attack progressed. Figure 1. Multi-phase phishing attack chain Phishing continues to be the most dominant means for attacking enterprises to gain initial entry. This campaign shows that the continuous improvement of visibility and protections on managed devices has forced attackers to explore alternative avenues. The potential attack surface is further broadened by the increase in employees who work-from-home which shifts the boundaries between internal and external corporate networks. Attackers deploy various tactics to target organizational issues inherent with hybrid work, human error, and “shadow IT” or unmanaged apps, services, devices, and other infrastructure operating outside standard policies. These unmanaged devices are often ignored or missed by security teams at join time, making them lucrative targets for compromising, quietly performing lateral movements, jumping network boundaries, and achieving persistence for the sake of launching broader attacks. Even more concerning, as our researchers uncovered in this case, is when attackers manage to successfully connect a device that they fully operate and is in their complete control. To fend off the increasing sophistication of attacks as exemplified by this attack, organizations need solutions that deliver and correlate threat data from email, identities, cloud, and endpoints. Microsoft 365 Defender coordinates protection across these domains, automatically finding links between signals to provide comprehensive defense. Through this cross-domain visibility, we were able to uncover this campaign. We detected the anomalous creation of inbox rules, traced it back to an initial wave of phishing campaign, and correlated data to expose the attackers’ next steps, namely device registration and the subsequent phishing campaign. Figure 2. Microsoft 365 Defender alert “Suspicious device registration following phishing” This attack shows the impact of an attacker-controlled unmanaged device that may become part of a network when credentials are stolen and Zero Trust policies are not in place. Microsoft Defender for Endpoint provides a device discovery capability that helps organizations to find certain unmanaged devices operated by attackers whenever they start having network interactions with servers and other managed devices. Once discovered and onboarded, these devices can then be remediated and protected. Figure 3. Microsoft Defender for Endpoint device discovery In this blog post, we share the technical aspects of a large-scale, multi-phase phishing campaign. We detail how attackers used the first attack wave to compromise multiple mailboxes throughout various organizations and implement an inbox rule to evade detection. This was then followed by a second attack wave that abused one organization’s lack of MFA protocols to register the attackers’ unmanaged device and propagate the malicious messages via lateral, internal, and outbound spam. First wave and rule creation The campaign leveraged multiple components and techniques to quietly compromise accounts and propagate the attack. Using Microsoft 365 Defender threat data, we found the attack’s initial compromise vector to be a phishing campaign. Our analysis found that the recipients received a DocuSign-branded phishing email, displayed below: Figure 4. First-stage phishing email spoofing DocuSign The attacker used a set of phishing domains registered under .xyz top-level domain. The URL domain can be described with the following regular expression syntax: UrlDomain matches regex @”^[a-z]{5}\.ar[a-z]{4,5}\.xyz” The phishing link was uniquely generated for each email, with the victim’s email address encoded in the query parameter of the URL. After clicking the link, the victim was redirected to a phishing website at newdoc-lnpye[.]ondigitalocean[.]app, which imitated the login page for Office 365. The fake login page was pre-filled with the targeted victim’s username and prompted them to enter their password. This technique increased the likelihood that the victim viewed the website as being legitimate and trustworthy. Figure 5. Phishing page with username prepopulated Next, we detected that the victim’s stolen credentials were immediately used to establish a connection with Exchange Online PowerShell, most likely using an automated script as part of a phishing kit. Leveraging the Remote PowerShell connection, the attacker implemented an inbox rule via the New-InboxRule cmdlet that deleted certain messages based on keywords in the subject or body of the email message. The inbox rule allowed the attackers to avoid arousing the compromised users’ suspicions by deleting non-delivery reports and IT notification emails that might have been sent to the compromised user. During our investigation of the first stage of this campaign, we saw over one hundred compromised mailboxes in multiple organizations with inbox rules consistently fitting the pattern below: Mailbox rule name Condition Action Spam Filter SubjectOrBodyContainsWords: “junk;spam;phishing;hacked;password;with you” DeleteMessage, MarkAsRead While multiple users within various organizations were compromised in the first wave, the attack did not progress past this stage for the majority of targets as they had MFA enabled. The attack’s propagation heavily relied on a lack of MFA protocols. Enabling MFA for Office 365 applications or while registering new devices could have disrupted the second stage of the attack chain. Device registration and second wave phishing One account belonging to an organization without MFA enabled was further abused to expand the attackers’ foothold and propagate the campaign. More specifically, the attack abused the organization’s lack of MFA enforcement to join a device to its Azure Active Directory (AD) instance, or possibly to enroll into a management provider like Intune to enforce the organization’s policies based on compliant devices. In this instance, the attackers first installed Outlook onto their own Windows 10 machine. This attacker-owned device was then successfully connected to the victim organization’s Azure AD, possibly by simply accepting Outlook’s first launch experience prompt to register the device by using the stolen credentials. An Azure AD MFA policy would have halted the attack chain at this stage. Though for the sake of comprehensiveness, it should be noted that some common red team tools, such as AADInternals and the command Join-AADIntDeviceToAzureAD, can be used to achieve similar results in the presence of a stolen token and lack of strong MFA policies. Azure AD evaluates and triggers an activity timestamp when a device attempts to authenticate, which can be reviewed to discover freshly registered devices. In our case, this includes a Windows 10 device either Azure AD joined or hybrid Azure AD joined and active on the network. The activity timestamp can be found by either using the Get-AzureADDevice cmdlet or the Activity column on the devices page in the Azure portal. Once a timeframe is defined and a potential rogue device is identified, the device can be deleted from Azure AD, preventing access to resources using the device to sign in. The creation of the inbox rule on the targeted account coupled with the attackers’ newly registered device meant that they were now prepared to launch the second wave of the campaign. This second wave appeared to be aimed at compromising additional accounts by sending lateral, internal, and outbound phishing messages. By using a device now recognized as part of the domain coupled with a mail client configured exactly like any regular user, the attacker gained the ability to send intra-organizational emails that were missing many of the typical suspect identifiers. By removing enough of these suspicious message elements, the attacker thereby significantly expanded the success of the phishing campaign. To launch the second wave, the attackers leveraged the targeted user’s compromised mailbox to send malicious messages to over 8,500 users, both in and outside of the victim organization. The emails used a SharePoint sharing invitation lure as the message body in an attempt to convince recipients that the “Payment.pdf” file being shared was legitimate. Figure 6. Second-stage phishing email spoofing SharePoint Like the first stage of the campaign, we found that the URL used in the second wave phishing emails matched the first’s wave structure and also redirected to the newdoc-lnpye[.]ondigitalocean[.]app phishing website imitating the Office 365 login page. Victims that entered their credentials on the second stage phishing site were similarly connected with Exchange Online PowerShell, and almost immediately had a rule created to delete emails in their respective inboxes. The rule had identical characteristics to the one created during the campaign’s first stage of attack. Generally, the vast majority of organizations enabled MFA and were protected from the attackers’ abilities to propagate the attack and expand their network foothold. Nonetheless, those that do not have MFA enabled could open themselves up to being victimized in potential future attack waves. Remediating device persistence: when resetting your password is not enough Analysis of this novel attack chain and the additional techniques used in this campaign indicates that the traditional phishing remediation playbook will not be sufficient here. Simply resetting compromised accounts’ passwords may ensure that the user is no longer compromised, but it will not be enough to eliminate ulterior persistence mechanisms in place. Careful defenders operating in hybrid networks need to also consider the following steps: Revocation of active sessions and any token associated with the compromised accounts Deletion of any mailbox rules eventually created by the actor Disable and removal of any rogue device joined to Azure AD by the actor If these additional remediation steps are not taken, the attacker could still have valuable network access even after successfully resetting the password of the compromised account. An in-depth understanding of this attack is necessary to properly mitigate and defend against this new type of threat. Defending against multi-staged phishing campaigns The latest Microsoft Digital Defense Report detailed that phishing poses a major threat to both enterprises and individuals, while credential phishing was leveraged in many of the most damaging attacks in the last year. Attackers targeting employee credentials, particularly employees with high privileges, typically use the stolen data to sign into other devices and move laterally inside the network. The phishing campaign we discussed in this blog exemplifies the increasing sophistication of these attacks. In order to disrupt attackers before