-
Posts
27,568 -
Joined
-
Last visited
-
Days Won
73
Content Type
Forums
Blogs
Events
Resources
Downloads
Gallery
Store
Everything posted by AWS
-
Looking back at the last two years, to say that our security strategies have evolved would be an understatement. Organizations around the world made overnight transitions to remote work models in response to a global pandemic, forcing them to reassess attack surface areas as they underwent an accelerated digital transformation. Meanwhile, cybercriminals seized new opportunities—introducing COVID-19-themed social engineering campaigns and accelerated ransomware attacks. Nation-state actors launched increasingly bold and sophisticated nation-state attacks.1 In this environment, security transformation has become key to survival. The mandate to explicitly verify every access request, focus on least privilege access overall, and constantly assume breach to maintain vigilance was made clear, as exemplified by calls from governments and businesses worldwide to accelerate the adoption of Zero Trust strategies. The evolution of Zero Trust Microsoft has embraced Zero Trust to defend our own estate and as a guiding principle for the development of our products. We have also helped thousands of our customers—including Siemens— deploy Zero Trust strategies, accelerate their digital transformation, and increase frequency of advanced attacks using our Zero Trust architecture. Figure 1: Learnings across thousands of Zero Trust deployments have informed our Zero Trust architecture, which emphasizes the critical importance of integrating policy enforcement and automation, threat intelligence, and threat protection across security pillars. Lessons learned and emerging trends Today, we’re publishing the new whitepaper, Evolving Zero Trust, to share the key lessons we’ve learned by embracing Zero Trust at Microsoft and supporting thousands of organizations in their Zero Trust deployments. This informs our beliefs on Zero Trust implementations needed to evolve to adapt and keep organizations protected. We’re also sharing the evolution of our recommended Zero Trust architecture and maturity model that has been informed by these insights. Highlights from the paper include: Lessons from the most successful organizations: The last couple of years have reinforced the importance of applying Zero Trust comprehensively across the digital estate. Organizations that were furthest along in their journeys were more resilient against sophisticated attacks, improved user experiences, and reduced implementation and management costs. We also saw that successful organizations doubled down on automation and a robust Zero Trust governance strategy—both of which can improve security posture and time to remediation while reducing the workload on scarce security personnel. Emerging industry trends: Zero Trust is a dynamic security model that continues to evolve to meet current threats and business realities. Going forward, we will see deeper integration of Zero Trust across pillars—leading to simplified policy automation, more advanced and intelligent threat detection, and more comprehensive attack mitigation. We also predict a wider adoption of the principles behind Zero Trust—verify explicitly, enforce least privilege access, and assume breach—to include the tools and processes used to develop applications, the hybrid and multi-cloud environments in which they run, as well as the application themselves. A more connected Zero Trust architecture: The learnings highlighted above led us to refine our Zero Trust architecture to more emphasize the critical importance of capturing telemetry from across the environment to inform policy decisions, provide better threat intelligence, measure the user experience, and more. The updated architecture showcases the importance of integrating policy enforcement and automation, threat intelligence, and threat protection across security pillars. This document showcases the incredible evolution and acceleration in the adoption of Zero Trust security strategies. Just a few years ago, Zero Trust was merely a new buzzword for many organizations. Today, 76 percent of large organizations have adopted a Zero Trust approach. We hope that the lessons, trends, and positions we shared in this document are helpful in the planning and application of your own Zero Trust strategy. The insights and actionable learnings in this document have been provided by a diverse group of customers, partners, and security-focused individuals working across applications, data, endpoint management, identity, infrastructure, networking, threat protection, and our own internal security organization. I’d like to thank our customers and partners for their expertise and insights, as well as my colleagues for their contributions to this whitepaper, architecture, and maturity model guidance. Learn More Get the complete Zero Trust whitepaper for key insights, Zero Trust architecture, and a maturity model to help accelerate your adoption. For a repository of technical resources to help accelerate the deployment and integration of Zero Trust across all security pillars, visit the Zero Trust Guidance Center. Use the Zero Trust Assessment tool to evaluate your Zero Trust security posture, maturity, and receive practical recommendations to help reach key milestones. Read the 2021 Microsoft Digital Defense Report (MDDR) for in-depth findings about Microsoft’s tracking of nation-state threat groups, specific threat actors, attack methods, and more. To learn more about Zero Trust, visit Microsoft Security’s Zero Trust website. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. 1Microsoft Digital Defense Report shares new insights on nation-state attacks, John Lambert, Microsoft. 25 October 2021. The post Evolving Zero Trust—Lessons learned and emerging trends appeared first on Microsoft Security Blog. Continue reading...
-
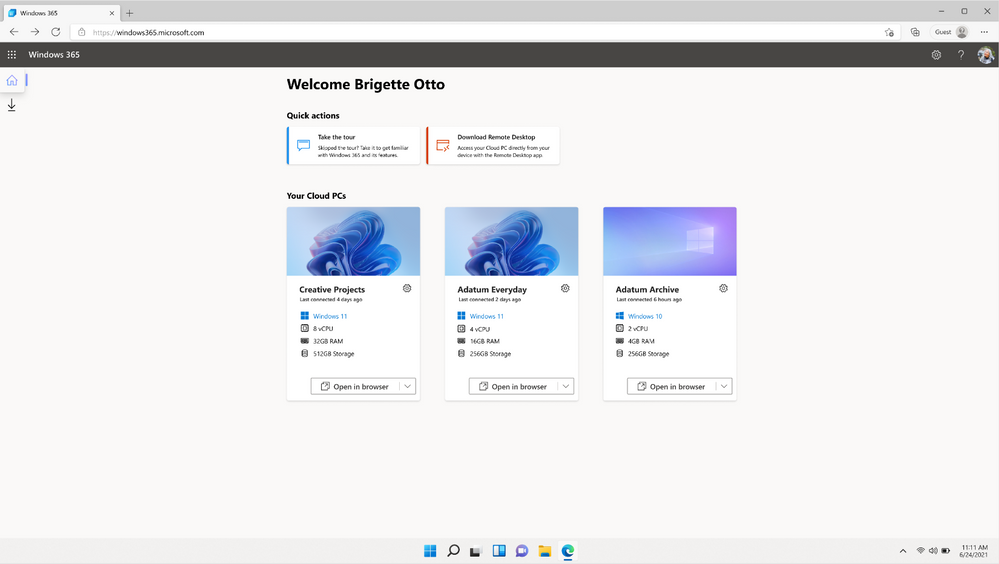
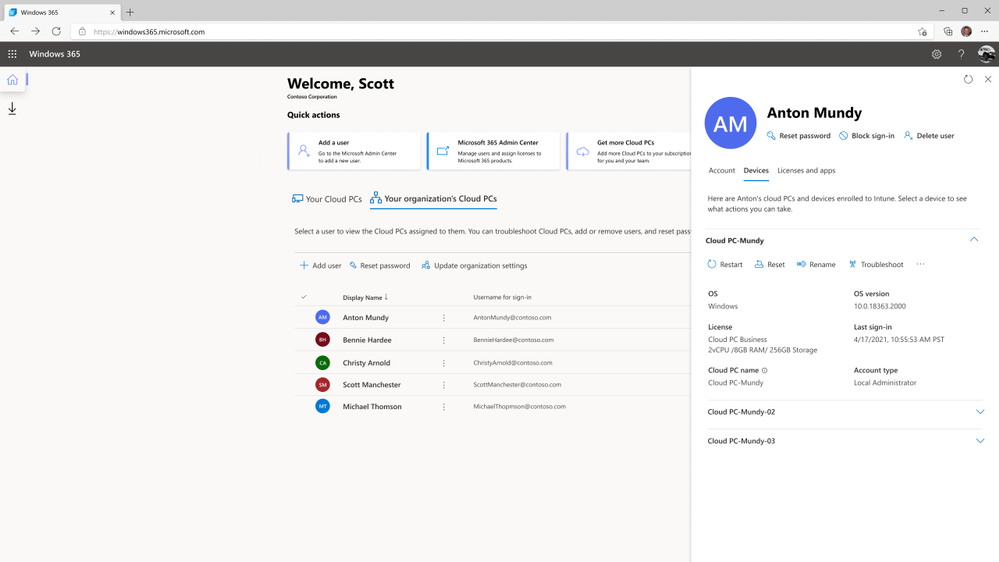
Windows 365 delivers a full, personalized PC experience from the cloud to any device, giving workers and organizations power, simplicity, and security for hybrid work. Tailored to the needs of small and medium-sized organizations, Windows 365 Business makes it easy to create Cloud PCs for your users. Today we are excited to announce four major updates to Windows 365 Business rolling out to customers as soon as the end of the year: Windows 11 support: Experience Windows 11 in the cloud on any device. Windows 365 Business will soon provide a powerful, simple, and secure Windows 11 experience for your users. Enhanced admin capabilities: Benefit from new lifecycle management features, including setting the default operating system (OS) and account type for your users’ devices at the organizational level, as well as device-level actions on individual Cloud PCs. Microsoft Graph API availability: Graph APIs will be available for Windows 365 Business, so organizations can build additional capabilities and automation on top of the service. Microsoft 365 Lighthouse integration: Managed Service Providers (MSPs) will be able to manage Windows 365 Business Cloud PCs on behalf of customers through the Microsoft 365 Lighthouse admin panel. Learn more about the new features. Watch Windows 365 Business: Hybrid work for your small business. Windows 11 support for newly created Cloud PCs Windows 11 is the operating system for hybrid work, delivering new experiences that work how you do. By default, new Cloud PCs will come with Windows 11 installed, so users can take advantage of the latest features and security improvements in the OS. From windows365.microsoft.com, users will be able to easily distinguish between their Windows 10 and Windows 11 Cloud PCs as shown below. Windows365.microsoft.com with options to launch a Windows 11 or Windows 10 Cloud PC Enhanced admin capabilities Windows 365 Business admins will have much greater control over the lifecycle of Cloud PCs in their organization, including the ability to manage organization-wide Cloud PC settings and perform device-level actions. These settings and actions will be configurable both in the Microsoft 365 Admin Center and on windows365.microsoft.com. Admins who are already comfortable managing in the Microsoft 365 Admin Center can continue to manage there. Admins who are managing a smaller number of users or products can perform license, user, and Cloud PC management all from within windows365.microsoft.com. At the organization level, admins will be able to control two settings: OS: By default, new Cloud PCs will have Windows 11. Admins can change the default to Windows 10 if that better suits their organization’s needs. Account type: By default, new Cloud PCs will be set up with a Standard user account type. If an admin chooses, they can change the default to Local Administrator to allow users to install apps and change all settings on their Cloud PC. Read on for more details on the “change account type” functionality. The OS and Account type organization settings will apply during the Cloud PC setup process. At the device level, admins will be able to perform five actions: Change account type: Admins will be able to seamlessly switch the role of user on their Cloud PC between Standard user and Local Administrator. Restart: Admins can restart a user’s Cloud PC on their behalf. Reset: If a user is having trouble with their Cloud PC, admins will be able to reset the Cloud PC for them. This will: Reinstall Windows (with the option to choose between Windows 11 and Windows 10). Remove all apps and locally stored files. Remove changes made to settings. [*]Rename: Admins can change the Cloud PC name that users see on windows365.microsoft.com. [*]Troubleshoot: Troubleshoot checks whether your organization’s Cloud PCs are in a connectable state. If there are any issues preventing a user from connecting to their Cloud PC, admins are given guidance on how to resolve them. (Troubleshoot is coming early 2022.) Admins will be able to perform other basic management capabilities on windows365.microsoft.com, including: Create and delete users Reset passwords Manage licenses for Windows 365 Cloud PCs and Microsoft 365 products Cloud PC management capabilities on windows365.microsoft.com Partner support Microsoft Graph APIs All Cloud PC device actions can be triggered by the Microsoft Graph APIs. Partners can use the Graph API documentation to build custom Windows 365 solutions to match the needs of their users or customers. Microsoft 365 Lighthouse integration The Microsoft 365 Lighthouse admin portal will soon support Windows 365 Business. Participating small and medium-sized business (SMB) partners will be able to use Microsoft 365 Lighthouse to monitor and manage Cloud PCs across multiple customer tenants from one portal, regardless of whether their customers deployed Windows 365 Enterprise or Windows 365 Business. What other features would you like to see? We are excited to launch these new features based on customer feedback we’ve received so far. To give feedback on these features or Windows 365 Business overall, please visit the Windows 365 Tech Community and submit your ideas to the Windows 365 feature requests board. Stay in the know To stay informed on the latest announcements and updates this week, check out the overview post of Windows 365 presence at Microsoft Ignite 2021. Continue reading...
-
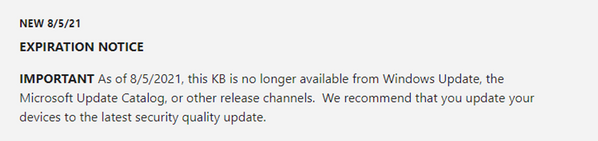
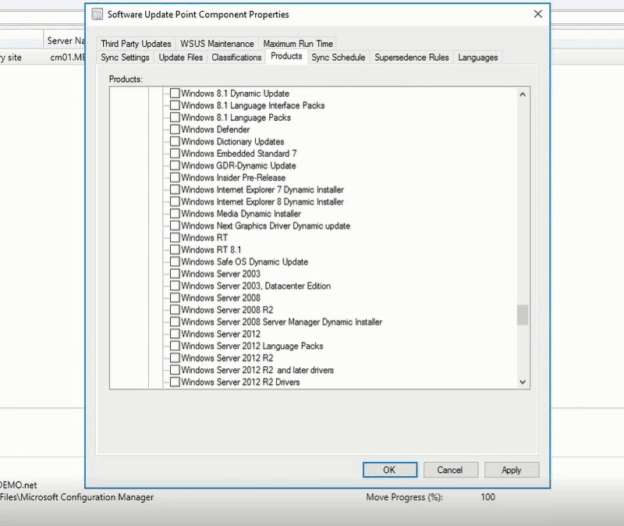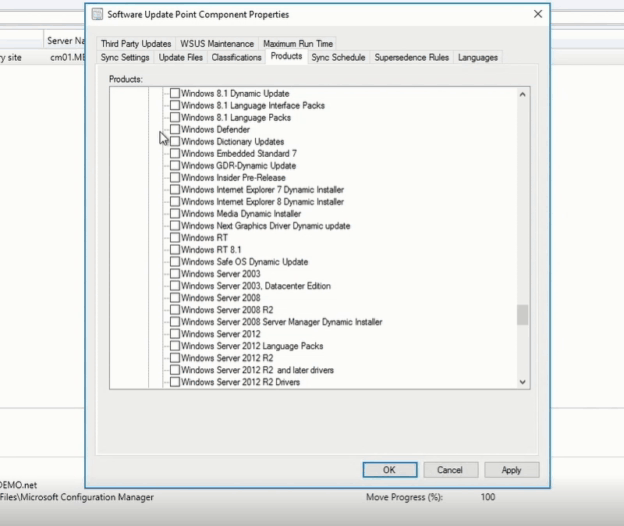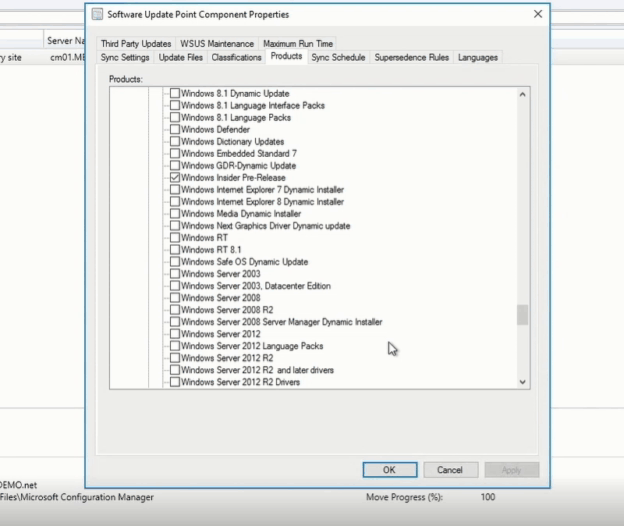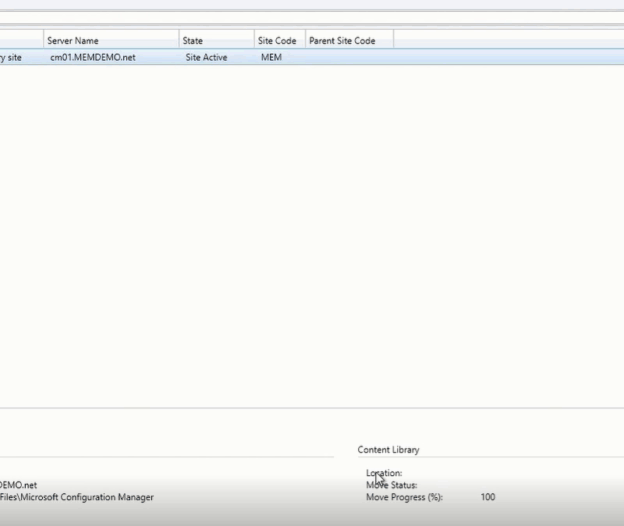
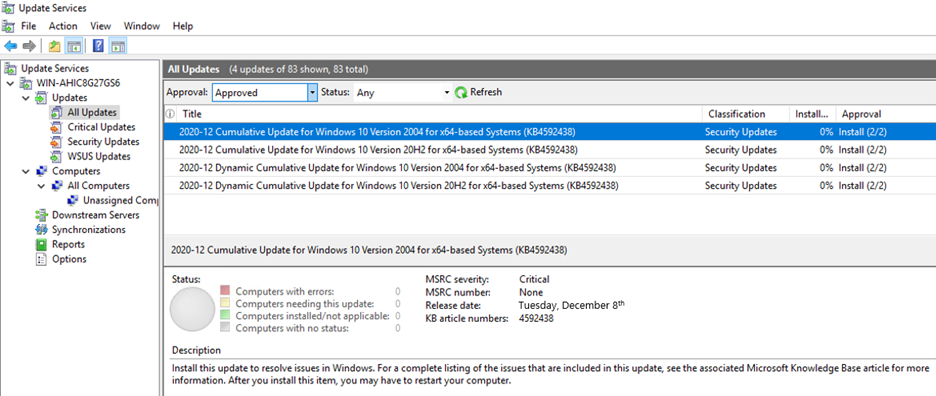
Microsoft produces two to three updates per supported Windows platform monthly. This results in a backlog of updates and potentially increases the size of update packages. Many of these updates, however, are cumulative and include all earlier updates that have been published for that platform. That means, when older packages expire, you still receive the updates contained in those packages by installing the cumulative update. By expiring older, redundant packages, you get better performance, shorter scan times, a faster user experience, and reduced risk of deploying older updates which have been superseded with newer, more secure ones. Here are answers to common questions we receive about our Windows update expiration policy. How often are update packages expired? Our published packages are evaluated for expiration on a regular basis. Once a large enough quantity of candidates have been found, an expiration will take place. Why aren't older updates expired? Some older packages may not yet have been evaluated or may not have met the criteria for expiration. It is also possible that they have not yet expired because of existing dependencies on that specific update. Are there any packages that cannot be expired? Security-only update packages for Windows 8.1, Windows Server 2012 SP2, Windows Server 2012, Windows 7 SP1, Windows Server 2008 R2, and Windows Server 2008 SP2 do not expire as they are not cumulative and hold only one month worth of fixes. Additionally, if a more recent update package has a dependency on an older package, the older package will not expire until it has been superseded by a newer package. How can find out if my update has expired? If an update has expired, you will see the word "EXPIRED" appended to the title of the release note article associated with that specific update on support.microsoft.com. There will also be an expiration notice at the top of the article. If you are using Windows Server Update Services (WSUS), you will see a banner at the top of the details pane if a given update has expired. Note: This policy only applies to Windows updates. Updates for other Microsoft software or firmware may have different policies and should be considered separately. Continue reading...
-
The data privacy regulation landscape is more complex than ever. With new laws emerging in countries like China and India, shifts in Europe and the United Kingdom, and currently 26 different laws across the United States, staying ahead of regulations can feel impossible. But this work is critical—to safeguarding people and the tools they use to stay connected, get work done, and thrive in today’s hybrid environment. We have been working closely with our customers to help. Today, I’m excited to share with you some of the new investments we’re making to attempt to bring some simplicity to the complex topic of data privacy regulations. Introducing Privacy Management for Microsoft 365 With the latest regulation going into effect soon in China, most of the world’s population will soon have its personal data covered under modern privacy regulations. But how organizations manage their regulatory responsibilities with all those laws in mind is often manual, time-consuming, and expensive. Today, I’m excited to announce that Privacy Management for Microsoft 365 is generally available to help customers safeguard personal data and build a privacy-resilient workplace. With role-based access controls and data de-identified by default, Privacy Management for Microsoft 365 helps organizations to have end-to-end visibility of privacy risks at scale in an automated way. Identify critical privacy risks and conflicts: One of the biggest challenges in managing privacy is finding where personal data is stored, especially in an unstructured environment. Most companies still use manual processes to maintain data inventory and mapping, primarily through email, spreadsheets, and in-person communication, which is costly and ineffective. Privacy Management automatically and continuously helps to discover where and how much private data is stored in customers’ Microsoft 365 environments by leveraging data classification and user mapping intelligence. Organizations can see an aggregated view of their privacy posture, including the amount, category, and location of private data, and associated privacy risks and trends over time. Automate privacy operations and response to subject rights requests: Privacy Management correlates data signals across the Microsoft 365 suite of solutions to deliver actionable insights that allow privacy administrators to automate privacy policies by using an out-of-box template—data transfers, data minimization, data overexposure, and subject-rights request management—or create a custom policy to meet an organization’s specific needs. Empower employees to make smart data handling decisions: To build a privacy-resilient culture, you need to educate your employees, so they know how to handle data properly. Privacy Management provides insights and contexts to administrators, enabling them to automate privacy policies and protect sensitive data. Additionally, data owners are given recommended actions, training, and tips to make smart data-handling decisions, eliminating the need to choose between privacy and productivity. Figure 1: Overview dashboard showcasing privacy risks and trends. You can learn more about Novartis’ experience with Privacy Management for Microsoft 365 in their case study. Partnering to give customers greater visibility beyond Microsoft 365 Because data lives across so many clouds, systems, and applications, solving the challenge of data privacy requires great insight—and partnership. To meet you where you are in your privacy journey, we have built APIs that allow you to integrate with your existing processes and solutions to automatically create and manage subject rights requests in Privacy Management. We’re also excited today to partner with leading privacy software companies—OneTrust, Securiti.ai, and WireWheel—to extend subject rights management capabilities to personal data stored outside of the Microsoft 365 environment, enabling customers to have a unified and streamlined response to subject requests. You can learn more about these partnerships in today’s Tech Community blog. New regulation assessments in Microsoft Compliance Manager Staying ahead of data privacy regulations and understanding the technical actions you can take to address compliance can be daunting. To help, Microsoft Compliance Manager today has more than 200 regulatory assessment templates covering global, industrial, and regional Data Protection and Privacy regulations, making it easier for customers to interpret, assess, and improve their compliance with regulatory requirements. We recently added three privacy-specific assessments for Colorado Privacy Act, Virginia Consumer Data Protection Act (CDPA), and Egypt Privacy Law. Additionally, we have mapped privacy-specific controls across these assessment templates to the new Privacy Management solution to help you scale your compliance efforts. You can learn more about Compliance Manager, our list of available assessments, and how to use the assessment in our documentation. You can also try the Compliance Manager 90-day trial, which gives you access to 25 assessments. Privacy is a journey We recognize that navigating the complexity of data privacy regulations is a journey, and we are excited to partner with you, our customers, and others in the ecosystem to help to ease some of the complexity, making the world a safer place for all. Privacy Management for Microsoft 365 is generally available to customers as an add-on to a Microsoft 365 or Office 365 subscription. To get started with Privacy Management, you can leverage the free 90-day trial. You can learn a lot more about Privacy Management in today’s Tech Community blog or watch the new Microsoft Mechanics video. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. The post Simplifying the complex: Introducing Privacy Management for Microsoft 365 appeared first on Microsoft Security Blog. Continue reading...
