-
Posts
27,568 -
Joined
-
Last visited
-
Days Won
73
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by AWS
-
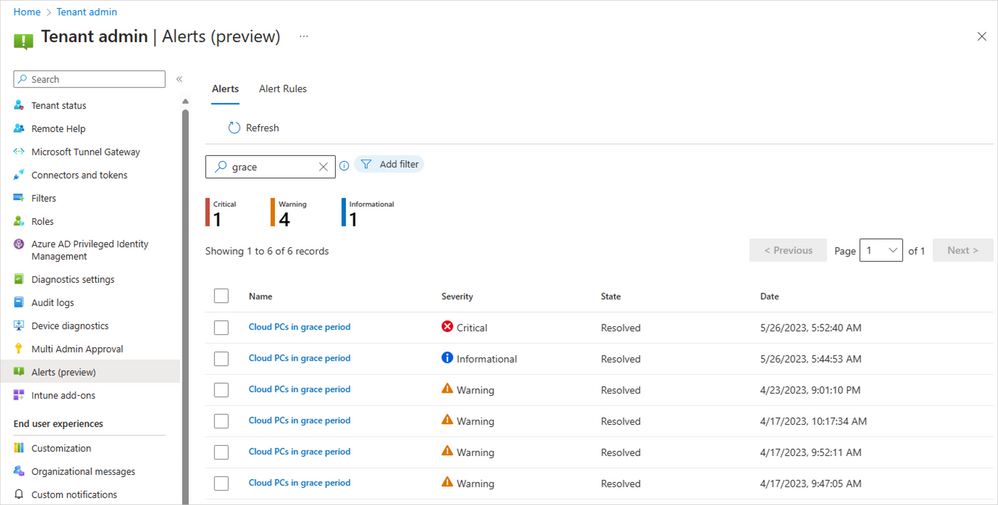
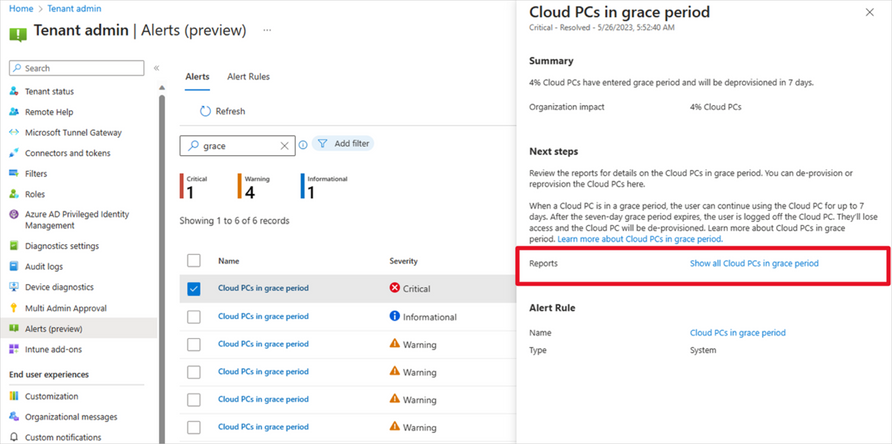
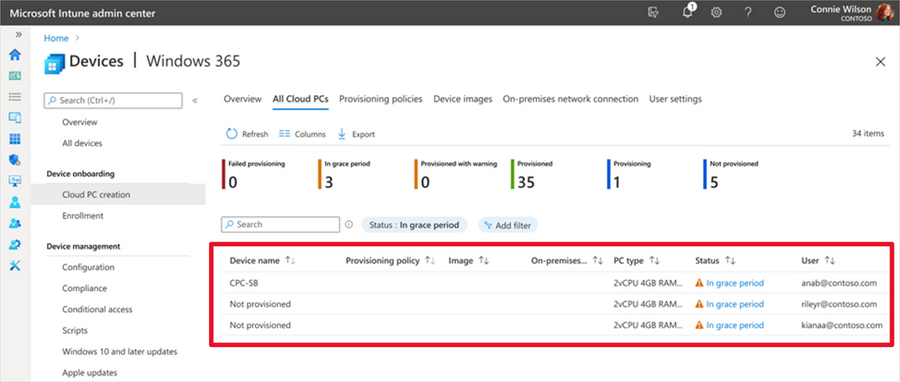
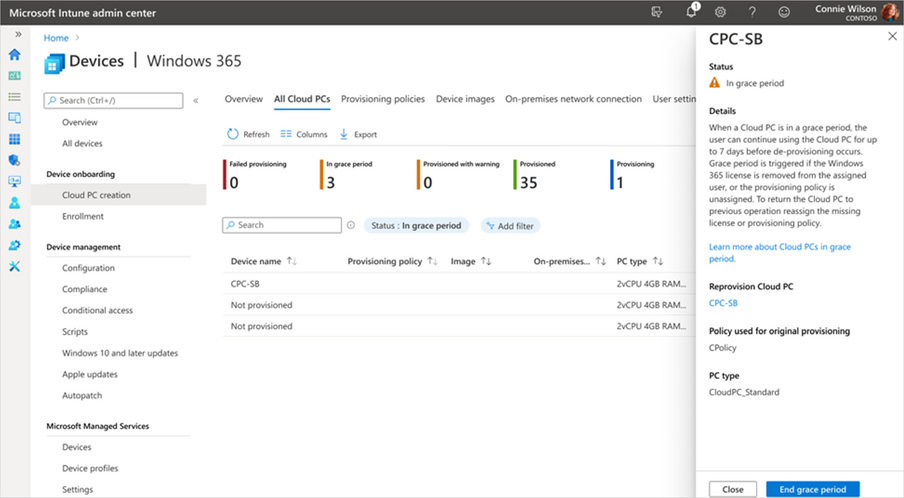
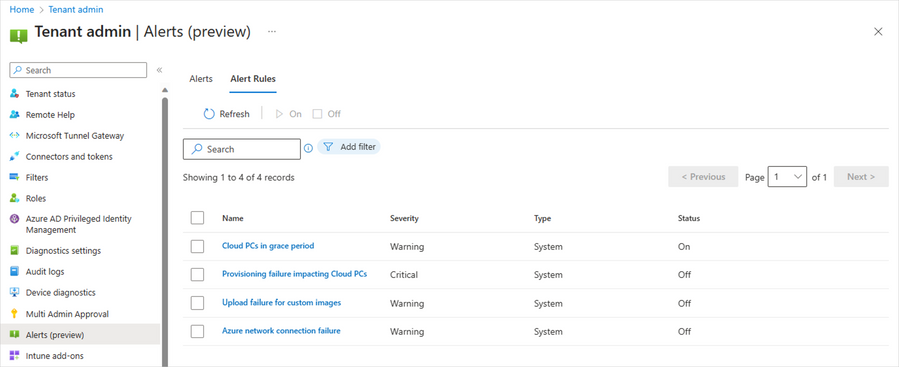
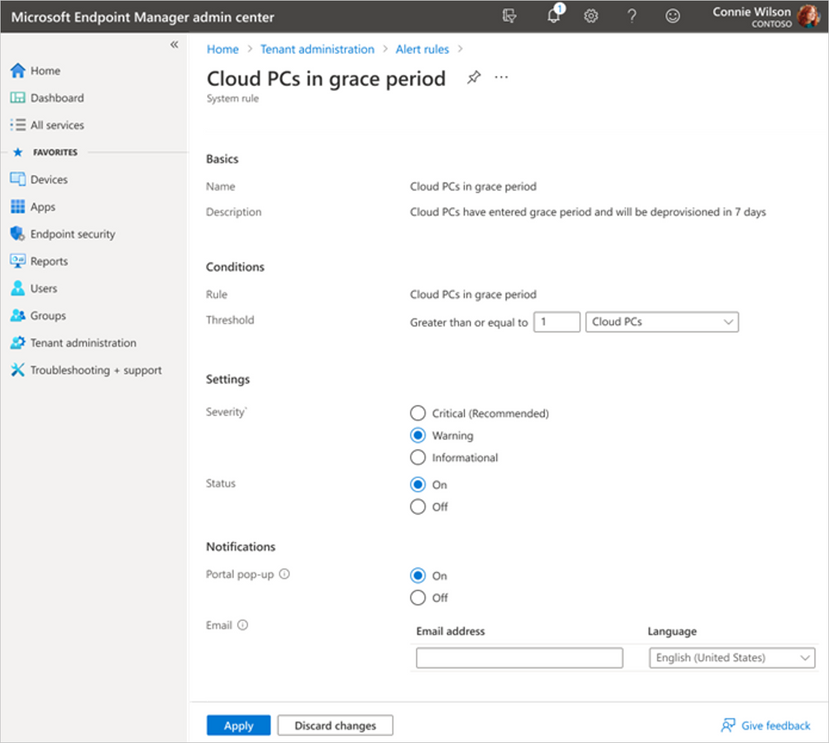
We are excited to announce the public preview of new alerts for IT admins managing Cloud PCs in Intune to better inform them about Cloud PCs in a grace period. This capability is available for Windows 365 Enterprise customers today! We heard you. You want to receive proactive alerts on Cloud PCs so you can easily take appropriate actions based on this information. This can help reduce risk in situations where an IT admin may not be fully aware of Windows 365 provisioning controls and, therefore, make changes to user licensing or group membership that inadvertently trigger the grace period. Then you need this capability to extend to automated scripts, ensuring comprehensive coverage and proactive notification. With this Windows 365 IT admin alerts, an email is delivered whenever a Cloud PC enters the grace period state. This provides admins with greater awareness of their environment so they can take appropriate actions and acts as a preventive measure against unintended Cloud PC deprovisioning. Windows 365 IT admin alerts offer the following features: Admins can establish and customize system-based alerts for Cloud PCs in the grace period based on their preferences. IT admins can define alert rules by selecting from the available options, setting thresholds, specifying frequency, and choosing notification channels for receiving alerts. IT admins are able to assess their environment and take informed decisions to either reprovision or end the grace period for specific Cloud PCs as needed. Enabling the functionality to generate alerts when a Cloud PC enters the grace period is a critical, precautionary measure. It acts as a safety net in scenarios such as Cloud PC license expiration or inadvertent changes made by IT admins to groups, resulting in a Cloud PC being set to deprovision within seven days. Why is this important? Windows 365 Enterprise users are granted a seven-day grace period to continue using a Cloud PC once it enters that state. After the grace period elapses, the user is logged off, loses access to the Cloud PC, and the Cloud PC undergoes deprovisioning. Deprovisioning is a significant and irreversible action. By proactively notifying IT admins, unnecessary deprovisioning of Cloud PCs can be mitigated. The Alerts (preview) in Microsoft Intune In the Microsoft Intune admin center, under Tenant admin, you can review the alert history and monitor the status of a Cloud PC alert event, including details such as severity, state, and date. Screenshot of Tenant admin in Alerts (preview) menu Easy-to-understand alert insights The event summary page provides a more detailed overview of the specific alert event that needs attention. This enables you to promptly investigate issues related to Cloud PCs in the grace period and gain a comprehensive understanding of the impact. Screenshot of Alerts (preview) menu with a red highlight on the reports “Show all Cloud PCs in grace period” When you select Show all Cloud PCs in grace, you are redirected to the corresponding alert event page, as displayed below. This page offers additional information about the alert event, enabling you to take appropriate actions to resolve the issue. Screenshot of All Cloud PCs tab under the Windows 365 menu with a red highlight over the status of devices in grace period If you select In grace period for a particular Cloud PC, a fly-out will appear, providing details about the impact of Cloud PCs in the grace period. You can then choose to either Reprovision Cloud PC or End the grace period. Screenshot of CPC-SB pop up menu showing the option to “reprovision Cloud PC” or “end grace period” Managing alert rules and email notifications With this new capability, you have the flexibility to customize and enable or disable the alert rules, including conditions, settings, and notifications, depending on their specific requirement. Additionally, you have the flexibility to configure your preferred notification methods for events by choosing options such as portal pop-up and email. We also provide support for email localization, allowing you to customize the language in which you prefer to receive alert notifications. Screenshot of Alerts (preview) under the Alert Rules tab showing the optional notification methods Screenshot of the Cloud PCs in grace period menu under the Alert rules tab showing more details on notification options Prerequisites and what's next Windows 365 system-based alerts are currently available for Windows 365 Enterprise customers and only with Microsoft Intune. The account needs to have the Intune Global Admin, Intune Admin, or Windows 365 Admin roles assigned. Enhanced IT admin alerts for Cloud PCs that are unable to connect are coming soon. You'll also soon have the ability to proactively notify IT admins when Cloud PCs encounter issues such as unhealthy hosts, persistent connection errors, suspected infrastructure problems, or other systemic issues. These new capabilities will also provide valuable insights to assist in resolving the problem promptly. For a demo on this new alerts capability for Cloud PCs in a grace period, now in public preview, please check out this video: Learn more Looking to see what the latest capabilities in Windows 365 alerts look like up close? See our documentation on Alerts in Windows 365. Finally, have feedback or suggestions? Visit this forum to share your ideas and help shape the future of Windows 365! Continue the conversation. Find best practices. Bookmark the Windows Tech Community and follow us @MSWindowsITPro on Twitter. Looking for support? Visit Windows on Microsoft Q&A. Continue reading...
-
Windows client roadmap updates help guide organizations with their planning processes. In our last Windows client roadmap update blog, we announced that Windows 10, version 22H2 would be the final version of Windows 10. It will reach end of support on October 14, 2025 for all editions of that version. We also announced that there would be a Windows 11-based Long- Term Servicing Channel (LTSC) release in the second half of 2024. Here's additional information on the lifecycle updates for specific versions of Windows 10 and Windows 11. Windows 11, version 23H2 will be available as an enablement package The upcoming Windows 11, version 23H2 shares the same servicing branch and code base as Windows 11, version 22H2. What does it mean for you? If you're running Windows 11, version 22H2, it will be a simple update to version 23H2 via a small enablement package (eKB). Do you remember updating from Windows 10, version 1903 to 1909? Or how you've managed recent updates beginning with Windows 10, version 20H2 through 22H2? It will be that simple. Moreover, since both versions share the same source code, you don't need to worry about application or device compatibility between the versions. Check out our whitepaper Windows and the shared servicing model for definitions and examples of how this works! Recommendation Don't wait for Windows 11, version 23H2. Continue (or begin) your Windows 11 rollout with version 22H2 now. Upon release in the fourth quarter of 2023, simply deploy the 23H2 enablement package via one of the following: Windows Server Update Services Windows Update for Business Windows Autopatch Stay current and reset the product lifecycle for your edition! Extend it by another three years for Enterprise, Education, and IoT Enterprise editions or by two years for the Pro edition. Note: The eKB is not available on Volume Licensing Service Center. Media packages contain the complete Windows 11 operating system. Windows 10 IoT Enterprise LTSC 2021 available through Volume Licensing Traditionally, Windows 10 IoT Enterprise LTSC has only been available through direct licensing from original equipment manufacturers (OEMs) that sell IoT devices. In response to your feedback, we're pleased to be able to make the licensing more flexible. We'll be offering Windows 10 IoT Enterprise LTSC 2021 through Volume Licensing starting August 1st. Consider this solution if your organization meets the following criteria: Requires the longer 10-year lifecycle of Windows 10 for devices specifically used in IoT scenarios. Doesn't purchase special devices that include the IoT LTSC license through OEMs. Recommendation If your organization meets the above criteria and has IoT use cases NOT related to knowledge worker scenarios, purchase the Windows 10 IoT Enterprise LTSC 2021 edition directly from Microsoft through Volume Licensing starting August. Windows IoT Enterprise is specifically designed for fixed function, industrial use scenarios in manufacturing, healthcare, retail, and more. Note: The Windows 10 Enterprise LTSC 2021 edition will continue to be supported for five years and is available as a standalone license in Volume Licensing or as part of the Windows E3/E5 subscription. If you're waiting for a Windows 11 LTSC release, you can begin planning and testing your applications and hardware on the current General Availability (GA) Channel release, Windows 11, version 22H2. Check out App confidence: Optimize app validation with Test Base for more tips on how to test your applications. Stay informed In the future, we'll add more information here and to the Windows release health page, which offers information about the GA Channel and LTSC under release information for appropriate versions. Continue the conversation. Find best practices. Bookmark the Windows Tech Community and follow us @MSWindowsITPro on Twitter. Looking for support? Visit Windows on Microsoft Q&A. Continue reading...