they reach their target, good credential hygiene, network segmentation, and similar best practices increase the “cost” to attackers trying to propagate through the network. These best practices can limit an attacker’s ability to move laterally and compromise assets after initial intrusion and should be complemented with advanced security solutions that provide visibility across domains and coordinate threat data across protection components. Organizations can further reduce their attack surface by disabling the use of basic authentication, enabling multi-factor authentication for all users, and requiring multi-factor authentication when joining devices to Azure AD. Microsoft 365 global admins can also disable Exchange Online PowerShell for individual or multiple end users via a list of specific users or filterable attributes, assuming that the target accounts all share a unique filterable attribute such as Title or Department. For additional security, customers can enforce our new Conditional Access (CA) control requiring MFA to register devices, which can be combined with other CA conditions like device platform or trusted networks. Microsoft 365 Defender correlates the alerts and signals related to initial phishing generated by suspicious inbox rule creation as well as suspicious device registration into a single easy to comprehend Incident. Figure 7. Microsoft 365 Defender incident with suspicious device registration and inbox rule Microsoft Defender for Office 365 protects against email threats using its multi-layered email filtering stack, which includes edge protection, sender intelligence, content filtering, and post-delivery protection, in addition to including outbound spam filter policies to configure and control automatic email forwarding to external recipients. Moreover, Microsoft Defender for Office 365 uses Safe Links feature to proactively protect users from malicious URLs in internal messages or in an Office document at time of click. Safe Links feature to proactively protect users from malicious URLs in internal messages or in an Office document at time of click. Advanced hunting queries Hunting for emails with phishing URL let startTime = ago(7d); let endTime = now(); EmailUrlInfo | where Timestamp between (startTime..endTime) | where UrlDomain matches regex @"^[a-z]{5}\.ar[a-z]{4,5}\.xyz" | project NetworkMessageId,Url | join (EmailEvents | where Timestamp between (startTime..endTime)) on NetworkMessageId Hunting for suspicious Inbox Ruleslet startTime = ago(7d); // Hunting for suspicious Inbox Rules let startTime = ago(7d); let endTime = now(); CloudAppEvents | where Timestamp between(startTime .. endTime) | where ActionType == "New-InboxRule" | where RawEventData contains "Spam Filter" | where RawEventData has_any("junk","spam","phishing","hacked","password","with you") | where RawEventData contains "DeleteMessage" | project Timestamp, AccountDisplayName, AccountObjectId, IPAddress Hunting for rogue device registrations // Hunting for rogue device registrations let startTime = ago(7d); let endTime = now(); CloudAppEvents | where Timestamp between(startTime .. endTime) | where ActionType == "Add registered owner to device." | where RawEventData contains "notorius" | where AccountDisplayName == "Device Registration Service" | where isnotempty(RawEventData.ObjectId) and isnotempty(RawEventData.ModifiedProperties[0].NewValue) and isnotempty(RawEventData.Target[1].ID) and isnotempty(RawEventData.ModifiedProperties[1].NewValue) | extend AccountUpn = tostring(RawEventData.ObjectId) | extend AccountObjectId = tostring(RawEventData.Target[1].ID) | extend DeviceObjectId = tostring(RawEventData.ModifiedProperties[0].NewValue) | extend DeviceDisplayName = tostring(RawEventData.ModifiedProperties[1].NewValue) | project Timestamp,ReportId,AccountUpn,AccountObjectId,DeviceObjectId,DeviceDisplayName The post Evolved phishing: Device registration trick adds to phishers’ toolbox for victims without MFA appeared first on Microsoft Security Blog. Continue reading...
-
20 years ago this week, Bill Gates sent a now-famous email to all Microsoft employees announcing the creation of the Trustworthy Computing (TwC) initiative. The initiative was intended to put customer security, and ultimately customer trust, at the forefront for all Microsoft employees. Gates’ memo called upon teams to deliver products that are “as available, reliable and secure as standard services such as electricity, water services, and telephony.” Protecting customers is core to Microsoft’s mission. With more than 8,500 Microsoft security experts from across 77 countries, dedicated red and blue teams, 24/7 security operations centers, and thousands of partners across the industry, we continue to learn and evolve to meet the changing global threat landscape. In 2003, we consolidated our security update process into the first Patch Tuesday to provide more predictability and transparency for customers. In 2008, we published the Security Development Lifecycle to describe Microsoft’s approach to security and privacy considerations throughout all phases of the development process. Of course, the Trustworthy Computing initiative would not be where it is today without the incredible collaboration of the industry and community. In 2005, Microsoft held its first-ever “Blue Hat” security conference, where we invited external security researchers to talk directly to the Microsoft executives and engineers behind the products they were researching. Today, the Microsoft Security Response Center (MSRC) works with thousands of internal and external security researchers and professionals to quickly address security vulnerabilities in released products. Over the past 20 years, MSRC has triaged more than 70,000 potential security vulnerability cases shared by thousands of external security researchers and industry partners through Coordinated Vulnerability Disclosure (CVD) we’ve since issued more than 7,600 CVEs to help keep customers secure. Beginning in 2011 with the first Bluehat Award, we have rewarded more than $40 million through the Microsoft Bug Bounty Program to recognize these vital partnerships with the global security research community in over 60 countries. The security journey that began with TwC has involved many thousands of people across Microsoft and the industry. To celebrate 20 years of this commitment, partnership, and learning in customer security, we’re sharing the thoughts and stories of some of these employees, industry partners, experts, and contributors that helped make this journey possible. —Aanchal Gupta, VP of Microsoft Security Response Center The genesis of Trustworthy Computing In 2001 a small number of us “security people” started moving away from “security products” to think more about “securing features.” Many people think of ‘security’ as security products, like antimalware and firewalls. But this is not the whole picture. We formed a team named the Secure Windows Initiative (SWI) and worked closely with individual development teams to infuse more thought about securing their features. It worked well, but, it simply wasn’t scalable. David LeBlanc and I talked about things we had found working with various teams. We noticed we got asked the same code-level security questions time and again. So, we decided to write a book on the topic to cover the basics so we could focus on the hard stuff. That book was Writing Secure Code. During 2001, a couple of worms hit Microsoft products: CodeRed and Nimda. These two worms led some customers to rethink their use of Internet Information Services. Many of the learnings from this episode went into our book and made the book better. The worms also caused the C++ compiler team to start thinking about how they could add more defenses to the compiled code automatically. Microsoft Research began work on analysis tools to find security bugs. I could feel a change in the company. In October, I was asked by the .NET security team to look at some security bugs they had found. Because of how great these findings were, we decided to pause development, equip everybody with the latest in security training, and go looking for more security bugs. A part of my job was to train the engineering staff and to triage bugs as they came in. We fixed bugs and added extra defenses to .NET and ASP.NET. This event was known as the “.NET Security Stand Down.” Around the end of the Stand Down, I heard that Craig Mundie (who reported to Bill) was working on ‘something’ to move the company in a more security-focused direction. At the time, that’s all I knew. In December 2001, Writing Secure Code finally came, and I was asked to present at a two-hour meeting with Bill Gates to explain the nuances of security vulnerabilities. At the end of the meeting, I gave him a copy of Writing Secure Code. The following Monday he emailed me to say he had read the book and loved it. A few days later, Craig Mundie shared what he had been thinking about. He wanted the company to focus on Security, Privacy, Reliability, and Business Practices. These became the four pillars of Trustworthy Computing. Bill was sold on it and this all led to the now-famous BillG Trustworthy Computing memo of January 2002. —Michael Howard, Senior Principal Cybersecurity Consultant The evolution of the Security Development Lifecycle The Security Development Lifecycle (SDL) is around 20 years old now and has evolved significantly since its beginning with Windows. When we started to roll out the SDL across all products back then we often received criticism from teams that it was too Windows-centric. So, the first step was to make the SDL applicable to all teams—keeping the design goal of one SDL but understanding that requirements would vary based on features and product types. We shared our experiences and made the SDL public, followed by the release of tooling we developed including the Threat Modeling Tool, Attack Surface Analyzer (ASA), and DevSkim (these last two we published on GitHub as Open Source projects). As Microsoft started to adopt agile development methodologies and build its cloud businesses, the SDL needed to evolve to embrace this new environment and paradigm. That meant major changes to key foundations of the SDL like the bug bar, our approach to threat modeling, and how tools are integrated into engineering environments. It also presented new challenges in keeping to the one SDL principle while realizing that cloud environments are very different from the on-premises software we had traditionally shipped to customers. We have embraced new technologies such as IoT and made further adaptions to the SDL to handle non-Windows operating systems such as Linux and macOS. A huge change was Microsoft’s adoption of Open Source which extended the