-
Posts
27,570 -
Joined
-
Last visited
-
Days Won
73
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by AWS
-
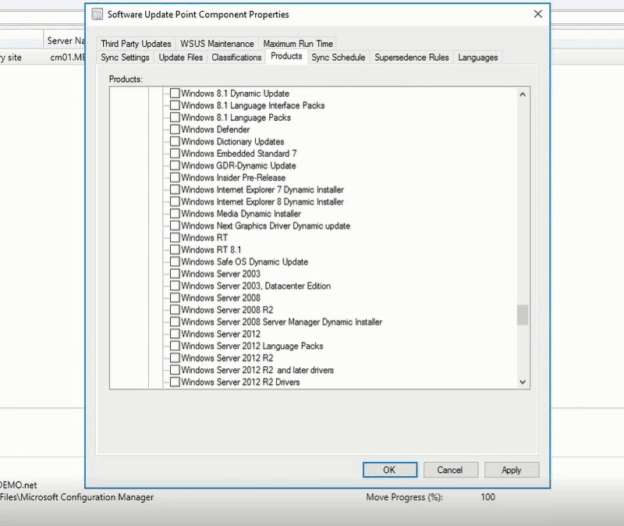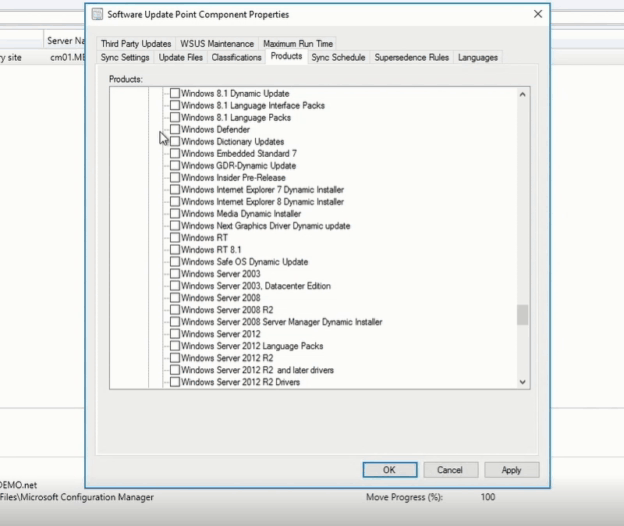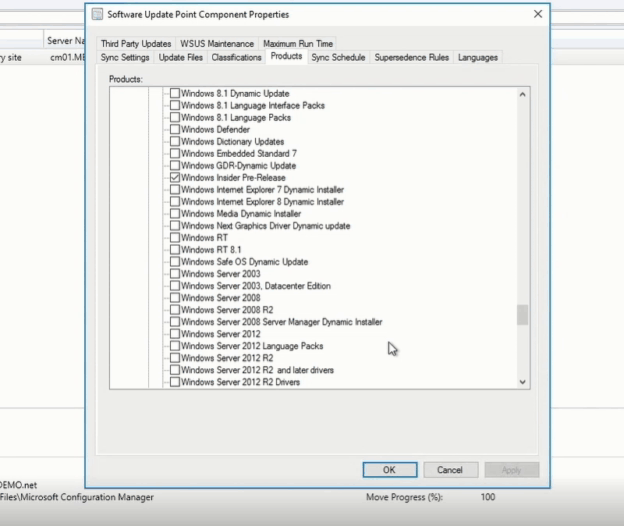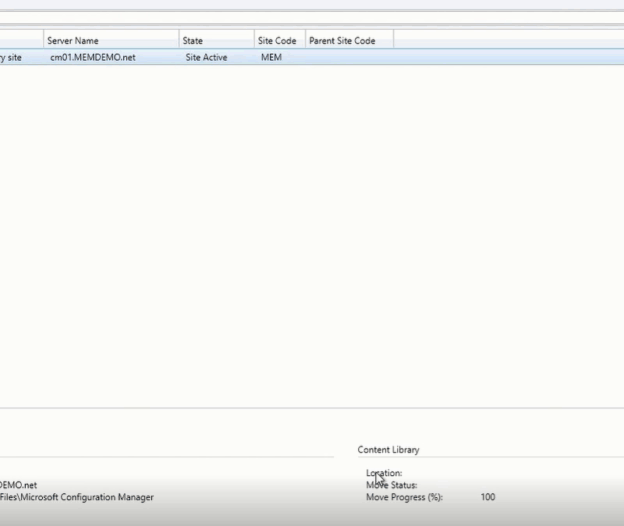
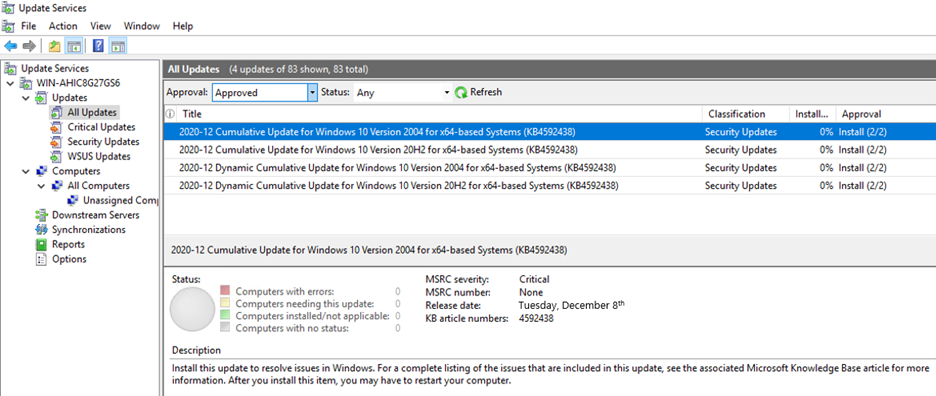
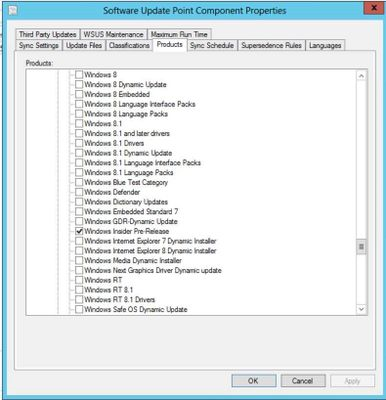
You can now deploy the December 2020 latest cumulative update (LCU) and servicing stack update (SSU) together via our new one cumulative update package, or separately. On September 9th, 2020, I announced the work in progress to simplify on premises deployments of servicing stack updates. Today, I am excited to announce that you can take advantage of this new capability using Windows Server Update Services (WSUS) and the Windows Insider Program for Business. We have released the December 2020 LCU and the December 2020 SSU to WSUS in two ways for devices running Windows 10, version 2004 and later: to the typical Security Updates category and to the Windows Insider Pre-Release category. To deploy the cumulative update and servicing stack update separately, no special action is needed. Just ensure, as always, that you deploy the SSU prior to deploying the LCU so that both updates install successfully on the device. To deploy the LCU and SSU together using the new one cumulative update package, simply follow three easy steps. Note: Before completing the steps below, ensure that you have installed the September 2020 SSU on the targeted devices. Step 1: Sync the Windows Insider Pre-Release category In the WSUS console, from Products and Classifications, select Windows Insider Pre-Release Product and Upgrades. Sync WSUS. In Microsoft Endpoint Manager Configuration Manager, navigate to the Products tab of Software Update Point Component Properties and select Windows Insider Pre-Release. Select OK to confirm this selection. Step 2: Select the OS version From the list of All Updates, select the cumulative update for the version of Windows 10 running on the device(s) that will receive the update. Currently, this would be either of the following: 2020-12 Cumulative Update for Windows 10 Version 2004 2020-12 Cumulative Update for Windows 10 Version 20H2 Step 3: Deploy the update Deploy the update to the desired devices in your organization the same way you would deploy any other monthly cumulative update. Note: When you deploy the update package to your devices, the client will automatically orchestrate the proper ordering of installation to ensure the SSU and LCU are both applied correctly on the device. This will be the exact same content as if you had deployed the December 2020 LCU and SSU separately. Check your preferred method of reporting and note that your devices are now running the December LCU (KB4592438) and SSU (KB4593175). That’s it! It’s that simple. The best part? Like all preview builds published to commercial devices in the Release Preview Channel and to the WSUS Windows Insider Pre-Release category, testing out this new deployment technology for LCUs and SSUs from WSUS is fully supported. If you run into an issue that prevents you or other users in your organization from deploying or updating using this new one cumulative package, use this online form to request assistance directly from Microsoft Support at no cost to you. Or contact customer support through your typical channel. Try out this new way of deploying LCUs and SSUs and let us know what you think by commenting below or reaching out to me directly on Twitter @ariaupdated. Continue reading...
-
While volume activation is a process that many have utilized over the years, today's post offers guidance to help you ensure that all your devices have been properly activated regardless of their connection to your organization's network. First, a refresher. Volume activation enables a wide range of Windows devices to receive a volume license and be activated automatically and en masse versus tediously entering an activation key on each Windows device manually. The most common methods of volume activation require that devices to be connected to an organization's network or connected via virtual private network (VPN) to “check in” from time to time with the organization’s activation service to maintain their licenses. When people work from home and off the corporate or school network; however, their devices’ ability to receive or maintain activation is limited. Volume activation methods There are several methods to activate devices via volume licensing. For detailed information, see Plan for volume activation. Here, however, is a summary for easy reference. Key Management Service Key Management Service (KMS) activation requires TCP/IP connectivity to, and accessibility from, an organization’s private network so that licenses are not accessible to anyone outside of the organization. By default, KMS hosts and clients use DNS to publish and find the KMS key. Default settings can be used, which require little or no administrative action, or KMS hosts and client computers can be manually configured based on network configuration and security requirements. KMS activations are valid for 180 days (the activation validity interval). KMS client computers must renew their activation by connecting to the KMS host at least once every 180 days. By default, KMS client computers attempt to renew their activation every 7 days. If KMS activation fails, the client computer retries to reach the host every two hours. After a client computer’s activation is renewed, the activation validity interval begins again. Multiple Activation Key A Multiple Activation Key (MAK) is used for one-time activation with Microsoft’s hosted activation services. Each MAK has a predetermined number of activations allowed. This number is based on volume licensing agreements, and it might not match the organization’s exact license count. Each activation that uses a MAK with the Microsoft-hosted activation service counts toward the activation limit. You can use a MAK for individual computers or with an image that can be duplicated or installed using Microsoft deployment solutions. You can also use a MAK on a computer that was originally configured to use KMS activation, which is useful for moving a computer off the core network to a disconnected environment. Active Directory-based activation Active Directory-based activation is similar to KMS activation but uses Active Directory instead of a separate service. Active Directory-based activation is implemented as a role service that relies on Active Directory Domain Services to store activation objects. Active Directory-based activation requires that the forest schema be updated using adprep.exe on a supported server operating system, but after the schema is updated, older domain controllers can still activate clients. Devices activated via Active Directory maintain their activated state for up to 180 days after the last contact with the domain. Devices periodically attempt to reactivate (every seven days by default) before the end of that period and, again, at the end of the 180 days. Windows 10 Subscription Activation Starting with Windows 10, version 1703 Windows 10 Pro supports the Subscription Activation feature, enabling users to “step-up” from Windows 10 Pro to Windows 10 Enterprise automatically if they are subscribed to Windows 10 Enterprise E3 or E5. With Windows 10, version 1903 the Subscription Activation feature also supports the ability to step-up from Windows 10 Pro Education to the Enterprise grade edition for educational institutions – Windows 10 Education. The Subscription Activation feature eliminates the need to manually deploy Windows 10 Enterprise or Education images on each target device, then later standing up on-prem key management services such as KMS or MAK based activation, entering GVLKs, and subsequently rebooting client devices. To step a device up to Windows 10 Education via Subscription Activation the device must meet the following requirements: Windows 10 Pro Education, version 1903 or later installed on the devices to be upgraded. A device with a Windows 10 Pro Education digital license. You can confirm this information in Settings > Update & Security > Activation. The Education tenant must have an active subscription to Microsoft 365 with a Windows 10 Enterprise license or a Windows 10 Enterprise or Education subscription. Devices must be Azure AD-joined or Hybrid Azure AD joined. Workgroup-joined or Azure AD registered devices are not supported. Note: If Windows 10 Pro is converted to Windows 10 Pro Education using benefits available in Store for Education, then the feature will not work. You will need to re-image the device using a Windows 10 Pro Education edition. Volume activation while working from home If you activate devices in your organization using MAK, the activation process is straightforward and the devices are permanently activated. If you are using KMS or Active Directory-based Activation, each device must connect to the organization’s local network at least once every 180 days to “check in” with either the KMS host or the Active Directory domain controller. Otherwise, the user will be warned to activate Windows again. With many users working or taking classes from home, a connection to the organization's network may not exist, which would ultimately leave their devices in a deactivated state. There are a few options to avoid this: Use a VPN. By having the device connect to your organization’s network via a VPN, it will be able to contact a KMS host or Active Directory domain controller and will be able to maintain its activation status. If you manage your devices through a wholly on-premises solution to deploy policies, collect inventory, and deploy updates and other software, there is a good chance you are already using a VPN. Depending on the VPN configuration, some manual configuration of the client device may be required to ensure the KMS service is accessible through the VPN. For more details on these settings, which can be implemented via script, see Slmgr.vbs options for obtaining volume activation information. Convert the devices from KMS to MAK activation. By converting from KMS to MAK activation, you replace the license that requires reactivation every 180 days with a permanent one, which requires no additional check-in process. There are some cases—in educational organizations, for example—where each device is re-imaged at the end of the school year to get ready for the next class. In this case, the license must be “reclaimed” by contacting your Microsoft licensing rep or a Microsoft Licensing Activation Center. One way of converting a device from KMS to MAK activation is to use the Windows Configuration Designer app (available from the Microsoft Store) to create a provisioning package, which includes the MAK, and deploy the package through email or a management solution such as Microsoft Intune. You can also deploy a MAK directly within Intune without creating a provisioning package by creating a simple PowerShell script with the following commands and deploying the script to a user group: slmgr.vbs /ipk XXXXX-XXXXX-XXXXX-XXXXX-XXXXX slmgr.vbs /ato (In the example above, XXXXX-XXXXX-XXXXX-XXXXX-XXXXX is your MAK key.) It is important to monitor the success of these activations and remove users from the target group once their devices have been activated so that their other devices do not receive a new license. Note: Windows Configuration Designer is also available as part of the Windows Assessment and Deployment Kit (ADK) for Windows 10. Use Subscription Activation. This requires the devices to be joined to your Azure AD domain, enabling activation in the cloud. This is possible if you have one of the following subscriptions: Windows 10 Enterprise E3/E5 Windows 10 Education A3/A5 Windows 10 Enterprise with Software Assurance Microsoft 365 E3/E5 Microsoft 365 E3/A5 Microsoft 365 F1/F3 Microsoft 365 Business Premium If you need assistance and have one of the preceding subscriptions with at least 150 licenses, you may be eligible for assistance through FastTrack. Contact your Microsoft representative or request assistance from FastTrack and a Microsoft FastTrack representative will contact you directly. Conclusion Windows volume activation has been around for a long time, but the increased number of users working from home may require your organization to re-evaluate how to best keep your devices activated if they cannot reach your on-premises activation service if you are using KMS or Active Directory-based Activation. It is important to consider the options available to you to ensure your devices stay activated. As always, there is no “one-size-fits-all” approach, so consider the pros and cons of each option as you plan on how to best support your remote workers and students. To learn more about activation, see Activate clients running Windows 10. Continue reading...