-
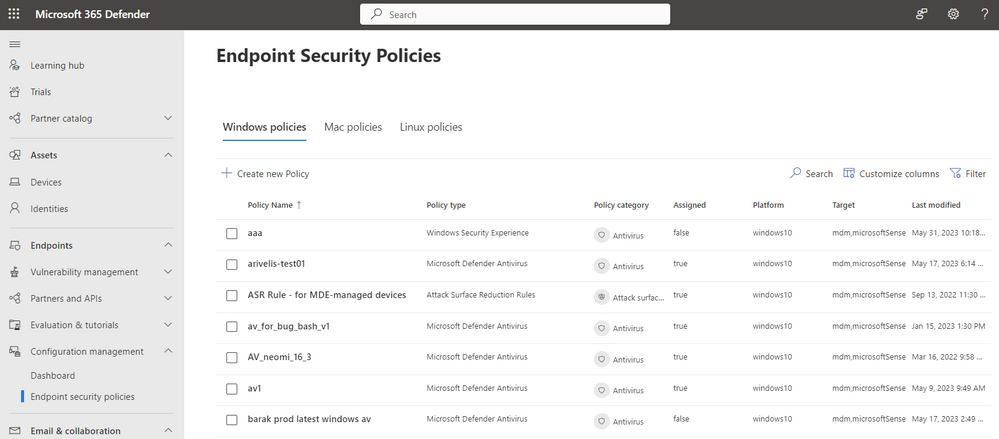
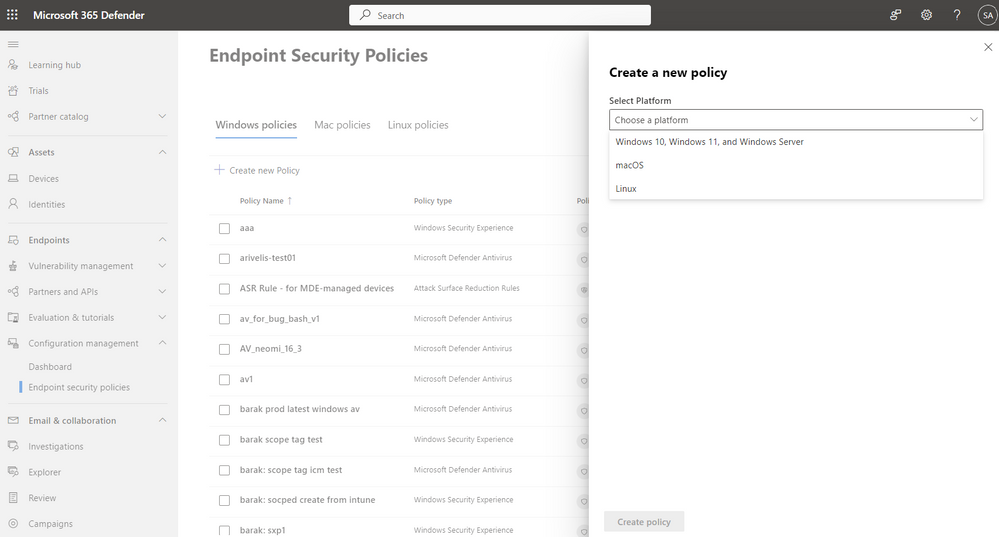
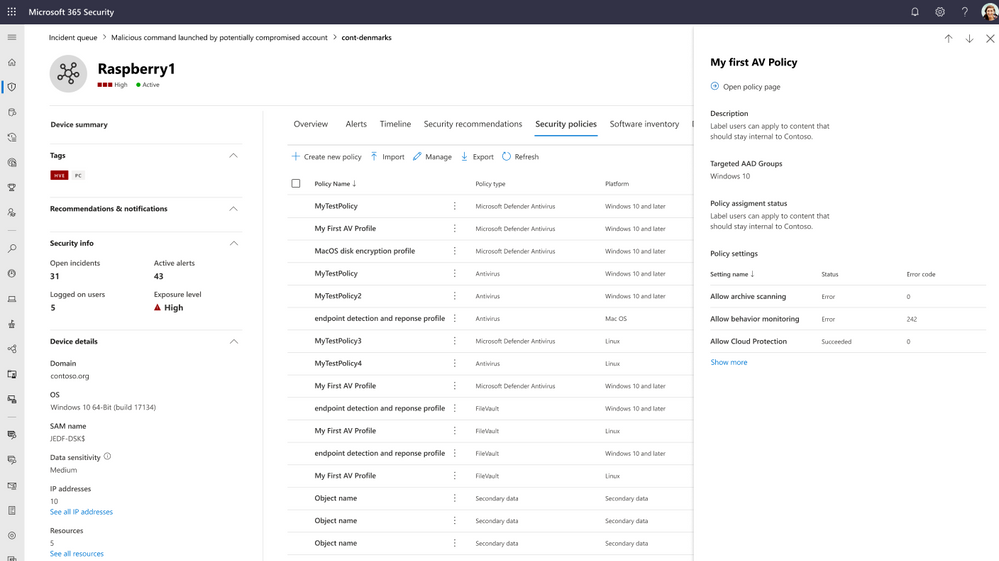
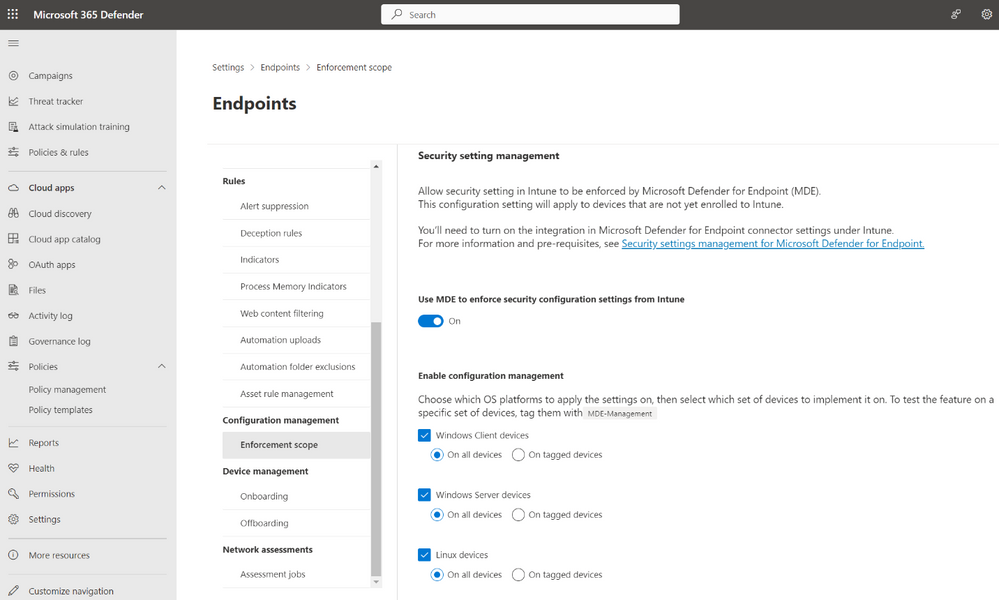
As advanced threats such as ransomware continue to increase in velocity, and sophistication, organizations are evolving their endpoint security strategies away from point solutions to a more holistic security approach focused on vendor consolidation. At the same time, we continue to see a gap between security and IT teams to achieve a seamless and effective operating model for effective endpoint security. While many endpoint security solutions now provide some level of endpoint management experience that include capabilities such as device inventory and policy authoring, they are often disconnected from the tools IT teams use to do many of the same things. This combination leads to a lack of visibility and coordination among these two groups, leaving too much room for security gaps to grow. Microsoft believes organizations can protect their endpoints more effectively by bringing their security and IT teams closer together. Today we are excited to announce the public preview of a unified security settings management experience that offers a consistent, single source of truth for managing endpoint security settings across Windows, macOS, and Linux. It is built into the Microsoft 365 Defender portal, and therefore easily accessible for security teams, but built on the powerful capabilities of Microsoft Intune. Starting today, customers will benefit from a host of new capabilities: Native security settings management capabilities in Defender for Endpoint that support Windows, macOS, and Linux Existing endpoint security policies are automatically ingested in the Microsoft 365 Defender portal Create and edit AV policies directly from the Microsoft 365 Defender portal Policies are automatically synced with Microsoft Intune to ensure coordination between IT and Security teams for organizations who use Intune as a full management suite. A new list on the device page, that shows all security policies and their settings Simplified device onboarding: Removal of Azure Active Directory hybrid join as a management prerequisite Cross-platform support Security administrators can now use the security settings management capabilities in Defender for Endpoint to manage their security configuration settings across Windows, macOS and Linux devices without the need for separate management tools, or updates to IT resources. Managing security policies in the Microsoft 365 Defender portal Up until today, security administrators were required to use additional tools to manage their endpoint security settings, which can slow down response. The new integration of Microsoft Intune’s endpoint security experience into the Microsoft Defender for Endpoint bridges this gap to help organizations better protect themselves by operating from a single portal. While Microsoft Intune is not a requirement, the seamless sync offers additional benefits for organizations using both products. All data is shared, always in sync and therefore ensures that IT and security teams share single source of truth for both IT administrators using Microsoft Intune and Security administrators – thanks to this integration, both administrators will see the same data between their portals, preventing confusion, misconfigurations and potential security gaps. Simplified device onboarding For organizations that wanted to use security settings management capabilities in the past, Defender for Endpoint required all devices to fully register with Azure AD. This required fixing of pre-existing misconfigurations that prevented devices from successfully joining their identity inventory. Starting today, devices no longer need to be joined to the organizations Azure AD and can instantly be managed with Defender for Endpoint. This significantly simplifies the onboarding process and security settings can be deployed to all in-scope devices immediately. Let’s take a look at the new, integrated experience. Manage your security policies View all your Intune security policies directly in the Microsoft 365 Defender portal by going to Configuration Management > Endpoint Security Policies. You can filter the list as well as search for specific policies using the built-in ‘filter’ and ‘search’ capabilities. Image 1: Security policy interface in the Microsoft 365 Defender portal AV policies for Windows, Linux and MacOS can be created from the portal. Image 2: Create a new policy The device page includes a list of received policies, as well as their respective settings and status: Image 3: New device page With this update we want to make sure that the transition is seamless for all existing customers. Here is how the transition will work: All Windows devices that previously used this management feature, will seamlessly transition to use the new, lightweight mechanism. Devices that were previously managed by Defender for Endpoint but had enrollment errors will now seamlessly be enrolled. Devices that are already fully registered with Azure AD and are receiving policies, will remain registered to Azure AD and continue to receive policies. Get started today! While this change doesn’t require any immediate administrative action, you can take the following actions to prepare for this upgrade: Step 1: Turn on preview features Make sure you have preview features enabled in order to use Native Security Settings Management for Microsoft Defender for Endpoint In the Microsoft 365 Defender portal navigation pane, select Settings > Endpoints > Advanced features > Preview features. Toggle the setting On and select Save preferences. Step 2: Review how Settings Management for Microsoft Defender for Endpoint is configured We recommend navigating to the Microsoft 365 Defender portal and reviewing which devices you intend to manage using by Defender for Endpoint at Settings > Endpoints > Configuration management > Enforcement scope. Make sure the feature is turned on, and that for each Operating System, your management preferences have been configured accurately. Advanced configuration options which were available until today remain effective and are outlined in our main documentation. Image 4: Security settings management configuration Step 3: Create a dynamic AAD group to automatically target devices with policies To ensure that all endpoints enrolled with security settings management capabilities for Defender for Endpoint receive policies, we recommend creating a dynamic Azure AD group based on the devices’ OS Type. Note that you can now also dynamically group servers in Azure AD. By targeting security policies to these dynamic Azure AD groups, all devices managed by Defender for Endpoint will automatically be protected - without requiring admins to perform any additional tasks like creating a new policy or fine tuning existing ones. Important : If until today you’ve been creating dynamic Azure AD groups based on the “MDEManaged” or "MDEJoined" system labels, these are currently not supported for new devices that enroll using Defender for Endpoint settings management. If you still intend to dynamically group devices in Azure AD based on this criterion, we recommend using the “Management Type = microsoftSense” attribute instead. More information: Get started now by checking out our documentation Continue reading...
-
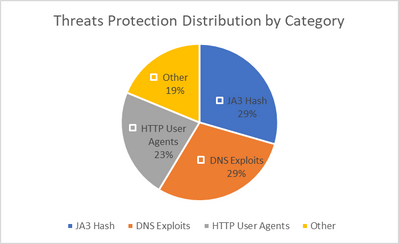
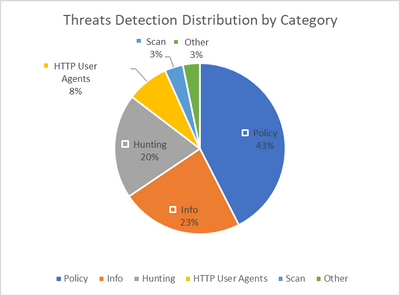
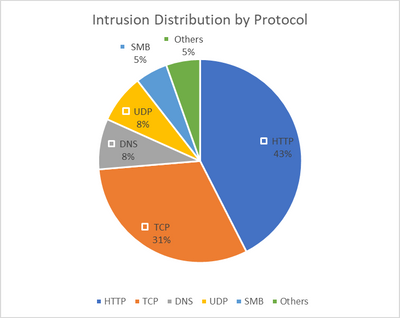
In this blog post, I will discuss the various threat protection capabilities that customers are leveraging to safeguard their workload deployments in Azure using Azure Firewall. Azure Firewall is a cloud-native firewall-as-a-service solution that empowers customers to centrally govern and log all their traffic flows using a DevOps approach. This service offers both application and network-level filtering rules, and it seamlessly integrates with the Microsoft Threat Intelligence feed to filter known malicious IP addresses and domains. Moreover, Azure Firewall boasts high availability and comes equipped with built-in auto scaling. While it may appear straightforward, the first line of defense can be effectively achieved through access restriction. Customers are adopting two simple approaches to bolster their security posture: Egress Traffic Blocking: This method involves blocking all egress traffic to the internet and only allowing access to specific domains that are deemed safe and necessary. Suspicious Site Blocking: Alternatively, customers can choose to allow all egress traffic to the internet while implementing measures to block access to suspicious sites. This approach mitigates potential risks associated with accessing untrustworthy destinations. URL (Uniform Resource Locator) and FQDN (Fully Qualified Domain Name) filtering play a crucial role in analyzing web traffic and deciding whether to allow or block access based on the URLs accessed by applications. This control mechanism is critical for safeguarding cloud workloads and data from malicious activities such as command-and-control connections and data exfiltration. Notably, URL filtering is particularly essential for cloud deployments, especially when protecting Virtual Desktop Infrastructure (VDI) environments. It's important to differentiate URL filtering from domain or FQDN filtering. FQDN filtering primarily focuses on the destination domain, while URL filtering takes into account the complete URL. Let's consider an example to illustrate this distinction. Suppose we examine the domain linkedIn.com. In this case, filtering based solely on FQDN would not suffice because distinguishing between different URLs within the domain (e.g., linkedIn.com/LegitUser vs. LinkedIn.com/MaliciousUser) becomes a critical detail when implementing a secure egress strategy. Consequently, filtering based on the URL becomes necessary. URL filtering also plays a crucial role in preventing attackers from establishing connections to their command-and-control (C2) servers or exfiltrating data to sites under their control. Moreover, organizations often need to adhere to security compliance standards and guidelines, such as PCI DSS and SOC2 Type2, which require the implementation of URL filtering as an essential security measure. TLS decryption is a prerequisite for implementing URL filtering since the URL is part of TLS-encrypted HTTPS traffic. And since the percentage of the encrypted web traffic is in constant incline, it is a mandatory requirement to enable TLS inspection in your Azure Firewall deployment. The need for Threat Intelligence Now that we understand the significance of URL filtering and the need for TLS inspection to implement it on encrypted traffic, how can we distinguish between safe and suspicious domains and URLs? Threat intelligence is our second ring of defense. It refers to the information an organization utilizes to comprehend the threats that have targeted, are targeting, or will target the organization. This valuable information aids in preparation, prevention, and identification of cyber threats aiming to exploit valuable resources. Azure Firewall leverages threat intelligence from the Microsoft Threat Intelligence feed, which encompasses multiple sources, including the Microsoft Cyber Security team. By enabling threat intelligence-based filtering on your firewall, you can receive alerts and block traffic associated with known malicious IP addresses and fully qualified domain names (FQDNs). With recent enhancements, Azure Firewall Threat Intelligence offers even more fine-grained filtering capabilities, including identification of malicious URLs within specific domains. Consequently, while customers may have access to a certain domain, any specific URL within that domain identified as malicious will be denied by Azure Firewall. To achieve optimal granularity, customers have the option to utilize a Threat Intelligence allow list, which allows trusted FQDNs, IP addresses, ranges, and subnets to bypass threat intelligence validation. In the case of HTTPS traffic, where URLs are encrypted, Azure Firewall Premium's TLS inspection comes into play. This feature enables URL-based threat intelligence analysis for encrypted traffic, ensuring comprehensive protection. Over the past year, we observed a consistent upward trend in the number of web requests being blocked as a result of Threat Intelligence filtering. On an average daily basis, we are witnessing over 20 million blocked requests to suspicious sites. Security Risks in Azure Cloud Workloads Unlike Threat Intel and URL/FQDN filtering which are mainly egress oriented, a third ring of defense that Azure Firewall offers is intrusion detection and prevention system (IDPS) which protect against both ingress and egress threats. IDPS is a security technology designed to detect and prevent unauthorized activities and potential threats within a computer network or system. An IDPS is typically comprised of two main components: Intrusion Detection System (IDS): This component monitors network traffic, system logs, and other sources of information to identify potential security breaches or malicious activities. It analyzes network packets, system events, and behavior patterns to detect signs of intrusion or suspicious behavior. Intrusion Prevention System (IPS): This component goes a step further than IDS by actively taking measures to prevent identified threats. It can automatically block or mitigate malicious network traffic or activities to protect the network or system from attacks. The main functions of IDPS include: Monitoring and Detection: The IDPS constantly scans network traffic, searching for known attack patterns or abnormal behavior that could indicate an intrusion or security breach. Alerting and Reporting: When the IDPS detects a potential threat, it generates alerts or notifications to notify security personnel. It provides detailed information about the detected event, including the type of attack and severity level. Response and Prevention: An IDPS takes action to mitigate or prevent attacks by blocking network traffic. Logging and Analysis: The system maintains logs and records of security events, which can be used for post-incident analysis, forensic investigations, and compliance requirements. Azure Firewall IDPS plays a crucial role in enhancing the security posture of networks and systems by detecting and preventing unauthorized activities, reducing the risk of data breaches, and helping organizations respond effectively to security incidents. In the last year, we noticed a notable surge in network and application layer attacks. Using Azure Firewall's IDPS, we were able to handle an average of over 5 million daily threat attempts. Over the past twelve months, the three main threats we've been preventing are malicious SSL certificates that use JA3 hashes, vulnerabilities in the Domain Name System (including DNS tunneling), and specific user agents associated with known malicious activity on the web. When customizing their firewall, customers can specify which threats should be mitigated and which only require detection and alerting. We've observed that alerted threats are distributed in different way, and that most such threats are caused by policy violations within an organization, as well as information events at the audit level that can be useful for identifying interesting activity. Although network layer attacks represent a significant portion of the pie chart, the majority of threats occur at Layer 7. Therefore, it's essential to use TLS inspection to protect against attackers who increasingly use SSL/TLS to keep their malicious activities hidden. Conclusion Azure Firewall offers robust threat protection capabilities for safeguarding workload deployments in Microsoft Azure. Customers can leverage its application and network-level filtering rules and its integration with Microsoft Threat Intelligence feed. URL and FQDN filtering play a crucial role in analyzing web traffic, and threat intelligence is essential for distinguishing between safe and suspicious domains and URLs. URL filtering is a vital component of a robust security strategy as it enables organizations to prevent unauthorized connections within their network and prevent data exfiltration attempts by threat actors. By leveraging TLS decryption, organizations can enhance their defenses and fortify their overall security posture. Azure Firewall's IDPS, comprising IDS and IPS components, provides an additional layer of defense by monitoring network traffic, detecting potential breaches, and taking preventive measures. Overall, Azure Firewall offers a comprehensive set of features to enhance security and protect against various threats in Azure cloud workloads, allowing customers to improve their security posture and become better protected against future threats. Continue reading...
-
After an incredible year of increased security and productivity, today we recap the current capabilities of Windows Autopatch, highlight new features coming to general availability, and look ahead to more value being added to the service. Whether you're a long-time user or just learning about Autopatch, there's something for everyone below, so read on! The first anniversary of Windows Autopatch The idea for Windows Autopatch came from our customers. As the transition to hybrid work accelerated, managing enterprise endpoints became more complex, and as cybersecurity threats posed increasing risk, the need for applying updates in a timely fashion became more urgent. IT admins asked for help – and we at Microsoft realized we could manage much of the update process on behalf of our customers. The result: Windows Autopatch! A still from the video explainer that launched with Windows Autopatch Over the last year we've heard positive feedback from customers about the time and effort they save updating Windows, Microsoft 365, Microsoft Edge, and Microsoft Teams apps. When those conversations also surface ideas about how Windows Autopatch can be even more helpful, we listen. This latest set of additional features comes directly from customer requests for customizations and flexibility to meet the needs of large enterprises while maintaining the simplicity that makes Autopatch so helpful. New features become generally available July 25, 2023 In our May 2023 announcement, we announced the public preview of features that extend the capability of Windows Autopatch. We are excited to announce that these features will be generally available beginning July 25, 2023. Current customers will also see an announcement in the Microsoft Intune message center detailing updates to the service. May's blog introduced the public preview of exciting new capabilities Before explaining these new capabilities, here is brief recap of Windows Autopatch. What can Windows Autopatch do for enterprises? Autopatch is built on the deployment service and core features of Windows Update for Business. So an IT administrator could configure many of the operations managed by Autopatch themselves. But, the value of the Windows Autopatch service extends beyond the orchestration of updates and time-saving: Evaluations of updates by Microsoft Insights and signals from Microsoft global footprint Security impact Releasing or pausing updates based on worldwide performance Read about the signals Autopatch uses to make release decisions [*]Critical "zero day" update expediting Updates can be deployed by the service in a single day Administrators retain the control to opt-out of this feature Learn more about expedited updates [*]Progressive deployment ring grouping Assign enrolled devices to ring groups automatically Issues that may arise affect a smaller number of devices rather than the entire estate Admins can move devices where needed Learn more about the default rings Customizable, flexible new Autopatch features Among the most-requested capabilities from customers was to be able to configure Windows Autopatch to match existing organizational needs or structures. The resulting features allow IT admins to apply different sets of Autopatch rules to sets of devices as needed: Autopatch Groups (currently in public preview, general availability on July 25, 2023) Divide your tenant into discrete groups that is aligned with your business with customizable configurations Up to 50 distinct groups (applies to Windows feature and quality updates only) Learn more about Autopatch Groups Demo the group creation experience [*]Custom deployment rings (currently in public preview, general availability on July 25, 2023) Up to 15 deployment rings per group Azure AD device groups or individual devices can be assigned dynamically or directly to rings Each ring can have a custom Scheduled or Deadline-driven deployment policy. Deadline-driven allows custom deferrals, deadlines, and grace periods. Scheduled updates can reduce restarts and minimize interruptions Read more about custom deployment cadences Demo the custom cadence and timing process [*]Custom policy naming (currently in public preview, general availability on July 25, 2023) Conform Autopatch policy names to fit your organizational naming standards Note: Renaming the underlying Autopatch deployment groups is not supported. More controls to fit your needs The default behaviors and settings of the service are configured to meet the needs of most organizations. The introduction of custom settings allows more enterprises to take advantage of Autopatch automation while addressing their unique use cases as with these content controls: Feature updates (currently in Public Preview, general availability on July 25, 2023) Upgrade from Windows 10 to Windows 11 "Phases" add a more deployment staggering combined with rings for more comprehensive testing and feedback Read more about automating feature updates. [*]Microsoft 365 apps opt-out Enrolled devices are set by default to "Monthly Enterprise channel" Opt-out allows admins to set another channel for enrolled devices Devices "opted-out" are updated according to the schedule defined for that channel. See Microsoft 365 update channels for more details. [*]Opt out of "Expedited" updates The default critical security update process bypasses the progressive deployment rings (read more about that at this Autopatch 'learn' page). IT admins can opt-out of "expedited" delivery of critical security updates Devices "opted-out" are updated through the Autopatch progressive deployment ring schedule Read more about turning off expedited releases. Demo the content opt-out experience [*]Drivers and firmware Microsoft pre-certifies and validates drivers from many original equipment manufacturers and independent hardware vendors. Automated deployment of recommended drivers Autopatch creates policies aligned with deployment rings Opt-out is available so IT admins can maintain manual control using Intune driver management features. Granular controls around drivers and firmware update management (coming 2023 Q4) - includes the ability to manually approve drivers on a ring-by-ring basis Better reporting and new issue remediation Customers have emphasized the importance of having visibility into all the work that Autopatch is doing on their behalf. A refresh is coming to Autopatch reporting with this July 25 GA announcement that gives more confidence to IT admins that the service is working, more help in resolving issues that may arise, and new banners and notifications help admins identify issues that require attention. Reporting Feature updates now included New integrated recommendations for issue resolution New filtering capabilities More up-to-date information Read about ring remediation functions Demo the reporting functions [*]Policy health and remediation Banners in-context alert admins to issues Policies and Deployment rings can be restored without raising a service incident "Inactive" status of Autopatch blades will direct admins to resolve tenant permission and licensing issues Read more about policy health and remediation Demo the policy health and tenant management experience The future of Windows Autopatch While all these features add up to a more powerful and helpful solution – and we're proud to acknowledge all the progress made in just one year – the development and enhancement of the service will continue. We are grateful to all the developers, product managers who have built this service, and to the customers who have enrolled devices and shared their experiences with our team to help it get better. All about Windows Autopatch If you want to share feedback, request features, or ask questions, please join our Windows Autopatch Tech Community. For those who want to learn more about the value the service has brought to other enterprises, read this report commissioned from Forrester: New Technology: The Projected Total Economic Impact™ Of Windows Autopatch Cost Savings And Business Benefits Enabled By Windows Autopatch March 2023. If you want to experience Windows Autopatch before enrolling devices, we have extensive demos – including some on the newly released features discussed above – at aka.ms/AutopatchDemo. And, finally, if you want to dive deeper, you can find all our resources in the Windows Autopatch resource guide. Want to stay up to date on all things Autopatch? Subscribe to Windows Autopatch blog updates and follow us at @MSWindowsITPro on Twitter! Continue reading...