need for SDL coverage to many different development environments, languages, and platforms. More recently we have incorporated new SDL content to cover the development of Artificial Intelligence and Machine Learning solutions which bring a whole new set of attack vectors. The SDL has evolved and adapted over the last 20 years but it remains, as always, one SDL. —Mark Cartwright, Security Group Program Manager Securing Windows I started my career at Microsoft as a pen tester in Windows during one of the first releases to fully implement the SDL. I cherish that experience. Every day it felt like I was on the front lines of security. We had an incredible group of people—from superstar pen testers to superstar developers all working together to implement a security process for one of the world’s largest security products. It was a vibrant time and one of the first times I saw a truly cross-disciplinary team of security engineers, developers, and product managers all working together toward a common goal. This left a long-lasting and powerful impression on me personally and on the Windows security culture. For me, the key lesson learned from Trustworthy Computing is that good security is a byproduct of good engineering. In my naïve view before this experience, I assumed that the best way to get security in a product is to keep hiring security engineers until security improves. In reality, that approach is not possible. There will never be enough scale with security engineers and simply put good security requires engineering expertise that pen testing alone cannot achieve. —David Weston, Partner Director of OS Security and Enterprise An ever-changing industry The security industry is amazing in that it never stops changing. What’s even more amazing to me is that the core philosophies of the Trustworthy Computing initiative have continued to hold true—even during 20 years of drastic change. Compilers are a great foundational example of this. In the early days of the Trustworthy Computing initiative, Microsoft and the broader security industry explored groundbreaking features to protect against buffer overflows, including StackGuard, ProPolice, and the /GS flag in Microsoft Visual Studio. As attacks evolved, the guiding principles of Trustworthy Computing led to Microsoft continuously evolving the foundational building blocks of secure software as well: Data Execution Protection (DEP), Address Space Layout Randomization (ASLR), Control-flow Enforcement Technology (CET) to defend against Return-Oriented Programming (ROP), and speculative execution protections, just to name a few. Just by compiling software with a few switches, everyday developers could protect themselves against entire classes of exploits. Matt Miller gives a fascinating overview of this history in his . At a higher level, one of the things that I’ve been happiest to see change is the evolution away from security absolutism. In 2001, there was a lot of energy behind the “10 Immutable Laws of Security”, including several variants of “If an attacker can run a program on your computer, it’s not your computer anymore”. The real world, it turns out, is shades of grey. The landscape has evolved, and it’s not game over until defenders say it is. We have a rich industry that continually innovates around logging, auditing, forensics, incident response, and have evolved our strategies to include Assume Breach, Defense in Depth, “Impose Cost”, and more. For example: as dynamic runtimes have come of age (PowerShell, Python, C#), those that have evolved during the Trustworthy Computing era have become truly excellent examples of software that actively tilts the field in favor of defenders. While you may not be able to prevent all attacks, you can certainly make attackers regret using certain tools and regret landing on your systems. For a great overview of PowerShell’s journey, check out Defending Against PowerShell Attacks—PowerShell Team. When we launched the Trustworthy Computing effort, we never could have imagined the complexity of attacks the industry would be fending off in 2022—nor the incredible capability of Blue Teams defending against them. But by constantly refining and improving security as threats evolve, the world is far more secure today than it was 20 years ago. —Lee Holmes, Principal Security Architect, Azure Security The cloud is born The TWC initiative and the SDL that it created recognized that security is a fundamental pillar of earning and keeping customer trust—so must be infused into all of Microsoft’s product development. Since it was created, however, software has evolved from physical packages that Microsoft offers for customers to install, configure, and secure—to now include cloud services that Microsoft fully deploys and operates on behalf of customers. Microsoft’s responsibility to customers now includes not just developing secure software—but also operating it in a secure manner. It also extends to ensuring that services and operational practices meet customer privacy promises and government privacy regulations. Microsoft Azure leveraged the SDL framework and Trustworthy Computing principles from the very beginning to incorporate these additional aspects of software security and privacy. Having this foundation in place meant that instead of starting from scratch, we could enhance and extend the tools and processes that were already there for box-product software. Tools and processes like Threat Modeling and static and dynamic analysis were incredibly useful all the way to cloud scenarios like hostile multi-tenancy and DevOps. As we created, validated, and refined, we and other Microsoft cloud service teams contributed back to the SDL and tooling—including publishing many of these for use by our customers. It’s not an understatement to say that Microsoft Azure’s security and privacy traces its roots directly back to the TWC initiative launch 20 years ago. The cloud is constantly changing with the addition of new application architectures, programming models, security controls, and technologies like confidential computing. Static analysis tools like CodeQL provide better detections and CI/CD pipeline checks like CredScan help prevent entirely new forms of vulnerabilities that are specific to services. At the same time, the threat landscape continues to get more sophisticated. Software that does not necessarily follow SDL processes is now a critical part of every company’s supply chain. Just as the SDL today is much more sophisticated and encompasses far more aspects of the software lifecycle than it did 20 years ago, Microsoft will continue to invest in the SDL to address tomorrow’s software lifecycle and threats. —Mark Russinovich, Chief Technology Officer and Technical Fellow, Microsoft Azure An amazing community of researchers The introduction of the Trustworthy Computing initiative coincided with my first serious forays into Windows security research. For that reason, it has defined how I view the problems and challenges of information security, not just on Windows but across the industry. Many things that I take for granted, such as security-focused development practices or automatic updates were given new impetus from the expectations laid down 20 years ago. The fact that I’m still a Windows security researcher after all this time might give you the impression that the TwC initiative failed, but I think that’s an unfair characterization. The challenges of information security have not been static because the computing industry has not been static. Few would have envisaged quite how pervasive computing would be in our lives, and every connected endpoint can represent an additional security risk. For every security improvement a product makes, there’s usually a corresponding increase in system complexity which adds an additional attack surface. Finding exploitable bugs is IMO definitely harder than it was 20 years ago, and yet there are more places to look. No initiative is likely to be able to remove all security bugs from a product, at least not in anything of sufficient complexity. I feel the lasting legacy of the TwC initiative is not that it brought in a utopia of utmost security, regular news reports make it clear we’re not there yet. Instead, it brought security to the forefront, enabling it to become a first-class citizen in the defining industry of the 21st century. —James Forshaw, First Bluehat Mitigation Bounty Winner What I learned about Threat Intelligence from Trustworthy Computing I spent 10 years at Microsoft in Trustworthy Computing (TwC). I remember being at the meeting with Bill Gates where we talked about the need for a memo on security. From the Windows security stand-down, to XP SP2, to the creation of the Security Development Lifecycle and driving it across every product, to meeting security researchers all over the world and learning from their brilliance and passion, the Trustworthy Computing initiative shaped my entire career. One aspect of security that carries forward with me to this day is about the attacks that take place. Spending time finding and fixing security bugs leads to the world of zero-day exploits and the attackers behind them. Today I run the Microsoft Threat Intelligence Center (MSTIC) and our focus is uncovering attacks by actors all over the globe and what we can do to protect customers from them. One thing I took from my time in TwC was how important community is. No one company or organization can do it alone. That is certainly true in threat intelligence. It often feels like we hear about attacks as an industry, but defend alone. Yet when defenders work together, something amazing happens. We contribute our understanding of an attack from our respective vantage points and the picture suddenly gets clearer. Researchers contribute new attacker techniques to MITRE ATT&CK building our collective understanding. They publish detections in the form of Sigma and Yara rules, making knowledge executable. Analysts can create Jupyter notebooks so their expert analysis becomes repeatable by other defenders. A community-based approach can speed all defenders. While much of my work in TwC was focused inward on Microsoft and the engineering of our products and services, today’s attacks really put customers and fellow defenders at the center. Defense is a global mission and I am excited and hopeful about the opportunity to work on today’s most challenging problems with the world’s defenders. —John Lambert, Distinguished Engineer, Microsoft Threat Intelligence Center Learn more To learn more about Microsoft Security solutions visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. The post Celebrating 20 Years of Trustworthy Computing appeared first on Microsoft Security Blog. Continue reading...