-
The Extended Security Update (ESU) program is a last resort for customers who need to run certain legacy Microsoft products past the end of support. Support for the following versions of Windows and Windows Server ended on January 14, 2020: Windows 7 SP1 (Professional, Enterprise) Windows 7 Professional for Embedded Systems Windows Server 2008 R2 SP1 and Windows Server 2008 SP2 Windows Server 2008 R2 SP1 for Embedded Systems and Windows Server 2008 SP2 for Embedded Systems If your organization has been unable to update devices running the versions of Windows listed above to a currently supported version before January 12, 2021, ESU can provide security updates to those devices through January 11, 2022—helping protect those devices while you complete your Windows and Windows Server upgrade projects. Many organizations have made the transition to the latest version of Windows 10 or Windows Server. Those who deployed Windows 10 benefit from strong protection against threats plus the latest security and manageability features such as Microsoft Defender Antivirus, richer device management policies, and Windows Autopilot. Other organizations running legacy applications shifted their Windows 7 devices to Windows Virtual Desktop, which includes ESU for Windows 7 virtual desktops at no additional cost, enabling you to continue running critical line-of-business apps while you continue your migration to Windows 10. As a last resort, however, a number of organizations purchased, installed, and activated their first year of ESU to receive security updates for eligible devices through January 12, 2021. What you need to know about year two coverage for ESU Because ESU are available as separate SKUs for each of the years in which they are offered (2020, 2021, and 2022)—and because ESU can only be purchased in specific 12-month periods—you will need to purchase the second year of ESU coverage separately and activate a new key on each applicable device in order for your devices to continue receiving security updates in 2021. If your organization did not purchase the first year of ESU coverage, you will need to purchase both Year 1 and Year 2 ESU for your applicable Windows 7 or Windows Server devices before installing and activating the Year 2 MAK keys to receive updates. The steps to install, activate, and deploy ESUs are the same for first and second year coverage. For more information, see Obtaining Extended Security Updates for eligible Windows devices for the Volume Licensing process and Purchasing Windows 7 ESUs as a Cloud Solution Provider for the CSP process. For embedded devices, contact your original equipment manufacturer (OEM). We recommend that you prepare now to install and activate the second year of ESU coverage for the devices in your organization that require it. To learn more about ESU, please watch our Microsoft Ignite 2019 session on How to manage Windows 7 Extended Security Updates (ESU) for on-premises and cloud environments. We're here to help We understand that everyone is at a different point in the upgrade process, which is why we offer assistance with tools like Desktop Analytics and services like Microsoft App Assure—as well as monthly Office Hours to help you deploy and stay current with Windows 10 across your organization. More information on ESU for Windows 7 and Windows Server 2008 and 2008 R2 is available in the Windows 7 end of support FAQ and Windows Server 2008 and 2008 R2 FAQ. Continue reading...
-
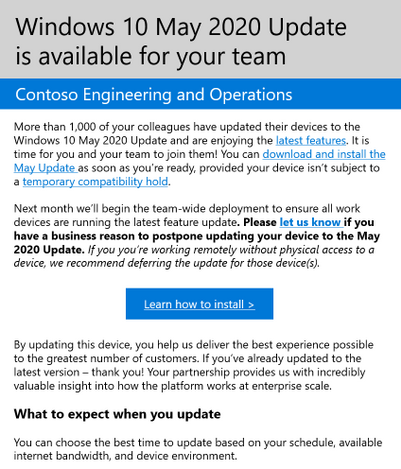
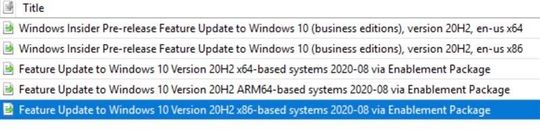
Windows 10, version 20H2 is now available through Windows Server Update Services (WSUS) and Windows Update for Business, and can be downloaded today from Visual Studio Subscriptions, the Software Download Center (via Update Assistant or the Media Creation Tool), and the Volume Licensing Service Center[1]. Today also marks the start of the 30-month servicing timeline for this Semi-Annual Channel release. Just like we did for devices upgrading from Windows 10, version 1903 to version 1909, we will be delivering Windows 10, version 20H2 (also referred to as the Windows 10 October 2020 Update) to devices running Windows 10, version 2004 via the new streamlined fashion, which we call an enablement package. For those updating to Windows 10, version 20H2 from earlier versions of Windows, the process will be similar to previous updates. For those of you that are new to “enablement packages,” Windows 10, version 2004 and Windows 10, version 20H2 share a common core operating system with an identical set of system files. As a result, the new features in version 20H2 were included in the monthly quality updates for version 2004 released on September 8, 2020, but were delivered in a disabled/dormant state. These features remain dormant until they are turned on with the Windows 10, version 20H2 enablement package: a small, quick to install “switch” that activates these features. Using an enablement package, the update to Windows 10, version 20H2 should take approximately the same amount of time as it does to install monthly quality updates. Note: If you are running Windows 10, version 2004 and have not installed the September 8, 2020 updates, you will not see the version 20H2 enablement package offered to your device. With today's release, we recommend IT administrators begin targeted deployments of Windows 10, version 20H2 to validate that the apps, devices, and infrastructure used by their organizations work as expected with the new features. If you will be updating devices used in remote or hybrid work scenarios, I also recommend reading Deploying a new version of Windows 10 in a remote world. For insight into our broader rollout strategy, see John Cable's post on How to get the Windows 10 October 2020 Update. If your organization is currently running Enterprise or Education editions of Windows 10, version 2004, you have 18 months of servicing. By using the enablement package to upgrade your devices to version 20H2, you will receive 30 months of servicing. Devices running Home, Pro, Pro for Workstations, and Pro Education will receive the standard 18 months of servicing. For more information, see the Windows lifecycle FAQ. New features As you begin to roll out Windows 10, version 20H2 to your organization, here are some of the new features and enhancements that will allow you to benefit from intelligent security, simplified updates, flexible management, and enhanced productivity. For the end user Theme-aware tiles in Start – The redesigned Start menu has a more streamlined design that removes the solid color backplates behind the logos in the apps list, and applies a uniform, partially transparent background to the tiles. This design creates a beautiful stage for your icons, especially the Fluent Design icons for Office and Microsoft Edge, as well as the redesigned icons for built-in apps like Calculator, Mail, and Calendar. ALT+TAB between tabs in Microsoft Edge – We introduced ALT+TAB (task switcher) allowing you to toggle between open windows way back in Windows 2.0! In Windows 10, version 20H2, you can now use ALT+TAB to rotate between not only your open apps but also the tabs in Microsoft Edge. Now rotating through ALT+TAB will allow you to open Microsoft Edge in the specific tab you're needing, not just the latest active tab. You can modify the ALT+TAB experience in Settings > System > Multitask. Improved notifications – Toast notifications now have the app's logo in the top left corner of the notification, so you can immediately see where the notification is coming from. We've also turned off the Focus Assist notifications, which tells you when Focus Assist is enabled – whether via automatic rule or manually enabling it. Settings – We continue to improve the Settings page, adding more and more classic Control Panel capabilities. In addition to added settings, we also added a [COPY] button to Settings > System > About so you can easily copy that information and paste it into a help desk ticket. Watch for even more improvements to come! Tablet experience – Previously, when you detach a keyboard on a 2-in-1 device, a toast notification would appear asking if you wanted to switch into Tablet Mode. If you tapped Yes, you would switch into Tablet Mode. But selecting No would bring you the Windows desktop. In Windows 10, version 20H2, the default is changed: the toast notification no longer appears and you are instead brought into the new tablet experience. You can change this behavior in Settings > System > Tablet. Refresh rate of display – Change the refresh rate of your display, giving you a smoother motion. This change can be made at Settings > System > Display > Advanced display settings. Note that this may require supported hardware. Microsoft Edge (built on Chromium) – And of course, Windows 10, version 20H2 is the first version of Windows to come with Microsoft Edge browser built on the Chromium engine. To keep up the latest improvements for end users, follow the Windows Insider Program Blog. For the IT professional Mobile device management (MDM) – Like you've been doing with Group Policy for 20 years, you can now make granular changes to Local Users and Groups on an MDM-managed Windows 10 device by using the Local Users and Groups MDM policy. Windows Autopilot – There have been many enhancements to Windows Autopilot since version 2004, including Windows Autopilot for HoloLens, Windows Autopilot and co-management, and enhancements to Autopilot reporting. For details on all of these and more, see Managing Windows Devices with Microsoft Endpoint Manager. Here's a summary of some of the enhancements: Windows Autopilot for HoloLens – You know HoloLens as that untethered, holographic device. HoloLens 2 devices are commercial-ready, support Azure AD, MDM, kiosk mode, BitLocker, Windows Store for Business, and Windows Update for Business. As adoption increases, setting up your HoloLens 2 devices just got easier, with a Windows Autopilot for HoloLens 2 self-deploying mode. Windows Autopilot with co-management – Co-management policy can be set during Autopilot deployment to ensure workloads are managed from the appropriate source. Windows Autopilot ESP + task sequences – Using a task sequence as part of Windows Autopilot allows you to take advantage of your Configuration Manager investments and reuse those task sequences to configure devices. The task sequence can integrate right into the Enrollment Status Page (ESP), blocking access to the desktop until the task sequence completes. Enhancements to Windows Autopilot deployment reporting – Currently in preview, you can monitor the status of Autopilot deployments in the Microsoft Endpoint Manager admin center: endpoint.microsoft.com. From there, select Devices > Monitor and scroll down to the Enrollment section. Click Autopilot deployment (preview). As this section grows, you will soon be able to see ESP duration broken down at a device and user targeted ESP and app installation status, policy status, and other enhancements. So stay tuned! [*]Microsoft Defender Application Guard for Office – Microsoft Defender Application Guard, designed for Windows 10, now supports Office! With this support, you can launch untrusted Office documents (those that come from outside the Enterprise) in an isolated container to prevent potentially malicious content from compromising the user's computer or exploiting their personal contents. [*]LCU + SSU = single payload – Many of you have asked us for many years to simplify the deployment of Latest Cumulative Updates (LCUs) and Servicing Stack Updates (SSUs). Starting with Windows 10, version 20H2, LCUs and SSUs have been combined into a single cumulative monthly update, available via Microsoft Catalog or Windows Server Update Services. [*]More secure biometric sign on – With enhanced sign-in security[2], Windows Hello now offers added support for virtualization-based security for certain fingerprint and face sensors, which protects, isolates, and secures a user's biometric authentication data. [*]Microsoft Edge on Chromium – Even more important for the IT pro, we're adding this feature here as well! Windows 10, version 20H2 is the first version of Windows to come with Microsoft Edge on Chromium. Need a reason why you should care? I'll give you five! I also invite you to learn more about the security features in Microsoft Edge. What else have we been up to? Aside from Windows 10, version 20H2, we've been busy with other new, exciting products and features that you may have heard about! Note that some of these may require additional licensing or services. Check out the links for details. Cortana – We continue to make investments in Cortana, adding a daily briefing email from Cortana, play my emails from Outlook, Cortana availability within the Microsoft Teams mobile app (available in English today, more languages coming!), and of course the updated and improved features of Cortana in Windows 10 itself. Universal Print – Universal Print provides cloud-managed print services built on Azure. Universal Print ensures that customers can print from anywhere, anytime, with secure identity credentials. And, it is integrated right into Microsoft Endpoint Manager making it easy to get started and join the thousands of Preview customers who have moved millions of print jobs to the cloud. Windows Virtual Desktop – Windows Virtual Desktop is a desktop and app virtualization service that runs on Microsoft Azure. It lets end users connect securely to a full desktop from any device. And now with Microsoft Endpoint Manager, you can secure and manage your Windows Virtual Desktop VMs with policy and apps at scale, after they're enrolled. Microsoft Tunnel Gateway – Microsoft Tunnel Gateway allows Microsoft Intune-enrolled iOS and Android devices to access on-premises apps and resources, with single sign-on Azure AD authentication, integrated Conditional Access policies, and is flexible enough to meet the needs of all organizations. (Questions about Microsoft Tunnel? Join