-
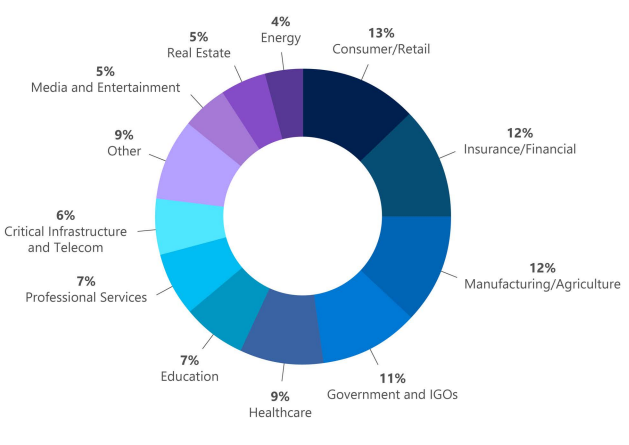
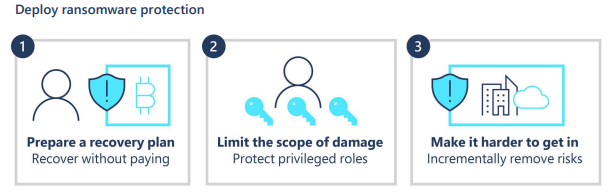
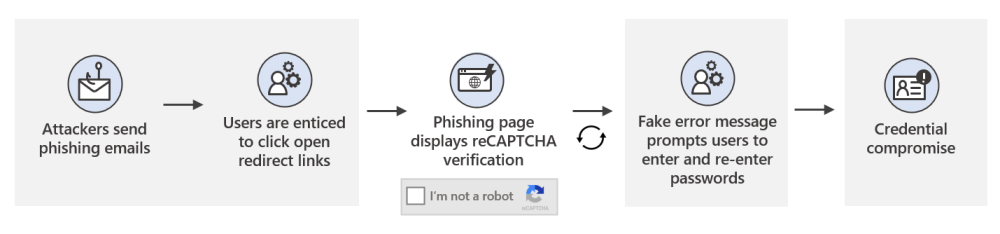
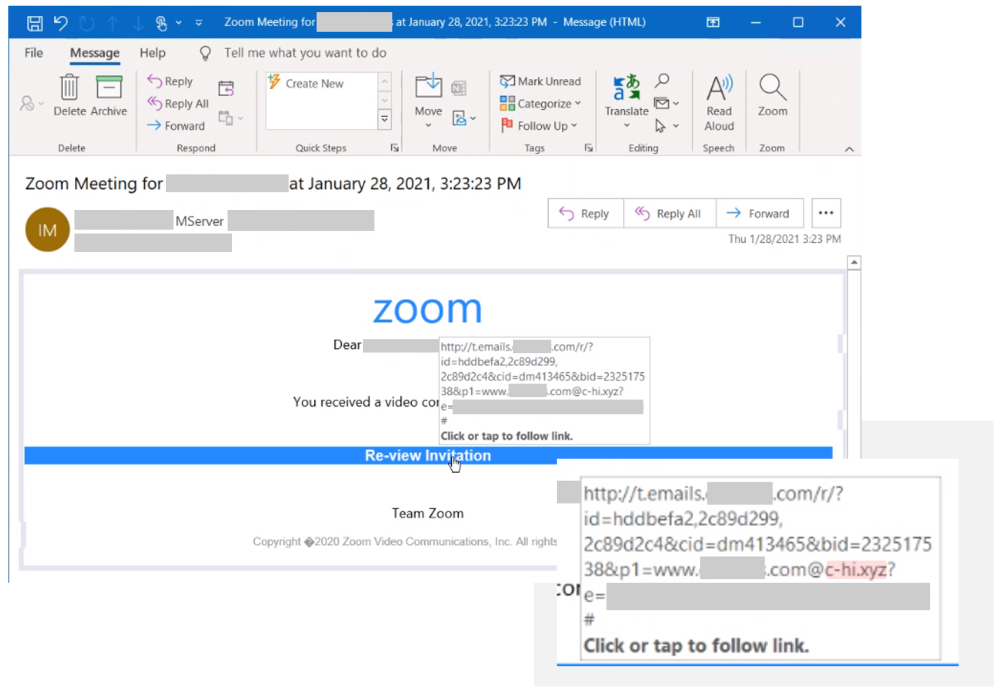
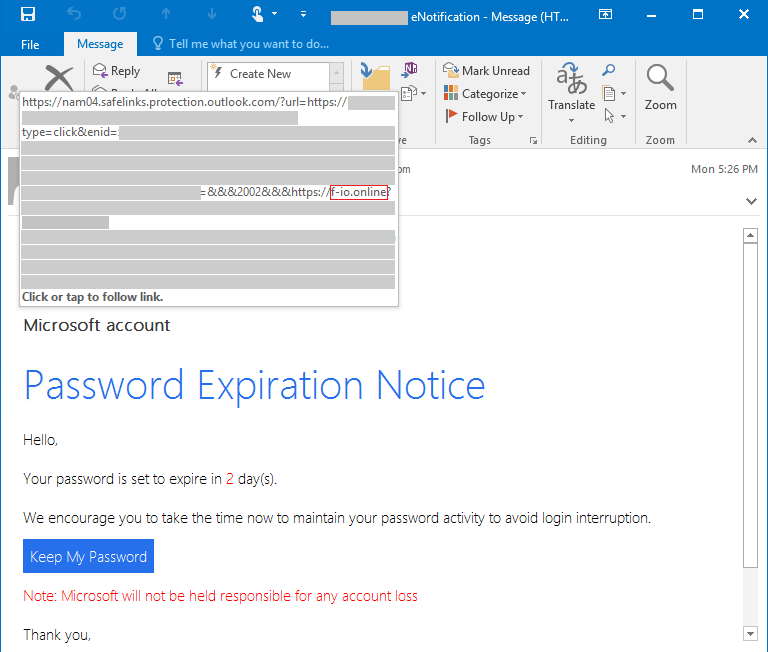
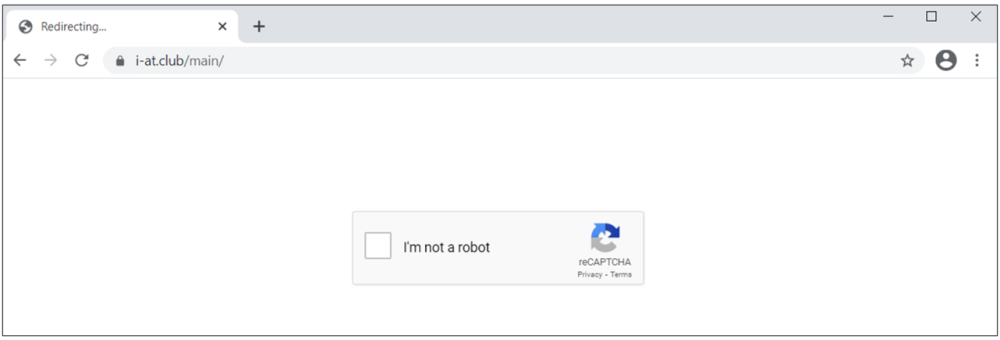
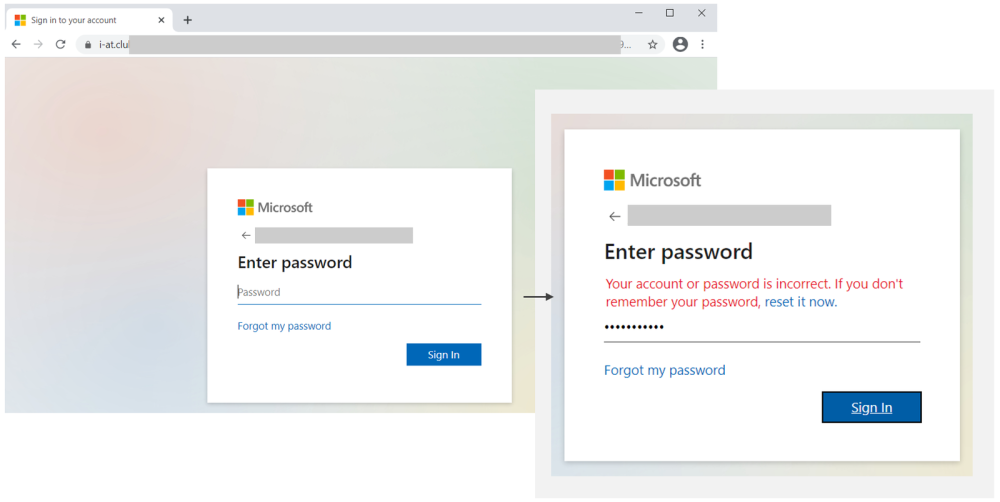
In 2021, cybercrime has become more sophisticated, widespread, and relentless. Criminals have targeted critical infrastructure—healthcare,1 information technology,2 financial services,3 energy sectors4—with headline-grabbing attacks that crippled businesses and harmed consumers. But there are positive trends—victims are coming forward, humanizing the toll of cyberattacks and prompting increased engagement from law enforcement. Governments are also passing new laws and allocating more resources as they recognize cybercrime as a threat to national security. Earlier this month, Microsoft published the 2021 Microsoft Digital Defense Report (MDDR). Drawing upon over 24 trillion daily security signals across the Microsoft cloud, endpoints, and the intelligent edge, the 2021 MDDR expands upon last year’s inaugural report and contains input from more than 8,500 security experts spanning 77 countries—including insights on the evolving state of ransomware, malicious email, malware, and more. Ransomware goes retail Ransomware offers a low-investment, high-profit business model that’s irresistible to criminals. What began with single-PC attacks now includes crippling network-wide attacks using multiple extortion methods to target both your data and reputation, all enabled by human intelligence. Through this combination of real-time intelligence and broader criminal tactics, ransomware operators have driven their profits to unprecedented levels. This human-operated ransomware, also known as “big game ransomware,” involves criminals hunting for large targets that will provide a substantial payday through syndicates and affiliates. Ransomware is becoming a modular system like any other big business, including ransomware as a service (RaaS). With RaaS there isn’t a single individual behind a ransomware attack; rather, there are multiple groups. For example, one threat actor may develop and deploy malware that gives one attacker access to a certain category of victims; whereas, a different actor may merely deploy malware. It’s effectively a crime syndicate where each member is paid for a particular expertise. Once a criminal actor compromises a network, they may steal confidential information, financial documents, and insurance policies. After analyzing this intelligence, they will demand an “appropriate” ransom to not only unlock their victim’s systems but also to prevent public disclosure of exfiltrated data. This is known as the double extortion model: a victim is extorted for ransom on stolen data and intellectual property (IP), and then again to prevent the attacker from publishing it. Typically, threat actors will demand payment through cryptocurrency wallets. The underlying blockchain technology enables the owners of crypto wallets to remain pseudonymous. But the criminal actor needs to find a way to cash out, which is where middlemen in the cryptocurrency ecosystem step in to facilitate ransom-related transactions and payments. Both the private sector and government agencies—through civil litigation, prosecution, regulatory enforcement, and international collaboration—can take coordinated action against ransomware intermediaries to disrupt the payment process. Data from Microsoft’s Detection and Response Team (DART) shows that the three sectors most targeted by ransomware were consumer, financial, and manufacturing. Figure 1: DART ransomware engagements by industry (July 2020 to June 2021). The best way to be prepared against ransomware is to make it harder for attackers to access systems while making it easier for victims to recover—without paying a ransom. Encouraging organizations to prepare for the worst is actually a proactive strategy, one that’s designed to minimize monetary incentives for attackers. To learn more about defending against ransomware, read the 2021 MDDR. Microsoft also supports the guidance presented in the Ransomware Playbook by the Cyber Readiness Institute. Figure 2: Three steps for limiting damage from ransomware. Malicious email: Bait and switch Reports of phishing attacks doubled in 2020, with credential phishing used in many of the most damaging attacks. The Microsoft Digital Crimes Unit (DCU) has investigated online organized crime networks involved in business email compromise (BEC), finding a broad diversification of how stolen credentials are obtained, verified, and used. Threat actors are increasing their investment in automation and purchasing tools, so they can increase the value of their criminal activities. Overall, phishing is the most common type of malicious email observed in our threat signals. All industries receive phishing emails, with some verticals more heavily targeted depending on attacker objectives, availability of leaked email addresses, or current events regarding specific sectors and industries. The number of phishing emails we observed in Microsoft Exchange global email flow increased from June 2020 to June 2021, with a pronounced surge in November potentially taking advantage of holiday-themed traffic. Figure 3: Malicious email techniques. Phishing sites frequently copy well-known, legitimate login pages, such as Microsoft Office 365, to trick users into inputting their credentials. In one recent example, attackers combined open redirector links with bait that impersonates well-known productivity tools and services. Users clicking the link were lead to a series of redirections—including a CAPTCHA verification page that adds a sense of legitimacy—before landing on a fake sign-in page and finally, credential compromise. Those stolen identities can then be weaponized in BEC attacks or via phishing websites. Even after a successful attack, threat actors may re-sell accounts if the credentials remain compromised. Microsoft Defender SmartScreen detected more than a million unique domains used in web-based phishing attacks in the last year, of which compromised domains represented just over five percent. Those domains typically host phishing attacks on legitimate websites without disrupting any legitimate traffic, so their attack remains hidden as long as possible. Domains created specifically for attacks tend to be active for shorter periods. Over the last year, Microsoft has seen attacks come in short bursts that begin and end within as little as one to two hours. Because those minutes matter, Microsoft is again co-sponsoring the annual Terranova Gone Phishing Tournament, which uses real-world simulations to establish accurate clickthrough statistics. By using a real phishing email template included in Microsoft Defender for Office 365, Attack Simulator provides context-aware simulations and hyper-targeted training to educate employees and measures behavior changes. Malware: Opportunity knocks Just as phishing has grown in scale and complexity over the last year, malware too has continued to evolve. Microsoft 365 Defender Threat Intelligence has observed recent innovations that can lead to greater success among attackers. Even with a range of attack goals—ransom, data exfiltration, credential theft, espionage—many malware types rely on time-tested strategies for establishing themselves in a network. Simple and effective, web shell usage continues to climb among both nation-state groups and criminal organizations, allowing attackers to execute commands and steal data from a web server, or use the server as a launchpad for further attacks. PowerShell, using suspicious flags or encoded values, was the most common behavior Microsoft observed from malware this year. Also popular is malware that attempts to rename or inject payloads to mimic system processes and collect data from browser caches. Other forms of malware in play were: use of specific reconnaissance strings; processes added to startup folders; Windows Antimalware Scan Interface (AMSI) and registry alterations; and executables dropped from Microsoft Office 365 files accompanied by other alerts. We also observed malware tactics that are more difficult to mitigate, such as: Fileless malware and evasive behavior—these include numerous fileless malware techniques employed by botnets, commodity downloaders, and advanced malware campaigns, all designed to make removal and detection more difficult. Legitimate service abuse in network communications—Google Drive, Microsoft OneDrive, Adobe Spark, Dropbox, and other sites are still popular for malware delivery, while “content dump” sites such as Pastebin.com, Archive.org, and Stikked.ch are increasingly popular for component download in multi-part and fileless malware. Learn more Every person and organization has the right to expect the technology they use to be secure and delivered by a company they can trust. As part of Microsoft’s differentiated approach to cybersecurity, the DCU represents an international team of technical, legal, and business experts that have been fighting cybercrime to protect victims since 2008. We use our expertise and unique view of online criminal networks to take action. We share insights internally that translate to security product features, we uncover evidence for criminal referrals to law enforcement throughout the world, and we take legal action to disrupt malicious activity. For a comprehensive look at the state of cybercrime today, including the rise of malicious domains and adversarial machine learning, download the 2021 Microsoft Digital Defense Report. Look for upcoming blog posts providing in-depth information for each themed week of Cybersecurity Awareness Month 2021. Visit our Cybersecurity Awareness Month page for more resources and information on protecting your organization year-round. Do your part. #BeCyberSmart To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. 1Cybercriminals Ramp Up Attacks on Healthcare, Again, James Liu, Security Boulevard. 03 June 2021. 2Microsoft Warns of Continued Attacks by the Nobelium Hacking Group, Nathaniel Mott, PCMag. 26 June 2021. 3Attacks on Financial Apps Jump 38% in First Half of 2021, Natasha Chilingerian, Credit Union Times. 23 August 2021. 4One password allowed hackers to disrupt Colonial Pipeline, CEO tells senators, Stephanie Kelly, Jessica Resnick-ault, Reuters. 08 June 2021. The post How cyberattacks are changing according to new Microsoft Digital Defense Report appeared first on Microsoft Security Blog. Continue reading...
-
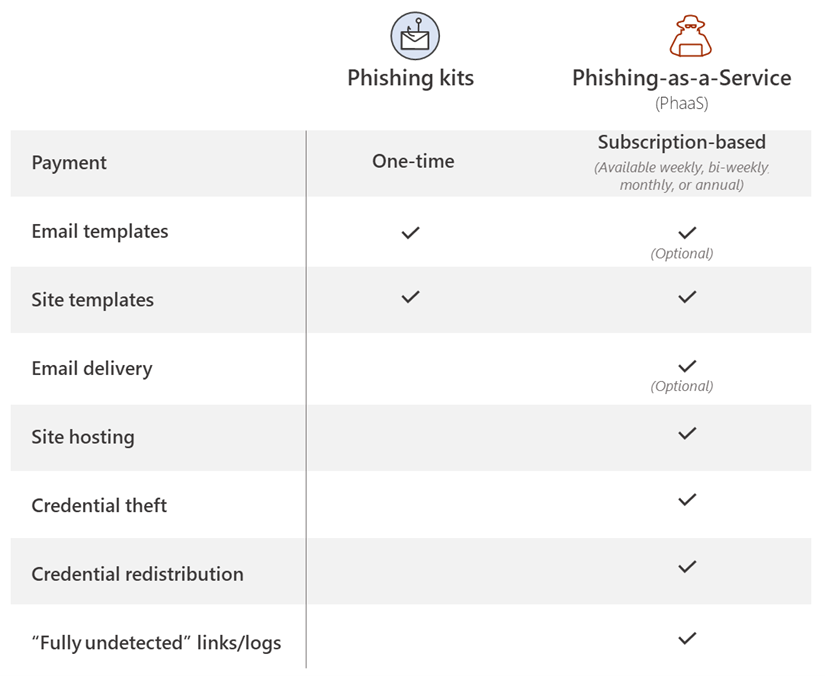
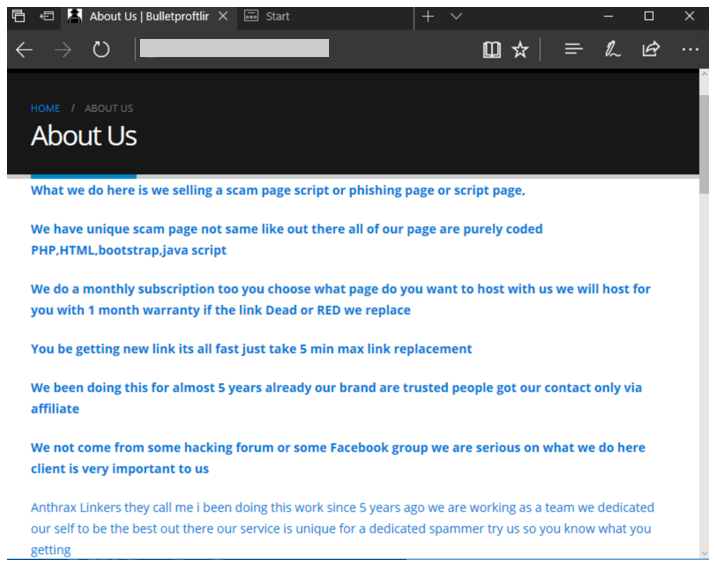
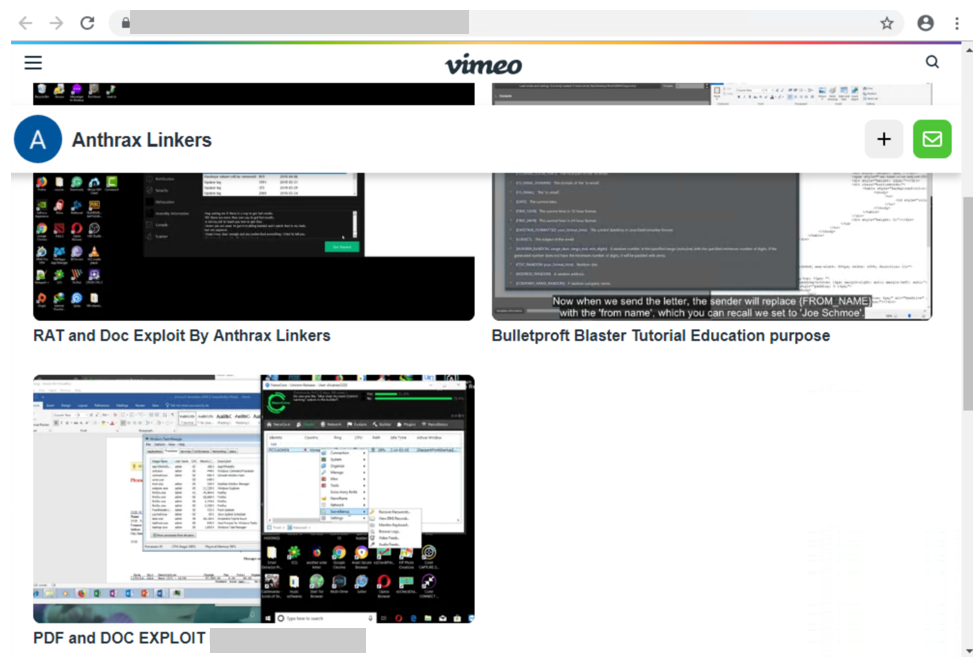
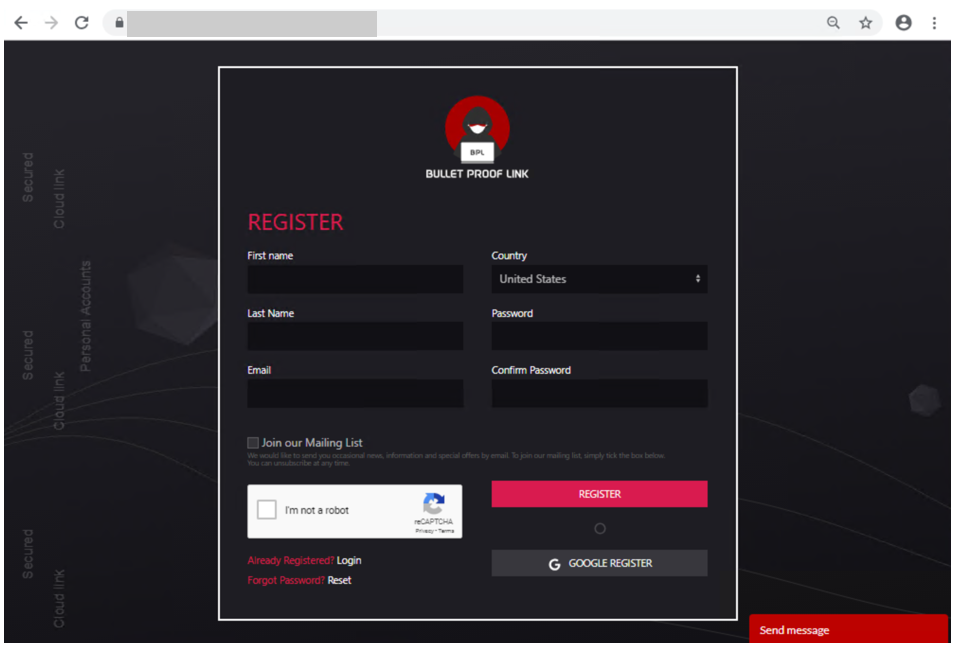
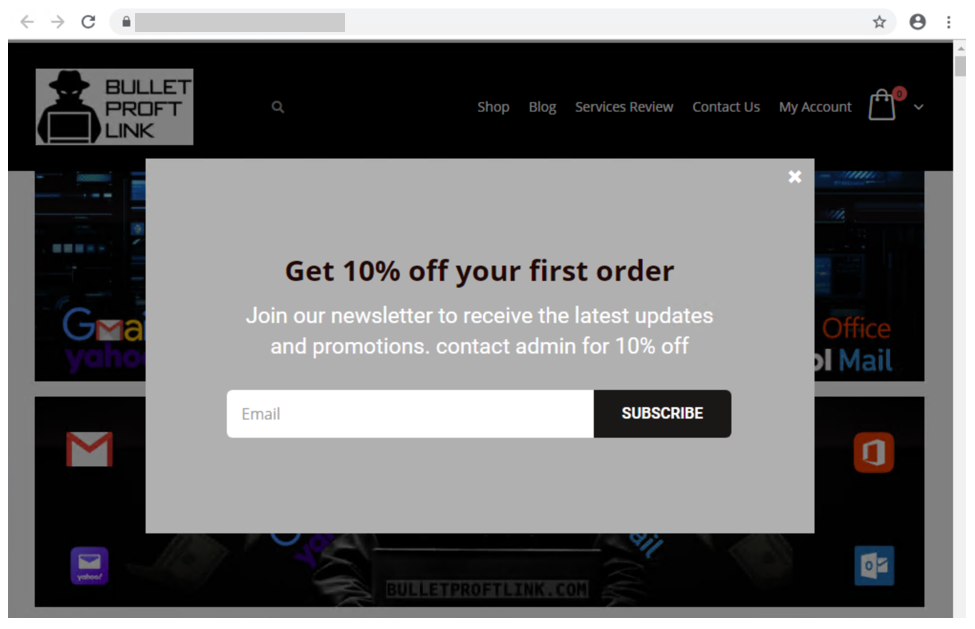
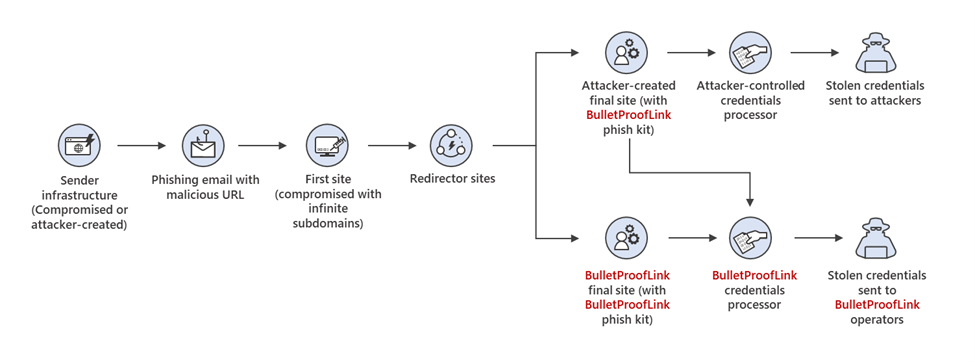
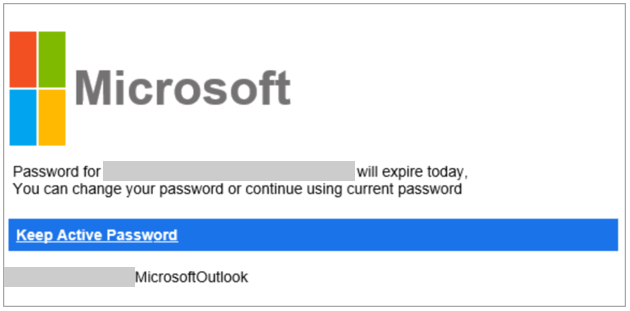
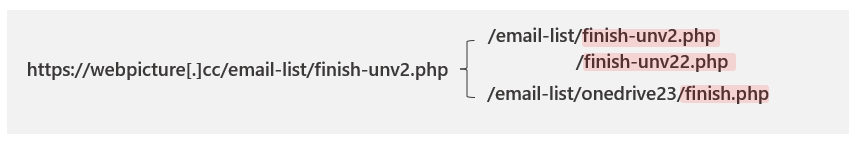
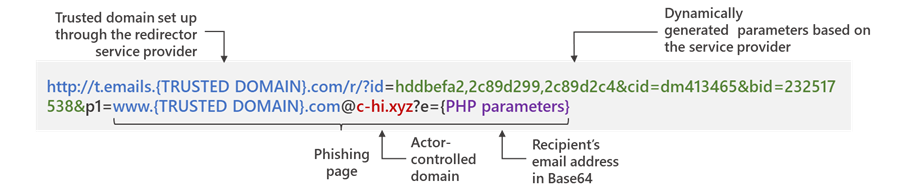
In researching phishing attacks, we came across a campaign that used a rather high volume of newly created and unique subdomains—over 300,000 in a single run. This investigation led us down a rabbit hole as we unearthed one of the operations that enabled the campaign: a large-scale phishing-as-a-service operation called BulletProofLink, which sells phishing kits, email templates, hosting, and automated services at a relatively low cost. With over 100 available phishing templates that mimic known brands and services, the BulletProofLink operation is responsible for many of the phishing campaigns that impact enterprises today. BulletProofLink (also referred to as BulletProftLink or Anthrax by its operators in various websites, ads, and other promotional materials) is used by multiple attacker groups in either one-off or monthly subscription-based business models, creating a steady revenue stream for its operators. This comprehensive research into BulletProofLink sheds a light on phishing-as-a-service operations. In this blog, we expose how effortless it can be for attackers to purchase phishing campaigns and deploy them at scale. We also demonstrate how phishing-as-a-service operations drive the proliferation of phishing techniques like “double theft”, a method in which stolen credentials are sent to both the phishing-as-a-service operator as well as their customers, resulting in monetization on several fronts. Insights into phishing-as-a-service operations, their infrastructure, and their evolution inform protections against phishing campaigns. The knowledge we gained during this investigation ensures that Microsoft Defender for Office 365 protects customers from the campaigns that the BulletProofLink operation enables. As part of our commitment to improve protection for all, we are sharing these findings so the broader community can build on them and use them to enhance email filtering rules as well as threat detection technologies like sandboxes to better catch these threats. Understanding phishing kits and phishing-as-a-service (PhaaS) The persistent onslaught of email-based threats continues to pose a challenge for network defenders because of improvements in how phishing attacks are crafted and distributed. Modern phishing attacks are typically facilitated by a large economy of email and false sign-in templates, code, and other assets. While it was once necessary for attackers to individually build phishing emails and brand-impersonating websites, the phishing landscape has evolved its own service-based economy. Attackers who aim to facilitate phishing attacks may purchase resources and infrastructure from other attacker groups including: Phish kits: Refers to kits that are sold on a one-time sale basis from phishing kit sellers and resellers. These are packaged files, usually a ZIP file, that come with ready-to-use email phishing templates designed to evade detection and are often accompanied by a portal with which to access them. Phish kits allow customers to set up the websites and purchase the domain names. Alternatives to phishing site templates or kits also include templates for the emails themselves, which customers can customize and configure for delivery. One example of a known phish kit is the MIRCBOOT phish kit. Phishing-as-a-service: Similar to ransomware-as-a-service (RaaS), phishing-as-a-service follows the software-as-a-service model, which requires attackers to pay an operator to wholly develop and deploy large portions or complete phishing campaigns from false sign-in page development, website hosting, and credential parsing and redistribution. BulletProofLink is an example of a phishing-as-a-service (PhaaS) operation. Figure 1. Feature comparison between phishing kits and phishing-as-a-service It’s worth noting that some PhaaS groups may offer the whole deal—from template creation, hosting, and overall orchestration, making it an enticing business model for their clientele. Many phishing service providers offer a hosted scam page solution they call “FUD” Links or “Fully undetected” links, a marketing term used by these operators to try and provide assurance that the links are viable until users click them. These phishing service providers host the links and pages and attackers who pay for these services simply receive the stolen credentials later on. Unlike in certain ransomware operations, attackers do not gain access to devices directly and instead simply receive untested stolen credentials. Breaking down BulletProofLink services To understand how PhaaS works in detail, we dug deep into the templates, services, and pricing structure offered by the BulletProofLink operators. According to the group’s About Us web page, the BulletProofLink PhaaS group has been active since 2018 and proudly boasts of their unique services for every “dedicated spammer”. Figure 2. The BulletProofLink’s ‘About Us’ page provides potential customers an overview of their services. The operators maintain multiple sites under their aliases, BulletProftLink, BulletProofLink, and Anthrax, including YouTube and Vimeo pages with instructional advertisements as well as promotional materials on forums and other sites. In many of these cases, and in ICQ chat logs posted by the operator, customers refer to the group as the aliases interchangeably. Figure 3. Video tutorials posted by the Anthrax Linkers (aka BulletProofLink) BulletProofLink registration and sign-in pages BulletProofLink additionally hosts multiple sites, including an online store where they allow their customers to register, sign in, and advertise their hosted service for monthly subscriptions. Over the course of monitoring this operation, their online store had undergone multiple revisions. The source code for the site’s pages contained references to artifacts elsewhere on the site, which included ICQ chat messages and advertisements. While those references are still present in newer versions, the sign-in page for the monthly subscription site no longer contains service pricing information. In previous versions, the sites alluded to the cost for the operator to host FUD links and return credentials to the purchasing party. Figure 4. BulletProofLink registration page Just like any other service, the group even boasts of a 10% welcome discount on customers’ orders when they subscribe to their newsletter. Figure 5. BulletProofLink welcome promotion for site visitors’ first order Credential phishing templates BulletProofLink operators offer over 100 templates and operate with a highly flexible business model. This business model allows customers to buy the pages and “ship” the emails themselves and control the entire flow of password collection by registering their own landing pages or make full use of the service by using the BulletProofLink’s hosted links as the final site where potential victims key in their credentials. The templates are designed to evade detection while successfully phishing for credentials, but may vary based on the individual purchasing party. Likewise, the wide variety of templates offered does not guarantee that all BulletProofLink facilitated campaigns will look identical. Instead, the campaigns themselves can be identified with a mixture of phishing page source code, combined with the PHP password processing sites referenced therein, as well as the hosting infrastructure used in their larger-scale campaigns. These password-processing domains correlate back to the operator through hosting, registration, email, and other metadata similarities during domain registration. The templates offered are related to the phishing pages themselves, so the emails that service them may seem highly disparate and handled by multiple operators. Services offered: Customer hosting and support The phishing operators list an array of services on their site along with the corresponding fees. As OSINT Fans noted in their blog, the monthly service costs as much as $800, while other services cost about $50 dollars for a one-time hosting link. We also found that Bitcoin is a common payment method accepted on the BulletProofLink site. In addition to communicating with customers on site accounts, the operators display various methods of interacting with them, which include Skype, ICQ, forums, and chat rooms. Like a true software business dedicated to their customers, the operators provide customer support services for new and existing customers. Figure 6. Screenshot of the BulletProofLink site, which offers a wide array of phishing services impersonating various legitimate services Figure 7. DocuSign scam page service listed on the BulletProofLink site The hosting service includes a weekly log shipment to purchasing parties, usually sent manually over ICQ or email. Analysis of individual activity on password-processing replies from the collected infrastructure indicates that the credentials are received on the initial template page and then sent to password-processing sites owned by the operator. Figure 8. An advertisement from BulletProofLink that showcases their weekly log shipment At the time of this report, BulletProofLink continues to operate active phishing campaigns, with large volumes of redirections to their password-processing links from legitimate web hosting providers. In the next section, we describe on such campaign. Tracking a BulletProofLink-enabled campaign As mentioned, we uncovered BulletProofLink while investigating a phishing campaign that used the BulletProofLink phishing kit on either on attacker-controlled sites or sites provided by BulletProofLink as part of their service. The campaign itself was notable for its use of 300,000 subdomains, but our analysis exposed one of many implementations of the BulletProofLink phishing kit: Figure 9. End-to-end attack chain of BulletProofLink-enabled phishing campaigns An interesting aspect of the campaign that drew our attention was its use of a technique we call “infinite subdomain abuse”, which happens when attackers compromise a website’s DNS or when a compromised site is configured with a DNS that allows wildcard subdomains. “Infinite subdomains” allow attackers to use a unique URL for each recipient while only having to purchase or compromise one domain for weeks on end. It is gaining popularity among attackers for the following reasons: It serves as a departure from previous techniques that involved hackers obtaining large sets of single-use domains. To leverage infinite subdomains for use in email links that serve to redirect to a smaller set of final landing pages, the attackers then only need to compromise the DNS of the site, and not the site itself. It allows phishing operators to maximize the unique domains they are able to use by configuring dynamically generated subdomains as prefix to the base domain for each individual email. The creation of unique URLs poses a challenge to mitigation and detection methods that rely solely on exact matching for domains and URLs. The phishing campaign also impersonated (albeit poorly) the Microsoft logo and branding. The impersonation technique used solid colors for the logo, which may have been done intentionally to bypass detection of the Microsoft logo’s four distinct colors. It is worth noting that later iterations of the campaign have switched to using the four colors in the Microsoft logo. Figure 10. Phishing lure from a recent credential phishing campaign These messages also used a technique called zero-point font, which pads the HTML of the message with characters that render as invisible to the user, to obfuscate the email body and attempt to evade detection. This technique is increasingly used by phishers to evade detection. Figure 11. HTML showing zero-point font date stuffing in an email We found that the phishing URL in the email contained Base64-encoded victim information along with an attacker-owned site where the user is meant to be redirected. In this campaign, a single base domain was used for the infinite subdomain technique to initiate the redirects for the campaign, which leveraged multiple secondary sites over several weeks. Figure 12. The format and an example of the phishing URL, which when decoded redirects to the compromised site. The compromised site redirected to a second domain that hosted the phishing page, which mimicked the Outlook sign-in screen and is generated for each user-specific URL. We found that the page is generated for any number of email addresses entered into the URI, and had no checking mechanisms to guarantee that it wasn’t already used or was related to a live phishing email. There can be one or more locations to which credentials are sent, but the page employed a few obfuscation techniques to obscure these locations. One attempt to obfuscate the password processing site’s location was by using a function that decodes the location based on calling back to an array of numbers and letters: We reversed this in Python and found the site that the credentials were being sent to: hxxps://webpicture[.]cc/email-list/finish-unv2[.]php. The pattern “email-list/finish-unv2.php” came in one of these variations: finish-unv2[.]php, finish-unv22[.]php, or finish[.]php. These variations typically used the term “email-list” as well as another file path segment referencing a particular phishing page template, such as OneDrive or SharePoint. Occasionally, multiple