-
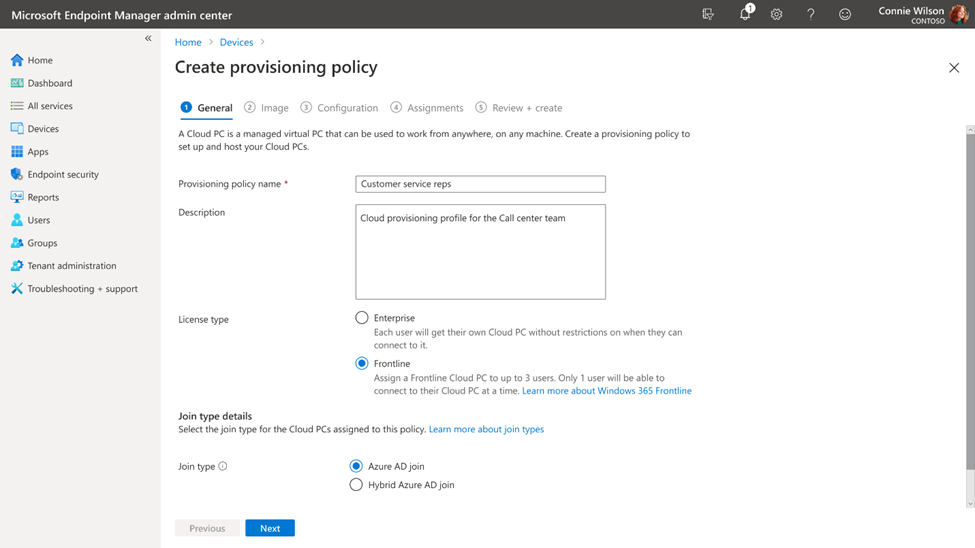
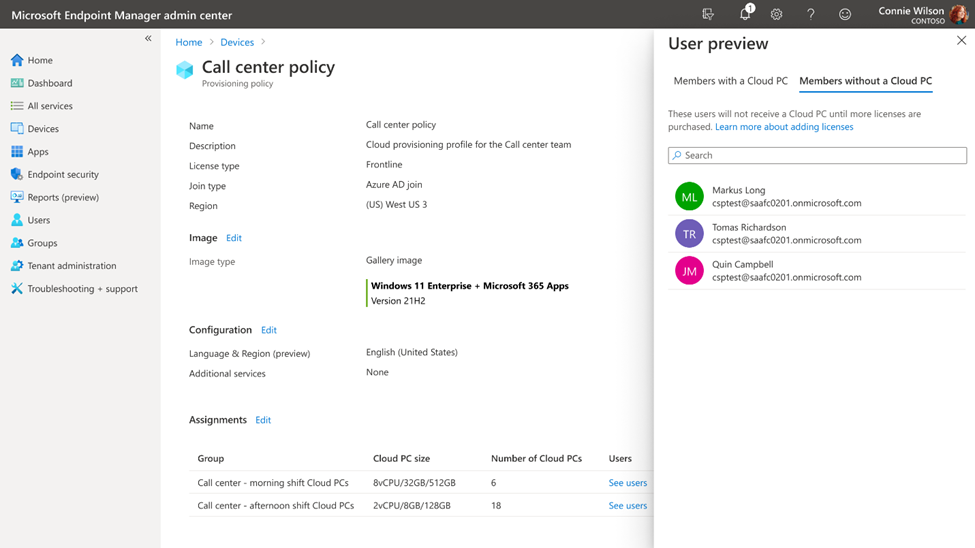
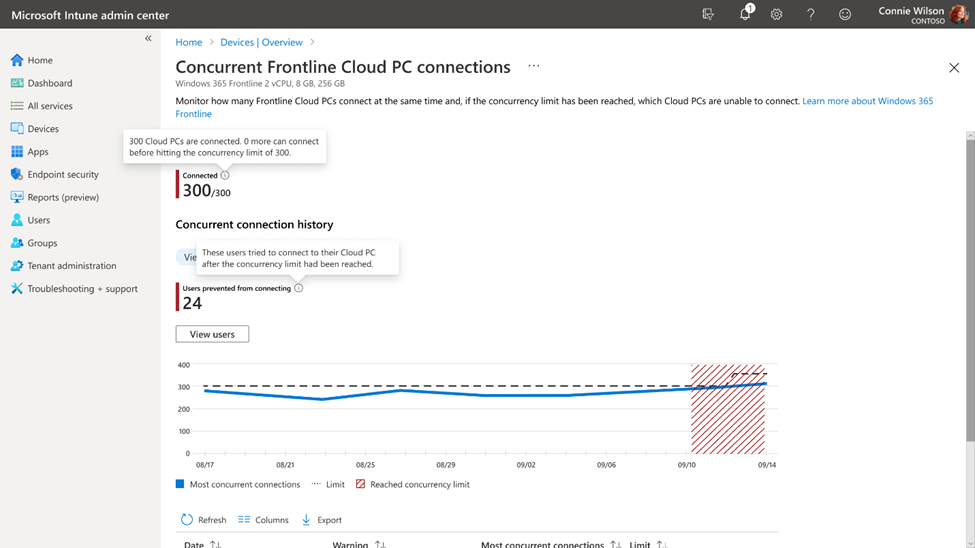
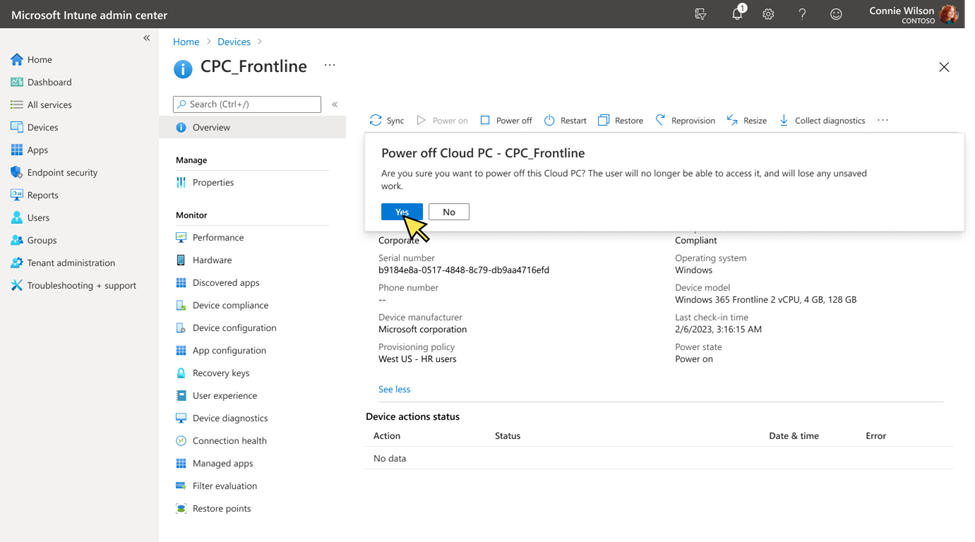
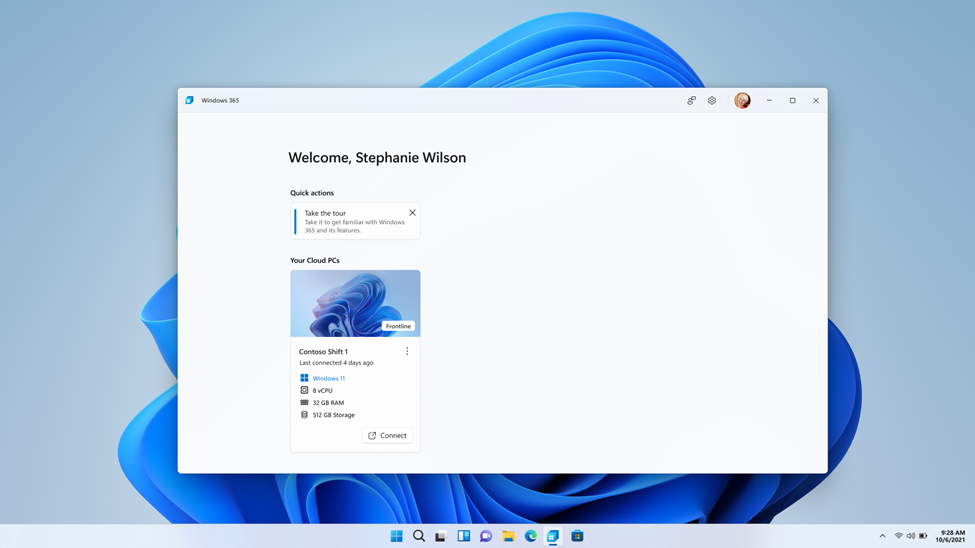
Since its launch two years ago, Windows 365 has changed how companies meet the needs of their flexible workforce. Now, with Windows 365 Frontline, companies can extend the power of Windows 365 Cloud PCs to shift and part-time workers —easily and affordably—allowing them to access their personalized, secure Frontline Cloud PC anywhere and on any device. Windows 365 Frontline is the first Windows solution designed to meet the distinct needs of shift and part-time employees. Instead of the common hassles that come with sharing physical PCs, Windows 365 Frontline provides Cloud PCs—freeing your frontline employees to work from anywhere, helping to boost their productivity, and improving job satisfaction. And, since shift workers typically don't require 24/7 access to their Cloud PCs, with Windows 365 Frontline, you don't need to purchase a Cloud PC for every employee. Rather, you only need enough Cloud PCs for the maximum number of active users at any given time. Windows 365 Frontline also doesn't require scheduling employees; it's automated so workers can log on and off as their shift starts and ends, and throughout their day. For many companies, the ability to extend Cloud PCs in this way can mean cost reductions and increased productivity of their workers, while IT admins also are able to easily manage Frontline Cloud PCs in Microsoft Intune alongside other Cloud PCs and physical devices. During preview, companies have been using Windows 365 Frontline already across an expansive list of scenarios and industries for a variety of cases where employees need access to their Cloud PC for a limited period of time—cases like healthcare clinicians, consultants, customer service representatives, and more. Read on to learn more about why Windows 365 Frontline may be a great solution for your organization, what features are available now and coming soon, and the top questions we've heard from companies during preview. Affordable, flexible Cloud PC access With Windows 365 Frontline, instead of purchasing a license for every shift worker, you can purchase only enough licenses for the number of active employees at any given time. For example, let's say you have nine employees but only three of them work at the same time. With Windows 365 Frontline, you only need three licenses to meet the needs of all nine employees. IT admins can immediately deploy up to three Cloud PCs per purchased license within the Windows 365 provisioning experience using Microsoft Intune. As employees log on, the Frontline Cloud PC is powered on and a license is used for the duration of their work. As they log off, the shared license is returned to the pool of shared licenses, and their Frontline Cloud PC is powered off. Any of the users within a defined group can access their Frontline Cloud PC without requiring a set schedule. This model empowers organizations to extend access to Cloud PCs to employees who may not have had such opportunities in the past and makes it a great solution for employees on a shift schedule—including customer representatives in call centers, help desk workers, and reception staff across many different verticals. The initial benefits you'll see in Windows 365 Frontline begin with affordability and flexibility, but in the coming months you'll continue to see expansion of that value with even more capabilities tailored to meet the needs of frontline, shift, and part-time workers. Note: Windows 365 licenses will show up in the Microsoft 365 admin center under the Products tab only, and do not need to be assigned to specific users. Provision Frontline Cloud PCs and provide users with multiple Cloud PCs Windows 365 Frontline licenses will show up in the Microsoft 365 admin center under the Products tab only, and do not need to be assigned to specific users. Licenses purchased will show the number of Cloud PCs you can deploy in the Windows 365 provisioning experience when choosing Frontline as a license type. This makes it easy to remove and add users to your workforce as it changes. Additionally, IT admins have the flexibility to provide each user with multiple Frontline Cloud PCs to support scenarios such as consultants who work for many different organizations. For more information on how to provision Frontline Cloud PCs, review our public preview blog and our provisioning documentation. A screenshot of Microsoft Intune admin center in the Devices menu, and Frontline and Azure AD Join are selected NEW! Admins can view which users received a Frontline Cloud PC and which users did not by easily viewing the provisioning policy after creation. A screenshot of Microsoft Intune with Window 365 provisioning policy for Windows 365 Frontline selected after creation to view users who received Cloud PCs Frontline Cloud PC concurrency report To deliver cost optimization, customers can use this report to understand trends of license usage over time to plan and adjust the correct number of licenses to ensure access during peak usage. The report provides alerts to IT admins if they are reaching the concurrency limit or have already reached the limit. For more information on how to review Frontline Cloud PC concurrent usage, please read the Cloud PC Utilization Report documentation. Coming soon IT admins will be able to configure email alerts when they are close to reaching max concurrency to ensure they purchase additional licenses to meet demand. A screenshot of Microsoft Intune admin center in the Devices menu, and Frontline Cloud PC concurrency status is selected Manage Cloud PCs easily leveraging existing technology investments Manage Windows 365 Frontline with Microsoft Intune alongside your other Cloud PCs and physical endpoints. Configure, deploy, and manage Windows 365 Frontline without requiring additional infrastructure components or special procedures, applying apps and settings in Intune. The key difference in management capabilities relative to Windows 365 Enterprise is that Frontline Cloud PCs are powered off when not in use. Therefore, some remote actions initiated by you may be completed only after the Cloud PC is powered on, if they are reliant on the Cloud PC being on. Restarting a Cloud PC is one such example. Power on and Power off There are situations in which you may wish to Power on a Frontline Cloud PC to perform a time sensitive action or you may wish to Power off a Cloud PC to free up a session to be used by another user. These new remote actions, along with the ability to view the power state of a Frontline Cloud PC, provides a way for you to respond to immediate action needed. Note: Powering on a Frontline Cloud PC will utilize an active session even if the user does not log on. For more information on how to use these remote actions, review our technical documentation and public preview blog. A Screenshot of the CPC_Frontline menu in the Microsoft Intune admin center, and a curser is hovering over the “Yes” in the “Power off Cloud PC – CPC_Frontline” pop-up Coming soon IT admins will be able to Power on and Power off Frontline Cloud PCs in bulk using Bulk Remote Actions in Microsoft Intune or Microsoft Intune Graph API. This feature enables organizations to build automation to Power on a group of Frontline Cloud PCs prior to a shift based on their scheduling system. Idle timeout default Windows 365 Frontline relies on end users to sign out or disconnect at the end of their Cloud PC session to make the license available for another user. However, frontline workers are often busy working away from their device and may forget to log off or disconnect. Windows 365 detects user inactivity and automatically disconnects after two hours by default. IT admins can use Microsoft Intune to modify the value and preferences for their organization to better meet the needs of specific workers. For more information on how to configure session timeout, review our technical documentation. Optimized for shift and part-time employees Windows 365 Frontline is designed for the way frontline, shift, and part-time workers work. Employees can use the Windows 365 app and web portal to connect to their Cloud PC. As employees connect, they are reminded to save their data and disconnect when they finish. Based on end-user behavior, an automated system will Power on and Power off Frontline Cloud PCs. This functionality will continue to evolve, further optimizing Cloud PC Power on based on shift patterns. Note: Employees can access their Frontline Cloud PC using Windows 365 app or windows365.microsoft.com only. Frontline Cloud PCs are not accessible from Remote Desktop App. Screenshot of the end user login screen for a Windows 365 Frontline Cloud PC Uniquely designed features of Windows 365 Frontline further enhance productivity for workers across various industries and use cases, including healthcare, manufacturing, retail, technical training, and more. Here are examples of initial optimizations that deliver a better experience: Windows Update optimizations for Frontline Cloud PCs: Many shift workers perform mission critical jobs. This feature works together with Windows Update for Business to apply OS reboots outside of work hours when the user disconnects, increasing their productivity and minimizing disruption. To leverage this feature, ensure you set the appropriate recommendations. Coming soon: Windows 365 will detect Frontline Cloud PCs that have not been Powered on for 30 days and will perform updates according to the organization's policies, keeping occasional users or employees productive when they log on next by keeping their Cloud PC up to date outside of work hours. Coming soon: Based on shift patterns, Windows 365 Frontline will Power on automatically prior to the user connecting for their workday. In addition, Windows 365 Frontline will detect shift change overlap and provide the end user with a short period of buffer over max concurrency. This functionality will reduce the delay for the user, letting them be productive immediately at the start of their shift. Coming soon: Windows 365 Boot makes it easier for people to log on to their Windows 11 experience on their Cloud PC. It's already available on Windows 365 Enterprise Cloud PCs in preview and will be coming soon to Frontline Cloud PCs too, helping frontline, shift, and part time workers become productive from the moment they logon. Frequently asked questions about Windows 365 Frontline Is Windows 365 Frontline limited to frontline workers? No, Windows 365 Frontline is not limited to frontline workers. While it is designed for shift and part-time employees, many of whom are frontline workers, scenarios like contingent staff may also only require access to a Cloud PC for a limited part of the day. To use Windows 365 Frontline, you must be licensed for Windows 11 Enterprise or Windows 10 Enterprise, Microsoft Intune, and Azure AD P1. In addition to being available independently, these licenses are included in Microsoft 365 E3, Microsoft 365 E5, Microsoft 365 F3, Microsoft 365 G3, Microsoft 365 G5, Microsoft 365 A3, Microsoft 365 A5. Employees can access their Frontline Cloud PC using Windows 365 app or windows365.microsoft.com only. Frontline Cloud PCs are not accessible from Remote Desktop App, Microsoft 365 Business Premium, and Microsoft 365 Education Student Use Benefit subscriptions. I purchased Windows 365 Frontline licenses, but why do I not see them when reviewing my licenses in Microsoft 365 admin center? Windows 365 Frontline licenses do not follow the same behavior as user-based licensing and as such, do not show up in the Microsoft 365 admin center Licenses tab and cannot be assigned to users. You can find your Windows 365 licenses in Microsoft 365 admin center under Billing > Your products. I can't access Windows 365 Frontline from Remote Desktop app. Is this expected? Windows 365 Frontline is supported through the Windows 365 app and windows365.microsoft.com only. End users can also access the Remote Desktop app by choosing to “open in Remote Desktop app” on Windows 365 web portal. As of July, Frontline Cloud PCs will not be accessible from the Remote Desktop app feed to avoid confusion. Can I continue to use the Frontline Cloud PCs I deployed during the public preview? Yes, you will be able to continue to use your Frontline Cloud PCs if you have purchased the licenses within the first 90 days after general availability. When do I use Windows 365 Frontline, and when do I use Windows 365 Enterprise? Windows 365 Enterprise is for employees that need dedicated, anytime access to their Cloud PC. Windows 365 Frontline is for workers that need access to a Cloud PC only for a limited amount of time, for example, during their shift and not after working hours, part-time, or for limited periods. Each worker will receive a unique Frontline Cloud PC, but licenses are shared. Continue reading...