-
With five months left until Internet Explorer 11 (IE11) retires on June 15, 2022 (for certain versions of Windows 10), it’s time to configure and test Internet Explorer (IE) mode in Microsoft Edge to make sure your business and your users are ready. This is also crucial if you are planning to upgrade to Windows 11 as Microsoft Edge with IE mode has officially replaced IE11 on that operating system and cannot be installed. If you’re just getting started with IE mode, stop before reading past this paragraph! We recommend you read our IE mode Getting Started Guide on our website or attend one of our webinars. While we wish we could offer 1:1 consultation for everyone, customers have appreciated interacting with Microsoft experts during a semi-live webinar or watching the on-demand webinar at their own pace to understand where to begin. And for your more detailed questions, we also have a technical FAQ, a comprehensive docs site, and a built to help you. If you’re in the process of setting up IE mode in Microsoft Edge, we also have you covered. In case you missed it, we recently released the new Cloud Site List Management experience, which lets you host your IE mode site list in an authenticated cloud endpoint accessed from the Microsoft 365 admin center. We’re also excited to share that Selenium’s IE Driver tool now supports automated, end-to-end testing for IE mode in Microsoft Edge. Read on to learn about how this can help you with site testing and to get additional tips on how to address the most common IE mode issues we’ve seen while working with customers. New capability for IE Driver lets you automate end-to-end browser testing for IE mode Businesses around the world have relied on Selenium’s IE Driver to automate their end-to-end browser testing needs and ensure their sites work with the Internet Explorer browser. With IE11 retirement fast approaching, Microsoft has collaborated with Selenium to extend IE Driver testing to include IE mode in Microsoft Edge. You can now take the same tests you’ve invested in and used across versions of IE and apply them for testing in IE mode. Running automated testing can catch issues early which, combined with testing through a pilot group of users, can help make sure you’re ready for IE retirement. Read more about how IE Driver can be used for IE mode testing in our docs. Avoid common IE mode issues: incorrect doc modes and missing neutral sites App Assure, our free site compatibility support program, provides customers with free expert remediation if they encounter site compatibility issues when setting up IE mode. Across hundreds of interactions, we’ve identified the most common customer issues and provided solutions: Common Issue #1: Using incorrect Document modes You can recognize that a site might be in the wrong document mode if the sizing and positioning of page elements are off or missing or, likewise, functionality is lost or not working. Key to solving this issue is to make sure to match the document mode and settings for the site when it worked correctly in IE11. You can also emulate various doc modes to see which works using the F12 Developer Toolbar. Read more about this here. Image of the F12 developer tool in Microsoft Edge Common Issue #2: Missing neutral sites Broken or looping user authentication experiences, or failed authentication errors, are common symptoms of this issue. Neutral sites play a key role in single sign-on (SSO) scenarios to maintain session and cookie information. If you notice that during the authentication experience that the site being redirected to drops the IE logo from the left side of the address bar (the visual indicator for being in IE mode) you’ll need to set that site as neutral in your enterprise site list. Read more about this here. For more tips, tricks, and questions answered about common issues, see our full IE mode troubleshooting guide. You can also contact App Assure directly if you have compatibility issues when setting up IE mode. Either request assistance or email them directly (ACHELP@microsoft.com) for free remediation assistance. Stress test your environment before IE retires The ultimate test to see if you are ready for IE retirement is to mimic the scenario before it happens. The added benefit is that if there are issues, you’ll still be able to revert to IE11 while addressing them. With the Disable Internet Explorer 11 as a standalone browser policy, you can do just that. Once you’ve configured and tested IE mode, your last step should be to enable this policy with a pilot group of users to make sure that everything works as tested. Not only will you get one final check, but it is also a great step in your change management process. Enabling the policy disables IE11 for users completely and will direct them to Microsoft Edge with IE mode instead. Learn more on how to enable this policy after setting up IE mode here. Customers have already found success moving from IE11 to Microsoft Edge with IE mode Setting up IE mode in Microsoft Edge not only prepares your business for IE retirement and for upgrading to Windows 11, but also gives your organization a dual engine advantage—your users will have IE mode to access those business-critical legacy sites and the fast, modern Chromium engine for everything else. But don’t just take our word for it! Customers around the world have transitioned from IE11 to Microsoft Edge with IE mode and are already seeing the benefits. Read about their stories here. Consolidated resources for IE retirement Phase 1: Get started with site discovery and more Website + Getting Started Guide IE Retirement Technical FAQ Learn about Cloud Site List Management Configure IE mode guided experience Phase 2: Test Use IE Driver to automate IE mode testing Avoid common issues using the Troubleshooting Guide Phase 3: Disable IE and implement change management Stress test your environment by disabling IE using Group Policy Review and use the adoption kit Continue the conversation. Find best practices. Visit the Windows Tech Community. Stay informed. For the latest updates on new releases, tools, and resources, stay tuned to this blog and follow us @MSWindowsITPro on Twitter. Continue reading...
-
Following our discovery of the “Shrootless” vulnerability, Microsoft uncovered a new macOS vulnerability, “powerdir,” that could allow an attacker to bypass the operating system’s Transparency, Consent, and Control (TCC) technology, thereby gaining unauthorized access to a user’s protected data. We shared our findings with Apple through Coordinated Vulnerability Disclosure (CVD) via Microsoft Security Vulnerability Research (MSVR). Apple released a fix for this vulnerability, now identified as CVE-2021-30970, as part of security updates released on December 13, 2021. We encourage macOS users to apply these security updates as soon as possible. Introduced by Apple in 2012 on macOS Mountain Lion, TCC is essentially designed to help users configure the privacy settings of their apps, such as access to the device’s camera, microphone, or location, as well as access to the user’s calendar or iCloud account, among others. To protect TCC, Apple introduced a feature that prevents unauthorized code execution and enforced a policy that restricts access to TCC to only apps with full disk access. We discovered that it is possible to programmatically change a target user’s home directory and plant a fake TCC database, which stores the consent history of app requests. If exploited on unpatched systems, this vulnerability could allow a malicious actor to potentially orchestrate an attack based on the user’s protected personal data. For example, the attacker could hijack an app installed on the device—or install their own malicious app—and access the microphone to record private conversations or capture screenshots of sensitive information displayed on the user’s screen. It should be noted that other TCC vulnerabilities were previously reported and subsequently patched before our discovery. It was also through our examination of one of the latest fixes that we came across this bug. In fact, during this research, we had to update our proof-of-concept (POC) exploit because the initial version no longer worked on the latest macOS version, Monterey. This shows that even as macOS or other operating systems and applications become more hardened with each release, software vendors like Apple, security researchers, and the larger security community, need to continuously work together to identify and fix vulnerabilities before attackers can take advantage of them. Microsoft security researchers continue to monitor the threat landscape to discover new vulnerabilities and attacker techniques that could affect macOS and other non-Windows devices. The discoveries and insights from our research enrich our protection technologies and solutions, such as Microsoft Defender for Endpoint, which allows organizations to gain visibility to their networks that are increasingly becoming heterogeneous. For example, this research informed the generic detection of behavior associated with this vulnerability, enabling Defender for Endpoint to immediately provide visibility and protection against exploits even before the patch is applied. Such visibility also enables organizations to detect, manage, respond to, and remediate vulnerabilities and cross-platform threats faster. In this blog post, we will share some information about TCC, discuss previously reported vulnerabilities, and present our own unique findings. TCC overview As mentioned earlier, TCC is a technology that prevents apps from accessing users’ personal information without their prior consent and knowledge. The user commonly manages it under System Preferences in macOS (System Preferences > Security & Privacy > Privacy): Figure 1. The macOS Security & Privacy pane that serves as the front end of TCC. TCC maintains databases that contain consent history for app requests. Generally, when an app requests access to protected user data, one of two things can happen: If the app and the type of request have a record in the TCC databases, then a flag in the database entry dictates whether to allow or deny the request without automatically and without any user interaction. If the app and the type of request do not have a record in the TCC databases, then a prompt is presented to the user, who decides whether to grant or deny access. The said decision is backed into the databases so that succeeding similar requests will now fall under the first scenario. Under the hood, there are two kinds of TCC databases. Each kind maintains only a subset of the request types: User-specific database: contains stored permission types that only apply to the specific user profile; it is saved under ~/Library/Application Support/com.apple.TCC/TCC.db and can be accessed by the user who owns the said profile System-wide database: contains stored permission types that apply on a system level; it is saved under /Library/Application Support/com.apple.TCC/TCC.db and can be accessed by users with root or full disk access macOS implements the TCC logic by using a special daemon called tccd. Indeed, there are at least two instances of tccd: one run by the user and the other by root. Figure 2. Two tccd instances: per-user and system-wide. Each type of request starts with a kTCCService prefix. While not an exhaustive list, below are some examples: Request type Description Handled by kTCCServiceLiverpool Location services access User-specific TCC database kTCCServiceUbiquity iCloud access User-specific TCC database kTCCServiceSystemPolicyDesktopFolder Desktop folder access User-specific TCC database kTCCServiceCalendar Calendar access User-specific TCC database kTCCServiceReminders Access to reminders User-specific TCC database kTCCServiceMicrophone Microphone access User-specific TCC database kTCCServiceCamera Camera access User-specific TCC database kTCCServiceSystemPolicyAllFiles Full disk access capabilities System-wide TCC database kTCCServiceScreenCapture Screen capture capabilities System-wide TCC database Table 1. Types of TCC requests. It should also be noted that the TCC.db file is a SQLITE database, so if a full disk access is granted to a user, they can view the database and even edit it: Figure 3. Dumping the TCC.db access table, given a full disk access. The database columns are self-explanatory, save for the csreq column. The csreq values contain a hexadecimal blob that encodes the code signing requirements for the app. These values can be calculated easily with the codesign and csreq utilities, as seen in Figure 4 below: Figure 4. Building the csreq blob manually for an arbitrary app. Given these, should a malicious actor gain full disk access to the TCC databases, they could edit it to grant arbitrary permissions to any app they choose, including their own malicious app. The affected user would also not be prompted to allow or deny the said permissions, thus allowing the app to run with configurations they may not have known or consented to. Securing (and bypassing) TCC: Techniques and previously reported vulnerabilities Previously, apps could access the TCC databases directly to view and even modify their contents. Given the risk of bypass mentioned earlier, Apple made two changes. First, Apple protected the system-wide TCC.db via System Integrity Protection (SIP), a macOS feature that prevents unauthorized code execution. Secondly, Apple enforced a TCC policy that only apps with full disk access can access the TCC.db files. Note, though, that this policy was also subsequently abused as some apps required such access to function properly (for example, the SSH daemon, sshd). Interestingly, attackers can still find out whether a user’s Terminal has full disk access by simply trying to list the files under /Library/Application