locations were used to send credentials to, including some that could be owned by the purchasing party instead of the operator themselves, which could be called in a separate function. This could be an example of legacy artifacts remaining in final templates, or of double-theft occurring. Figure 13. The final site’s format comes in either of these pattern variations Analyzing these patterns led us to an extensive list of password-capturing URIs detailed in an OSINT Fans blog post about the BulletProofLink phishing service operators. We noticed that they listed patterns similar to the ones we had just observed, enabling us to find the various templates BulletProofLink used, including the phishing email with the fake Microsoft logo discussed earlier. One of the patterns we noted is that many of the password-processing domains used in the campaigns directly had associated email addresses with “Anthrax”,” BulletProofLink”, “BulletProftLink” or other terms in the certificate registration. The email addresses themselves were not listed identically on every certificate, and were also tied to domains not used exclusively for password-processing, as noted in additional reporting by OSINT Fans. From then on, we drew even more similarities between the landing pages seen in the infinite subdomain surge campaign we were tracking and the existing in-depth research on the adversaries behind the BulletProofLink operations. This process ultimately led us to track and expand on the same resources referenced in the OSINT Fans research, as we uncovered even more information about the long-running and large-scale phishing service BulletProofLink. Furthermore, we were able to uncover previous and current password-processing sites in use by the operator, as well as large segments of infrastructure hosted on legitimate hosting sites for this operation’s other components. “Double theft” as a PhaaS monetization effort The PhaaS working model as we’ve described it thus far is reminiscent of the ransomware-as-a-service (RaaS) model, which involves double extortion. The extortion method used in ransomware generally involves attackers exfiltrating and posting data publicly, in addition to encrypting them on compromised devices, to put pressure on organizations to pay the ransom. This lets attackers gain multiple ways to assure payment, while the released data can then be weaponized in future attacks by other operators. In a RaaS scenario, the ransomware operator has no obligation to delete the stolen data even if the ransom is already paid. We have observed this same workflow in the economy of stolen credentials in phishing-as-a-service. With phishing kits, it is trivial for operators to include a secondary location for credentials to be sent to and hope that the purchaser of the phish kit does not alter the code to remove it. This is true for the BulletProofLink phishing kit, and in cases where the attackers using the service received credentials and logs at the end of a week instead of conducting campaigns themselves, the PhaaS operator maintained control of all credentials they resell. In both ransomware and phishing, the operators supplying resources to facilitate attacks maximize monetization by assuring stolen data, access, and credentials are put to use in as many ways as possible. Additionally, victims’ credentials also likely to end up in the underground economy. For a relatively simple service, the return of investment offers a considerable motivation as far as the email threat landscape goes. How Microsoft Defender for Office 365 defends against PhaaS-driven phishing attacks Investigating specific email campaigns allows us to ensure protections against particular attacks as well as similar attacks that use the same techniques, such as the infinite subdomain abuse, brand impersonation, zero-point font obfuscation, and victim-specific URI used in the campaign discussed in this blog. By studying phishing-as-a-service operations, we are able to scale and expand the coverage of these protections to multiple campaigns that use the services of these operations. In the case of BulletProofLink, our intelligence on the unique phishing kits, phishing services, and other components of phishing attacks allows us to ensure protection against the many phishing campaigns this operation enables. Microsoft Defender for Office 365—which uses machine learning, heuristics, and an advance detonation technology to analyze emails, attachments, URLs, and landing pages in real time—recognizes the BulletProofLink phishing kit that serves the false sign-in pages and detects the associated emails and URLs. In addition, based on our research into BulletProofLink and other PhaaS operations, we observed that numerous phishing kits leverage the code and behaviors of existing kits, such as those sold by BulletProofLink. Any kit that attempts to leverage similar techniques, or stitch together code from multiple kits can similarly be detected and remediated before the user receives the email or engages with the content. With Microsoft 365 Defender, we’re able to further expand that protection, for example, by blocking of phishing websites and other malicious URLs and domains in the browser through Microsoft Defender SmartScreen, as well as the detection of suspicious and malicious behavior on endpoints. Advanced hunting capabilities allow customers to search through key metadata fields on mailflow for the indicators listed in this blog and other anomalies. Email threat data is correlated with signals from endpoints and other domains, providing even richer intelligence and expanding investigation capabilities. To build resilience against phishing attacks in general, organizations can use anti-phishing policies to enable mailbox intelligence settings, as well as configure impersonation protection settings for specific messages and sender domains. Enabling SafeLinks ensures real-time protection by scanning at time of delivery and at time of click. In addition to taking full advantage of the tools available in Microsoft Defender for Office 365, administrators can further strengthen defenses against the threat of phishing by securing the Azure AD identity infrastructure. We strongly recommend enabling multifactor authentication and blocking sign-in attempts from legacy authentication. Learn how you can stop credential phishing and other email threats through comprehensive, industry-leading protection with Microsoft Defender for Office 365. Microsoft 365 Defender Threat Intelligence Team Indicators of compromise Password-processing URLs hxxps://apidatacss[.]com/finish-unv22[.]php hxxps://ses-smtp[.]com/email-list/office19999999/finish[.]php hxxps:// ses-smtp[.]com/email-list/onedrive25/finish[.]php hxxps:// ses-smtp[.]com/email-list/office365nw/finish[.]php hxxps://smtpro101[.]com/email-list/onedrive25/finish[.]php hxxps://smtpro101[.]com/email-list/office19999999/finish[.]php hxxps://plutosmto[.]com/email-list/office365nw/finish[.]php hxxps://smtptemp[.].site/email-list/office365nw/finish[.]php hxxps://trasactionsmtp[.]com/email-list/finish-unv2[.]php hxxps://smtptemp[.]site/email-list/office365nw/finish-unv22[.]php hxxps://apidatacss:com/finish-unv22[.]php hxxps://smtptemp.site/email-list/otlk55/finish[.]php hxxps://smtptemp.site/email-list/onedrive25/finish[.]php hxxps://plutosmto[.]com/email-list/kumar/finish[.]php hxxps://laptopdata.xyz/email-list/office365nw/finish[.]php hxxps://jupitersmt[.]com/email-list/office365nw/finish[.]php hxxps://plutosmto[.]com/email-list/onedrive25/finish[.]php hxxps://plutosmto[.]com/email-list/sharepointbuisness/finish[.]php hxxps://ghostsmtp[.]com/email-list/sharepoint/finish[.]php hxxps://jupitersmt[.]com/email-list/otlk/finish[.]php hxxps://earthsmtp[.]com/email-list/onedrive25/finish[.]php hxxps://earthsmtp[.]com/email-list/office365nw/finish[.]php hxxps://trasactionsmtp[.]com/email-list/defaultcustomers/johnphilips002021/finish[.]php hxxps://trasactionsmtp[.]com/email-list/office365nw/finish[.]php hxxps://trasactionsmtp[.]com/email-list/universalmail/finish[.]php hxxps://trasactionsmtp[.]com/email-list/onedrive25/finish[.]php hxxps://moneysmtp[.]com/email-list/office365nw/finish[.]php hxxps://moneysmtp[.]com/email-list/otlk/finish[.]php hxxps://moneysmtp[.]com/hxxp://moneysmtp[.]com/email-list/office365nw/finish[.]php hxxps://feesmtp[.]com/email-list/office365rd40/finish[.]php hxxps://feesmtp[.]com/email-list/onedrive25/finish[.]php hxxps://Failedghostsmtp[.]com/email-list/sharepoint/finish[.]php hxxps://bomohsmtp[.]com/email-list/office365-21/finish[.]php hxxps://bomohsmtp[.]com/email-list/onedrive25/finish[.]php hxxps://foxsmtp[.]com/email-list/onedrive25/finish[.]php hxxps://dasmtp[.]com/email-list/dropboxoffice1/finish[.]php hxxps://rosmtp[.]com/email-list/onedrive23/finish[.]php hxxps://ghostsmtp[.]com/email-list/adobe20/finish[.]php hxxps://josmtp[.]com/email-list/onedrive23/finish[.]php hxxps://ghostsmtp[.]com:443/email-list/onedrive23/finish[.]php hxxps://ghostsmtp[.]com/email-list/onedrive23/finish[.]php hxxps://winsmtp[.]com/email-list/excel/finish[.]php hxxps://linuxsmtp[.]com/email-list/adobe20/finish[.]php?phishing-processor hxxps://gpxsmtp[.]com/email-list/office1/finish[.]php?phishing-processor hxxps://gpxsmtp[.]com/email-list/onedrive23/finish[.]php?phishing-processor hxxps://gpxsmtp[.]com/email-list/excel5/finish[.]php hxxps://gpxsmtp[.]com/email-list/adobe3/finish[.]php hxxps://gpxsmtp[.]com/email-list/office1/finish[.]php hxxps://gpxsmtp[.]com/email-list/onedrive23/finish[.]php hxxps://panelsmtp[.]com/email-list/onedrive-ar/finish[.]php hxxps://mexsmtp[.]com/email-list/onedrive23/finish[.]php?phishing-processor hxxps://racksmtp[.]com/email-list/domain-au1/finish[.]php hxxps://racksmtp[.]com/email-list/finish[.]php hxxps://racksmtp[.]com/email-list/sharepoint/finish[.]php hxxps://mainsmtp[.]com/email-list/onedrive23/finish[.]php hxxps://prvtsmtp[.]com/email-list/onedrive23/finish[.]php?i-am-a-phishing-processor hxxps://prvtsmtp[.]com/email-list/onedrive23/finish[.]php?this-is-a-phishing-processor hxxps://prvtsmtp[.]com/email-list/office1/finish[.]php hxxps://prvtsmtp[.]com/email-list/onedrive23/finish[.]php hxxps://apiserverdata1[.]com/email-list/office1/finish[.]php hxxps://webpicture.cc/email-list/excel/finish[.]php hxxps://webpicture.cc/email-list/office1/finish[.]php?this-is-a=phishing-processor hxxps://valvadi101[.]com/email-list/office1/finish[.]php hxxps://moneysmtp[.]com/email-list/finish-unv2[.]php hxxps://foxsmtp[.]com/email-list/finish-unv2[.]php hxxps://bomohsmtp[.]com/email-list/finish-unv2[.]php hxxps://rosmtp[.]com/email-list/finish-unv2[.]php hxxps://linuxsmtp[.]com/email-list/finish-unv2[.]php?phishing-processor hxxps://voksmtp[.]com/email-list/finish-unv2[.]php?phishing-processor hxxps://gpxsmtp[.]com/email-list/finish-unv2[.]php?phishing-processor hxxps://gpxsmtp[.]com/email-list/finish-unv2[.]php hxxps://webpicture.cc/email-list/finish-unv2[.]php hxxps://Faileduebpicture.cc/email-list/finish-unv2[.]php hxxps://Failedsendapidata[.]com/email-list/finish-unv2[.]php hxxps://webpicture.cc/email-list/finish-unv2[.]php?phishing-processor hxxps://prvtsmtp[.]com/email-list/finish-unv2[.]php hxxps://webpicture.cc/email-list/finish-unv2.ph hxxps://apiserverdata1[.]com/email-list/finish-unv2[.]php hxxps://sendapidata[.]com/email-list/finish-unv2[.]php Password-processing domains: hxxps://apidatacss[.]com hxxps://apiserverdata1[.]com hxxps://baller[.]top hxxps://datacenter01.us hxxps://f1smtp[.]com hxxps://ghostsmtp[.]com hxxps://gpxsmtp[.]com hxxps://gurl101[.]services hxxps://hostprivate[.]us hxxps://josmtp[.]com hxxps://link101[.]bid hxxps://linuxsmtp[.]com hxxps://migration101[.]us hxxps://panelsmtp[.]com hxxps://racksmtp[.]com hxxps://rosmtp[.]com hxxps://rxasmtp[.]com hxxps://thegreenmy87[.]com hxxps://vitme[.]bid hxxps://voksmtp[.]com hxxps://winsmtp[.]com hxxps://trasactionsmtp[.]com hxxps://moneysmtp[.]com hxxps://foxsmtp[.]com hxxps://bomohsmtp[.]com hxxps://webpicture[.]cc hxxps://Faileduebpicture[.]cc hxxps://Failedsendapidata[.]com hxxps://prvtsmtp[.]com hxxps://sendapidata[.]com hxxps://smtptemp.site hxxps://plutosmto[.]com hxxps://laptopdata[.]xyz hxxps://jupitersmt[.]com hxxps://earthsmtp[.]com hxxps://feesmtp[.]com hxxps://Failedghostsmtp[.]com hxxps://dasmtp[.]com hxxps://mexsmtp[.]com hxxps://mainsmtp[.]com hxxps://valvadi101[.]com hxxps://ses-smtp[.]com The post Catching the big fish: Analyzing a large-scale phishing-as-a-service operation appeared first on Microsoft Security Blog. Continue reading...
-
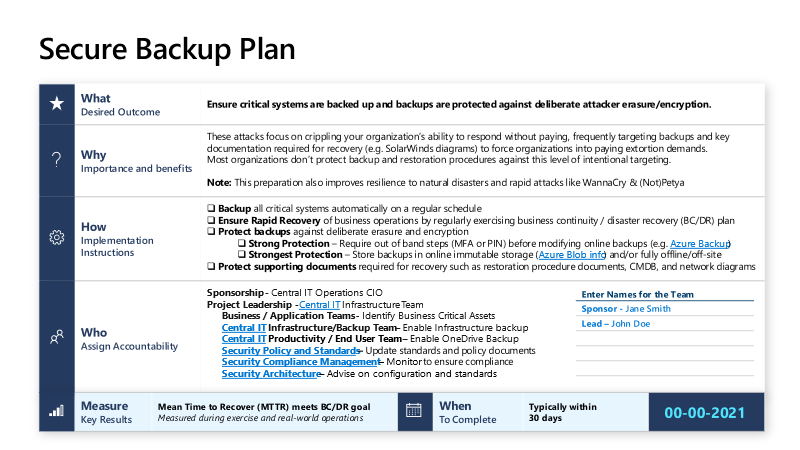
This blog is part one of a two-part series focused on how Microsoft DART helps customers with human-operated ransomware. For more guidance on human-operated ransomware and how to defend against these extortion-based attacks, refer to our human-operated ransomware docs page. Microsoft’s Detection and Response Team (DART) has helped customers of all sizes, across many industries and regions, investigate and remediate human-operated ransomware for over five years. This blog aims to explain the process and execution used in our customer engagements to provide perspective on the unique issues and challenges regarding human-operated ransomware. We will also discuss how DART leverages Microsoft solutions such as Microsoft Defender for Endpoint, Microsoft Defender for Identity, and Microsoft Cloud App Security (MCAS) within customer environments while collaborating with cross-functional threat intelligence teams across Microsoft who similarly track human-operated ransomware activities and behaviors. Human-operated ransomware is not a malicious software problem—it’s a human criminal problem. The solutions used to address commodity problems aren’t enough to prevent a threat that more closely resembles a nation-state threat actor. It disables or uninstalls your antivirus software before encrypting files. They locate and corrupt or delete backups before sending a ransom demand. These actions are commonly done with legitimate programs that you might already have in your environment and are not considered malicious. In criminal hands, these tools are used maliciously to carry out attacks. Responding to the increasing threat of ransomware requires a combination of modern enterprise configuration, up-to-date security products, and the vigilance of trained security staff to detect and respond to the threats before data is lost. Key steps in DART’s approach to conducting ransomware incident investigations To maximize DART’s efforts to restore business continuity while simultaneously analyzing the details of the incident, a careful and thorough investigation is coordinated with remediation measures to ensure that the root cause is determined. These efforts take place as we assist and advise customers with the task of getting the organization up and running again in a secure manner. Every effort is made to determine how the adversary gained access to the customer’s assets so that vulnerabilities can be remediated. Otherwise, it is highly likely that the same type of attack will take place again in the future. In some cases, the threat actor takes steps to “cover their tracks” and destroy evidence, so it is possible that the entire chain of events may not be evident. The following are three key steps in our ransomware investigations: Figure 1. Key steps in DART’s ransomware investigations. 1. Assess the current situation This is critical to understanding the scope of the incident and for determining the best people to assist and to plan and scope the investigation and remediation tasks. Asking these initial questions is crucial in helping us determine the situation being dealt with: What initially made you aware of the ransomware attack? If the initial threat was identified by IT staff (like noticing backups being deleted, antivirus (AV) alert, endpoint detection and response (EDR) alert, suspicious system changes), it is often possible to take quick decisive measures to thwart the attack, typically by disabling all inbound and outbound internet communication. This may temporarily affect business operations, but that would typically be much less impactful than an adversary deploying ransomware. If the threat was identified by a user call to the IT helpdesk, there may be enough advance warning to take defensive measures to prevent or minimize the effects of the attack. If the threat was identified by an external entity (like law enforcement or a financial institution), it is likely that the damage is already done, and you will see evidence in your environment that the threat actor has already gained administrative control of your network. This can range from ransomware notes, locked screens, or ransom demands. What date/time did you first learn of the incident? Establishing the initial activity date and time is important because it helps narrow the scope of the initial triage for “quick wins.” Additional questions may include: What updates were missing on that date? This is important to understand what vulnerabilities may have been exploited by the adversary. What accounts were used on that date? What new accounts have been created since that date? What logs (such as AV, EDR, and VPN) are available, and is there any indication that the actor is currently accessing systems? Logs are an indicator of suspected compromise. Follow-up questions may include: Are logs being aggregated in a SIEM (like Microsoft Azure Sentinel, Splunk, ArcSight) and current? What is the retention period of this data? Are there any suspected compromised systems that are experiencing unusual activity? Are there any suspected compromised accounts that appear to be actively used by the adversary? Is there any evidence of active command and controls (C2s) in EDR, Firewall, VPN, Proxy, and other logs? As part of assessing the current situation, DART may require a domain controller (DC) that was not ransomed, a recent backup of a DC, or a recent DC taken offline for maintenance/upgrades. We also ask our customers whether multifactor authentication (MFA) was required for everyone in the company and if Microsoft Azure Active Directory was used. 2. Identify line-of-business (LOB) apps that are unavailable due to the incident This step is critical in figuring out the quickest way to get systems back online while obtaining the evidence required. Does the application require an identity? How is authentication performed? How are credentials such as certificates or secrets stored and managed? Are tested backups of the application, configuration, and data available? Are the contents and integrity of backups regularly verified using a restore exercise? This is particularly important after configuration management changes or version upgrades. 3. Explain the compromise recovery (CR) process This is a follow-up engagement that may be necessary if DART determines that the control plane (typically Active Directory) has been compromised. DART’s investigation always has a goal of providing output that feeds directly into the CR process. CR is the process by which we remove the nefarious attacker control from an environment and tactically increase security posture within a set period. CR takes place post-security breach. To learn more about CR, read the Microsoft Compromise Recovery Security Practice team’s blog CRSP: The emergency team fighting cyber attacks beside customers. Once we have gathered the responses to the questions above, we can build a list of tasks and assign owners. A key factor in a successful incident response engagement is thorough, detailed documentation of each work item (such as the owner, status, findings, date, and time), making the compilation of findings at the end of the engagement a straightforward process. How DART leverages Microsoft security solutions to combat human-operated ransomware DART leverages cross-functional teams, such as internal threat intelligence teams, who track adversary activities and behaviors, customer support, and product development teams behind Microsoft products and services. DART also collaborates with other incident response vendors the customer may have engaged and will share findings whenever possible. DART relies heavily on data for all investigations. The team uses existing deployments of Microsoft solutions, such as Defender for Endpoint, Defender for Identity, and MCAS within customer environments along with custom forensic data collection for additional analysis. If these sensors are not deployed, DART also requests that the customer deploy these to gain deeper visibility into the environment, correlate against threat intelligence sources, and enable our analysts to scale in speed and agility. Microsoft Defender for Endpoint Microsoft Defender for Endpoint is Microsoft’s enterprise endpoint security platform designed to help enterprise network security analysts prevent, detect, investigate, and respond to advanced threats. As shown in the image below, Defender for Endpoint can detect attacks using advanced behavioral analytics and machine learning. DART analysts use Defender for Endpoint for attacker behavioral analytics. Figure 2. Sample alert in Microsoft Defender for Endpoint for a pass-the-ticket attack. DART analysts can also perform advanced hunting queries to pivot off indicators of compromise (IOCs) or search for known behavior if a threat actor group is identified. Figure 3. Advanced hunting queries to locate known attacker behavior. In Defender for Endpoint, customers have access to a real-time expert-level monitoring and analysis service by Microsoft Threat Experts for ongoing suspected actor activity. Customers can also collaborate with experts on demand for additional insights into alerts and incidents. Figure 4. Defender for Endpoint shows detailed ransomware activity. Microsoft Defender for Identity DART leverages Microsoft Defender for Identity to investigate known compromised accounts and to find potentially compromised accounts in your organization. Defender for Identity sends alerts for known malicious activity that actors often use such as DCSync attacks, remote code execution attempts, and pass-the-hash attacks. Defender for Identity enables our team to pinpoint nefarious activity and accounts to narrow down our investigation. Figure 5. Defender for Identity sends alerts for known malicious activity related to ransomware attacks. Microsoft Cloud App Security MCAS allows DART analysts to detect unusual behavior across cloud apps to identify ransomware, compromised users, or rogue applications. MCAS is Microsoft’s cloud access security broker (CASB) solution that allows for monitoring of cloud services and data access in cloud services by users. Figure 6. The Microsoft Cloud App Security dashboard allows DART analysis to detect unusual behavior across cloud apps. Microsoft Secure Score The Microsoft 365 Defender stack provides live remediation recommendations to reduce the attack surface. Microsoft Secure Score is a measurement of an organization’s security posture, with a higher number indicating more improvement actions taken. Refer to our documentation to find out more about how your organization can leverage this feature to prioritize remediation actions that are based on their environment. Understand your business risks Beyond the immediate risk of encrypted files, understanding the disruption to business operations, data theft, extortion, follow-on attacks, regulatory and compliance reporting, and damage to reputation fall outside technical controls. Microsoft DART recommends each organization weigh these risks when determining the appropriate way to respond based on the organization’s policies, risk appetite, and applicable regulatory requirements. Microsoft Defender for Endpoint, Microsoft Defender for Identity, and MCAS all work seamlessly together to provide customers with enhanced visibility of the attacker’s actions within and investigate attacks. Given our vast experience and expertise in investigating countless human-operated ransomware events over the past few years, we have shared what we consider best practices. Learn more Want to learn more about DART? Read our past blog posts. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. The post A guide to combatting human-operated ransomware: Part 1 appeared first on Microsoft Security Blog. Continue reading...