-
In vista di Microsoft Inspire | 19 e 20 luglio, l’evento più atteso per accelerare la trasformazione AI, far crescere i propri clienti e alimentare la crescita economica dei partner, ecco alcune risorse correlate: AI Resources AI skilling and learning resources on MCAPS Academy Governing AI: A Blueprint for the Future AI For Good Lab Transparency Note for Azure OpenAI Service Full Pitch Deck - Lead the AI era with Microsoft Cloud Azure OpenAI Service Microsoft 365 Copilot Microsoft 365 Copilot: The AI-Powered Future of Work Latest partner deck for Microsoft 365 Copilot How to prepare for Microsoft 365 Copilot Get started with Microsoft 365 Copilot Dati, privacy e sicurezza per Microsoft 365 Copilot Microsoft 365 Copilot technical overview deck Dynamics 365 Copilot Dynamics 365 Copilot pitch deck Dynamics 365 Copilot in Customer Experience Copilot in Power Platform Power Platform Generative AI pitch deck Power Platform Resources Microsoft Security Copilot Microsoft Security Copilot pitch deck Ecco le opportunità di formazione consultabili in lingua inglese: Azure Open AI Azure AI Bootcamp Azure OpenAI Service Documentation | MS Learn Introduction to Azure OpenAI Service | MS Learn What's new in Azure OpenAI Service | MS Learn Azure OpenAI Service Workshop | GitHub Learning Plan Resources for Azure OpenAI | GitHub ¶ Azure OpenAI Business Briefing | YouTube AI For Good Lab | MS Research GSI Azure OpenAI Readiness KPIs GSI Readiness by Region Cross Solution Microsoft Sales Acceleration Bootcamp Cloud Fundamentals for Partners A deeper dive into Microsoft Supply Chain Platform Do More with Less Sales Bootcamp Azure Azure Cloud Week for Partners Azure Depth On-Demand Workshops Azure Sales Bootcamp Modern Work Modern Work GTM Pre-Day Microsoft Viva learning path M365 SMB Masters Program: Sales Track learning path M365 SMB Masters Program: Technical Track learning path Modern Work Cloud Week for Partners Modern Work Sales Bootcamp Security Security Cloud Week for Partners Security, Compliance, and Identity Management Security Sales Bootcamp Business Applications Business Applications Cloud Week for Partners Business Applications Depth On-Demand Workshops Viva Sales: scenarios, features and partner opportunity Business Applications Sales Bootcamp *** Registratevi alle prossime sessioni di Microsoft Partner Academy, progettate per aiutare la vostra organizzazione a crescere come partner Microsoft. Partecipate all’iniziativa Skill your own way for a more profitable future in ambito Technical o Sales e costruite il percorso di apprendimento maggiormente in linea con le vostre esigenze e competenze. Consultate le Guide e i Playbook suddivisi per argomenti e Solution Area, fondamentali per migliorare le vostre skills Microsoft! Infine, personalizzate il vostro percorso formativo anche su Microsoft Learn, la piattaforma di formazione online gratuita che offre risorse di apprendimento interattivo per i prodotti Microsoft e altro ancora! STAY TUNED AND SKILL UP! Continue reading...
-
Microsoft 365 Defender Monthly news July 2023 Edition [attachment=44312:name] This is our monthly "What's new" blog post, summarizing product updates and various new assets we released over the past month across our Defender products. In this edition, we are looking at all the goodness from June 2023. Legend: [attachment=44313:name] Product videos [attachment=44314:name] Webcast (recordings) [attachment=44315:name] Docs on Microsoft [attachment=44316:name] Blogs on Microsoft [attachment=44317:name] GitHub [attachment=44318:name] External [attachment=44319:name] Product improvements [attachment=44320:name] Previews / Announcements Microsoft 365 Defender [attachment=44321:name] Prevent repeat attacks with threat-informed security posture recommendations. Microsoft 365 Defender now makes it easy for security operations (SOC) teams to identify and prioritize the right controls with the general availability of threat-informed security posture recommendations. [attachment=44322:name] [attachment=44323:name] Share your feedback on Microsoft 365 Defender via the new feedback portal. We’re excited to announce that Microsoft 365 Defender is now part of the new community feedback experience, and our customers now have a dedicated platform to submit their suggestions and feature requests for our security products. [attachment=44324:name] Ninja Show Season 4 recap! In this season we had a special mini-series on incident response, with lots of demos on how to investigate incidents following playbooks. Check out this summary and let us know your favorite topic from this season or what you’re looking forward to next! [attachment=44325:name] Microsoft Defender for Endpoint [attachment=44326:name] Forcibly releasing devices from isolation is now available for public preview. This new capability allows you to forcibly release devices from isolation, when isolated devices become unresponsive. For more information, see Take response actions on a device in Microsoft Defender for Endpoint. [attachment=44327:name] New Monthly security summary. Gain insights into an organization’s security posture and performance, as well as visualizing the team’s effort in managing the environment. Microsoft Defender for Cloud Apps [attachment=44328:name] [attachment=44329:name] App governance is now included as part of the Defender for Cloud Apps licenses and no longer requires an add-on license. In the Microsoft 365 Defender portal, go to Settings > Cloud apps > App governance > Service status to either enable app governance if available, or sign up for the waitlist. Webinar: App Governance Inclusion in Defender for Cloud Apps Overview. [attachment=44330:name] Safeguarding your OAuth apps with App Governance. Learn why App Governance is the essential layer of defence to protect your Oauth apps. Learn how to enable it and start using in a couple of steps. [attachment=44331:name] Defender for Cloud Apps Operational Guide is ready to download for your SOC and security teams to help with planning and performing security activities. [attachment=44332:name] Update Defender for Cloud Apps IP addresses for reverse proxy infrastructure. We recently completed infrastructure enhancements which resulted in new IPs that need to be added for Defender for Cloud Apps proxy infrastructure. We recommend that customers review the network list for proxy and ensure these have been updated in their environments. [attachment=44333:name] Enhanced hunting experience for OAuth app activities. App governance now makes it easy for you to take hunting with app data to the next level by providing deeper OAuth app insights, helping your SOC identify an app’s activities and the resources it has accessed. OAuth app insights include: Out-of-the-box queries that help to streamline the investigationVisibility into the data using the results viewThe ability to include OAuth app data such as resource, app, user, and app activity details in custom detections. For more information, see Hunt for threats in app activities. [attachment=44334:name] App hygiene update with Microsoft Entra. Starting June 1, 2023, management of unused apps, unused credentials, and expiring credentials will only be available to app governance customers with Microsoft Entra Workload Identities Premium. See Secure apps with app hygiene features and What are workload identities?. Microsoft Defender for Identity [attachment=44335:name] Advanced hunting with an enhanced IdentityInfo table. For tenants with Defender for Identity deployed, the Microsoft 365 IdentityInfo advanced hunting table now includes more attributes per identity, as well as identities detected by the Defender for Identity sensor from your on-premises environment. For more information, see the Microsoft 365 Defender advanced hunting documentation. [attachment=44336:name] Webinar recording: Become an Advisor to Our Product Engineering Team. The Defender for Identity product engineering team is excited to share a program for customers to become trusted advisors and impact our feature planning. Engage directly with the engineering team, learn what's coming, test out private previews, and share your experiences and recommendations. Microsoft uses the program to put the customer at the center of product development and, ultimately, help us better secure your organization and your customers. Microsoft Defender for IoT [attachment=44337:name] On June 1, 2023, Microsoft Defender for IoT moved to site-based licensing for organizations looking to protect their operation technology (OT) environments. The previous Azure consumption model for this solution will no longer be available for purchase by new customers. Existing customers can choose to transition to site-based licensing or remain on the consumption model. [attachment=44338:name] IoT devices and Linux-based systems targeted by OpenSSH trojan campaign. Microsoft has uncovered an attack leveraging custom and open-source tools to target internet-facing IoT devices and Linux-based systems. The attack involves deploying a patched version of OpenSSH on affected devices to allow root login and the hijack of SSH credentials. Microsoft Defender for Business [attachment=44339:name] Streaming API for Defender for Business customers is now in public preview! We are delighted to announce that Microsoft Defender for Business now supports streaming events through Advanced Hunting! This means that Defender for Business customers can stream the data to Event Hubs, Azure, or local storage. Blogs on Microsoft Security [attachment=44340:name] Detecting and mitigating a multi-stage AiTM phishing and BEC campaign. Microsoft Defender Experts observed a multi-stage adversary-in-the-middle (AiTM) and business email compromise (BEC) attack targeting banking and financial services organizations over two days. This attack originated from a compromised trusted vendor, involved AiTM and BEC attacks across multiple supplier/partner organizations for financial fraud, and did not use a reverse proxy like typical AiTM attacks. [attachment=44341:name] Cadet Blizzard emerges as a novel and distinct Russian threat actor. Microsoft attributes several campaigns to a distinct Russian state-sponsored threat actor tracked as Cadet Blizzard (DEV-0586), including the WhisperGate destructive attack, Ukrainian website defacements, and the hack-and-leak front “Free Civilian”. Microsoft 365 Defender Threat Analytics reports (Portal access needed) Detecting and mitigating a multi-stage AiTM phishing and BEC campaign. In April 2023 Microsoft Defender Experts uncovered a multi-stage adversary-in-the-middle (AiTM) phishing and business email compromise (BEC) attack against banking and financial services organizations. The attack originated from a compromised trusted vendor and showcases the complexity of AiTM and BEC threats which abuse trusted relationships between vendors, suppliers, and other partner organizations with the intent of financial fraud. Technique profile: Antivirus tampering. One of the first steps many attackers take after the initial compromise of an organization is to identify and tamper with security solutions. By disabling or otherwise tampering with defenses, attackers gain time to install malicious tools, exfiltrate data for espionage or extortion, and potentially launch destructive attacks like ransomware. Vulnerability profile: MOVEit Transfer zero-day exploitation (CVE-2023-34362). On May 31, 2023, Progress Software Corporation disclosed a critical SQL injection vulnerability (CVE-2023-34362) in their MOVEit Transfer application that could lead to unauthenticated access to the underlying database. Microsoft has observed active exploitation of the MOVEit Transfer vulnerabilities as early as May 27, 2023. MediaArena potentially unwanted application detection surge. Microsoft observed an increasing number of detections for a new family of unwanted applications named MediaArena, a highly prevalent family of browser modifier applications that bypass a browser's supported extensibility model to change Microsoft Edge's default search provider. Actor profile: Lace Tempest ransomware and extortion group. Lace Tempest (DEV-0950) is a cybercriminal group known to conduct ransomware operations. They target organizations across a diverse array of industries and have traditionally used phishing campaigns and exploited public-facing Serv-U FTP server vulnerabilities to obtain initial access. Recently, Microsoft observed activity originating from Raspberry Robin worm infections attributed to Lace Tempest. Activity Profile: Peach Sandstorm uses sophisticated TTPs in a new campaign. Microsoft observed a resurgence of activity attributed to Peach Sandstorm, an Iran-based nation state actor. While the majority of activity Microsoft saw in this campaign can be characterized as reconnaissance, in March 2023, Microsoft identified a successful intrusion where Peach Sandstorm used a GoldenSAML attack to ultimately exfiltrate data from a compromised organization. Actor profile: Cadet Blizzard. Cadet Blizzard (DEV-0586) is a Russian GRU-sponsored threat group that Microsoft began tracking following disruptive and destructive events occurring at multiple government agencies in Ukraine in mid-January 2022. Primary targeted sectors include government organizations and information technology providers in Ukraine, although organizations in Europe and Latin America have also been targeted. Actor profile: Storm-0288 leverages handoffs from multiple actors to deploy ransomware. Storm-0288 (DEV-0288) is a financially-motivated cybercrime group known to use the malware families PUNCHBUGGY, BadHatch, and White Rabbit, among others. Identified operations have focused on point-of-sale compromise, data exfiltration, extortion, and ransomware deployment. Actor profile: Storm-0396 operates LockBit ransomware as a service. Storm-0396 (DEV-0396) is a cybercriminal group known as the likely operators of LockBit ransomware as a service (RaaS). They manage the LockBit RaaS offerings, including LockBit 2.0, LockBit Black (aka LockBit 3.0), the recently discovered variant LockBit Green, and an ESXI variant to encrypt Linux servers. LockBit RaaS is one of the most prominent RaaS models and has historically impacted numerous organizations worldwide. Activity profile: Storm-1359 launches distributed denial of service attacks. Microsoft has attributed distributed denial of service (DDoS) attacks in early June 2023 to the threat actor tracked as Storm-1359. These attacks against multiple Microsoft cloud services, including Microsoft 365 and Azure, likely rely on access to multiple virtual private servers (VPS) in conjunction with rented cloud infrastructure, open proxies, and DDoS tools. Threat insights: Storm-0875 uses social engineering and AADInternals to compromise cloud identities. In April and May 2023, Microsoft Threat Intelligence attributed multiple attacks involving cloud identity compromise in Microsoft Azure and Office 365 tenants to the threat actor that Microsoft tracks as Storm-0875 (DEV-0875). To compromise cloud identities, Storm-0875 (also known as 0ktapus) used extensive social engineering tactics to compromise Global Administrator accounts, then used the AADInternals tool to establish a federated backdoor and generate security assertion markup language (SAML) tokens. The tokens allowed the actor to sign-in as additional accounts for persistence and follow-on malicious activities, including pivoting to access on-premises resources. Actor profile: Storm-0201. Storm-0201 (DEV-0201) is a criminal group that focuses on the development and distribution of the Emotet malware. They are known to primarily target organizations in opportunistic email attacks worldwide, and prior Storm-0201 infections have led to ransomware. Storm-0201 is tracked by other security companies as Mummy Spider and TA542. Activity profile: Midnight Blizzard credential attacks. Since at least March 2023, Microsoft Threat Intelligence detected an increase in credential attacks and initial access operations utilizing residential proxy services conducted by the threat actor that Microsoft tracks as Midnight Blizzard. The credential attacks use a variety of password spray, brute force, and token theft techniques to gain access to target environments. Actor profile: Storm-0558. Storm-0558 (DEV-0558) is a nation-state activity group based out of China. They focus on espionage, data theft, and credential access. They are also known to use custom malware that Microsoft tracks as Cigril and Bling, for credential access. IoT devices and Linux-based systems targeted by OpenSSH trojan campaign. Microsoft researchers have recently discovered an attack leveraging custom and open-source tools to target internet-facing Linux-based systems and IoT devices. The attack uses a patched version of OpenSSH to take control of impacted devices and install cryptomining malware. Tool profile: Greatness adversary-in-the-middle phishing-as-a-service platform. Greatness is a phishing-as-a-service (PhaaS) platform with adversary-in-the-middle (AiTM) capabilities that has been active since mid-2022 and is attributed to the threat that Microsoft tracks as Storm-1295 (DEV-1295). Continue reading...