Support/com.apple.TCC. A successful attempt means that the Terminal has full disk access capabilities, and an attacker can, therefore, freely modify the user’s TCC.db. In addition, there have been several previously reported vulnerabilities related to TCC bypass. These include the following: Time Machine mounts (CVE-2020-9771): macOS offers a built-in backup and restore solution called Time Machine. It was discovered that Time Machine backups could be mounted (using the apfs_mount utility) with the “noowners” flag. Since these backups contain the TCC.db files, an attacker could mount those backups and determine the device’s TCC policy without having full disk access. Environment variable poisoning (CVE-2020-9934): It was discovered that the user’s tccd could build the path to the TCC.db file by expanding $HOME/Library/Application Support/com.apple.TCC/TCC.db. Since the user could manipulate the $HOME environment variable (as introduced to tccd by launchd), an attacker could plant a chosen TCC.db file in an arbitrary path, poison the $HOME environment variable, and make TCC.db consume that file instead. Bundle conclusion issue (CVE-2021-30713): First disclosed by Jamf in a blog post about the XCSSET malware family, this bug abused how macOS was deducing app bundle information. For example, suppose an attacker knows of a specific app that commonly has microphone access. In that case, they could plant their application code in the target app’s bundle and “inherit” its TCC capabilities. Apple has since patched these vulnerabilities. However, based on our research, the potential bypass to TCC.db can still occur. The following section discusses the vulnerability we discovered and some details about the POC exploits we developed to prove the said vulnerability. Modifying the home directory: The ‘powerdir’ vulnerability In assessing the previous TCC vulnerabilities, we evaluated how Apple fixed each issue. One fix that caught our attention was for CVE-2020-9934 (the $HOME environment variable poisoning vulnerability). The fix can be seen in the _db_open function in tccd: Figure 5. The tccd fix for CVE-2020-9934. We noted that instead of expanding the $HOME environment variable, Apple decided to invoke getpwuid() on the current user (retrieved with getuid()). First, the getpwuid function retrieves a structure in memory (struct password*) that contains information about the given user. Then, tccd extracts the pwdir member from it. This pwdir member includes the user’s home directory, and its value persists even after the $HOME environment variable is modified. While the solution indeed prevents an attack by environment variable poisoning, it does not protect against the core issue. Thus, we set out to investigate: can an app programmatically change the user’s home directory and plant a fake TCC.db file? The first POC exploit Our first attempt to answer the above question was simple: plant a fake TCC.db file and change the home directory using the Directory Services command-line utility (dscl): While requiring root access, we discovered that this works only if the app is granted with the TCC policy kTCCServiceSystemPolicySysAdminFiles, which the local or user-specific TCC.db maintains. That is weaker than having full disk access, but we managed to bypass that restriction with the dsexport and dsimport utilities. Next, simply by exporting the Directory Services entry of a user, manipulating the output file, and importing the file again, we managed to bypass the dscl TCC policy restriction. Our first POC exploit, therefore, does the following: Get a csreq blob for the target app. Plant a fake TCC.db file with required access and the csreq blob. Export the user’s Directory Services entry with dsexport. Modify the Directory Services entry to change the user’s home directory. Import the modified Directory Services entry with dsimport. Stop the user’s tccd and reboot the process. Using this exploit, an attacker could change settings on any application. In the screenshot below, we show how the exploit could allow attackers to enable microphone and camera access on any app, for example, Teams. Figure 6. Our first working POC exploit working without a popup notification from TCC. We reported our initial findings to the Apple product security team on July 15, 2021, before becoming aware of a similar bypass presented by Wojciech Reguła and Csaba Fitzl at BlackHat USA 2021 in August. However, our exploit still worked even after Apple fixed the said similar finding (now assigned as CVE-2020-27937). Therefore, we still considered our research to be a new vulnerability. Monterey release and the second POC exploit We shared our findings to Apple through Coordinated Vulnerability Disclosure (CVD) via Microsoft Security Vulnerability Research (MSVR) before the release of macOS Monterey in October. However, upon the release of the said version, we noticed that our initial POC exploit no longer worked because of the changes made in how the dsimport tool works. Thus, we looked for another way of changing the home directory silently. While examining macOS Monterey, we came across /usr/libexec/configd, an Apple binary shipped with the said latest macOS release that is a System Configuration daemon responsible for many configuration aspects of the local system. There are three aspects of configd that we took note and made use of: It is an Apple-signed binary entitled with “com.apple.private.tcc.allow” with the value kTCCServiceSystemPolicySysAdminFiles. This means it can change the home directory silently. It has extensibility in configuration agents, which are macOS Bundles under the hood. This hints that it might load a custom Bundle, meaning we could inject code for our purposes. It does not have the hardened runtime flag to load custom configuration agents. While this aspect is most likely by design, it also means we could load completely unsigned code into it. By running configd with the -t option, an attacker could specify a custom Bundle to load. Therefore, our new POC exploit replaces the dsexport and dsimport method of changing the user’s home directory with a configd code injection. This results in the same outcome as our first POC exploit, which allows the modification of settings to grant, for example, any app like Teams, to access the camera, among other services. As before, we shared our latest findings with Apple. Again, we want to thank their product security team for their cooperation. Detecting the powerdir vulnerability with Microsoft Defender for Endpoint Our research on the powerdir vulnerability is yet another example of the tight race between software vendors and malicious actors: that despite the continued efforts of the former to secure their applications through regular updates, other vulnerabilities will inevitably be uncovered, which the latter could exploit for their own gain. And as system vulnerabilities are possible entry points for attackers to infiltrate an organization’s network, comprehensive protection is needed to allow security teams to manage vulnerabilities and threats across all platforms. Microsoft Defender for Endpoint is an industry-leading, cloud-powered endpoint security solution that lets organizations manage their heterogeneous computing environments through a unified security console. Its threat and vulnerability management capabilities empower defenders to quickly discover, prioritize, and remediate misconfigurations and vulnerabilities, such as the powerdir vulnerability. In addition, Defender for Endpoint’s unparalleled threat optics are built on the industry’s deepest threat intelligence and backed by world-class security experts who continuously monitor the threat landscape. One of the key strengths of Defender for Endpoint is its ability to generically detect and recognize malicious behavior. For example, as seen in the previous section, our POC exploits conduct many suspicious activities, including: Dropping a new TCC.db file with an appropriate directory structure Killing an existing tccd instance Suspicious Directory Services invocations such as dsimport and dsexport By generically detecting behavior associated with CVE-2020-9934 (that is, dropping a new TCC.db file fires an alert), Defender for Endpoint immediately provided protection against these exploits before the powerdir vulnerability was patched. This is a testament of Defender for Endpoint’s capabilities: with strong, intelligent generalization, it will detect similar bypass vulnerabilities discovered in the future. Figure 7. Microsoft Defender for Endpoint detecting potential TCC bypass. Learn how Microsoft Defender for Endpoint delivers a complete endpoint security solution across all platforms. Jonathan Bar Or Microsoft 365 Defender Research Team The post New macOS vulnerability, “powerdir,” could lead to unauthorized user data access appeared first on Microsoft Security Blog. Continue reading...
-
Merry Christmas to all of you and your families. Have a great holiday.
-
The Cloud Site List Management experience allows you to host your Internet Explorer (IE) mode site list in an authenticated cloud endpoint in the Microsoft 365 admin center and is now generally available for you to use. With this experience and the companion Configure IE mode deployment guide, you can create, host, and deploy your IE mode site list and related policies directly from the Microsoft 365 admin center. This is the latest addition to the tools shared in previous blogs to help businesses in their Internet Explorer to Microsoft Edge journey. Store and manage your site list in the cloud The Cloud Site List Management experience enables you to manage your site lists for IE mode in the cloud without needing on-premises infrastructure to host your organization's site list. You can access this through the Microsoft Edge site lists page found in Settings > Org settings within the Microsoft 365 admin center. You can create, import, edit, and export your site lists, as well as publish site lists from the cloud. The Org settings page and where to find Microsoft Edge site lists. You can create and publish multiple site lists from the Microsoft Edge site lists page and use group policy to assign different groups of devices to use those different lists. For a walkthrough of the Cloud Site List Management experience through the Microsoft Edge site lists page, you can check out the latest video from Microsoft Mechanics. Apply IE mode policies and site lists to users To use a cloud site list, your users must be signed into Microsoft Edge version 93 or later with a work or school account from your organization. You also need to have the InternetExplorerIntegrationLevel and the InternetExplorerIntegrationCloudSiteList group policies configured on their devices. The quickest way to deploy the necessary policies is to click the link for the Configure IE mode deployment guide after you’ve published your site list. The link for this guide is conveniently provided on the Microsoft Edge site lists page as seen below. Accessing the Configure IE mode deployment guide from the Microsoft Edge site lists page When using the Configure IE mode deployment guide, you will start by selecting your deployment method. When your devices are managed by Microsoft Intune, the guide will help you deploy a device configuration profile for either a cloud or on-premises site list. Or, if you prefer to use Configuration Manager or just group policy, the guide will generate a script to verify your on-premises configuration and automatically configure these settings. Configuring an IE mode device configuration profile in the Microsoft 365 admin center Regardless of where you are in the process or the management tool you’re using, you can use the Configure IE mode deployment guide to meet the following goals: Add sites to a site list one at a time Deploy Enterprise Site Discovery policies to find sites that should go on the site list Build a site list from site discovery data you’ve collected previously Apply a completed cloud or on-premises site list to users In addition, the following improvements are coming to the Configure IE mode deployment guide in the coming weeks. >While building your site list, it will detect sites that are on the Microsoft Edge required sites public list so you can easily identify and remove them. You’ll be able to import and merge site lists between the .v1 and .v2 schema format. How to access these tools Permissions Global administrators can use all the features of both experiences, but we know that admins who manage browsers may not have the global admin role. To use the Cloud Site List Management experience on the Microsoft Edge site lists page in the Microsoft 365 admin center, you must use an account with at least the Edge administrator role, and it must have an Exchange mailbox. To use the Configure IE mode deployment guide, you must use an account with at least the Global Reader admin role. To deploy Intune policies in the guide, your account must be assigned the Intune administrator role. For more information, see About admin roles. Navigation If you already know what sites you need to add and want to host your list in the cloud, open the Org settings page in the Microsoft 365 admin center and select Microsoft Edge site lists. If you’re just getting started with IE mode, go to the Configure IE mode guide first. For Microsoft Edge guidance that encompasses IE mode and beyond, go to the Microsoft Edge setup guide. You can find more information about both guides—and how to use them—in our previous blog, Proven tools to accelerate your move to Microsoft Edge. Continue the conversation. Find best practices. Visit the Windows Tech Community. Stay informed. For the latest updates on new releases, tools, and resources, stay tuned to this blog and follow us @MSWindowsITPro on Twitter. Continue reading...