-
In August, Microsoft Threat Intelligence Center (MSTIC) identified a small number of attacks (less than 10) that attempted to exploit a remote code execution vulnerability in MSHTML using specially crafted Microsoft Office documents. These attacks used the vulnerability, tracked as CVE-2021-40444, as part of an initial access campaign that distributed custom Cobalt Strike Beacon loaders. These loaders communicated with an infrastructure that Microsoft associates with multiple cybercriminal campaigns, including human-operated ransomware. The observed attack vector relies on a malicious ActiveX control that could be loaded by the browser rendering engine using a malicious Office document. Customers who enabled attack surface reduction rules to block Office from creating child processes are not impacted by the exploitation technique used in these attacks. While these attacks used a vulnerability to access entry point devices and run highly-privileged code, the secondary actions taken by the attackers still rely on stealing credentials and moving laterally to cause organization-wide impact. This illustrates the importance of investing in attack surface reduction, credential hygiene, and lateral movement mitigations. Customers are advised to apply the security patch for CVE-2021-40444 to fully mitigate this vulnerability. This blog details our in-depth analysis of the attacks that used the CVE-2021-40444, provides detection details and investigation guidance for Microsoft 365 Defender customers, and lists mitigation steps for hardening networks against this and similar attacks. Our colleagues at RiskIQ conducted their own analysis and coordinated with Microsoft in publishing this research. Exploit delivery mechanism The initial campaigns in August 2021 likely originated from emails impersonating contracts and legal agreements, where the documents themselves were hosted on file-sharing sites. The exploit document used an external oleObject relationship to embed exploitative JavaScript within MIME HTML remotely hosted content that results in (1) the download of a CAB file containing a DLL bearing an INF file extension, (2) decompression of that CAB file, and (3) execution of a function within that DLL. The DLL retrieves remotely hosted shellcode (in this instance, a custom Cobalt Strike Beacon loader) and loads it into wabmig.exe (Microsoft address import tool.) Figure 1. The original exploit vector: an externally targeted oleObject relationship definition bearing an MHTML handler prefix pointed at an HTML file hosted on infrastructure that has similar qualities to the Cobalt Strike Beacon infrastructure that the loader’s payload communicates with. Content that is downloaded from an external source is tagged by the Windows operating system with a mark of the web, indicating it was downloaded from a potentially untrusted source. This invokes Protected Mode in Microsoft Office, requiring user interaction to disable it to run content such as macros. However, in this instance, when opened without a mark of the web present, the document’s payload executed immediately without user interaction – indicating the abuse of a vulnerability. Figure 2. Attack chain of DEV-0413 campaign that used CVE-2021-40444 DEV-0413 observed exploiting CVE-2021-40444 As part of Microsoft’s ongoing commitment to tracking both nation state and cybercriminal threat actors, we refer to the unidentified threat actor as a “development group” and utilize a threat actor naming structure with a prefix of “DEV” to indicate an emerging threat group or unique activity during the tracking and investigation phases before MSTIC reaches high confidence about the origin or identity of the actor behind an operation. MSTIC tracks a large cluster of cybercriminal activity involving Cobalt Strike infrastructure under the name DEV-0365. The infrastructure we associate with DEV-0365 has several overlaps in behavior and unique identifying characteristics of Cobalt Strike infrastructure that suggest it was created or managed by a distinct set of operators. However, the follow-on activity from this infrastructure indicates multiple threat actors or clusters associated with human-operated ransomware attacks (including the deployment of Conti ransomware). One explanation is that DEV-0365 is involved in a form of command- and-control infrastructure as a service for cybercriminals. Additionally, some of the infrastructure that hosted the oleObjects utilized in the August 2021 attacks abusing CVE-2021-40444 were also involved in the delivery of BazaLoader and Trickbot payloads — activity that overlaps with a group Microsoft tracks as DEV-0193. DEV-0193 activities overlap with actions tracked by Mandiant as UNC1878. Due to the uncertainty surrounding the nature of the shared qualities of DEV-0365 infrastructure and the significant variation in malicious activity, MSTIC clustered the initial email campaign exploitation identified as CVE-2021-40444 activity separately, under DEV-0413. The DEV-0413 campaign that used CVE-2021-40444 has been smaller and more targeted than other malware campaigns we have identified leveraging DEV-0365 infrastructure. We observed the earliest exploitation attempt of this campaign on August 18. The social engineering lure used in the campaign, initially highlighted by Mandiant, aligned with the business operations of targeted organizations, suggesting a degree of purposeful targeting. The campaign purported to seek a developer for a mobile application, with multiple application development organizations being targeted. In most instances, file-sharing services were abused to deliver the CVE-2021-40444-laden lure. It is worth highlighting that while monitoring the DEV-0413 campaign, Microsoft identified active DEV-0413 infrastructure hosting CVE-2021-40444 content wherein basic security principles had not been applied. DEV-0413 did not limit the browser agents able to access the server to their malware implant or known targets, thereby permitting directory listing for their web server. In doing so, the attackers exposed their exploit to anyone who might have gained interest based on public social media discussion. Figure 3. Content of the original DEV-0413 email lure seeking application developers At least one organization that was successfully compromised by DEV-0413 in their August campaign was previously compromised by a wave of similarly-themed malware that interacted with DEV-0365 infrastructure almost two months before the CVE-2021-40444 attack. It is currently not known whether the retargeting of this organization was intentional, but it reinforces the connection between DEV-0413 and DEV-0365 beyond sharing of infrastructure. In a later wave of DEV-0413 activity on September 1, Microsoft identified a lure change from targeting application developers to a “small claims court” legal threat. Figure 4. Example of the “Small claims court” lure utilized by DEV-0413 Vulnerability usage timeline On August 21, 2021, MSTIC observed a social media post by a Mandiant employee with experience tracking Cobalt Strike Beacon infrastructure. This post highlighted a Microsoft Word document (SHA-256: 3bddb2e1a85a9e06b9f9021ad301fdcde33e197225ae1676b8c6d0b416193ecf) that had been uploaded to VirusTotal on August 19, 2021. The post’s focus on this document was highlighting the custom Cobalt Strike Beacon loader and did not focus on the delivery mechanism. MSTIC analyzed the sample and determined that an anomalous oleObject relationship in the document was targeted at an external malicious HTML resource with an MHTML handler and likely leading to abuse of an undisclosed vulnerability. MSTIC immediately engaged the Microsoft Security Response Center and work began on a mitigation and patch. During this process, MSTIC collaborated with the original finder at Mandiant to reduce the discussion of the issue publicly and avoid drawing threat actor attention to the issues until a patch was available. Mandiant partnered with MSTIC and did their own reverse engineering assessment and submitted their findings to MSRC. On September 7, 2021, Microsoft released a security advisory for CVE-2021-40444 containing a partial workaround. As a routine in these instances, Microsoft was working to ensure that the detections described in the advisory would be in place and a patch would be available before public disclosure. During the same time, a third-party researcher reported a sample to Microsoft from the same campaign originally shared by Mandiant. This sample was publicly disclosed on September 8. We observed a rise in exploitation attempts within 24 hours. Figure 5. Graphic showing original exploitation on August 18 and attempted exploitation increasing after public disclosure Microsoft continues to monitor the situation and work to deconflict testing from actual exploitation. Since the public disclosure, Microsoft has observed multiple threat actors, including ransomware-as-a-service affiliates, adopting publicly disclosed proof-of-concept code into their toolkits. We will continue to provide updates as we learn more. Mitigating the attacks Microsoft has confirmed that the following attack surface reduction rule blocks activity associated with exploitation of CVE-2021-40444 at the time of publishing: Block all Office applications from creating child processes Apply the following mitigations to reduce the impact of this threat and follow-on actions taken by attackers. Apply the security updates for CVE-2021-40444. Comprehensive updates addressing the vulnerabilities used in this campaign are available through the September 2021 security updates. Run the latest version of your operating systems and applications. Turn on automatic updates or deploy the latest security updates as soon as they become available. Use a supported platform, such as Windows 10, to take advantage of regular security updates. Turn on cloud-delivered protectionin Microsoft Defender Antivirus or the equivalent for your antivirus product to cover rapidly evolving attacker tools and techniques. Cloud-based machine learning protections block the majority of new and unknown variants. Turn on tamper protectionin Microsoft Defender for Endpoint, to prevent malicious changes to security settings. Run EDR in block modeso that Microsoft Defender for Endpoint can block malicious artifacts, even when your non-Microsoft antivirus doesn’t detect the threat or when Microsoft Defender Antivirus is running in passive mode. EDR in block mode works behind the scenes to remediate malicious artifacts that are detected post-breach. Enable investigation and remediationin full automated mode to allow Microsoft Defender for Endpoint to take immediate action on alerts to resolve breaches, significantly reducing alert volume. Use device discoveryto increase your visibility into your network by finding unmanaged devices on your network and onboarding them to Microsoft Defender for Endpoint. Microsoft 365 Defender detection details Antivirus Microsoft Defender Antivirus detects threat components as the following malware: TrojanDownloader:O97M/Donoff.SA – Detects the Word Doc files in the observed attacks TrojanDownloader:HTML/Donoff.SA – Detects the remotely-loaded HTML Trojan:Win32/Agent.SA — Detects the .inf(Dll)/CAB components in the observed attacks Trojan:Win32/CplLoader.A – Blocks Rundll32/Control abuse used in this CVE exploitation Behavior:Win32/OfficeMhtInj.A – Detects the injection into wabmig.exe TrojanDownloader:O97M/Donoff.SA!CAB – Detects CAB files in observed attacks TrojanDownloader:O97M/Donoff.SA!Gen – Detects Office documents in observed attacks Endpoint detection and response (EDR) Alerts with the following titles in the security center can indicate threat activity on your network: Possible exploitation of CVE-2021-40444 (requires Defender Antivirus as the Active AV) The following alerts might also indicate threat activity associated with this threat. These alerts, however, can be triggered by unrelated threat activity and are not monitored in the status cards provided with this report. Suspicious Behavior By Office Application (detects the anomalous process launches that happen in exploitation of this CVE, and other malicious behavior) Suspicious use of Control Panel item Microsoft Defender for Office365 Signals from Microsoft Defender for Office 365 informs Microsoft 365 Defender, which correlates cross-domain threat intelligence to deliver coordinated defense, that this vulnerability has been detected when a document is delivered via email when detonation is enabled. The following alerts in your portal will indicate that a malicious attachment has been blocked, although these alerts are also used for many different threats: Malware campaign detected and blocked Malware campaign detected after delivery Email messages containing malicious file removed after delivery Advanced hunting To locate possible exploitation activity, run the following queries. Relative path traversal (requires Microsoft 365 Defender) Use the following query to surface abuse of Control Panel objects (.cpl) via URL protocol handler path traversal as used in the original attack and public proof of concepts at time of publishing: DeviceProcessEvents | where (FileName in~('control.exe','rundll32.exe') and ProcessCommandLine has '.cpl:') or ProcessCommandLine matches regex @'\".[a-zA-Z]{2,4}:\.\.\/\.\.' The post Analyzing attacks that exploit the CVE-2021-40444 MSHTML vulnerability appeared first on Microsoft Security Blog. Continue reading...
-

3 steps to prevent and recover from ransomware
AWS posted a topic in Microsoft Support & Discussions
On July 14, 2021, the National Cybersecurity Center of Excellence1 (NCCoE) at the National Institute of Standards and Technology2 (NIST) hosted a virtual workshop3 to seek feedback from government and industry experts on practical approaches to preventing and recovering from ransomware and other destructive cyberattacks. After we wrote up our feedback for NIST, we realized it would be helpful to share this perspective more broadly to help organizations better protect themselves against the rising tide of (highly profitable) ransomware attacks. While ransomware and extortion attacks are still evolving rapidly, we want to share a few critical lessons learned and shed some light on common misconceptions about ransomware attacks. Clarifying attack terminology and scope One common misconception about ransomware attacks is that they only involve ransomware—”pay me to get your systems and data back”—but these attacks have actually evolved into general extortion attacks. While ransom is still the main monetization angle, attackers are also stealing sensitive data (yours and your customers’) and threatening to disclose or sell it on the dark web or internet (often while holding onto it for later extortion attempts and future attacks). We’re also seeing a widespread perception that ransomware is still constrained to basic cryptolocker style attacks, first seen in 2013, that only affect a single computer at a time (also known as the commodity model). Today’s attackers have evolved far beyond this—using toolkits and sophisticated affiliate business models to enable human operators to target whole organizations, deliberately steal admin credentials, and maximize the threat of business damage to targeted organizations. The ransomware operators often buy login credentials to organizations from other attack groups, rapidly turning what seems like low-priority malware infections into significant business risks. Simple, prioritized guidance We’ve also seen that many organizations still struggle with where to start, especially smaller operations with limited staff and experience. We believe all organizations should begin with simple and straightforward prioritization of efforts (three steps) and we have published this, along with why each priority is important. Figure 1: Recommended mitigation prioritization. Create detailed instructions Microsoft has also found that many organizations struggle with the next level of the planning process. As a result, we built guidance to make following these steps as clear and easy as possible. Microsoft already works with NIST NCCoE on several efforts, including the Zero Trust effort, which supports Presidential Executive Order (EO) 14028 on Improving the Nation’s Cybersecurity. We welcome the opportunity for any additional ransomware-related work by providing clarifying guidance using whatever tools and technologies organizations have available. Figure 2: Secure backup instructions from Microsoft’s human-operated ransomware page. Microsoft’s recommended mitigation prioritization Based on our experience with ransomware attacks, we’ve found that prioritization should focus on these three steps: prepare, limit, and prevent. This may seem counterintuitive since most people want to simply prevent an attack and move on. But the unfortunate truth is that we must assume breach (a key Zero Trust principle) and focus on reliably mitigating the most damage first. This prioritization is critical because of the high likelihood of a worst-case scenario with ransomware. While it’s not a pleasant truth to accept, we’re facing creative and motivated human attackers who are adept at finding a way to control the complex real-world environments in which we operate. Against that reality, it’s important to prepare for the worst and establish frameworks to contain and prevent attackers’ abilities to get what they’re after. While these priorities should govern what to do first, we encourage organizations to run as many steps in parallel as possible (including pulling quick wins forward from step three whenever you can). Step 1. Prepare a recovery plan: Recover without paying What: Plan for the worst-case scenario and expect that it will happen at any level of the organization. Why: This will help your organization: Limit damage for the worst-case scenario: Restoring all systems from backups is highly disruptive to business, but it’s still more efficient than trying to do recovery using low-quality attacker-provided decryption tools after paying to get the key. Remember: paying is an uncertain path; you have no guarantee that the attackers’ key will work on all your files, that the tools will work effectively, or the attacker—who may be an amateur using a professional’s toolkit—will act in good faith. Limit the financial return for attackers: If an organization can restore business operations without paying, the attack has effectively failed and resulted in zero return on investment for the attackers. This makes it less likely they will target your organization again in the future (and deprives them of funding to attack others). Remember: attackers may still attempt to extort your organization through data disclosure or abusing/selling the stolen data, but this gives them less leverage than possessing the only means of accessing your data and systems. [*]How: Organizations should ensure they: Register risk. Add ransomware to the risk register as a high-likelihood and high-impact scenario. Track mitigation status via your Enterprise Risk Management (ERM) assessment cycle. Define and backup critical business assets. Automatically back up critical assets on a regular schedule, including correct backup of critical dependencies, such as Microsoft Active Directory. Protect backups. To safeguard against deliberate erasure and encryption, use offline storage, immutable storage, and/or out-of-band steps (multifactor authentication or PIN) before modifying or erasing online backups. Test ‘recover from zero’ scenario. Ensure that your business continuity and disaster recovery (BC/DR) can rapidly bring critical business operations online from zero functionality (all systems down). Conduct practice exercises to validate cross-team processes and technical procedures, including out-of-band employee and customer communications (assume all email and chat are down). Important: protect (or print) supporting documents and systems required for recovery, including restoration-procedure documents, configuration management databases (CMDBs), network diagrams, and SolarWinds instances. Attackers regularly destroy these documents. Reduce on-premises exposure. Move data to cloud services with automatic backup and self-service rollback. Step 2. Limit the scope of damage: Protect privileged roles (starting with IT admins) What: Ensure you have strong controls (prevent, detect, respond) for privileged accounts, such as IT admins and other roles with control of business-critical systems. Why: This slows or blocks attackers from gaining complete access to steal and encrypt your resources. Taking away the attacker’s ability to use IT admin accounts as a shortcut to resources will drastically lower the chances that they’ll be successful in controlling enough resources to impact your business and demand payment. How: Enable elevated security for privileged accounts—tightly protect, closely monitor, and rapidly respond to incidents related to these roles. See Microsoft’s recommended steps that: Cover end-to-end session security (including multifactor authentication for admins). Protect and monitor identity systems. Mitigate lateral traversal. Promote rapid threat response. Step 3. Make it harder to get in: Incrementally remove risks What: Prevent a ransomware attacker from entering your environment, as well as rapidly respond to incidents and remove attacker access before they can steal and encrypt data. Why: This causes attackers to fail earlier and more often, undermining their profits. While prevention is the preferred outcome, it may not be possible to achieve 100 percent prevention and rapid response across a real-world organization with a complex multi-platform, multi-cloud estate and distributed IT responsibilities. How: Identify and execute quick wins that strengthen security controls to prevent entry and rapidly detect and evict attackers, while implementing a sustained program that helps you stay secure. Microsoft recommends following the principles outlined in the Zero Trust strategy. Against ransomware, organizations should prioritize: Improving security hygiene by reducing the attack surface and focusing on vulnerability management for assets in their estate. Implementing protection, detection, and response controls for digital assets, as well as providing visibility and alerting on attacker activity while responding to active threats. The takeaway To counter the threat of ransomware, it’s critical to identify, secure, and be ready to recover high-value assets—whether data or infrastructure—in the likely event of an attack. This requires a sustained effort involving obtaining buy-in from the top level of your organization (like the board) to get IT and security stakeholders working together asking nuanced questions. For example, what are the critical parts of the business that could be disrupted? Which digital assets map to these business segments (files, systems, databases)? How can we secure these assets? This process may be challenging, but it will help set up your organization to make impactful changes using the steps recommended above. To learn more, visit our page on how to rapidly protect against ransomware and extortion. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. 1National Cybersecurity Center of Excellence. 2National Institute of Standards and Technology, US Department of Commerce. 3Virtual Workshop on Preventing and Recovering from Ransomware and Other Destructive Cyber Events, National Cybersecurity Center of Excellence, 14 July 2021. The post 3 steps to prevent and recover from ransomware appeared first on Microsoft Security Blog. Continue reading...-
- 1
-

-
Microsoft has been actively tracking a widespread credential phishing campaign using open redirector links. Attackers combine these links with social engineering baits that impersonate well-known productivity tools and services to lure users into clicking. Doing so leads to a series of redirections—including a CAPTCHA verification page that adds a sense of legitimacy and attempts to evade some automated analysis systems—before taking the user to a fake sign-in page. This ultimately leads to credential compromise, which opens the user and their organization to other attacks. The use of open redirects in email communications is common among organizations for various reasons. For example, sales and marketing campaigns use this feature to lead customers to a desired landing web page and track click rates and other metrics. However, attackers could abuse open redirects to link to a URL in a trusted domain and embed the eventual final malicious URL as a parameter. Such abuse may prevent users and security solutions from quickly recognizing possible malicious intent. For instance, users trained to hover on links and inspect for malicious artifacts in emails may still see a domain they trust and thus click it. Likewise, traditional email gateway solutions may inadvertently allow emails from this campaign to pass through because their settings have been trained to recognize the primary URL without necessarily checking the malicious parameters hiding in plain sight. Figure 1. Attack chain for the open redirect phishing campaign This phishing campaign is also notable for its use of a wide variety of domains for its sender infrastructure—another attempt to evade detection. These include free email domains from numerous country code top-level domains (ccTLDs), compromised legitimate domains, and attacker-owned domain generated algorithm (DGA) domains. As of this writing, we have observed at least 350 unique phishing domains used for this campaign. This not only shows the scale with which this attack is being conducted, but it also demonstrates how much the attackers are investing in it, indicating potentially significant payoffs. Today’s email threats rely on three things to be effective: a convincing social engineering lure, a well-crafted detection evasion technique, and a durable infrastructure to carry out an attack. This phishing campaign exemplifies the perfect storm of these elements in its attempt to steal credentials and ultimately infiltrate a network. And given that 91% of all cyberattacks originate with email, Organizations must therefore have a security solution that will provide them multilayered defense against these types of attacks. Microsoft Defender for Office 365 detects these emails and prevents them from being delivered to user inboxes using multiple layers of dynamic protection technologies, including a built-in sandbox that examines and detonates all the open redirector links in the messages, even in cases where the landing page requires CAPTCHA verification. This ensures that even the embedded malicious URLs are detected and blocked. Microsoft Defender for Office 365 is backed by Microsoft experts who enrich the threat intelligence that feeds into our solutions through expert monitoring of email campaigns. Attack analysis: Credential phishing via open redirector links Credential phishing emails represent an extremely prevalent way for threat actors to gain a foothold in a network. The use of open redirects from legitimate domains is far from new, and actors continue to abuse its ability to overcome common precautions. Phishing continues to grow as a dominant attack vector with the goal of harvesting user credentials. From our 2020 Digital Defense Report, we blocked over 13 billion malicious and suspicious mails in the previous year, with more than 1 billion of those emails classified as URL-based phishing threats. In this campaign, we noticed that the emails seemed to follow a general pattern that displayed all the email content in a box with a large button that led to credential harvesting pages when clicked. The subject lines for the emails varied depending on the tool they impersonated. In general, we saw that the subject lines contained the recipient’s domain and a timestamp as shown in the examples below: [Recipient username] 1 New Notification Report Status for [Recipient Domain Name] at [Date and Time] Zoom Meeting for [Recipient Domain Name] at [Date and Time] Status for [Recipient Domain Name] at [Date and Time] Password Notification for [Recipient Domain Name] at [Date and Time] [Recipient username] eNotification Figure 2. Sample phishing email masquerading as an Office 365 notification Once recipients hover their cursor over the link or button in the email, they are shown the full URL. However, since the actors set up open redirect links using a legitimate service, users see a legitimate domain name that is likely associated with a company they know and trust. We believe that attackers abuse this open and reputable platform to attempt evading detection while redirecting potential victims to phishing sites. Figure 3. Hover tip showing an open redirect link with a legitimate domain and phishing link in the URL parameters The final domains used in the campaigns observed during this period mostly follow a specific domain-generation algorithm (DGA) pattern and use .xyz and .club TLDs. The “Re-view invitation” button in Figure 3 points to a URL with a trusted domain followed by parameters, with the actor-controlled domain (c-hi[.]xyz) hidden in plain sight. Figure 4. The actor-controlled domain uses a DGA pattern and a .XYZ top-level domain In August, we detected a fresh spam run from this campaign that used a slightly updated Microsoft-spoofing lure and redirect URL but leveraged the same infrastructure and redirection chain. Figure 5. Sample phishing email from a recent spam run from this phishing campaign These crafted URLs are made possible by open redirection services currently in use by legitimate organizations. Such redirection services typically allow organizations to send out campaign emails with links that redirect to secondary domains from their own domains. For example, a hotel might use open redirects to take email recipients to a third-party booking website, while still using their primary domain in links embedded in their campaign emails. Attackers abuse this functionality by redirecting to their own malicious infrastructure, while still maintaining the legitimate domain in the full URL. The organizations whose open redirects are being abused are possibly unaware that this is even occurring. Redirecting to phishing pages Users who clicked one of the crafted redirect links are sent to a page in attacker-owned infrastructure. These pages used Google reCAPTCHA services to possibly evade attempts at dynamically scanning and checking the contents of the page, preventing some analysis systems from advancing to the actual phishing page. Figure 6. reCAPTCHA service used by phishing page Upon completion of the CAPTCHA verification, the user is shown a site that impersonates a legitimate service, such as Microsoft Office 365, which asks the user for their password. The site is prepopulated with the recipient’s email address to add legitimacy to the request. This technique leverages familiar