-

Microsoft 365 Admin Monthly Digest – June 2023
AWS posted a topic in Microsoft Support & Discussions
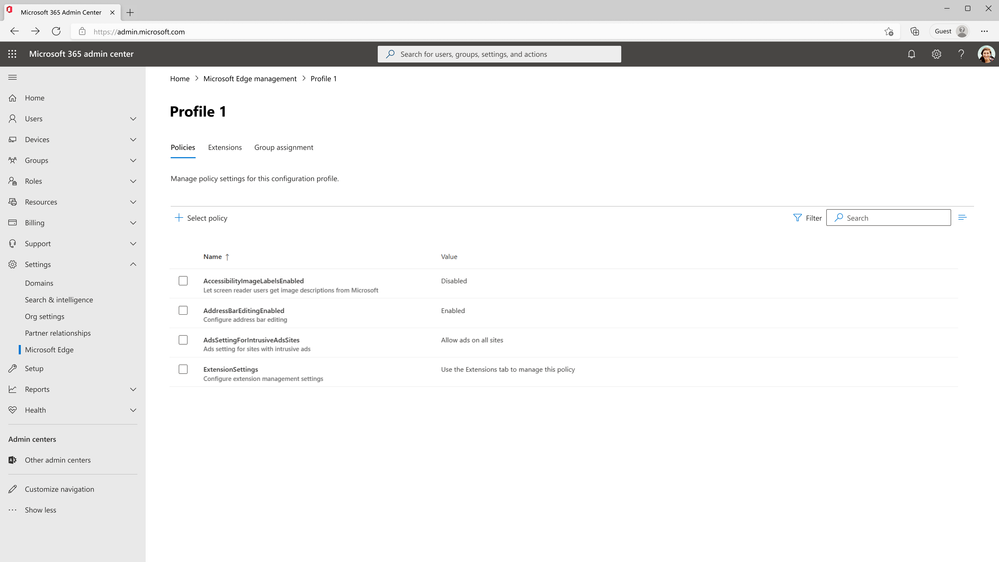
A banner image with the text: "Microsoft 365 Admin Digest: Your monthly IT admin blog for all things Microsoft 365." Welcome to the Microsoft 365 IT admin blog, your monthly source of tips, insights, and best practices for managing and optimizing your Microsoft 365 environment. In this edition, we'll explore how you can get your tenant ready for Microsoft 365 Copilot, and the impact of healthy Microsoft 365 adoption on talent acquisition and retention while embracing generational diversity. Learn about enhancements to the admin center and read on to catch up about all things Microsoft 365 administration. Get your tenant ready for AI (and join the community) We’re excited to help you start preparing for Microsoft 365 Copilot. While availability is limited to select customers as part of the Early Access Program, Microsoft published a series of articles on steps you can take now to get your tenant ready. In the first blog post in the brand-new Microsoft 365 Copilot community, we provide best practices and recommendations that you can implement to help you get ready for Copilot. Microsoft 365 Copilot uses your existing permissions and policies to deliver the most relevant information, building on top of Microsoft’s existing commitments to data security and data privacy in the enterprise. This emphasizes the need for good content management practices to begin with. Therefore, understanding permissions and sensitivity labels, implementing data loss prevention policies, and leveraging reports on data access governance are good practices for a healthy digital environment. The blog also provides additional details on security, privacy, and data residency, and tips for staying up to date with changes and announcements, so you can help drive Copilot adoption with your users. The new Microsoft 365 Copilot community is a hub for the latest news and updates from Microsoft on Copilot. There, you’ll find relevant discussions across Microsoft 365 apps and services and a space to interact with other members. We look forward to having you join the community and be part of the conversation. Highlights across Microsoft 365 administration Let’s check out some of the latest features we have launched in the Microsoft 365 admin center and how they could be useful for you. In our continued effort to make it easier for you to drive adoption, Adoption Score is now available to all commercial customers by default. Group Level Aggregates, now included in Adoption Score, offers data segmentation by Azure Active Directory attributes to help you better assess your adoption data by different areas within your organization. Also, in preview for organizations using Adoption Score, Organizational Messages allows you to use these insights to send relevant tips and guidance on usage best practices directly to your users. Accessible in the Microsoft 365 admin center, Adoption Score is a set of anonymous user metrics and tools that give you visibility into how your organization works with Microsoft 365 and provide insights into where you can improve user experiences by sharing best practices for using Microsoft 365 features. Additionally, Experience insights, now in preview to customers with at least 2000 seats, can help you better support users and increase satisfaction. With Experience insights, organizations gain visibility into sentiment, help article consumption, and usage of Microsoft 365 applications such as Outlook, Teams, SharePoint and more. This data is curated in a single view to help you identify and address issues that may hinder productivity or cause frustration for users. Read the full announcement here. In addition to tracking adoption, you can use the Microsoft 365 Health dashboard in the Microsoft 365 admin center to understand how well apps and services are running in your organization. Designed to give you a snapshot of the overall health of your environment, the dashboard helps ensure you are keeping updated with the latest software, following best practices for security, and using the products and service you’re paying for. At the bottom of the dashboard, you’ll also find recommended actions for improving your organization’s health across the Microsoft 365 environment. The Microsoft Edge management service was recently made available for Public Preview (Roadmap ID 123856). You can access the service through the Microsoft 365 admin center, Org settings > Microsoft Edge, and can configure Microsoft Edge browser settings for your organization and apply these settings by group assignment or group policy. Through the portal, you can also manage browser extensions and policies or view user requests for browser extensions. To learn more, read about the Microsoft Edge management service. An image of the Microsoft Edge management service portal in the Microsoft 365 admin center. We know you spend a lot of time ensuring your Microsoft 365 tenant is secure from threats. Microsoft is making it easier for you to protect user accounts right from the start with Microsoft 365 security defaults. When turned on, security defaults provide settings that keep your organization safe by establishing strong multi-factor authentication (MFA) settings. To enable or confirm enablement of security defaults, go to the Azure portal, click on Manage Azure Active Directory > View > Properties > Manage security defaults. Learn more here. Furthermore, it’s good to ensure that you’ve taken all the necessary precautions with your admin accounts because of the elevated privileges they have. Simple best practices include Global admins having at least one other Global admin account created with another user as backup, and keeping their admin account only for administration activities while using a separate user account for their regular use of Microsoft 365 apps. You don’t have to assign a Microsoft 365 license to the administrative account since it won’t be used. Requiring MFA should be a given, and general best practice is to avoid custom permissions for admins and instead use the default permission groups for simpler management. Read more about protecting admin accounts. The MS-102: Microsoft 365 Administrator exam launches in early July. Currently in beta, this certification confirms the ability to perform Microsoft 365 tenant-level implementation and administration of cloud and hybrid environments. Covering a range of foundational topics including administration and establishing a Microsoft 365 tenants, the exam is also a prerequisite to the Microsoft 365 Administrator Expert certification. Microsoft certifications accredit skills that not only align with workplace needs but can also open doors for Microsoft 365 administrators in their career. To learn more about other certifications across Microsoft administration, check out this blog post. Viva Pulse is a new employee feedback experience that will be available for use with your Viva Suite subscription. Viva Pulse empowers managers and project team leaders to request and receive feedback from their teams at any time. Global admins will be able to enable the preview for their organization by visiting the Viva Pulse site. From there, select Manage access, then toggle Public Preview access on. Support Microsoft 365 adoption and embrace generational diversity A recent study conducted by Enterprise Strategy Group explores how organizations in the Public Sector are facing a generational shift in their workforce, navigating a wave of retiring baby boomers and the challenge of attracting and retaining millennials and Gen Z. Taking lessons from the study, empowering your workforce with modern productivity, collaboration, and security tools can help your organization embrace generational diversity and across four critical areas: recruitment, retention, productivity, and learning. In the constantly evolving work environment, creating a healthy digital environment to attract new talent and retain experienced employees ultimately helps keep companies competitive in their field. Read the blog here. An infographic depicting the findings of the Enterprise Strategy Group research study outlining the positive benefits of healthy Microsoft 365 adoption across Recruitment, Retention, Productivity, and Learning. IT departments are increasingly tasked with ensuring digital tools are successfully adopted, and this digest blog series has previously covered tools provided in the Microsoft 365 admin center and on adoption.microsoft.com to help track utilization and offer recommendations on how to improve it. Check out the Transforming State and Local Government IT blog post to learn more. Join these upcoming Tech Community events Viva Engage & Yammer Rebranding - What's next! AMA on July 11th, at 9:00–10:00am Pacific time Adoption Score AMA on July 12th, at 9:00–10:00am Pacific time Microsoft 365 Copilot AMA on July 13th, at 9:00–10:00am Pacific time Stay updated As always, stay current with the latest updates Microsoft 365 admin center updates from the Microsoft 365 roadmap and message center. In addition, we also highlight new feature releases and enhancements released each month in our What's new in the Microsoft 365 admin center article. Comment below if there are IT admin or change management topics you would like us to explore in the future! Continue the conversation by joining us in the Microsoft 365 community! Want to share best practices or join community events? Become a member by "Joining" the Microsoft 365 community. For tips & tricks or to stay up to date on the latest news and announcements directly from the product teams, make sure to Follow or Subscribe to the Microsoft 365 Blog space! Continue reading... -
Welcome to the June 2023 update. We celebrated Pride this month, read more on how to add a touch of Pride to your Excel here. This month we also bring you Formula Suggestions and Formula by Example for Excel web users. Use Image and Data Types in PivotTables are now available for Windows and Mac Insider users, and Generate an Accessible PDF is available to all Mac users. Many of these features are the result of your feedback. THANK YOU! Your continued Feedback in Action (#FIA) helps make Excel better for everyone. Excel for web: Formula Suggestions Formula by Example Support Chart Formatting via Selection & Ribbon Buttons Move Chart Elements within Chart Player Name Manager #FIA Excel for Windows: Office Scripts (Current Channel and Monthly Enterprise Channel) Get data from Dynamic Arrays (Current Channel) #FIA Rapid Refresh (Current Channel) #FIA Guided Reapply (Current Channel) Use Image and Data Types in PivotTables (Insiders) Excel for Mac: Generate an Accessible PDF #FIA Enhanced Search Experience #FIA Use Image and Data Types in PivotTables (Insiders) Excel for web 1. Formula Suggestions Type the “=” sign in a cell or the formula bar and Excel will auto-suggest the best formula based on contextual insights from your data. Formulas that can be suggested are SUM, AVERAGE, COUNT, COUNTA, MIN, and MAX. This feature is now available for all web users who have English set as their primary language. Read more here > 2. Formula by Example As you are performing manual and repetitive data entry in a column, Excel will now suggest you to fill the entire column with a formula in case we identify a pattern. This is similar to Flash Fill, however, instead of static text - now formulas can be suggested. This feature is now available for all web users. 3. Support Chart Formatting via Selection & Ribbon Buttons Format your chart using the Home Ribbon Formatting controls. 4. Move Chart Elements within Chart Player Click and drag chart element and trend line equation to move them in the chart. This expands users' ability to customize how their chart looks. #FIA 5. Name Manager Create named ranges from the Name Box in Excel for the web. Users can also search in the name box for any named ranges. Excel for Windows 1. Office Scripts Automate repetitive worksheet tasks without needing any programming experience. Perform the actions you want in Excel, and the recorder will create an Office Script to replay those actions for you. Read more > Record worksheet actions using Office Scripts #FIA 2. Get Data from Dynamic Arrays Get Data from Table/Range now includes Dynamic Arrays! Select any Dynamic Array on the grid and import it using Power Query. #FIA 3. Rapid Refresh Rapid Refresh is a feature that automatically reloads the workbook in coauthoring scenarios where the user may be prompted to refresh manually. Multi-workbook support and support in Excel for Mac coming soon. Rapid Refresh experience on Win32 4. Guided Reapply Previously, when coauthoring got interrupted for one reason or another, users would have to select “Save As” (which creates another copy of the file) or “Discard” their changes to get back to the shared file. With Guided Reapply, users can review the pending changes and return to the shared file with confidence. Guided Reapply for Windows 5. Use Image and Data Types in PivotTables (Insiders) Data types and in-cell images are a powerful part of modern Excel, and now, they come intact to your PivotTable rows and columns including the same interactions you have in your source data (image cards, data type icons, data type cards, and so on). Read more > Use images and data types in PivotTables, for Windows and Mac Insiders Excel for Mac #FIA! 1. Generate an Accessible PDF Previously when you exported to PDF on Mac, there were no tags added to communicate the structure of the document so all of the content was jumbled together. Now, the PDF service automatically creates accessibility tags, which brings the experience on par with Win32. Generate an accessible PDF on Mac #FIA 2. Enhanced Search Experience (Insiders) The search experience has been revamped to provide a single place to find content from multiple sources. This function provides smart search suggestions before you type as well as supporting searching for more than just text in your document, i.e., you can also search for commands, help articles, or web results (such as definitions, media, and Bing results). Read more here > Enhanced Search Experience in Excel for Insiders Mac users 3. Use Image and Data Types in PivotTables (Insiders) Data types and in-cell images are a powerful part of modern Excel, and now, they come intact to your PivotTable rows and columns including the same interactions you have in your source data (image cards, data type icons, data type cards, and so on). Read more > Use images and data types in PivotTables, for Windows and Mac Insiders Check if a specific feature is in your version of Excel Click here to open in a new browser tab Your feedback helps shape the future of Excel. Please let us know how you like a particular feature and what we can improve upon—send us a smile or frown. You can also submit new ideas or vote for other ideas via Microsoft Feedback. Subscribe to our Excel Blog and the Insiders Blog to get the latest updates. Stay connected with us and other Excel fans around the world – join our Excel Community and follow us on Twitter. Special thanks to our Excel MVP David Benaim for his contribution to this month's What's New in Excel article. David publishes weekly YouTube videos and regular LinkedIn posts about the latest innovations in Excel and more. Continue reading...
-
Happy Friday, everyone I hope you’ve all had a good week. Let’s recap some of this week’s MTC highlights! MTC Moments of the Week This week, we welcomed Windows 365 users to join us for our June Windows 365 AMA to discuss the latest W365 features, deployment, customization, and best practices. We had experts from the engineering and product teams live streaming and answering questions as they came in (shout out to Christian Montoya, Christiaan Brinkhoff, and Andrew Miyasato!). Keep your eyes peeled for the July AMA date coming soon! And speaking of AMAs, on Thursday, we had a new Tech Community Live with Microsoft Intune to help users learn best practices for managing ALL the endpoints – whether they’re based in Windows and macOS to iOS, Linux, Android, you name it! Engineering and product teams joined us on camera and in chat to answer questions about a whole host of endpoint management topics, from drivers, firmware, and AutoPatch to endpoint security, privilege management, and more! You can catch up on all the sessions here and watch on-demand any time. A big thank you to the Intune team who hosted and contributed to these sessions, including Matt Call, Danny Guillory, Arnab Biswas, Dilip Radhakrishnan, David Guyer, Christian Montoya, Christiaan Brinkhoff, Andrew Miyasato, Rinku Stephen, Joe Lurie, Arnab Biswas, Aman Haq, Clay_Taylor, Lothar Zeitler, Courtenay Bernier, Max Stein, Heather Poulsen and Charlize Cheesman! Over on the Blogs, we’re talking Microsoft 365 Copilot and the technical requirements you need to meet before you can use it. Check out this article by @Yana Terukhova explaining these requirements and other important onboarding info! And we’re shining our MTC Member of the Week spotlight this week on @Jan Karel Pieterse! Jan is a professional Excel developer based in the Netherlands and a Microsoft MVP for over 20 years. We’re so happy to have you sharing your expertise in the Excel forums, Jan! Upcoming Events - Mark Your Calendars! June 27, 2023, 08:00 AM - 12:00 PM (PDT) - Microsoft Entra Tech Accelerator June 27, 2023, 08:00 AM - 09:00 AM (PDT) - Unpacking Endpoint Management: A cloud management gateway - how much will it cost me? June 28, 2023, 08:00 AM - 08:30 AM (PDT) - What’s next in end user experiences for Windows 365 June 28, 2023, 09:00 AM - 10:00 AM (PDT) - Microsoft Teams AMA July 11, 2023, 09:00 AM - 10:00 AM (PDT) - Viva Engage & Yammer Rebranding – What’s next! July 12, 2023, 09:00 AM - 10:00 AM (PDT) - Microsoft 365 AMA July 13, 2023, 09:00 AM - 10:00 AM (PDT) - Microsoft 365 Copilot AMA ----- For today’s fun fact… On this day in 2005, the online social media forum website Reddit was founded in Medford, Massachusetts. As of 2023, Reddit boasts over 430 million monthly active users from around the world. And with that, have a great weekend, everyone! Continue reading...
-
In this episode of MidDay Café hosts Tyrell Barnes and Michael Gannotti discuss Human/AI partnership. Many organizations are trying to figure out AI strategy but seem to be taking a tech/product first approach. What Tyrelle and Michael discuss is how to anchor on people/employees first with AI/Tech in support. Listen to the Audio podcast version: Subscribe to the Audio Podcast on Spotify Subscribe to the Audio Podcast on Apple Podcasts Subscribe to the Audio Podcast on Google Podcasts Resources: Introducing Microsoft 365 Copilot | Microsoft 365 Blog Introducing Microsoft 365 Copilot – your copilot for work - The Official Microsoft Blog Get started with Copilot (preview) - Power Automate | Microsoft Learn Artificial Intelligence Solutions | Microsoft AI Reinventing search with a new AI-powered Microsoft Bing and Edge, your copilot for the web - The Official Microsoft Blog Introducing Microsoft 365 Copilot — your copilot for work A Whole New Way of Working (microsoft.com) Copilot in Viva Sales innovates with next-generation AI - Microsoft Dynamics 365 Blog Thanks for Visiting! Tyrelle Barnes LinkedIn : Michael Gannotti LinkedIn | Twitter Continue reading...
-
When it comes to keeping the clocks in your organization running normally, you rely on our Windows engineers. We, in turn, look to governments for timely collaboration. Let's talk about the importance and complexity of time zone (TZ) changes, as well as some best practices to help your organization always be on time! Why are time zones important? Imagine how difficult it would be for you to coordinate if clocks had shown different times with each passing longitude – a 4-minute difference every few kilometers? That's where time zones come into the picture. They split the earth in near vertical strips and group together places for which it is convenient to have the same time for communication. This helps create a uniform standard time for social, commercial, and legal purposes. But what if there's a change in a specific time zone? What if a country decides to move from one time zone to another? These and many other scenarios pertaining to daylight saving time (DST) changes create a very tricky situation for countries around the world and for you as an IT pro to manage. With Windows at the center of computing for a large portion of worldwide devices, it's apparent that such TZ changes must be reflected accurately on devices, on time and consistently, to ensure businesses run smoothly. The complexity behind the scenes of time zone changes We closely monitor time zone changes by keeping track of government announcements, updates on Time Zone Database, and when you reach out to our support team. This sets in motion a series of internal processes that cater to delivering the changes in a period of about 8 weeks. On the one hand, we need appropriate time to ensure the right level of quality of this update, just as we do with any update. On the other hand, we want to avoid unnecessary disruptions for the world by coupling these updates with the predictable update cadence. Therefore, in order to deliver these updates as part of the monthly updates or latest cumulative updates (LCU), the team requires sufficient notice to develop, validate, and release a quality fix. Here's what that timeline would look like! Illustrative timeline for developing a TZ fix in 8 weeks since government announcement and before DST change takes effect We can't overlook the fact that sometimes a government announces a TZ change with shorter lead time. The times it has happened, no release vehicle was available that could accommodate a high-quality change in time. Let's learn from a recent example before getting to the practical recommendations. On August 8th of 2022, a South American nation government announced that a new DST change would begin on September 10th. This one-month notice, unfortunately, was too short to develop a fix with the right quality on time. It was eventually available in the October security update, missing the TZ change trigger date by over a month. Considering an 8-week workflow, we would have needed to receive that notice no later than early July of that year. But even this 8-week period doesn't account for the fact that the uptake of the released fix often times isn't immediate. Indeed, it is crucial that governments give sufficient time so that we can release TZ changes on time with quality and that users consume them with reasonable planning. How would you do that? Let's see some best practices. Best practices For governments Please help Microsoft provide an update at the earliest and ensure a seamless transition to the new DST and TZ policies. Microsoft recommends that governments provide the following: Ample advance notice (one year or more, but not fewer than 8 weeks) of the planned change Official published confirmation of planned changes to DST or time zones Concentrated efforts to promote the change to affected citizens If available, notify your Microsoft country officers of the change. In either case, please include this information on the government official website. For IT admins Whenever a TZ change is announced by the government, look out for and get the changes built into a specific release. Keep track of the DST Community Blog. It is regularly updated to announce when Microsoft becomes aware of a TZ change, when it will release the fix, and if there is an interim guidance to be followed. When changes are delivered via a preview release, download and install it as soon as it becomes available for your devices. Preview releases often provide an early opportunity to test and implement the time zone fix. How to get the time fix When a time zone change is ready to be shipped, get it for your organization through a specific release via Windows Update. You can get the change as part of the monthly security update, released on the second Tuesday of the month. As such, it reaches all the supported devices through your regular update management process and without any intervention from your end users. Sometimes the change is part of the monthly optional non-security update, released the fourth week of the month. You'd need to download this update from Windows Update to get the changes. If you don't install it at this time, the change is automatically included in the next monthly security update. Read about the difference between these releases in Windows monthly updates explained. Check out Daylight saving time help and support for details about our notice time requirements, our support policy, and solutions offered for different time zone scenarios. Continue the conversation. Find best practices. Bookmark the Windows Tech Community and follow us @MSWindowsITPro on Twitter. Looking for support? Visit Windows on Microsoft Q&A. Continue reading...