-
Multiple Qakbot campaigns that are active at any given time prove that the decade-old malware continues to be many attackers’ tool of choice, a customizable chameleon that adapts to suit the needs of the multiple threat actor groups that utilize it. Since emerging in 2007 as a banking Trojan, Qakbot has evolved into a multi-purpose malware that provides attackers with a wide range of capabilities: performing reconnaissance and lateral movement, gathering and exfiltrating data, or delivering other payloads on affected devices. Its modular nature allows Qakbot to persist in today’s computing landscape because it enables attackers to pick and choose the “building blocks” they need for each attack chain depending on the network environment the malware lands on. In many cases, the attackers who deliver Qakbot also sell access to affected devices to other threat actors, who use the said access for their own goals. For example, Qakbot infections have been known to lead to human-operated ransomware, including Egregor or Conti. Its impact, therefore, is far-reaching: based on our threat data, recent Qakbot activities are seen in several countries and territories across almost all the continents: Africa, Asia, Europe, and the Americas. Qakbot’s modularity and flexibility could pose a challenge for security analysts and defenders because concurrent Qakbot campaigns could look strikingly different on each affected device, significantly impacting how these defenders respond to such attacks. Therefore, a deeper understanding of Qakbot is paramount in building a comprehensive and coordinated defense strategy against it. Based on our research and analysis of three recent notable Qakbot campaigns, we break down a Qakbot attack chain into several distinct building blocks. Within each campaign, some of these building blocks are consistent, although not all will be observed. Knowing these details allows defenders to correctly identify related threats and attacks, regardless of their source. Such intelligence and insights also feed into Microsoft’s multi-layer protection technologies, like those delivered through Microsoft 365 Defender, to detect and block these threats at various stages of the attack chain. This blog post provides technical details of each of the building blocks that comprise Qakbot campaigns. It also includes mitigation recommendations and advanced hunting queries to help defenders proactively surface this threat. From email to ransomware: Breaking down a Qakbot campaign Like other modular malware, Qakbot infections may look differently on each affected device, depending on the operator using the said malware and their deployment of the threat campaign. However, based on our analysis, one can break down a Qakbot-related incident into a set of distinct “building blocks,” which can help security analysts identify and respond to Qakbot campaigns. Figure 1 below represents these building blocks. From our observation, each Qakbot attack chain can only have one block of each color. The first row and the macro block represent the email mechanism used to deliver Qakbot. Figure 1. Qakbot attack chain “building blocks” observed Certain building blocks within each campaign are consistent, but not all of them are observed on each affected device. As seen in a sample Qakbot campaign below (Figure 2), the top two rows represent the mechanisms adopted to deliver the malware on the three devices, while the succeeding ones are the activities it performs once running on each device. For instance, notice that Devices A and C were seen to have email exfiltration, while Device B was not: Figure 2. Sample differences among devices affected by a single Qakbot campaign Therefore, from an analyst’s viewpoint, what Figure 2 implies is that even if email exfiltration was not observed in one device, it doesn’t mean that this routine didn’t happen at all in their organization’s network. From our research, we identified ten building blocks, which we will discuss in the succeeding sections. Email delivery Qakbot is delivered via one of three email methods: malicious links, malicious attachments, or, more recently, embedded images. The messages in these email campaigns typically consist of one- or two-sentence lures (for example, “please see attached” or “click here to view a file”). Such brevity provides sufficient information and a call to action for the target users but little for content security solutions to detect. Figure 3. Sample Qakbot campaign email message Malicious links The email campaigns we observed delivering Qakbot typically include the URLs that download the malware on target devices in the message body. Earlier this year, we began to observe that some of these URLs were missing the HTTP or HTTPS protocol, rendering them unclickable in most email clients. Therefore, to download the malware, target recipients had to manually enter the link into a browser. Figure 4. Sample Qakbot campaign email containing an unclickable URL and fake-reply lure Although the missing protocol poses a challenge for some email security solutions that detonate links through sandboxing, the extra step needed from targets to copy and paste the URL hinders the attack’s success rate. However, it should also be noted that what the messages sometimes lack in formatting, they make up for in the content by using fake-reply lures. This fake-reply technique, which has already been seen in previous Qakbot and other major malware delivery campaigns, uses stolen subject lines and message content to construct a malicious reply to appear as part of a prior email thread. Qakbot is also known for reusing email threads exfiltrated from prior infections to create new templates for their next email campaign runs, allowing an attacker to use an actual subject line and message content to construct the spoofed reply. This increases the likelihood of target users clicking or copy-pasting the link because the message they receive from this campaign feels more expected. At the same time, attackers benefit from growing entropy among messages because no two emails in the same campaign will be alike. Unfortunately, such entropy also makes it more difficult for security analysts and defenders to fully scope a campaign. Malicious attachments Some Qakbot-related emails sent by attackers may include a ZIP file attachment. Within the ZIP is a spreadsheet containing Excel 4.0 macros. The attachment name is meant to appear as an official corporate document to trick a target recipient into opening it. For example, between September and November this year, the naming patterns we observed for the attachment included but were not limited to the following: CMPL-[digits]-[month]-[day].zip Compensation_Reject-[digits]-[mmddyyyy].zip Document_[digits]-[mmddyyyy].zip Document_[digits]-Copy.zip PRMS-[digits].zip Rebate-[digits]-[mmddyyyy].zip REF-[digits]-[month]-[day].zip TXN-[digits].zip Figure 5. Sample Qakbot campaign email containing a ZIP attachment Embedded images In its third and most recent evolution, Qakbot arrives via an email message that only contains an embedded image in its body, a stark contrast to its previous delivery methods that used file attachments or direct hyperlinks. We uncovered this Qakbot campaign while investigating malware infections from malicious Excel files associated with emails that abuse Craigslist’s email messaging system to deliver malicious files—a routine first reported by INKY. This campaign is more involved than previous Qakbot email campaigns because, unlike its previous delivery methods, the malicious components in the email (in this case, the malicious URL) are not in the message body as text but are contained instead within an image designed to look like the message body. The image instructs recipients to type the URL directly in their browser to download an Excel file that eventually leads to Qakbot. The said image is a screenshot of text formatted to impersonate an automated Craigslist notification, and it informs the target recipient of a supposed policy infraction on their Craigslist posting. The said fake notification further instructs the user to enter a URL into a browser to access a form for more detailed information, threatening to delete their account if they don’t follow. Figure 6. Craigslist campaign email luring targets with an embedded image Attackers crawl Craigslist ad posts to harvest email relay addresses, where they then send custom-crafted messages directly. The email relay receives the sent messages and removes personal data—including the sender’s actual email address, appends original post details to the end of the message, then forwards it through Craigslist infrastructure to mask the original sender. As a result, the ad owner will receive an anonymized email sent from the legitimate craigslist.org domain. The attackers’ abuse of the email relay system allows them to remain anonymous and impersonate Craigslist. It also adds a sense of legitimacy to the messages because it comes from a popular domain that is generally deemed safe by traditional security solutions. Based on our observation, this email campaign replies to job-related ads, which we believe is the attackers’ attempt to target recipients who open such types of messages while connected to a corporate network. However, based on our threat data, users’ success rate accessing the related malicious domains is relatively low. Such a result is likely because the campaign requires the target recipients to perform the additional step of typing a URL. Macro enablement Despite the varying email methods attackers are using to deliver Qakbot, these campaigns have in common their use of malicious macros in Office documents, specifically Excel 4.0 macros. It should be noted that while threats use Excel 4.0 macros as an attempt to evade detection, this feature is now disabled by default and thus requires users to enable it manually for such threats to execute properly. Once the user downloads and opens the malicious Excel file, the text in the document attempts to lure them into enabling the macro. The said text claims that the file is “protected” by a service such as Microsoft or DocuSign, and that the user must enable the macro to view the document’s actual content. Figure 7. XLS file with a DocuSign lure urging targets to enable macros If the user goes ahead and enables the macro, Excel immediately checks if there is a subprocedure predefined in the macro to run automatically once the document opens; in this case, auto_open(). The Visual Basic for Applications (VBA) code written within this subprocedure