single sign-on (SSO) behavior to trick users into keying in corporate credentials or other credentials associated with the email address. To do this, attackers send unique URLs to each recipient with PHP parameters that cause tailored information to render in the phishing page. In some instances, phishing pages are specially crafted to include company logos and other branding tied to the recipient’s domain. Figure 7. Fake sign-in page prefilled with the recipient email address alongside a fake error message prompting users to re-enter their passwords If the user enters their password, the page refreshes and displays an error message stating that the page timed out or the password was incorrect and that they must enter their password again. This is likely done to get the user to enter their password twice, allowing attackers to ensure they obtain the correct password. Once the user enters their password a second time, the page directs to a legitimate Sophos website that claims the email message has been released. This adds another layer of false legitimacy to the phishing campaign. Figure 8. Legitimate Sophos page displayed after users re-enter their passwords Tracking attacker-controlled domains Some of the domains used this campaign include the following: c-tl[.]xyz a-cl[.]xyz j-on[.]xyz p-at[.]club i-at[.]club f-io[.]online For the observed campaigns, the sender infrastructure was fairly unique and notable as the actors used a wide variety of sender domains, with most of the domains having at least one of the following characteristics: Free email domains Compromised legitimate domains Domains ending in .co.jp Attacker-owned DGA domains Many of the final domains hosting the phishing pages follow a specific DGA pattern: [letter]-[letter][letter].xyz [letter]-[letter][letter].club The free email domains span a wide variety of ccTLDs, such as: de com.mx com.au ca The attacker-owned DGA domains follow a few distinct patterns, including: [word or string of characters]-[word][number], incrementing by one, for example: masihtidur-shoes08[.]com [number][word or string of characters]-[number], incrementing by one, for example: 23moesian-17[.]com [word][word][number], incrementing by one, for example: notoficationdeliveryamazon10[.]com [word or letters][number]-[number], incrementing by one, for example: dak12shub-3[.]com While these are the most prevalent patterns observed by Microsoft security researchers, over 350 unique domains have been observed during these campaigns. How Microsoft Defender for Office 365 protects against modern email threats The abuse of open redirectors represents an ongoing threat that Microsoft experts constantly monitor, along with other threat trends and attacker techniques used in attacks today. Microsoft’s breadth of visibility into threats combined with our deep understanding of how attackers operate will continue to inform the advanced protection delivered by Microsoft Defender for Office 365 against email-based attacks. For mitigations against the abuse of open redirector links via known third-party platforms or services, users are advised to follow the recommended best practices of their service providers, such as updating to the latest software version, if applicable, to prevent their domains from being abused in future phishing attempts. Microsoft Defender for Office 365 protects customers from this threat by leverages its deep visibility into email threats and advanced detection technologies powered by AI and machine learning. We strongly recommend that organizations configure recommended settings in Microsoft Defender for Office 365, such as applying anti-phishing, Safe Links, and Safe Attachments policies. We also recommend installing the Report Message add-in for Outlook to enable users to report suspicious messages to their security teams and optionally to Microsoft. Attack simulation lets organizations run realistic, yet safe, simulated phishing and password attack campaigns in your organization. These simulated attacks can help identify and find vulnerable users before a real attack makes a real impact. Investigation capabilities in Microsoft Defender 365 allows organizations to respond phishing and other email-based attacks. Microsoft 365 Defender correlates signals from emails and other domains to deliver coordinated defense. Microsoft Defender for Endpoint blocks malicious files and other malware as well as malicious behavior that result from initial access via email. Microsoft Defender SmartScreen integrates with Microsoft Edge to block malicious websites, including phishing sites, scam sites, and other malicious sites, while Network protection blocks connections to malicious domains and IP addresses. Learn how you can stop credential phishing and other email threats through comprehensive, industry-leading protection with Microsoft Defender for Office 365. Microsoft 365 Defender Threat Intelligence Team Advanced hunting queries To locate possible credential phishing activity, run the following advanced hunting queries in Microsoft 365 Defender. Open redirect URLs in t-dot format Find URLs in emails with a leading “t”, indicating possible open redirect URLs. Note: the use of a redirector URL does not necessitate malicious behavior. You must verify whether the emails surfaced via this AHQ are legitimate or malicious. EmailUrlInfo | where Url matches regex @"s?\:\/\/(?:www\.)?t\.(?:[\w\-\.]+\/+)+(?:r|redirect)\/?\?" Open redirect URLs pointing to attacker infrastructure Find URLs in emails possibly crafted to redirect to attacker-controlled URLs. EmailUrlInfo //This regex narrows in on emails that contain the known malicious domain pattern in the URL from the most recent campaigns | where Url matches regex @"^[a-zA-Z]\-[a-zA-Z]{2}\.(xyz|club|shop|online)" Indicators of compromise Following is a list of domains that match the DGA pattern used in sender addresses in this and other malicious campaigns. Note that these have not all been observed in mail flow related to this campaign. masihtidur-shoes08[.]com masihtidur-shoes07[.]com masihtidur-shoes04[.]com masihtidur-shoes02[.]com masihtidur-shoes01[.]com wixclwardwual-updates9[.]com wixclwardwual-updates8[.]com wixclwardwual-updates7[.]com wixclwardwual-updates6[.]com wixclwardwual-updates5[.]com wixclwardwual-updates10[.]com wixclwardwual-updates1[.]com zxcsaxb-good8[.]com zxcsaxb-good6[.]com zxcsaxb-good5[.]com zxcsaxb-good4[.]com zxcsaxb-good3[.]com zxcsaxb-good10[.]com trashxn-euyr9[.]com trashxn-euyr7[.]com trashxn-euyr6[.]com trashxn-euyr5[.]com trashxn-euyr3[.]com trashxn-euyr20[.]com trashxn-euyr2[.]com trashxn-euyr19[.]com trashxn-euyr18[.]com trashxn-euyr17[.]com trashxn-euyr16[.]com trashxn-euyr15[.]com trashxn-euyr14[.]com trashxn-euyr12[.]com trashxn-euyr11[.]com trashxn-euyr10[.]com trashxn-euyr1[.]com berangberang-9[.]com berangberang-7[.]com berangberang-12[.]com berangberang-6[.]com notoficationdeliveryamazon8[.]com berangberang-8[.]com berangberang-3[.]com berangberang-4[.]com berangberang-10[.]com berangberang-11[.]com berangberang-13[.]com berangberang-5[.]com 77support-update23-4[.]com posher876ffffff-30[.]com posher876ffffff-5[.]com posher876ffffff-25[.]com fenranutc0x24ai-11[.]com organix-xtc21[.]com fenranutc0x24ai-13[.]com fenranutc0x24ai-4[.]com fenranutc0x24ai-17[.]com fenranutc0x24ai-18[.]com adminsecurity102[.]com adminsecurity101[.]com 23moesian-17[.]com 23moesian-10[.]com 23moesian-11[.]com 23moesian-26[.]com 23moesian-19[.]com 23moesian-2[.]com cokils2ptys-3[.]com cokils2ptys-1[.]com 23moesian-20[.]com 23moesian-15[.]com 23moesian-18[.]com 23moesian-16[.]com sux71a37-net19[.]com sux71a37-net1[.]com sux71a37-net25[.]com sux71a37-net14[.]com sux71a37-net18[.]com sux71a37-net15[.]com sux71a37-net12[.]com sux71a37-net13[.]com sux71a37-net20[.]com sux71a37-net11[.]com sux71a37-net27[.]com sux71a37-net2[.]com sux71a37-net21[.]com bimspelitskalix-xuer9[.]com account-info005[.]com irformainsition0971a8-net16[.]com bas9oiw88remnisn-12[.]com bas9oiw88remnisn-27[.]com bas9oiw88remnisn-26[.]com bas9oiw88remnisn-11[.]com bas9oiw88remnisn-10[.]com bas9oiw88remnisn-5[.]com bas9oiw88remnisn-13[.]com bas9oiw88remnisn-1[.]com bas9oiw88remnisn-7[.]com bas9oiw88remnisn-3[.]com bas9oiw88remnisn-20[.]com bas9oiw88remnisn-8[.]com bas9oiw88remnisn-23[.]com bas9oiw88remnisn-24[.]com bas9oiw88remnisn-4[.]com bas9oiw88remnisn-25[.]com romanseyilefreaserty0824r-2[.]com romanseyilefreaserty0824r-1[.]com sux71a37-net26[.]com sux71a37-net10[.]com sux71a37-net17[.]com maills-activitymove02[.]com maills-activitymove04[.]com solution23-servviue-26[.]com maills-activitymove01[.]com copris7-yearts-6[.]com copris7-yearts-9[.]com copris7-yearts-5[.]com copris7-yearts-8[.]com copris7-yearts-37[.]com securityaccount102[.]com copris7-yearts-4[.]com copris7-yearts-40[.]com copris7-yearts-7[.]com copris7-yearts-38[.]com copris7-yearts-39[.]com romanseyilefreaserty0824r-6[.]com rick845ko-3[.]com rick845ko-2[.]com rick845ko-10[.]com fasttuamz587-4[.]com winb2as-wwersd76-19[.]com winb2as-wwersd76-4[.]com winb2as-wwersd76-6[.]com org77supp-minty662-8[.]com winb2as-wwersd76-18[.]com winb2as-wwersd76-1[.]com winb2as-wwersd76-10[.]com org77supp-minty662-9[.]com winb2as-wwersd76-12[.]com winb2as-wwersd76-20[.]com account-info003[.]com account-info012[.]com account-info002[.]com laser9078-ter17[.]com account-info011[.]com account-info007[.]com notoficationdeliveryamazon1[.]com notoficationdeliveryamazon20[.]com notoficationdeliveryamazon7[.]com notoficationdeliveryamazon17[.]com notoficationdeliveryamazon12[.]com contackamazon1[.]com notoficationdeliveryamazon6[.]com notoficationdeliveryamazon5[.]com notoficationdeliveryamazon4[.]com notoficationdeliveryamazon18[.]com notoficationdeliveryamazon13[.]com notoficationdeliveryamazon3[.]com notoficationdeliveryamazon14[.]com gaplerr-xt5[.]com posher876ffffff-29[.]com kenatipurecehkali-xt3[.]com kenatipurecehkali-xt13[.]com kenatipurecehkali-xt4[.]com kenatipurecehkali-xt12[.]com kenatipurecehkali-xt5[.]com wtbwts-junet1[.]com kenatipurecehkali-xt6[.]com hayalanphezor-2sit[.]com hayalanphezor-1sit[.]com noticesumartyas-sc24[.]com noticesumartyas-sc13[.]com noticesumartyas-sc2[.]com noticesumartyas-sc17[.]com noticesumartyas-sc22[.]com noticesumartyas-sc5[.]com noticesumartyas-sc4[.]com noticesumartyas-sc21[.]com noticesumartyas-sc25[.]com appgetbox3[.]com notoficationdeliveryamazon19[.]com notoficationdeliveryamazon10[.]com appgetbox9[.]com appgetbox8[.]com appgetbox6[.]com notoficationdeliveryamazon2[.]com appgetbox7[.]com appgetbox5[.]com notoficationdeliveryamazon23[.]com appgetbox10[.]com notoficationdeliveryamazon16[.]com hvgjgj-shoes08[.]com hvgjgj-shoes13[.]com jgkxjhx-shoes09[.]com hvgjgj-shoes15[.]com hvgjgj-shoes16[.]com hvgjgj-shoes18[.]com hvgjgj-shoes20[.]com hvgjgj-shoes12[.]com jgkxjhx-shoes02[.]com hvgjgj-shoes10[.]com jgkxjhx-shoes03[.]com hvgjgj-shoes11[.]com hvgjgj-shoes14[.]com jgkxjhx-shoes05[.]com jgkxjhx-shoes04[.]com hvgjgj-shoes19[.]com jgkxjhx-shoes08[.]com hpk02h21yyts-6[.]com romanseyilefreaserty0824r-7[.]com gets25-amz[.]net gets30-amz[.]net gets27-amz[.]net gets28-amz[.]net gets29-amz[.]net gets32-amz[.]net gets3-amz[.]net gets31-amz[.]net noticesumartyas-sc19[.]com noticesumartyas-sc23[.]com noticesumartyas-sc18[.]com noticesumartyas-sc15[.]com noticesumartyas-sc20[.]com noticesumartyas-sc16[.]com noticesumartyas-sc29[.]com rick845ko-1[.]com bas9oiw88remnisn-9[.]com rick845ko-5[.]com bas9oiw88remnisn-21[.]com bas9oiw88remnisn-2[.]com bas9oiw88remnisn-19[.]com rick845ko-6[.]com bas9oiw88remnisn-22[.]com bas9oiw88remnisn-17[.]com bas9oiw88remnisn-16[.]com adminmabuk103[.]com account-info008[.]com suppamz2-piryshj01-3[.]com dak12shub-1[.]com securemanageprodio-02[.]com securemanageprodio-05[.]com securemanageprodio-01[.]com dak12shub-3[.]com dak12shub-9[.]com dak12shub-8[.]com dak12shub-6[.]com dak12shub-10[.]com dak12shub-4[.]com securemanageprodio-03[.]com org77supp-minty662-7[.]com winb2as-wwersd76-7[.]com org77supp-minty662-10[.]com bimspelitskalix-xuer2[.]com gets34-amz[.]net gets35-amz[.]net service-account-7254[.]com service-account-76357[.]com service-account-7247[.]com account-info004[.]com service-account-5315[.]com bas9oiw88remnisn-14[.]com solution23-servviue-23[.]com organix-xtc18[.]com romanseyilefreaserty0824r-4[.]com hayalanphezor-7sit[.]com bimspelitskalix-xuer7[.]com securemanageprodio-04[.]com solution23-servviue-15[.]com solution23-servviue-1[.]com suppamz2-piryshj01-9[.]com suppamz2-piryshj01-6[.]com solution23-servviue-25[.]com solution23-servviue-7[.]com solution23-servviue-16[.]com solution23-servviue-11[.]com solution23-servviue-27[.]com romanseyilefreaserty0824r-5[.]com cokils2ptys-6[.]com solution23-servviue-9[.]com solution23-servviue-19[.]com solution23-servviue-8[.]com solution23-servviue-17[.]com solution23-servviue-18[.]com suppamz2-piryshj01-1[.]com solution23-servviue-30[.]com solution23-servviue-13[.]com solution23-servviue-12[.]com solution23-servviue-10[.]com solution23-servviue-4[.]com solution23-servviue-20[.]com solution23-servviue-24[.]com solution23-servviue-5[.]com solution23-servviue-14[.]com service-account-7243[.]com service-account-735424[.]com service-account-8457845[.]com service-account-374567[.]com service-account-764246[.]com service-account-762441[.]com gxnhfghnjzh809[.]com xcfhjxfyxnhnjzh10[.]com accountservicealert002[.]com accountservicealert003[.]com care887-yyrtconsumer23-24[.]com bas9oiw88remnisn-15[.]com care887-yyrtconsumer23-23[.]com care887-yyrtconsumer23-27[.]com care887-yyrtconsumer23-25[.]com care887-yyrtconsumer23-26[.]com laser9078-ter11[.]com bimspelitskalix-xuer6[.]com laser9078-ter10[.]com hayalanphezor-6sit[.]com hayalanphezor-4sit[.]com hayalanphezor-3sit[.]com romanseyilefreaserty0824r-3[.]com solution23-servviue-6[.]com ressstauww-6279-3[.]com ressstauww-6279-10[.]com sytesss-tas7[.]com ressstauww-6279-7[.]com ressstauww-6279-1[.]com hvgjgj-shoes01[.]com ketiak-muser14[.]com ketiak-muser13[.]com ketiak-muser15[.]com spammer-comingson01[.]com spammer-comingson02[.]com spammer-comingson04[.]com spammer-comingson05[.]com spammer-comingson07[.]com posidma-posidjar01[.]com posidma-posidjar03[.]com posidma-posidjar05[.]com posidma-posidjar06[.]com tembuslah-bandar01[.]com tembuslah-bandar02[.]com tembuslah-bandar03[.]com tembuslah-bandar04[.]com tembuslah-bandar05[.]com tembuslah-bandar06[.]com tembuslah-bandar07[.]com tembuslah-bandar08[.]com tembuslah-bandar09[.]com tembuslah-bandar10[.]com The post Widespread credential phishing campaign abuses open redirector links appeared first on Microsoft Security Blog. Continue reading...
-
Mozi is a peer-to-peer (P2P) botnet that uses a BitTorrent-like network to infect IoT devices such as network gateways and digital video records (DVRs). It works by exploiting weak telnet passwords1 and nearly a dozen unpatched IoT vulnerabilities2 and it’s been used to conduct distributed denial-of-service (DDoS) attacks, data exfiltration, and command or payload execution3. While the botnet itself is not new, Microsoft’s IoT security researchers recently discovered that Mozi has evolved to achieve persistence on network gateways manufactured by Netgear, Huawei, and ZTE. It does this using clever persistence techniques that are specifically adapted to each gateway’s particular architecture. Network gateways are a particularly juicy target for adversaries because they are ideal as initial access points to corporate networks. Adversaries can search the internet for vulnerable devices via scanning tools like Shodan, infect them, perform reconnaissance, and then move laterally to compromise higher value targets—including information systems and critical industrial control system (ICS) devices in the operational technology (OT) networks. By infecting routers, they can perform man-in-the-middle (MITM) attacks—via HTTP hijacking and DNS spoofing—to compromise endpoints and deploy ransomware or cause safety incidents in OT facilities. In the diagram below we show just one example of how the vulnerabilities and newly discovered persistence techniques could be used together. Of course, there are many more possibilities. Figure 1: Attack flow for Mozi botnet. Guidance: Proactive defense Businesses and individuals that are using impacted network gateways (Netgear, Huawei, and ZTE) should take the following steps immediately to ensure they are resistant to the attacks described in this blog: Ensure all passwords used on the device are created using strong password best practices. Ensure devices are patched and up-to-date. Doing so will reduce the attack surfaces leveraged by the botnet and prevent attackers from getting into a position where they can use the newly discovered persistence and other exploit techniques described in more detail below. The intelligence of our security cloud and all of our Microsoft Defender products, including Microsoft 365 Defender (XDR), Azure Sentinel (cloud-native SIEM/SOAR), as well as Azure Defender for IoT also provide protection from this malware and are continuously updated with the latest threat intelligence as the threat landscape continues to evolve. The recent acquisition of ReFirm Labs will further enhance Azure Defender for IoT’s ability to protect customers with its upcoming deep firmware scanning, analysis capabilities which will be integrated with Device Update for Azure IoT Hub’s patching capabilities. Technical description of new persistence capabilities Apart from its known extensive P2P and DDoS abilities, we have recently observed several new and unique capabilities of the Mozi botnet. Targeting Netgear, Huawei, and ZTE gateways, the malware now takes specific actions to increase its chances of survival upon reboot or any other attempt by other malware or responders to interfere with its operation. Here are some examples: Achieving privileged persistence A specific check is conducted for the existence of the /overlay folder, and whether the malware does not have write permissions to the folder /etc. In this case, it will try to exploit CVE-2015-1328. Successful exploitation of the vulnerability will grant the malware access to the following folders: /etc/rc.d /etc/init.d Then the following actions are taken: It places the script file named S95Baby.sh in these folders. The script runs the files /usr/networks or /user/networktmp. These are copies of the executable. It adds the script to /etc/rcS.d and /etc/rc.local in case it lacks privileges. ZTE devices A specific check is conducted for the existence of the /usr/local/ct folder; this serves as an indicator of the device being a ZTE modem/router device. The following actions are taken: It copies its other instance (/usr/networks) to /usr/local/ct/ctadmin0; this provides persistency for the malware. It deletes the file /home/httpd/web_shell_cmd.gch. This file can be used to gain access through exploitation of the vulnerability CVE-2014-2321; deleting it prevents future attacks. It executes the following commands. These disable Tr-069 and its ability to connect to auto-configuration server (ACS). Tr-069 is a protocol for remote configuration of network devices; it’s usually utilized by service providers to configure customers’ equipment. sendcmd 1 DB set MgtServer 0 Tr069Enable 1 sendcmd 1 DB set PdtMiddleWare 0 Tr069Enable 0 sendcmd 1 DB set MgtServer 0 URL http://127.0.0.1 sendcmd 1 DB set MgtServer 0 UserName notitms sendcmd 1 DB set MgtServer 0 ConnectionRequestUsername notitms sendcmd 1 DB set MgtServer 0 PeriodicInformEnable 0 sendcmd 1 DB save Huawei devices Execution of the following commands changes the password and disables the management server for Huawei modem/router devices. It also prevents others from gaining access to the device through the management server. cfgtool set /mnt/jffs2/hw_ctree.xml InternetGatewayDevice.ManagementServer URL http://127.0.0.1 cfgtool set /mnt/jffs2/hw_ctree.xml InternetGatewayDevice.ManagementServer ConnectionRequestPassword acsMozi To provide an additional level of persistence it also creates the following files if needed and appends an instruction to run its copy from /usr/networks. /mnt/jffs2/Equip.sh /mnt/jffs2/wifi.sh /mnt/jffs2/WifiPerformance.sh Preventing remote access The malware blocks the following TCP ports: 23—Telnet 2323—Telnet alternate port 7547—Tr-069 port 35000—Tr-069 port on Netgear devices 50023—Management port on Huawei devices 58000—Unknown usage These ports are used to gain remote access to the device. Shutting them increases the malware’s chances of survival. Script infector It scans for .sh files in the filesystem, excluding the following paths: /tmp /dev /var /lib /haha /proc /sys It also appends a line to each file. The line instructs the script to run a copy of the malware from /usr/networks. This increases its chances of survival on various devices. Traffic injection and DNS spoofing capabilities The malware receives commands from its distributed hash table (DHT) network. The latter is a P2P protocol for decentralized communications. The commands are received and stored in a file, of which parts are encrypted. This module works only on devices capable of IPv4 forwarding. It checks whether /proc/sys/net/ipv4/ip_forward is set to 1; such positive validation is characteristic of routers and gateways. This module works on ports UDP 53 (DNS) and TCP 80 (HTTP). Configuration commands Apart from the previously documented commands in Table 1—for more information, read A New Botnet Attack Just Mozied Into Town—we also discovered these commands: [hi] – Presence of the command indicates it needs to use the MiTM module. [set] – Contains encrypted portion which describes how to use the MiTM module. Command Description [ss] Bot role [ssx] enable/disable tag [ss] [cpu] CPU architecture [cpux] enable/disable tag [cpu] [nd] new DHT node [hp] DHT node hash prefix [atk] DDoS attack type [ver] Value in V section in DHT protocol [sv] Update config [ud] Update bot [dr] Download and execute payload from the specified URL [rn] Execute specified command [dip] ip:port to download Mozi bot [idp] report bot [count] URL that used to report bot Table 1. Previously documented Mozi commands. DNS spoofing Mozi receives a very simple list of DNS names which are then spoofed. Its structure is as follows: : Each DNS request is answered with the spoofed IP. This is an efficient technique to redirect traffic to the attackers’ infrastructure. HTTP session hijacking This part of the MITM functionality is responsible for hijacking HTTP sessions. Not every HTTP request is processed. There are several conditions for it to be qualified for hijacking, most of which are meant to restrict the module’s “level of noise” to lower the chances of it being discovered by network defenders. The following are some of the rules: It works only for HTTP GET requests. This means forms and more complex requests are ignored. A random number in the configuration states how many queries it would inject. This shows the attackers understand the importance of hiding this functionality. In other words, they are lowering its footprint in order to avoid alerting the user of the hijacking. Some domains are ignored, most likely to avoid interference with the normal operation of certain types of equipment or to avoid detection by various security countermeasures. It only spoofs external traffic; HTTP requests inside the LAN are ignored. A test is conducted to validate that the URL doesn’t contain the string “veri=20190909”—this is done to prevent injecting the already-injected pages. It returns a random HTTP response derived from a predefined list of responses. It has nine different types of hijacking; the specific type of hijacking and its parameters are derived from the configuration file. Below are a few examples of these hijacking techniques. Some of the spoofing occurs via redirection using the HTTP Location header, as seen below. Example 1: Spoofing via redirection using the HTTP Location header. This should automatically redirect without any user interaction. Example 2: A hijacking method that only injects JavaScript; it is designed for ajax calls that evaluate the response, so this hijack method will inject a new script into the page. Protecting from Mozi Malware It is important to note that Microsoft Security solutions have already been updated to protect, detect, and respond to Mozi and its enhanced capabilities. Customers can use the network device discovery capabilities found in Microsoft Defender for Endpoint to discover impacted internet gateways on their IT networks and run vulnerability assessments. Additionally, the agentless network-layer capabilities of Azure Defender for IoT can be used to perform continuous asset discovery, vulnerability management, and threat detection for IoT and OT devices on their OT networks. This solution can be rapidly deployed (typically less than one day per site), and it is available for both on-premises and cloud-connected environments. Defender for IoT is also tightly integrated with Azure Sentinel, which provides a bird’s eye view across your entire enterprise—leveraging AI and automated playbooks to detect and respond to multi-stage attacks that often cross IT and OT boundaries. In addition to detecting targeted attacks and living-off-the-land (LOTL) tactics via IoT/OT-aware behavioral analytics, Defender for IoT incorporates threat information derived from trillions of signals analyzed daily by Microsoft’s global team of security experts using AI and machine learning. This helps ensure our customers are continuously protected against both new and existing threats. While we offer many solutions, it remains critical that each of the recommendations in the “Guidance: Proactive defense” section above be implemented on the impacted internet gateways to prevent them from becoming a vector of attack. To learn more about how our integrated SIEM/XDR solutions, combined with Azure Defender for IoT, can help secure your organization, please refer to the following resources: Azure Defender for IoT Overview of Azure Defender for IoT Azure Sentinel Overview of Azure Sentinel Microsoft 365 Defender Overview of Microsoft 365 Defender Device discovery overview for Microsoft Defender for Endpoint and Microsoft 365 Defender To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. 1Mozi, Another Botnet Using DHT, Alex Turing, Hui Wang, NetLab 360, 23 December 2019. 2Mozi IoT Botnet, CERT-In, Ministry of Electronics and Information Technology Government of India, 12 November 2020. 3New Mozi Malware Family Quietly Amasses IoT Bots, Black Lotus Labs, Lumen, 13 April 2020. The post How to proactively defend against Mozi IoT botnet appeared first on Microsoft Security Blog. Continue reading...
-
We learn a tremendous amount from your feedback and I'm excited to announce that we are now extending combined cumulative update capabilities to more versions of Windows! Servicing stack updates (SSUs) provide fixes to the servicing stack, the component that installs Windows updates. Last September, we announced that we were working to simplify the on-premises deployment of servicing stack updates. We shared a plan to ease the efforts of IT administrators by providing a single monthly update containing both the latest cumulative update (LCU) fixes as well as the latest SSU, if applicable. This single update package can be installed on a device to ensure that updates are applied in the correct order, thus reducing the chances of installation failures. Based on learnings from your comments and suggestions, we are improving this capability. Let's take a closer look! Expanding capabilities to more versions of Windows We are thrilled to announce that combined cumulative update deployment capabilities are coming to Windows 10, version 1809, Windows Server 2019, and Windows 10, version 1909. Beginning today, you can leverage the Windows Insider Pre-release Category in Windows Server Update Services (WSUS) to deploy the August 2021 monthly quality update and SSU together as a single package to devices running these versions. More detailed instructions on how to leverage the Windows Insider Pre-release update to deploy these combined packages can be found in our previous post. Deploy Windows SSUs and LCUs together with one cumulative update. Note: Devices running Windows 10, version 1809 will first need the July 20, 2021 optional cumulative update for .NET Framework 3.5 and 4.7.2 (KB5004335) or later in order to leverage this new capability. Devices running Windows 10, version 1909 will first need the July 13, 2021 cumulative update for .NET Framework 3.5 and 4.8 (KB5003539) or later. Dependencies on SSUs and rare exceptions When we released the first combined Windows cumulative update package, we simultaneously introduced a prerequisite on the September 2020, or later, SSU. This SSU contained the changes that were needed to make devices compatible with the combined cumulative update package, enabling the servicing stack to: Expand the contents of this package. Orchestrate the install of a new SSU. Proceed with installing an LCU using the updated version of servicing stack. Similarly, when we have updates to the servicing stack that improve reliability or address a vulnerability in the update process for the LCU, they are effective immediately for the installation of the LCU packaged inside the combined update package type that carries the SSU. In rare cases, especially as we enhance this capability, there can be breaking changes in the interface between the servicing stack and the combined update package format. In these circumstances, an SSU that makes the servicing stack compatible with the new interface must be deployed prior to the combined (LCU + SSU) update. Such a change occurred with the May 11, 2021 SSU which is included in the May 2021 Windows 10 monthly quality update (KB5003173) for Windows 10. Here we enhanced bootstrapping capability of servicing stack for offline servicing of the OS image. This introduced a dependency on a new interface, hence the June 2021 monthly quality update (KB5003637) included a prerequisite. While this had little to no impact on most organizations who regularly leverage monthly updates, or any impact on those who connect their devices directly to Windows Update, some organizations were negatively affected by this prerequisite. Therefore, today we are releasing a standalone SSU (KB5005260) that can be applied to Windows 10 devices that have not yet installed the May 2021 monthly quality update. Going forward, we will strive to minimize any changes that require an SSU as a prerequisite, but if such a change occurs, we will make a standalone SSU available in addition to the combined monthly update to ensure easy manageability. Please continue to share your thoughts Thank you for your continued enthusiasm and feedback on making our improved servicing capabilities the best they can be. For the latest updates on new releases, tools, and resources, stay tuned to this blog and follow us @MSWindowsITPro and @ariaupdated on Twitter, or visit the Windows Tech Community for more information. Continue reading...