our Microsoft Tunnel AMA Thursday, October 22, 2020 - 8:00 a.m. to 9:00 a.m. Pacific Time.) Endpoint analytics – Endpoint analytics aims to improve user productivity and reduce IT support costs by providing insights into the user experience. The insights enable IT to optimize the end-user experience with proactive support and to detect regressions to the user experience by assessing user impact of configuration changes. Enroll devices into Endpoint analytics while enabling tenant attach in Configuration Manager. Productivity Score – Productivity Score provides visibility into how your organization works, helping you understand the employee experience, including how collaborative your people are. It also gives visibility into their technology experience, focusing on their endpoints, network connectivity, and Microsoft 365 apps. Microsoft 365 apps – Office 365 ProPlus is the version of Microsoft Office that comes with several enterprise, government, and education subscription plans. Earlier this year we announced a name change to Microsoft 365 apps. If you have internal wikis, packages used by Configuration Manager – specifically any automatic deployment rules (ADRs), or product flows, you may need to update references to Office 365 ProPlus to this new name. Microsoft Defender for Endpoint – Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP) recently went through a name change as well – to Microsoft Defender for Endpoint. Explore the latest features or functionality and find information on the new name and the products affected in the Microsoft Defender for Endpoint blog. Developers! Developers! Developers! – For information on what's new for developers, including Project Reunion and new PowerToys. see Windows Dev Center. (And if you don't know why I introduce this bullet in this way, check out any of the videos here!) Test Base for Microsoft 365 – Test Base provides intelligent application testing from an Azure environment, making it easier for your ISVs (software vendors) to make support statements for a new version of Windows. Frequently asked questions Is there also a Windows Server release with this release? Yes. The next Windows Server semi-annual channel (SAC) release is also available today. The Windows Server semi-annual channel is designed for customers who wish to take advantage of new operating system capabilities at a faster pace. Windows Server, version 20H2 is focused on reliability, performance, and other general improvements. It is also available on Azure Marketplace or the Volume Licensing Service Center. Will there be a Long-Term Servicing Channel (LTSC) release with this release? No. Windows 10 Enterprise LTSC 2019 is the current LTSC option, and was released with Windows 10, version 1809 in November 2018. The next LTSC release can be expected toward the end of 2021. Customers currently using Long-Term Servicing Branch (LTSB) 2015 for special-purpose devices should start working to upgrade those devices to Windows 10 Enterprise LTSC 2019, as mainstream support for LTSB 2015 ended on Oct. 13, 2020, and it entered into extended support. See the lifecycle policy here. Can I upgrade our devices from Windows 7 directly to Windows 10, version 20H2? Yes. You can directly upgrade from Windows 7 to Windows 10, version 20H2. We strongly encourage you to begin your upgrade process immediately as Windows 7 is no longer supported. How can I preview versions of Windows 10 before they become available? I want to start testing these new features early so I can deploy them when they are released! The Windows Insider Program for Business team has focused on enabling IT administrators to view and provide feedback on upcoming security, management, and productivity features ahead of release. And you can manage the installation of Windows 10 Insider Preview Builds across multiple devices in your organization! Read the Windows Insider Program for Business documentation for more information. Where can I ask specific questions about rolling out Windows 10, version 20H2 and managing updates in general? We hold monthly "office hours" in the Windows 10 servicing community on Tech Community with a broad group of servicing, deployment, endpoint management, and security experts. Submit your questions live during the one-hour event—or post them in advance by adding a label for "Office Hours"—and we'll do our best to help! Visit Office hours: managing Windows 10 devices & updates for more information and calendar links for upcoming events. Or click here to save the date for our November 19th session! Tools and resources To support the release of Windows 10, version 20H2, we have released updated versions of the following resources: Security baseline (draft) for Windows 10 and Windows Server, version 20H2 ADMX templates for Windows 10, version 20H2 Group Policy settings reference spreadsheet for Windows 10, version 20H2 Windows 10 Enterprise Evaluation (free 90-day evaluation) Also, if you haven't seen it yet, the Windows release health dashboard (introduced with the release of Windows 10, version 1903) provides you with timely information on the status of the Windows 10, version 20H2 rollout, details on any safeguard holds or known issues (including the status of those issues, workarounds, and resolutions), and other important announcements, such as those related to lifecycle updates, upcoming events, and best practices. For help with configuring and deploying updates, please see the following resources: Overview of Windows as a service Simplifying Windows 10 deployment with Configuration Manager Build deployment rings for Windows 10 updates Deploy updates using Windows Update for Business Deploy Windows 10 updates using WSUS Deploy Windows 10 updates using Configuration Manager Manage device restarts after updates Manage additional Windows Update settings Deploying a new version of Windows 10 in a remote world To see a summary of the latest documentation updates, see What's new in Windows 10, version 20H2 IT pro content on Docs. And finally, for a list of features and functionality that have been removed from Windows 10, or might be removed in future releases, see Features and functionality removed in Windows 10. For the latest updates on new releases, tools, resources, AMAs, Ask the Experts, or Windows Office Hours, stay tuned to this blog and follow us @MSWindowsITPro on Twitter. You can also follow me on Twitter @LURIE_MSFT for the latest on Microsoft Endpoint Manager, Windows, and other exciting news and events for IT pros. [1] It may take a day for downloads to be fully available in the VLSC across all products, markets, and languages. [2] Enhanced sign-in security requires specialized hardware and software components that can be leveraged starting on devices shipping with Windows 10 October 2020 Update configured out of factory. Documentation will be available later this year. Continue reading...
-
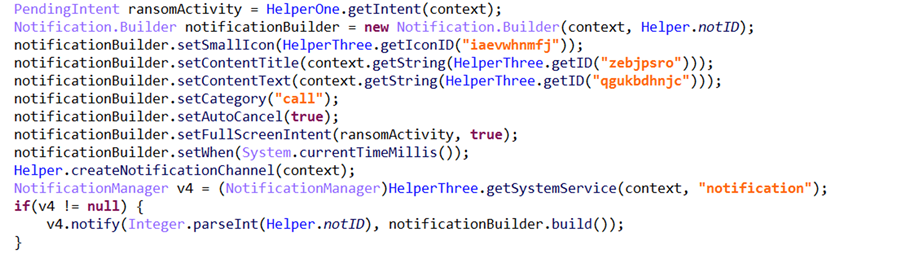
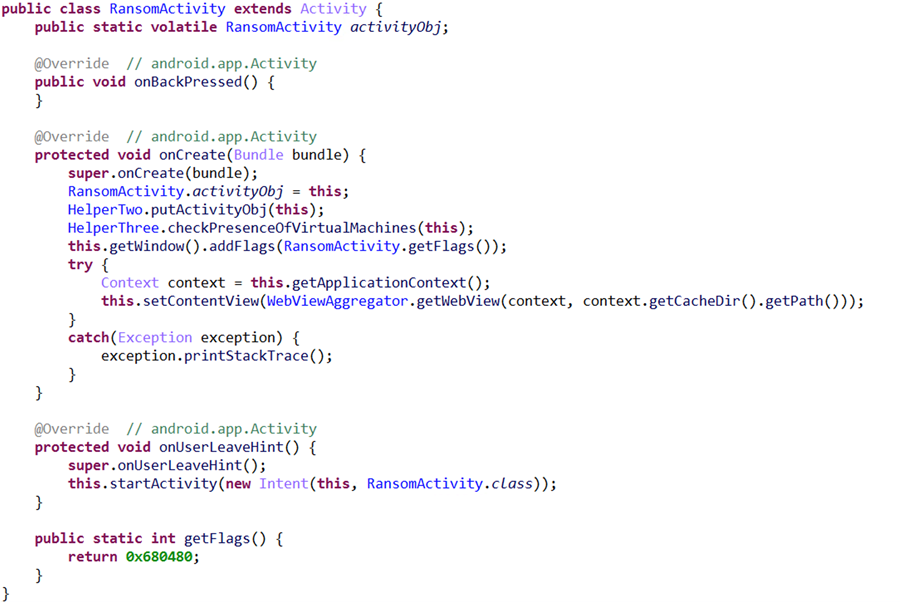
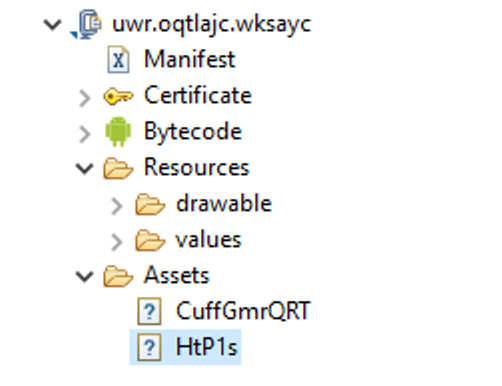
Attackers are persistent and motivated to continuously evolve – and no platform is immune. That is why Microsoft has been working to extend its industry-leading endpoint protection capabilities beyond Windows. The addition of mobile threat defense into these capabilities means that Microsoft Defender for Endpoint (previously Microsoft Defender Advanced Threat Protection) now delivers protection on all major platforms. Microsoft’s mobile threat defense capabilities further enrich the visibility that organizations have on threats in their networks, as well as provide more tools to detect and respond to threats across domains and across platforms. Like all of Microsoft’s security solutions, these new capabilities are likewise backed by a global network of threat researchers and security experts whose deep understanding of the threat landscape guide the continuous innovation of security features and ensure that customers are protected from ever-evolving threats. For example, we found a piece of a particularly sophisticated Android ransomware with novel techniques and behavior, exemplifying the rapid evolution of mobile threats that we have also observed on other platforms. The mobile ransomware is the latest variant of a ransomware family that’s been in the wild for a while but has been evolving non-stop. This ransomware family is known for being hosted on arbitrary websites and circulated on online forums using various social engineering lures, including masquerading as popular apps, cracked games, or video players. The new variant caught our attention because it’s an advanced malware with unmistakable malicious characteristic and behavior and yet manages to evade many available protections, registering a low detection rate against security solutions. As with most Android ransomware, this new threat doesn’t actually block access to files by encrypting them. Instead, it blocks access to devices by displaying a screen that appears over every other window, such that the user can’t do anything else. The said screen is the ransom note, which contains threats and instructions to pay the ransom. Figure 1. Sample ransom note used by older ransomware variants What’s innovative about this ransomware is how it displays its ransom note. In this blog, we’ll detail the innovative ways in which this ransomware surfaces its ransom note using Android features we haven’t seen leveraged by malware before, as well as incorporating an open-source machine learning module designed for context-aware cropping of its ransom note. New scheme, same goal In the past, Android ransomware used a special permission called “SYSTEM_ALERT_WINDOW” to display their ransom note. Apps that have this permission can draw a window that belongs to the system group and can’t be dismissed. No matter what button is pressed, the window stays on top of all other windows. The notification was intended to be used for system alerts or errors, but Android threats misused it to force the attacker-controlled UI to fully occupy the screen, blocking access to the device. Attackers create this scenario to persuade users to pay the ransom so they can gain back access to the device. To catch these threats, security solutions used heuristics that focused on detecting this behavior. Google later implemented platform-level changes that practically eliminated this attack surface. These changes include: Removing the SYSTEM_ALERT_WINDOW error and alert window types, and introducing a few other types as replacement Elevating the permission status of SYSTEM_ALERT_WINDOW to special permission by putting it into the “above dangerous” category, which means that users have to go through many screens to approve apps that ask for permission, instead of just one click Introducing an overlay kill switch on Android 8.0 and later that users can activate anytime to deactivate a system alert window To adapt, Android malware evolved to misusing other features, but these aren’t as effective. For example, some strains of ransomware abuse accessibility features, a method that could easily alarm users because accessibility is a special permission that requires users to go through several screens and accept a warning that the app will be able to monitor activity via accessibility services. Other ransomware families use infinite loops of drawing non-system windows, but in between drawing and redrawing, it’s possible for users to go to settings and uninstall the offending app. The new Android ransomware variant overcomes these barriers by evolving further than any Android malware we’ve seen before. To surface its ransom note, it uses a series of techniques that take advantage of the following components on Android: The “call” notification, among several categories of notifications that Android supports, which requires immediate user attention. The “onUserLeaveHint()” callback method of the Android Activity (i.e., the typical GUI screen the user sees) is called as part of the activity lifecycle when the activity is about to go into the background as a result of user choice, for example, when the user presses the Home key. The malware connects the dots and uses these two components to create a special type of notification that triggers the ransom screen via the callback. Figure 2. The notification with full intent and set as “call’ category As the code snippet shows, the malware creates a notification builder and then does the following: setCategory(“call”) – This means that the notification is built as a very important notification that needs special privilege. setFullScreenIntent() – This API wires the notification to a GUI so that it pops up when the user taps on it. At this stage, half the job is done for the malware. However, the malware wouldn’t want to depend on user interaction to trigger the ransomware screen, so, it adds another functionality of Android callback: Figure 3. The malware overriding onUserLeaveHint As the code snippet shows, the malware overrides the onUserLeaveHint() callback function of Activity class. The function onUserLeaveHint() is called whenever the malware screen is pushed to background, causing the in-call Activity to be automatically brought to the foreground. Recall that the malware hooked the RansomActivity intent with the notification that was created as a “call” type notification. This creates a chain of events that triggers the automatic pop-up of the ransomware screen without doing infinite redraw or posing as system window. Machine learning module indicates continuous evolution As mentioned, this ransomware is the latest variant of a malware family that has undergone several stages of evolution. The knowledge graph below shows the various techniques this ransomware family has been seen using, including abusing the system alert window, abusing accessibility features, and, more recently, abusing notification services. Figure 4. Knowledge graph of techniques used by ransomware family This ransomware family’s long history tells us that its evolution