creates a new macrosheet and then writes Excel 4.0 formulas in several of its cells. Next, it jumps to one cell in this sheet by calling the Application.Run method. In this way, the VBA code starts the Excel 4.0 macro code that was just written to the macrosheet. Figure 8. Example of an Excel 4.0 macro generated by the VBA script. Generating and calling Excel 4.0 macro from VBA is an evasion technique to prevent static analysis tools from decoding the macro. When the user closes the document, the auto_close() function launches to clean up and remove the malicious macrosheet created by the VBA macro. Qakbot delivery Once macros are enabled, the next phase of the attack begins. First, the macro connects to a predefined set of IP addresses or domains to download the malicious files. Some macros are designed to connect to three domains simultaneously, downloading a file of the same name. This is likely done for one of two reasons: first, as a redundancy measure to ensure that the malware is still delivered even if one or two of the domains have been blocked or taken down; and second, to enable the attacker to deliver multiple payloads if desired. Figure 9. Portion of the generated Excel 4.0 macro that shows its attempts to download three payloads from three locations. In most cases, the downloaded file is a Portable Executable (PE) file renamed with either an .htm or .dat file extension, in order to bypass web filtering systems that prevent certain file types. Depending on the specific campaign, the naming of these files varies greatly. For example, a recent campaign using .htm files named them with simple letters and numbers, such as goh[1].htm or j[1].htm. However, a separate campaign that used an invoice theme and used .dat files named them with an extremely long string of numbers, such as 44494.4409064815[1].dat. Again, these differences from campaign to campaign highlight that Qakbot is used simultaneously by different threat actors, which can make concurrent campaigns of the same malware look strikingly different. Once this file is downloaded onto the device, the file is promptly renamed to a different file name with a nonexistent file name extension. Some examples include test.test and good.good (derived from .htm files), or GiCelod.waGic and Celod.wac (derived from .dat files). In many of the incidents involving .htm files, a folder called C:\Datop is created, and the files are saved in that location. Meanwhile, the incidents with .dat files are saved in the C:\Users\AppData\Local\Temp location. Process injection for discovery Whichever file the user ends up with is loaded using regsvr32.exe, which injects into a legitimate process. Both MSRA.exe and Mobsync.exe have been used for this process injection behavior in recent Qakbot-related campaigns. The injected process is then used for a series of discovery commands, including the following: Scheduled tasks The injected process from the previous building block then creates a .dll file with a randomly generated name. This DLL is used to query existing scheduled tasks for a specific ID, and if that scheduled task does not already exist, the DLL creates the task. The scheduled task is to run a predefined task as a means of persistence, as outlined in the following command line: This scheduled task is created with the /F flag, which is used to suppress warnings if the specified task already exists, even though the malware has already queried for a specific scheduled task. Credential and browser data theft Qakbot attempts to steal credentials from multiple locations. First, the injected MSRA.exe or Mobsync.exe process loads the Vault Credential Library file to enumerate credentials. Additionally, this process injects into ping.exe and attempts to read credentials from CredMan using the passport.net\* parameter. Qakbot also targets browser data. The injected process launches the esentutl.exe process. Browser data, including cookies and browser history, are recovered from the web cache using the following commands: These commands specifically look for log files, system files, and database files (/l, /s, and /d). Email exfiltration As mentioned in a previous section, many of the emails delivering Qakbot use the fake-reply technique. To do this, Qakbot is also designed to exfiltrate emails from affected devices. To exfiltrate emails, the injected process launches into the ping.exe process and launches a command to ping localhost: From there, ping.exe is used to copy dozens of email message files and save them in an “Email Storage” folder. These email messages are saved with sequential naming schema, starting with 1.eml and increasing by one for as many email messages as the attacker copies. We have identified instances where the attacker copied out over 100 message files from a single device. Once the copied email files are exfiltrated, the evidence of the action is deleted by removing the “Email Storage” folder using the rmdir command. Additional payloads, lateral movement, and ransomware As is the case with many malware variants today, getting Qakbot onto a device is frequently just the first step in what ends up being a larger attack. Attackers can use the access from Qakbot infections to deliver additional payloads or sell access to other threat actors who can use the purchased access for their objectives. In many cases, attackers will expand the scope of their attack by using credentials obtained in earlier stages of the attack to move laterally throughout the network. In several instances, attackers would move laterally using Windows Management Instrumentation (WMI) and drop a malicious DLL on the newly accessed device. From there, the attacker will run the same series of discovery commands as they did on the initial access device and will conduct further credential theft. In other instances, other malicious files are dropped in conjunction with the malicious DLL. For example, several BAT files that were specifically designed to turn off security tools on the affected device were dropped before dropping the malicious DLL. These slight differences in the attack chain are evidence of multiple actors using Qakbot for lateral movement. In addition to lateral movement, attackers frequently drop additional payloads on affected devices, especially Cobalt Strike. Qakbot has a Cobalt Strike module, and actors who purchase access to machines with prior Qakbot infections may also drop their own Cobalt Strike beacons and additional payloads. Using Cobalt Strike lets attackers have full hands-on-keyboard access to the affected devices, enabling them to perform additional discovery, find high-value targets on the network, move laterally, and drop additional payloads, especially human-operated ransomware variants such as Conti and Egregor. Resurging and evolving threats require coordinated threat defense Qakbot’s continued prevalence in the threat landscape demands comprehensive protection capable of detecting and stopping this malware, its components, and other similar threats at every stage of the attack chain: email delivery, network activity, endpoint behavior, and follow-on attacker activities. Microsoft 365 Defender provides coordinated defense using multiple layers of dynamic protection technologies—including machine learning-based protection—and correlating threat data from email, endpoints, identities, and cloud apps. It is also backed by a global network of threat experts who continuously monitor the threat landscape for new, resurging, and evolving attacker tools and techniques. Microsoft Defender for Office 365 detects and blocks emails that attempt to deliver Qakbot. Safe Links and Safe Attachments provide real-time protection by leveraging a built-in sandbox that examines and detonates links and attachments in messages before they get delivered to target recipients. However, for those messages without such artifacts, Microsoft Defender SmartScreen in Microsoft Edge and other web browsers that support it blocks the malicious websites and prevents downloading the malicious Excel file on devices. On endpoints, attack surface reduction rules detect and block common attack techniques used by Qakbot and subsequent threats that may result from its activities. Endpoint detection and response (EDR) capabilities detect malicious files, malicious behavior, and other related events before and after execution. Network protection also blocks subsequent attempts by Qakbot to connect to malicious domains and IP addresses, and Advanced hunting lets defenders create custom detections to proactively find this malware and other related threats. Defenders can also do the following mitigation steps to reduce the impact of Qakbot in their organizations: Check your Office 365 email filtering settings to ensure you block spoofed emails, spam, and emails with malware. Use Office 365 security for enhanced phishing protection and coverage against new threats and polymorphic variants. Configure Office 365 to recheck links on click. Enable Zero-hour auto purge (ZAP) in Exchange Online, which is an email protection capability that retroactively detects and neutralizes malicious messages that have already been delivered in response to newly acquired threat intelligence. Encourage users to use Microsoft Edge and other web browsers that support SmartScreen, which identifies and blocks malicious websites, including phishing sites, scam sites, and sites that contain exploits and host malware. Enable network protection to prevent applications or users from accessing malicious domains and other malicious content on the internet. Stop malicious XLM or VBA macros by ensuring runtime macro scanning by Windows Antimalware Scan Interface (AMSI) is on. This feature—enabled by default—is on if the Group Policy setting for Macro Run Time Scan Scope is set to Enable for All Files or Enable for Low Trust Files. Turn on cloud-delivered protection in Microsoft Defender Antivirus or the equivalent for your antivirus product to cover rapidly evolving attacker tools and techniques. Cloud-based machine learning protections block a huge majority of new and unknown variants. Turn on tamper protection features to prevent attackers from stopping security services. Run EDR in block mode so that Microsoft Defender for Endpoint can block malicious artifacts, even when your non-Microsoft antivirus doesn’t detect the threat or when Microsoft Defender Antivirus is running in passive mode. EDR in block mode works behind the scenes to remediate malicious artifacts that are detected post-breach. Enable investigation and remediation in full automated mode