-

Don't Install the Leaked Windows 11 Build
AWS replied to starbuck's topic in Tech Help and Discussions
Leaks happen and people will always install them. On another note I just got my invite to the Windows 11 beta. The email said they expect to open the beta in late fall. -
Organizations often know they need to identify and address their cybersecurity blind spots. They also know the technology exists to help them do that. However, they don’t often understand how to communicate this need within their organization to justify the expense, nor do they know how to share with employees how they may be impacted. When I spoke with Jules Okafor on an episode of Afternoon Cyber Tea with Ann Johnson, she shared how she has seen many cybersecurity projects fail not because of the technology put in place, but rather, the organization’s inability to communicate responsibilities or the expected results. One of the biggest pitfalls is the result of a very good intention when a new technology is excitedly implemented before developing a process. Jules Okafor, JD, is the Founder and CEO of RevolutionCyber, a full-service privacy information security awareness and marketing communications firm, and the former Senior Vice President of Global Security Solutions for Fortress Information Security. Jules also advocates for greater diversity and inclusion in the cybersecurity industry. During our discussion, she shared how she believes the industry has been insulated from discussions about race because the focus has been on protecting companies from cyberattacks without the lens of futureproofing against biases. Companies can and should be doing more, including sharing examples of technology bias with the public, assessing their own practices to check for unintended bias, and listening when employees approach management and human resources with concerns. Many accomplished women and people of color are leaving the industry because they don’t feel heard. In the real world, bias and racism are costing people their lives. In the online world, bias in technologies, like facial recognition software, can be detrimental. While on a recent Slack channel conversation where a participant mentioned a product that promised to let you undertake diversity and inclusion work via text message, she thought, “This is the problem.” This experience suggests that people are trying to automate complex, multi-generational problems to satisfy compliance. Until his death, civil rights activist and leader John Lewis was all-in when it came to fighting racial injustice and bias. Until people in the cybersecurity industry are all-in to that extent, there won’t be much change. During our conversation, we also spoke about how a Craigslist post started her cybersecurity career and strategies to effectively sell cybersecurity solutions. One aspect of her job she especially enjoys is making the technical understandable to non-technical people. This can be a missing piece for some technology companies, too. Many are overly focused on building tools rather than on addressing business challenges. Most successful cybersecurity is invisible to most people, so purchasing technology becomes a tangible way to justify their role. To learn steps to take that show your company cares about becoming more diverse and solving business problems, listen to Afternoon Cyber Tea with Ann Johnson: Fortifying security strategies with a cyber mindset on Apple Podcasts or Podcast One. What’s next A new season of Afternoon Cyber Tea with Ann Johnson will launch on June 15, 2021. In this important cyber series, I talk with cybersecurity influencers about trends shaping the threat landscape and explore the risk and promise of systems powered by AI, IoT, and other emerging tech. You can listen to Afternoon Cyber Tea with Ann Johnson on: Apple Podcasts: You can also download the episode by clicking the Episode Website link. Podcast One: Includes the option to subscribe, so you’re notified as soon as new episodes are available. CISO Spotlight page: Listen alongside our CISO Spotlight episodes, where customers and security experts discuss similar topics such as Zero Trust, compliance, going passwordless, and more. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. Or reach out to me on LinkedIn or Twitter if you have guest or topic suggestions. The post Afternoon Cyber Tea: Cybersecurity challenged to meet diversity goals appeared first on Microsoft Security. Continue reading...
-
This blog post is part of the Microsoft Intelligent Security Association (MISA) guest blog series. Learn more about MISA. The fight against malware has become the epic battle of our generation, placing businesses of all sizes against a never-ending stream of hackers and zero-day attacks bent on compromising security perimeters. The recent SolarWinds breach¹ illustrates how much is currently at stake. According to the Verizon 2020 Data Breach Investigations Report2, an estimated 94 percent of malware is delivered via email with 90 percent of malware hidden in common file types such as PDF, Word, Excel, and Zip. What is Content Disarm and Reconstruction (CDR)? CDR describes the process of creating a safe copy of an original file by including only the safe elements from the original file. The process offers a detection-less and streamlined solution that is notably different from common sandbox-based antimalware tools in the market. On a granular level, CDR focuses on verifying the validity of the file structure on the binary level and disarms both known and unknown threats. With CDR, most malware forms–including zero-days, which are maliciously embedded in transit files–are sanitized and purged of malicious content. This ensures the end-user can access only malware-free content, while still maintaining maximum file functionality. odix, an Israel-based cybersecurity company leading the way in content disarm and reconstruction technology, has developed a range of solutions to fully complement and strengthen existing Microsoft security systems. Through the addition of FileWall, a Microsoft certified Cloud Solution Provider (CSP) can easily improve email security within a few clicks. FileWall’s granular type filter optimizes administrator’s malware protection capabilities, allowing them to easily ensure only necessary file types can get through to the end-user, according to their varying file access permissions. The FileWall type filter ideally leverages CDR technology to purge embedded and nested files. By adding the CDR process to Microsoft’s existing sandbox-based protections, users are better prepared to defend against the threats of unknown malware. How FileWall integrates with Microsoft security technology odix’s FileWall solution was created from square one to fully integrate with the Microsoft Graph Security API, Microsoft Azure Sentinel, and Exchange Online. As a result of odix’s native level integration with many of Microsoft’s core security mechanisms, FileWall’s deep file inspection capabilities don’t impact latency or compromise Microsoft’s native security protection. FileWall’s integration enables simultaneous reporting of malicious events and embedded suspicious content discovered within files to Microsoft Azure Sentinel. For the user in complex file scenarios, such as nested files, password-protected attachments where traditional sandbox methods could miss or result in lengthy-time delays, and disruption of business processes, FileWall relies upon a detection-less process to remove unknown malware and block malicious elements embedded in files. FileWall provides near-instant sanitization and reconstruction of files with simple click deployment. FileWall provides maximum security cooperation and allows for greater visibility of incoming files and triggers an automated response from Microsoft Exchange Online to mitigate the impact of malware accordingly. Microsoft 365 and Exchange Online administrators can get a free license of FileWall here. Protecting emails: FileWall’s granular type filter The FileWall file type filter allows the Microsoft 365 system admin to define which file types are permitted to enter the organization and which should be blocked. This minimizes the attack surface the organization is exposing via email by eliminating the threat vectors available in certain file types. The type filter has three main controls: On/Off: Enabling or disabling the filter functionality on all file types. Work mode (Whitelist/Blacklist): The ability to create pre-set lists of permitted and non-permitted file types for specific users within the organization. Default settings: Suggested default policy by FileWall which includes 204 file types categorized as dangerous [including executable files (exe)], windows batch files (bat), windows links (lnk), and others. The sandbox can manage executables and active content. This allows the sandbox to work only on files that were not treated by FileWall. As most organizational traffic consists of non-executable documents, this method can reduce sandbox load by 90 to 95 percent, lowering the total costs and improving the average latency. FileWall complements Exchange Online security capabilities As a native-level security add-on within Microsoft Exchange Online, with no SMTP relay required, FileWall doesn’t harm productivity. Consequently, all FileWall’s settings have been configured to complement existing security protocols. FileWall’s speed in processing files is near-instantaneous for common file types. Learn more odix is an industry leader in developing and optimizing CDR technology for the enterprise and small and medium business markets. odix’s flagship CDR add-on, FileWall, is available for direct purchase in the Microsoft marketplaces. FileWall has already proven its worth in the field, providing best-in-class email protection in a broad range of IT and industrial settings. Clariter, a global clean-tech company, was seeking an additional security layer to enhance its email security systems and found FileWall the ideal solution. Read the full case study here. To learn more about FileWall, visit our listing in the Azure Marketplace. To learn more about the Microsoft Intelligent Security Association (MISA), visit our website, where you can learn about the MISA program, product integrations and find MISA members. Visit the to learn about the strength of member integrations with Microsoft products. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. ¹SolarWinds hack was ‘largest and most sophisticated attack’ ever: Microsoft president, The Associated Press, February 14, 2021. 22020 Data Breach Investigations Report, Verizon Business, May 19, 2020. The post odix and Microsoft: Protecting users against malware attacks with free FileWall license appeared first on Microsoft Security. Continue reading...
-
Modern computing devices can be thought of as a collection of discrete microprocessors each with a dedicated function like high-speed networking, graphics, Disk I/O, AI, and everything in between. The emergence of the intelligent edge has accelerated the number of these cloud-connected devices that contain multiple specialized sub-processors each with its own firmware layer and often a custom operating system. Many vulnerability analysis and endpoint detection and response (EDR) tools find it challenging to monitor and protect devices at the firmware level, leading to an attractive security gap for attackers to exploit. At the same time, we have also seen growth in the number of attacks against firmware where sensitive information like credentials and encryption keys are stored in memory. A recent survey commissioned by Microsoft of 1,000 security decision-makers found that 83 percent had experienced some level of firmware security incident, but only 29 percent are allocating resources to protect that critical layer. And according to March 2021 data from the National Vulnerability Database included in a presentation from the Department of Homeland Security’s Cybersecurity and Infrastructure Agency (CISA) at the 2021 RSA, difficult-to-patch firmware attacks are continuing to rise. Microsoft’s Azure Defender for IoT team (formerly CyberX) recently announced alongside the Department of Homeland Security a series of more than 25 critical severity vulnerabilities in IoT and OT devices The challenge in securing these devices starts with securing the supply chain. Device builders typically integrate third-party software and components in their solution, but they are missing the tools and the expertise in analyzing the components they consume and as a result may unknowingly ship devices with security vulnerabilities. This is where ReFirm Labs comes in. Microsoft believes that firmware is not a future threat, but an imperative to secure now as more devices flood the market and expand the available attack surface. We are committed to helping customers protect from these sophisticated threats now and in the future, which is why we’re announcing that we have acquired ReFirm Labs. Microsoft will enhance chip-to-cloud protection with ReFirm Labs We are excited to announce that ReFirm Labs is joining Microsoft to enrich our firmware analysis and security capabilities across devices that form the intelligent edge, from servers to IoT. The addition of ReFirm Labs to Microsoft will bring both world-class expertise in firmware security and the Centrifuge firmware platform to enhance our ability to analyze and help protect firmware backed by the power and speed of our cloud. ReFirm are the authors of the well-respected Binwalk open-source software, which has been used to analyze thousands of device types for firmware security issues, uncovering unpatched common vulnerabilities and exposures (CVEs), insecure secrets, and a multitude of other security problems in plugin IoT devices and embedded firmware. ReFirm’s firmware analysis technology will advance Microsoft’s existing capabilities to help secure IoT and OT devices via Azure Defender for IoT which was recently enhanced with technology from our acquisition of CyberX. Together, we will provide device builders and customers the ability to both discover, protect, and assess device risk both at the firmware and network level and then patch devices with an easy-to-use cloud-based solution as is explained in this video. Microsoft has already taken steps to bring the power of the cloud to help secure and eliminate gaps between hardware and software with the announcement of Secured-core PCs, the creation of the Pluton security processor with our partners, and most recently the extension of secured-core to servers and edge devices. This acquisition marks the next step in our journey and ability to help secure customers from the chip to the cloud, backed by more than 3,500 defenders at Microsoft and the >8 trillion security signals we process every day. We are thrilled to take this next step with ReFirm Labs to proactively address what is already becoming the next big attack surface, firmware. Together, will continue to provide innovation and value to our customers by helping them discover, monitor, and update all of their network-connected devices. The technology and expertise that ReFirm brings will be an incredible addition to Microsoft and help us continue to deliver on our commitment to protecting from the chip to the cloud. Learn more To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. The post Microsoft acquires ReFirm Labs to enhance IoT security appeared first on Microsoft Security. Continue reading...
-
The future of Internet Explorer (“IE”) on Windows 10 is in Microsoft Edge. What does this mean for commercial organizations, IT admins, developers, and end users? Microsoft Edge brings you a faster, more secure, and more modern web experience than Internet Explorer. Also, Microsoft Edge with Internet Explorer mode (“IE mode”), is the only browser with built-in compatibility for legacy IE-based sites and apps. As announced today, Microsoft Edge with IE mode is officially replacing the Internet Explorer 11 desktop application on Windows 10. As a result, the Internet Explorer 11 desktop application will go out of support and be retired on June 15, 2022 for certain versions of Windows 10. Which platforms will be affected when the IE11 desktop application is retired and goes out of support on June 15, 2022? In scope at the time of this announcement (will be retired): Internet Explorer 11 desktop application delivered via the Semi-Annual Channel (SAC): Windows 10 client SKUs (version 20H2 and later) Windows 10 IoT (version 20H2 and later) Out of scope at the time of this announcement (unaffected): Internet Explorer mode in Microsoft Edge Internet Explorer platform (MSHTML/Trident), including WebOC Internet Explorer 11 desktop application on: Windows 8.1 Windows 7 Extended Security Updates (ESU) Windows 10 Server SAC (all versions) Windows 10 IoT Long-Term Servicing Channel (LTSC) (all versions) Windows 10 Server LTSC (all versions) Windows 10 client LTSC (all versions) What about Windows 10 LTSC and Windows Server? In-market Windows 10 LTSC and Windows Server are out of scope (unaffected) for this change. What if Microsoft Edge is already installed? Great! You already have a faster, more secure, and more modern browser than Internet Explorer and have completed some of the steps to help with your migration. If you’re an organization, the next steps will be to determine if your organization has legacy browser dependencies. To enable legacy browser support in Microsoft Edge, you’ll need to set up Internet Explorer mode. Learn more on our Internet Explorer mode webpage and read the Getting Started guide. What does this announcement mean for my organization? If your organization has legacy apps and sites dependent on IE11, you can follow the Getting Started Guide to start configuring IE mode. You may be concerned about change management, so please check out the Internet Explorer Retirement Adoption Kit for ready-made content to help you notify users and leaders in your organization about the upcoming changes and help move them to Microsoft Edge. What does this announcement mean for developers? Apps developed for IE should work in Microsoft Edge through IE mode. If you encounter an issue, contact App Assure for remediation assistance (ACHELP@microsoft.com). For developers working on modern websites or applications, we understand that it has been increasingly difficult to support Internet Explorer side-by-side with modern browsers. While this announcement will start the transition of moving users from Internet Explorer to the more modern Microsoft Edge browser, it will take time and we recommend that you develop a plan to end support for Internet Explorer. Read this Moving users to Microsoft Edge from Internet Explorer article to learn how we can help. What does this announcement mean for end users? Microsoft Edge offers a faster, more secure, and modern browsing experience than Internet Explorer, and a growing number of websites no longer support Internet Explorer. After the Internet Explorer desktop application is retired on June 15, 2022, it will be out of support. After this date, the IE11 desktop application will be disabled and will redirect to Microsoft Edge if a user tries to access it. If a user encounters a broken website that requires IE11, they should open it in IE mode. They can open websites that require Internet Explorer without leaving Microsoft Edge. Learn more about Internet Explorer mode in Microsoft Edge. What is the MSHTML (Trident) engine? How does that relate to IE mode? The MSHTML (Trident) engine is the underlying platform for Internet Explorer 11. This is the same engine used by IE mode and it will continue to be supported (in other words, unaffected by this announcement). WebOC will also continue to be supported. If you have a custom or third-party app that relies on the MSHTML platform, you can expect it to continue to work. For future app development, we recommend using WebView2. How long will IE mode be supported? IE mode support follows the lifecycle of Windows client, Server, and IoT releases at least through 2029. Additionally, Microsoft will give one year of notice before retiring the IE mode experience when the time comes. Windows support dates are documented on the Product Lifecycle page. Some editions of Windows may require an ESU license, if available, to receive operating system security updates beyond end of support dates. End of service dates for currently supported versions of Windows are as follows: Platform Windows release End of service Windows client Windows 10 Enterprise, version 20H2 5/9/2023 Windows 10 Enterprise, version 2004 12/14/2021 Windows 10 2019 LTSC 1/9/2029 Windows 8.1 1/10/2023 Windows 7 (ESU required) 1/10/2023 Windows Server Windows Server, version 20H2 (SAC) 5/10/2022 Windows Server, version 2004 (SAC) 12/14/2021 Windows Server 2019 (LTSC) 1/9/2029 Windows IoT Windows 10 IoT Enterprise, version 20H2 5/9/2023 Windows 10 IoT Enterprise, version 2004 12/14/2021 Windows 10 IoT 2019 LTSC 1/9/2029 Windows Server IoT 2019 1/9/2029 If I reach out to Microsoft for an exception to this timeline, can I continue to use the Internet Explorer 11 desktop application after June 15, 2022? Microsoft Edge provides a dual engine advantage of Internet Explorer mode for compatibility with legacy websites and the Chromium project–the technology that powers many of today’s browsers–for world-class compatibility and performance with modern websites. As such, we’re not allowing exceptions or providing extended support to continue using the IE11 desktop application on the in-scope platforms after June 15, 2022. For those using IE11 at home, you can run IE mode in Microsoft Edge by following the steps outlined on this support page: Internet Explorer mode in Microsoft Edge. Commercial IT pros will need to set up IE mode in Microsoft Edge to enable access to legacy IE-based sites and apps for their commercial users. To set up IE mode, use the resources in the Getting Started guide. Supporting IE mode through at least 2029 is not long enough. Can I get an extension? IE mode will continue to be supported through at least 2029 and Microsoft will give one year notice before deprecating the IE mode experience in-market when the time comes. What IE functionality is available in IE mode? IE mode supports all document and enterprise modes, Active X controls (such as Java or Silverlight), and more. For a list of what is supported and what is not supported, see the What is Internet Explorer (IE) mode Docs page. Are there any changes to the Microsoft Edge lifecycle? There are no changes to the Microsoft Edge lifecycle. Microsoft Edge continues to be supported. For more details, please visit the Microsoft Edge Lifecycle page. How do I set up Internet Explorer mode in my organization? You can get detailed guidance on how to set up Internet Explorer mode through our Getting Started guide or by visiting our IE mode documentation. Will the Internet Explorer 11 desktop application be removed from devices? No. The IE11 desktop application will not be removed from devices, as the IE11 engine is required for IE mode to function. However, after the IE11 desktop application is retired on June 15, 2022, it will be disabled permanently. Will iexplore.exe be removed from devices? No, but if a user tries to access it, they will be unable to open IE11 and will be redirected to Microsoft Edge. If my browser default isn't Internet Explorer 11, will the retirement affect my browser default? No, this retirement will only change your browser default if your default had been set to Internet Explorer 11. If IE11 is set as your browser default, you will now have Microsoft Edge. Will Internet Explorer-based sites and apps open automatically in Microsoft Edge after the Internet Explorer 11 desktop application is retired on June 15, 2022? After the IE11 desktop application is retired, IE11 will redirect to Microsoft Edge. To open Internet Explorer-based websites and apps, you will need to either set up Internet Explorer mode (as an organization) or enable Internet Explorer mode (as a consumer at home). If you’re an organization, you can set up IE mode using the Getting Started guide. If you are an end user, you can enable IE mode by following the steps in this Internet Explorer mode in Microsoft Edge support article. What if some of my sites don’t work in Microsoft Edge using Internet Explorer mode? How do I get help for website compatibility issues? If you’re an organization and experience compatibility issues such as an error loading a site, please connect with the App Assure team for remediation assistance. You can submit a request for assistance through their website or reach out via email (ACHELP@microsoft.com). If you’re a consumer at home and encounter an error loading a page, try loading it in IE mode by following the instructions in this Internet Explorer mode in Microsoft Edge support article. If the issue persists, please notify us by sending feedback through the in-product feedback tool found in the three-dot settings menu under ‘Help and feedback’ or by using the shortcut Alt + Shift + I. When submitting feedback, please check the box to ‘Send diagnostic data’. Will the IE Group Policies work in IE mode? We are committed to have IE Group Policies work in IE mode. If for any reason you encounter an issue, please connect with us at AppAssure for assistance. You can submit a request for assistance through their website or reach out via email (ACHELP@microsoft.com). Continue the conversation. Find best practices. Visit the Windows Tech Community. Stay informed. For the latest updates on new releases, tools, and resources, stay tuned to this blog and follow us @MSWindowsITPro on Twitter. Continue reading...
-

A New Windows 10 Update Is Causing Blue Screen Crashes
AWS replied to starbuck's topic in Tech Help and Discussions
Been a while since this has happened. Last time I remember was back with Windows 7 which was also a printer issue. -
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. It’s no secret that the security industry generally likes Microsoft Defender for Endpoint. After a few months of using and integrating it with our platform here at Expel, we feel the same. On Expel’s EXE Blog, we regularly share our thought process on how we think about security operations at scale at Expel and the decision support (or additional context) we provide our analysts through automation. In short, Defender for Endpoint makes it easy for us to achieve our standard of investigative quality and response time, but it doesn’t require a heavy lift from our analysts. And that’s good news both for our customers and for us. So, what is Microsoft Defender for Endpoint? Defender for Endpoint is an enterprise endpoint security product that supports Mac, Linux, and Windows operating systems, along with Android and iOS. There are lots of cool things that Defender for Endpoint does at an administrative level (such as attack surface reduction and configurable remediation). However, from our vantage point, we know it best for its detection and response capabilities. Defender for Endpoint is unique because not only does it combine an Endpoint Detection and Response (EDR) and AV detection engine into the same product, but for Windows 10 hosts, this functionality is built into the operating system, removing the need to install an endpoint agent. With an appropriate Microsoft license, Defender for Endpoint and Windows 10 provide out-of-the-box protection without the need to mass-deploy software or provision sensors across your fleet. How EDR tools help us as an XDR vendor When we integrate with an EDR product like Defender for Endpoint in support of our customers, our goal is to predict the investigative questions that an analyst will ask and then automate the action of getting the necessary data from that tool. This frees up our analysts to make the decision—versus making them spend time extracting the right data. We think Defender for Endpoint provides the right toolset that helps us reach that goal—and removes some burden from our analysts—thanks to its APIs. Thanks to Defender for Endpoint’s robust APIs, we augmented its capability to provide upfront decision support to our analysts. As a result, we’re able to arm them with the answers to the basic investigative questions we ask ourselves with every alert. To find these answers, there are a few specific capabilities of Defender for Endpoint we use that allow us to pull this information into each alert: Advanced hunting database. Prevalence information. Detailed process logging. AV actions. This way, our analysts don’t need to worry about fiddling with the tool but instead focus on analyzing the rich data it provides. Check out a real-life example of how Expel analysts use Defender for Endpoint to triage an alert on behalf of a customer. Defender for Endpoint helps reduce our alert-to-fix time The decision support—or additional context about an alert—that Defender for Endpoint enables us to generate is powerful because it allows us to become specialists at analysis rather than specialists of a specific technology. Defender for Endpoint provides a platform that allows our analysts to quickly and accurately answer important questions during an investigation. Most importantly, though, having these capabilities emulated in the API allowed us to build on top of the Defender for Endpoint platform to be more efficient in providing high-quality detection and response. And that’s a win-win for both Expel and our customers. Learn more To learn more about Expel, visit our listing on the Azure Marketplace. To learn more about the Microsoft Intelligent Security Association (MISA), visit our website, where you can learn about the MISA program, product integrations and find MISA members. Visit the to learn about the strength of member integrations with Microsoft products. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. The post What we like about Microsoft Defender for Endpoint appeared first on Microsoft Security. Continue reading...
-
Microsoft’s response to Solorigate Since December, the United States, its government, and other critical institutions including security firms have been addressing the world’s latest serious nation-state cyberattack, sometimes referred to as ‘Solorigate’ or ‘SUNBURST.’ As we shared earlier this is a moment of reckoning for our industry and needs a unified response of defenders across public and private sectors. Microsoft is committed to protecting our customers and safeguarding our communities and we are proud to partner with industry partners to respond to this attack and strengthen our collective defenses. We believe transparency and clarity are important for strong cybersecurity and in that spirit, we are sharing information about some commonly asked questions. We look forward to serving and protecting our customers and communities. Question: What has Microsoft’s role been in the Solorigate incident? Answer: As Brad Smith wrote on December 17, 2020, Solorigate is a moment of reckoning for security. We believe the Solorigate incident is an opportunity for the industry to work together to share information, strengthen defenses, and respond to attacks. We are proud to be part of the collaborative work being done to empower the defender community. Over the past two months, there have been several disclosures related to the Solorigate actor and Microsoft has had a unique perspective from several angles: Helping investigate with FireEye. Using indicators to find unusual activity and notifying customers and partners. Helping with customer investigations. Investigating our own environment. In all of our investigations to date, data hosted in Microsoft services (including email) was sometimes a target in the incidents, but the attacker had gained privileged credentials in some other way. Find the latest findings and guidance on Solorigate here. Question: With your broad engagement, you’ve been criticized for not disclosing details as soon as you knew about them. How do you respond? Answer: We believe the Solorigate incident is an opportunity for the industry to work together to share information, strengthen defenses, and respond to attacks. We have a very talented and experienced cybersecurity response team. In those situations where we provide investigative support to other organizations, we are restricted from sharing details. In these engagements, as well as when we notify organizations, those organizations have control in deciding what details they disclose and when they disclose them. Additionally, investigations sometimes discover early indicators that require further research before they are actionable. Taking the time to thoroughly investigate incidents is necessary in order to provide the best guidance to the broader security community, our customers, and our partners. We share actionable information regularly on our Solorigate resource center, and we are committed to providing additional updates if and when we discover new information to help inform and enable the community. Question: The Cybersecurity & Infrastructure Security Agency (CISA) says other attack vectors have been discovered apart from SolarWinds. Has Microsoft in any way been an initial entry point for the Solorigate actor? Answer: No. In our investigations to date, data hosted in Microsoft services (including email) was sometimes a target in the incidents, but the attacker had gained privileged credentials in some other way. From the beginning, we have said that we believe this is a sophisticated actor that has many tools in its toolkit, so it is not a surprise that a sophisticated actor would also use other methods to gain access to targets. In our investigations and through collaboration with our industry peers, we have confirmed several additional compromise techniques leveraged by the actor, including password spraying, spearphishing, use of webshell, through a web server, and delegated credentials. As we learn more from our engagements, we will continue to improve our security products and share learnings with the community. For the most up-to-date information and guidance, please visit our resource center. Question: What should we know about the Microsoft notifications to customers? Does that mean you detected a compromise in Microsoft services? Answer: No, it means our telemetry indicated unusual activity in authorized accounts. As part of the investigative team working with FireEye, we were able to analyze the attacker’s behavior with a forensic investigation and identify unusual technical indicators that would not be associated with normal user interactions. We then used our telemetry to search for those indicators and identify organizations where credentials had likely been compromised by the Solorigate actor. Microsoft directly notifies the affected customers to provide the indicators they need to investigate the observed behavior with their organizational knowledge and within their specific context. Question: Some have interpreted the wording in the SolarWinds 8K to mean that they were made aware of or were investigating an attack vector related to Microsoft Office 365. Has that been investigated? The 8K wording is, “SolarWinds uses Microsoft Office 365 for its email and office productivity tools. SolarWinds was made aware of an attack vector that was used to compromise the Company’s emails and may have provided access to other data contained in the Company’s office productivity tools.” Answer: We have investigated thoroughly and have found no evidence they were attacked via Office 365. The wording of the SolarWinds 8K filing was unfortunately ambiguous, leading to erroneous interpretation and speculation, which is not supported by the results of our investigation. SolarWinds has confirmed these findings in their blog on February 3, 2021. Question: Reuters broke news on December 17, 2020, alleging that “Microsoft’s own products were then used to further the attacks” and saying it was not immediately clear “how many Microsoft users were affected by the tainted products.” Is that article accurate? Answer: No, it is not accurate. As we said at the time, and based upon all investigations since, we have found no indications that our systems were used to attack others. Data hosted in Microsoft services (including email) were sometimes a post-compromise target of attack, but only after an attacker had gained privileged credentials in some other way. Question: Some companies say the hackers entered its systems via Microsoft products. Do you dispute this? Answer: We’ve investigated each situation as we became aware of it and in each case, data hosted in Microsoft services (including email) were a target in the incident, but the attacker had gained privileged credentials in another way. Question: When did Microsoft know about being attacked by the Solorigate actor? Answer: Our security teams work continually to protect users, devices, and data from ongoing threats to our environment, but the investigations specifically focused on the Solorigate actor began when we became aware of the malicious SolarWinds applications. We published a Microsoft Internal Solorigate Investigation Update on December 31, 2020, and will provide another update soon. Question: Given how serious Solorigate is, what can be done? What is the big takeaway? Answer: The cybersecurity industry has long been aware that sophisticated and well-funded actors were theoretically capable of advanced techniques, patience, and operating below the radar, but this incident has proven that it isn’t just theoretical. We believe the Solorigate incident has proven the benefit of the industry working together to share information, strengthen defenses, and respond to attacks. Additionally, the attacks have reinforced two key points that the industry has been advocating for a while now—defense-in-depth protections and embracing a zero trust mindset. Defense-in-depth protections and best practices are really important because each layer of defense provides an extra opportunity to detect an attack and take action before they get closer to valuable assets. We saw this ourselves in our internal investigation, where we found evidence of attempted activities that were thwarted by defense-in-depth protections. So, we again want to reiterate the value of industry best practices such as outlined here, and implementing Privileged Access Workstations (PAW) as part of a strategy to protect privileged accounts. A zero trust, “assume breach” philosophy is an important approach to defense. Many of the techniques we’ve observed are post-compromise techniques, so security companies and Microsoft are looking for ways to improve detections and provide protection even when an attacker gains unauthorized access. The post Sophisticated cybersecurity threats demand collaborative, global response appeared first on Microsoft Security. Continue reading...