is far from over. We expect it to churn out new variants with even more sophisticated techniques. In fact, recent variants contain code forked from an open-source machine learning module used by developers to automatically resize and crop images based on screen size, a valuable function given the variety of Android devices. The frozen TinyML model is useful for making sure images fit the screen without distortion. In the case of this ransomware, using the model would ensure that its ransom note—typically fake police notice or explicit images supposedly found on the device—would appear less contrived and more believable, increasing the chances of the user paying for the ransom. The library that uses tinyML is not yet wired to the malware’s functionalities, but its presence in the malware code indicates the intention to do so in future variants. We will continue to monitor this ransomware family to ensure customers are protected and to share our findings and insights to the community for broad protection against these evolving mobile threats. Protecting organizations from threats across domains and platforms Mobile threats continue to rapidly evolve, with attackers continuously attempting to sidestep technological barriers and creatively find ways to accomplish their goal, whether financial gain or finding an entry point to broader network compromise. This new mobile ransomware variant is an important discovery because the malware exhibits behaviors that have not been seen before and could open doors for other malware to follow. It reinforces the need for comprehensive defense powered by broad visibility into attack surfaces as well as domain experts who track the threat landscape and uncover notable threats that might be hiding amidst massive threat data and signals. Microsoft Defender for Endpoint on Android, now generally available, extends Microsoft’s industry-leading endpoint protection to Android. It detects this ransomware (AndroidOS/MalLocker.B), as well as other malicious apps and files using cloud-based protection powered by deep learning and heuristics, in addition to content-based detection. It also protects users and organizations from other mobile threats, such as mobile phishing, unsafe network connections, and unauthorized access to sensitive data. Learn more about our mobile threat defense capabilities in Microsoft Defender for Endpoint on Android. Malware, phishing, and other threats detected by Microsoft Defender for Endpoint are reported to the Microsoft Defender Security Center, allowing SecOps to investigate mobile threats along with endpoint signals from Windows and other platforms using Microsoft Defender for Endpoint’s rich set of tools for detection, investigation, and response. Threat data from endpoints are combined with signals from email and data, identities, and apps in Microsoft 365 Defender (previously Microsoft Threat Protection), which orchestrates detection, prevention, investigation, and response across domains, providing coordinated defense. Microsoft Defender for Endpoint on Android further enriches organizations’ visibility into malicious activity, empowering them to comprehensively prevent, detect, and respond to against attack sprawl and cross-domain incidents. Technical analysis Obfuscation On top of recreating ransomware behavior in ways we haven’t seen before, the Android malware variant uses a new obfuscation technique unique to the Android platform. One of the tell-tale signs of an obfuscated malware is the absence of code that defines the classes declared in the manifest file. Figure 5. Manifest file The classes.dex has implementation for only two classes: The main application class gCHotRrgEruDv, which is involved when the application opens A helper class that has definition for custom encryption and decryption This means that there’s no code corresponding to the services declared in the manifest file: Main Activity, Broadcast Receivers, and Background. How does the malware work without code for these key components? As is characteristic for obfuscated threats, the malware has encrypted binary code stored in the Assets folder: Figure 6. Encrypted executable code in Assets folder When the malware runs for the first time, the static block of the main class is run. The code is heavily obfuscated and made unreadable through name mangling and use of meaningless variable names: Figure 7. Static block Decryption with a twist The malware uses an interesting decryption routine: the string values passed to the decryption function do not correspond to the decrypted value, they correspond to junk code to simply hinder analysis. On Android, an Intent is a software mechanism that allows users to coordinate the functions of different Activities to achieve a task. It’s a messaging object that can be used to request an action from another app component. The Intent object carries a string value as “action” parameter. The malware creates an Intent inside the decryption function using the string value passed as the name for the Intent. It then decrypts a hardcoded encrypted value and sets the “action” parameter of the Intent using the setAction API. Once this Intent object is generated with the action value pointing to the decrypted content, the decryption function returns the Intent object to the callee. The callee then invokes the getAction method to get the decrypted content. Figure 8. Decryption function using the Intent object to pass the decrypted value Payload deployment Once the static block execution is complete, the Android Lifecycle callback transfers the control to the OnCreate method of the main class. Figure 9. onCreate method of the main class decrypting the payload Next, the malware-defined function decryptAssetToDex (a meaningful name we assigned during analysis) receives the string “CuffGmrQRT” as the first argument, which is the name of the encrypted file stored in the Assets folder. Figure 10. Decrypting the assets After being decrypted, the asset turns into the .dex file. This is a notable behavior that is characteristic of this ransomware family. Figure 11. Asset file before and after decryption Once the encrypted executable is decrypted and dropped in the storage, the malware has the definitions for all the components it declared in the manifest file. It then starts the final detonator function to load the dropped .dex file into memory and triggers the main payload. Figure 12. Loading the decrypted .dex file into memory and triggering the main payload Main payload When the main payload is loaded into memory, the initial detonator hands over the control to the main payload by invoking the method XoqF (which we renamed to triggerInfection during analysis) from the gvmthHtyN class (renamed to PayloadEntry). Figure 13. Handover from initial module to the main payload As mentioned, the initial handover component called triggerInfection with an instance of appObj and a method that returns the value for the variable config. Figure 14. Definition of populateConfigMap, which loads the map with values Correlating the last two steps, one can observe that the malware payload receives the configuration for the following properties: number – The default number to be send to the server (in case the number is not available from the device) api – The API key url – The URL to be used in WebView to display on the ransom note The malware saves this configuration to the shared preferences of the app data and then it sets up all the Broadcast Receivers. This action registers code components to get notified when certain system events happen. This is done in the function initComponents. Figure 15. Initializing the BroadcastReceiver against system events From this point on, the malware execution is driven by callback functions that are triggered on system events like connectivity change, unlocking the phone, elapsed time interval, and others. Dinesh Venkatesan Microsoft Defender Research The post Sophisticated new Android malware marks the latest evolution of mobile ransomware appeared first on Microsoft Security. Continue reading...
-
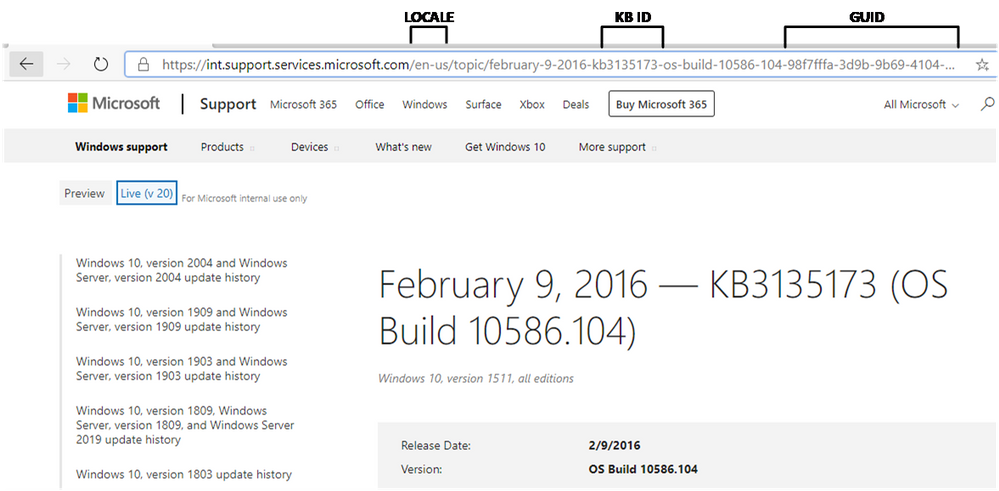
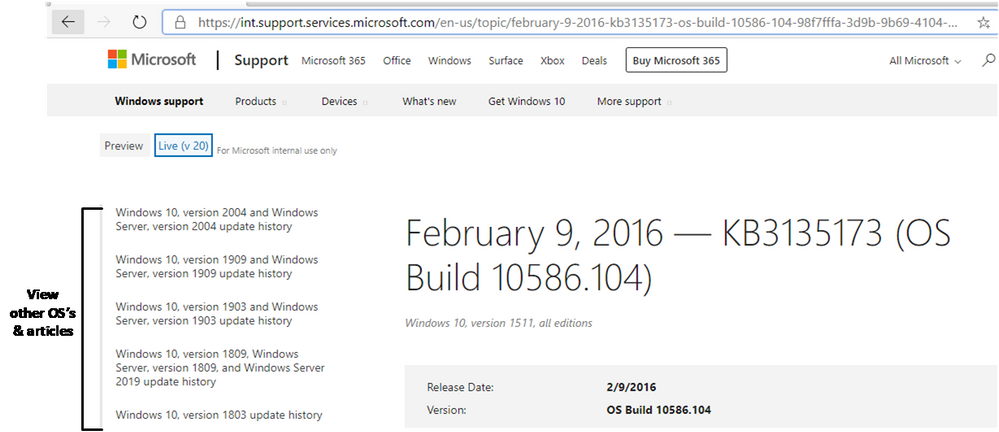
Microsoft has consolidated support.office.com and support.microsoft.com into a unified support site to make it easier for you to find support and troubleshooting resources for Microsoft 365. As part of this effort, you will see a number of changes and improvements to Windows release notes, the Windows update history pages, and related informational articles. Behind the scenes, we'll also be making foundational changes—to formatting, the user interface, and the type of metadata available. In addition to making it easier to locate relevant support articles when using a search engine, the consolidation of these two information experiences increases our ability to quickly publish new articles and keep existing articles up to date. There is nothing you need to do to benefit from these changes. We will begin to roll them out in the coming weeks. For those interested in the fine details, here are some of the changes you can expect. Authoritative URLs As you can see from the preview screenshot below, the knowledge base (KB) ID will be prominently displayed in the new URL structure and on the page itself. This makes it easier to search for support articles by KB ID and to distinguish one article from another when page titles look similar. New support article URL structure Our current URL structure is: http://support.microsoft.com/[locale]/help/[kb-id]/[url-title]. To find an article by KB ID, you simply append the KB ID to the root URL, https://support.microsoft.com/help. At times, however, KB IDs are not listed in the article itself, and can only be found within the KB URL. The tie between the KB ID is not as strongly associated with the article by search engines and articles can be more difficult to find. For greater consistency and to support improved search indexing, the URL structure moving forward will include both the GUID and the KB ID. Since many are familiar with appending the KB ID to the URL, we will continue to support this approach and use automatic redirects to ensure you land on the appropriate article. Greater ability to share You will continue to be able to share articles through email as you do today, but you will soon have the ability to share them on Facebook and LinkedIn using convenient share controls at the bottom of each page, as shown below: Share controls for support articles What's not changing While we are consolidating our content management system (CMS) and web endpoints, there is no change to our content delivery strategy. We will continue to release the following documentation: All existing release notes, including: Monthly security updates ("B" releases) Non-security updates (Preview releases) Out of band updates ("OOB" releases) [*]Existing support articles dating back to 2016, including informational and standalone articles, for supported operating systems. [*]New articles for supported operating systems and those supported by extended security updates (ESUs). [*]Content for existing channels, such as Windows Update, Microsoft Catalog, and Windows Server Update Services. We will also continue to localize the latest cumulative update and rollup articles in the same languages—and support the best parts of the existing user experience, such as the ability to: Quickly find related articles (or articles for other versions of Windows) Leave feedback in the form of a comment on an individual article Quickly find information for other versions of Windows with the Windows update history pages Metadata changes If you use tools to find our pages using metadata, the information below may help you with this transition. Articles will no longer be served as JSON objects Currently, support.microsoft.com serves articles in a JSON format and then renders them on the client. The new support.microsoft.com rendering service will not deliver articles in a JSON format. Instead, the articles will be rendered in HTML. Metadata will no longer be available in the JSON format Metadata related to the article will no longer be served as JSON. Instead, article metadata will be rendered in a block of meta tags similar to the following: A reduced set of metadata will be available in the page source The previous service exposed the entire JSON object for each article. The new service will expose a limited set of metadata as tags. Some metadata that was previously available in JSON will be available as rendered HTML. See the table below for a list of common metadata items and a description of how they will render on the new service. Previous item Description Rendering from previous service Rendering from the new service KB numbers Used as a unique KB ID for KB articles. id in JSON object and viewable on page Rendered in and elements if the KB was included in the article title Release date Date of article publication releaseDate in JSON object and viewable on page Rendered as HTML content Last updated Date of the most recent change publishedOn in JSON object and viewable on page Rendered as lastPublishedDate meta tag Applies to List of applicable operating systems (OS). supportAreaPaths and supportAreaPathNodes in JSON object and viewable on page as Applies To: string Rendered as HTML content Version OS build information releaseVersion in JSON object and viewable on page Rendered as HTML content Heading Title of article; heading is used for the title that is rendered on the page. Title is used for the title bar in the browser. There are also title attributes for each section. heading in JSON object and viewable on page as topic title Rendered in HTML content in both and elements Locale The language of the article. locale in JSON object Derived from URL. Not available in page content. We believe that these changes will make it easier for you to search for, and find, the resources you need to support and get the most out of your Windows and Office experience. Continue reading...