-
Today, we are releasing our latest version of Windows Admin Center – version 2306! Thank you to our customers, partners, and fans for helping us to continue to improve and make Windows Admin Center better. In this release, we have made improvements across our entire product! From updates to our platform, improving your core tool management experiences, introducing new features, and bridging some of the gap for the legacy tool parity. We hope you will read on and share our excitement for the new features we are introducing this summer. If you’re as excited as we are, you can download right away! Platform updates WDAC support for servers, client, and clusters is now GA Last year, we introduced the preview for Windows Admin Center to manage WDAC-enforced servers, client machines, and clusters. After hearing your feedback, and making major improvements, we are excited to say that this support is now generally available! With thousands of new malicious files created every day, traditional methods like antivirus solutions - signature-based detection to fight against malware – only provide one aspect of your defense in depth strategy. In most organizations, information is the most valuable asset. Ensuring that only approved users have access to that information is imperative. However, when a user runs a process, that process typically has the same level of access to data that the user has. As a result, sensitive information could easily be deleted or transmitted out of the organization if a user knowingly or unknowingly runs malicious software. Windows Defender application control (WDAC) can help mitigate many security threats by restricting the applications that users are allowed to run and the code that runs in the System Core (kernel). Application control policies can also block unsigned scripts and MSIs, and restrict Windows PowerShell to run in Constrained Language Mode. Learn more about Application Control for Windows. Windows Admin Center now fully supports managing servers and clusters with Constrained Language Mode enabled (with the right WDAC policy in place). The experience in Windows Admin Center is no different – simply add your server, client, or cluster and use Windows Admin Center as you always do. Learn more. Gateway registration and Azure sign-in improvements In this release, we have improved a few scenarios with Windows Admin Center registration and Azure sign-in experiences, including fixing an issue with stale registration and sign-in data in the Azure Stack HCI registration workflow. We also added a longer delay between the creation of a new application ID and logging in to Azure to reliably finish gateway registration. Tool updates Improved Hyper-V virtual machine management The Hyper-V virtual machine management tool has improved multiple experiences. Our vision is make Hyper-V tool your go to tool to manage your virtual machines! A few highlights include: Ability to move virtual machine between clusters Ability to move virtual machine with storage Ability to download your VM list with the corresponding properties as a CSV file, so you are able to open and do data analysis to understand the usage of your VMs Ability to pop out a VM’s RDP session, so you don’t have to switch context and leave your current view Configure your un-clustered VM running on a cluster to be highly available Check it, and let us know what you would like to see next on the virtual machine tool! File editor We have heard that convenient file access has been a challenge, especially with .txt or .log files. You are now able to modify these files right here in Windows Admin Center and save your changes without ever having to leave this tool or switch context. Editable files will show up as blue, click-able items in your file directory under the “Files & file sharing” tool. Azure Arc status Azure Arc-enabled servers lets you manage Windows and Linux physical servers and virtual machines hosted outside of Azure, using the Azure control plane. Windows Admin Center provides an Azure Arc for servers onboarding experience through our Azure hybrid center. In this update, you do not have to navigate to the Azure Arc for Servers blade in your server settings to view the status of your Azure Arc-enabled machine. There is now a new field on the Overview page that displays your Azure Arc agent status. Context menu integration Accessibility is a constant priority for Windows Admin Center. We know that some users prefer to use the keyboard instead of the mouse to navigate Windows Admin Center, and that keyboard navigation can occasionally be inconvenient. That is why we’ve added a context menu. The context menu shows the extension actions by pressing the keyboard shortcut Shift+F11. From here, you can quickly perform extension actions and reduce the amount of time you must spend navigating the webpage. While this feature is not available for every extension just yet, we have expanded the context menu integration to cover more tools in this release, including: Local users & groups Certificates Networks Devices Firewall Apps & features Registry We will continue to roll out the context menu feature to additional extensions to ensure users who prefer keyboard navigation can get their tasks done efficiently. Cluster management Cluster-aware event viewer Recently we updated our Events tool for servers with an improved interface to better serve your management needs. We are continuing to invest in the ability to view and analyze the events from your systems in this release with the preview of the Events tool for clusters! The cluster-aware version of the Events tool collects data from all nodes within a cluster and presents it in a unified interface. You can create, modify workspaces, save, and delete them, and open existing workspaces to pick up right where you left off. In addition to the filters that are present in the Events tool for server, including event sources, levels, and IDs, we have also added a filter to the cluster-aware version of this tool to filter by node in the cluster. We have also improved the tool to better handle larger volumes of data and load results quickly. This interface provides a consistent experience whether you are managing single servers or multi-node clusters. Azure Stack HCI Cluster Updates tool The current updates tool in Windows Admin Center based on Cluster-aware updates (CAU) will continue to be supported for clusters running 22H2 or older. There are several quality fixes to the existing CAU-based updates flow in Windows Admin Center to improve the reliability of this experience. We have now added support to upgrade single node 22H2 Azure Stack HCI clusters as part of this experience. Move a volume to another server The Volumes tool in Cluster Manager now contains a ‘Move’ button. This enables you to move a volume to another server in the cluster. You can verify which server currently owns the volume by adding the ‘Server’ column to the Inventory table. Learn more. Storage Spaces and pools settings The Storage Spaces and pools Settings section in Cluster Manager now contains 3 new settings: Status, Health status and Capacity alert threshold. The Status and Health status values can help alert the user of unexpected storage or S2D issues. The Capacity alert threshold dropdown lets the user select a threshold between 50% and 100%. When the storage pool fills to this threshold, a notification will be displayed on the Dashboard. Bringing consistency to deploying Azure hybrid services on Azure Stack HCI Many of the Azure hybrid services offered in Windows Admin Center on-premises are not yet compatible with the Azure Stack HCI operating system. To represent the Azure Stack HCI management experience more accurately, we have made the following changes: We have hidden all Azure hybrid services for server connections except Azure Arc for Servers and Microsoft Defender for Cloud Azure Monitor and Azure Site Recovery have been hidden for Azure Stack HCI cluster connections When you begin the onboarding flow for Azure Arc with an Azure Stack HCI node that is clustered, you will receive a warning explaining that the Azure Arc onboarding should be completed at the cluster level instead of the node level Windows Admin Center in Azure Windows Admin Center in Azure continuously releases new updates monthly, providing you with the latest and greatest that Windows Admin Center has to offer. Check out our release history to see the new features we released every month. AAD Authentication for Azure Stack HCI Last year, we introduced Azure AD authentication for Windows Admin Center in Azure for Windows Server machines, but Azure Stack HCI clusters still required you to enter your local administrator credentials for management. We are happy to announce that Azure AD authentication is now supported for Azure Stack HCI clusters too! As long as your Azure AD identity is part of the “Windows Admin Center Administrator Login” role, that’s all you need to start managing your cluster using Windows Admin Center in Azure to manage your cluster. You can: Reduce reliance on local administrator accounts Get SSO to your Azure Stack HCI cluster Use all the protection and security with Azure AD Conditional Access and Identity Protection that are enforced for the Azure Portal (multifactor authentication, compliant device, user/sign-in risk, and others) to protect your Azure Stack HCI cluster Use Azure RBAC to grant the appropriate access to clusters based on need and remove it when it’s no longer needed Partner Ecosystem Windows Admin Center was built to be an extensible platform, and we value the contributions of our partners to the Windows Admin Center ecosystem. Several partners, including DataON, Lenovo, and Dell, have updated their extensions since the start of the calendar year. SDK improvements This release includes improvements and bug fixes that will elevate the developer experience and provide partners with a seamless workflow to develop new extensions. Here are the highlights: SDK updates to address some blocking wac-cli bugs Extension template fix to modify gulp processes Updated extension development documentation Lenovo XClarity Integrator The Lenovo XClarity Integrator extension has been updated to version 4.3.7. Here is what has changed since our last release: Support for XClarity Administrator 4.0.0 Support for the following new hardware: Lenovo ThinkSystem SR630 V3 (7D72, 7D73, 7D74) Lenovo ThinkSystem SR650 V3 (7D75, 7D76, 7D77) Lenovo ThinkSystem SR645 V3 (7D9C, 7D9D) Lenovo ThinkSystem SR665 V3 (7D9A, 7D9B) [*]Support for ThinkAgile MX Best Recipe versions 2301 and 2303 [*]Refinement to the account requirements for system update, processor core enablement and call home features An Active Directory domain account that’s also a member of the local Administrators group is required for cluster nodes An Active Directory domain account that's also a member of the local Administrators group, or the built-in administrator is required for non-clustered servers [*]Enhancements to the cluster consistency function for supporting HBA adapter (ThinkSystem 4350) and NIC adapter (Intel E810) and optimizing the HBA and NIC adapters probing logic [*]Fixed the issue where extension failed to test AD users for system update functions and call home function [*]Fixed the issue where extension failed to download system update packages. [*]Added workaround for the system update packages in which the ThinkAgile MX system machine types are missing from the metafiles [*]Added workaround for the Broadcom network adapters with static IP address which sometimes becomes duplicated after the driver update is installed Dell OpenManage Integration The Dell OpenManage extension has been updated to version 4.3.7. Here are the major changes that this version has: Onboarding Dell SCP policies to Azure Arc for PowerEdge server: Support for Dell Server Configuration Policy (SCP) onboarding to Azure Arc for monitoring server configuration Configuration Recommendation for PowerEdge server: Enables support for configuration compliance and remediation options for 14G and above PowerEdge servers based on Dell Server Configuration Profile policies Single Node HCI cluster feature enablement: Ability to validate and remediate (with manual reboot) single node HCI cluster using HCP policies to ensure that the cluster shows better resiliency and performance, and remains compliant with Dell recommended configurations throughout the life cycle of the HCI cluster. Support for Dell HCI Configuration Policy onboarding to Azure Arc for monitoring cluster configuration Auto-handling BitLocker for server: Enabled support for automatic suspension of BitLocker and resuming back as part of any operation which involves rebooting of the AX node from Dell OpenManage extension running in Azure Stack HCI 22H2 and above Warranty information for server and cluster nodes: Provides information on overall warranty status and entitlements of PowerEdge servers and AX nodes Additional partner extension updates QLogic Fibre Channel QConvergeConsole Extension by Marvell version 2.2.0 - Added Port level driver and firmware statistics display support, target link statistic display support, and “Link Uncorrectable FEC Count” display support in Port and Target USCM statistics DataON MUST version 4.1.0 - Added CAU update parameters to fix updating bugs as well as registration email and alert email checking logic DataON MUST Pro version 3.2.0 - Added CAU update parameters to fix updating bugs as well as registration email and alert email checking logic Download today! We hope you enjoy this latest update of Windows Admin Center, the various new functionality in preview, and all the extensions now available. Learn more and download today! As always, thanks for your ongoing support, adoption, and feedback. Your contributions through user feedback continue to be vital and valuable to us, helping us prioritize and sequence our investments. Windows Admin Center is continuously evolving and growing as a tool and a platform, and we are beyond thrilled to have you part of our journey. To skill up on Windows Admin Center and Windows Server 2022, check out our Windows Server Hybrid Administrator Certification and other featured Learn courses. Thank you, Windows Admin Center Team (@servermgmt) Continue reading...
-
This is another blog post on a topic that I constantly see on forums such as Reddit, StackOverflow, and Docker forum – what is the deal with Docker Desktop on Windows versus Windows Server? I decided to write this blog post so it’s clear why and what works on a Windows client or Windows Server when it comes to Docker and Docker Desktop. Docker Desktop, Windows and Linux containers, and container runtimes Most likely, you are familiar with Docker Desktop. Docker Desktop is a one-click-install tool focused on developers writing applications for containers and micro-services. It provides a nice, friendly GUI and CLI to manage your container images and containers running locally. If you are running containers on a Windows client machine, Docker Desktop is likely the preferred option to run containers. You can run both Windows and Linux containers, albeit, not at the same time. Docker Desktop gives you the option to switch between Linux containers – which use WSL 2 in the background – and Windows containers – which use the underlying containers feature on Windows. Docker Desktop is built from an open-source project called Moby. It is important to understand that Docker Desktop is a commercial product from the Docker company that follows the updates to the open-source Moby project. The reason this is important is because under the hood, the Moby project calls into containerd – a container runtime that has been accepted as the default container runtime for running containers on Kubernetes. That is true for Linux containers, but not yet for Windows containers. When you switch to Linux containers on Docker Desktop, it uses WSL 2 to run a Linux utility VM that runs your containers via containerd. When you switch to Windows containers, is calls into the Windows APIs via the Host Compute Service (HCS). Updates to Moby are underway to move it to containerd. At the end of the day, you operate either Linux or Windows containers via Docker Desktop on Windows 10 or 11 pretty much the same way – either via the GUI or CLI. Docker and Windows Server On Windows Server, the story is different. First, Docker Desktop is not available for Windows Server. This is because, as mentioned, Docker Desktop is focused on development and testing of containerized applications while Windows Server is supposed to run production scenarios. So, the question is: How do I run containers on Windows Server? Today, there are three options to run containers on Windows Server: Moby/DockerCE Docker Community Edition (CE) provides a standard runtime environment for containers with a common API and CLI. It is managed by the open-source community as part of the Moby Project. Mirantis Container Runtime The Mirantis Container Runtime, formally known as Docker EE (Enterprise Edition), provides the same functionality as Docker CE plus extra features built specifically for enterprise deployments. Keep in mind that the Mirantis Container Runtime is a paid product provided by Mirantis, but different than Docker Desktop, specifically designed for production scenarios. Containerd Containerd, as mentioned, is an industry-standard container runtime. Since it is available as a daemon for Linux and Windows, it can manage the complete container lifecycle. However, containerd only provides the APIs for the container management. You need a CLI on top of it to be able to interact with it. The most common ones are critcl and nerdctl. How to install Moby or containerd on Windows Server For both Moby and containerd, Microsoft provides scripts that download and deploy the necessary components for you to get your environment ready to go. If you have familiarity with Docker and just want to run Windows containers on it, you should go with the Moby project: Invoke-WebRequest -UseBasicParsing "https://raw.githubusercontent.com/microsoft/Windows-Containers/Main/helpful_tools/Install-DockerCE/install-docker-ce.ps1" -o install-docker-ce.ps1 .\install-docker-ce.ps1 If you want to deploy a Windows node for use with Kubernetes, on which you’ll operate the environment via the Kubernetes APIs, you should try containerd: Invoke-WebRequest -UseBasicParsing "https://raw.githubusercontent.com/microsoft/Windows-Containers/Main/helpful_tools/Install-ContainerdRuntime/install-containerd-runtime.ps1" -o install-containerd-runtime.ps1 .\install-containerd-runtime.ps1 More information on these options can be found on our documentation page. Conclusion Docker Desktop is the leading tool for running containers, both Windows and Linux. You can run Docker Desktop on Windows 10 and 11, but on Windows Server, you need to choose either Docker CE/Moby, Mirantis Container Runtime, or Containerd with a CLI tool and Microsoft offers scripts to install Moby or Containerd on Windows Server. I hope this was helpful to you and clarifies what to run on Windows client or Server. Let us know what you think in the comments section below! Continue reading...
-
Happy Friday, MTC! Wonder what you may have missed this week? Let's talk about it! MTC Moments of the Week On Wednesday, we had a special collab edition of Tech Community Live! Experts from across four Microsoft content collaboration products - SharePoint, OneDrive, Lists, and Stream – went live for an AMA video stream to talk about their recent innovations and future roadmaps, as well as answer questions. Huge kudos to all the experts, their teams, and community personnel involved on this highly engaging event, including (but not limited to) Mark Kashman, Dave Cohen (US), Cathy Dew, Suyog Gadgil, Miceile Barrett, Paul Diamond , Gaia Carini, Carter Green, Vishal Lodha, Miceile Barrett, Lincoln DeMaris, Harini Saladi, Marc Mroz, Daniel Escapa, Paul Diamond, Ignacio Davila, Owen Paulus, and Emily Perina! We also had our monthly Windows Office Hours this week, where the team hops on to answer any burning user questions about keeping devices up to date effectively with product experts representing Windows, Microsoft Intune, Configuration Manager, Windows 365, Windows Autopilot, security, public sector, FastTrack, and more. Thank you to our panelists Jason Sandys, Joe Lurie, Jay Simmons, Roy Barton, Aria Carley, and Steve Thomas for joining us! Keep an eye out for the next Office Hours session to be announced soon! Over on the Blogs, the Microsoft Viva team has announce that as of June 14, Viva Pulse is available for public preview! Viva Pulse is a lightweight feedback solution designed to empower managers and team leaders to get real-time insights into how their teams are doing. To learn more about how Viva Pulse works and how to try it out for yourself, check out this blog post by @TranissaCreme_PMM! And last, but certainly not least, our MTC Member of the Week spotlight this week goes to @David Mehr! Based in Switzerland, David is an M365 Apps & Services MVP who is about to celebrate 7 years as a member of the MTC. We appreciate all you do for Microsoft and the MTC, David! Upcoming Events - Mark Your Calendars! June 20, 2023, 06:30 AM - 07:30 AM (PDT) - Viva Goals - From Theory to Results: How to Implement OKRs Successfully in Your Organization June 21, 2023, 08:00 AM - 09:00 AM (PDT) - Windows 365 AMA June 22, 2023, 07:30 AM - 11:30 AM (PDT) – Tech Community Live: Microsoft Intune June 22, 2023, 08:00 AM - 09:00 AM (PDT) - Introducing Microsoft 365 Copilot: The AI-Powered Future of Work June 27, 2023, 08:00 AM - 12:00 PM (PDT) - Microsoft Entra Tech Accelerator June 28, 2023, 08:00 AM - 08:30 AM (PDT) - What’s next in end user experiences for Windows 365 June 28, 2023, 09:00 AM - 10:00 AM (PDT) - Microsoft Teams AMA ----- For today’s fun fact… On this day in 1911, IBM was founded as the Computing-Tabulating-Recording Company in Endicott, New York, making it one of the world’s oldest technology companies! And with that, have a great weekend, everyone! Continue reading...
-
Robust security means evolving from simply maintaining protection to being resilient against current and evolving threats. Cyber resilience is an organizational effort that demands accountability from everyone. Organizations need an integrated approach—with security built into every layer from chip-to-cloud—to ensure people and data are protected wherever they work. Microsoft has designed Surface devices to minimize the risk of threats against firmware, operating systems, and cloud applications. With Zero Trust built in from the ground up, this means security and IT decision-makers can feel confident in investing resources in strategies and technologies to prevent attacks in the future rather than constantly defending against the onslaught of attacks aimed at them today. Old devices can’t protect against new threats Microsoft Surface devices are designed to facilitate basic security hygiene measures with every layer maintained by Microsoft, from the firmware to the operating system to the cloud. Surface devices, Windows 11, and Microsoft 3651 help achieve organizational resilience with a Zero Trust approach to security and risk management that doesn’t sacrifice innovation or productivity. Companies that own Surface can experience up to 34% fewer security incidents, reducing time spent on security incident response.2 Surface device users also experience up to 20% fewer security breaches.3 Remote management made simple and secure Surface Management Portal is built into Microsoft Intune1, a cloud-based endpoint management solution designed to address the challenges of managing and configuring users, apps, and devices at scale. Microsoft Intune handles mobile application management (MAM) and mobile device management (MDM). Windows Update manages roll-out and update of firmware, software, and drivers. End-to-end protection ensures that only approved content is installed. The ability to manage device security remotely can mean huge time savings for your IT team, reducing the possibility of firmware or ransomware attacks and remediating problems before they get too far. Working alongside Intune, Windows Autopilot saves more time by streamlining secure remote deployment and preconfiguring new devices with the required security settings and policies. Security that’s built into the hardware Our security approach begins with hardware. Surface protects data through encryption as the device boots. A Trusted Platform Module 2.0 (TPM 2.0) acts as a secure vault for storing passwords, PINs, and certificates, protecting hardware from tampering, and restricting access to authorized individuals. At every stage of the boot cycle, firmware code is inspected for authenticity to ensure the system doesn't execute any malicious code. At startup, password-less, secure sign-in with Windows Hello for Business offers the highest level of biometric security with infrared camera sensors to enhance facial recognition. Biometric sign-in is the most difficult to replicate, ensuring only authorized users can access the device. We design many Surface devices with removable SSDs4 to provide an extra layer of protection for sensitive data stored on the device. Firmware that’s locked down Surface devices proactively block threats by eliminating a key external access point to firmware through the Unified Extensible Firmware Interface (UEFI). The Microsoft-built UEFI is managed through Microsoft Intune1admin center. With no reliance on third-party source code, risk at the firmware level is minimized and access that hackers could eventually exploit is eliminated. The Microsoft UEFI and Device Firmware Configuration Interface (DFCI) allows for more granular control of firmware through Microsoft Intune. DFCI reduces the attack surface by disabling unnecessary hardware components and removes dependency on the local UEFI (BIOS) password. DFCI provides the ability to lock down boot options to prevent users from booting into another OS, while security updates running in the background provide ongoing, up-to-date protection against the latest threats. Security out of the box with Windows 11 Surface devices with Windows 11 include a new set of hardware security features enabled right out of the box. These features are designed to build a foundation even stronger and more resilient to attacks: virtualization-based security (VBS) and Hypervisor-enforced Code Integrity (HVCI), also known as memory integrity. These work in tandem to provide better protection against common and sophisticated malware. VBS performs sensitive security operations in an isolated environment by checking code executions before they start, preventing malware from making its way to the system memory. If a threat gains access to system resources, the HVCI can limit and contain the malware's effects. We ship Surface devices with Windows 11 from the factory with security features enabled. That helps security and business leaders normalize security-centric behaviors within your organization, satisfying the need for accountability across your teams. Even before signing in with a variety of biometric options to avoid passwords and PINs, Secure Boot helps ensure firmware is as genuine as it was when it left the factory. Together, Secure Boot and Trusted Boot prevent malware and corrupted components from loading during startup. After start-up, BitLocker encryption helps render data inaccessible even on lost, stolen, or inappropriately decommissioned devices. Want to learn more about how Surface, Windows 11, and Microsoft 365 work together to form an integrated, cyber resilient solution designed by Microsoft? Download the e-book “Choose wisely: How device choice can make or break your cyber resilience plan.” References 1. Software license required for some features. Sold separately. 2. A Business Value White Paper, commissioned by Microsoft September 2022 | Doc. #US49453722 IDC Research Study conducted from surveys and interviews between December 2021–February 2022. All respondents were IT decision-makers at large organizations (250-5000+ employees) representing organizations from the United States, Australia, India, Spain, France, United Kingdom, New Zealand, and Germany. Cost & Savings findings based on average cost and time estimates provided directly by respondents; actual costs and savings may vary based on your specific Device Mix and deployment. For the detailed study, click here. 3. A Forrester Total Economic Impact™ Study commissioned by Microsoft, Maximizing Your ROI from Microsoft 365 Enterprise with Microsoft Surface, Cost Savings and Business Benefits, July 2020. Results based on a composite organization with a Microsoft 365 Enterprise E5 license and standardized mix of Surface Book 3, and Surface Hub devices set up and configured using Windows Autopilot and onboarded to the Microsoft Defender ATP service. Based on a survey of 143 Global Microsoft 365 powered device users. 4. Customer Replaceable Units (CRUs) are components available for purchase through your Surface Commercial Authorized Device Reseller. Components can be replaced on-site by a skilled technician following Microsoft's Service Guide. Opening and/or repairing your device can present electric shock, fire and personal injury risks and other hazards. Use caution if undertaking do-it-yourself repairs. Device damage caused during repair will not be covered under Microsoft's Hardware Warranty or protection plans. Components will be available shortly after initial launch; timing of availability varies by component and market. Continue reading...