-
GDPR, HIPPA, GLBA, all 50 U.S. States, and many countries have privacy breach reporting requirements. If an organization experiences a breach of customer or employee personal information, they must report it within the required time frame. The size and scope of this reporting effort can be massive. Using Microsoft 365 Advanced Audit and Advanced eDiscovery to better understand the scope of the breach can minimize the burden on customers as well as the financial and reputational cost to the organization. A changing privacy landscape In 2005 ChoicePoint, a Georgia-based financial data aggregator had a data breach of 145,000 of its customers. There were multiple security lapses and resulting penalties, but initially, only ChoicePoint’s California-based customers were required to be notified because, at the time, California, with California Senate Bill 1386, was the only state that had a mandatory privacy breach notification law. Since that time, all 50 U.S. States have put in place mandatory privacy breach notification laws. Countries in the Americas, the Middle East, Europe, and Asia have adopted privacy standards including mandatory breach notification. Broader regulations that address this issue include California Consumer Privacy Act, China’s Personal Information Security Specification, Brazil’s Lei Geral de Proteção de Dados Pessoais (LGPD), and the European General Data Protection Regulation (GDPR). Given how often these laws are added or updated, it’s challenging for any organization to keep up. As one solution, Microsoft 365 Compliance Manager provides a set of continually updated assessments (174 and growing) to assist our customers with these standards. A board-level business risk The reputational and financial risk to a company from a privacy breach can be massive. For example, under California Civil Code 1798.80, which deals with the breach of personal health information, there is a penalty of up to $25,000 per patient record breached. For many standards, there are not only regulatory penalties imposed, but also the right of private action by those whose records have been breached (such as, those who have had their records breached can sue for damages, creating financial liability for a company beyond the regulatory penalties). There are timeframes under which notification must be made. The California Code requires notification to the regulator within 15 days after unauthorized disclosure is detected. Article 33 of GDPR requires notification to the regulator within 72 hours after the organization becomes aware of the breach. According to a list compiled by the Infosec Institute, the average cost of a data breach in 2019 was $3.9 million but can range as high as $2 billion in cases like the Equifax breach of 2017. The reputational damage associated with a breach of customer, employee, or other stakeholders’ personal or business information can substantially reduce a company’s value. The scope of notification (if any is needed at all) and remediation depends on understanding the scope of the breach in a timely fashion. In the absence of reliable information, companies need to make worst-case assumptions that may result in larger notifications, higher costs, and unnecessary hardship for customers and other stakeholders. Preparation for breach As security and compliance professionals, our priority is to avoid breaches with a defense in depth strategy including Zero Trust architecture. Microsoft has comprehensive security solutions for Microsoft 365, as well as compliance and risk management solutions that enable our compliance pillar framework: But we also must prepare for breaches even as we defend against them. Part of that preparation is putting our organization in a position to scope a breach and limit its impact. This means ensuring we have the data governance and signal in place before the breach happens. Security professionals know that they have to deploy solutions like Data Loss Prevention, firewalls, and encryption to defend against attacks, but they may not focus as much on having the right audit data available and retained, and visualizations and playbooks in place beforehand to scope a future breach. Use Microsoft 365 Advanced Audit and Advanced eDiscovery to investigate compromised accounts The Microsoft 365 Advanced Audit solution makes a range of data available that is focused on what will be useful to respond to crucial events and forensic investigations. It retains this data for one year (rather than the standard 90-day retention), with an option to extend the retention to ten years. This keeps the audit logs available to long-running investigations and to respond to regulatory and legal obligations. These crucial events can help you investigate possible breaches and determine the scope of compromise. Advanced Audit provides the following crucial events: MailItemsAccessed: Triggered when mail data is accessed by mail protocols and mail clients. Send: Triggered when a user sends, replies to, or forwards an email message. SearchQueryInitiatedExchange: Triggered when a user searches for items in an Exchange mailbox. SearchQueryInitiatedSharePoint: Triggered when a user searches for items in SharePoint sites of the organization. There are built-in default alert policies that use the Advanced Audit data to provide situational awareness either through Microsoft 365’s own security and compliance portal, through Microsoft’s Azure Sentinel cloud-native SIEM, or through a customer’s third-party SIEM. A customer can create customized alerts to use the audit data as well. Let’s look at how a customer might use Advanced Audit to investigate a compromised account and scope the extent of a data breach: In an account takeover, an attacker uses a compromised user account to gain access and operate as a user. The attacker may or may not have intended to access the user’s email. If they intend to access the user’s email, they may or may not have had the chance to do so. This is especially true if the defense in-depth and situational awareness discussed above is in place. The attack may have been detected, password changed, account locked, and more. If the user’s email has confidential information of customers or other stakeholders, we need to know if this email was accessed. We need to separate legitimate access by the mailbox owner during the account takeover from access by the attacker. With Advanced Audit, we have this ability. Without it, a customer will have to assume all information in the user’s mailbox is now in the hands of the attacker and proceed with reporting and remediation on this basis. The MailItemsAccessed audit data item will indicate if a mailbox item has been accessed by a mail protocol. It covers mail accessed by both sync and bind. In the case of sync access, the mail was accessed by a desktop version of the Outlook client for Windows or Mac. In bind access, the InternetMessageId of the individual message will be recorded in the audit record. We have the ability to forensically analyze mail access via a desktop client or via Outlook Web Access. We also need to differentiate between the mailbox owner’s legitimate access to a mail item during the attack time period and access by the attacker. We can do this by examining the audit records to see the context of the access, including the session ID and IP address used for access. We match these with other audit records and known good access by the user. Advanced Audit retains other events like Teams Joins, File Accessed, Messages Sent, Searches Queries, and many others that can support a breach analysis. When we’ve properly scoped the data that the attacker has had access to, we want to deep dive and inspect the content. With Advanced eDiscovery we can collect all emails, documents, Microsoft Teams, and Yammer interactions of the account that was taken over. We can search for confidential information and metadata to identify the material in question: There is metadata for each item which, for emails, includes InternetMessageID as well as many other items such as from, to, and when it was sent, and any Microsoft Information Protection sensitivity label. Advanced Audit and Advanced eDiscovery are an important part of an effective security risk and compliance strategy. These Microsoft 365 native tools allow our customers to understand the true scope of a breach. It has the potential to substantially reduce or eliminate the reporting requirements stemming from a compromised account. Advanced Audit can reduce the financial and reputational damage to a company, its customers, employees, partners, and other stakeholders. To learn more about Microsoft Security solutions visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. This document is provided “as-is.” Information and views expressed in this document, including URL and other Internet Web site references, may change without notice. You bear the risk of using it. This document is not intended to communicate legal advice or a legal or regulatory compliance opinion. Each customer’s situation is unique, and legal and regulatory compliance should be assessed in consultation with their legal counsel. The post Privacy breaches: Using Microsoft 365 Advanced Audit and Advanced eDiscovery to minimize impact appeared first on Microsoft Security. Continue reading...
-
Microsoft security researchers continue to investigate and respond to the sophisticated cyberattack known as Solorigate (also referred to as Sunburst by FireEye) involving a supply chain compromise and the subsequent compromise of cloud assets. While the related investigations and impact assessments are ongoing, Microsoft is providing visibility into the attack chains and related threat intelligence to the defender community as early as possible so organizations can identify and take action to stop this attack, understand the potential scope of its impact, and begin the recovery process from this active threat. We have established a resource center that is constantly updated as more information becomes available at Solorigate Resource Center – updated December 28th, 2020 – Microsoft Security Response Center. This blog is a comprehensive guide for security operations and incident response teams using Microsoft 365 Defender to identify, investigate, and respond to the Solorigate attack if it’s found in your environment. The description of the attack in this blog is based on current analysis and investigations by researchers across Microsoft, our partners, and the intelligence community who are actively collaborating to respond to the attack. This is an active threat that continues to evolve, and the findings included here represent what we know at the time of publishing. We continue to publish and update intelligence, indicators, tactics, techniques, and procedures (TTPs), and related details as we discover them. The report from the Microsoft Security Response Center (MSRC) includes the latest analysis of this threat, known indicators of compromise (IOCs), and initial recommended defenses, and will be updated as new data becomes available. This blog covers: The Solorigate attack chain Reviewing affected devices and related incidents with Threat analytics Detecting and blocking malicious activity on endpoint (Microsoft Defender for Endpoint, Microsoft 365 Defender hunting) Detecting hands-on-keyboard activity within on-prem environment (Microsoft Defender for Endpoint, Microsoft Defender for Identity, Microsoft 365 Defender hunting) Detecting hands-on-keyboard activity in the cloud environment (Microsoft Cloud App Security, Microsoft 365 Defender hunting) Summary of detections and hunting queries across Microsoft 365 Defender Tracking the cross-domain Solorigate attack from endpoint to the cloud The Solorigate attack is an example of a modern cross-domain compromise. Since these kinds of attacks span multiple domains, having visibility into the entire scope of the attack is key to stopping and preventing its spread. This attack features a sophisticated technique involving a software supply chain compromise that allowed attackers to introduce malicious code into signed binaries on the SolarWinds Orion Platform, a popular IT management software. The compromised application grants attackers “free” and easy deployment across a wide range of organizations who use and regularly update the application, with little risk of detection because the signed application and binaries are common and are considered trusted. With this initial widespread foothold, the attackers can then pick and choose the specific organizations they want to continue operating within (while others remain an option at any point as long as the backdoor is installed and undetected). Based on our investigations, the next stages of the attack involve on-premises activity with the goal of off-premises access to cloud resources through the following steps: Using the compromised SolarWinds DLL to activate a backdoor that enables attackers to remotely control and operate on a device Using the backdoor access to steal credentials, escalate privileges, and move laterally to gain the ability to create valid SAML tokens using any of two methods: Stealing the SAML signing certificate (Path 1) Adding to or modifying existing federation trust (Path 2) [*]Using attacker-created SAML tokens to access cloud resources and perform actions leading to the exfiltration of emails and persistence in the cloud Figure 1. High-level end-to-end Solorigate attack chain This attack is an advanced and stealthy campaign with the ability to blend in, which could allow attackers to stay under the radar for long periods of time before being detected. The deeply integrated cross-domain security capabilities in Microsoft 365 Defender can empower organizations and their security operations (SOC) teams to uncover this attack, scope out the end-to-end breach from endpoint to the cloud, and take action to block and remediate it. This blog will offer step-by-step guidance to do this by outlining: How indicators of attack show up across endpoints, identity, and the cloud How Microsoft 365 Defender automatically combines alerts across these different domains into a comprehensive end-to-end story How to leverage the powerful toolset available for deep investigation, hunting, and response to enable SOCs to battle the attackers and evict these attackers from both on-premises and cloud environments Threat analytics: Understanding and responding to active attacks As soon as this attack was discovered, Microsoft researchers published two threat analytics reports to help organizations determine if they are affected, assess the impact of the attack, and identify actions to contain it. Sophisticated actor attacks FireEye provides information about the FireEye breach and compromised red team tools Solorigate supply chain attack provides a detailed analysis of the SolarWinds supply chain compromise The reports are published in Microsoft 365 security center, available to all Microsoft Defender for Endpoint customers and Microsoft 365 Defender early adopters. In addition to detailed descriptions of the attack, TTPs, and indicators of compromise (IoCs), the reports provide real-time data aggregated from signals across Microsoft 365 Defender, indicating the all-up impact of the threat to the organization, as well as details about relevant incidents and alerts to initiate investigation on. These reports continue to be updated as additional information becomes available. Given the significance of this threat, we are making similar relevant Microsoft threat intelligence data, including the updated list of IOCs, available to everyone publicly. A comprehensive list of guidance and insights is available at Solorigate Resource Center – updated December 28th, 2020 – Microsoft Security Response Center. Figure 2. Threat analytics report on Solorigate attack We recommend Microsoft 365 Defender customers to start their investigations here. After gaining deep understanding of the threat and getting the latest research findings, you can take the following recommended steps: Find devices with the compromised SolarWinds Orion application The threat analytics report uses insights from threat and vulnerability management to identify devices that have the compromised SolarWinds Orion Platform binaries or are exposed to the attack due to misconfiguration. From the Vulnerability patching status chart in threat analytics, you can view the mitigation details to see a list of devices with the vulnerability ID TVM-2020-0002, which was added specifically to help with Solorigate investigations: Figure 3. Threat and vulnerability management data shows data on exposed devices Threat and vulnerability management provides more info about the vulnerability ID TVM-2020-0002, as well as all relevant applications, via the Software inventory view. There are also multiple security recommendations to address this specific threat, including instructions to update the software versions installed on exposed devices. Figure 4. Security recommendations from threat and vulnerability management Investigate related alerts and incidents From the threat analytics report, you can quickly locate devices with alerts related to the attack. The Devices with alerts chart identifies devices with malicious components or activities known to be directly related to Solorigate. Click through to get the list of alerts and investigate. Some Solorigate activities may not be directly tied to this specific threat but will trigger alerts due to generally suspicious or malicious behaviors. All alerts in Microsoft 365 Defender provided by different Microsoft 365 products are correlated into incidents. Incidents help you see the relationship between detected activities, better understand the end-to-end picture of the attack, and investigate, contain, and remediate the threat in a consolidated manner. Review incidents in the Incidents queue and look for those with alerts relevant to this attacker’s TTPs, as described in the threat analytics report (also listed at the end of this blog). Figure 5. Consolidated Incident view for Solorigate Some alerts are specially tagged with Microsoft Threat Experts to indicate malicious activities that Microsoft researchers found in customer environments during hunting. As part of the Microsoft Threat Experts service, researchers investigated this attack as it unfolded, hunting for associated attacker behaviors, and sent targeted attack notifications. If you see an alert tagged with Microsoft Threat Experts, we strongly recommend that you give it immediate attention. Figure 6. Microsoft Threat Experts targeted attack notification Additionally, Microsoft Threat Experts customers with Experts on demand subscriptions can reach out directly to our on-demand hunters for additional help in understanding the Solorigate threat and the scope of its impact in their environments. Hunt for related attacker activity The threat analytics report also provides advanced hunting queries that can help analysts locate additional related or similar activities across endpoint, identity, and cloud. Advanced hunting uses a rich set of data sources, but in response to Solorigate, Microsoft has enabled streaming of Azure Active Directory (Azure AD) audit logs into advanced hunting, available for all customers in public preview. These logs provide traceability for all changes done by various features within Azure AD. Examples of audit logs include changes made to any resources within Azure AD, such as adding or removing users, apps, groups, roles, and policies. Customers who do not have Microsoft Defender for Endpoint or are not early adopters for Microsoft 365 Defender can see our recommended advanced hunting queries. Currently, this data is available to customers who have Microsoft Cloud App Security with the Office365 connector. Our intent is to expand availability to more Microsoft 365 Defender customers. The new log data is available in the CloudAppEvents table: CloudAppEvents | where Application == “Office 365” The log data contains activity logs useful for investigating and finding Azure AD-related activities. This data further enriches the CloudAppEvents table, which also has Exchange Online and Microsoft Teams activities. As part of making this new data available, we also published a handful of relevant advanced hunting queries, identified by the suffix [solorigate], to the GitHub repo. Here’s an example query that helps you see when credentials are added to an Azure AD application after ‘Admin Consent’ permissions were granted: CloudAppEvents | where Application == “Office 365” | where ActionType == “Consent to application.” | where RawEventData.ModifiedProperties[0].Name == “ConsentContext.IsAdminConsent” and RawEventData.ModifiedProperties[0].NewValue == “True” | extend spnID = tostring(RawEventData.Target[3].ID) | parse RawEventData.ModifiedProperties[4].NewValue with * “=> [[” dummpy “Scope: ” After “]]” * | extend PermissionsGranted = split(After, “]”,0) | project ConsentTime = Timestamp , AccountDisplayName , spnID , PermissionsGranted | join ( CloudAppEvents | where Application == “Office 365” | where ActionType == “Add service principal credentials.” or ActionType == “Update application – Certificates and secrets management “ | extend spnID = tostring(RawEventData.Target[3].ID) | project AddSecretTime = Timestamp, AccountDisplayName , spnID ) on spnID | where ConsentTime AccountDisplayName1 Microsoft 356 Defender advanced hunting can also assist in many of the recommended incident investigation tasks outlined in the blog, Advice for incident responders on recovery from systemic identity compromises. In the remaining sections, we will discuss select examples of alerts raised by Microsoft 365 solutions that monitor and detect Solorigate activities across the attack chain on endpoint, identity, and the cloud. These are alerts you may encounter when investigating incidents in Microsoft 365 security center if your organization is affected by this threat. We will also indicate activities which are now blocked by Microsoft 365 Defender. Lastly, each section contains examples of hunting queries you will find useful for hunting for various attacker activities in your environment. Detecting and blocking malware and malicious behavior on endpoints Figure 7. Solorigate attack chain: Initial access and command-and-control Discovering and blocking backdoor activity When the compromised SolarWinds binary SolarWinds.Orion.Core.BusinessLayer.dll gets loaded on a device through normal update channels, the backdoor goes through an extensive list of checks to ensure it’s running in an actual enterprise network and not on an analyst’s machine. It then contacts a command-and-control (C2) server using a subdomain that is generated partly with information gathered from the affected device, which means a unique subdomain is generated for each affected domain. The backdoor allows the attackers to remotely run commands on the device and move to the next stages of the attack. For more information, read our in-depth analysis of the Solorigate malware. Microsoft Defender for Endpoint delivers comprehensive protection against this threat (see full list of detection and protection alerts at the end of this blog). Microsoft Defender Antivirus, the default antimalware solution on Windows 10, detects and blocks the malicious DLL and its behaviors. It quarantines the malware, even if the process is running. Figure 8. Microsoft Defender for Endpoint blocks malicious binaries If the malicious code is successfully deployed, the backdoor lies dormant for up to two weeks. It then attempts to contact numerous C2 domains, with the primary domain being *.avsvmcloud[.]com. The backdoor uses a domain generation algorithm to evade detection. Microsoft 365 Defender detects and blocks this behavior. Figure 9. Microsoft Defender for Endpoint prevented malicious C2 callback Discovering potentially tampered devices To evade security software and analyst tools, the Solorigate malware enumerates the target system looking for certain running processes, loaded drivers, and registry keys, with the goal of disabling them. The Microsoft Defender for Endpoint sensor is one of the processes the malware attempts to disable. Microsoft Defender for Endpoint has built-in protections against many techniques attackers use to disable endpoint sensors ranging from hardened OS protection, anti-tampering policies, and detections for a variety of tampering attempts, including “Attempt to stop Microsoft Defender for Endpoint sensor”, “Tampering with Microsoft Defender for Endpoint sensor settings”, or “Possible sensor tampering in memory”. Successfully disabling Microsoft Defender for Endpoint can prevent the system from reporting observed activities. However, the multitude of signals reported into Microsoft 365 Defender provides a unique opportunity to hunt for systems where the tampering technique used might have been successful. The following advanced hunting query can be used to locate devices that should be reporting but aren’t: // Times to be modified as appropriate let timeAgo=1d; let silenceTime=8h; // Get all silent devices and IPs from network events let allNetwork=materialize(DeviceNetworkEvents | where Timestamp > ago(timeAgo) and isnotempty(LocalIP) and isnotempty(RemoteIP) and ActionType in (“ConnectionSuccess”, “InboundConnectionAccepted”) and LocalIP !in (“127.0.0.1”, “::1”) | project DeviceId, Timestamp, LocalIP, RemoteIP, ReportId); let nonSilentDevices=allNetwork | where Timestamp > ago(silenceTime) | union (DeviceProcessEvents | where Timestamp > ago(silenceTime)) | summarize by DeviceId; let nonSilentIPs=allNetwork | where Timestamp > ago(silenceTime) | summarize by LocalIP; let silentDevices=allNetwork | where DeviceId !in (nonSilentDevices) and LocalIP !in (nonSilentIPs) | project DeviceId, LocalIP, Timestamp, ReportId; // Get all remote IPs that were recently active let addressesDuringSilence=allNetwork | where Timestamp > ago(silenceTime) | summarize by RemoteIP; // Potentially disconnected devices were connected but are silent silentDevices | where LocalIP in (addressesDuringSilence) | summarize ReportId=arg_max(Timestamp, ReportId), Timestamp=max(Timestamp), LocalIP=arg_max(Timestamp, LocalIP) by DeviceId | project DeviceId, ReportId=ReportId1, Timestamp, LocalIP=LocalIP1 Microsoft is continuously developing additional measures to both block and alert on these types of tampering activities. Detecting hands-on-keyboard activity within an on-premises environment Figure 10. Solorigate attack chain: Hands-on-keyboard attack on premises After establishing a backdoor connection on an affected device, the attacker’s next goal is to achieve off-premises access to the organization’s cloud services. To do this, they must find a way to gain permissions to those services. One technique we have seen the attackers use is to go after the organization’s Active Directory Federation Services (AD FS) server to obtain the proverbial “keys” to the identity kingdom. AD FS enables federated identity and access management by securely sharing digital identity and entitlement rights across security and enterprise boundaries; effectively, it is the “LSASS for the cloud.” Among other things, AD FS stores the Security Assertion Markup Language (SAML) token signing certificate, which is used to create authorization tokens for users or services in the organization so they can access cloud applications and resources after authentication. To attack the AD FS infrastructure, the attackers must first obtain appropriate domain permissions through on-premises intelligence gathering, lateral movement, and credential theft. Building from the backdoor described above, the attackers leverage fileless techniques for privilege escalation, persistence, and lateral movement, including evading analysis by using system binaries and exploration tools that masquerade as other benign binaries. The attackers also carefully chose organization-specific command-and-control (C2) domains and use custom organization-specific tool naming and locations. Microsoft Defender for Endpoint detects a wide array of these attack techniques, allowing SOC teams to track the attacker’s actions in the environment and take actions to contain the attack. The following section covers detections for the techniques used by the attackers to compromise the AD FS infrastructure. Identifying attacker reconnaissance Attackers collect data from Active Directory using a renamed version of the utility ADFind, running queries against Domain Controllers as part of the reconnaissance stage of the attack. Microsoft Defender for Endpoint detects this behavior and allows the SOC analyst to track compromised devices at this stage to gain visibility into the information the attacker is looking for. Figure 11. Microsoft Defender for Endpoint detects usage of masquerading exploration tools Figure 12. Microsoft Defender for Endpoint detects usage LDAP query for reconnaissance. Stopping lateral movement and credential theft To gain access to a highly privileged account needed for later steps in the kill chain, the attackers move laterally between devices and dump credentials until an account with the needed privileges is compromised, all while remaining as stealthy as possible. A variety of credential theft methods, such as dumping LSASS memory, are detected and blocked by Microsoft Defender for Endpoint. The example below shows the detection of lateral movement using Windows Management Instrumentation (WMI) to run the attacker’s payload using the Rundll32.exe process. Figure 13. Microsoft Defender for Endpoint alert for suspicious remote WMI execution highlighting the attacker’s device and payload Microsoft Defender for Identity also detects and raises alerts on a variety of credential theft techniques. In addition to watching for alerts, security analysts can hunt across identity data in Microsoft 365 Defender for signs of identity compromise. Here are a couple of example Microsoft Defender for Identity queries looking for such patterns: Enumeration of high-value DC assets followed by logon attempts to validate stolen credentials in time proximity let MaxTime = 1d; let MinNumberLogon = 5; //devices attempting enumeration of high-value DC IdentityQueryEvents | where Timestamp > ago(30d) | where Application == “Active Directory” | where QueryTarget in (“Read-only Domain Controllers”) //high-value RODC assets | project Timestamp, Protocol, Query, DeviceName, AccountUpn | join kind = innerunique ( //devices trying to logon {MaxTime} after enumeration IdentityLogonEvents | where Timestamp > ago(30d) | where ActionType == “LogonSuccess” | project LogonTime = Timestamp, DeviceName, DestinationDeviceName) on DeviceName | where LogonTime between (Timestamp .. (Timestamp + MaxTime)) | summarize n=dcount(DestinationDeviceName), TargetedDC = makeset(DestinationDeviceName) by Timestamp, Protocol, DeviceName | where n >= MinNumberLogon High-volume of LDAP queries in short time filtering for non-DC devices let Threshold = 12; let BinTime = 1m; //approximate list of DC let listDC=IdentityDirectoryEvents | where Application == “Active Directory” | where ActionType == “Directory Services replication” | summarize by DestinationDeviceName; IdentityQueryEvents | where Timestamp > ago(30d) //filter out LDAP traffic across DC | where DeviceName !in (listDC) | where ActionType == “LDAP query” | parse Query with * “Search Scope: ” SearchScope “, Base Object:” BaseObject “, Search Filter: ” SearchFilter | summarize NumberOfDistinctLdapQueries = dcount(SearchFilter) by DeviceName, bin(Timestamp, BinTime) | where NumberOfDistinctLdapQueries > Threshold At this point, SOC teams can take containment measures within the Microsoft 365 security center, for example, using indicators to isolate the devices involved and block the remotely executed payload across the environment, as well as mark suspect users as compromised. Detecting and remediating persistence Microsoft Defender for Endpoint also detects the advanced defense evasion and masquerading techniques used by the attackers to make their actions as close to normal as possible, such as binding a WMI event filter with a logical consumer to remain persistent. Follow the recommended actions in the alert to remove persistence and prevent the attacker’s payload from loading after reboot. Figure 14. Microsoft Defender for Endpoint alert for WMI event filter bound to a suspicious consumer showing the persistence and the scheduled command line Catching AD FS compromise and the attacker’s ability to impersonate users in the cloud The next step in the attack focuses on the AD FS infrastructure and can unfold in two