-
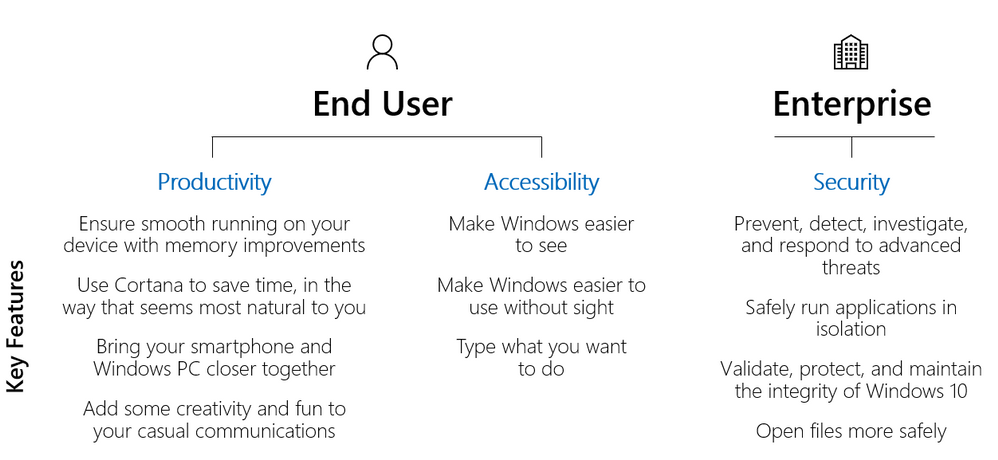
If you're looking or guidance on how to plan for new capabilities in Windows—and tie the benefits of staying up to date to real value for your end users and your business—this is the post for you. Today I'm going to walk you through existing resources available from Microsoft to help you plan for new and improved capabilities in the Windows operating system. I'll discuss best practices around notifying users, support teams, and business leaders depending on your deployment scenario—and offer tips on how to take advantage of the newest innovations. As part of the Windows 10 update process, IT pros focus their planning and preparation efforts towards validating critical line-of-business (LoB) applications, updating supporting infrastructure, and, in some instances, updating deployment tools and third-party endpoint solutions. Focusing on these critical tasks can make it challenging to keep track of new capabilities or features in the OS. Our vision for Windows as a service is to support IT pros to be more efficient with their approach to updates and enhance their end user’s experience. By staying current, customers can benefit from an agile deployment process, which allows IT pros to understand product improvements in each release more quickly and thoroughly. By adapting to the quicker cadence, IT pros can be more involved in the feature development process as they get access and testing capabilities of new features as soon as they are released. The impact on the end user’s experience becomes incremental, reducing the need for extensive employee retraining or IT resource effort. For upcoming Windows 10 feature updates, our recommended process for identifying, validating, and amplifying new capabilities includes the following tasks: Review what’s new in the most recent Windows 10 feature update by reading articles inside Windows 10 blogs (listed below) to identify the new capabilities or features applicable to your organization. Categorize new features and capabilities across productivity, accessibility, and security to determine who benefits from the new features. Validate new features and capabilities through a pilot deployment group. Amplify the most relevant features and capabilities coming to Windows 10 by creating targeted or broad communications. Use the Windows Insider for Business program to get an early look at what is coming in feature updates with Windows to assist with planning efforts for the next release. Review what’s new in Windows 10 When a Windows 10 feature update is made available, several blogs and articles are released the same day to showcase new features and capabilities. We suggest reviewing each of these articles to see what capabilities can be applied within your organization: What’s new in Windows 10 Windows 10 Blogs in Windows 10 Windows IT Pro Blog Windows 10 Accessibility Features Windows 10 Security Features You should also examine the features and functionality that Microsoft removed in Windows 10, as well as the features that are no longer being developed to determine if there is any immediate or future impact on endpoints. Categorize new features and capabilities Once new capabilities are understood, the next step is to categorize these features across productivity, accessibility, and security, and separate them into two areas – the benefit to end users and the benefit to the enterprise. Figure 1. List of highlighted capabilities with Windows updates New capabilities in Windows 10 feature updates enhance the end user experience by improving performance, using existing device features to provide new or better experiences, providing new OS features, or unlocking new functionality when managed by supporting infrastructures such as Configuration Manager or Microsoft Intune. Productivity Platform productivity gains are typically made by leveraging the device’s full capabilities and taking advantage of multitasking improvements. As device hardware is refreshed, new working methods can be discovered through different form factors or input types such as touch or inking. Over the span of Throughout several Windows 10 feature updates, improvements were made in the following areas to support those goals: Ensure smooth running on your device with memory improvements – Beginning with the Windows 10 May 2020 Update, we aim to ensure Microsoft Edge on Chromium continues to serve as a trusted browser for compatibility and performance. For users on the Chromium version of Microsoft Edge, we have decreased Microsoft Edge’s memory usage to improve the experience of multi-taskers. Use Cortana to save time, in the way that seems most natural to you – Your productivity assistant now has an updated chat-based interface where you can type or speak requests in natural language to save time finding what you need and staying on track. Cortana helps you connect with people, check your schedule, add tasks, set reminders, and more. Bring your smartphone and Windows PC closer together – Beginning with the Windows 10 May 2020 Update, you can now place, receive, or text replies to your incoming phone calls directly on your PC, reducing the need for switching context across multiple devices. Some existing features that may also be useful to your environment include: Easily get back to what you were working on – First introduced in the Windows 10 April 2018 Update, Timeline enhances Task View to show you currently running apps and past activity to quickly help you remember and jump into what you were last doing. Record steps to reproduce a problem – Steps Recorder, a feature present in the OS since Windows 7, lets you troubleshoot a problem on your device by recording the exact steps you took when the problem occurred, so you can get help from a support professional and get back to work. Accessibility Everyone should be empowered to use their devices to create and consume content and collaborate with their teams. At Microsoft, we are committed to making sure those who can be supported by our accessibility improvements know what exists for them and know what developments are coming next. The release of quality and feature updates helps Microsoft provide improvements in accessibility to end users. Here are examples of what is included in the Windows 10 May 2020 Update: Make Windows easier to see – Resize icons, adjust text size and color, customize the mouse cursor, and more—our display and vision settings make it easy to personalize your viewing experience. Make Windows easier to use without sight – Narrator is improved to make reading and browsing in Edge and Outlook much more natural and efficient. Type what you want to do – Microsoft Search lets you quickly access commands in Microsoft 365 applications without navigating the command ribbon. Security Windows feature updates provide enhanced security and capabilities to simplify administration or reduce administrative effort. When looking at what is new in Windows 10, version 2004, approximately 70% of the improvements provide IT pros with options to use in their environment. Consider looking for capabilities recently unlocked by updates or investments in supporting infrastructure, and improvements that address gaps filled by third-party software to reduce cost or effort. If one or more Windows 10 feature updates have been skipped, review the improvements of those feature updates in addition to the latest feature updates. The following sections highlight key security features enabled by Windows 10, versions 1809 to 2004 across that are selectively available in Windows 10 Enterprise E3 and in E5 licensing constructs that can provide additional benefit to your organization. Prevent, detect, investigate, and respond to advanced threats – Available since the Windows 10 Creators Update, Microsoft Defender Advanced Threat Protection allows you to discover vulnerabilities and misconfigurations in real-time, get expert-level threat monitoring and analysis, quickly move from alert to remediation, and block sophisticated threats and malware. This will be useful with the shift to a secure remote workforce that becomes more cloud capable. This feature requires Windows 10 Enterprise E5 licensing or other alternatives, as listed here. Safely run applications in isolation – Available since the April 2019 Update, Windows Sandbox is an isolated, temporary, desktop environment where you can run external software without the fear of the lasting impact on your PC. It ensures your host device remains secure and that everything is discarded once the application is closed. This can be useful during situations such as critical application testing for remote workers, or even everyday use when you are browsing through the web. Validate, protect, and maintain the integrity of Windows 10 – First introduced in the October 2018 Update, Secure Launch leverages Dynamic Root of Trust for Measurement to launch the OS into a trusted state. The May 2020 feature update provides increases in checks and measurements to allow you to reach further security hardening and to posture to protect sensitive resources. Open files more safely – Application Guard has been available since October 2017 to help protect your device from familiar and emerging threats by using containers to open files from potentially unsafe locations. With the May 2020 Update, Application Guard now provides support for Microsoft Edge on Chromium. Validate selected features and capabilities Once features and capabilities have been categorized, they can be presented to users during the Pilot Deployment phase of a feature update deployment. IT pros should include a mix of users who typically test devices and applications, as well as power users who are interested in supporting the new tools or features that will benefit the organization. This group’s feedback will help IT pros validate new features and capabilities and provide feedback on what additional context or ways of working can be included to show value in having the update deployed. This information can be included in broader communications discussed in the section below. Amplify new features and capabilities Once capabilities in the platform have been assessed and validated during pilot deployment, attention shifts to how to communicate these changes to users broadly. Factors that influence a company’s communication depend on the feature update deployment strategy and the time it takes to deploy the feature update to all devices. Typically, customers deploy feature updates using one of the following deployment strategies: Data-driven deployment (e.g. Desktop Analytics targeting deployment for defined audiences) Role-based deployment (e.g. updating devices for Finance teams during their off-peak times) Geography-based deployment (e.g. deploy by country or region) Company-wide deployment (e.g. if your organization is entirely ready for deployment all at once) For each deployment strategy, the communication approach can change based on the organizational culture and time taken to deploy the feature update. For example, for customers that deploy feature updates in less than a month to their entire organization, a single communication leveraging collaboration tools such as Teams, Yammer, or email can be the most effective way of informing users. For customers who deploy feature updates over a 6-, 12-, or 18-month period, communicating once to all users will be less effective due to the length of time between the communication being sent and the device’s update. The communication methods below are discussed in terms of their effectiveness for the different deployment strategies and deployment duration: Landing page - A landing page is useful to provide an on-demand resource that users can pull from when needed and can be used to provide information on new features, future update plans, efforts to improve user experience, and reductions in deployment times. Landing pages can also open opportunities to highlight company performance with features such as Productivity Score and endpoint analytics. Here is an example of how a typical landing page might look: Figure 2. Example “What’s new in Windows 10” landing page This communication approach is recommended for all deployment types. Company email – Team, region, or organization-wide emails can be used to give your end users a heads up of an upcoming deployment, how it might impact their working environment, and the benefits that will come from deploying the update. When a new feature update is available, Microsoft uses a targeted company email to share how many devices are currently updated in the organization, explain the user experience that comes with the update, and how it will impact the user based on the deployment tool used to apply the feature update to the device. Deployment emails are useful when you know which team(s) you might want to target or when there is a large announcement you want to make to everyone in the organization. Here is an example of how this might look: Figure 3. Windows 10 update team announcement email sample Note that the longer a deployment of a Windows 10 feature update takes in an organization, the less effective a single email will be to reach users and amplify new features within. Use Windows Insider for Business for an early look at new capabilities and features For organizations interested in reviewing and shaping improvements of Windows 10 feature updates ahead of release, the Windows Insider Program for Business program gives you the opportunity to review and validate pre-release features and validate critical application. To provide this functionality for end users, consider using an opt-in program that enables users to receive early access to new products within the organization. Our Microsoft Elite program allows users to opt-in to the program to provide our Engineering teams with feedback to make our products and services better. Summary We want your organization to have the best possible experience with Windows 10. This post aims to help make this easier by providing a process that you can use to find and convey the value of Windows 10 feature updates to your business leadership and users. I recommend that you consider using this process for each feature update planning cycle so that you can assess relevant features and engage more users at as faster cadence, which is even more possible when switching to cloud-based update management technologies. It is also useful to communicate with end users to continually gather feedback on what capabilities are working effectively for their environment and what needs improvements. Let us know if you find this article helpful below, and what other best practices your organization uses to communicate value with your users. Continue reading...