to allow Microsoft Defender for Endpoint to take immediate action on alerts to resolve breaches, significantly reducing alert volume. Use device discovery to increase your visibility into your network by finding unmanaged devices on your network and onboarding them to Microsoft Defender for Endpoint. Use multi-factor authentication (MFA) to mitigate credential theft and prevent attacker access. Keep MFA always-on for privileged accounts and apply risk-based MFA for normal accounts. Consider transitioning to a passwordless primary authentication method, such as Azure MFA, certificates, or Windows Hello for Business. Run realistic, yet safe, simulated phishing and password attack campaigns in your organization using Attack Simulator for Microsoft Defender for Office 365. Run spear-phishing (credential harvest) simulations to train end users against clicking URLs in unsolicited messages and disclosing their credentials. Educate end users about identifying lures in spear-phishing emails and watering hole attacks, protecting personal and business information in social media, and filtering unsolicited communication. Encourage users to report reconnaissance attempts and other suspicious activity. Learn how you can stop attacks through automated, cross-domain security with Microsoft 365 Defender. Microsoft 365 Defender Threat Intelligence Team Appendix Microsoft researchers published the following threat analytics reports, which are available to Microsoft 365 Defender customers through the Microsoft 365 security center: Malware profile: Qakbot provides additional information about Qakbot’s building blocks discussed in this blog post, including references to previously monitored campaigns and detailed mitigation steps Threat Insights: Qakbot abuses Craigslist email relay provides more technical details about the Craigslist email abuse campaign that was recently seen delivering Qakbot These reports serve as a good starting point for organizations to understand these active attacks, determine if they are affected, and investigate related incidents and alerts. The reports provide and consolidate real-time data aggregated from across Microsoft 365 Defender, indicating the all-up impact of the threat to the organization. The following sections provide the specific Microsoft 365 Defender detections that can help surface Qakbot and related threats. Antivirus Microsoft Defender Antivirus detects Qakbot installers as the following malware: Qakbot downloader TrojanDownloader:O97M/Qakbot Qakbot implant Trojan:Win32/QBot Trojan:Win32/Qakbot TrojanSpy:Win32/Qakbot Qakbot behavior Behavior:Win32/Qakbot.A Additional detections based on activity group behavior Due to Qakbot’s high likelihood of transitioning to human-operated attack behaviors including data exfiltration, lateral movement, and ransomware by multiple actors, the detections seen after infection can vary widely. During the activity described in this report, at least one major activity group was provided Qakbot access after initial infection, but other groups have been known to purchase access so any initial infection indicated by advanced hunting queries, behavior, or Qakbot infection should be fully investigated. Behavior:Win32/Mikatz.gen!B Behavior:Win32/MimikatzTrigger Behavior:Win32/TurtleLoader.A!dha Behavior:Win32/CobaltStrike.A!nri Behavior:Win32/UACBypassExp.A!mmc Endpoint detection and response (EDR) Alerts with the following titles in the security center can indicate threat activity on your network related directly to the material in this report covering Qakbot initial infection and future human operated or ransomware activity: Qakbot malware Qakbot credential stealer Qakbot download URL Qakbot network infrastructure Email security Microsoft Defender for Office 365 offers enhanced solutions for blocking and identifying malicious emails. In the email entity page, administrators can get enhanced information on emails in a unified view. Administrators can view known campaigns impacting inboxes and investigate malicious emails by drilling down to view all attachments or URL detonation details from dynamic analysis. The following dynamic detonation signature may indicate threat activity associated with Qakbot. By utilizing email Campaigns view, you can filter based on campaign subtype for the following signals. These signals, however, can be triggered by unrelated threat activity: Downloader_Macro_Donoff_ZGA Advanced hunting The following Advanced Hunting Queries are accurate as of this writing. For the most up-to-date queries, visit aka.ms/QakbotAHQ. To locate possible exploitation activity, run the following queries in Microsoft 365 Defender. Craigslist impersonation domains lead to XLS download Use this query to locate devices connecting to malicious domains registered to impersonate Craigslist.org. These domains act as redirectors which direct the target to a malicious XLS download. DeviceNetworkEvents | where RemoteUrl matches regex @"abuse\.[a-zA-Z]\d{2}-craigslist\.org" Qakbot-favored process execution after anomalous Excel spawning Use this query to find Excel launching anomalous processes congruent with Qakbot payloads which contain additional markers from recent Qakbot executions. The presence of such anomalous processes indicate that the payload was delivered and executed, though reconnaissance and successful implantation hasn’t been completed yet. DeviceProcessEvents | where InitiatingProcessParentFileName has "excel.exe" or InitiatingProcessFileName =~ "excel.exe" | where InitiatingProcessFileName in~ ("excel.exe","regsvr32.exe") | where FileName in~ ("regsvr32.exe", "rundll32.exe") | where ProcessCommandLine has @"..\" Qakbot reconnaissance activities Use this query to find reconnaissance and beaconing activities after code injection occurs. Reconnaissance commands are consistent with the current version of Qakbot and occur automatically to exfiltrate system information. This data, once exfiltrated, will be used to prioritize human operated actions. DeviceProcessEvents | where InitiatingProcessFileName == InitiatingProcessCommandLine | where ProcessCommandLine has_any ( "whoami /all","cmd /c set","arp -a","ipconfig /all","net view /all","nslookup -querytype=ALL -timeout=10", "net share","route print","netstat -nao","net localgroup") | summarize dcount(FileName), make_set(ProcessCommandLine) by DeviceId,bin(Timestamp, 1d), InitiatingProcessFileName, InitiatingProcessCommandLine | where dcount_FileName >= 8 Qakbot email stealing by ping.exe Use this query to find email stealing activities ran by Qakbot that will use “ping.exe -t 127.0.0.1” to obfuscate subsequent actions. Email theft that occurs might be exfiltrated to operators and indicates that the malware completed a large portion of its automated activity without interruption. DeviceFileEvents | where InitiatingProcessFileName =~ 'ping.exe' | where FileName endswith '.eml' General attempts to access local email store Use this query to find attempts to access files in the local path containing Outlook emails. DeviceFileEvents | where FolderPath hasprefix "EmailStorage" | where FolderPath has "Outlook" | project FileName, FolderPath, InitiatingProcessFileName, InitiatingProcessCommandLine, DeviceId, Timestamp Email collection for exfiltration Use this query to find attempts to copy and store emails for later exfiltration. DeviceFileEvents | where InitiatingProcessFileName =~ 'ping.exe' and InitiatingProcessCommandLine == 'ping.exe -t 127.0.0.1' and InitiatingProcessParentFileName in~('msra.exe', 'mobsync.exe') and FolderPath endswith ".eml" The post A closer look at Qakbot’s latest building blocks (and how to knock them down) appeared first on Microsoft Security Blog. Continue reading...
-
It seems to be. I have it running with 2 cores and 4GIGS ram. Runs like a champ.
-
I've had installed in a VM since the first beta release. It runs very well in the VM. Better than Windows 10 ever did.
-
Windows 11 was released for the general public starting October 5, 2021. The rollout through Windows update has started to the eligible devices and continue until 2022. Windows 11: A new era for the PC begins today | Windows Experience Blog Introducing Windows 11 | Windows Experience Blog What’s coming in Windows 11 Accessibility | Windows Experience Blog DOWNLOAD PC HEALTH CHECK APP (aka.ms) Windows 11 available on October 5 | Windows Experience Blog Download Windows 11 (microsoft.com) Windows 11 known issues and notifications | Microsoft Docs Resources for Windows 11 on Microsoft Community: The following Forum Articles from our Article Authors at Microsoft Community would help to get started with Windows 11, including upgrading manually and a deeper dive at the new features incoming with Windows 11: List of Changed or removed features/functionalities in Windows 11 Frequently Asked Questions: Windows 11 - Microsoft Community Windows 11 Keyboard Shortcuts - Microsoft Community How to Upgrade from Windows 10 to Windows 11 Upgrade from Windows 10 to Windows 11 using ISO file Troubleshoot Windows 11 upgrade and Installation errors How to Reset Windows 11 How to make clean install of Windows 11 Convert an existing Windows 10 Installation from Legacy BIOS to UEFI (microsoft.com) How to: Complete the Windows 11 Out of Box Experience Downgrade from Windows 11 to Windows 10 Forum articles on Features in Windows 11: The Forum Articles on Features in Windows 11 are as under: How to login automatically to Windows 11 How to: Use Snap Layouts and Snap groups in Windows 11 Widgets in Windows 11 How to Perform a Backup Using File History in Windows 11 or Windows 10 How to create a Local account in Windows 11 Get Started with Chat for Microsoft Teams in Windows 11 - Preview How to try out the new Office 365 Experience on Windows 11 How to Create a System Image in Windows 11 - 2021 Edition How to Connect or Pair Wireless and Bluetooth Devices in Windows 11 Add Clock to the second Display in Windows 11 - Microsoft Community Support Documents from Microsoft Support: Ways to install Windows 11 Installing Windows 11 on devices that don't meet minimum system requirements Pin apps and folders to the desktop or taskbar (microsoft.com) How to use the taskbar in Windows 11 (microsoft.com) Customize the taskbar notification area (microsoft.com) How to open notification center and quick settings (microsoft.com) You can always start a new post for any questions or assistance regarding Windows 11.
-
I was a little slow getting this one added. Better late than never I say. In any case I have added a new forum for Windows 11 help and discussions. Visit the new Windows 11 forum.