separate paths that lead to the same outcome—the ability to create valid SAML tokens allowing impersonation of users in the cloud: Path 1 – Stealing the SAML signing certificate: After gaining administrative privileges in the organization’s on-premises network, and with access to the AD FS server itself, the attackers access and extract the SAML signing certificate. With this signing certificate, the attackers create valid SAML tokens to access various desired cloud resources as the identity of their choosing. Path 2 – Adding to or modifying existing federation trust: After gaining administrative Azure Active Directory (Azure AD) privileges using compromised credentials, the attackers add their own certificate as a trusted entity in the domain either by adding a new federation trust to an existing tenant or modifying the properties of an existing federation trust. As a result, any SAML token they create and sign will be valid for the identity of their choosing. In the first path, obtaining the SAML signing certificate normally entails first querying the private encryption key that resides on the AD FS container and then using that key to decrypt the signing certificate. The certificate can then be used to create illicit but valid SAML tokens that allow the actor to impersonate users, enabling them to access enterprise cloud applications and services. Microsoft Defender for Endpoint and Microsoft Defender for Identity detect the actions that attackers take to steal the encryption key needed to decrypt the SAML signing certificate. Both solutions leverage unique LDAP telemetry to raise high-severity alerts highlighting the attacker’s progress towards creating illicit SAML tokens. Figure 15. Microsoft Defender for Endpoint detects a suspicious LDAP query being launched and an attempted AD FS private key extraction Figure 16. Microsoft Defender for Identity detects private key extraction via malicious LDAP requests For the second path, the attackers create their own SAML signing certificate outside of the organization’s environment. With Azure AD administrative permissions, they then add the new certificate as a trusted object. The following advanced hunting query over Azure AD audit logs shows when domain federation settings are changed, helping to discover where the attackers configured the domain to accept authorization tokens signed by their own signing certificate. As these are rare actions, we advise verifying that any instances identified are the result of legitimate administrative activity. ADFSDomainTrustMods let auditLookback = 1d; CloudAppEvents | where Timestamp > ago(auditLookback) | where ActionType =~ “Set federation settings on domain.” | extend targetDetails = parse_json(ActivityObjects[1]) | extend targetDisplayName = targetDetails.Name | extend resultStatus = extractjson(“$.ResultStatus”, tostring(RawEventData), typeof(string)) | project Timestamp, ActionType, InitiatingUserOrApp=AccountDisplayName, targetDisplayName, resultStatus, InitiatingIPAddress=IPAddress, UserAgent If the SAML signing certificate is confirmed to be compromised or the attacker has added a new one, follow the best practices for invalidating through certificate rotation to prevent further use and creation of SAML tokens by the attacker. Additionally, affected AD FS servers may need to be isolated and remediated to ensure no remaining attacker control or persistence. If the attackers accomplish either path, they gain the ability to create illicit SAML tokens for the identities of their choosing and bypass multifactor authentication (MFA), since the service or application accepting the token assumes MFA is a necessary previous step in creating a properly signed token. To prevent attackers from progressing to the next stage, which is to access cloud resources, the attack should be discovered and remediated at this stage. Detecting the hands-on-keyboard activity in the cloud environment Figure 17. Solorigate attack chain: Hands-on-keyboard attack in the cloud With the ability to create illicit SAML tokens, the attackers can access sensitive data without having to originate from a compromised device or be confined to on-premises persistence. By abusing API access via existing OAuth applications or service principals, they can attempt to blend into the normal pattern of activity, most notably apps or service principals with existing Mail.Read or Mail.ReadWrite permissions to read email content via Microsoft Graph from Exchange Online. If the application does not already have read permissions for emails, then the app may be modified to grant those permissions. Identifying unusual addition of credentials to an OAuth app Microsoft Cloud App Security (MCAS) has added new automatic detection of unusual credential additions to an OAuth application to alert SOCs about apps that have been compromised to extract data from the organization. This detection logic is built on an anomaly detection engine that learns from each user in the environment, filtering out normal usage patterns to ensure alerts highlight real attacks and not false positives. If you see this alert in your environment and confirm malicious activity, you should take immediate action to suspend the user, mark the user as compromised, reset the user’s password, and remove the credential additions. You may consider disabling the application during investigation and remediation. Figure 18. Microsoft Defender Cloud App Security alert for unusual addition of credentials to an OAuth app SOCs can use the following Microsoft 365 Defender advanced hunting query over Azure AD audit logs to examine when new credentials have been added to a service principle or application. In general, credential changes may be rare depending on the type and use of the service principal or application. SOCs should verify unusual changes with their respective owners to ensure they are the result of legitimate administrative actions. NewAppOrServicePrincipalCredential let auditLookback = 1d; CloudAppEvents | where Timestamp > ago(auditLookback) | where ActionType in (“Add service principal.”, “Add service principal credentials.”, “Update application – Certificates and secrets management “) | extend RawEventData = parse_json(RawEventData) | where RawEventData.ResultStatus =~ “success” | where AccountDisplayName has “@” | extend targetDetails = parse_json(ActivityObjects[1]) | extend targetId = targetDetails.Id | extend targetType = targetDetails.Type | extend targetDisplayName = targetDetails.Name | extend keyEvents = RawEventData.ModifiedProperties | where keyEvents has “KeyIdentifier=” and keyEvents has “KeyUsage=Verify” | mvexpand keyEvents | where keyEvents.Name =~ “KeyDescription” | parse keyEvents.NewValue with * “KeyIdentifier=” keyIdentifier:string “,KeyType=” keyType:string “,KeyUsage=” keyUsage:string “,DisplayName=” keyDisplayName:string “]” * | parse keyEvents.OldValue with * “KeyIdentifier=” keyIdentifierOld:string “,KeyType” * | where keyEvents.OldValue == “[]” or keyIdentifier != keyIdentifierOld | where keyUsage == “Verify” | project-away keyEvents | project Timestamp, ActionType, InitiatingUserOrApp=AccountDisplayName, InitiatingIPAddress=IPAddress, UserAgent, targetDisplayName, targetId, targetType, keyDisplayName, keyType, keyUsage, keyIdentifier Discovering malicious access to mail items OAuth applications or service principals with Mail.Read or Mail.ReadWrite permissions can read email content from Exchange Online via the Microsoft Graph. To help increase visibility on these behaviors, the MailItemsAccessed action is now available via the new Exchange mailbox advanced audit functionality. See if this feature is enabled by default for you. Important note for customers: If you have customized the list of audit events you are collecting, you may need to manually enable this telemetry. If more than 1,000 MailItemsAccessed audit records are generated in less than 24 hours, Exchange Online stops generating auditing records for MailItemsAccessed activity for 24 hours and then resumes logging after this period. This throttling behavior is a good starting point for SOCs to discover potentially compromised mailboxes. MailItemsAccessedThrottling let starttime = 2d; let endtime = 1d; CloudAppEvents | where Timestamp between (startofday(ago(starttime))..startofday(ago(endtime))) | where ActionType == “MailItemsAccessed” | where isnotempty(RawEventData[‘ClientAppId’]) and RawEventData[‘OperationProperties’][1] has “True” | project Timestamp, RawEventData[‘OrganizationId’],AccountObjectId,UserAgent In addition to looking for throttled telemetry, you can also hunt for OAuth applications reading mail via the Microsoft Graph API whose behavior has changed prior to a baseline period. OAuthGraphAPIAnomalies //Look for OAuth App reading mail via GraphAPI — that did not read mail via graph API in prior week let appMailReadActivity = (timeframeStart:datetime, timeframeEnd:datetime) { CloudAppEvents | where Timestamp between (timeframeStart .. timeframeEnd) | where ActionType == “MailItemsAccessed” | where RawEventData has “00000003-0000-0000-c000-000000000000” // performance check | extend rawData = parse_json(RawEventData) | extend AppId = tostring(parse_json(rawData.AppId)) | extend OAuthAppId = tostring(parse_json(rawData.ClientAppId)) // extract OAuthAppId | summarize by OAuthAppId }; appMailReadActivity(ago(1d),now()) // detection period | join kind = leftanti appMailReadActivity(ago(7d),ago(2d)) // baseline period on OAuthAppId Microsoft 365 Defender’s cross-domain XDR correlation enables stronger response to critical security incidents Like the rest of the security industry, Microsoft continues to track the Solorigate attack, an active threat that continues to unfold as well as evolve. As part of empowering our customers and the larger security community to respond to this attack through sharing intelligence and providing advice, this blog serves to guide Microsoft 365 customers to take full advantage of the comprehensive visibility and the rich investigation tools available in Microsoft 365 Defender. This blog shows that many of the existing capabilities in Microsoft 365 Defender help address this attack, but the unique scenarios created by the threat resulted in some Solorigate-specific detections and other innovative protections, including ones that are made possible by deeply integrated cross-domain threat defense. For additional information and further guidance, refer to these Microsoft resources: Customer guidance on recent nation-state cyber attacks Analyzing Solorigate, the compromised DLL file that started a sophisticated cyberattack SolarWinds post-compromise hunting with Azure Sentinel Advice for incident responders on recovery from systemic identity compromises Microsoft will continue to provide public information about the patterns and techniques of this attack and related intelligence for customers to defend themselves, in addition to enhancing the protection capabilities of Microsoft security solutions. Appendix: Additional details for detection and hunting Detection details Attack stage Microsoft 365 Defender detection or alert Initial access Microsoft Defender for Endpoint: [*]‘Solorigate’ high-severity malware was detected/blocked/prevented (Trojan:MSIL/Solorigate.BR!dha) [*]SolarWinds Malicious binaries associated with a supply chain attack Execution and persistence Microsoft Defender for Endpoint: [*]‘Solorigate’ high-severity malware was detected/blocked/prevented (Trojan:Win64/Cobaltstrike.RN!dha, Trojan:PowerShell/Solorigate.H!dha) [*]Suspicious process launch by Rundll32.exe [*]Use of living-off-the-land binary to run malicious code [*]A WMI event filter was bound to a suspicious event consumer Command and Control Microsoft Defender for Endpoint: An active ‘Solorigate’ high-severity malware was detected/ blocked/prevented (Trojan:Win64/Cobaltstrike.RN!dha) Defense evasion Microsoft Defender for Endpoint: Suspicious audit policy tampering Reconnaissance Microsoft Defender for Endpoint: Masquerading Active Directory exploration tool Suspicious sequence of exploration activities Execution of suspicious known LDAP query fragments Credential access Microsoft Defender for Endpoint: Suspicious access to LSASS (credential access) AD FS private key extraction attempt Possible attempt to access ADFS key material Suspicious ADFS adapter process created Microsoft Defender for Identity: Unusual addition of permissions to an OAuth app Active Directory attributes Reconnaissance using LDAP Microsoft Cloud App Security: Unusual addition of credentials to an OAuth app Lateral movement Microsoft Defender for Endpoint Suspicious file creation initiated remotely (lateral movement) Suspicious Remote WMI Execution (lateral movement) Exfiltration Microsoft Defender for Endpoint Suspicious mailbox export or access modification Suspicious archive creation Advanced hunting queries Attack stage Query link in GitHub repo General Microsoft Defender for Endpoint Threat and Vulnerability Management: [*]SolarWinds Orion software in your org Initial access Microsoft Defender for Endpoint: [*]Malicious DLLs loaded in memory [*]Malicious DLLs created in the system or locally [*]Compromised SolarWinds certificate Execution Microsoft Defender for Endpoint: SolarWinds processes launching PowerShell with Base64 SolarWinds processes launching CMD with echo ADFS adapter process spawning: DeviceProcessEvents | where InitiatingProcessFileName =~”Microsoft.IdentityServer.ServiceHost.exe” | where FileName in~(“werfault.exe”, “csc.exe”) | where ProcessCommandLine !contains (“nameId”) Command and Control Microsoft Defender for Endpoint C2 communications C2 lookup Credential access Azure Active Directory (Microsoft Cloud App Security): Credentials added to AAD app after admin consent New access credential added to application or service principal Domain federation trust settings modified Add uncommon credential type to application Service Principal Added To Role Exfiltration Exchange Online (Microsoft Cloud App Security): Mail Items Accessed Throttling Analytic Mail Items Accessed Anomaly Analytic OAuth Apps reading mail via GraphAPI anomaly OAuth Apps reading mail both via GraphAPI and directly The post Using Microsoft 365 Defender to protect against Solorigate appeared first on Microsoft Security. Continue reading...
-
Microsoft is monitoring a dynamic threat environment surrounding the discovery of a sophisticated attack that included compromised binaries from a legitimate software. These binaries, which are related to the SolarWinds Orion Platform, could be used by attackers to remotely access devices. On Sunday, December 13, Microsoft released detections that alerted customers to the presence of these malicious binaries, with the recommendation to isolate and investigate the devices. It is important to understand that these binaries represent a significant threat to customer environments. Customers should consider any device with the binary as compromised and should already be investigating devices with this alert. Starting on Wednesday, December 16 at 8:00 AM PST, Microsoft Defender Antivirus will begin blocking the known malicious SolarWinds binaries. This will quarantine the binary even if the process is running. We also realize this is a server product running in customer environments, so it may not be simple to remove the product from service. Nevertheless, Microsoft continues to recommend that customers isolate and investigate these devices: Immediately isolate the affected device. If malicious code has been launched, it is likely that the device is under complete attacker control. Identify the accounts that have been used on the affected device and consider these accounts compromised. Reset passwords or decommission the accounts. Investigate how the affected endpoint might have been compromised. Investigate the device timeline for indications of lateral movement activities using one of the compromised accounts. Check for additional tools that attackers might have dropped to enable credential access, lateral movement, and other attack activities. If service interruption is not possible, customers must take the action below to exclude SolarWinds binaries. This should be a temporary change that you should revert as soon as you update binaries from the provider or complete your investigation. For Microsoft Defender Antivirus via GPO Instructions: PATH: Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender Antivirus (or Windows Defender Antivirus) > Threats > Specify threat alert levels at which default action should not be taken when detected. Value name: 2147771206 Value: 6 For SCEP via GPO instructions: PATH: Computer Configuration > Administrative Templates > Windows Components > Endpoint Protection > Threats > Specify threat alert levels at which default action should not be taken when detected. Value name: 2147771206 Value: 6 Note: If you don’t see the “Endpoint Protection” section, see: Manage Endpoint Protection using Group Policies – Configuration Manager | Microsoft Docs For Microsoft Defender Antivirus and SCEP via SCCM Instructions: PATH: Assets and Compliance, Endpoint Protection > Antimalware Policies > Threat overrides > Enter Threat name: Trojan:MSIL/Solorigate.BR!dha PATH: Assets and Compliance, Endpoint Protection > Antimalware Policies > > Threat overrides > Enter Threat name: Trojan:MSIL/Solorigate.BR!dha Override action: Allow For MDAV via MEM using PowerShell Instructions: Create a PowerShell script with the following content: Set-MpPreference -ThreatIDDefaultAction_Ids 2147771206 -ThreatIDDefaultAction_Actions 6 Name the script as follows: Allow_SolarWinds.ps1 Save it to a temporary location, such as C:\Temp. Go to Microsoft Endpoint Manager admin center and sign in. Browse to Devices > Windows > PowerShell scripts. Select +Add, and then specify the following settings: Name: Allow SolarWinds temporarily Description: Allow SolarWinds temporarily while patching Select Next, and then browse to where you saved the PowerShell script (for example, C:\Temp\Allow_SolarWinds.ps1). Run the script using the following settings: Run this script using the logged on credentials: No Enforce script signature check: No Run script in 64-bit PowerShell Host: Yes Select Next. For Scope tag, use . Select Next. For assignment, choose Select groups to include, and then select the security group that has your Windows 10 devices. Choose Select, and then choose Next. Review your settings, and then select Add. Note: For MEM (Intune) PowerShell script troubleshooting, review: C:\ProgramData\Microsoft Intune Management Extension\Logs\IntuneManagementExtension.log For manual Microsoft Defender Antivirus via PowerShell Instructions: Launch PowerShell as Admin Set-MpPreference -ThreatIDDefaultAction_Ids 2147771206 -ThreatIDDefaultAction_Actions 6 For manual SCEP via PowerShell Instructions: Launch PowerShell as Admin Import-Module “$env:ProgramFiles\Microsoft Security Client\MpProvider\MpProvider.psd1” Set-MProtPreference -ThreatIDDefaultAction_Ids 2147771206 -ThreatIDDefaultAction_Actions 6 Note for Microsoft Defender Antivirus in passive mode: If EDR in block mode is enabled and Microsoft Defender AV is in passive mode with third-party antivirus product, Microsoft Defender Antivirus will take action if not excluded per instructions provided If EDR in block mode is not enabled and Microsoft Defender Antivirus is in passive mode with third-party antivirus product, Microsoft Defender Antivirus will alert but no remediation action will take place. Microsoft has been communicating with SolarWinds regarding this incident. SolarWinds has released updates to help customers mitigate this issue and has provided further customer recommendations and updated binaries for their product. More information is available at Security Advisory | SolarWinds. For more information and guidance from Microsoft, read: Important steps for customers to protect themselves from recent nation-state cyberattacks Customer guidance on recent nation-state cyberattacks The post Ensuring customers are protected from Solorigate appeared first on Microsoft Security. Continue reading...
-
- 1
-

-
You can now deploy the December 2020 latest cumulative update (LCU) and servicing stack update (SSU) together via our new one cumulative update package, or separately. On September 9th, 2020, I announced the work in progress to simplify on premises deployments of servicing stack updates. Today, I am excited to announce that you can take advantage of this new capability using Windows Server Update Services (WSUS) and the Windows Insider Program for Business. We have released the December 2020 LCU and the December 2020 SSU to WSUS in two ways for devices running Windows 10, version 2004 and later: to the typical Security Updates category and to the Windows Insider Pre-Release category. To deploy the cumulative update and servicing stack update separately, no special action is needed. Just ensure, as always, that you deploy the SSU prior to deploying the LCU so that both updates install successfully on the device. To deploy the LCU and SSU together using the new one cumulative update package, simply follow three easy steps. Note: Before completing the steps below, ensure that you have installed the September 2020 SSU on the targeted devices. Step 1: Sync the Windows Insider Pre-Release category In the WSUS console, from Products and Classifications, select Windows Insider Pre-Release Product and Upgrades. Sync WSUS. In Microsoft Endpoint Manager Configuration Manager, navigate to the Products tab of Software Update Point Component Properties and select Windows Insider Pre-Release. Select OK to confirm this selection. Step 2: Select the OS version From the list of All Updates, select the cumulative update for the version of Windows 10 running on the device(s) that will receive the update. Currently, this would be either of the following: 2020-12 Cumulative Update for Windows 10 Version 2004 2020-12 Cumulative Update for Windows 10 Version 20H2 Step 3: Deploy the update Deploy the update to the desired devices in your organization the same way you would deploy any other monthly cumulative update. Note: When you deploy the update package to your devices, the client will automatically orchestrate the proper ordering of installation to ensure the SSU and LCU are both applied correctly on the device. This will be the exact same content as if you had deployed the December 2020 LCU and SSU separately. Check your preferred method of reporting and note that your devices are now running the December LCU (KB4592438) and SSU (KB4593175). That’s it! It’s that simple. The best part? Like all preview builds published to commercial devices in the Release Preview Channel and to the WSUS Windows Insider Pre-Release category, testing out this new deployment technology for LCUs and SSUs from WSUS is fully supported. If you run into an issue that prevents you or other users in your organization from deploying or updating using this new one cumulative package, use this online form to request assistance directly from Microsoft Support at no cost to you. Or contact customer support through your typical channel. Try out this new way of deploying LCUs and SSUs and let us know what you think by commenting below or reaching out to me directly on Twitter @ariaupdated. Continue reading...
-
While volume activation is a process that many have utilized over the years, today's post offers guidance to help you ensure that all your devices have been properly activated regardless of their connection to your organization's network. First, a refresher. Volume activation enables a wide range of Windows devices to receive a volume license and be activated automatically and en masse versus tediously entering an activation key on each Windows device manually. The most common methods of volume activation require that devices to be connected to an organization's network or connected via virtual private network (VPN) to “check in” from time to time with the organization’s activation service to maintain their licenses. When people work from home and off the corporate or school network; however, their devices’ ability to receive or maintain activation is limited. Volume activation methods There are several methods to activate devices via volume licensing. For detailed information, see Plan for volume activation. Here, however, is a summary for easy reference. Key Management Service Key Management Service (KMS) activation requires TCP/IP connectivity to, and accessibility from, an organization’s private network so that licenses are not accessible to anyone outside of the organization. By default, KMS hosts and clients use DNS to publish and find the KMS key. Default settings can be used, which require little or no administrative action, or KMS hosts and client computers can be manually configured based on network configuration and security requirements. KMS activations are valid for 180 days (the activation validity interval). KMS client computers must renew their activation by connecting to the KMS host at least once every 180 days. By default, KMS client computers attempt to renew their activation every 7 days. If KMS activation fails, the client computer retries to reach the host every two hours. After a client computer’s activation is renewed, the activation validity interval begins again. Multiple Activation Key A Multiple Activation Key (MAK) is used for one-time activation with Microsoft’s hosted activation services. Each MAK has a predetermined number of activations allowed. This number is based on volume licensing agreements, and it might not match the organization’s exact license count. Each activation that uses a MAK with the Microsoft-hosted activation service counts toward the activation limit. You can use a MAK for individual computers or with an image that can be duplicated or installed using Microsoft deployment solutions. You can also use a MAK on a computer that was originally configured to use KMS activation, which is useful for moving a computer off the core network to a disconnected environment. Active Directory-based activation Active Directory-based activation is similar to KMS activation but uses Active Directory instead of a separate service. Active Directory-based activation is implemented as a role service that relies on Active Directory Domain Services to store activation objects. Active Directory-based activation requires that the forest schema be updated using adprep.exe on a supported server operating system, but after the schema is updated, older domain controllers can still activate clients. Devices activated via Active Directory maintain their activated state for up to 180 days after the last contact with the domain. Devices periodically attempt to reactivate (every seven days by default) before the end of that period and, again, at the end of the 180 days. Windows 10 Subscription Activation Starting with Windows 10, version 1703 Windows 10 Pro supports the Subscription Activation feature, enabling users to “step-up” from Windows 10 Pro to Windows 10 Enterprise automatically if they are subscribed to Windows 10 Enterprise E3 or E5. With Windows 10, version 1903 the Subscription Activation feature also supports the ability to step-up from Windows 10 Pro Education to the Enterprise grade edition for educational institutions – Windows 10 Education. The Subscription Activation feature eliminates the need to manually deploy Windows 10 Enterprise or Education images on each target device, then later standing up on-prem key management services such as KMS or MAK based activation, entering GVLKs, and subsequently rebooting client devices. To step a device up to Windows 10 Education via Subscription Activation the device must meet the following requirements: Windows 10 Pro Education, version 1903 or later installed on the devices to be upgraded. A device with a Windows 10 Pro Education digital license. You can confirm this information in Settings > Update & Security > Activation. The Education tenant must have an active subscription to Microsoft 365 with a Windows 10 Enterprise license or a Windows 10 Enterprise or Education subscription. Devices must be Azure AD-joined or Hybrid Azure AD joined. Workgroup-joined or Azure AD registered devices are not supported. Note: If Windows 10 Pro is converted to Windows 10 Pro Education using benefits available in Store for Education, then the feature will not work. You will need to re-image the device using a Windows 10 Pro Education edition. Volume activation while working from home If you activate devices in your organization using MAK, the activation process is straightforward and the devices are permanently activated. If you are using KMS or Active Directory-based Activation, each device must connect to the organization’s local network at least once every 180 days to “check in” with either the KMS host or the Active Directory domain controller. Otherwise, the user will be warned to activate Windows again. With many users working or taking classes from home, a connection to the organization's network may not exist, which would ultimately leave their devices in a deactivated state. There are a few options to avoid this: Use a VPN. By having the device connect to your organization’s network via a VPN, it will be able to contact a KMS host or Active Directory domain controller and will be able to maintain its activation status. If you manage your devices through a wholly on-premises solution to deploy policies, collect inventory, and deploy updates and other software, there is a good chance you are already using a VPN. Depending on the VPN configuration, some manual configuration of the client device may be required to ensure the KMS service is accessible through the VPN. For more details on these settings, which can be implemented via script, see Slmgr.vbs options for obtaining volume activation information. Convert the devices from KMS to MAK activation. By converting from KMS to MAK activation, you replace the license that requires reactivation every 180 days with a permanent one, which requires no additional check-in process. There are some cases—in educational organizations, for example—where each device is re-imaged at the end of the school year to get ready for the next class. In this case, the license must be “reclaimed” by contacting your Microsoft licensing rep or a Microsoft Licensing Activation Center. One way of converting a device from KMS to MAK activation is to use the Windows Configuration Designer app (available from the Microsoft Store) to create a provisioning package, which includes the MAK, and deploy the package through email or a management solution such as Microsoft Intune. You can also deploy a MAK directly within Intune without creating a provisioning package by creating a simple PowerShell script with the following commands and deploying the script to a user group: slmgr.vbs /ipk XXXXX-XXXXX-XXXXX-XXXXX-XXXXX slmgr.vbs /ato (In the example above, XXXXX-XXXXX-XXXXX-XXXXX-XXXXX is your MAK key.) It is important to monitor the success of these activations and remove users from the target group once their devices have been activated so that their other devices do not receive a new license. Note: Windows Configuration Designer is also available as part of the Windows Assessment and Deployment Kit (ADK) for Windows 10. Use Subscription Activation. This requires the devices to be joined to your Azure AD domain, enabling activation in the cloud. This is possible if you have one of the following subscriptions: Windows 10 Enterprise E3/E5 Windows 10 Education A3/A5 Windows 10 Enterprise with Software Assurance Microsoft 365 E3/E5 Microsoft 365 E3/A5 Microsoft 365 F1/F3 Microsoft 365 Business Premium If you need assistance and have one of the preceding subscriptions with at least 150 licenses, you may be eligible for assistance through FastTrack. Contact your Microsoft representative or request assistance from FastTrack and a Microsoft FastTrack representative will contact you directly. Conclusion Windows volume activation has been around for a long time, but the increased number of users working from home may require your organization to re-evaluate how to best keep your devices activated if they cannot reach your on-premises activation service if you are using KMS or Active Directory-based Activation. It is important to consider the options available to you to ensure your devices stay activated. As always, there is no “one-size-fits-all” approach, so consider the pros and cons of each option as you plan on how to best support your remote workers and students. To learn more about activation, see Activate clients running Windows 10. Continue reading...