-
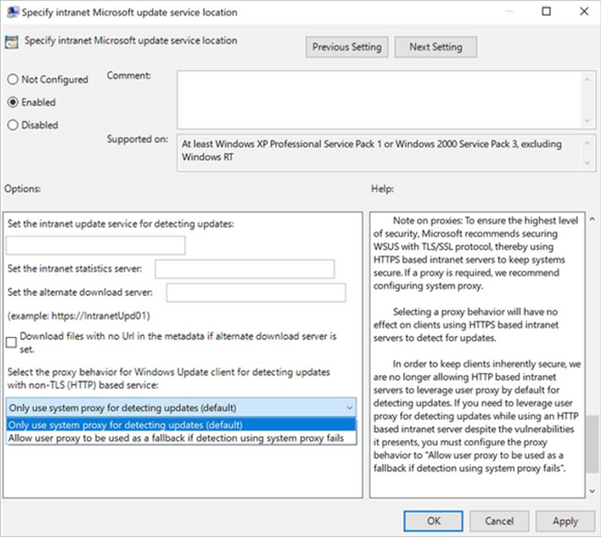
With the September 2020 cumulative update for Windows 10, we introduced changes that help improve the security of devices that scan Windows Server Update Services (WSUS) for their updates. This post will describe those changes, outline the actions you need to take to ensure your devices continue to scan for updates, and offer basic recommendations to help you better secure the devices in you organization. Secure by default First, beginning with the September 2020 cumulative update, HTTP-based intranet servers will be secure by default. To ensure that your devices remain inherently secure, we are no longer allowing HTTP-based intranet servers to leverage user proxy by default to detect updates. If you have a WSUS environment not secured with TLS protocol/HTTPS and a device requires a proxy in order to successfully connect to intranet WSUS Servers—and that proxy is only configured for users (not devices)—then your software update scans against WSUS will start to fail after your device successfully takes the September 2020 cumulative update. Recommendations for greater security To help ensure the security of your WSUS infrastructure, Microsoft recommends using the TLS/SSL protocol between your devices and your WSUS servers. The Microsoft Update system (including WSUS) relies on two types of content: update payloads and update metadata. Update payloads are the data files that contain the software update components that make up the update. Update metadata is all the information that the Microsoft Update system needs to know about the updates, including which updates are available, which devices each update can be applied to, and where to retrieve the payloads for each update. Both types of content are crucial and they both need to be protected to help keep your computers secure and up to date. Update payloads are protected against modification by multiple means, including digital signature checks and cryptographic hash verifications. HTTPS provides a proper chain of custody which the client uses to prove the data is trusted. When a device receives updates directly from Microsoft Update, that device receives update metadata directly from Microsoft servers. This metadata is always transmitted via HTTPS to prevent tampering. When you use WSUS or Configuration Manager to manage your organization's updates, the update metadata travels from Microsoft servers to your devices via a chain of connections. Each one of these connections needs to be protected against malicious attacks. Your WSUS server connects with Windows Update servers and receives update metadata. This connection always uses HTTPS, and the HTTPS security features guard the metadata against tampering. If you have multiple WSUS servers arranged in a hierarchy, the downstream servers receive metadata from the upstream servers. Here, you have a choice: you can use HTTP or HTTPS for these metadata connections. Using HTTP; however, can be very dangerous as it breaks the chain of trust and can leave you vulnerable to attack. Using HTTPS enables the WSUS server to prove that it trusts the metadata it receives from the upstream WSUS server. In order to maintain the chain of trust and prevent attacks on your client computers, you must ensure that all metadata connections within your organizations – the connections between upstream and downstream WSUS servers, and the connections between the WSUS servers and your client computers – are defended against attacks. To do so, we highly recommend that you configure your WSUS network to protect these connections using HTTPS. To learn more, see Michael Cureton’s post Security best practices for Windows Server Update Services (WSUS). Even with HTTPS configured, it is still very important that you utilize a system-based proxy rather than a user-based proxy if a proxy is needed. When using a user-based proxy, a user, even one without elevated privileges, could intercept and manipulate the data being exchanged between the update client and the update server. Recommendations for those who absolutely need user proxy If you do need to leverage a user-based proxy to detect updates while using an HTTP-based intranet server, despite the vulnerabilities it presents, make sure to configure the proxy behavior to "Allow user proxy to be used as a fallback if detection using system proxy fails." Group Policy path: Windows Components>Windows Update>Specify intranet Microsoft update service location Configuration Service Provider path: Update/ SetProxyBehaviorForUpdateDetection Next steps If you are an IT administrator who currently manages an HTTP-configured WSUS environment and relies on user-based proxy for client scans, please consider taking one of the following actions as soon as possible. If none of these actions are taken your devices will stop successfully scanning for software updates after the September 2020 security update. Options to ensure that devices in your environment can continue to successfully scan for updates: Secure your WSUS environment with TLS/SSL protocol (configure servers with HTTPS). Set up system-based proxy for detecting updates if needed. Continue reading...
-
We have heard your feedback and understand your need to focus on business continuity in the midst of the global pandemic. As a result, we have decided to delay the scheduled end-of-service date for the Enterprise, Education, and IoT Enterprise editions of Windows 10, version 1803. This means that security updates will continue to be released monthly until May 11, 2021. The final security update for these editions of Windows 10, version 1803 will be released on May 11, 2021 instead of November 10, 2020. Security updates for Windows 10, version 1803 will be available via our standard servicing outlets: Windows Update, Windows Server Update Services, and the Microsoft Update Catalog. You will not need to alter your current update management workflows. After May 11, 2021, devices running the Enterprise, Education, and IoT Enterprise editions of Windows 10, version 1803 will no longer receive security updates. Organizations should plan to update their devices to the latest version of Windows 10 to remain supported after this date. For a comprehensive list of end-of-service dates for all versions and editions of the Windows client and Windows Server operating systems, bookmark the Windows lifecycle fact sheet or use the Microsoft Lifecycle Policy search tool to find lifecycle information for all commercial Microsoft products. We also recommend you bookmark the Windows message center and follow @WindowsUpdate for the latest news and announcements. Continue reading...
-
Windows 10, version 20H2, is now available for commercial customers to begin feature exploration and validation prior to being released for general availability. As previously announced, version 20H2 will be delivered to devices currently running Windows 10, version 2004 using an enablement package. This is the same technology we used to update devices from Windows 10, version 1903 to version 1909. Do you want to see how quickly devices update from version 2004 to version 20H2, and how little downtime is involved? Do you want to explore the new Local Users and Groups mobile device management (MDM) policy, which allows administrators to make granular changes to a local group on a managed device? Now you can! You can access Windows 10, version 20H2 through all standard outlets, including Windows Update, Windows Server Update Services (WSUS), and Azure Marketplace, or you can download an ISO file. If you manage updates directly from Windows Update, or have devices enrolled in the Beta Channel (previously the Slow ring) or the Release Preview Channel for validation purposes, you don’t need to take any action. Windows 10, version 20H2 will be automatically deployed to all commercial devices in the Beta and Release Preview Channels and those who have devices on Windows 10, version 2004 will get to experience the remarkably fast update that comes with moving from version 2004 to version 20H2 via an enablement package. Note: We consider a device a commercial device if it isn’t running the Home edition of Windows 10, is being managed by an IT administrator (whether via Microsoft Endpoint Manager or a third-party MDM tool), or if the device has a volume license key, a CommercialID, or is joined to a domain. As with Windows 10, versions 1903 and 1909, versions 2004 and 20H2 share a common core operating system with an identical set of system files. New features are included in monthly quality updates for version 2004 in an inactive and dormant state. These new 20H2 features remain dormant until they are turned on through the “enablement package,” a small, quick-to-install “master switch” that activates the Windows 10, version 20H2 features. The enablement package is a great option for installing a scoped feature update like Windows 10, version 20H2 as it enables an update from version 2004 to version 20H2 with a single restart, reducing update downtime. If you are managing updates with WSUS, you will have the option of taking a full feature update to 20H2 or testing out the enablement package path. As with any other validation done on pre-release updates published to WSUS, you will need to first ensure that you have synced the “Windows Insider Preview” category. Once you have synced this category, you should see the following updates show up in your console as shown below: Note: Windows 10, version 20H2 will be made available as an enablement package to devices already running Windows 10, version 2004 that have also installed the June 2020 monthly quality update. It will be available as a full feature update for devices running Windows 10, version 1909 and prior. To see the greatest number of new features, we recommend being on the latest cumulative update. To test out this experience on a virtual machine, check out the Windows 10 Preview on Azure Marketplace or, if you would prefer, you can download the Windows 10, version 20H2 ISO. We not only want to ensure that you have access to the upcoming Windows 10 feature update payload via any channel you may use today, we also want to enable you to validate with confidence. Therefore, customers in the Windows Insider Program for Business can once again receive Microsoft Support for the Windows 10, version 20H2 build available through WSUS, ISO download, Azure Marketplace, and directly from Windows Update in the Beta and Release Preview Channels. If you run into a severe issue that prevents you or other users in your organization from using a device, or compromises security or personal data, use the online form to request assistance directly from Microsoft Support—at no cost to you. We hope you enjoy Windows 10, version 20H2! ~ The Windows Insider Program for Business team For more information, check out these useful links for exploring and validating pre-release Windows feature updates: Learn how to manage pre-release using the Windows Insider Program Manage Insider Preview builds across your organization Get support for 20H2 builds The Windows Insider Program for Business Publishing pre-release Windows 10 feature updates to WSUS Continue reading...