-
Microsoft Defender for Cloud Monthly news June 2023 Edition [attachment=42115:name] This is our monthly "What's new" blog post, summarizing product updates and various new assets we released over the past month. In this edition, we are looking at all the goodness from May 2023. Legend: [attachment=42116:name] Product videos [attachment=42117:name] Webcasts (recordings) [attachment=42118:name] Docs on Microsoft [attachment=42119:name] Blogs on Microsoft [attachment=42120:name] GitHub [attachment=42121:name] External content [attachment=42122:name] Product improvements [attachment=42123:name] Announcements Microsoft Defender for Cloud [attachment=42124:name] Watch new episodes of the Defender for Cloud in the Field show to learn about API Security with Defender for APIs, how to create custom recommendations for AWS and GCP, and new data-aware security posture capabilities in Defender for Cloud. [attachment=42125:name] We're announcing the release of Vulnerability Assessment for Linux images in Azure container registries powered by Microsoft Defender Vulnerability Management (MDVM) in Defender CSPM. This release includes daily scanning of images. Findings used in the Security Explorer and attack paths rely on MDVM Vulnerability Assessment instead of the Qualys scanner. [attachment=42126:name] We're seeking your feedback on Defender for APIs. In this form you will be able to share feedback with the product team about your experience with the Defender for APIs capabilities. The survey will take approximately 6 minutes to complete. Thank you! [attachment=42127:name] The Defender for Cloud Onboarding Workbook V2 is the latest version of this workbook that was originally published August 2022. Please review this blog post to learn what has changed. This workbook helps you track which Azure subscriptions under your Tenant are onboarded with Defender for Cloud. Also, it lists the resources deployed into these subscriptions that can be protected by the Defender for Cloud workload protection plans, and it checks if any required agents are missing for the workload protection. [attachment=42128:name] Microsoft Defender for APIs, a new plan in Defender for Cloud, offers full lifecycle protection, detection, and response coverage for APIs published in Azure API Management. One of the main capabilities is the ability to detect exploits of the OWASP API Top 10 vulnerabilities through runtime observations of anomalies using machine learning-based and rule-based detections. This blog will outline the steps for simulating an action that will trigger an alert for one of your API endpoints through Defender for APIs. [attachment=42129:name] Microsoft Defender for Cloud is a Cloud Native Application Protection Platform (CNAPP) that offers crucial insights and protective measures through its Attack Path risk analysis feature. A frequent requirement from customers is the ability to receive notifications whenever new attack paths are detected. This article presents an automated solution utilizing Azure Logic Apps to address this need. By deploying a custom Logic App using an Azure Resource Manager (ARM) template, organizations can establish a streamlined notification system for newly reported attack paths by Microsoft Defender for Cloud. This solution guarantees that security teams receive prompt alerts, empowering them to promptly respond and safeguard their cloud resources efficiently. [attachment=42130:name] Defender for DevOps Code and IaC has expanded its recommendation coverage in Microsoft Defender for Cloud to include Azure DevOps security findings for the following two recommendations: Code repositories should have code scanning findings resolvedCode repositories should have infrastructure as code scanning findings resolved Previously, coverage for Azure DevOps security scanning only included the secrets recommendation. [attachment=42131:name] Recently, we’ve added agentless container security posture capabilities in the Defender Cloud Security Posture Management (CSPM) plan. Previously, to discover parts of the Kubernetes estate, the Defender Profile, deployed as part of the Defender for Containers plan, needed to be deployed on each cluster. Defender CSPM now collects inventory of the Kubernetes cluster, without the use of an agent and without dependency on Defender for Containers. These insights are included as part of the Cloud Security Explorer and Attack Path Analysis. However, security posture management is not enough to get full visibility into potential threats and security risks. Defender for Containers and its’ agent-based capabilities are significant in detecting near real time threats on the cluster. In this blog, we highlight how Defender CSPM and Defender for Containers can be used to help organizations secure their containerized environments in the cloud. [attachment=42132:name] Agentless scanning for VMs now supports processing of instances with encrypted disks in AWS, using both CMK and PMK. This extended support increases coverage and visibility over your cloud estate without impacting your running workloads. Support for encrypted disks maintains the same zero impact method on running instances. For new customers enabling agentless scanning in AWS - encrypted disks coverage is built in and supported by default.For existing customers that already have an AWS connector with agentless scanning enabled, you'll need to reapply the CloudFormation stack to your onboarded AWS accounts to update and add the new permissions that are required to process encrypted disks. The updated CloudFormation template includes new assignments that allow Defender for Cloud to process encrypted disks. [attachment=42133:name] Defender for DevOps has expanded its Pull Request (PR) annotation coverage in Azure DevOps to include Infrastructure as Code (IaC) misconfigurations that are detected in ARM and Bicep templates. Developers can now see annotations for IaC misconfigurations directly in their PRs. Developers can also remediate critical security issues before the infrastructure is provisioned into cloud workloads. To simplify remediation, developers are provided with a severity level, misconfiguration description, and remediation instructions within each annotation. [attachment=42134:name] To help you manage your AWS CloudTrail costs and compliance needs, you can now select which AWS regions to scan when you add or edit a cloud connector. You can now scan selected specific AWS regions or all available regions (default), when you onboard your AWS accounts to Defender for Cloud. [attachment=42135:name] Microsoft Defender Vulnerability Management (MDVM) is now enabled as the default, built-in solution for all subscriptions protected by Defender for Servers that don't already have a VA solution selected. If a subscription has a VA solution enabled on any of its VMs, no changes are made and MDVM won't be enabled by default on the remaining VMs in that subscription. You can choose to enable a VA solution on the remaining VMs on your subscriptions. [attachment=42136:name] In today’s application development landscape, organizations are widely adopting Infrastructure-as-Code (IaC) technology to automate the provisioning and management of resources to support cloud native applications and workloads across their multi-cloud environments. By utilizing IaC, organizations can manage infrastructures with the same versioning, testing, and automation processes that they use for their application code, leading to more reliable, efficient, and secure operations. In this blog, you will learn how to identify and remediate critical misconfigurations in your Infrastructure-as-Code templates with Defender for DevOps. [attachment=42137:name] Have you ever found yourself in a situation where you wanted to determine which AWS resources are missing a tag? You can accomplish this use case using custom recommendations for AWS workloads in Defender for Cloud. The following steps solve the problem of creating a custom recommendation that identifies which Amazon RDS instances are missing a tag, but they can be applied to other use cases too. To learn more about this feature, please check out this article. [attachment=42138:name] Securing container images is essential to ensure data protection, reduce the risk of data breaches, and improve regulatory compliance. By understanding potential vulnerabilities, businesses can create a robust security strategy to protect their containerized applications, thereby safeguarding their sensitive data, reputation, and customer trust. In this blog we discuss how Microsoft Defender for Cloud Security Posture Management (DCSPM) can help you identify and remediate vulnerabilities in your container image repositories. [attachment=42139:name] Discover how other organizations successfully use Microsoft Defender for Cloud to protect their cloud workloads. This month we are featuring Newington College – an Australian primary and secondary school – that uses Microsoft security solutions, including Defender for Cloud, to secure their environment. [attachment=42140:name] Join our experts in the upcoming webinars to learn what we are doing to secure your workloads running in Azure and other clouds. Note: If you want to stay current with Defender for Cloud and receive updates in your inbox, please consider subscribing to our monthly newsletter: Microsoft Forms Continue reading...
-
Are you following Zero Trust principles of verifying explicitly, using least-privileged access, and assuming breach with respect to your apps? Browse the assortment of Windows security solutions for apps and add layers of security to what you're currently using. Season your choices with some practical walkthroughs of app building, advanced endpoint management, and code integrity policies for Windows Defender Application Control. Time to learn: 111 minutes [attachment=41898:name]WATCH Microsoft Defender Application Control Application control uses a Zero Trust approach to provide defense beyond traditional antivirus solutions. See how App Control works, as well as how you can enable and manage it through an allow-list. This creates a circle of trusted applications, while blocking the rest. (5 mins) App Control + WDAC + Smart App Control + Windows 11 + LOB + Circle of Trust + Block Rules + Reputation + Intune + Policies [attachment=41899:name]READ Microsoft Defender Application Guard What is Application Guard and how does it work? Learn about this hardware isolation approach and the types of devices that should use it. Specifically, read about enterprise desktops, enterprise mobile laptops, bring-your-own-device (BYOD) mobile laptops, and personal devices. (3 mins) Application Guard + Hyper-V + Kernel + Edge + Office + Intune + ConfigMgr [attachment=41900:name]READ AppLocker After browsing the capabilities of AppLocker, learn when to use it and how to install it. Read additional considerations for virtualization and security, as well as guidance to create application control policies setting by setting. Additional guides are linked for use in different scenarios. (8 mins) App Control + AppLocker + WDAC + DLL + AD RMS + ACL + ActiveX + Group Policy + DoS + Virtualization + Security [attachment=41901:name]READ Windows Sandbox If you need to safely run applications in isolation, use this lightweight desktop environment. Learn all about Windows Sandbox, prerequisites for running it, installation instructions, and usage recommendations. (3 mins) Virtualization + GPU + ARM64 + AMD64 + BIOS +Pro + Enterprise + Education + PowerShell [attachment=41902:name]READ Configure S/MIME for Windows Secure/Multipurpose Internet Mail Extensions (S/MIME) helps you to secure email messages. First, familiarize yourself with message encryption, digital signatures, and prerequisites. Then follow the steps to choose S/MIME settings, encrypt or sign individual messages, read signed or encrypted messages, and finally install certificates from a received message. (3 mins) Email + Encryption + Signatures + EAS + Office 365 + PFX + PIN + Certificate [attachment=41903:name]READ Microsoft Defender SmartScreen overview Apply another defense layer to protect against phishing, malware, and downloading of potentially malicious files. Consider the benefits and the mechanism of Microsoft Defender SmartScreen. Then follow the steps to submit files for review. (4 mins) Phishing + Malware + URL + Download + Group Policy + Intune + Edge + PUA [attachment=41904:name]READ What is Smart App Control? Consider a new Windows 11 protection to add on top of your other security software: Smart App Control. Find common questions and answers to what it is, how it works, and all you need to know to configure Smart App Control for your context. (6 mins) Apps + Windows 11 + Zero Trust + Windows Security + Diagnostic Data + Antivirus + Developer + Certificate [attachment=41905:name]READ How Microsoft identifies malware and potentially unwanted applications Potentially unwanted applications (PUA) represent an evolving security risk. See how Microsoft distinguishes between unknown/unrecognized software and malware. Specifically, learn about 14 different types of malicious software. Furthermore, see how unwanted software limits your control, even if it's not malware. (10 mins) M365 Defender + PUA + Malware + Exploit + Trojan + Control + Installation + Removal + Advertisements + Edge + Antivirus [attachment=41906:name]WATCH Creating secure identities for apps using the Microsoft identity platform If you're an app developer, learn how to manage identities in your apps. Attend this recorded session to master the Microsoft identity platform and secure your apps through compliant authentication and permissions. (31 mins) Developer + Identities + Authentication + Authorization + MS Identity Platform + Permissions + Compliance + Open-Source + AAD [attachment=41907:name]READ Learn about using Endpoint Privilege Management with Microsoft Intune What if you don't have administrator rights? Complete tasks that require elevated privileges with Microsoft Intune Endpoint Privilege Management. Learn about the prerequisites, getting started, important capabilities, and role-based access controls. (7 mins) Intune + EPM + Zero Trust + Windows 11 + Windows 10 + AAD + HAADJ + Policies + RBAC [attachment=41908:name]WATCH Introducing advanced endpoint management solutions for Microsoft Intune Learn how Microsoft Intune's new advanced management suite takes device management to the next level. Take advantage of reduced total cost of ownership, Zero-Trust security trajectory, and help with ever-growing challenges in IT. (30 mins) Endpoints + Intune + Hybrid + On-Prem + Apps + M365 + VPN + Certificates + Remote Help + Microsoft Tunnel + MAM [attachment=41909:name]EXPERIENCE Microsoft WDAC policy wizard Download the Windows Defender Application Control (WDAC) policy wizard and start building and deploying code integrity policies in PowerShell. (1 mins) WDAC + CI + Policies + PowerShell Got some spare time to learn about how Windows Defender Application Control has been evolving? Watch Balancing security and flexibility when implementing Windows Defender Application Control (WDAC) (time to watch: 19 mins). We've been catering weekly skilling snacks for four months now! What other topics would you like us to add to Windows skilling snacks: bite-sized learning for IT pros? Continue the conversation. Find best practices. Bookmark the Windows Tech Community and follow us @MSWindowsITPro on Twitter. Looking for support? Visit Windows on Microsoft Q&A. Continue reading...
-

Introducing the Microsoft Mac Admins community
AWS posted a topic in Microsoft Support & Discussions
By Arnab Biswas - Sr. Product Manager - Microsoft Intune Microsoft is excited to officially announce the launch of Microsoft Mac Admins, a new online community for IT professionals who are passionate and knowledgeable about using Microsoft products on Apple Mac devices in the enterprise. This community is a place for Mac admins working with Microsoft 365 or Intune Mac management to connect with other users, share experiences and best practices, learn from experts and peers, get help with common issues, and be inspired by the latest innovations. Whether you’re new to using Microsoft 365 for Macs or a seasoned pro, you’ll find valuable resources and insights in this community. We were inspired to create this community based on feedback from many organizations who have adopted Microsoft 365 products, including Microsoft Intune, to manage Macs in the enterprise. Mac management has been a focus for Microsoft 365 that is demonstrated in the macOS capabilities offered and we continue to see phenomenal growth and customer-interest in macOS management. So, we wanted to provide a platform where organizations, and specifically the IT community, can showcase their achievements, exchange tips and tricks, and collaborate with other Microsoft 365 or Intune administrators around the world. The community is open to anyone who has a Microsoft 365 account and wants to join the conversation on Microsoft Viva Engage. You can ask questions, offer solutions, provide feedback, and participate in discussions on various topics related to your Microsoft 365 experience on Macs. You can also browse through the existing posts and comments to discover solutions and advice that might help you with your own challenges. The Microsoft Mac Admins community is moderated by members from the Microsoft Intune product team. Note that this community is not a substitute for official product support from Microsoft. If you need technical assistance with a Microsoft product, please contact Microsoft Support. The community is meant to complement the existing support resources by providing a peer-to-peer platform for informal discussions and knowledge sharing. The community is meant to complement the existing support resources by providing a peer-to-peer platform for informal discussions and knowledge sharing. We hope that you’ll find the Microsoft Mac Admins community useful for your Microsoft 365 journey. To join the community, simply email MacAdmins@microsoft.com and provide a Microsoft 365 email address. Community members can access the Microsoft Mac Admins page on Viva Engage at Yammer. Did you miss the recent Intune news regarding macOS management? Read the latest in these relevant articles: 10 ways Microsoft Intune improves Apple device management What’s new in Microsoft Intune: 2304 (April) edition 2301 (January) edition 2208 (August 2022) edition 2206 (June 2022) edition We can't wait to welcome you to our community and hope to see you there! Let us know if you have any questions by leaving a comment below or reaching out to us on Twitter @IntuneSuppTeam. Continue reading... -
In the past year, I have been working on improving our documentation and learning content for Windows containers – in addition to the blog posts you have seen here. Today, I wanted to spend some time on the new content available for Windows containers on Microsoft Learn: New learning path: Deploy, manage, and monitor Windows containers on Azure Kubernetes Service Learning paths are collections of Learn module designed to provide a guided learning experience on a specific topic. This new learning path is the first one dedicated to Windows containers. The path is composed of the following modules: Introduction to Docker containers Run containers on Windows Server Build a containerized web application with Docker Introduction to Kubernetes Introduction to Azure Kubernetes Service Manage Azure Kubernetes Service on Azure Stack HCI Deploy a containerized application on Azure Kubernetes Service The above content can provide a learning experience for someone new to containers and Kubernetes to a place where they feel comfortable getting started, and get a good understanding of how the platform works. The modules include Windows containers and also the platform components so the learner gain a comprehensive understanding of how everything fits together. Note that we’ll continue to update the existing modules to include more Windows container goodness. New learning module: Troubleshooting Windows Containers This new module is fresh off the oven, and focus on post-deployment. While troubleshooting content is usually regarded as Level 300-400, this module is an entry level guidance on how troubleshooting applications and environments with Windows containers works. It assumes a reader knows how to troubleshoot Windows applications on VMs and takes the learner into the journey of understanding how troubleshooting Windows apps on Windows containers, Docker, and Kubernetes works. It also gives the reader the pointers to use native Azure services to troubleshoot Windows on Azure Kubernetes Service. The module is composed of the following units: Introduction Understanding the Windows container platform Troubleshooting Windows containers on Windows hosts Troubleshooting Windows containers on Docker Troubleshooting Windows containers on Azure Kubernetes Service Troubleshooting Windows containers with Azure Monitor At the end of the module, we have a Knowledge Check that gives you XPs for your Microsoft Learn account. Windows containers documentation Overall, the Windows containers documentation has been getting updates constantly. In the past year, there are a few things that are worth checking out: Lift and Shift to Windows containers: This is a documentation page dedicated to customers planning their containerization process with Windows containers. If you have a Windows application that you are considering moving to container, this is your one stop shop for technical information. It covers what can and cannot be containerized, what are the considerations for containerization with Windows containers, and much more. What’s new for Windows Server 2022: Containers allow for a much simpler upgrade process, so it’s always good to know what’s new in the latest release of Windows containers. This page covers platform improvements, application compatibility, improved Kubernetes experience, and Windows container tooling. Prep Windows for containers: This is the main page on our documentation, but the reason I put it here is because there has been changes in the past year. Mainly, we now provide a new experience to install Docker CE/Moby, Mirantis Container Runtime, or ContainerD on Windows Server and Windows. Tell us what you’d like to see! This documentation and content effort is based on your feedback. If you’re working with Windows containers and would like to see more learning content, or a new set of documentation, please let us know! You can write to us in the comments below, or on the Windows containers GitHub repo. Continue reading...