-
On June 15, 2020, Windows introduced Windows Insider Channels, which change the way we release new builds to all Windows Insiders. We are converting our current ring model, based on the frequency of builds, to a new channel model that pivots on the quality of builds and will better support parallel coding efforts. The goal of this blog post is to provide clarity for existing and new Windows Insiders as you choose the channel experience that is right for you. We want to provide clear guidance on how IT administrators can leverage the Windows Insider Program and the new channels to get ahead. Specifically, we want to share how you, as an IT administrator, can leverage the new Dev Channel, Beta Channel, and Release Preview Channel, and how your policies can map to these channels. Image depicting a comparison of key characteristics for Dev, Beta, and Release Preview Channels, and how those channels map to the rings previously used for the Windows Insider Program Note: Release Preview builds are only supported for IT administrators enrolled in the Windows Insider Program for Business. Explore new features using the Beta Channel The Beta Channel is recommended for IT administrators who want to explore new features as they are being created, and for those who want to provide feedback with maximum impact to help shape the product. We recommend that you enroll a small subset of devices in the Beta Channel. These devices can be within the IT department or with end users who are Windows enthusiasts and enroll their devices. Updates from the Beta Channel will be tied to the upcoming Windows 10 version. Users on Beta Channel will receive security updates to ensure preview builds stay patched in line with production software. To receive Beta Channel builds via Windows Update for Business, follow these steps: Enable preview builds. Type Policy Name Configure to Group Policy Windows Update > Windows Update for Business > Manage preview builds Enable preview builds Configuration service provider (CSP) Update/ManagePreviewBuilds 2, Enable preview builds Table showing configuration settings to enable preview builds using Group Policy or CSP Configure policies to receive Beta builds. Type Policy Name Configure to Group Policy Windows Update > Windows Update for Business > Select when Preview Builds and Feature Updates are received > Select the Windows readiness level for the updates you receive Preview build – Slow CSP Update/BranchReadinessLevel 4, Windows Insider build – Slow Table showing configuration settings required in Group Policy or configuration service provider to get Beta builds Note: Due to the nature of Group Policy templates and configuration service provider policies, the naming in management tools will change with a new Windows 10 version release. Prior to this change, IT administrators will have to set “Preview build – Slow" in Group Policy or “Windows Insider build – Slow” in configuration service policies to get Beta builds. Validate the upcoming release using the Release Preview Channel Having devices in the Beta Channel allows you to explore upcoming features as they are being created; however, you may decide to focus your validation efforts on a version of Windows 10 that is about to be released. In that case, we recommend that you have a set of devices on the Release Preview Channel. This channel allows you to validate the next version of Windows 10 a few months prior to release, and the release is supported for IT administrators enrolled in the Windows Insider Program for Business. We recommend that 1% of your organization’s devices run on Release Preview. Ideally, this 1% is a diverse group of devices that represents the hardware and software used across your organization. To fully leverage Release Preview, utilize your preferred management tool with your typical policy set. This will ensure that you can validate the upcoming release and that your policies and rollout process are working as expected prior to release. To get Release Preview builds, leverage Windows Update for Business, Windows Server Update Service (WSUS), or Azure Marketplace, or utilize ISOs. Regardless of which method you use to install Release Preview builds, these builds will be the same, and will have the same quality level and release cadence. Use Windows Update for Business to deploy Release Preview builds Enable preview builds. Type Policy Name Configure to Group Policy Windows Update > Windows Update for Business > Manage preview builds Enable preview builds Configuration service provider Update/ManagePreviewBuilds 2, Enable preview builds Table showing configuration settings to deploy Release Preview builds using Group Policy or configuration service provider Configure policies to receive Release Preview builds. Type Policy Name Configure to Group Policy Windows Update > Windows Update for Business > Select when Preview Builds and Feature Updates are received > Select the Windows readiness level for the updates you receive Release Preview Configuration service provider Update/BranchReadinessLevel 8, Release Preview Insider build Table showing configuration settings required in Group Policy or configuration service provider to get Release Preview builds Use WSUS and Configuration Manager to deploy Release Preview builds Enable the Windows Insider Pre-Release product. In the Products tab of Software Update Point Component Properties, select the box next to Windows Insider Pre-Release. How Windows Insider Pre-Release builds appear in WSUS From the list of Windows 10 updates in WSUS, select "Windows Insider Pre-release Feature Update". If you manage your organization’s deployments using Microsoft Endpoint Configuration Manager, use the same procedure you currently use to deploy any other Windows 10 feature update (Software Library > Overview > Windows 10 Servicing > All Windows 10 Updates). Once you reach the list of All Windows 10 Updates, you will see an option for “Windows Insider Pre-release Feature Update to Windows 10 Version 2004.” Deploy the release the same way you would deploy any other feature update. Create Release Preview virtual machines (VMs) with Azure Marketplace To create a VM based on a specific Release Preview build, visit the Azure Marketplace and either search for "Windows 10 Preview" or select Products > Windows 10 Preview. Windows 10 Preview in the Azure Marketplace Download Release Preview ISOs Visit the Windows Insider Program website and select the ISOs labeled from the Release Preview Channel. ISOs are typically released for Release Preview builds within a week of being shipped via Windows Update. Submit feedback For any major issues that may become deployment blockers after a feature update is released, IT administrators can use the Microsoft Support option for the Release Preview build of the upcoming Windows 10 release. To provide feedback, search for “Feedback Hub” using the search bar in Windows 10. In Feedback Hub, you can report problems and suggest features, quickly navigate to the Windows Insider site, and find more ways to connect with the Windows Community. Screenshot of Feedback Hub Select Feedback in the left pane. Then you can enter your feedback in the fields provided and explore additional information and feedback. Screenshot of feedback options in Feedback Hub We appreciate your new or continued support of the Windows Insider Program for Business. Please let us know what we can do to best meet your needs for feature exploration and validation of upcoming feature updates prior to release. For additional information: Manage Windows 10 Insider Preview Builds Publishing pre-release Windows 10 feature updates to WSUS Getting the May 2020 Update Ready for Release Continue reading...
-
Today we are excited to announce the public preview of Universal Print, a Microsoft 365 service that enables an intuitive, rich, and secure print experience for users, while helping IT reduce time and effort. Organizations moving to the cloud with Microsoft 365 have responded en masse since we announced the private preview of Universal Print in March, and today we have more than 2,500 customers testing the new service. Many of them have accelerated their adoption of cloud services and Universal Print because employees and teachers working from home can now print to company or school printers from anywhere when connected to the internet. While many processes have gone paperless, many critical business processes – especially in education, healthcare, and other industries – still require print. What is Universal Print? Universal Print provides a user-friendly, easy print experience that also: Eliminates the need to install printer drivers because it is built into the Windows experience Helps you to find printers both near and outside of your current location Enables print from zero-trust networks via single sign-on (SSO) when connected to the internet and authenticated to Azure Active Directory (Azure AD). For IT professionals who are managing print, Universal Print offers: A print solution to unblock the move to the cloud and support print for Azure AD users. Managed printing in zero-trust networks. Eliminates the need to manage print servers or the need for complex hybrid print solutions. A centralized portal that enables robust management capabilities. Visibility and insights into your print with reporting. Print data stored in the same manner as other Microsoft Office data, in accordance with Microsoft’s data management guidelines. Printer deployment and default printer configuration on end-user devices using Microsoft Endpoint Manager (Microsoft Intune). The ease of sharing a printer with Universal Print Universal Print public preview rolling out globally We are ready to roll out the Universal Print public preview to data centers in North America, Europe, and Asia Pacific in waves over the next weeks. We will start with Microsoft 365 E5 and A5 tenants, followed by customers who have a Microsoft 365 E3 or A3 subscriptions, and then those who have Windows 10 E3, A3 and E5 only subscriptions. And finally, we will complete the roll-out with Microsoft 365 Business Premium and Microsoft 365 Firstline F3 customers. Details will be published on the Universal Print release page, where you can start your journey with us. Partners are essential to Universal Print Universal Print partners Customers are not the only ones getting onboard. The service opens opportunities to many partners who are selling print solutions to Microsoft 365 customers. Partners are hard at work to integrate cloud solutions, software solutions, and printers with Universal Print. For existing printers, customers can simply use a Universal Print connector application that connects printers to Universal Print. It is available for download and can be installed on any Windows 10 PC, learn more here. However, Printers that natively support Universal Print will offer the best cloud experience. Brother is actively working on native device support for Universal Print. “Brother is working with Microsoft to offer integration with the Universal Print service on select Brother devices in order for organizations to manage their print infrastructure through Microsoft 365 cloud services. This integration should be complete in early 2021.” -- Frank Martin, Senior Director, Solutions Development Business Machine Group Canon Inc. joined the Universal Print effort as a part of the private preview in March, and today is reaffirming its commitment to integrate with Universal Print: “Canon, a leader in digital imaging solutions, will support the Universal Print solution natively with current imageRUNNER ADVANCE products beginning in 2H 2020. uniFLOW Online Express, a free SaaS solution running on Microsoft Azure, can provide device authentication, print/copy/scan/fax reporting, and scan to myself while using Universal Print.” -- Isamu Sato, Senior General Manager, Digital Printing Business Operations, Canon Inc. In addition, HP Inc. announced it will work with Microsoft to build a cloud-to-cloud integration with Universal Print and the HP Managed Print Cloud Services platform. Through this collaboration, organizations will be able to increase security, manage devices, and limit print jobs to authorized users. “By collaborating with Microsoft to integrate Universal Print with HP Managed Print Cloud Services, we’re providing our customers with the flexibility to choose the solution that best suits their needs. This cloud-to-cloud integration will enable Universal Print users to print virtually anywhere, simply and securely.” -- David Prezzano, General Manager and Global Head, Print Services and Solutions Category, HP Inc. Kofax will be integrating Kofax ControlSuite with Universal Print: “Kofax ControlSuite and Universal Print represent the future of work, providing customers a modern print infrastructure delivered through cloud services. Customers benefit from Microsoft’s cloud services while Kofax ControlSuite provides a single print management, cognitive capture and output management platform across the enterprise, resulting in reduced cost of ownership and improved, secure experiences for employees.” -- Chris Huff, Chief Strategy Officer at Kofax. Konica Minolta is partnering with Microsoft to integrate digital workplace services with Universal Print: Konica Minolta is excited about the Universal Print technology from Microsoft that enhances our cloud printing services to the next level. Konica Minolta provides multifunction printers with hybrid print solution, unified technology of on-premises and cloud printing, to add more value to Universal Print - such as print management, secure printing and print-from-anywhere incl. home office to make remote work efficiently. Konica Minolta’s hybrid solution and services with Universal Print help customers digital transformation from on-premises to cloud smoothly to keep pace with customer’s maturity level. -- Kazuo Taira, General Manager Digital Workplace Business at Konica Minolta Today, Lexmark announces availability of firmware updates for currently marketed devices to provide native Universal Print support: “Aligning with a cloud strategy is key for our customers as they continue down their journey for document optimization and infrastructure consolidation. Lexmark has a full product portfolio of devices that enable our customers to place the right device where it’s required within their business process. In partnership with Microsoft, we are committed to supporting initiatives such as Universal Print and working together on many other offerings to continue to enable digital transformation for our customers.” -- Larry Early, director, Lexmark software and industry marketing NT-ware, a member of the Canon Group, is working on integration with Universal Print for uniFLOW Online. “Cloud technology is the future and Universal Print is another excellent proof that traditional server infrastructure can be moved to the cloud while simultaneously providing new benefits to organizations. uniFLOW Online supports Universal Print and is the answer for businesses seeking enhanced functionality, such as secure printing and scanning, all hosted in Azure.“ -- Karsten Huster, CEO, NT-ware PaperCut is building a native Universal Print connector: "PaperCut brings all the print management power you need to give you the best Universal Print experience. The integration’s built in, making it easy for customers to track, control, and secure their Universal Print jobs." -- Jamie McClunie, Product Manager PaperCut Pharos started on the cloud print path in 2013 and is now partnering with Microsoft on Universal Print: Microsoft and Pharos share a vision of a world in which printing is simple, secure, and free of print servers. We look forward to supporting our customers who plan to use Universal Print and Azure Active Directory to simplify their printing operations. -- Kevin Pickhardt, CEO, Pharos Ringdale is partnering with us to integrate FollowMe: "Strategically partnering with Microsoft allows Ringdale to augment Universal Print with our security and compliance features that are essential for large enterprises that are transforming their workplaces. Our customers and partners will be able to take advantage of Universal Print with their existing printing fleets." -- Jan Bollmann, Executive Vice President at Ringdale Y Soft is announcing availability of YSoft OMNI BridgeTM, a serverless edge device that instantly connects in-market printers to Universal Print, with YSoft OMNI UP365TM, the first of YSoft OMNI AppsTM: "For companies to accelerate Digital Transformation and take advantage of the Universal Print ecosystem today, they need their existing printer fleets to connect with Universal Print natively or keep maintaining costly on-premises infrastructure. With the YSoft OMNI SeriesTM product family, in particular YSoft OMNI Bridge, a serverless edge device, and YSoft OMNI UP365TM we are proud to work with Microsoft to address the need to support in-market printers with an instant and cost effective way to connect to Universal Print -- truly providing businesses with the Future of Print!" -- Bruce Leistikow, Director Product Marketing, Y Soft There is a lot of excitement in the print industry with the introduction of Universal Print as part of Microsoft 365. Give Universal Print a try and let us know how it works for you! If you would like to participate in the public preview, go aka.ms/UP_TryNow for the details. If you are already part of the private preview, your Universal Print service will continue to work. We invite you to join our other customers and partners in the Universal Print Tech Community to discuss your experiences, ask questions or get support. Universal Print is a fully supported service, even during public preview. This is also where the Universal Print team is sharing what they are working on, and where you can engage with them and share feedback, questions, and requests. For more technical details and requirements, see the Universal Print documentation. Continue reading...