-
Introduction Microsoft Defender for Cloud is a Cloud Native Application Protection Platform (CNAPP) that offers crucial insights and protective measures through its Attack Path risk analysis feature. A frequent requirement from customers is the ability to receive notifications whenever new attack paths are detected. This article presents an automated solution utilizing Azure Logic Apps to address this need. By deploying a custom Logic App using an Azure Resource Manager (ARM) template, organizations can establish a streamlined notification system for newly reported attack paths by Microsoft Defender for Cloud. This solution guarantees that security teams receive prompt alerts, empowering them to promptly respond and safeguard their cloud resources efficiently. The Challenge - Timely Notification of New Attack Paths One of the key challenges faced by organizations using Microsoft Defender for Cloud Attack Path analysis is the lack of built-in notification functionality for new attack paths. Attack paths provide crucial information about potential vulnerabilities and the paths that attackers can exploit to infiltrate cloud environments. However, without timely notifications, security teams may not be aware of these new attack paths, leaving their cloud infrastructure exposed to potential threats. Moreover, the data stored within the Azure Resource Graph, where attack path information is collected, does not include timestamps indicating when attack paths were first generated or updated. As a result, organizations lack visibility into the recency of attack path reports, further hindering their ability to prioritize and respond to potential risks effectively. One way to overcome this challenge is to use Azure Logic Apps and custom notifications to provide security teams with real-time updates on new attack paths. By deploying the Logic App using the provided ARM template, organizations can establish a reliable and automated process for receiving notifications whenever Microsoft Defender for Cloud reports new attack paths. This empowers security teams to stay ahead of potential vulnerabilities and take proactive measures to secure their cloud environments effectively. Next, we will delve into the details of the solution, explaining how the Logic App works and the benefits it offers in terms of timely attack path notifications. Attack Path Notification Process Let's walk through the process of how this solution works: Trigger: The Logic App is set to run daily using a recurring trigger. This ensures that Attack Paths are evaluated regularly. Query Attack Paths: The Logic App retrieves Attack Paths data by making an API request to the Azure Resource Graph. It fetches important details such as Attack Path ID, display name, description, and attack path type. Evaluate Attack Paths: The Logic App processes each Attack Path using a loop. For each path, it performs the following steps: Check Existence: The Logic App checks if the Attack Path already exists in the storage account table by making an API request. Update or Insert Entity: If the Attack Path exists, the Logic App updates the LastUpdate timestamp. If it doesn't exist, a new entity is created with the Attack Path details, and the Notified flag is set to "False" to indicate a pending notification. Send Notification: After updating or inserting the entity, the Logic App sends email notification using the Office 365 connector. The notification includes important Attack Path details and a link to view the details in Defender for Cloud. Notification Body: The Logic App constructs the email notification body using HTML formatting, making it visually appealing and informative. Storage Account and Table: It's important to have a storage account and table in place for the Logic App to function correctly. Attack Path entities are stored in this table, enabling the Logic App to query and update them. This is necessary because the Azure Resource Graph data for Attack Paths lacks the specific date and time of their generation and update. Recurring Frequency: It is recommended to set the Logic App's recurrence frequency to once a day. This aligns with the frequency at which Attack Paths are evaluated and reported by Defender for Cloud. Prerequisites For the Logic App to work and utilize its capabilities to send Attack Path notifications, there are several prerequisites that need to be in place. Here are the prerequisites you need to consider: Logic App System Identity: A Logic App System Identity is created when deployed, however there is a need to configure it with the necessary permissions to read all subscriptions. This will enable the Logic App to query for Attack Paths data using the Azure Resource Graph API. The required permissions should include read access to relevant subscriptions where Attack Paths is enabled (Defender for CSPM). Storage Account and Table: Set up a storage account in Azure that will be used to store the Attack Path entities and enable the Logic App to query and update them. Create a table within the storage account to store the Attack Path data. This table will serve as the central repository for storing information related to Attack Paths. MS365 Outlook Account: Ensure that you have an active Microsoft 365 (MS365) Outlook account or an account with access to the Microsoft 365 email service. This account will be used by the Logic App to send email notifications for the new Attack Paths detected. Logic App API Connections: Configure the necessary API connections within the Logic App to access the Storage Account Table and send emails via MS365 Outlook. You will need to provide the appropriate connection details and authenticate the Logic App with the required permissions for accessing the Storage Account and sending emails. Storage Account Shared Storage Key: Obtain the shared storage key for the configured storage account. This key will be used to authenticate the Logic App when accessing the Storage Account Table and perform operations such as querying and updating Attack Path entities. Optional Step: Populating Azure Storage Account and Table with Existing Attack Paths As part of the solution, we provide an optional PowerShell script that enables you to create an Azure Storage Account and Table, and populate it with the existing Attack Paths. This step is particularly useful if you have multiple Attack Paths already present and you prefer not to receive notifications for all of them. By populating the table, you can set the state to zero and ensure that only new Attack Paths detected from that moment onward trigger notifications. To use the provided script, follow these instructions: Ensure that you have the Azure PowerShell modules "Az", “Az.ResourceGraph”, “AzTable” installed. Replace with the ID of the Azure subscription you want to work with. Replace with the Azure Storage Account Name of your choice. After executing the script, you will see a success message indicating that the data has been successfully populated in the specified table. By following these steps and populating the Azure Storage Account and Table with existing Attack Paths, you can ensure that only new Attack Paths trigger notifications while excluding the ones already present in the table. Please note that this step is optional and only necessary if you have existing Attack Paths that you want to exclude from the initial notification process. Verifying and Configuring API Connections Once you have deployed the Logic App, it is essential to verify and configure the API connections used within the Logic App to ensure their proper functioning. The API connections, namely "Azuretables" and "Office365," require attention to establish successful communication with the corresponding services. Follow the steps below to verify and configure the API connections: Access the Azure portal and navigate to the deployed Logic App. Within the Logic App designer, identify the API connections utilized by the Logic App: "Azuretables" and "Office365." Click on each API connection to access its settings and configuration. For the "Azuretables" API connection: a. Confirm that the connection is enabled. b. Verify the connection details, including the storage account and table, to ensure they align with your configuration. c. Make any necessary modifications to the connection settings as per your requirements. For the "Office365" API connection: a. Enable the connection if it is not already enabled. b. Validate the connection details, such as the M365 Outlook account and other settings. c. Adjust the connection settings if needed to match your specific configuration. Save the changes made to the API connections. Proceed to test the API connections to ensure their proper functioning: a. Within the Logic App designer, locate the "Test" button at the top of the screen. b. Follow the provided prompts to supply any required inputs for the test. c. Execute the test and carefully examine the results for any errors or issues. If the test runs successfully without any errors, it indicates that the API connections are properly configured and functional. Conclusion By diligently following these steps, you can verify and configure the API connections used within the Logic App. This process guarantees seamless communication between the Logic App and the corresponding services, enabling the accurate and timely delivery of notifications based on the Attack Path data. Additional Resources If you are using Attack Path and Cloud Security Explorer and want to share your feedback with the Defender for Cloud Team, please e-mail us directly from here. You can also use the resources below to learn more about these capabilities: (Video) Identify and remediate attack paths Microsoft Defender for Cloud Security Posture Management GitHub Repository - Notify-NewAttackPath Reviewers Yuri Diogenes, Principal PM Manager, CxE Defender for Cloud Continue reading...
-
Companies often provide mobile devices to frontline workers that need to be shared between shifts. Microsoft’s shared device mode allows frontline workers to easily authenticate by automatically signing users in and out of all the apps that have enabled this feature. Today, we are excited to unlock key scenarios on Android shared devices for customers. We are announcing the general availability of Outlook, Edge, Viva Engage (previously Yammer), and Power Apps on shared Android devices, joining the portfolio of apps including, Microsoft Teams and Managed Home Screen. An animated image demonstrating how to sign into a work account and easily sign out with one click on an Android shared device. Once signed into a shared Android device, frontline workers can immediately send and receive emails on Outlook to communicate with team members and their leadership team. Many organizations are automating manual and fragmented processes with the help of Power Apps to save frontline workers’ time to focus more on customers - whether that is an inspection app to easily complete a customized inspection checklist or an app to help retail store associates document service and inventory issues. An image of two mobile screenshots side by side: On the left is an example of an email list in the Outlook app. On the right is an example of an inventory request in the Power Apps mobile app. With shared device mode support on Edge, frontline workers can now access any web-based app after signing into a shared Android device - they can easily resolve customer issues by bringing up a shipping app to check delivery status or searching internal wikis to answer technical questions. With Viva Engage (previously Yammer), frontline workers can now connect with relevant communities at work. Through these connections, frontline workers can easily receive communications from leadership, get information on company mission and strategic priorities, and learn valuable skills from others that have similar job roles. An image of two mobile screenshots side by side: On the left is a browser tab on the Microsoft Edge mobile app. On the right is the Communities tab in the Viva Engage mobile app. At the end of their shifts, frontline workers can sign-out easily with just one-click, removing all browser information on Edge or personal information on Viva Engage so that they can return it to the device pool for the next person to use. When used with Intune’s Application Protection Policies, you can provide additional data protection so other parts of the device do not leave data behind. For further guidance on deploying frontline solutions, read the frontline deployment documentation. For steps to setup shared device mode with Intune, read the Intune setup blog. Did you know? The Microsoft 365 Roadmap is where you can get the latest updates on productivity apps and intelligent cloud services. Check out what features are in development or coming soon on the Microsoft 365 Roadmap, or view roadmap item, Microsoft 365 app: [Android] Shared Device Mode for Front Line Workers. Continue reading...
-
Today, we are releasing our latest version of Windows Admin Center to public preview – version 2306! Thank you to our customers, partners, and fans for helping us to continue to improve and make Windows Admin Center better! In this release, we’ve made improvements across our entire product! From updates to our platform, improving your core tool management experiences, introducing new features, and bridging more of the gap for the legacy tool parity. We hope you’ll read on and share in our excitement for the new features we’re introducing this summer. Platform updates WDAC support for servers, client, and clusters is now GA Last year, we introduced the preview for Windows Admin Center to manage WDAC-enforced servers, client machines, and clusters. After hearing your feedback, and making major improvements, we’re excited to say that this support is now generally available! With thousands of new malicious files created every day, traditional methods like antivirus solutions - signature-based detection to fight against malware – only provide one aspect of your defense in depth strategy. In most organizations, information is the most valuable asset. Ensuring that only approved users have access to that information is imperative. However, when a user runs a process, that process typically has the same level of access to data that the user has. As a result, sensitive information could easily be deleted or transmitted out of the organization if a user knowingly or unknowingly runs malicious software. Windows Defender application control (WDAC) can help mitigate many security threats by restricting the applications that users are allowed to run and the code that runs in the System Core (kernel). Application control policies can also block unsigned scripts and MSIs, and restrict Windows PowerShell to run in Constrained Language Mode. Learn more about Application Control for Windows. Windows Admin Center now fully supports managing servers and clusters with Constrained Language Mode enabled (with the right WDAC policy in place). The experience in Windows Admin Center is no different – simply add your server, client, or cluster and use Windows Admin Center as you always do. Learn more. Gateway registration and Azure sign-in improvements In this release, we’ve improved a few scenarios with gateway registration and Azure sign-in experiences, including fixing an issue with stale registration and sign-in data in the Azure Stack HCI registration workflow. We also added a bigger delay between the creation of a new application ID and logging in to Azure to reliably finish gateway registration. Tool updates Improved Hyper-V Virtual machine management The Hyper-V virtual machine management tool has improved multiple experiences. These include move virtual machine between clusters, move virtual machine with storage, and much more! Our vision is make Hyper-V tool your go to tool to manage your virtual machines! In this Public Preview, here are some examples of what you will see: Ability to download your VM list with corresponding properties as CSV file Feature to pop out a VM’s RDP session Ability to configure the VM to be highly available Cluster-aware event viewer Recently we updated our Events tool for servers with an improved interface to better serve your management needs. We’re continuing to invest in the ability to view and analyze the events from your systems in this release with the preview of the Events tool for clusters! The cluster-aware version of the Events tool collects data from all nodes within a cluster and presents it in a unified interface. You can create and modify workspaces, save and delete them, and open existing workspaces to pick up right where you left off. In addition to the filters that are present in the Events tool for server, including event sources, levels, and IDs, we’ve also added a filter to the cluster-aware version of this tool to filter by node in the cluster. We’ve also improved the tool to better handle larger volumes of data and load results quickly. This interface provides a consistent experience whether you’re managing single servers or multi-node clusters. File editor We have heard that convenient file access has been a challenge, especially with .txt or .log files. You are now able to modify these files right here in Windows Admin Center and save your changes without ever having to leave this tool or switch context. Editable files will show up as blue, click-able items in your file directory under the “Files & file sharing” tool. Azure Arc status Azure Arc-enabled servers lets you manage Windows and Linux physical servers and virtual machines hosted outside of Azure, on your corporate network, or other cloud provider. Windows Admin Center provides an Azure Arc for servers onboarding experience through our Azure hybrid center. In this update, you don’t have to navigate to the Azure Arc for Servers blade in your server settings to view the status of your Azure Arc-enabled machine. There is now a new field on the Overview page that displays your Azure Arc agent status. In this release, you may see errors on the Overview page if your Windows Admin Center gateway is not registered with Azure. This is a known issue that will be addressed before this version of Windows Admin Center is generally available. Context menu integration Accessibility is a constant priority for Windows Admin Center. We know that some users prefer to use the keyboard instead of the mouse to navigate Windows Admin Center, and that keyboard navigation can occasionally be inconvenient. That’s why we’ve added a context menu. The context menu shows the extension actions by pressing the keyboard shortcut Shift+F11. From here, you can quickly perform extension actions and reduce the amount of time you must spend navigating the webpage. While this feature is not available for every extension just yet, we have expanded the context menu integration to cover more tools in this release, including: Local users & groups Certificates Networks Devices Firewall Apps & features Registry We will continue to roll out the context menu feature to additional extensions to ensure users who prefer keyboard navigation can get their tasks done efficiently. Azure Stack HCI deployment & management Azure Stack HCI Security Settings With the Azure Stack HCI supplemental package, HCI is a secure-by-default product and has more than 200 settings enabled by default. These settings provide a consistent security baseline and ensure that the device always starts in a known good state. The security baseline on Azure Stack HCI: Enables you to closely meet Center for Internet Security (CIS) benchmark and Defense Information System Agency (DISA) Security Technical Implementation Guide (STIG) requirements for the operating system (OS) and the Microsoft recommended security baseline. Reduces the operating expenditure (OPEX) with its built-in drift protection mechanism and consistent at-scale monitoring via the Azure Arc Hybrid Edge baseline. Improves the security posture by disabling legacy protocols and ciphers. Windows Admin Center provides an experience for you to easily look at the status of a set of crucial security settings, and toggle settings that do not meet the security requirements. It allows you to view and manage your WDAC status and configure settings such as maintaining security defaults (drift control), Signing for SMB traffic, Side Channel mitigation, and many more! New HCI Diagnostics tool If you have an HCI cluster running with the supplemental package. There will be a new diagnostics tool available. With this new tool, users are now able to proactively collect logs, with the flexibility to enable or disable this at will. These logs are sent straight to Azure by default. You can collect your logs on-demand, download them to your local machine, and view the history of logs collected from the last 90 days. Furthermore, you have the ability to specify a time when logs will be sent so you can automate your workflow and tasks. Move a volume to another server The Volumes tool in Cluster Manager now contains a ‘Move’ button. This enables you to move a volume to another server in the cluster. You can verify which server currently owns the volume by adding the ‘Server’ column to the Inventory table. Learn more. Storage Spaces and pools settings The Storage Spaces and pools Settings section in Cluster Manager now contains 3 new settings: Status, Health status and Capacity alert threshold. The Status and Health status values can help alert the user of unexpected storage or S2D issues. The Capacity alert threshold dropdown lets the user select a threshold between 50% and 100%. When the storage pool fills to this threshold, a notification will be displayed on the Dashboard. Windows Admin Center in Azure Windows Admin Center in Azure continuously releases new updates on a monthly basis, providing you with the latest and greatest that Windows Admin Center has to offer. AAD Authentication for Azure Stack HCI Last year, we introduced Azure AD authentication for Windows Admin Center in Azure for Windows Server machines, but Azure Stack HCI clusters still required you to enter your local administrator credentials for management. We’re happy to announce that Azure AD authentication is now supported for Azure Stack HCI clusters too! As long as your Azure AD identity is part of the “Windows Admin Center Administrator Login” role, that’s all you need to start managing your cluster using Windows Admin Center in Azure to manage your cluster. You can: Reduce reliance on local administrator accounts Get SSO to your Azure Stack HCI cluster Use all the protection and security with Azure AD Conditional Access and Identity Protection that are enforced for the Azure Portal (multifactor authentication, compliant device, user/sign-in risk, and others) to protect your Azure Stack HCI cluster Use Azure RBAC to grant the appropriate access to clusters based on need and remove it when it’s no longer needed Download today! We hope you enjoy this latest update of Windows Admin Center, the various new functionality in preview, and all the extensions now available. Learn more and download today! As always, thanks for your ongoing support, adoption, and feedback. Your contributions through user feedback continue to be vital and valuable to us, helping us prioritize and sequence our investments. Windows Admin Center is continuously evolving and growing as a tool and a platform, and we are beyond thrilled to have you part of our journey. To skill up on Windows Admin Center and Windows Server 2022, check out our Windows Server Hybrid Administrator Certification and other featured Learn courses. Thank you, Windows Admin Center Team (@servermgmt) Continue reading...
-
Hello everyone! I´m Stefan Röll, Cloud Solution Architect at Microsoft Germany for Intune and Microsoft Configuration Manager. In the past weeks, I got a lot of questions from customers around the recently released Unified Update Platform (UUP). In this Blog I want to cover some of them. The challenge with large updates UUP Updates are a big step forward for on-prem environments that want to leverage features, which were previously reserved for online environments. However, every cumulative update (CU) is now about 10GB in size which might be a challenge to handle for slow connected systems. However, Microsoft Configuration Manager (ConfigMgr) uses clever technologies to limit the impact on the backend side. Do I have to download 10GB every month to my source location? When you have successfully downloaded the first UUP update, you might wonder if you must download 10 GB every month to your source directory: At a first glance it looks like it, but if you look closely at the PatchDownloader.log (normally stored in the %temp% folder), you can see that the downloader tries to create hard links: That means all the files that stay the same every month don´t need additional space at your source location nor will they be downloaded. This scenario only works if the files will be downloaded to the same share as the previous updates. If the files are found on a different share, they will take up additional space, but will not be downloaded from the internet, but instead copied over locally. It´s hard to catch hard links. In the screenshot below it looks like the updates from March and April take up 18.5 GB of space on the hard disk T: However, in this test these are the only files stored on this drive. Therefore, we can see the used space in the properties of the drive: Another way to verify that hard links are being used is fsutil: Do we have to distribute 10GB to all DPs monthly? The next question that easily comes up is if you have distribute 10 GB to all your Distribution Points (DPs) every month. But, since ConfigMgr 2012 it uses a single instance store better known as the Content Library (ContentLib). It will only store a single instance of each file in it. As the largest files of UUP updates stay the same every month, there is no need for big data transfers every month. But let´s have a closer look. I´ve downloaded the March and the April UUP Updates into separate deployment packages: It looks like this in the content source: To make things a little easier, we will focus on the largest file. This file has the same hash value in both packages: BCEFB8987E4368CC43DF40D0D2F73B9AB6404AF5FC1F6E0D4B451D15E3DA5A13 Using the first four letters, we can find it in the ContentLib – only one time: If we transfer only the Win-03 Package from the Primary Site to a DP, we can see that the file in question is getting transferred: Once completed, we can distribute the Win11-04 deployment package. It will complete quickly, and the file did not transfer again: To further prove the behaviour, I´ve captured a Wireshark trace on the DP while transferring the Win11-03 package: And while transferring the Win11-04 package: So you don´t need to worry about the monthly traffic from your Primary Site to DPs or Pull DPs. However, one challenge could be if a deployment package gets into a failed state for whatever reason. If that happens you have to distribute the complete 10 GB content to your DP. Unfortunately, there is no supported way to get around this behavior. What about Site-to-Site traffic? If you have a Central Administration Site (CAS) and one or more Primary Sites, which you should only have if you must manage more than 150k clients, content is not transferred with the Package Transfer Manager. It is transferred via Site-to-Site traffic and here the single instance store is not used in every scenario. If you add for example the April CU to the same package as the March CU, only the delta will be transferred: However, if you create a new package for the April CU, all content will be transferred: Do we need to open port 8005? In the Ports used for connections documentation you can find the port 8005 for Distribution Points. This port was required for express updates but is not required for UUP Updates on the Distribution Point side. On the client side you don’t have to open the port in the client firewall. However, if a local third-party software uses the port 8005, you might have to change it in the client settings. Is the download on the Client side optimized by peer-to-peer technology from Delivery Optimization? When the Client downloads an UUP update, it is downloaded by the Delivery Optimization downloader and not BITS. When the UUP update is available and downloaded from your Distribution Points, then peer-to-peer technology is not used. You can check this by running Get-DeliveryOptimizationStatus, after the download of an update. However, if the update is not available on a DP it will be downloaded from the internet, if you allowed it in the deployment. If that´s the case, Delivery Optimizations peer-to-peer technology will be used: Is the download on the Client side optimized by peer-to-peer technology from BranchCache? When the Client downloads an UUP update, it is downloaded by the Delivery Optimization downloader and not BITS. Therefore, BranchCache is not used when downloading UUP updates. If you want to find out more about the difference between DO and BITS, check out my previous Blog. Do I need to enable ‘Allow clients to download delta content when available’ in the Client settings? UUP Updates are downloaded with the ‘download delta content’ method. When you are on ConfigMgr 2203 and above, there is no need to enable this setting. If the setting is disabled, only UUP Updates will be downloaded over this method. All other updates will download as usual over BITS. However, if you enable it, all updates will be downloaded over this method. Next steps Have a look at the links below to get even more information about UUP Updates. Stefan Röll Cloud Solution Architect – Microsoft Germany Helpful resources and references: Unified update platform (UUP) FAQ's Unified update platform (UUP) FAQ's Optimize Windows 10 or later update delivery with Configuration Manager Optimize Windows update delivery - Configuration Manager Allow clients to download delta content when available https://learn.microsoft.com/en-us/mem/configmgr/core/clients/deploy/about-client-settings#allow-clients-to-download-delta-content-when-available Get ready for the first UUP on premises updates coming in March! Get ready for the first UUP on premises updates coming in March! What’s UUP? New update style coming next week! What’s UUP? New update style coming next week! What is Delivery Optimization? What is Delivery Optimization? - Windows Deployment FAQ: WSUS and Unified Update Platform (UUP) on premises FAQ: WSUS and Unified Update Platform (UUP) on premises Modern Content Distribution: Microsoft Endpoint Manager and Connected Cache Modern Content Distribution: Microsoft Endpoint Manager and Connected Cache Disclaimer: The sample scripts are not supported under any Microsoft standard support program or service. The sample scripts are provided AS IS without warranty of any kind. Microsoft further disclaims all implied warranties including, without limitation, any implied warranties of merchantability or of fitness for a particular purpose. The entire risk arising out of the use or performance of the sample scripts and documentation remains with you. In no event shall Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the scripts be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary loss) arising out of the use of or inability to use the sample scripts or documentation, even if Microsoft has been advised of the possibility of such damages. Continue reading...