-
Windows 10, version 1909 is now available through Windows Server Update Services (WSUS) and Windows Update for Business, and can be downloaded from Visual Studio Subscriptions, the Software Download Center (via the Media Creation Tool[1]), and the Volume Licensing Service Center (VLSC)[2]. We recommend IT administrators begin targeted deployments of Windows 10, version 1909 to validate that the apps, devices, and infrastructure used by their organizations work as expected with the new features. As recently announced in blogs by John Cable and John Wilcox, Windows 10, version 1909 can be delivered in a new, streamlined fashion to devices currently running Windows 10, version 1903. For details on this new delivery approach, read John Wilcox’s blog post on Windows 10, version 1909 delivery options. The update process will be the same as previous feature updates for devices running Windows 10, version 1809 and older—or if you choose to deploy Windows 10, version 1909 from media. Today marks the start of the servicing timeline for this Semi-Annual Channel release. By updating to Windows 10, version 1909, devices running the Enterprise and EDU editions will receive 30 months of support. (Devices running the Home, Pro, Pro for Workstations, Pro Education, and IoT Core will receive the standard 18 months of support.) For more details, see the Windows lifecycle fact sheet. New features in Windows 10, version 1909 As you begin to roll out this new update to your organization, here are some of the new, key features and enhancements that will allow you to benefit from intelligent security, simplified updates, flexible management, and enhanced productivity. Calendar – You can now create new events in your Calendar app by clicking the date and time on the Taskbar. Cloud Clipboard[3] – Let’s face it, you work on multiple devices. With this feature enabled, you can copy text, links, graphics – just about anything! – from one device and paste it onto another. Or you can go back and view the history of what’s recently been copied. You can use Cloud Clipboard with either an Azure Active Directory (Azure AD) account or Microsoft Account (MSA). CPU rotation – A CPU may have multiple “favored” cores. To provide better performance and reliability, we’ve implemented a rotation policy that distributes the work more fairly among the favored cores. Digital assistants – Third-party digital assistants can activate above the Lock screen using your voice commands. Reduced inking latency – We’ve reduced inking latency by basing latency on the hardware capabilities of the devices rather than the latency selected on typical hardware configuration by the OS. Intel processor debugging – We’ve added additional debugging capabilities for newer Intel processors, for our OEM partners and hardware manufacturers. Kiosk mode – Users can customize their experience in Kiosk mode, while keeping their devices locked down. For example, you can allow a user to switch to a different language while blocking access to network settings. Microsoft BitLocker key rolling – BitLocker and Mobile Device Management (MDM) with Azure AD[4] work together to protect your devices from accidental password disclosure. Now, a new key-rolling feature securely rotates recovery passwords on MDM-managed devices. The feature is activated whenever a BitLocker-protected drive is unlocked using Microsoft Intune/MDM tools or a recovery password. As a result, the recovery password will be better protected when users manually unlock a BitLocker drive. Narrator – Narrator and other assistive technologies can now detect the location of the dedicated FN key, and determine if it is locked or unlocked. Notifications – We’ve made several improvements to manage and configure notifications: There is now a “Manage Notifications” button at the top of Action Center. You can configure and turn off notifications directly from the notification, both from the banner and from Action Center. The default sorting for notification senders will be by most recently shown notification, rather than sender name. [*]Windows 10 Pro and Enterprise in S mode – You can deploy and run traditional Win32 (desktop) apps without leaving the security of S mode by configuring the Windows 10 in S mode policy to support Win32 apps, then deploy them with Mobile Device Management (MDM) software such as Microsoft Intune[5]. [*]Windows Defender Credential Guard – Windows Defender Credential Guard is now available for ARM64 devices, for additional protection against credential theft for enterprises deploying ARM64 devices in their organizations, such as Surface Pro X. [*]Windows Sandbox – Windows Sandbox is an isolated desktop environment where you can install software without the fear of lasting impact to your device. This feature is available in Windows 10, version 1903. In Windows 10, version 1909 you have even more control over the level of isolation. [*]Windows Search – The Search box in Explorer is now powered by Windows Search, allowing results to include online OneDrive content. Additionally, the results appear instantly as you type. 11.21.2019 Editor's note: We have updated this section to remove an error. Windows Sandbox does not support mixed-container scenarios at this time. What else have we been up to? To complement your Windows 10, version 1909 experience, we’ve been busy with other new, exciting products and features that you may have heard about! Windows Virtual Desktop[6] – Windows Virtual Desktop is now generally available. Windows Virtual Desktop is a comprehensive desktop and app virtualization service running in the cloud. It’s the only virtual desktop infrastructure (VDI) that delivers simplified management, multi-session Windows 10, optimizations for Office 365 ProPlus, and support for Remote Desktop Services (RDS) environments. Deploy and scale your Windows desktops and apps on Azure in minutes and get built-in security and compliance features. Desktop Analytics[7] – Desktop Analytics is now generally available. Desktop Analytics is a cloud-connected service, integrated with Configuration Manager, that gives you data-driven insights to the management of your Windows endpoints. It provides insight and intelligence that you can use to make more informed decisions about the update readiness of your Windows endpoints. Microsoft Connected Cache – Together with Delivery Optimization, Microsoft Connected Cache installed on your Configuration Manager distribution point, Windows Server, or Linux Server can seamlessly offload your traffic to local sources, caching content efficiently at the byte range level. Connected Cache is a “configure once and forget it” solution that transparently caches content that your devices on your network need. Microsoft Endpoint Manager – As announced at Microsoft Ignite, Microsoft Endpoint Manager is a single, integrated endpoint management platform for managing all of your endpoints. We’re bringing Configuration Manager and Microsoft Intune together and removing the migration barriers to allow you to leverage your existing Configuration Manager investments, while taking advantage of the power of the Microsoft cloud. Frequently asked questions On Tuesday, November 19, 2019 from 9:00-10:00 AM Pacific Time, we will be hosting a live Windows 10 Ask Microsoft Anything (AMA) event on the Tech Community. This event is your opportunity to talk to the engineers and product managers—and ask them any questions you may have about update management, deployment, device management, identity management, policy settings, you name it. To participate, visit Sign in to your account at 9:00 AM on November 19th, sign in to Tech Community, and post your questions! We’ll have members of the Windows Autopilot, Microsoft Endpoint Manager, Microsoft Defender ATP, Microsoft Edge, Windows Servicing & Delivery, and other teams standing by to provide answers. In the meantime, here are some answers to frequently asked questions that come up when we release a Windows 10 feature update. Is there also a Windows Server release with this release? Yes. The next Windows Server semi-annual channel (SAC) release is also available today. The Windows Server semi-annual channel is designed for customers who wish to take advantage of new operating system capabilities at a faster pace. Windows Server, version 1909 is focused on reliability, performance and other general improvements. It will be available from Azure Marketplace or the VLSC. Will there be a new Long-Term Servicing Channel (LTSC) release? No. Windows 10 Enterprise LTSC 2019 is the current LTSC option, and was released with Windows 10, version 1809 in November of 2018. The next LTSC release can be expected toward the end of 2021. Customers currently using the LTSC for special-purpose devices should start working to upgrade those devices to Windows 10 Enterprise LTSC 2019 as mainstream support for that release will continue until January 9, 2024. Can I upgrade our devices from Windows 7 directly to Windows 10, version 1909? Yes. You can directly upgrade from Windows 7 to Windows 10, version 1909. We strongly encourage you to begin your upgrade process immediately to avoid missing the January 14, 2020 end-of-support date for Windows 7. How can I preview versions of Windows 10 before they become available? I want to start testing these new features early so I can deploy them when they are released! The Windows Insider Program for Business team enables IT administrators to view and provide feedback on upcoming security, management, and productivity features ahead of release. Plus you can manage the installation of Windows 10 Insider Preview Builds across multiple devices in your organization using WSUS and Configuration Manager. For more information, see Publishing pre-release Windows 10 feature updates to WSUS. Kits, tools, and resources Windows 10, versions 1903 and 1909 share a common core operating system with an identical set of system files (again, see Windows 10, version 1909 delivery options for details), you can continue to use the Windows Assessment and Deployment Kit (Windows ADK) for Windows 10 that was released with Windows 10, version 1903 for Windows 10, version 1909. This applies to developer kits, like the Windows HLK, HCK, and WinDbg. We will, however, be updating the following resources for this release: Windows 10 Enterprise Evaluation (free 90-day evaluation) – available now Security baseline for Windows 10, version 1909 and Windows Server, version 1909 – available in the coming week The Windows release health dashboard has also been updated so that you can easily see and track any known issues for Windows 10, version 1909 until they are mitigated and resolved. To see a summary of the latest documentation updates, see What’s new in Windows 10, version 1909 IT pro content on Docs. [1] Update Assistant support for Windows 10, version 1909 will be available the week of November 18, 2019. [2] It may take 24 hours for downloads to be fully available in the VLSC across all products, markets, and languages. [3] Cloud Clipboard requires users to be signed into all devices using either MSA or AAD. Users must be signed into the same account across all devices. [4] Sold separately [5] Sold separately [6] Windows Virtual Desktop requires a Microsoft E3 or E5 license, or a Microsoft 365 E3 or E5 license, as well as an Azure tenant. Each sold separately. [7] Desktop Analytics requires a Windows E3 or E5 license, or a Microsoft 365 E3 or E5 license; sold separately. Continue reading...
-
Here is an article showing how to convert the file: https://theitbros.com/convert-windows-esd-file-to-windows-wim-file/
-

After Microsoft support for Windows 7 finishes
AWS replied to Kick's topic in Tech Help and Discussions
You will have no problems using them. I haven't used Windows in a few years and have no problem syncing my One Drive files on my Mac. Microsoft doesn't care what OS you use. -
On May 14, Microsoft released fixes for a critical Remote Code Execution vulnerability, CVE-2019-0708, in Remote Desktop Services – formerly known as Terminal Services – that affects some older versions of Windows. In our previous blog post on this topic we warned that the vulnerability is ‘wormable’, and that future malware that exploits this vulnerability could propagate from vulnerable computer to vulnerable computer in a similar way as the WannaCry malware spread across the globe in 2017. Microsoft is confident that an exploit exists for this vulnerability, and if recent reports are accurate, nearly one million computers connected directly to the internet are still vulnerable to CVE-2019-0708. Many more within corporate networks may also be vulnerable. It only takes one vulnerable computer connected to the internet to provide a potential gateway into these corporate networks, where advanced malware could spread, infecting computers across the enterprise. This scenario could be even worse for those who have not kept their internal systems updated with the latest fixes, as any future malware may also attempt further exploitation of vulnerabilities that have already been fixed. It's been only two weeks since the fix was released and there has been no sign of a worm yet. This does not mean that we’re out of the woods. If we look at the events leading up to the start of the WannaCry attacks, they serve to inform the risks of not applying fixes for this vulnerability in a timely manner. Our recommendation remains the same. We strongly advise that all affected systems should be updated as soon as possible. It is possible that we won’t see this vulnerability incorporated into malware. But that’s not the way to bet. EternalBlue Timeline Almost two months passed between the release of fixes for the EternalBlue vulnerability and when ransomware attacks began. Despite having nearly 60 days to patch their systems, many customers had not. A significant number of these customers were infected by the ransomware. March 14, 2017: Microsoft releases security bulletin MS17-010 which includes fixes for a set of SMBv1 vulnerabilities. April 14 2017: ShadowBrokers publicly releases a set of exploits, including a wormable exploit known as 'EternalBlue' that leverage these SMBv1 vulnerabilities. May 12, 2017: The EternalBlue exploit is used in ransomware attacks known as WannaCry. Hundreds of thousands of vulnerable computers across the globe are infected. Resources Links to downloads for Windows 7, Windows 2008 R2, and Windows 2008 Links to downloads for Windows Vista, Windows 2003 and Windows XP Simon Pope, Director of Incident Response, Microsoft Security Response Center (MSRC) Continue reading...
-
I have now made Edge my default browser. In the last upgrade they enabled extensions on the Mac version. I now have all the extensions I had installed on Firefox installed on Edge. I really think Microsoft has a winner here.
-
Direct link to download Edge Canary. https://officecdn.microsoft.com/pr/C1297A47-86C4-4C1F-97FA-950631F94777/MacAutoupdate/MicrosoftEdgeCanary-76.0.151.0.pkg
-
I see the user agent for Edge is showing as Chrome although it seems to be a different build.
-
Testing to see user agent with Chrome to compare difference.
-
So far I am liking what I see with Chromium based Edge. They released a version for MacOS yesterday. I installed it this morning on Mojave and have been using it all day. I like the clean look. What blows me away is the speed of it. It is faster than Firefox and Safari. Just a tad slower then Chrome. Microsoft did a good job making the UI look and act like all other MacOS apps. If only there was an Adblocker available to make it the perfect browser.
-
Upgrade done and styles turned on. As always let me know if you run into any problems.
-
I am upgrading the site to the newest version of xenForo. This is a major version upgrade so I have temporarily shut off the custom styles which are not compatible with the new version. I will upgrade the styles once the site is upgraded.
-
I rolled back PHP until I can upgrade the site. There is a bug in the version of xenforo we run when using PHP 7.3.